5
OPERATING SYSTEM: MS-DOS AND WINDOWS
Chapter Outline
5.2 Operating System: Definition
5.3 Evolution of Operating System
5.1 INTRODUCTION
In the early days of computer use, computers were huge machines, which were expensive to buy, run, and maintain. The user at that time interacted directly with the hardware through machine language. A software was required which could perform basic tasks, such as recognising input from the keyboard, sending output to the display screen, keeping track of files and directories on the disk, and controlling peripheral devices such as printer and scanner. The search for such software led to the evolution of modern day operating system (OS). This software is loaded onto the top of memory and performs all the aforesaid basic tasks.
Initially, the operating systems provided a command line interface (CLI) to the users. This interface provides a command prompt, and the user has to type all the commands to perform various functions. As a result, the user had to memorise many commands. One of the most popular CLI-based operating systems is the Disk Operating System (DOS) developed by Microsoft. However, with the advancement in technology, operating system became more user-friendly by providing graphical user interface (GUI). The GUI-based operating system allows manipulation of software by using visual objects such as windows, pull-down menus, mouse pointers, and icons. Consequently, operating the computer became easy and intuitive. Microsoft Windows is one of the most popular series of GUI-based operating systems.
5.2 OPERATING SYSTEM: DEFINITION
An operating system is a collection of system programs that together controls the operation of a computer system. The operating system along with hardware, application and other system software, and users constitute a computer system. It is the most important part of any computer system. It acts as an intermediary between a user and the computer hardware. The operating system has two objectives, which are as follows:
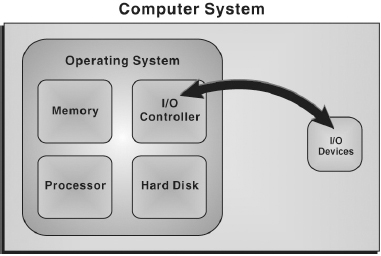
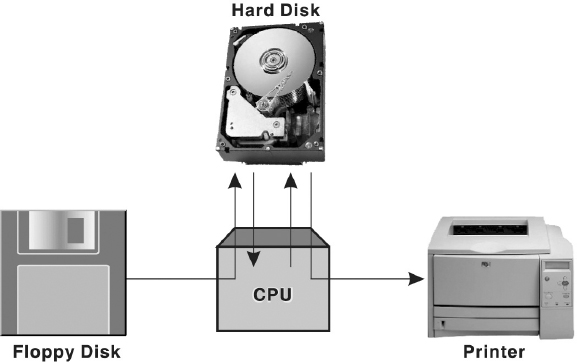
- Managing Hardware: The prime objective of the operating system is to manage and control various hardware resources of a computer system. These hardware resources include processor, memory, disk space, I/O devices, and so on. The operating system supervises which input device's data is requesting for being processed and which processed data is ready to be displayed on the output device. In addition to communicating with hardware, the operating system provides an error handling procedure and displays an error notification. If a device is not functioning properly, the operating system tries to communicate with the device again. If it is still unable to communicate with the device, it provides an error message notifying the user about the problem. Figure 5.1 illustrates how operating system manages the hardware resources of a computer system.
Figure 5.1 Managing Hardware
- Providing an Interface: The operating system organises applications so that users can easily access, use, and store them. When an application is opened, the operating system assists the application to provide the major part of the user interface. It provides a stable and consistent way for applications to deal with the hardware without the user having to know all the details of the hardware. If the application program is not functioning properly, the operating system again takes control, stops the application, and displays an appropriate error message.
Figure 5.2 Computer System Components
5.3 EVOLUTION OF OPERATING SYSTEM
In the early days, the computers lacked any form of operating system. The user would arrive at the machine armed with his program and data, often on punched paper tape. The program would be loaded into the machine and the machine set to work. Then came machines with libraries of support code (initial operating systems), which were linked to the user's program to assist in operations such as input and output. At this stage, operating systems were very diverse with each vendor producing one or more operating systems specific to its particular hardware. Typically, whenever new hardware architecture was introduced, there was a need of new operating system compatible with the new architecture. This state of affairs continued until 1960s when IBM developed the S/360 series of machines. Although there were enormous performance differences across the range, all the machines ran essentially the same operating system called S/360.
Then came the small 4 bit and 8 bit processors known as microprocessors. The development of microprocessors provided inexpensive computing for the small businesses. This led to the widespread use of interchangeable hardware components using a common interconnection and thus, an increasing need for standardised operating system to control them. The most important among the early operating systems was CP/M-80 for the 8080/8085/Z-80 microprocessors. With the development of microprocessors like 386, 486, and the Pentium series by Intel, the whole computing world got a new dimension. AT&T and Microsoft came up with character-based operating systems, namely, Unix and Disk Operating System, respectively which supported the prevalent hardware architectures. After the character-based operating systems, Microsoft and Apple Macintosh came with their Windows 3.1 and MAC, which were GUI-based operating systems and well suited for the Desktop PC market. Today, operating systems such as Windows XP and Red Hat Linux have taken the driver's seat in personal desktops. These operating systems with their remarkable GUI and network support features can handle diverse hardware devices.
5.4 TYPES OF OPERATING SYSTEM
The operating system has evolved immensely from its primitive days to the present digital era. From batch processing systems to the latest embedded systems, the different types of operating system can be classified into six broad categories:
- Batch Processing Operating System: This type of operating system was one of the first to evolve. Batch processing operating system allowed only one program to run at a time. These kinds of operating systems can still be found on some mainframe computers running batches of jobs. Batch processing operating system works on a series of programs that are held in a queue. The operating system is responsible for scheduling the jobs according to priority and the resources required. Batch processing operating systems are good at churning through large numbers of repetitive jobs on large computers. For example, this operating system would be best suited for a company wishing to automate their payrolls. A list of employees will be entered, their monthly salaries will be calculated, and corresponding pay slips would be printed. Batch processing is useful for this purpose since these procedures are to be repeated for every employee and each month.
- Multi-user or Time-sharing Operating System: This system is used in computer networks which allow different users to access the same data and application programs on the same network. The multi-user operating system builds a user database account, which defines the rights that users can have on a particular resource of the system.
- Multi-tasking Operating System: In this system, more than one process (task) can be executed concurrently. The processor is switched rapidly between the processes. Hence, a user can have more than one process running at a time. For example, a user on his computer can have a word processor and an audio CD player running at the same time. The multi-tasking operating system allows the user to switch between the running applications and even transfer data between them. For example, a user can copy a picture from an Internet opened in the browser application and paste it into an image editing application.
- Real-time Operating System (RTOS): This system is designed to respond to an event within a predetermined time. This kind of operating system is primarily used in process control, telecommunications, and so on. The operating system monitors various inputs which affect the execution of processes, changing the computers model of the environment, thus affecting the output, within a guaranteed time period (usually less than 1 second). As the real-time operating systems respond quickly, they are often used in applications such as flight reservation system, railway reservation system, military applications, etc.
- Multi-processor Operating System: This system can incorporate more than one processor dedicated to the running processes. This technique of using more than one processor is often called parallel processing. The main advantage of multi-processor systems is that they increase the system throughput by getting more work done in less time.
- Embedded Operating System: It refers to the operating system that is self-contained in the device and resident in ROM. Since embedded systems are usually not general-purpose systems, they are lighter or less resource intensive as compared to general-purpose operating systems. Most of the embedded operating systems also offer real-time operating system qualities. Typical systems that use embedded operating systems are household appliances, car management systems, traffic control systems, and energy management systems.
5.5 FUNCTIONS OF OPERATING SYSTEM
The main functions of a modern operating system are process management, memory management, file management, device management, security management, and user interface.
5.5.1 PROCESS MANAGEMENT
A process is an execution of a sequence of instructions or program by the central processing unit (CPU). It can also be referred as the basic unit of a program that the operating system deals with the help of the processor. For example, a text editor program running on a computer is a process. This program may cause several other processes to begin like it can furnish a request for printing while editing the document. Thus, we can say that the text editor is a program that initiates two processes—one for editing the text and second for printing the document.
Hence, a process is initiated by the program to perform an action, which can be controlled by the user or the operating system. A process in order to accomplish a task needs certain resources like CPU time, memory allocation, and I/O devices. Therefore, the idea of process management in an operating system is to accomplish the process assigned by the system or the user in such a way that the resources are utilised in a proper and efficient manner.
THINGS TO REMEMBER
States in a Process
A process changes various states during its lifetime where each state indicates the current activity of the process. These states are as follows:
- New: The process is being created.
- Ready: The process is ready to be assigned to the processor.
- Running: The process is being executed.
- Waiting: The process is waiting for signal from some other process.
- Terminated: The process has finished its execution.
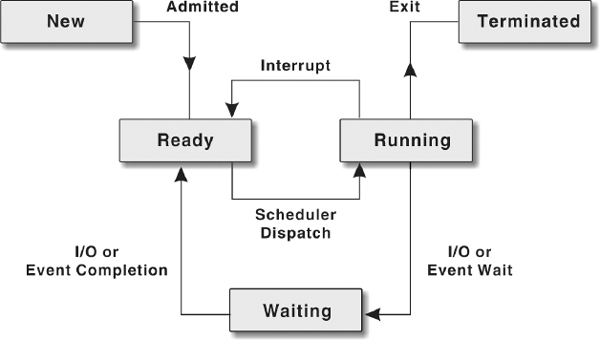
Life Cycle of a Process
The operating system is responsible for managing all the processes that are running on a computer and allocating each process a certain amount of time to use the processor. In addition, the operating system also allocates various other resources that processes need during execution such as computer memory or disk space. To keep track of all the processes, the operating system maintains a table known as the process table. This table stores many pieces of information associated with a specific process, that is, program counter, allocated resources, process state, CPU-scheduling information, and so on.
Initially, a process is in the new state. When it becomes ready for the execution and needs CPU, it switches to the ready state. Once the CPU is allocated to the process, it switches to the running state. From the running state, the process goes back to the ready state if an interrupt occurs or to the waiting state if the process needs some I/O operation. In case the process has switched to ready state, it again comes to running state after the interrupt has been handled. On the other hand, if the process has switched to waiting state, then after completion of I/O, it switches to ready state and then to running state. Thus, a process continues to switch among the ready, running, and waiting states during its execution. Finally, it switches to terminated state after completing its execution.
