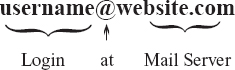13
THE INTERNET
13.1 INTRODUCTION
In the past two decades, computers have played a significant role in our everyday life. With the growth in popularity and networking of computers, intercommunication between different computers became easier, which led to evolution of Internet. It is the most talked about computer technology in recent years. For a majority of people, who are unaware of computer technology, Internet depicts some enigmatic computer gizmo, which has something to do with games, music, and generally entertainment. However, Internet is a much broader concept than mere entertainment and recreational activities. It is revolutionising and enhancing the ways of human interaction and communication.
The word Internet is derived from two words: Interconnection and Networks. Also referred to as “the Net”, Internet is a worldwide system of computer networks, that is, a network of networks, which allows the participants (users) to share information. It consists of thousands of separately administered networks of various sizes and types. Each of these networks comprises tens of thousands of computers. Moreover, the total number of users of the Internet is known to be in millions. This high level of connectivity encourages an unparalleled degree of communication, resource sharing, and information access. It is probably the most powerful and important technological advancement since the introduction of the desktop computer. In order to benefit from what the net has to offer, a basic understanding of what it is and how it works is helpful.
13.2 EVOLUTION OF INTERNET
The foundation of Internet was laid in 1969 by the Department of Defense (DOD) of United States of America. They wanted to create a computer network that could continue to function in the event of a disaster, such as a nuclear war. Even if a part of the network was damaged or destroyed, the rest of the system would continue to work. That network was known as ARPANET (Advanced Research Projects Agency Network), which linked US scientific and academic researchers. It was the forerunner of today's Internet.
Later in 1980, another agency, the National Science Foundation (NSF) created a new network of computers based on ARPANET, called NSFNET, which turned out to be more efficient and capable. Initially, NSFNET was designed to link five super computers situated at the major universities of NSF and allowed only academic research. Over the time, this network expanded to include sites for business, universities, government, etc. and finally becoming a network consisting of millions of computers, now known as the Internet.
In the 1980s, Usenet newsgroups and Electronic Mail (e-mail) came into picture. To keep track of the information on the Internet, indices such as Archie and the Wide Area Information Server (WAIS) were also created in this decade. To give users an easy-to-use interface to work with, the University of Minnesota created Gopher, a simple menu driven system for accessing files. Internet really became popular in the 1990s after the development of the World Wide Web (WWW). Before that, it was open for a handful of sites only. It is amazing that as recently as June 1993, there were only 130 websites, but now there are millions.
With the growth of Internet, the quality, quantity, and variety of information also grew. The Internet today is a repository of every type of information. Nowadays, an Internet user can get all sorts of information ranging from how to add to the design of a functional spaceship to choosing a product for personal use.
Figure 13.1 Hypothetical Diagram of the Internet
13.3 OWNER OF INTERNET
Now that you are aware of how the Internet evolved, you may ask that who owns the Internet. Well, the answer is ‘nobody'. The Internet is a loosely organised international collaboration of autonomous, interconnected networks, which supports host-to-host communication through voluntary adherence to open protocols and procedures defined by Internet Standards. Nobody really owns or controls the Internet. However, there are some governing bodies overseeing the technical aspects of the Internet. These are bodies that define how the Internet works and how new technology is to be implemented. Some of the important governing bodies of Internet are given below:
- Internet Society (ISOC): Internet Society is concerned with the growth and evolution of the Internet and the way in which the Internet is and can be used.
- Internet Architecture Board (IAB): It is a technical advisory group of the ISOC and is chartered to provide oversight of the architecture of the Internet and its protocols.
- Internet Engineering Task Force (IETF): It is a self-organised group of people who provides technical and other contributions to the engineering and evolution of the Internet and its technologies.
- Internet Engineering Steering Group (IESG): This group is responsible for the technical management of IETF activities and the Internet standards' development process.
- Internet Research Task Force (IRTF): Its main purpose is to create research groups that focus on Internet protocols, applications, architecture, and technology.
- Internet Assigned Number Authority (IANA): The task of IANA is to assign protocol parameters such as Internet addresses, domain names, and protocol numbers for the Internet.
- Internet Network Information Center (InterNIC): InterNIC is a collaborative activity of AT&T, Network Solutions Inc., and NSF (National Science Foundation). It provides directory and database services, the Internet white pages, and domain name registration.
- World Wide Web Consortium (W3C): It was founded in 1994 to develop common protocols for the evolution of the World Wide Web.
13.4 ANATOMY OF INTERNET
As you know, the Internet is a large collection of interconnected networks spanning a large geographical area (country or even a continent). However, the entire structure of the Internet can be viewed as composed of a few basic components including host, networks, and routers.
- Host: A machine that a user uses to run application programs in order to avail services from the Internet (or network).
- Network: When two or more hosts communicate with each other in order to share information or resources, we say they form a network.
- Router: A networking device that helps in finding a feasible route for data as well as forwarding it so that it reaches its destination.
13.5 INTERNET TERMINOLOGY
Now let us familiarise ourselves with some basic Internet terms.
World Wide Web (WWW)
The World Wide Web (abbreviated as the Web or WWW) is a collection of linked documents or pages, stored on millions of computers and distributed across the world. The concept of the Web began at CERN (the European Center for Nuclear Research) Geneva, Switzerland in the year 1989. Since then, WWW is the most popularly used Internet sub network. One of the main reasons that led to its popularity is that it provides information in multimedia form, that is, in more than one medium such as, text, graphics, video, and audio. Further, it provides a simple and consistent way of accessing the information available on the Internet by using hypertext system. In hypertext system, the documents are connected to other related documents on the Internet through links. The Web uses a specific Internet protocol called HTTP to support hypertext documents.
Note: Although the WWW is often referred to as the Internet, they are actually two different concepts. The WWW is one of the most popular services available on Internet.
Web Page
The hypertext documents on the World Wide Web are known as web pages. A web page is written in a language called HTML (Hypertext Markup Language) which enables to embed hypertext links (discussed later in this section) in the document. Using these hyperlinks, user can jump from one web page to another.
Note: Web pages are also known as HTML documents.
Website
A website is a set of related web pages (linked through hypertext links), published by an organisation or an individual. Typically, a website contains a home page along with other additional web pages. Each website is accessed by its own address known as URL (Uniform Resource Locator). All the websites on the Internet constitute the World Wide Web.
Home page
When you browse the World Wide Web, you will often see the term ‘Home Page’. A home page (also called index page) is the starting point or a doorway to the website; it refers to the web page that identifies a website and contains the hyperlinks to other web pages in the website. It may contain links to other websites also. Like the table of contents of a book, the home page usually provides an overview of what could be found at the website. If there is not much information, the home page may be the only page of the website. However, usually you will find at least a few other pages.
Browser
A browser (short for web browser) is special software that enables users to read/view web pages and jump from one web page to another. It is the software that is needed to find, retrieve, view, and send information over the Internet. The most popular browsers are Microsoft Internet Explorer and Netscape Navigator. Browsers are of two types:
- Graphical browsers allow retrieval of text, images, audio, and video. Navigation is accomplished by pointing and clicking with a mouse on highlighted words and graphics. Netscape Navigator, Internet Explorer and Mozilla are graphical browsers.
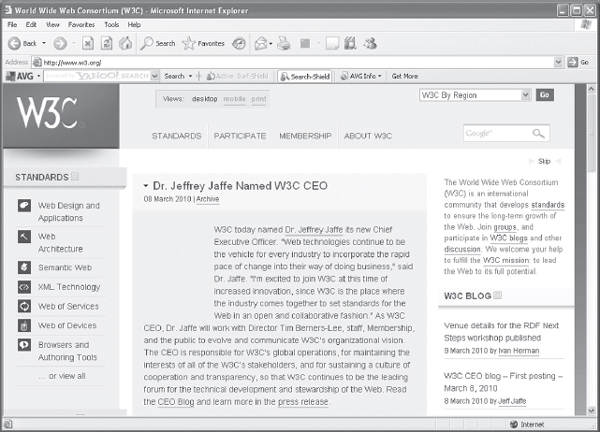
Figure 13.2 A Web Page on a Graphical Browser
- Text browsers provide access to the web in text-only mode. Navigation is accomplished by highlighting emphasised words on the screen with the arrow up and down keys, and then pressing the Enter key to follow the link. Lynx is an example of text-based browser.
Uniform Resource Locator (URL)
Each web page has a unique address, called a Uniform Resource Locator (URL) that identifies its location on the Internet. Usually, the format of an URL consists of four parts: protocol, name of the web server (or domain name), path, and filename. Here is an example, http://www.w3.org/Consortium/activities.html. The structure of this URL is:
- Protocol: http
- Web Server Name/Domain Name: www.w3.org
- Path: Consortium/
- File Name: activities.html
Figure 13.3 Uniform Resource Locator
The first part of the address, the part before the colon, is the protocol. Most of the time you see http (hypertext transfer protocol) for accessing a web page. Apart from http, you could also find other protocols such as ftp (file transfer protocol), news (news server), and telnet (for accessing remote computers). After the protocol, comes the domain name. The protocol and the domain name are separated by colons and slashes.
THINGS TO REMEMBER
Domain Types
Some of the domains that are typical on the Internet are:
| com | Commercial and for profit organisations |
| edu | Colleges and universities (education providers) |
| gov | Federal government agencies |
| mil | US military sites |
| net | Internet infrastructure and service providers |
| org | Miscellaneous and non-profit organisations |
A domain name is a unique name that identifies a particular website and represents the name of the server where the web pages reside. They are the human-readable addresses and hence are easier to remember. Domain names have two or more parts separated by dots. The letters occurring after the dot (.) identify the domain type. A domain type represents the type of organisation or countries to which the web server (sometimes called host computer) belongs.
Dozens of domain types have been assigned to identify and locate files stored on host computers in countries across the world. These are referred to as two-letter Internet country codes, and have been standardised by the International Standards Organisation (ISO). For example, uk for the United Kingdom, de for Germany, au for Australia, and in for India. The last part of a URL consists of the path and the file name. Path name specifies the hierarchic location of the said file on the computer. For instance, in http://www.w3.org/Consortium/activities.html, the file activities.html is located in Consortium directory.
