Welcome to Instant Java Password and Authentication Security. In this book you will learn how to create strong and secure hashes to protect sensitive passwords and keys.
As an introduction, we will learn the basics of hashing using MD5 hashes to get familiarized with the concept.
Later, we will check out the Secure Hash Algorithm, which is a family of standard cryptographic hash functions. After learning the basics, we will see how to protect our hashes against certain types of attacks by salting them—a useful technique.
Of course, malicious hackers are always developing new techniques and technology evolves every day, and to keep up with this, we will learn how to use a very secure technique that allows us to strengthen our hashes over time.
This task involves a basic hashing technique to create basic MD5 hashes.
The following are the steps to create the initial hash (Signup):
- Get the password value as plain text.
- Get a
MD5 MessageDigestinstance. - Put the password in the
MessageDigestinstance. - Execute the
digestmethod to get the hash byte array. - Encode each byte to a Hexadecimal format into a String Builder.
- Get the built string from the
StringBuilderfunction. - The built String is a Hexadecimal representation of the
MD5Hash. - The password can now be stored.
The following is a screenshot of the code that allows us to perform the steps enumerated before; I've added comments to explain which step we are fulfilling in each piece of code:
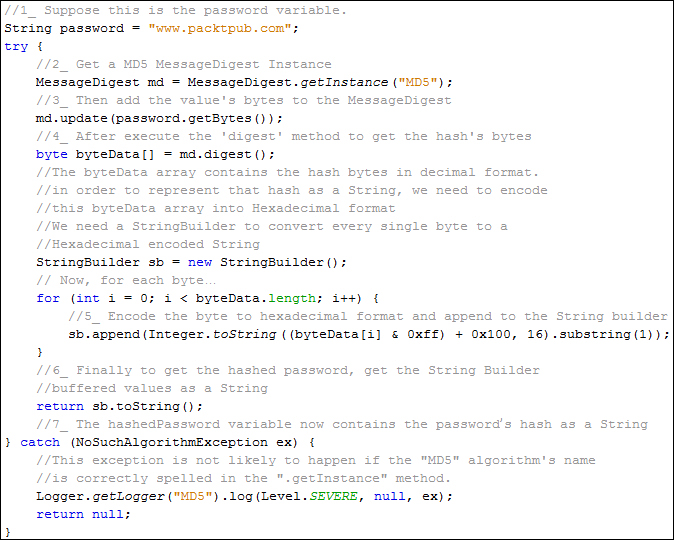
The hashed password can now be saved in the database instead of the plain text password. When the user logs in with his password, we need to create the hash again and compare it with the hash in the database. By doing this, the plain text password is never stored, so nobody knows the original password but the account owner.
MD5 is a cryptographic hash function that produces a 128-bit hash value (32 characters in length). It's very simple and straightforward; the basic idea is to map data sets of variable length to data sets of a fixed length. In order to do this, the input message is split into chunks of 512-bit blocks; padding is added so that its length can be divided by 512. Now these blocks are processed by the MD5 algorithm that operates in a 128-bit state and the result will be a 128-bit hash value.
But this algorithm has already been implemented; you only have to use it as in the example code.
Note that two very similar messages processed by the MD5 algorithm will result, most likely, in very different hashes.
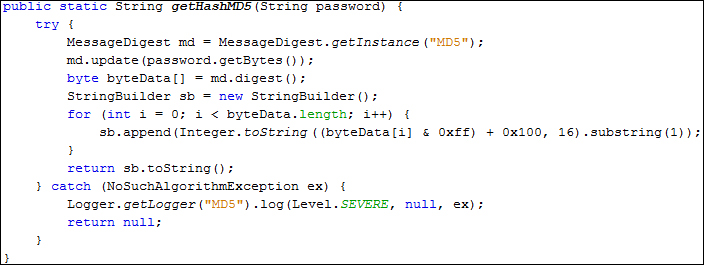
Let's wrap the previous code into a function, getHashMD5 (comments removed), as shown in the following screenshot:
Now, we can test our MD5 function by running the following code as shown in the screenshot:
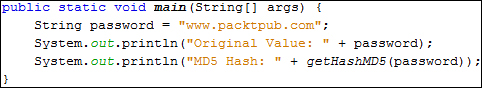
After executing the preceding code, we will get the following output as shown in the screenshot:
Congratulations! You have successfully generated your first MD5 Hash. I know it's exciting doing this for the first time, however, this is just the introduction, and I want to be very clear about this: never, and I mean never, use MD5 hashes for storing passwords; they are really weak and easy to break.
Although MD5 is a widely used hashing algorithm, it is far from being secure since MD5 generates fairly weak hashes.
- The advantages of MD5 hashes are as follows:
- Easy to implement
- Very fast in execution and cost-effective in resources
- The disadvantages of MD5 hashes are as follows:
- MD5 hashes are not collision resistant. This means different passwords can eventually result in the same hash
- Since it's fast in execution, it's susceptible to brute force and dictionary attacks
- Rainbow tables with words and generated hashes allow very quick searches for a known hash and also get the original word quickly
Even so, MD5 is useful to check Big Data consistency and it's better than plain text, but it's not a good option to keep really sensitive data (such as passwords) safe.
When we store a hashed password, it's virtually impossible to get the original value, or at least that's the idea. This is because a hash has only one way; unlike encryption, which has two ways (encrypt and decrypt), there is no "de-hash".
So, when a user forgets his password, we can't send him the original password to his e-mail account; instead, we can recover the password in the following two ways:
- Generate a new random password and send it to the user via e-mail, cell phone, and so on. It would be ideal if the system forces the user to change the password after resetting it.
- Generate a link with a code, which allows him to reset his password, and send that link to his e-mail. It's a good idea to make that code expire after a given time frame.