Figure 5.3 Life Cycle of a Process
Note: The change of the state of the process from one form to another is called context change and this course of action is known as context switching.
Let us consider the steps in an example of two processes, a text editor and a calculator, running simultaneously on a computer system.
| Step 1: | The operating system receives a request to open a text editor. |
| Step 2: | A new process for the text editor is initiated by the operating system. |
| Step 3: | Resources such as keyboard, memory, and hard disk are made available and the process enters in ready state. |
| Step 4: | The scheduler then dispatches the text editor in running state. |
| Step 5: | In the meantime, another process, a calculator is initiated by the user. |
| Step 6: | A new process is created by the operating system for the calculator. |
| Step 7: | Resources such as keyboard and memory are made available and this process enters in ready state. |
| Step 8: | Now as the calculator process is ready for the processor to work upon, the text editor process, if not terminated (finished), is kept in either waiting state or ready state. |
| Step 9: | The calculator process then attains the running state by the scheduler and when finished is terminated. |
| Step 10: | Then the text editor process again enters in the running state from ready state. |
Threads
A thread is a task that runs concurrently with other tasks within the same process. Also known as lightweight process, a thread is the simplest unit of a process. The single thread of control allows the process to perform only one task at one time. An example of a single thread in a process is a text editor where a user can either edit the text or perform any other task like printing the document. In a multi-tasking operating system, a process may contain several threads, all running at the same time inside the same process. It means that one thread of a process can be editing the text, while another is printing the document. Generally, when a thread finishes performing a task, it is suspended or destroyed.
Uniprogramming and Multiprogramming
As the name implies, uniprogramming means only one program at a time. In uniprogramming, users can perform only one activity at a time. In multiprogrammed systems, multiple programs can reside in main memory at the same time. These programs can be executed concurrently thereby requiring the system resources to be shared among them. In multiprogrammed systems, an operating system must ensure that all processes get a fair share of the CPU time.
FACT FILE
Multithreading
Writing a program where a process creates multiple threads is called multithread programming. It is the ability by which an OS is able to run different parts of the same program simultaneously. It offers better utilisation of processor and other system resources. For example, word processor makes use of multithreading—can check spelling in the foreground as well as save document in the background.
Process Scheduling
In a multiprogramed system, at any given time, several processes will be competing for the CPU's time. Thus, a choice has to be made which process to allocate the CPU next. This procedure of determining the next process to be executed on the CPU is called process scheduling and the module of operating system that makes this decision is called scheduler. The prime objective of scheduling is to switch the CPU among processes so frequently that users can interact with each program while it is running.
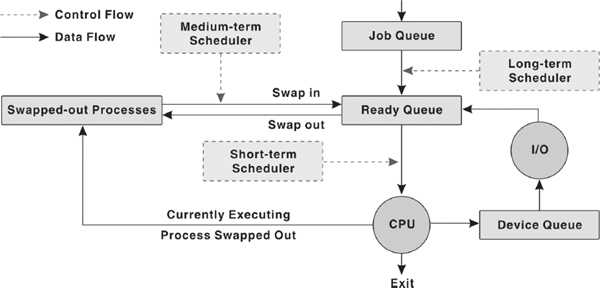
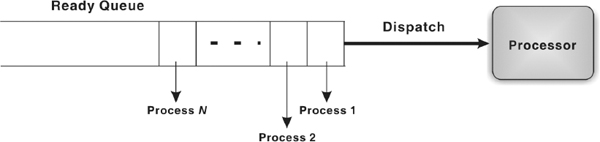
For scheduling purposes, there exist different queues in the system: job queue, ready queue, and device queue. As the processes enter the system for execution, they are kept into job queue (or input queue) on a mass storage device such as hard disk. From the job queue, the processes which are ready for the execution are brought into the main memory. In the main memory, these processes are kept into ready queue. In other words, the ready queue contains all those processes that are waiting for the CPU. For each I/O device attached to the system, a separate device queue is maintained. The process that needs to perform I/O during its execution is kept into the queue of that specific I/O device and waits there until it is served by the device.
Depending on the level of scheduling decisions to be made, the following types of schedulers may coexist in a complex operating system:
- Long-term Scheduler: Also known as job scheduler or admission scheduler works with the job queue. It selects the next process to be executed from the job queue and loads it into the main memory for execution. This scheduler is generally invoked only when a process exits from the system. Thus, the frequency of invocation of long-term scheduler depends on the system and workload and is much lower than other two types of schedulers.
- Short-term Scheduler: Also known as CPU scheduler selects a process from the ready queue and allocates CPU to it. This scheduler is required to be invoked frequently as compared to long-term scheduler. This is because generally a process executes for a short period and then it may have to wait either for I/O or some other reason. At that time, CPU scheduler must select some other process and allocate CPU to it. Thus, the CPU scheduler must be fast in order to provide the least time gap between executions.
- Medium-term Scheduler: Also known as swapper comes into play whenever a process is to be removed from the ready queue (or from the CPU in case it is being executed) thereby reducing the degree of multiprogramming. This process is stored at some space on the hard disk and later brought into the memory to restart execution from the point where it left off. This task of temporarily switching a process in and out of main memory is known as swapping. The medium-term scheduler selects a process among the partially executed or unexecuted swapped-out processes and swaps it in the main memory. The medium-term scheduler is usually invoked when some space becomes free in memory by the termination of a process or the supply of ready process reduces below a specified limit.
Figure 5.4 Types of Schedulers
Preemptive and Nonpreemptive Scheduling
CPU scheduling may take place under the following four circumstances:
- When a process switches from the running state to waiting state.
- When a process switches from the running state to ready state.
- When a process switches from the waiting state to ready state.
- When a process terminates.
When scheduling takes place under ‘first’ and ‘fourth’ circumstances, it is said to be nonpreemptive scheduling and if the scheduling takes place under ‘second’ and ‘third’ circumstances, it is said to be preemptive. In preemptive scheme, the scheduler can forcibly remove the processor from the currently running process before its completion in order to allow some other process to run. In nonpreemptive scheme, once the processor is allocated to a process, it cannot be taken back until the process voluntarily releases it (in case the process has to wait for I/O or some other event) or the process terminates. Thus, the main difference between the two schemes is that in preemptive scheme, the operating system has the control over the process current states whereas in case of nonpreemptive scheme, the process once entered in running state gets the full control of the processor.
The scheduler uses some scheduling procedure to carry out the selection of a process for execution. Two popular scheduling procedures implemented by different operating systems are First-Come-First-Served and Round Robin scheduling.
- First-Come-First-Served (FCFS): As the name suggests, in FCFS, the processes are executed in the order of their arrival in the ready queue, which means the process that enters the ready queue first, gets the CPU first. To implement FCFS scheduling procedure, the ready queue is managed as a FIFO (First-in First-out) queue. Each time, the process at the start of queue is dispatched to the processor and all other processes move up one slot in the queue. When new processes arrive, they are put at the end of the queue. FCFS falls under non-preemptive scheduling and its main drawback is that a process may take a very long time to complete, and thus holds up other waiting processes in the queue.
Figure 5.5 First-Come-First-Served Procedure
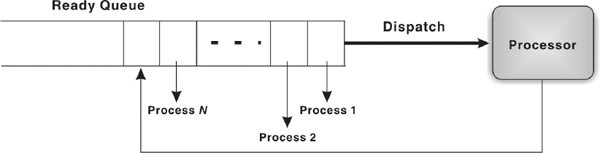
- Round Robin: Round Robin scheduling was designed keeping in mind the limitations of the FCFS scheduling procedure. This procedure falls under preemptive scheduling in which a process is selected for execution from the ready queue in FIFO sequence. However, the process is executed only for a fixed period known as time slicing or quantum period after which it will be interrupted and returned to the end of the ready queue. In Round Robin procedure, processes are allocated the CPU time on a turn basis.
Figure 5.6 Round Robin procedure
Nowadays, it is common in operating systems for processes to be treated according to priority. This may involve a number of different queues and scheduling mechanisms, using priority based on previous process activity. For example, time required by the process for execution or how long it has been, since it was last executed by the processor.
Deadlock
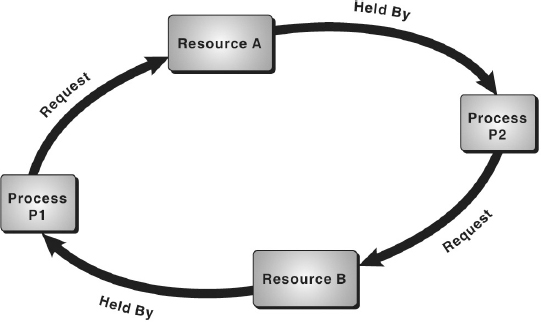
In a multiprogramming environment, several processes may compete for a limited number of resources. A process requests for the required resource and if it is not available then the process enters in the waiting state and remains in that state until it acquires the resource. There might be a situation when the process has to wait endlessly because the requested resource may be held by other waiting process. This type of situation is known as deadlock. To illustrate the deadlock situation, consider a system with two resources (say, printer and disk drive) and two processes P1 and P2 running simultaneously. During execution, P1 requests for printer and P2 for disk drive. As the requested resources are available, the request of both P1 and P2 is granted and the desired resources are allocated to them. Further, P1 requests for disk drive held by P2 and P2 requests for printer held by P1. Here, both processes will enter in waiting state. Since each process is waiting for the release of resource held by other, they will remain in waiting state forever, thus producing a deadlock.
Figure 5.7 Deadlock
A deadlock situation arises if the following four conditions hold simultaneously on the system:
- Mutual Exclusion: Only one process can use a resource at a time. If another process requests for the resource, the requesting process has to wait until the requested resource is released.
- Hold and Wait: In this situation, a process might be holding some resource while waiting for additional resource, which is currently being held by other process.
- No Preemption: Resources cannot be preemptive, that is, resources cannot be forcibly removed from a process. A resource can only be released voluntarily by the holding process, after that process has completed its task.
- Circular Wait: This situation may arise when a set of processes waiting for allocation of resources held by other processes forms a circular chain in which each process is waiting for the resource held by its successor process in the chain.
To ensure that deadlocks never occur, the system can use either a deadlock-prevention or a deadlock-avoidance scheme.
- Deadlock Prevention: Deadlock can occur only when all the four deadlock causing conditions hold true. Hence, the system should ensure that at least one of the four deadlock causing conditions would not hold true so that deadlock can be prevented.