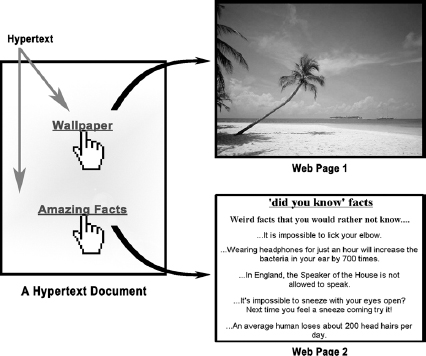
Hypertext
The hypertext is a system that provides a simple and consistent way to organise large data (that includes text, images, pictures videos, etc) available on the Internet. In hypertext systems, the documents contain links to other related documents on the Internet. These links are called hyperlinks, hotlink or simply links. A hyperlink is used to jump to another part of the same page or to load a different web page. Usually hypertext links appear in a different colour (typically in blue and underlined) from the rest of the text. When the cursor is moved over a text link or over a graphic link, it will change from an arrow to a hand. The hypertext words often provide a hint about the connected page. When the user returns to a page with a link he/she had already visited, the hypertext words will often be in a different colour (usually magenta), indicating that the link has already been used. However, the user can certainly use that link again.
Hyperlinks are the foundation of the web and the operation of the web relies primarily on them as it is a means of information retrieval. Producing hypertext for the web is accomplished by creating documents with HTML (Hypertext Markup Language).
Figure 13.4 Hypertext Links
Internet Service Provider (ISP)
An Internet Service Provider (ISP) is an organisation that connects its subscribers' computer using modem to the Internet. The connections can be provided by telephone lines, cable lines, or wireless connections. In order to use the Internet connection, the user has to first log on to the host computer using the username and password provided by the ISP. Some of the well known ISPs are America Online (AOL), Microsoft Network (MSN), Yahoo!, etc.
While choosing an ISP, many factors should be kept in mind for subscribing. First, the user should check the speed and consistency of the Internet access. He/she should also check ISP's reliability, that is, whether the ISP provides consistent access to the Internet or does it have frequent down times. Apart from these two criteria, the price of the ISP and other additional services provided by it should also be considered. For example, many ISPs provide free web space so that users can create their own website, free e-mail address, and much more. Last but not the least, the user should also check whether the ISP provides a round-the-clock technical assistance.
Web Server
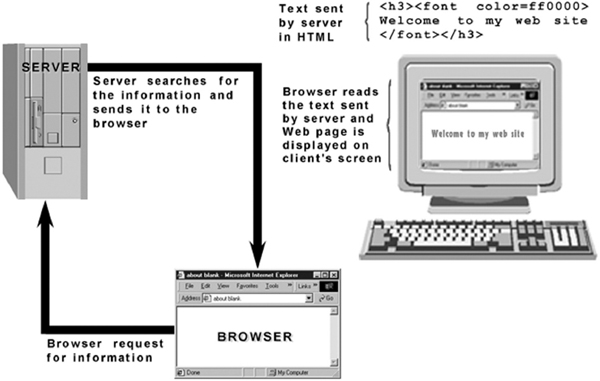
A server is a computer equipped with server software, which provides a specific kind of services to client software running on other computers. It can refer to a particular piece of software, for example, a web server, or to a machine on which the server software is running. A web server receives request from the clients, process this request, and sends the result back to the client (see Fiugre 13.5). In other words, web server fulfils the client's (browser) requests.
Figure 13.5 Data Transfer from Web Server to Browser
To view a website, the browser sends a request to the server. On receiving the request, the server sends the appropriate web page to the client's machine. The client's machine (browser) receives the information in the form of HTML commands. The browser interprets the HTML, finds all the pictures (or other types of media), and displays the information onto the user's screen.
Download and Upload
Download refers to the act of transmitting data from a remote computer on the Internet or other network to one's own computer. When the user downloads a file, he/she is actually copying a particular file from the remote computer and placing it on his/her hard drive. Downloading allows a user to save file for later use thereby reduces the time spent online and the corresponding charges.
Upload is just the opposite of download. Upload refers to the act of transmitting data from local computer to any other computer on the Internet or network. For example, a software company may upload a demonstration of its new software onto the web so that users can then download the software.
Online and Offline
The term online is commonly referred to the state of being connected to the networked computer system or Internet. For example, if you are browsing the WWW, your computer is said to be online. Being online also refers to any peripheral device (like printer) that is connected to the system and ready to use.
Offline is just the opposite of online; it refers to the state of not being connected to the remote computer or Internet. A printer or other peripheral that is not ready to use is also considered offline.
13.6 INTERNET PROTOCOLS
The communication among different types of computers connected via network is possible by using a protocol that offers a standard format and method for communication. A protocol is a formal set of rules and conventions that governs how computers exchange information over a network medium. There are large numbers of protocols that can be used in a network depending upon the need they fulfil. Some of the protocols used on the Internet are given below:
- TCP/IP (Transmission Control Protocol/Internet Protocol): It is the suite of communication protocols which is used as a standard for transmitting data over networks. TCP/IP consists of two protocols, namely, TCP and IP. The TCP (Transmission Control Protocol) is responsible for dividing the message or file into small packets at the source computer that are transmitted over the network. Then at the destination computer, it reassembles the packets into the original message or file. On the other hand, the IP (Internet Protocol) handles the address part of each packet so that it reaches the right destination. Any computer or other device connected to the Internet must support TCP/IP.
- SMTP (Simple Mail Transfer Protocol): It is a mail protocol used for sending e-mail messages from one computer to another on a network.
- HTTP (HyperText Transfer Protocol): It is the Internet protocol responsible for transferring and displaying web pages. It provides a way for web clients and web servers to communicate with each other by sending messages.
- FTP (File Transfer Protocol): It is used for transferring files and folders between computers on the Internet. It allows you to access the files stored in the remote computer connected to the Internet. It is the fastest way of transferring digital information from one computer to another.
- NNTP (Network News Transfer Protocol): It is used to transfer news messages over the Internet. The NNTP server is a computer that collects a copy of news messages from the newsgroups and allows users to read these messages. It also allows users to send their messages to the same groups.
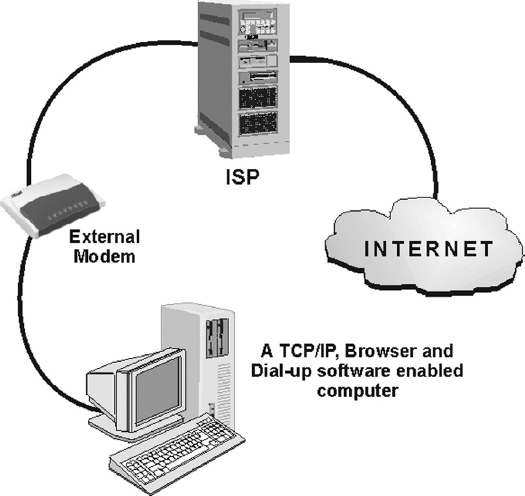
13.7 GETTING CONNECTED TO INTERNET
Now you are aware of the basic Internet terms, let us shift our focus on how to connect to the Internet. The basic requirements for getting connected to the Internet are discussed in this section.
The Computer
The computer must have at least 386-microprocessor chip with a minimum of 16MB of RAM. For a good browsing experience, use a faster chip (Pentium III/Pentium IV) with more RAM (128/256MB). In addition, a colour monitor, with at least 640 × 480 resolution and a capability of displaying a minimum of 256 colours, is also vital. The system should also possess a hard disk, with at least 200 MB of free space, to store Internet software and temporary Internet files. Since the web is a multimedia medium, you can also enjoy sound on your system with a sound card and a pair of speakers.
Modem
Apart from the previously mentioned configuration, a computer system must have a device called modem, which enables a computer to transmit data over telephone lines. A modem (acronym for modulator-demodulator) is a hardware, which converts digital data into analog signals (that is, modulation) that can be sent over an analog telephone line and convert the analog signal back into digital data (that is, demodulation). Thus, when the modem receives the data from a web server via phone system, it reconstitutes the analog signal into digital form so that the computer can understand it. The most critical aspect of the modem is its speed of operation. The speed of modem is measured in Kilobits per second (Kbps). Modern modem supports 28Kbps to 56Kbps speeds. Modems are of two types:
- Internal Modem is a card, which is fitted inside the computer with a lead running directly from the computer to the phone socket.
- External Modem is a small external box wired between the computer and the phone socket.
Internet Connection
Before connecting to the Internet, you need to buy an Internet connection from an authorised Internet Service Provider (ISP). The speed of accessing the Internet entirely depends upon the type of connection you bought from the ISP. Some of connections available for the users these days are given below:
- Dial-up: A dial-up connection is the access method that uses telephone lines to connect to the Internet. It is the most common way for individuals who use home computers to connect to the Internet. To connect to the Internet by using dial up, the user needs to specify a username, a password, and a telephone number. After the connection is established, the user can start browsing sites on the Internet.
- ISDN: It stands for Integrated Services Digital Network and is more common in business and commercial use. It was the first high-speed alternative to regular analog phone modems. ISDN involves the digitisation of telephone network so that voice, graphics, text, and other data can be provided to users from a single terminal over existing telephone wiring. Digital connections have fewer errors in transmission, which means speed of downloading graphics, web pages, sound, and so on is increased to four times faster than with dial-up modems.
- Cable Modem: A cable modem connects the user to the Internet through a cable television line. Nowadays, many cable companies offer Internet along with television accessibility. A cable modem will typically have two connections, one to the television outlet and the other to the computer. Cable modems not only provide a faster Internet access (10 to 100 times as fast as the dial-up modem), but interactivity to the television also.
- Leased Line: This facility provides reliable, high-speed Internet access ranging from 2.4 Kbps to 45 Mbps. A leased line connection is an affordable way to link two or more sites for a fixed monthly charge. Usually leased lines facility can be provided via a fibre optic or copper lines. Leased line service provides a consistent amount of bandwidth and is an excellent way to provide data, voice, and video links between sites.
