VirtualBox allows you to choose different networking modes for the network adapter used in the VM. The following is the list of available options:
- Not attached: This mode implies that the guest VM has an Ethernet card but no network connection; it's like an Ethernet cable that is not connected to the network card.
- Network Address Translation (NAT): This is the default networking mode, and it requires no configuration on either the host or the guest VM. This is great if you just want to browse the web within the guest.
- Host-only: In this mode, the guest VMs can interact with each other as well as with the host, but they cannot talk to the outside world. In this mode, a virtual interface is created on the host, which provides connectivity across the guest VM and the host.
- Bridged networking: This networking mode helps you to set up routing between the guest and the rest of the network. It does so by using a virtual network interface, which filters data from the physical network adapter, so that the guest and the host can talk to each other, and also with other VMs on the network and in the outside world.
- Internal networking. This mode is similar to a bridged network mode when it comes to communicating with the other VMs on the same host, but it is more secure and does not let you communicate with an external network. This mode has two sub-modes:
- UDP tunnel: This sub-mode helps to interconnect guest VMs running on different physical hosts directly and transparently over the existing network infrastructure.
- VDE (Virtual Distributed Ethernet) networking: This mode helps to connect to a Virtual Distributed Ethernet switch on a Linux or a FreeBSD host. To enable this mode VirtualBox needs compilation because this feature does not come by default with VirtualBox.
If you want to access an external network from a guest, VM Network Address Translation (NAT) helps to do so. There is no extra configuration required, neither from the host nor the guest system, to enable this mode; this works out of the box. This is the default networking mode in VirtualBox.
A guest machine with the NAT mode enabled works similar to a physical host connected to a router. The only exception in this case is in the scenario in which the VirtualBox networking engine routes traffic from and to the guest VM transparently. In VirtualBox, this router is placed between each guest VM and the host. This separation ensures security, as the default VMs cannot talk to each other. Guest VMs placed in the NAT mode are invisible and unreachable from the outside network, which means that unless you set up a port forwarding request, you can't reach it. We will discuss detailed port forwarding in the next section.
When a guest VM OS sends network traffic, the network frames are received by VirtualBox's NAT engine. Once it receives the frames, the NAT engine extracts the TCP/IP data and resends it using the host OS. So for an application on the same host, or another in the same network, it looks like the data was sent by the VirtualBox application on the host, using an IP address belonging to the same host. VirtualBox listens for replies to the packages sent, and repacks and resends them to the guest machine on its private network. The VM receives its IP and configuration on the private network from a DHCP server built in VirtualBox. The IP address assigned to the VM by the DHCP server is usually on a completely different network than the host. More than one card of a VM can be set up to use NAT.
Let's look at the following example:
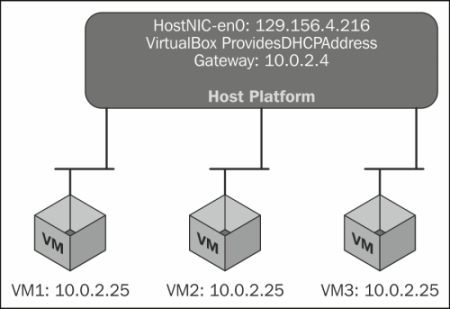
When the guest OS boots, DHCP provides the IP. VirtualBox takes care of the DHCP request and also assigns an IP address and the gateway address for routing outbound connections. In this mode, every VM is assigned the same IP address (for example, 10.0.2.25) because each VM thinks it is on its own isolated network. And when it sends the traffic via the gateway (for example, 10.0.2.2), VirtualBox rewrites the packets to make them appear as if they originated from the host rather than the guest. This ensures that the guest VM will work even if the host moves from one network to another.
As already discussed, in the NAT mode the guest VM is connected to the private network, which is internal to VirtualBox and not visible to the host. So the network services in the guest VM are not accessible to the host machine or other machines in the same network. With the help of port forwarding, the selected services can be exposed to the outside world. When you configure port forwarding, VirtualBox lists specific ports on the hosts and resends all packets, which are received by the guest OS on the same or a different port.
For an application on the same or a different host on the network, it looks as though the service being proxied is actually running on the host. This also means that you cannot run the same service on the same ports on the host. The VBoxManage command line can be used to configure a proxy; also, GUI can be leveraged to configure it as well.
To configure port forwarding, you need to know on which port the service uses for the guest and which ports to use for the host.
For example, if you want to configure port forwarding for TCP traffic received on port 1234 in the host to port 22 in the guest, you can use the following command:
VBoxManage modifyvm "VM name" --natpf1 "Testssh,tcp,1234 ,22"
To remove this forwarding rule again, use the following command:
VBoxManage modifyvm "VM name" --natpf1 delete "Testssh"
To specify the guest IP (static), use the following command:
VBoxManage modifyvm "VM name" --natpf1 "Testssh,tcp,1234,<IP Address> ,22"
To forward all incoming traffic arriving on a local interface from port 1234 to port 22 in the guest, use the following command:
VBoxManage modifyvm "VM name" --natpf1 "Testssh,tcp,127.0.0.1,1234 ,22"
Despite all the advantages, it has some limitations. For example, it does not support any other protocol (such as PPTP) other than TCP and UDP. And for Linux- and Unix-based hosts, it is not possible to bind to ports below 1024 from applications that are not run by the root. In this case, if you try to configure port forwarding, the guest VM will refuse to start.