- Deadlock Avoidance: Additional information concerning which resources a process will require and use during its lifetime should be provided to the operating system beforehand. For example, in a system with one CD drive and a printer, process P might request first for the CD drive and later for the printer, before releasing both resources. On the other hand, process Q might request first for the printer and the CD drive later. With this knowledge in advance, the operating system will never allow allocation of a resource to a process if it leads to a deadlock thereby avoiding the deadlock.
5.5.2 MEMORY MANAGEMENT
In addition to managing processes, the operating system also manages the primary memory of the computer. The part of the operating system that handles this job is called the memory manager. Since every process must have some amount of primary memory to execute, the performance of the memory manager is crucial to the performance of the entire system. As the memory is central to the operation of any modern operating system, its proper use can make a huge difference. The memory manager is responsible for allocating main memory to processes and for assisting the programmer in loading and storing the contents of the main memory. Managing the main memory, sharing, and minimising memory access time are the basic goals of the memory manager. The major tasks accomplished by the memory manager so that all the processes function in harmony, are:
- Relocation: Each process must have enough memory to execute.
- Protection and Sharing: A process should not run into another process's memory space.
Relocation
When a process is to be executed, it has to be loaded from the secondary storage (like hard disk) to the main memory (RAM). This is called process loading. Since, main memory is limited and other processes also need it for their execution, an operating system swaps the two processes, which is called swapping. Once the process is “swapped out”, it is uncertain to tell when it will be “swapped in” because of the number of processes running concurrently.
Normally, when the process is swapped back into main memory, it will be placed back to the same memory space that it occupied previously. However, in certain cases, it is not possible to place the process at the same memory location. This is not of much importance if the process is not address-sensitive. However, if the process requires some of its data or instruction to occupy memory with specific address, the process needs to be relocated. It is the responsibility of the memory manager to modify the addresses used in address-sensitive instructions (that use memory addresses) of the process so that it can execute correctly from the assigned area of memory.
Figure 5.8 Process Swapping
Protection and Sharing
In multiprogrammed systems, as a number of processes may reside in main memory at the same time, there is a possibility that a user program during execution may access the memory location allocated either to other user processes or to the operating system. It is the responsibility of the memory manager to protect the operating system from being accessed by other processes and the processes from one another. At the same time, the memory protection program should be flexible enough to allow concurrent processes to share the same proportion of the main memory. For example, consider a program that initiates different processes. If the memory manager allocates the same portion of memory to all the processes instead of different memory allocations to different processes, a lot of memory is saved. Therefore, the memory protection routine of the operating system should allow controlled sharing of the memory among different processes without letting them breach the protection criteria. If a process attempts to modify the contents of memory locations that do not belong to it, the memory protection routine intervenes and usually terminates the program.
Memory Allocation
In uniprogramming systems, where only one process runs at a time, memory management is very simple. The process to be executed is loaded into the part of memory space that is unused. Early MS-DOS systems support uniprogramming. The main challenge of efficiently managing memory comes when a system has multiple processes running at the same time. In such a case, the memory manager can allocate a portion of primary memory to each process for its own use. However, the memory manager must keep track of the running processes along with the memory locations occupied by them, and must also determine how to allocate and de-allocate available memory when new processes are created and old processes have finished their execution respectively
While different strategies are used to allocate space to processes competing for memory, three of the most popular are:
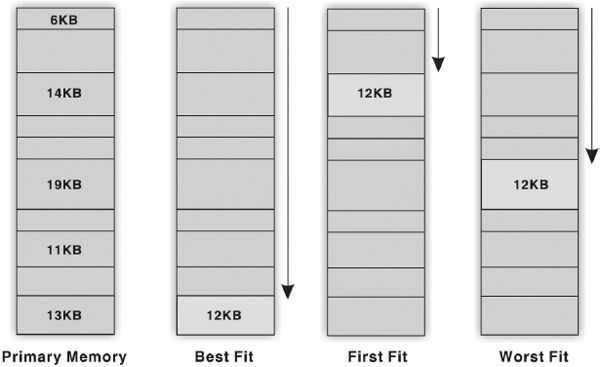
- Best Fit: In this case, the memory manager places a process in the smallest block of unallocated memory in which it will fit. For example, a process requests 12KB of memory and the memory manager currently has a list of unallocated blocks of 6KB, 14KB, 19KB, 11KB, and 13KB blocks. The best fit strategy will allocate 12KB of the 13KB block to the process.
- First Fit: The memory manager places the process in he first unallocated block that is large enough to accommodate the process. Using the same example to fulfil 12KB request, first fit will allocate 12KB of the 14KB block to the process.
- Worst Fit: The memory manager places a process in the largest block of unallocated memory available. To furnish the 12KB request again, worst fit will allocate 12KB of the 19KB block to the process, leaving a 7KB block for future use.
Figure 5.9 Strategies for Memory Allocation
Figure 5.9 illustrates that in best fit and first fit strategies, the allocation of memory results in the creation of a tiny fragment of unallocated memory. Since the amount of memory left is small, no new processes can be loaded here. This job of splitting primary memory into segments as the memory is allocated and de-allocated to the processes is known as fragmentation. The worst fit strategy attempts to reduce the problem of fragmentation by allocating the largest fragments to the new processes. Thus, a larger amount of space in the form of tiny fragments is left unused. To overcome this problem, concept of paging was introduced.
Paging
Paging is a memory management scheme that allows the processes to be stored non-contiguously in memory. The memory is divided into fixed size chunks called page frames. The operating system breaks the program's address space (the collection of addresses used by the program) into fixed size chunks called pages, which are of same size as that of page frames. Generally, page size is of 4KB. However, some systems support even larger page sizes such as 8KB, 4MB, etc. When a process is to be executed, its pages are loaded into unallocated page frames (not necessarily contiguous).
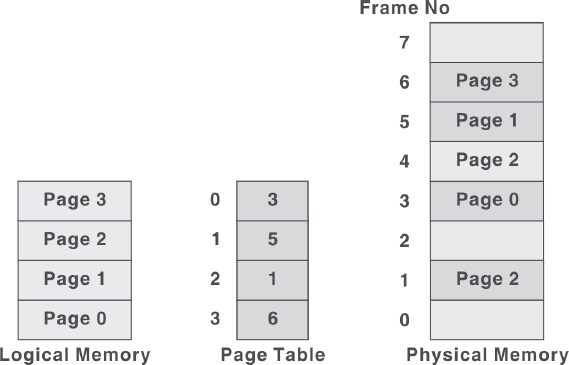
Each address generated by CPU (that is, logical address) is divided into two parts: page number (high-order bits) and a page offset or displacement (low-order bits). Since the logical address is a power of 2, the page size is always chosen as a power of 2 so that the logical address can be converted easily into page number and page offset. To map the logical addresses to physical addresses in memory, a mapping table called page table is used. The operating system maintains a page table for each process to keep track of which page frame is allocated to which page. It stores the frame number allocated to each page and the page number is used as index to the page table. Figure 5.10 shows the logical memory, page table, and physical memory.
Figure 5.10 Logical Memory, Page Table, and Physical Memory
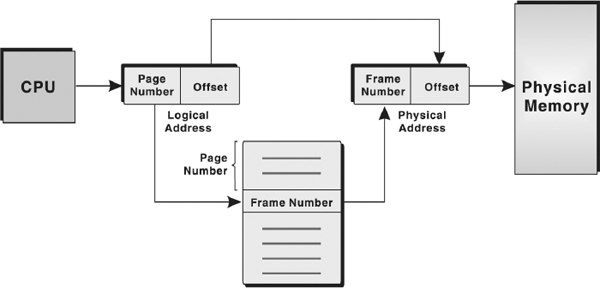
Now let us see how address translation is performed in paging. To map a given logical address to the corresponding physical address, the system first extracts the page number and the offset. The system, in addition, also checks whether the page reference is valid (that is, it exists within the logical address space of the process). If the page reference is valid, the system uses the page number to find the corresponding page frame number in the page table. That page frame number is attached to the high-order end of the page offset to form the physical address in memory. The mechanism of translation of logical address into physical address is shown in Figure 5.11.
The main advantage of paging is that it minimises the problem of fragmentation since memory allocated is always in fixed units and any free frame can be allocated to a process.
THINGS TO REMEMBER
Physical and Logical Address
Every byte in memory has a specific address known as physical address. Whenever a program is brought into main memory for execution, it occupies certain memory locations. The set of all physical addresses used by the program is known as its physical address space. However, before execution, a program is compiled to run starting from some fixed address and accordingly all the variables and procedures used in the program are assigned some specific address known as logical address. The set of all logical addresses used by the program is known as its logical address space.
Figure 5.11 Address Translation in Paging
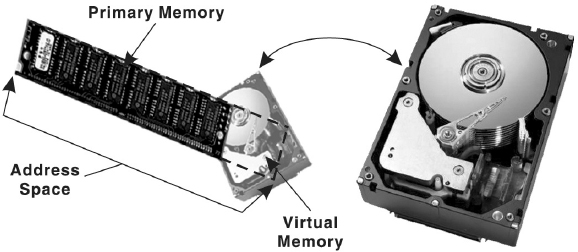
Concept of Virtual Memory
A process executes only in the main memory, which is limited in size. Today with the advent of graphic-oriented applications like 3D video games, business applications, and so on, a user requires large memory for running such applications than the main memory. Note that it is not essential that the whole program must be loaded in the main memory for processing as only the currently referenced page needs to be present in the memory at the time of execution. Therefore, the remaining pages of the program can reside in a hard disk portion allocated as virtual memory and can be loaded into main memory whenever needed. This process of swapping the pages from the virtual memory to main memory is called page-in or swap-in. With virtual memory, the system can run programs that are actually larger than the primary memory of the system. Virtual memory allows for very effective multiprogramming and relieves the user from the unnecessarily tight constraints of main memory.
Virtual memory, in other words, is a way of showing the main memory of a computer system to appear effectively larger than it really is. The system does this by determining which parts of its memory are often sitting idle, and then makes a command decision to empty their contents onto a disk, thereby freeing up precious RAM.
Note: In virtual memory systems, the logical address is referred to as virtual address and logical address space is referred to as virtual address space.