- DSL: DSL or Digital Subscriber Line service is provided through an existing phone line, but it works differently than regular analog modem dial-up access. DSL operates over normal telephone lines and it can be used simultaneously with the telephone. DSL can increase the connection speed by as much as ten-fold from a standard dial-up modem.
- Broadband: This type of access is good for remote locations, where ISDN, cable or DSL are not available. It gives a decent download speed, but to upload data, the user still needs a regular analog modem to dial in, via a phone line. Satellite connection can be either a two-way service or a oneway service. In case of two-way satellite service, the data is transmitted via satellite to a dish antenna at the user's house. In one-way system, the user needs a conventional modem and telephone link to an ISP. Satellite connection is expensive but sometimes is the only fast option for people who are beyond the service area of cable and DSL providers.
Before deciding the type of Internet connectivity, one should first decide what his requirements are. If the user wants the Internet mainly for sending e-mail, occasional chats, infrequent browsing, then he should work with regular modem dial-up access. In this case, user should invest in a good quality 56Kbps modem and a good ISP. If the user is using the Internet frequently for research, downloading or uploading a fair amount of data, to play multi-player games or to use the Internet's multimedia capabilities like live audio or video streaming, then he should look into other high speed accesses such as cable modem or ISDN.
Internet Software
To connect to the Internet, a computer requires mainly three different kinds of software:
- TCP/IP: TCP/IP, or Transmission Control Protocol/Internet Protocol, is the basic communication protocol of the Internet. It allows programs on user's computer to communicate over the Internet. Usually, when you are set up with direct access to the Internet, your computer is provided with a copy of the TCP/IP. Similarly, every other computer that you may send messages to or get information from also has a copy of TCP/IP.
- Dialler Software: This software is provided by the ISP to instruct the modem to dial the phone number and to identify the user's machine to the access provider's system for access to the network.
- Browser: To use the Internet, a web browser is essential which allows the user to view the information available on the World Wide Web. Web browser is discussed in detail in Section 13.8.
Figure 13.6 Connecting to the Internet
13.8 WEB BROWSER
A web browser (or simply browser) is a software application, which provides a graphical user interface (GUI) so that the user can navigate the Internet easily by clicking on menus, icons, or buttons instead of learning difficult keyboard commands. A web browser uses the HTTP protocol to request web pages from the web server. These pages contain special instructions (written in HTML) that tell the browser how to display the web contents on the user's screen. The instructions may include hyperlinks to other web pages, information about text formatting and colour, position information for images contained in the document, and other such things. Most browsers natively support a variety of formats in addition to HTML, such as the JPEG, PNG, and GIF image formats, and can be extended to support more through the use of plug-ins (an add-on piece of software that extends the features or functionality of a larger application). The two most popular web browsers are Netscape Navigator and Microsoft Internet Explorer.
13.8.1 WEB BROWSER FEATURES
There are many web browsers available having different features. However, every browser shares some of the basic features mentioned below:
- A browser handles requests for HTML files, interprets links, and deals with embedded images, audio, and video elements.
- A browser keeps the history of the websites visited.
- A browser lets a user to save a collection of pages, allowing for later retrieval.
- A browser provides a row of buttons at the top of the browser window for browsing the Internet conveniently.
- A browser connects to an e-mail program for importing favourites/bookmarks and sending and receiving e-mails from the most commonly used applications and formats.
- A browser supports web standards currently in use such as HTML, HTTP, JavaScript, and Unicode.
- A browser supports multimedia data in three ways.
- Native Support: A browser supports some of the image formats natively. In other words, a browser presents the image as a part of the web page in the browser window.
- Plug-ins: A plug-in is a program that adds functions to the web browser, such as an audio player or a compression utility. A plug-in is a set-up within the browser through which it functions properly and correctly.
- Helper Programs: Helper programs are external applications launched by a web browser or Internet client program to view non-native file formats and data types. These programs are not integrated with the browser.
Note: In this book, we have used Internet Explorer 6.0 (IE 6.0) for explaining web browser concepts. Internet Explorer 6.0 is freely available from Microsoft (www.microsoft.com). It is also bundled with the Windows XP operating system.
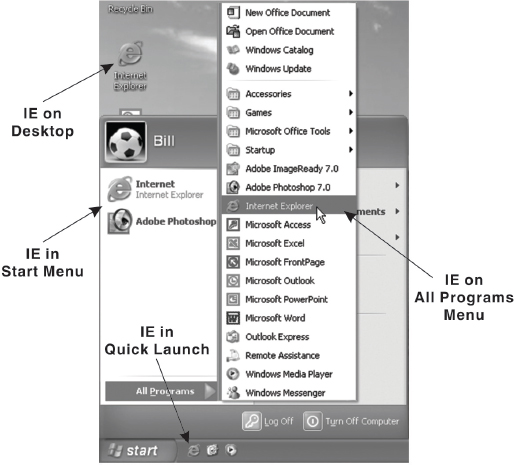
13.8.2 OPENING INTERNET EXPLORER
To open Internet Explorer, perform any one of the following steps:
- Double-click the Internet Explorer icon located on the desktop.
- Click the Internet Explorer icon from Quick Launch.
- Click Start, and select Internet Explorer.
- Click Start, select All Programs, and then select Internet Explorer.
Figure 13.7 Opening Internet Explorer
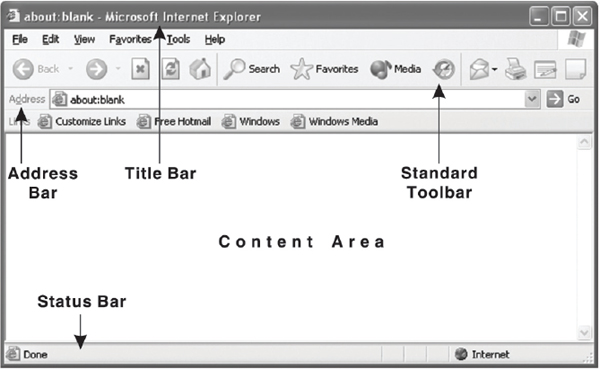
13.8.3 INTERNET EXPLORER ENVIRONMENT
When Internet Explorer is opened, the main screen of the program is displayed (see Figure 13.8). This main window has many parts to it; these parts are described in detail below.
Figure 13.8 Internet Explorer Browser Window
Title Bar
It is located at the very top of the window and tells you the title of the page you are viewing. Title bar also tells you which Internet Explorer application is currently active. In addition, like all other Microsoft applications, it has the Minimize, Restore/Maximize, and Close buttons.
Menu Bar
This bar has many different sub-menus, which control all options, functions, and commands for the entire Internet Explorer program. Some of the browsing controls can also be found in these sub-menus. Each command in the menu bar represents a menu and is activated by pressing Alt+ the underlined letter of the menu from the keyboard. Different menus include File, Edit, View, and so on.
Standard Toolbar
This toolbar contains the most frequently used commands and the browsing functions. It contains thirteen different buttons. Table 13.1 provides a brief description of the buttons of Standard toolbar.
Table 13.1 Standard Toolbar Options

Address Bar
This bar displays the Internet address (URL) of the page currently being displayed. You can access a site by typing its URL into the Address box and clicking on Go or by pressing Enter. Click the down arrow (![]() ) to the right of the Address box to view site addresses that you have previously entered here.
) to the right of the Address box to view site addresses that you have previously entered here.
Link Bar
This bar contains shortcuts to useful Internet websites. A web site can be accessed quickly by clicking the Links button.
Content Area or Document View
The content area is the portion of the window that holds the document page or other resources as the browser presents it. Any text, images, animation, links, or any other application files is shown in this area. The scroll bars located on the right side and on the bottom of this window allow the user to view the page even when the page is too large to fit in the screen. Sometimes the content area is divided into or consists of several independent portions called frames. Each frame has its own scroll bar, and the user can move through one frame while staying in the same position in others.
Status Bar
This bar displays the current state of activity of the web pages. Apart from this, other information that appears on the status bar includes the size of the web page, percentage of the web page that has been downloaded, error in the web page being downloaded, and whether the user is working online or offline.
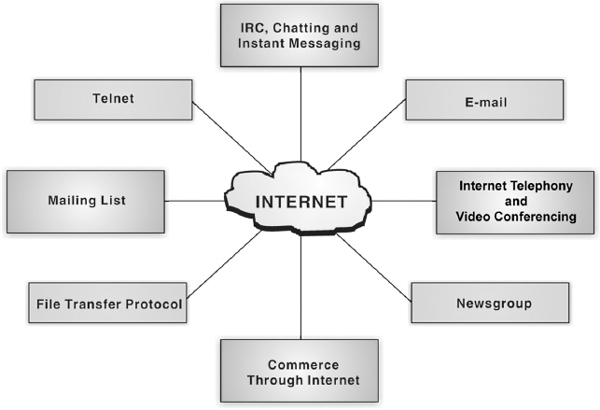
13.9 USES OF INTERNET TO SOCIETY
Today, the Internet has grown from a small network to biggest network of computers. Due to this colossal growth, the Internet has become the biggest domain of information. Nowadays, an Internet user has access to a wide variety of services such as electronic mail, file transfer, vast information resources, interest group membership, interactive collaboration, multimedia displays, real-time broadcasting, shopping opportunities, and much more. Some of the important services provided by the Internet are briefed in the following few sections.
Figure 13.9 Internet Applications
13.9.1 ELECTRONIC MAIL (E-MAIL)
Electronic mail, or e-mail, is a fast, easy, and inexpensive way to communicate with other Internet users around the world. It is one of the basic and earliest services of the Internet and the most used application on the Internet too. E-mail overcomes most of the problems and delays of getting a physical document from one person to another. Rather, it has the dual advantage of not only being faster but cheaper to use as well.
Each user of e-mail has a mailbox address to which messages are sent and the mailbox can be accessed from anywhere and at anytime. It does not matter what type of connectivity the user is having, he will always be able to use this service. One can receive and send e-mails from all systems whether it is a Windows PC or a UNIX machine. Not only this, e-mail can also be used to send documents, images, audio, video, and so on as an attachment along with the mail.
13.9.2 FILE TRANSFER PROTOCOL (FTP)
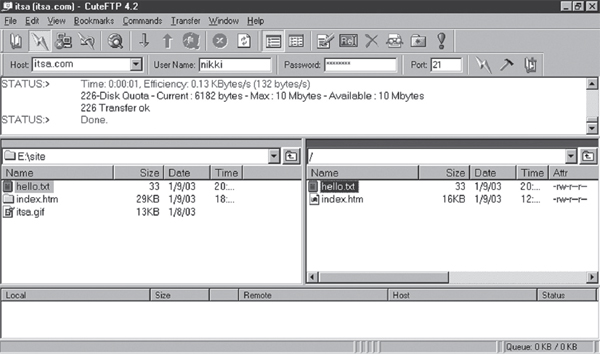
The File Transfer Protocol (FTP) is a set of rules that enables a user to transfer files from one system to another. It was the first service developed for the Internet so that government and educational institutions could easily exchange files. It allows the user to get access to the files stored in the directory of a remote computer that is connected to the Internet. Using FTP, one can upload and download files from the remote computer (known as FTP servers), if he/she has access permission on the remote machine. Though files can be transferred using e-mail, this is not a good choice if the file size is large or when there are many files. FTP sites can consist of hundreds to thousands of files with information on books, music, software, games, images, sounds, multimedia, course ware, etc. FTP can be done using the command prompt, browsers, and various GUI based FTP software such as CuteFTP and WS_FTP.
Figure 13.10 FTP using Graphical FTP Software
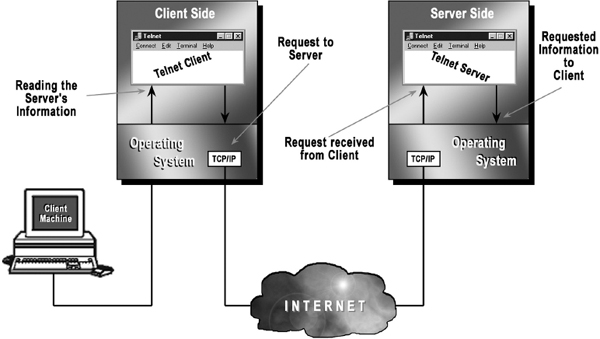
13.9.3 TELNET
The word “telnet” is derived from telecommunications and net work and is a protocol that allows a user to log on to a remote computer. Telnet is also known as remote login, which means connecting one machine to another in such a way that a person may interact with another machine as if it is being used locally. It means that someone in New Delhi could connect to a computer in the New York City Public Library and search the card catalogue the same way as someone located at a terminal in the library. Once connected, the user's computer emulates the remote computer. When the user types in commands, they are executed on the remote computer. The user's monitor displays what is taking place on the remote computer during the telnet session.
THINGS TO REMEMBER
Telnet
The telnet client computer must run a telnet client application and the telnet server must run a telnet server application. Moreover, the user's machine has to be connected to the Internet or to a network in order to use telnet. In addition, to transmit information between the telnet client and the telnet server, the TCP/IP protocol is used. Note that unlike FTP, telnet does not have file transfer capability. It can only be used to access information, run programs, and edit files with the help of certain telnet commands.
The user's computer, which initiates the connection, is referred to as the local computer or telnet client, and the machine being connected to, which accepts the connection, is referred to as the remote computer or telnet server.
Figure 13.11 Remote Login through Telnet
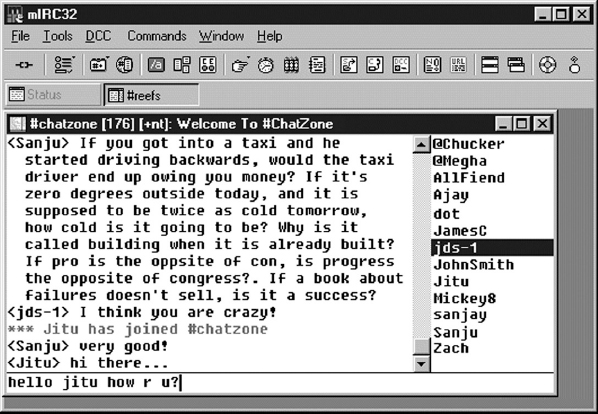
13.9.4 INTERNET RELAY CHAT (IRC)
IRC or Internet Relay Chat is a service on the Internet that allows people to communicate in real time and carry on conversations via the computer with one or more people. It provides the user with the facility to engage in simultaneous (synchronous) online “conversations” with other users from anywhere in the world. Unlike other forms of group communication on the Internet, chat is an instant communication. However, both parties must be connected to the Internet and that too at the same time, running the right software and actively participating in order to chat.
Figure 13.12 Internet Relay Chat
Generally, the user runs a program (called client) to connect to an IRC server. The server relays information to and from other servers on the same net. Popular IRC client applications are mIRC, Virc, and LeafChat. Once connected to an IRC server on an IRC network, the user will usually join one or more “channels” (also known as chat rooms) and converse with others there. Each channel is devoted to a different topic. Conversations may be public (where everyone in a channel can see what the user types) or private (messages between only two people, who may or may not be on the same channel).
13.9.5 CHATTING AND INSTANT MESSAGING
Chat programs allow users on the Internet to communicate with each other by typing in real time. They are sometimes included as a feature of a website, where users can log into chat rooms to exchange comments and information about the topics addressed on the site. For example, America Online is well known for sponsoring a number of topical chat rooms. Chatting has become one of the “killer applications” of Internet and has become quite popular with all kinds of Internet users. It is quite cheap to chat online. Although e-mail is also a cheap source of communication but it is not done on “real time” and the response to the message solely depends on the recipient. Note that even though chatting is based on standardised IRC system, but unlike IRC, the user does not need to have any special software to connect to any chat rooms.
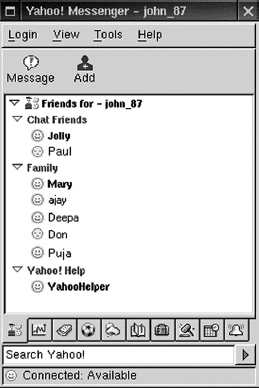
A variation of chat is instant messaging where a user on the web can contact another user currently logged in and type a conversation. To avail this Internet service, the user must have software called instant messenger installed on the system. Instant messaging is just as if making a text-only phone call over the Internet, that is, the user is “talking” to the other person (possibly more) instantly. There are various products out there for instant messaging such as MSN Messenger and Yahoo Messenger.
Figure 13.13 Instant Messenger
13.9.6 INTERNET TELEPHONY
Internet telephony is the use of the Internet rather than the traditional telephone company infrastructure, to exchange spoken or other telephonic information. It consists of hardware and software that enable people to use the Internet as a transmission medium for telephone calls. There are many Internet telephony applications available. Some applications such as CoolTalk and NetMeeting, come bundled with popular web browsers.
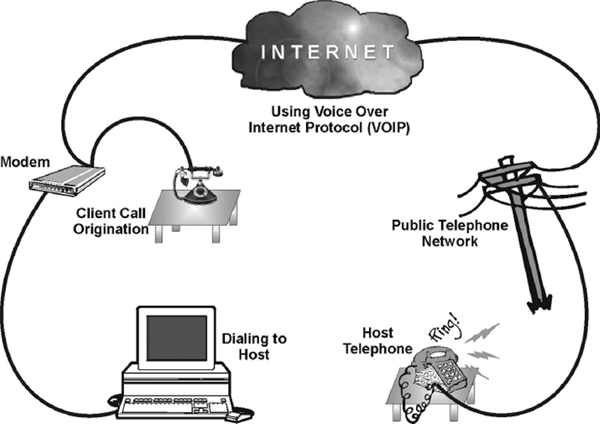
The required hardware for Internet telephony generally (see Figure 13.14) consists of end devices (either traditional telephones or audio-equipped personal computers) and gatekeepers that provide call admission control, bandwidth management, addresses translation, authentication, and user location. They communicate with each other using the Voice Over Internet Protocol (VOIP). For the cost of a local connection to their service providers, users can call anywhere in the world. Note that there is no single Internet phone standard at this time. Therefore, participants need to use the same software at each end of the connection.
Figure 13.14 Internet Telephone
13.9.7 VIDEO CONFERENCING
Video conferencing uses the same technology as IRC, but also provides sound and video pictures. It enables direct face-to-face communication across networks. A video conferencing system has two or more parties in different locations, which have the ability to communicate using a combination of video, audio, and data. A video conference can be person to person (referred to as point-to-point) or can involve more than two people (referred to as multipoint) and the video conferencing terminals are often referred to as endpoints.
In this form of meeting, participants in remote locations can view each other and carry on discussions via web cameras, microphones, and other communication tools. The following five elements are common to all video conferencing endpoints:
Figure 13.15 Video Conferencing
- Web Camera: It captures live images to send across the network.
- Visual Display: It displays the images of the people taking part in the video conference.
- Audio System: It includes both microphones to capture audio from the endpoint and loudspeakers to play back the audio received from other endpoints across the network connection.
- Compression: Videos are very bandwidth-intensive and they take a long time to load. Therefore, video systems include technologies, often referred to as codecs, to compress and decompress video and audio data, allowing transmission across a network connection in near-real time.
- User Interface and Control System: The user interface allows the users to control interactions, for example, placing calls, storing and locating numbers, and adjusting environment settings such as volume. The control system handles the underlying communication that takes place between endpoints.
Video conferencing has many benefits, as a tool for both teaching and learning. A key factor is that it provides real-time, visual communication, unlike other communications methods such as e-mail. Video conferencing technology is still in its infancy, and one of its major limitations is the bandwidth (the volume of information per unit time that a computer or transmission medium can handle) available on the Internet. As the protocols and applications for video conferencing develop higher resolution and improved speed, participation will increase.