Figure 5.11 Virtual Memory
Page Faults
In virtual memory systems, the page table of each process stores an additional bit to differentiate the pages in main memory from that on the hard disk. This additional bit is set to 1 in case the page is in main memory; otherwise 0. Whenever a page reference is made, the operating system checks the page table to determine whether the page is main memory. If the referenced page is not found in the main memory, a page fault occurs and the control is passed to the page fault routine in the operating system. To handle page fault, the page fault routine first of all checks whether the virtual address for the desired page is valid (that is, it exists within the virtual address space of the process). If it is invalid, it terminates the process giving error. Otherwise, it locates for a free page frame in memory and allocates it to the process, swaps the desired page into this allocated page frame, and updates the page table to indicate that the page is in memory.
While handling page fault, there is a possibility that the memory is full and no free frame is available for allocation. In that case, the operating system has to evict a page from the memory to make space for the desired page to be swapped in. To decide which page frame is to be replaced with new page, the operating system must track the usage information for all pages. In this way, the operating system can determine which pages are being actively used and which are not (and therefore, can be removed from the main memory). Often the ‘least currently accessed’ page (the page that has gone the longest time without being referenced) is selected.
5.5.3 FILE MANAGEMENT
File system is one of the most visible aspects of the operating system. It provides a uniform logical view of the information storage, organised in terms of files, which are mapped onto the underlying physical device like hard disk. While the memory manager is responsible for the maintenance of primary memory, the file manager is responsible for the maintenance of the file system. In the simplest arrangement, file system contains a hierarchical structure of data. This file system maintains user data and meta-data (the data describing the files of user data). The hierarchical structure usually contains the metadata in the form of directories of files and sub-directories. Each file is a named collection of data stored on the disk. The file manager implements this abstraction and provides directories for organising files. It also provides a spectrum of commands to read/write the contents of a file, to set the read/write position, to use the protection mechanism, to change the ownership, to list files in a directory, and to remove a file. The file manager provides a protection mechanism to allow users to administer how processes executing on behalf of different users can access the information contained in different files.
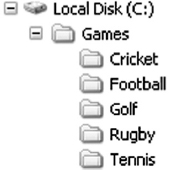
The file manager also provides a logical way for users to organise files in the secondary storage. To assist users, most file managers allow files to be grouped into a bundle called a directory or a folder. This allows a user to organise his or her files according to their purpose by placing related files in the same directory. By allowing directories to contain other directories, called sub-directories, a hierarchical organisation can be constructed. For example, a user may create a directory called Games that contains sub-directories called Cricket, Football, Golf, Rugby, and Tennis (see Figure 5.13). Within each of these sub-directories are files that fall within that particular category. A sequence of directories within directories is called a directory path.
Figure 5.13 File System
5.5.4 DEVICE MANAGEMENT
Device management in an operating system refers to the process of managing various devices connected to the computer. The device manager manages the hardware resources and provides an interface to hardware for application programs. A device communicates with the computer system by sending signals over a cable. The device communicates with the machine through a connection point called port. The communication using port is done through rigidly defined protocols, like when to send the data and when to stop. These ports are consecutively connected to a bus (a set of wires) which one or more device uses to communicate with the system. The operating system communicates with the hardware with the help of standard software provided by the hardware vendor called device drivers. Device driver works as a translator between the electrical signals from the hardware and the application programs of the operating system. Drivers take data that the operating system has defined as a file and translate them into streams of bits placed in specific locations on storage devices. There are differences in the way that the driver program functions, but most of them run when the device is required, and function much the same as any other process. The operating system will frequently assign processes based on priority to drivers so that the hardware resources can be released and set free for further use.
Broadly, managing input and output is a matter of managing queues and buffers. A buffer is a temporary storage area that takes a stream of bits from a device like keyboard to a serial communication port. Buffers hold the bits and then release them to the CPU at a convenient rate so that the CPU can act on it. This task is important when a number of processes are running and taking up the processor's time. The operating system instructs a buffer to continue taking the input from the device. In addition, it also instructs the buffer to stop sending data back to the CPU if the process, using the input, is suspended. When the process, requiring input, is made active once again, the operating system will command the buffer to send data again. This process allows a keyboard to deal with external users at a higher speed.
Spooling
SPOOL is an acronym for Simultaneous Peripheral Operation On-line. Spooling refers to storing jobs in a buffer so that CPU can be efficiently utilised. Spooling is useful because devices access data at different rates. The buffer provides a waiting station where data can rest while the slower device catches up. The most common spooling application is print spooling. In print spooling, documents are loaded into a buffer, and then the printer pulls them off from the buffer at its own rate. Meanwhile, a user can perform other operations on the computer while the printing takes place in the background. Spooling also lets a user place a number of print jobs on a queue instead of waiting for each one to finish before specifying the next one. The operating system manages all requests to read or write data from hard disk through spooling.
Figure 5.14 Spooling
5.5.5 SECURITY MANAGEMENT
Security in terms of a computer system covers every aspect of its protection in case of a catastrophic event, corruption of data, loss of confidentiality, and so on. Security requires not only ample protection within the system, but from the external environment also, in which the system operates. In this section, we will be covering security in terms of internal protection, which is one of the most important functions of the operating system. This involves protecting information residing in the system from unauthorised access. Various security techniques employed by the operating system to secure the information are user authentication and backup of data.
User Authentication
The process of authenticating users can be based on a user's possession like a key or card, user information like the username and password or user attributes like fingerprints and signature. Apart from these techniques, user information is often the first and most significant line of defence in a multi-user system. After the user identifies himself by a username, he is prompted for a password. If the password supplied by the user matches the password stored in the system, the system authenticates the user and gives him access to the system. A password can also be associated with other resources (files, directories, and so on), which when requested, prompts the user for password. Unfortunately, passwords can often be guessed, illegally transferred, or exposed. To avoid such situations, a user should keep the following points in mind:
- Password should be at least six characters in length.
- The system should keep track of any event about any attempt to break the password.
- The system should allow limited number of attempts for submitting a password on a particular system.
- Password based on dictionary words should be discouraged by the system. Alphanumeric passwords, such as PASS011, should be used.
Backup of Data
No matter what kind of information a system contains, backup of data is of utmost importance for its users. Backup or archiving is an important issue for a user and especially for business organisations. Typically, a computer system uses hard drives for online data storage. These drives may sometimes fail, or can be damaged in case of a catastrophic event, so care must be taken to ensure that the data is not lost. To ensure this, operating system should provide a feature of backing up of data, say from a disk to another storage device such as a floppy disk or an optical disk. The purpose of keeping backups is to restore individual files or complete file system in case of data loss. Recovery from the loss of an individual file, or of an entire disk, may be done from backup. Operating system usually provides some system software that is used for taking backups of the data.
5.5.6 USER INTERFACE
Operating system organises applications so that users can easily access them, use them, and store application data. When an application is opened, the operating system lets the application provide the majority of the user interface. The operating system still has the responsibility of providing access to the hardware for whatever the application needs. If the program cannot function properly, the operating system again takes control, stops the application, and displays an error message. An effective interface of an operating system does not concern the user with the internal workings of the system. A good user interface should attempt to anticipate the user's requirements and assist him to gather information and use necessary tools. Common interfaces provided by different operating systems can be categorised as Command Line Interface (CLI) and Graphical User Interface (GUI).
Figure 5.15 Command Line Interface
Command Line Interface (CLI)
In early days of computing, operating systems provided the user with the facility of entering commands via an interactive terminal. Those were the only means of communication between a program and its user, based solely on textual input and output. Commands were used to initiate programs, applications, and so on. A user had to learn many commands for proper operation of the system.
Graphical User Interface (GUI)
With the the development in chip designing technology, computer hardware became quicker and cheaper, which led to the birth of GUI-based operating system. These operating systems provide users with pictures rather than just characters to interact with the machine. The operating system displays icons, buttons, dialog boxes, etc., on the screen. The user sends instructions by moving a pointer on the screen (generally mouse) and selecting certain objects by pressing buttons on the mouse while the mouse pointer is pointing at them.
Figure 5.16 Graphical User Interface
5.6 WORKING WITH MS-DOS
The Disk Operating System is a single user operating system released by Microsoft in the early 80's. DOS, also known as MS-DOS, is a command line user interface, which enables users to organise data files, load and execute (run) program files, and control the input and output devices attached to the computer. Every operation that can be performed with a GUI can also be performed with DOS.
MS-DOS Environment
The DOS environment gives the user a quick and direct access to the basic utilities of a computer. All tasks are accomplished by typing commands at a command prompt (at the cursor location). A prompt is defined as a character or string of characters used in the command line interface to indicate that a computer is ready to accept commands from users. In DOS, ‘>’ is used as a prompt, which is preceded by other information such as current drive and path of the current working directory. (see Figure 5.17) To display the command prompt, Click Start, point to All Programs, point to Accessories, and then select Command Prompt from the submenu that appears.
Figure 5.17 Command Prompt
THINGS TO REMEMBER
File Naming Conventions
For naming a file, certain rules are followed in DOS, which are:
- A filename can consist of characters (a to z), numbers (0 to 9), and other characters ($, #, @, !, %, (), -, ~, ^).
- Characters such as /, , [], <, >, +, =, ;, :, ?, *, {} are not allowed in a filename.
- DOS is not case-sensitive. This implies that upper and lower case letters can be used interchangeably.
- Blank spaces are not allowed.
Working with Files and Directories
This section introduces the most fundamental aspects of using computer, working with files, and organizing those files into directories.
- File: A file is a primary unit of storage in computers. DOS uses a unique filename to describe the content of a file and keep track of the file so that you can use it later. In DOS, the name of a file is divided into two parts: the filename itself and an extension. For example, the filename Stu.doc has two parts, namely, Stu (filename) and .doc (extension). The filename consists of one to eight characters and the extension consists of one to three characters. The file extension is optional, but it is advisable to use it as it describes the content of the file. DOS uses different file extensions such as .com, .exe, .bat, .txt, etc.
- Directory: Files are organised under different directories. A directory allows users to group files under one category. Every disk has one basic directory called the root directory, which is created automatically when the disk is formatted. In addition to files, a directory can contain other directories also in itself known as subdirectories. Each subdirectory can hold files and further subdirectories. The number of subdirectories on a disk is limited only by the amount of storage space on the disk.