13.9.8 COMMERCE THROUGH INTERNET
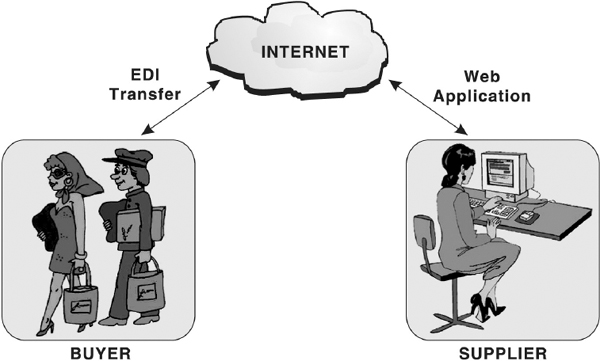
Today business is taking place through electronic telecommunication media. Nowadays, various organisations offer the facility of shopping online. This type of business model is known as Electronic Commerce or E-commerce. E-commerce refers to buying and selling goods and services online. It integrates communication, data management and security capabilities, which allow organisations to exchange information about the sales of goods and services. Essentially, it is the end-to-end digital exchange of information needed to conduct business including Electronic Data Interchange (EDI) and Electronic Funds Transfer (EFT). EDI is the computer-to-computer exchange of routine business transactions including payments, information exchange, and purchase order requests. EFT is a technology that allows the transfer of funds from the bank account of one person or organisation to that of another.
While discussing about e-commerce, we normally talk about virtual shopping malls, up front store where the user virtually visits and selects the product(s) of his/her choice. After selecting the desired product(s), the payment for the purchase is done. Online payment can be done through credit card. Techniques for cash transactions have also been developed in the form of Internet money such as Cyber cash and Digital money. After transfer of money, the items are received at the doorstep, which means delivery of the product is done at the address desired by the buyer.
Figure 13.16 Electronic Commerce
Through the development of e-commerce, the Internet has established an electronic global worldwide market that operates 24 hours and 365 days a year. Organisations and individuals are able to market goods and services, while purchasing is supported by secure facilities such as digital signatures (the process that operates on a message to assure message source authenticity and integrity) and encryption (a method of ensuring data secrecy). Developments in software mean that an increased number of facilities are becoming available all the time. Some of the well-known e-commerce sites are www.amazon.com and www.ebay.com.
The increased use of mobile devices such as PDAs (Personal Digital Assistants) and mobile phones has opened a new horizon of proliferation in the electronic market and has coined a new term “Mobile Commerce”. Mobile commerce or M-commerce refers to transactions through a mobile phone network and data connection that result in the transfer of value (monetary or otherwise) in exchange for goods and services. Mobile commerce has evolved as a new and simpler concept to operate financial transaction through mobile phones and it includes services such as banking, payment, and ticketing. M-commerce users may view and interact with information that appears through SMS (Short Message Service), WAP (Wireless Application Protocol) or a standard HTML browser on a PDA, web-enabled mobile phone or laptop computer connected to a mobile phone on a wireless network.
13.9.9 NEWSGROUPS (USENET)
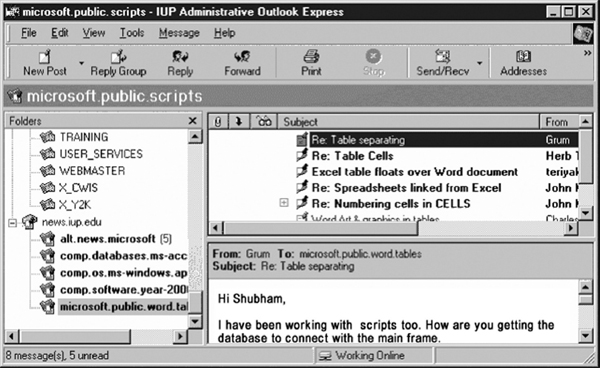
Newsgroups are international discussion groups that focus on a particular topic and helps in gathering information about that topic. The topics discussed here cover all the fields such as politics, computers, technology, and many more. The information or articles that make up the “news” are written by people interested in a specific topic. These articles are posted to the newsgroup so that others can read, reply, and comment on them. To read and post articles in a newsgroup, newsreader software such as Microsoft Outlook Express or Netscape News is required. Some newsgroups are devoted to current events and headlines. However, newsgroups usually describe topical discussion groups, not “the news” in the traditional sense. Most newsgroups exist on a network known as Usenet, which contains thousands of newsgroups.
Figure 13.17 Reading News with Newsreader
Newsgroups provide a source of information and a medium through which users can ask questions from the Internet community. They provide a forum for users to discuss topics of mutual interest. It is normal to post the rules, restrictions, and subject matter for the newsgroup in a message called Frequently Asked Questions (FAQ). To simplify the selection of suitable newsgroups, they are divided into subject classifications known as top-level categories. These top-level categories are then further sub-divided and this continues down the hierarchy. There are 20 top-level categories including those shown in Table 13.2.
Table 13.2 Newsgroups Prefixes and Forums
| Prefixes | Forums |
| biz | Business |
| comp | Computers and Software |
| news | News and topical subjects |
| rec | Recreation and entertainment |
| sci | Science |
| soc | Social issues and socialising |
| talk | Debate and discussion |
| Misc | Anything else |
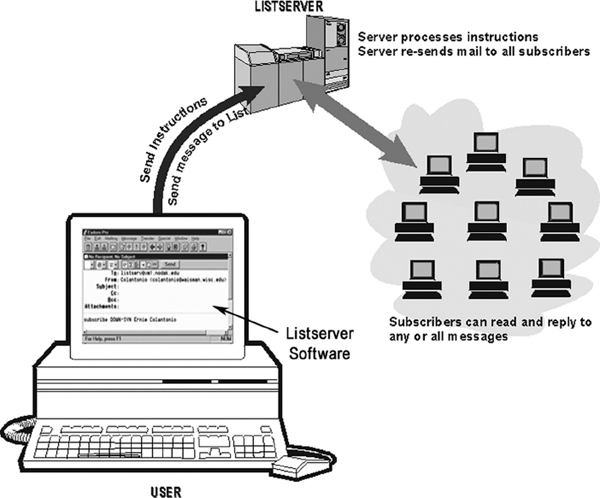
13.9.10 MAILING LISTS (LISTSERVER)
The Internet is home to a large community of individuals who carry out active discussions, organised around topic-oriented forums that are distributed via e-mail. This method of Internet communication is known as mailing list and it enables people with similar interests from all over the world to communicate and share information with each other. The mailing list groups are administered by a software program known as listserver. There are varieties of programs available such as Listserv and Majordomo. A listserver watches for incoming mail on a certain mailbox continuously and forwards any message to a list of other addresses. Such a mailing list can bring people together with a common interest.
THINGS TO REMEMBER
Mailing Lists
There are hundreds of mailing lists, each for a different subject. Subscribers can send special messages to a separate address to retrieve files from the archive or to get other information about the mailing list. When the user subscribes to a listserver, messages from the other subscribers are automatically sent to their electronic mailbox (E-mail address). Note that to participate in a listserver discussion, the user must have an E-mail account. To subscribe to a listserver, the user has to send an E-mail message to the desired listserver located on computer networks throughout the world.
13.10 ELECTRONIC MAIL
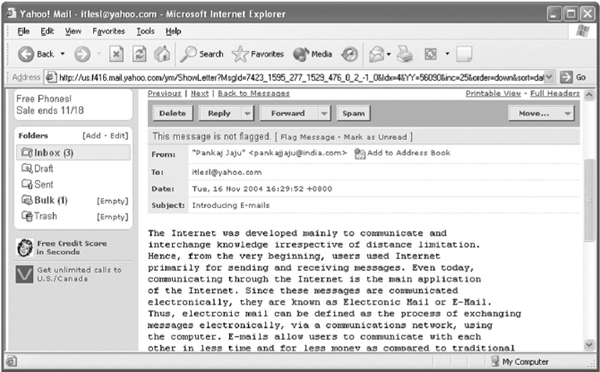
The Internet was developed mainly to communicate and interchange knowledge irrespective of the distance limitation. Hence, from the very beginning, users used Internet primarily for sending and receiving messages. Even today, communicating through the Internet is the main application of the Internet. Since these messages are communicated electronically, they are known as Electronic Mail or E-Mail. Thus, electronic mail can be defined as the process of exchanging messages electronically, via a communications network, using the computer. E-mails allow users to communicate with each other in less time and at nominal cost as compared to traditional phone or mail services. Apart from a textual message, e-mails can also consist of other data formats such as pictures, sound, and video. E-mails can be sent anywhere in the world using your computer and a modem. Its delivery is almost instant and is very economical to use especially for international messages, costing only the price of the telephone connection to the ISP. You may send many messages at one time or just one to a designated location.
13.10.1 E-MAIL ADDRESS STRUCTURE
In order to use e-mail, one must have access to the Internet and an e-mail account. An e-mail account is a service that allows the user to send and receive e-mails through the Internet. Usually, e-mail accounts are provided as part of Internet Service Provider's (ISP's) monthly packages. One can also obtain free e-mail accounts such as Yahoo and Hotmail on the Web. An e-mail account provides a unique e-mail address and a mailbox where the user can save all his/her mails.
Generally, there are two parts of an e-mail address: the logon identity and the identity of the e-mail server. These are separated by the symbol @ (pronounced as at the rate). For example, a typical e-mail address would look like:
The first part of the address indicates the identifiable name of the user. It is just like a home address (and it is unique) so that the mails could be sent to that address. The user name is a name, which was assigned to or desired by the user, while signing up for e-mail address. For example, [email protected]. The @ symbol in the address is used to separate the user name from the rest of the address. Next comes the host name (itlesl), also called the domain name. This refers to the mail server, the computer where the recipient has an electronic mailbox. It is usually the name of a company or organisation. The end of the domain name consists of a dot (.) followed by three or more letters (such as .com or .net). This part of the domain name indicates the type of organisation or the country where the host server is located. Note that you may find variations in e-mail addresses, but these common elements will always remain the same.
Note: There are no spaces in an e-mail address and it is usually (but not always) in lower case letters.
13.10.2 CHECKING E-MAILS
To send and receive e-mail, the user must have an e-mail account. Let us assume that we have an e-mail account such as [email protected] and we are logged on to the Internet. Now follow the steps given below to check mails.
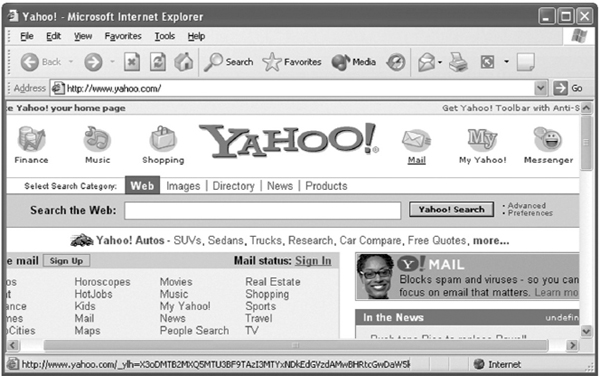
- Open Internet Explorer and type www.yahoo.com into the address bar and press the Enter key to display Yahoo's home page. Now click the Mail link as shown in Figure 13.19.
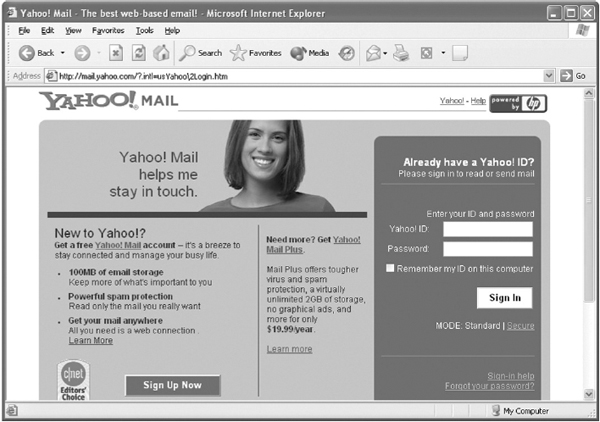
- When the Mail link is clicked, Yahoo loads a new web page (see Figure 13.20), which allows users to log on to their mail accounts. To log in, you have to enter your username (e-mail address) along with the password. After entering the information, either press the Enter key or click the Sign In button.
In case, you do not have a Yahoo mail account, press the Sign Up Now button to open the registration page. Just fill the registration form to get registered with Yahoo and obtain a unique Yahoo e-mail account.
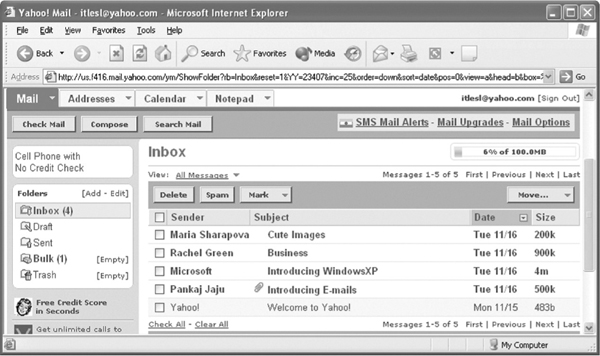
- To check for new e-mail(s), click the Inbox link. The screen would look as shown in Figure 13.21.
Figure 13.19 Home Page of Yahoo
Figure 13.21 Inbox Page
- To read e-mail, simply click on the subject of the e-mail. The screen would look as shown in Figure 13.22.
- After reading the mail, you can reply to the mail or forward the same mail to other persons by clicking the Reply and Forward buttons, respectively. In case, you do not want to keep the mail in the mailbox, click Delete button to delete it.
13.10.3 SENDING E-MAILS
One of the important functions of an e-mail service is to provide a platform to send e-mails. A user can reply to the received e-mail or send a new e-mail. To send e-mail, follow the steps given below:
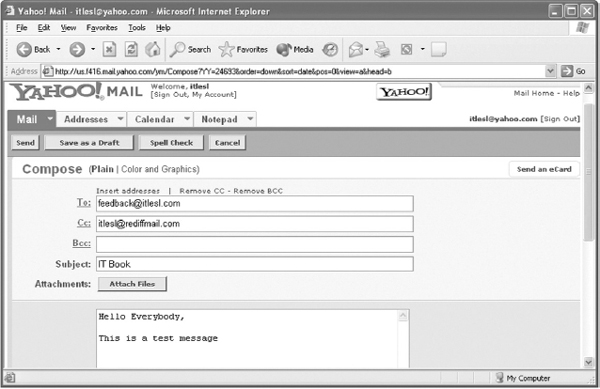
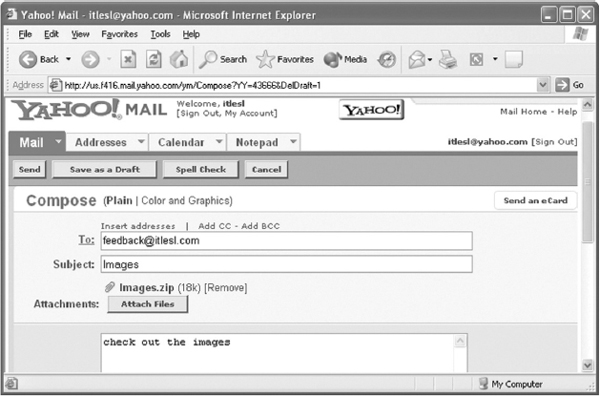
- Click on the Compose button so that you can create and send e-mail to the desired address. When the Compose button is clicked, the compose page will be displayed as shown in Figure 13.23.
The key elements of the compose window are listed below:
- To: It denotes to whom the mail is to be sent. The user has to write the recipient's e-mail address.
- Cc: Cc or Carbon copy is used to specify the addresses of all the recipients who will also receive copies of the same mail. It is used to send the same message to several people (all the addresses are separated with commas).
Figure 13.23 Compose Page
- Bcc: Bcc or Blind carbon copy is used to send message to several addresses without showing everyone all the addresses.
- Subject: It denotes the subject of the message as specified by the sender.
- Attachment: This link is used to send files, created with other programs such as Microsoft Word or a Zip file, along with (or attached to) the e-mail.
- 2. Now write the desired contents in the text area, and after composing, click the Send button.
13.10.4 E-MAIL ATTACHMENTS
Earlier we discussed how to send and receive e-mails that involves only text message. However, sometimes one needs to send or receive files like compressed (.ZIP) files or any executable (.EXE) files. Since Internet Explorer does not natively support these files, you will have to ‘attach’ them in your e-mails.
Receiving and sending attachment is similar to receiving and sending normal mails, with some extra steps. To view an e-mail containing an attached file, follow the steps given below:
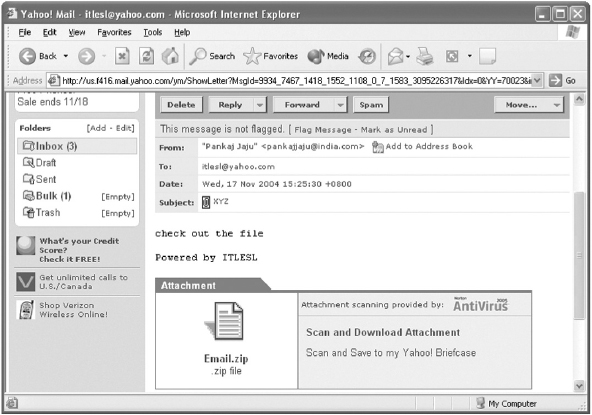
- When you open an e-mail that contains an attachment, it will be displayed as an icon in the lower part of the page, as shown in Figure 13.24.
- Click on the icon or the Scan and Download Attachment link, which displays the File Download dialog box. This dialog box prompts you to save the attached file onto your hard disk.
Note: Always scan the attached file(s) for viruses. In addition, it is a good practise to avoid unsolicited attachments because they may contain virus.
To send an attachment with the mail, follow the steps given below:
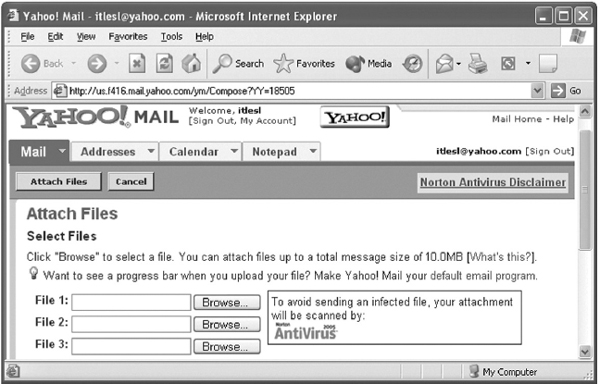
- When you compose a mail, click the Attach Files button (see Figure 13.23), which will display a page similar to the one shown in Figure 13.25.
Figure 13.24 Attachment
- Click on the Browse button to display the Choose file dialog box, which allows you to select desired file to be sent as an attachment. Repeat this process to attach multiple files.
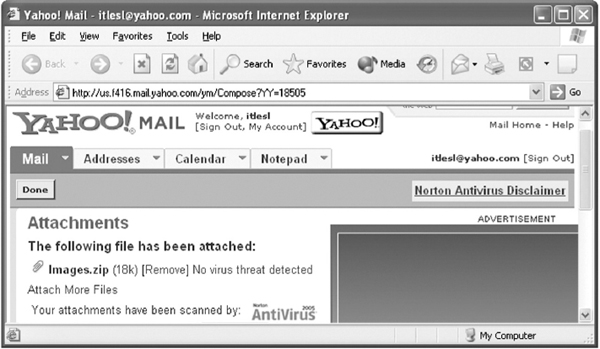
- Click on Attach Files button to attach the file(s) to your message. When Yahoo attaches the file(s), it will display it in a new page, as shown in Figure 13.26.
- Click the Done button to return to the compose page. This page will now display all the attached file's names over the Attach Files button (see Figure 13.27).
- Finally, click the Send button to send the mail along with the attachments.