- Pathname: To access a file, a user may have to traverse through different directories. Thus, a pathname is used to instruct the computer where to look for any particular file. A pathname is a sequence of directories separated by a backslash (‘’) followed by a filename. For example, the pathname for a file named STU can be C:StudentDetailsStu.doc. In this pathname, C drive contains a directory Student in which Details is a subdirectory where the file Stu.doc is stored. A pathname can be either absolute or relative. An absolute pathname mentions the path to a specific file from the root directory while a relative pathname mentions the path to a specific file from the current working directory and does not begin with ‘’.
Note: For both files and directories, the same naming conventions are used.
5.6.1 USING MS-DOS COMMANDS
In MS-DOS, commands are used to perform different operations such as copying files, deleting files, creating a directory, etc. In an operating system, a command is defined as a directive given to the computer to perform a specific operation. MS-DOS commands are broadly classified into two categories, namely, internal and external.
FACT FILE
Wild Card Characters
MS-DOS allows using two special characters known as wild card characters * asterisk and? (question mark) in the filenames or extension or both while using DOS commands. The character* means matching files having any number of characters in place of* in their name while the character? means matching files having any character in place of? in their name. For example, S*.doc means all the file names starting with the character S, followed by any number of characters and having an extension .doc. On the other hand, S?? .doc means all the file names starting with the character S, followed by any two characters and having an extension .doc.
Internal MS-DOS Commands
The internal commands are built into the operating system as part of a file called COMMAND. COM, which is loaded into the main memory during the booting process. The internal commands are easy to execute as they are present in the main memory as long as the computer is on and do not need to be located on the hard drive. Some of the most commonly used internal DOS commands are:
- DATE: It is used to display or set the system date. The syntax of this command is:
DATE [/T]
Where
[/T] displays only the current date.
For example, to display the current date, use the following command.
C:>DATE/T 15/03/2010If you type the DATE command without any parameter (/T), DOS displays the current date and prompts you to enter a new date as shown below:
C:>DATE The current date is: 15/03/2010 Enter the new date: (dd-mm-yy)_Press the Enter key to keep the same date.
Note: The parameter specified within square brackets [] is optional.
- TIME: It is used to display or set the system time. The syntax of this command is:
TIME [/T]
Where
[/T] displays only the current time.
For example, to display the current time, use the following command.
C:>TIME/T 03:59 PMLike DATE command, if you type the TIME command without any parameter (/T), DOS displays the current system time and prompts you to enter a new system time.
C:>TIME The current time is: 15:59:08.18 Enter the new time:_Press the Enter key to keep the same time.
- CLS: It is used to clear the screen. The syntax of this command is:
CLS
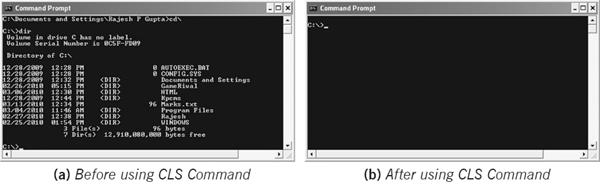
Figure 5.18(a) and 5.18(b) show the command prompt before and after using the CLS command respectively.
Figure 5.18 Using the CLS Command
- PROMPT: It is used to change the command prompt. The syntax of this command is:
PROMPT [Text]
Where
[Text] specifies the new command prompt.
In DOS, the command prompt can be changed to any specific character with the help of a special code. Table 5.1 lists various special codes used in DOS.
Special Codes Characters $A & (Ampersand) $B | (Pipe) $C ((Left parenthesis) $D Current Date $E Escape Code $F) (Right parenthesis) $G > (Greater than) $H Backspace $L < (Less than) $N Current Drive $P Current drive and path $Q = (Equal sign) $S (Space) $T Current time $V Windows XP version number $_ Carriage return and linefeed $$ $ (Dollar sign) For example, to change the prompt to $, use the following command.
C:>PROMPT $$ $
Note that the command prompt can be changed to any other character (other than those listed in Table 5.1) or string. For example, if you want to change the command prompt to a particular character (say, N), use the following command.
C:>PROMPT N
If you want to change the command prompt to a particular string (say, DOS), use the following command.
C:>PROMPT DOS DOS
Note: To set the command prompt back to the default prompt, simply type PROMPT and press the Enter key.
- VER: It is used to display the version number of MS-DOS. The syntax of this command is:
VER
For example, use the following command to know the current version of DOS.
C:>VER MS-DOS version 6.20 - BREAK: It is used to enable or disable the Ctrl+C check in DOS. The Ctrl+C check is used to cancel a batch process or any other process in DOS. The syntax of BREAK command is:
BREAK [ON/OFF]
Where
ON enables the BREAK command.
OFF disables the BREAK command.
For example, to enable the check, use the following command.
C:> BREAK ON
On the other hand, to disable the check, use the following command.
C:> BREAK OFF
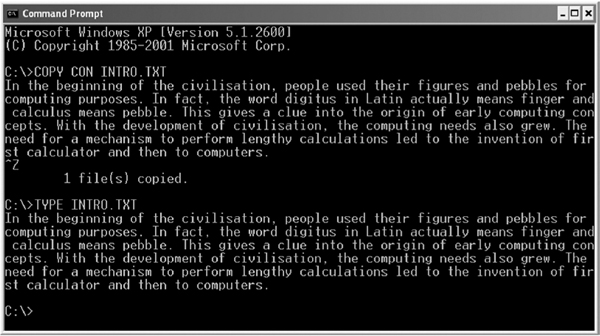
- COPY CON: It is used to create a new file. The syntax of this command is:
COPY CON Filename
Where
Filename specifies the name of the file to be created.
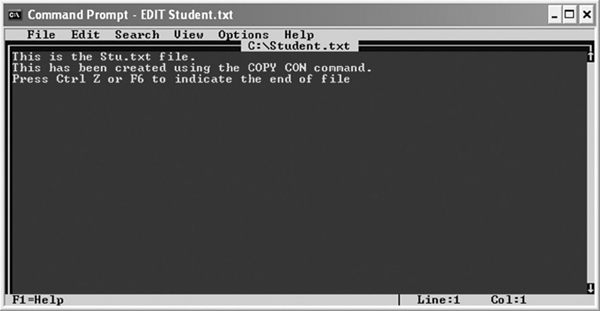
For example, to create a new file Stu.txt, use the following command.
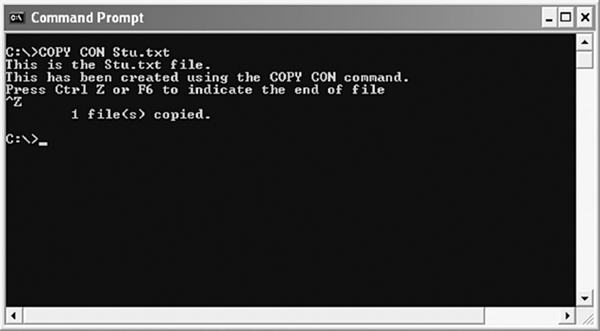
C:>COPY CON Stu.txt
As you press the Enter key after typing the above command, the cursor moves to the next line, where you can type the text. After writing all the text, press Ctrl+Z or F6 and then press the Enter key (see Figure 5.19).
Figure 5.19 Using COPY CON Command
- TYPE: It is used to display the contents of a specified file. The syntax of this command is:
TYPE [Drive:] [Path] Filename
Where
[Drive:] specifies the drive where the file is stored.
[Path] specifies the pathname of the file.
Filename specifies the name of the file.
For example, Figure 5.20 displays the contents of Stu.txt file.
Figure 5.20 Using TYPE Command
- COPY: It is used to copy a file or files from one location to another. The syntax of this command is:
COPY [/V][/Y|/-Y][/A|/B] Source [/A |/B] [+ Source [/A |/B] [+…] Destination [/A|/B]Where
[/V] verifies whether the new file is written correctly.
[/Y] suppresses prompting of the system in case of file overwriting.
[/-Y] activates prompting of the system in case of file overwriting.
[/B] specifies a binary file.
[/A] specifies an American Standard Code Interface Interchange (ASCII) text file.
[Source] specifies the source filename.
[Destination] specifies the destination filename.
For example, to copy Stu.txt file to the directory (say, Student) in D drive, use the following command.
C:>COPY Stu.txt D:Student
You can also copy more than one file (stored at the same location) to another location at once. For example, to copy Stu.txt and Stu1.txt (which also resides in C drive) to D drive, use the following command.
C:>COPY Stu.txt + Stu1.txt D:
You can also copy all the files at once. For example, to copy all the text files from C:Data to D: Data, use the following command.
C:>COPY C:Data*.txt D:Data
- DEL or ERASE: It is used to delete one or more files. The syntax of this command is:
DEL [/P][/F][/S][/A[[:]Attributes]] Name ERASE [/P][/F][/S][/A[[:]Attributes]] NameWhere
[/P] asks for a confirmation before deleting each file.
[/F] forces deleting of read only files.
[/S] deletes a specified file from all subdirectories.
[/A[[:]Attributes]] deletes files on the basis of their attributes.
Name specifies the name of a file or files to be deleted.
For example, to delete file Stu.txt, use the following command.
C:>DEL Stu.txt
You can also delete all the files at once. For example, to delete all text files from the D:New directory, use the following command.
C:>DEL D:New*.txt
If you want to delete only some specific files but not all, you can do so using the (/P) parameter with the DEL command. For example, to delete all text files from the D:New directory (which contains three text files One.txt, Two.txt, and Three.txt) except Three.txt, use the following command.
C:>DEL D:New*.txt/P
As you press the Enter key, the computer prompts you for confirmation before deleting each file. Type Y for all the files except Three.txt as shown below:
D:NewOne.txt, Delete (Y/N)? Y D:NewThree.txt, Delete (Y/N)? N D:NewTwo.txt, Delete (Y/N)? Y - RENAME or REN: It is used to rename a file or files. The syntax of this command is:
RENAME [Drive:] [Path] Oldfile Newfile REN [Drive:] [Path] Oldfile NewfileWhere
[Drive:] specifies the drive name.
[Path] specifies the pathname.
Oldfile specifies the old filename.
Newfile specifies the new filename.
For example, to rename file Stu.txt as Student.txt, use the following command.
C:>RENAME Stu.txt Student.txt
Note: While renaming a file, you cannot specify a new path or drive for it. The renamed file remains at its original location.
- DIR: It is used to display the list of files or subdirectories present in a directory. The syntax of this command is:
DIR [Drive:] [Path] [Filename] [/A [[:] Attributes] [/B] [/C] [/D] [/L] [/N] [/O [[:] Sortorder]] [/P] [/Q] [/S] [/T [[:] Time-field]] [/W] [/X] [/4]
Where
[Drive:] specifies the drive.
[Path] specifies the pathname.
[Filename] specifies the filename.
[/A] displays files with the specified attributes. Different attributes are D (directory), H (hidden files), S (system files), R (read-only files), A (files ready for archiving), - (prefix meaning not).
[/B] uses bare format with no heading information or summary.
[/C] displays thousand separators in the file size.
[/W] uses the wide list format.
[/D] same as /w, the only difference is files are sorted by column.
[/L] uses lowercase
[/N] displays a new long list format, where filenames are displayed on the far right.
[/O] lists files in sorted order. The sort order is specified by N (name), E (extension), G (group directory first), S (size), D (date) or - (prefix to reverse order).
[/P] pauses after each screen full of information.
[/Q] displays the owner of the file.
[/S] displays files in a specified directory and all subdirectory.
[/T] determines which time field is used for sorting. Timefield options are C (creation), A (last access) or W (last written).
[/X] displays short names, inserted before the long name.
[/4] displays years in 4 digits.
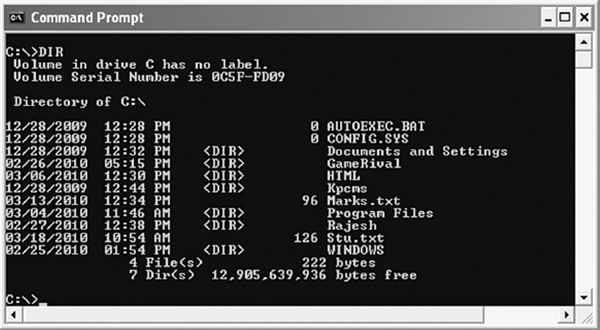
For example, if you want to list all the files and subdirectories in the current working directory, use the following command (see Figure 5.21).
C:>DIR
If you want to list all the hidden files in the current working directory, use (/A) parameter with attribute H as shown below:
C:>DIR/A:H
Figure 5.21 Using DIR Command
Note: A hidden file is a file that is present in the directory; however, not visible to the user.
- MD or MKDIR: It is used to create a directory in a drive. The syntax of this command is:
MD [Drive:] Path MKDIR [Drive:] Path
For example, to create a directory (Newdir) in E drive, use the following command.
C:>MD E:Newdir
If you do not specify any drive, the new directory is created in the current working directory. For example, if you use the following command, the Newdir directory will be created in C drive.
C:>MD Newdir
- CD or CHDIR: It is used to change the current directory. The syntax of this command is:
CD [/D] [Drive:][Path] CHDIR [/D][Drive:][Path]
Where
[/D] allows users to change the current drive, in addition to the changing directory for a drive.
[Drive:] specifies the drive.
[Path] specifies the pathname.
For example, to change to the New directory from the current directory, use the following command.
C:>CD New
As you press Enter after typing the above command, the directory will be changed as shown below:
C:New>
Now, if you want to change back to the parent directory, use the following command.
C:New>CD..
If you want to change from current directory to a different directory in a different drive (say, Newdir directory in E drive), use the following command.
C:>CD/D E:Newdir
- RD or RMDIR: It is used to remove or delete a directory from a drive. The syntax of this command is:
RD [/S][/Q] [Drive:] Path RMDIR [/S][/Q] [Drive:] Path
Where
[/S] deletes a directory tree which implies that all the subdirectories and files are deleted in addition to the directory specified.
[/Q] is the quiet mode that does not ask for confirmation while deleting directory tree with /S.
For example, to delete all the directories and files in the New directory, use the following command.
C:>RD/S New
As you press the Enter key, the computer prompts you for confirmation before deleting as shown below:
New, Are you sure (Y/N)?
Press Y to delete all the files and directories, otherwise press N.
- VOL: It is used to display the disk volume label and serial number. The syntax of this command is:
VOL [Drive:]
For example, to display the volume label and the serial number of the current drive, use the following command.
C:>VOL
As you press the Enter key, DOS displays information similar to the following.
Volume in drive C is My Drive Volume Serial Number is FCFA-B977
You can also display the volume label and serial number of a drive other than the current drive. For example, to display volume information of D drive, use the following command.
C:>VOL D:
External MS-DOS Commands
Since the storage capability of the main memory is limited, not all DOS commands are stored in the main memory. There are some commands that take a lot of storage space and are not used as frequently as the internal commands. These commands are stored in a separate file (with .com, .exe, or .bat file extension) on the hard disk drive and are known as external commands. Some of the most commonly used external DOS commands are:
- PRINT: It is used to print a text file. The syntax of this command is:
PRINT [/D: Device] [[Drive:] [Path] Filename[..]]
Where
[/D: Device] specifies the name of the print device (LPT1, LPT2, etc.).
[Drive:] specifies the drive (C:, A:, D:, etc.).
[Path] specifies the pathname.
Filename[..] specifies the filename or filenames.
For example, to print file Student.txt, use the following command.
C:>PRINT/D: LPT2 Student.txt
- MEM: It is used to display the amount of used and free memory on the computer. The syntax of this command is:
MEM[/PROGRAM][/CLASSIFY][/DEBUG]
Where
[/PROGRAM] shows the status of the currently loaded program.
[/CLASSIFY] classifies a program by memory usage. It lists the program name, program size, and total bytes available to programs.
[/DEBUG] shows the status of programs and internal drivers loaded in the memory along with their address, name, size, and type.
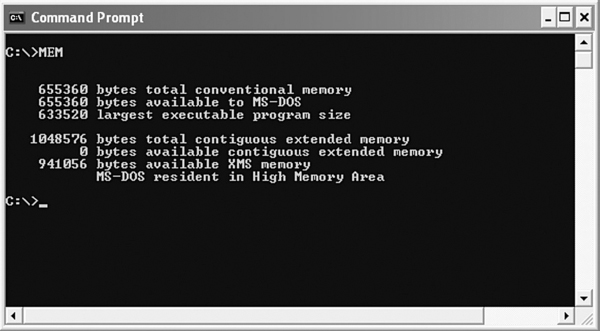
For example, to know the amount of used and free memory, simply type MEM at the command prompt (see Figure 5.22).
Figure 5.22 Using MEM Command
- HELP: It is used to provide information of various commands used in MS-DOS. The syntax of this command is:
HELP [Command name]
Where
[Command name] specifies the name of a command.
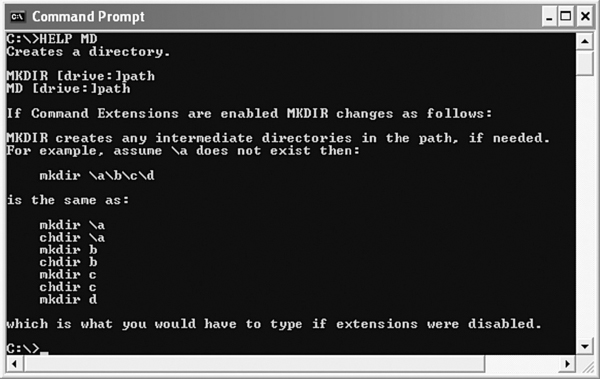
For example, to display information about MD command (see Figure 5.23), use the following command.
C:>HELP MD
Note: You can also list the definition of all the commands by simply typing HELP at the command prompt.
Figure 5.23 Using HELP Command
- EDIT: It is used to edit a text file by using DOS's built-in text editor. Using this editor, you can create, edit, save and print text files. The syntax of EDIT command is:
EDIT [/B][/H][/R][/S][Filename]
Where
[/B] opens the editor in the monochrome (black and white window) mode.
[/H] shows the maximum number of lines possible on your monitor.
[/R] opens the file in the read-only mode.
[/S] forces the use of short filenames.
[Filename] specifies the name of the file to be loaded.
For example, to edit Student.txt file, use the following command.
C:>EDIT Student.txt
As you press the Enter key after giving the above command, DOS displays the built-in text editor (see Figure 5.24).
Figure 5.24 DOS Built-in Text Editor
You can perform various operations on a file by selecting the appropriate menu and then selecting a suitable option. Table 5.2 lists some useful options available in the text editor.
Table 5.2 Useful Options in Text Editor
| Options | Description |
| File->New | To create a new file |
| File->Open | To open an existing file |
| File->Save | To save a file |
| Edit->Cut | To extract the selected text |
| Edit->Copy | To copy the selected text |
| Edit->Paste | To paste the cut or copied text at the desired location |
| Search->Find | To find the occurrence of a string or character in a file |
| Search->Replace | To replace the searched string or character with another string or character |
| View->Split | Window To divide the window into two parts |
| View->Close | Window To close an open window |
| Help->Commands | To show various commands for cursor movement |
Note: You can return from the text editor to command prompt by selecting Exit from the File menu.
- ATTRIB: It is used to set or change the attributes of a file. The syntax for this command is:
ATTRIB[+R|-R][+A|-A][+S|-S][+H|-H][Drive:][Path][Filename] [/S] [/D]
Where
+ sets an attribute.
- clears an attribute.
R sets the read-only attribute.
A sets the archive file attribute.
S sets the system file attribute.
H sets the hidden file attribute.
Drive: specifies the drive.
Path specifies the pathname.
Filename specifies the name of the file.
/S processes matching files in the current folder and all subfolders.
/D processes folders as well.
For example, if you want to make Student.txt file a hidden file, use the following command.
C:>ATTRIB +H student.txt
Now, if you use the DIR command, Student.txt will not be listed.
- TREE: It is used to graphically display the folder structure of a drive or path. The syntax of this command is:
TREE [Drive:][Path] [/F][/A]
Where
[Drive:] specifies the drive.
[Path] specifies the pathname.
[/F] shows the name of files in each folder.
[/A] uses American Standard Code for Information Interchange (ASCII) characters instead of extended characters.
Figure 5.25 Using TREE Command
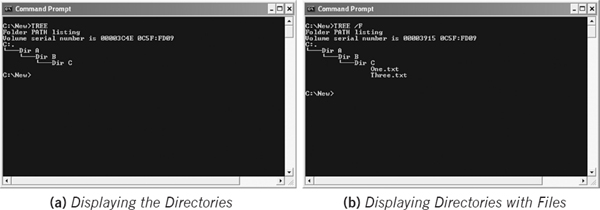
- For example, to display all subdirectories in the New directory of C drive, use the following command (see Figure 5.25 (a)).