Figure 13.25 Attach Files Page
Figure 13.26 Attachments Page
Figure 13.27 Sending E-mail with an Attachment
13.10.5 HOW E-MAIL WORKS
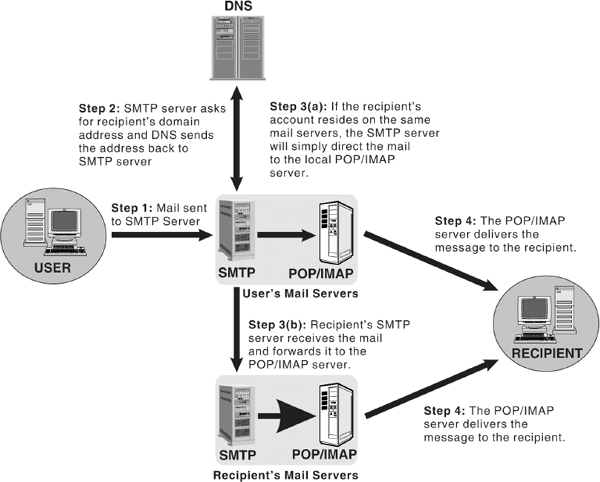
To send e-mail, one needs a connection to the Internet and access to a mail server, which forwards the mail. The standard protocol used for sending e-mail is called SMTP (Simple Mail Transfer Protocol). It works in conjunction with POP (Post Office Protocol) and IMAP (Internet Mail Access Protocol) servers.
Figure 13.28 Working of E-mail System
When an e-mail is sent to a person, who has an e-mail address like [email protected], it is broken down into two parts: xyz (the recipient's account name) and hisdomain.com (the recipient's domain name). The SMTP server contacts a DNS (Domain Name Service) server, and asks for the location of hisdomain.com. The DNS server sends the address back to the SMTP server. The SMTP server then sends the e-mail message to the SMTP server where hisdomain.com is located. This SMTP server delivers the e-mail message to xyz's account on the POP or IMAP server. Finally, when xyz logs on to his computer and opens his e-mail client, his e-mail client requests the POP or IMAP server to send all mails from the account to his computer. Note that if you are sending mail to someone whose account resides on the same mail servers, the SMTP server will simply direct the mail to the local POP or IMAP server, where it will be delivered to the appropriate account.
13.10.6 NETIQUETTE
Communicating online, whether by e-mail, chat rooms or message boards, is informal, quick, and easy. However, there are certain unsaid rules that one should follow. On the Web, you are what you write, so take some pride in your work and do it correctly. The standard rules of a polite Internet behaviour are called netiquette. Like e-mail and other online communication, the rules of netiquette are short and to the point. Some of these rules are briefed below:
- Never do anything online that you would not do in real life. Even while communicating online, you are dealing with real people. Therefore, do not say anything over the Internet that you would not say on their faces.
- Good discussion should always be welcomed but do not waste other people's time with useless queries. For example, if you respond to a listserver to send a private message to one person, you have wasted a lot of people's time. Moreover, before participating in a newsgroup discussion, one should read the FAQs (frequently asked questions).
- Do not use all upper case letters because using all caps equates to yelling. A single word in upper-case (to emphasise) is acceptable, but use upper case words sparingly.
- Never send unsolicited junk mail and do not forward junk mail or chain letters.
- Respect other people's privacy and copyrights. Treat the mails that you receive as confidential unless the sender permits you to share it with others. Moreover, if you are quoting something from an online book or paper, always mention the source.
- When posting a message to a public bulletin board, forum or newsgroup, stick to the topic. Posting unrelated comments to a newsgroup is known as spamming, which leads to another unpleasant Internet practice known as flaming. Flaming is the practice of attacking people on a personal level.
- Respect other people's time and bandwidth. While mailing or posting to a discussion group, you are taking up other people's time. It is your responsibility to ensure that the time they spend reading your posting is not wasted. Hence, be concise and brief while mailing and posting information online.
- When someone makes a mistake, whether it is a spelling error, an unnecessarily long answer, be kind about it. If it is a minor error, try to avoid it and even if you feel strongly about it, be polite and point it preferably by private e-mail rather than in public.
13.10.7 ADVANTAGES AND DISADVANTAGES OF E-MAIL
E-mail can be sent anywhere in the world to anyone who has an e-mail address. It can take days to send a letter across the country and weeks to go around the world. To save time and money, more and more people are using e-mail. However, the slightest error in the address can deliver the mail to the wrong address. Hence, like there are two faces of a coin, e-mail also comes with its own share of benefits and limitations.
Table 13.3 Advantages and Disadvantages of e-mail
| Advantages | Disadvantages |
| The delivery of messages is very fast, sometimes almost instantaneous, even though the message is meant for overseas or just to a friend next door. | Although e-mail is delivered instantly, the recipient may or may not read his/her mail on time. That defeats the quickness of electronic mailing. |
| The cost of e-mailing is almost free as it involves negligible amount of telephone and ISP charges. | The user must stay online to read and write more than one mail. In addition, most webmail either display advertisements during use or append them to mails sent. It results in increased size of the original mail, which brings a significant decrease in speed of use. |
| Multiple copies of the same message can be sent to a group of people at the same time and can be sent as easily to a single person. | Since e-mail passes through a network, therefore it may be intercepted in between. |
| Pictures, documents, and other files can also be attached to messages. | The slightest error in the address or a failure in one of the links between sender and receiver is enough to prevent a delivery. |
13.11 SEARCH ENGINES
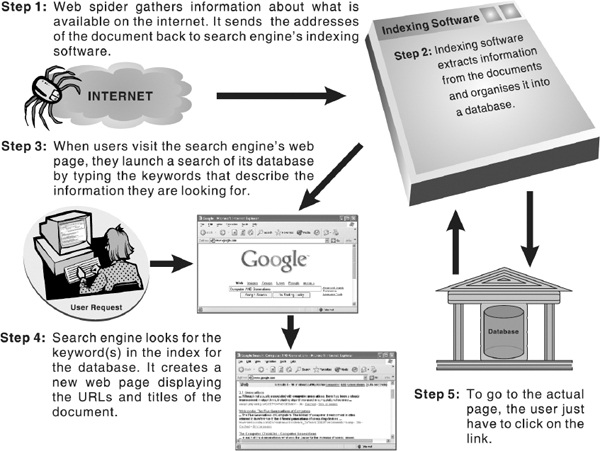
The Internet provides access to a wealth of information on countless topics contributed by people throughout the world. However, the Internet is not a library in which all its available items are identified and can be retrieved by a single catalogue. In fact, no one knows how many individual files (could be in billions) reside on the Internet. Hence, to conduct a search on the Internet, a special search tool known as search engines is used. A search engine searches a database of Internet files collected by a computer program called a wanderer, crawler, or spider. It allows the user to enter keywords relating to particular topics and retrieve information about the Internet sites containing those keywords. As such, a search engine consists of four components:
- Spider: Program that traverses the Web from link to link, identifying and reading pages.
- Indexing Software: Program that analyses web pages that are downloaded by spiders.
- Database: Warehouse of the web pages downloaded and processed.
- Search Engine Mechanism: Software that enables users to query the index and that usually returns results in term relevancy ranked order.
A search engine does not really search the Web directly. To find information on the millions of web pages, a search engine employs special software, called spiders. After spiders find pages, they pass them on to another computer program for indexing. This program identifies the text, links, and other content in the page and stores it in the search engine database's files so that the database can be searched by keyword. Note that creating index and updating search database is a never-ending process because of the constantly changing nature of the Web. As a result, the spiders are always ‘crawling’.
Figure 13.29 Working of a Search Engine
When users search the Web using a search engine, they are provided with the links of all the searched web pages. On clicking on the links provided in a search engine's search results, the current versions of the web pages are retrieved from the server.
Figure 13.30 Google Search Engine
13.11.1 SEARCHING THE INTERNET
With most search engines, you fill out a form with your search terms and then ask the search engine to find web pages relevant to the search terms. Some of the well-known search engines are www.google.com, www.hotbot.com, www.lycos.com, and www.altavista.com.
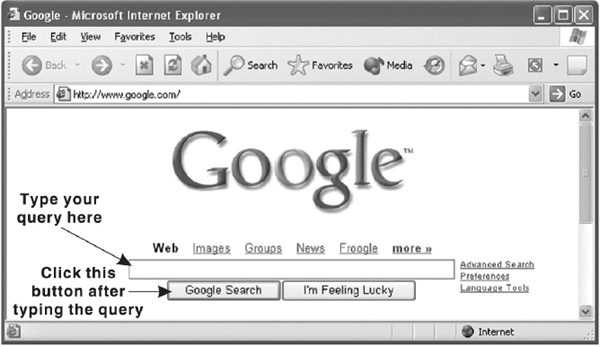
Let us assume that you want to search the Web to get information regarding computer generations. To do this, first open the search engine's website (such as www.google.com). Now type your keyword(s) in the search box and click the Google Search button or press Enter (see Figure 13.30).
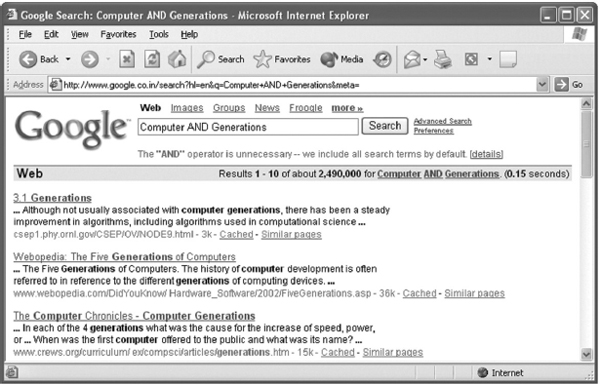
The engine searches its index and generates a page with links to those resources containing some or all of the search terms. Clicking on any link opens a website or web page in which the searched keyword appears.
Figure 13.31 Search Result Page
13.11.2 REFINING THE SEARCH
The major search engines allow the user to choose whether to search for the exact typed phrase, all the words in the phrase, any of the words in a phrase, and so on. However, a few search engines do not provide such options. In this case, the user can refine the search by adding one or more words or symbols to the search topic.