C:New>TREE
If you want to display the name of files in each directory, use the following command (see Figure 5.25 (b)).
C:New>TREE/F
- MOVE: It is used to move the files from one location to another and rename files and directories. The syntax of this command is:
MOVE [/Y][/-Y] [Drive:][Path] Filename1[…] Destination MOVE [/Y][/-Y] [Drive:][Path] OldDir NewDir
Where
[Drive][Path]Filename1 specifies the location of file or files that you want to move.
Destination specifies the new destination of a file.
OldDir specifies the directory you want to rename.
NewDir specifies the new name of the directory.
[/Y] does not prompt the user in case of overwriting.
[/-Y] prompts the user in case of overwriting.
For example, to move a file One.txt from C drive to D drive, use the following command.
C:>MOVE One.txt D:
If you want to move One.txt and rename it also as Two.txt, use the following command.
C:>MOVE One.txt D:Two.txt
You can also rename a directory using the MOVE command. For example, to rename the directory New as Newdir, use the following command.
C:>MOVE New Newdir
- XCOPY: It is used to copy directories, their subdirectories and files to the specified destination. The syntax of this command is:
XCOPY Source Destination [/Y] [/-Y] [/A] [/M] [/D:date] [/P][/S] [/E] [/V] [/W]
Where
[/Y] replaces the existing files without prompting.
[/-Y] prompts for confirmation when replacing a file.
[/A] copies the files that have their archive attribute set. Archive attribute in copied files remain unchanged.
[/M] is same as /A, the only difference is that it turns off the archive attribute.
[/D:date] copies only those files that have changed on or after the specified date.
[/P] prompts you to confirm whether you want to create each destination file.
[/S] copies directories and subdirectories, unless they are empty.
[/E] copies subdirectories even if they are empty.
[/V] verifies each file as it is written to the destination.
[/W] waits for the user input before copying files.
For example, to copy all the files in New directory to the E:Newdir directory, use the following command.
C:>XCOPY C:New E:Newdir
- LABEL: It is used to create, change, or delete the volume label of a disk. The syntax of this command is:
LABEL [Drive:] [Label]
Where
[Drive:] specifies the drive.
[Label] specifies the new label.
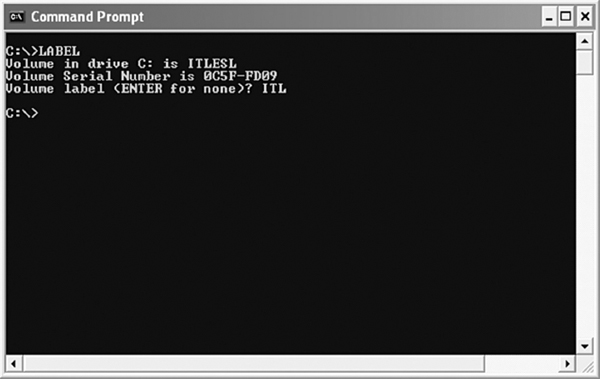
For example, to change the volume label of the current drive, use the following command.
C:>LABEL
As you press the Enter key after giving the above command, DOS asks you to enter a new label (see Figure 5.26), which can be up to 11 characters.
Figure 5.26 Changing Label of Current Drive
If you want to create or change the label of another drive (say, D drive) other than the current drive, use the following command.
C:>LABEL D:
- CHKDSK: It is used to check a disk and display its status report including total disk space, number of folders and hidden files, etc. The syntax of this command is:
CHKDSK [Drive:][/F]
Where
[Drive:] specifies the drive.
[/F] fixes errors on the disk.
For example, to perform disk checking for C drive, use the following command.
C:>CHKDSK
As you press the Enter key after typing the above command, the disk checking of C drive is performed and its status is displayed, as shown in Figure 5.27.
Figure 5.27 Using CHKDSK Command
Note that the previous command only displays the disk status and does not fix any errors (if any). If you want to fix the errors on the disk, use (/F) parameter with CHKDSK command, as shown below:
C:>CHKDSK /F
- FORMAT: It is used to format a disk. The syntax of this command is:
FORMAT Volume [/FS:filesystem][/V:label][/Q][/X][/A:size] [/F:size] [/T:tracks][/N:sectors]
Where
Volume specifies the drive.
[/FS:filesystem] specifies the file-system.
[/V:label] specifies the volume label.
[/Q] performs a quick format.
[/X] forces the volume to dismount first, if necessary.
[/A:size] overrides the default allocation unit size.
[/F:size] specifies the floppy disk size.
THINGS TO REMEMBER
Formatting a Disk
Information in a disk is stored in tracks and sectors. Tracks are concentric circles on a disk, which are further classified into sectors. Formatting a disk implies creating and marking new tracks and sectors on a disk. The number of tracks and sectors in a disk depend on the type of disk and its capacity.
[/T:tracks] specifies the number of tracks each side.
[/N:sectors] specifies the number of sectors per track.
For example, to format D drive, use the following command.
C:>FORMAT D:
Note: The FORMAT command deletes any previous data stored on the disk.
5.7 MODERN OPERATING SYSETEMS
As stated earlier, MS-Windows is the most popular series of operating systems in the past decade. Windows 95 revolutionised the personal computer system market. Then came Windows NT, Windows 98, Windows ME, Windows 2000, Windows XP, and now Windows Vista. Out of these operating systems, Windows 2000 and XP are the most commonly used and have already gained reputation amongst the business market. Windows Vista is a successor to Windows XP and offers many powerful and unique features. In this section, we will discuss in brief Windows 2000 and Vista.
Note: Windows XP is discussed in detail in Chapter 06.
5.7.1 WINDOWS 2000
Windows 2000 operating system is a 32-bit preemptive multitasking operating system. It is the successor to the Windows NT operating system. It introduces new concepts like X.500-based directory service, support for plug and play devices, a new file system, which supports distributed file system, and support for more processors and memory. Microsoft introduced four versions of Windows 2000 including Windows 2000 Professional, Windows 2000 Server, Windows 2000 Advanced Server, and Windows 2000 Datacenter Server.
Windows 2000 as Process Manager
Windows 2000 process manager provides basic services for creating, scheduling, and deleting processes. It differentiates processes based on priorities. Every process is created as a single executing thread; the process can create additional threads. The highest priority ready process is moved to standby state, so it will be the first process to run among the pool of other ready processes. The scheduler operates over all threads.
Windows 2000 as Memory Manager
The memory manager in Windows 2000 primarily acts as a virtual memory (VM) manager. The VM manager in Windows 2000 uses the paging management scheme with page size of 4 KB. The memory architecture of Windows 2000 is based on a flat, linear address space accessed via 32-bit addresses. Windows 2000 supports multiple paging files. Performance can be greatly enhanced if multiple paging files are created on different disks.
Windows 2000 as File Manager
MS-DOS file system maintained a table of pointers called File Allocation Table (FAT) for managing user-defined files. It consisted of 16-bit values, which correspond to different clusters of the disk space. Each entry in the FAT corresponds to one and only one cluster of the disk space; initially all the FAT entries are set to zero indicating a free cluster. The 16-bit FAT file system had several short-comings like fragmentation, size limit of 2GB, and lack of security. The 32-bit FAT file system solved the initial problems of fragmentation and size limit but security of files remained an issue for which New Technology File System (NTFS) was introduced. Windows 2000 server handles the FAT32 and NTFS file systems much better. In addition, disk defragmentation capabilities are built-in and the powerful backup utility is incorporated in Windows 2000. The NT File System which comes as a native file system for windows 2000 was designed to include many features, including data security, recovery, large files, and fault tolerance.
Windows 2000 as Device Manager
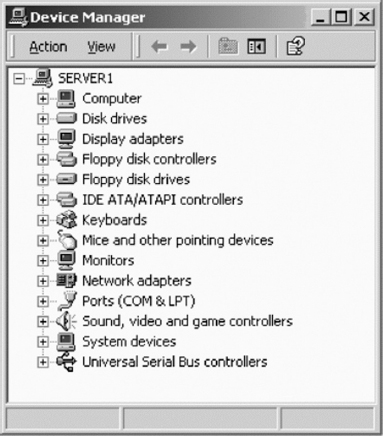
The device manager in Windows 2000 provides a description about the drivers and equipment that are installed on a computer, and how they are functioning. Windows 2000 server incorporates the plug and play (PnP) manager to recognise and adjust to the changes in the hardware configuration. Compatible devices can now be installed and Windows 2000 will automatically configure the device. The resources used by different devices, or the resources, which could be used by devices, and loading of appropriate drives for devices is being looked after by the PnP manager. Figure 5.28 illustrates the device manager in Windows 2000.
Figure 5.28 Device Manager in Windows 2000
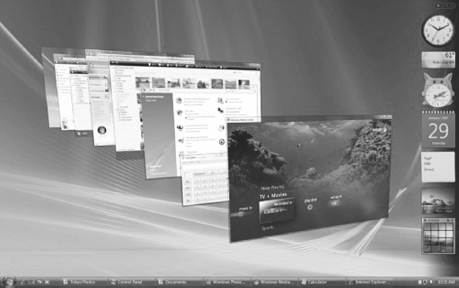
5.7.2 WINDOWS VISTA
Windows Vista, the successor to Windows XP, was released in 2008 by Microsoft. Since its release, it has revolutionised the market of desktop operating systems. It includes a wide variety of features that tend to increase the efficiency and productivity of users. By keeping in mind the needs of both home and business users, Microsoft has released five editions of Windows Vista, which are: Windows Vista Home Basic, Windows Vista Home Premium, Windows Vista Ultimate, Windows Vista Business, and Windows Vista Enterprise. Out of these editions, the Home Basic and Home Premium editions are specifically designed for home users depending on their levels of personal computing, while the Business and Enterprise editions best suit to the needs of business users. The Ultimate edition combines the best features of home and business editions and thus, is well suited for both home and business users. Figure 5.29 shows the interface of Windows Vista.
Note: The main difference between home and business editions is that home editions include entertainment features that are not included in business editions and business editions include management features that are not the part of home editions.
Figure 5.29 Windows Vista's Interface
Features of Windows Vista
Windows Vista includes many features, some of which are entirely new while others have been improved as compared to earlier versions of Windows.
- Windows Aero: All the basic elements of Windows like icons, menus, dialog window, etc., have been redesigned to provide better visuals. The Aero interface takes advantage of latest graphics hardware and provides smoother window handling, enhanced animations, and glass visual effects (transparencies).
- Windows Sidebar: It is a transparent panel (see Figure 5.29) on which you can place gadgets, which are small applications providing specific information like weather, time, calendar, etc. The Sidebar can be placed at any side of the screen (left or right). Though Vista comes with some gadgets, you can also download different types of gadgets from the Internet as per your choice and add them to the Sidebar.
- Instant Search: Windows Vista includes an Instant Search feature that lets you search files, folders, or whatever you want from almost every system window including Explorer and Start Menu. In addition, as you type in the search box, Windows searches instantly and provides you the search results. This makes the searching easier and faster.
- Windows Flip and Flip 3D: Unlike previous versions in which pressing Alt+Tab displays icons of open programs, Windows Vista displays preview of each open window. In addition, you can arrange the open windows in form of cascading stacks (as shown in Figure 5.29) and even rotate them using the mouse scroll wheel so that you can simultaneously preview all the open windows.
- Network Map: This feature is available within the Network Center that graphically depicts all your network connections. In case any network problem occurs like losing connectivity, you can easily spot the problem and find out the solution. All this helps in improving network performance.
- Windows Defender: This feature monitors the system to protect it against spyware, pop-ups, poor system performance, etc. It also keeps track of all the programs running on the system and automatically stops any suspected program. Moreover, by enabling the Autoupdate option available in Windows Defender, you can make the program to download the latest spyware definitions from Microsoft.
- Windows ReadyBoost: This is the new surprising feature in Windows Vista that enables you to use USB flash memory as main memory thereby improving system performance. Hence, you need not purchase a RAM chip and insert it into motherboard slot; rather you can just plug a USB flash memory. As you plug a flash memory, Vista determines whether using flash memory as RAM can increase the system performance and if it is, you will be asked whether to use flash as RAM.
LET US SUMMARISE
- An operating system is a collection of system programs that together controls the operation of a computer system. The two objectives of an operating system are managing the computer's hardware and providing an interface between the user and machine.
- Operating system has six major functions to perform: process management, memory management, file management, device management, security management, and providing user interface.
- A process is an execution of a sequence of instructions or program by the central processing unit (CPU). It may be in one of a number of different possible states, such as new, running, waiting, ready, or terminated.
- A thread is a task that runs concurrently with other tasks within the same process. The single thread of control allows the process to perform only one task at one time. In a multi-tasking operating system, a process may contain several threads, all running at the same time inside the same process.
- In uniprogramming system, users can perform only one activity at a time while in a multiprogrammed systems, multiple programs can reside in main memory at the same time.
- The procedure of determining the next process to be executed on the CPU is called process scheduling and the module of operating system that makes this decision is called scheduler.
- In preemptive scheduling, the scheduler can forcibly remove the processor from the currently running process before its completion in order to allow some other process to run. Round Robin scheduling is an example of preemptive scheduling procedure.
- In non-preemptive scheduling, once the processor is allocated to a process, it cannot be taken back until the process voluntarily releases it (in case the process has to wait for I/O or some other event) or the process terminates. First-come-first-served (FCFS) is an example of non-preemptive scheduling procedure.
- The process of switching from one process to another is called context switching. A period that a process runs for before being context switched is called a time slice or quantum period.
- A process is said to be in a state of deadlock when it is waiting for an event, which will never occur. It can occur if four conditions prevail simultaneously; they are mutual-exclusion, circular wait, hold and wait, and no preemption.
- The part of the operating system that manages the primary memory of the computer is called the memory manager.
- Paging is a memory management scheme that allows the processes to be stored non-contiguously in memory.
- Virtual memory is a way of showing the main memory of a computer system to appear effectively larger than it really is.
- The system that an operating system uses to organise and keep track of files is known as file management system.
- A program that controls a device is called the device driver. Operating system's device manager uses this program to let a user use the specific device.
- A user interface is a set of commands or menus through which a user communicates with the system.
- The Disk Operating System is a single user operating system released by Microsoft in the early 80's. It is a command line user interface, which enables users to organise data files, load and execute (run) program files, and control the input and output devices attached to the computer.
- The DOS environment gives the user a quick and direct access to the basic utilities of a computer. All tasks are accomplished by typing commands at a command prompt (at the cursor location).
- A prompt is defined as a character or string of characters used in the command line interface to indicate that a computer is ready to accept commands from users. In DOS, ‘>’ is used as a prompt, which is preceded by other information such as current drive and path of the current working directory.
- A file is a primary unit of storage in computers. DOS uses a unique filename to describe contents of a file and keep track of the file so that you can use it later.
- A directory allows users to group files under one category. Every disk has one basic directory called the root directory, which is created automatically when the disk is formatted. In addition to files, a directory can contain other directories also in itself known as subdirectories.
- To access a file, a user may have to traverse through different directories. Thus, a pathname is used to instruct the computer where to look for any particular file. A pathname is a sequence of directories separated by a backslash (‘’) followed by a filename.
- In MS-DOS, commands are used to perform different operations such as copying files, deleting files, creating a directory, etc. In an operating system, a command is defined as a directive given to the computer to perform a specific operation. MS-DOS commands are broadly classified into two categories, namely, internal and external.
- The internal commands are built into the operating system as part of a file called COMMAND. COM, which is loaded into the main memory during the booting process. Some of the most commonly used internal DOS commands are DATE, TIME, CLS, PROMPT, COPY CON, COPY, DEL, DIR, etc.
- The external commands are stored in a separate file (with.com, .exe, or .bat file extension) on the hard disk drive and are not used as frequently as the internal commands. Some of the most commonly used external DOS commands are PRINT, HELP, MEM, EDIT, TREE, MOVE, XCOPY, LABEL, etc.
- Windows 2000 operating system is a 32-bit preemptive multitasking operating system. It is the successor to the Windows NT operating system.
- Windows Vista, the successor to Windows XP, was released in 2008 by Microsoft. Since its release, it has revolutionised the market of desktop operating systems. It includes a wide variety of features that tend to increase the efficiency and productivity of users.
EXERCISES
Fill in the Blanks
- A table where many pieces of information associated with a specific process, that is, program counter, process state, CPU-scheduling information, and so on are stored, is known as ____________
- ____________ is also called as a lightweight process.
- ____________ refers to storing the jobs in the buffer so that CPU can be efficiently utilised.
- A process is said to be in a state of ____________ when it is waiting for an event that will never occur.
- The major tasks accomplished by the memory manager so that all the processes function in harmony, are ____________ and ____________
- RTOS stands for____________
- The ____________ is a single user operating system released by Microsoft in the early 80's.
- The ____________ is an external command in DOS which checks a disk and displays its status report.
- A pathname can be either ____________ or ____________
- A ____________ is defined as a character or a string of characters used in the command line interface to indicate that a computer is ready to accept commands from users.
Multiple Choice Questions
- Which of the following is a non-preemptive scheduling?
- (a) First-Come-First-Served
- (b) Round Robin
- (c) Last-In-First-Out
- (d) Shortest-Job-First
- The operating system that allows only one program to run at a time is:
- (a) Real Time
- (b) Embedded
- (c) Batch Processing
- (d) Multitasking
- The substitution made by the operating system between the processes to allocate space is:
- (a) Swapping
- (b) Deadlock
- (c) Fragmentation
- (d) Paging
- The memory management scheme that allows the processes to be stored non-contiguously in memory:
- (a) Spooling
- (b) Paging
- (c) Swapping
- (d) None of the above
- The fit policy of a memory manager to place a process in the largest block of unallocated memory is:
- (a) First fit
- (b) Best fit
- (c) Worst fit
- (d) Bad fit
- With which memory, the system can run programs that are actually larger than the primary memory of the system?
- (a) Virtual memory
- (b) Primary memory
- (c) Cache memory
- (d) None of the above
- The scheduler that selects a process from the ready queue and allocates CPU to it is:
- (a) Short-term
- (b) Long-term
- (c) Medium-term
- (d) All the above
- Which of the following DOS files contains the internal DOS commands?
- (a) IO.SYS
- (b) CONFIG.SYS
- (c) AUTOEXEC.BAT
- (d) COMMAND.COM
- Which of these DOS commands is used to clear the screen?
- (a) CLEAN
- (b) CLS
- (c) CLEAR
- (d) CL
- Which of these DOS commands is used to delete a directory?
- (a) RMDIR
- (b) DEL
- (c) DELETE
- (d) ERASE
State True or False
- Operating system is a hardware component.
- Virtual memory allows for very effective multiprogramming.
- Another term for time-sharing is multi-tasking.
- Railway reservation systems use batch-processing operating systems.
- Round robin is a non-preemptive scheduling technique.
- Best-fit, first-fit, and worst-fit are memory allocation techniques.
- The directory structure of Microsoft Windows operating system is hierarchical.
- The job of splitting the primary memory into segments as the memory is allocated and deallocated to the processes is known as fragmentation.
- BREAK is an external DOS command.
- Information in a disk is stored in tracks and sectors.
Descriptive Questions
- What is an operating system? Explain various types of operating system.
- Define a process. Explain the life cycle of a process with the help of a diagram.
- Discuss various types of interfaces in the operating system.
- What is a deadlock? How can it be eliminated from the system?
- Explain how memory protection and process allocation is done by an operating system.
- Write down the differences between:
- (a) Uniprogramming and multiprogramming
- (b) Preemptive and non preemptive scheduling
- (c) Deadlock avoidance and deadlock prevention
- Differentiate between internal and external DOS commands.
- Write the rules that are to be followed while naming a file in MS-DOS.
- Explain the following commands with the help of an example.
- (a) PRINT
- (b) HELP
- (c) MKDIR
- (d) RMDIR
- List some new features available in Windows Vista.
ANSWERS
Fill in the Blanks
- Process table
- Thread
- Spooling
- Deadlock
- Relocation, protection and sharing
- Real-time operating system
- DOS 8. CHKDSK
- Absolute, relative
- Prompt
Multiple Choice Questions
- (a)
- (c)
- (a)
- (b)
- (c)
- (a)
- (b)
- (d)
- (b)
- (a)
State True or False
- False
- True
- False
- False
- False
- True
- True
- True
- False
- True