- AND: It is used to search for two or more terms on the same page. Type the word AND between the terms (for example, poverty AND crime) or put a plus sign right before the second term (example: poverty+crime).
- OR: It is used to search for either of two (or more) terms on the same page. Type the word OR between the terms (for example, college OR university).
- NOT: It is used to search for pages that include the first term but not the second. Type the words NOT between the terms (for example, cats NOT dogs) or put a minus sign right before the second term (for example, cats-dogs).
- “”: Double quotes are used to search for an exact phrase. For example, “desktop wallpapers”.
- (): Parentheses are used to group parts of the search phrase. For example, type desktop AND (themes OR wallpapers). This returns pages with the words desktop and themes or both the words themes and wallpapers.
- *: Asterisk is used to search for various forms of a word. For example, prior* returns pages with the words prior, prioritise, priority, and so on.
LET US SUMMARISE
- Internet is a worldwide system of computer networks, which allows the participants to share information. The foundation of Internet was laid in 1969 by the Department of Defense (DOD) of United States of America.
- Nobody really owns or controls the Internet. However, there are some governing bodies overseeing the technical aspects of the Internet. These are the bodies that define how the Internet works and how new technology is to be implemented.
- The entire structure of the Internet can be viewed as composed of a few basic components including host, networks, and routers.
- The World Wide Web (abbreviated as the Web or WWW) is a collection of linked documents or pages, stored on millions of computers and distributed across the world.
- A web page is a document on the WWW, which is created with HTML (Hypertext Markup Language). The web pages are linked together through hyperlinks, which enables the user to jump from one web page to another by clicking on a link.
- A website is a set of related (linked through hypertext links) web pages, published by an organisation or an individual. All the websites on the Internet constitute the World Wide Web.
- A home page (also called index page) is the starting point or a doorway to the website; it refers to the web page that identifies a website and contains the hyperlinks to other web pages in the website.
- A browser (short for web browser) is special software that enables users to read/view web pages and jump from one web page to another. It is the software that is needed to find, retrieve, view, and send information over the Internet.
- Each web page has a unique address, called a Uniform Resource Locator ( URL ) that identifies its location on the Internet.
- The hypertext is a system that provides a simple and consistent way to organise large data (that includes text, images, pictures videos, etc) available on the Internet. In hypertext systems, the documents contain links to other related documents on the Internet. These links are called hyperlinks, hotlink or simply links.
- An Internet Service Provider (ISP) is an organisation that connects its subscribers' computer using modem to the Internet. Some of the well known ISPs are America Online (AOL), Microsoft Network (MSN), Yahoo!, etc.
- A web server receives request from the clients, process this request, and sends the result back to the client. In other words, web server fulfils the client's (browser) requests.
- Download refers to the act of transmitting data from a remote computer on the Internet or other network to one's own computer. On the other hand, upload refers to the act of transmitting data from local computer to any other computer on the Internet or network.
- A protocol is a formal set of rules and conventions that governs how computers exchange information over a network medium. Some of the protocols used on the Internet are TCP/IP, SMTP, HTTP, FTP, and NNTP.
- Modem is a device that allows computers to communicate over telephone lines. It converts digital data into analog signals that can be sent over an analog telephone line and converts the analog signal back into digital data.
- Some of the common types of Internet connections available for the users these days are dial-up, ISDN, cable modem, leased line, DSL, and broadband.
- To connect to the Internet, a computer requires mainly three different kinds of software: TCP/IP, dialler software, and browser.
- TCP/IP is the basic communication protocol of the Internet. It allows programs on user's computer to communicate over the Internet.
- The dialer software is provided by the ISP to instruct the modem to dial the phone number and to identify the user's machine to the access provider's system for access to the network.
- A web browser (or simply browser) is a software application, which provides a graphical user interface (GUI) so that the user can navigate the Internet easily by clicking on menus, icons, or buttons instead of learning difficult keyboard commands.
- There are many web browsers available having different features. However, every browser shares some of the basic features like handling requests for HTML files, interpreting links, saving a web pages, connecting to an e-mail program, and so on.
- The content area is the portion of the window that holds the web page present in the current tab. Text, images, animation, and links available on the web page appear in this area.
- Status bar displays the current state of activity on the web page. The information that appears on the Status bar includes the size of the web page, percentage of the web page that has been downloaded, error in the web page being downloaded, and so on.
- Electronic mail, or e-mail, is a fast, easy, and inexpensive way to communicate with other Internet users around the world. It is one of the basic and earliest services of the Internet and the most used application on the Internet too.
- The File Transfer Protocol (FTP) is a set of rules that enables a user to transfer files from one system to another.
- Telnet is a protocol that allows a user to log on to a remote computer. Also known as remote login, it connects the user's machine to another in such a way that the user may interact with another machine as if it is being used locally.
- Internet Relay Chat (IRC) is a service on the Internet that allows people to communicate in real time and carry on conversations via the computer with one or more people.
- A chat room is a virtual meeting room where computer users can communicate with each other in real time. People from all over the world can come together in a chat room to discuss topics of mutual interest.
- Internet telephony is the use of Internet instead of traditional telephone infrastructure to exchange spoken or other telephonic information. It consists of hardware and software that enable people to use the Internet as a transmission medium for telephone calls.
- Video conferencing is a form of meeting in which participants in remote locations can view each other and carry on discussions via web cameras, microphones, and other communication tools.
- E-commerce refers to buying and selling goods and services online and if the transaction is done through a mobile phone network, it is known as mobile commerce or m-commerce.
- Newsgroups are international discussion groups that focus on a particular topic and helps in gathering information about that topic. To read and post articles in a newsgroup, newsreader software such as Microsoft Outlook Express or Netscape News is required.
- Mailing list enables people with similar interests from all over the world to communicate and share information with each other.
- Communicating online, whether by e-mail, chat rooms or message boards, is informal, quick, and easy. However, there are certain unsaid rules that one should follow. The standard rules of a polite Internet behaviour are called netiquette.
- To conduct a search on the Internet, a special search tool known as search engines is used. Search engine searches a database of Internet files collected by a computer program called a wanderer, crawler, or spider. It allows the user to enter keywords relating to particular topics and retrieve information about the Internet sites containing those keywords. Some of the well-known search engines are www.google.com, www.hotbot.com, www.lycos.com, and www.altavista.com.
EXERCISES
Fill in the Blanks
- A computer on a network that requests files from another computer is known as ____________.
- Each web page has a unique address, called ____________ that identifies its location on the Internet.
- The ____________ is a collection of linked documents or pages, stored on millions of computers and distributed across the world.
- A program that enables users to read/view web pages and jump from one web page to another is known as ____________.
- ____________ refers to the act of transmitting data from a remote computer on the Internet or other network to one's own computer.
- The US Department of Defense laid the foundation of the Internet with a network called ____________.
- AltaVista, Google, and HotBot are the examples of ____________.
- Internet Explorer is a ____________ that allows user to communicate, locate, display, and use web documents.
- The technique for ____________ is known as Telnet.
- The mailing list groups, administered by a software program known as ____________.
Multiple Choice Questions
- URL is…………………….
- (a) A computer software program
- (b) A type of web server
- (c) The address of a document or “page” on the World Wide Web
- (d) An acronym for Unlimited Resources for Learning
- Which of the following connectors is not used for searching?
- (a) *
- (b) {}
- (c) “”
- (d) ()
- What does the URL http://www.uni.edu tell you about the source?
- When a user subscribes to a newsgroup:
- (a) All new posts are e-mailed to the user automatically
- (b) The user must agree with everything said in that newsgroup
- (c) The user is billed annually for the subscription
- (d) The user is barraged with Spam
- The Internet is owned by:
- (a) The US government
- (b) A consortium of telecommunications companies
- (c) The IETF
- (d) None of the above
- A home page is:
- (a) A web page created by an individual home user, as opposed to one created by a corporation
- (b) The web page you like to visit the most
- (c) The entry page of most websites
- (d) A web page you eventually reach by clicking a series of hyperlinks
- Which of the following is not a type of Internet connection?
- (a) ISDN
- (b) Dial up
- (c) Leased line
- (d) ISP
- Which of the following components of Internet Explorer contains shortcuts of useful Internet websites?
- (a) Standard toolbar
- (b) Address bar
- (c) Link bar
- (d) Explorer bar
- Which one is not the language of Internet?
- (a) Perl
- (b) Cobol
- (c) XML
- (d) HTML
- Choose the odd one out.
- (a) Web page
- (b) Home page
- (c) Index page
- (d) Cover page
State True or False
- WWW cannot incorporate sound.
- All URLs are unique.
- Telnet cannot be used for remote login.
- .EDU is a valid domain type.
- Internet Explorer is a character-based browser.
- Messengers can be used to send e-mails.
- Dial-up is the fastest possible Internet connection.
- Microsoft owns Internet.
- Outlook Express can be used for reading news.
- E-mail address has no spaces in between.
Descriptive Questions
- Explain the typical structure of a URL.
- List various uses of Internet to the society.
- What is a newsgroup? How can you subscribe to it?
- Distinguish between Internet and World Wide Web.
- What is e-mail? Explain its working with the help of an example.
- Describe some of the components of Internet Explorer.
- What are search engines? How do they help users in using information on the Internet?
- Define the following:
- (a) Web page
- (b) Home page
- (c) Website
- Write short notes on the following:
- (a) Chatting
- (b) Instant messaging
- (c) Internet telephony
- (d) Video conferencing
- Suppose you want to send an e-mail to one of your friends having e-mail address niceperson@ indiatimes.com. Type a message, inviting him on your birthday (Nov 8 2004). Also attach a file named ‘Invitation Card’ describing the venue and time of party.
ANSWERS
Fill in the Blanks
- Client
- Uniform Resource Locator
- World Wide Web (WWW)
- Web browser
- Downloading
- ARPANET
- Search engine
- Browser
- Remote login
- Listserver
Multiple Choice Questions
- (c)
- (d)
- (a)
- (a)
- (d)
- (c)
- (d)
- (c)
- (b)
- (d)