1
Internet of Things: A Key to Unfasten Mundane Repetitive Tasks
Hemanta Kumar Palo* and Limali Sahoo
Department of Electronics and Communication Engineering, ITER, Siksha ‘O’ Anusandhan (Deemed to be University), Bhubaneswar, India
Abstract
The emergence of the Internet of Things (IoT) finds its footprints in many vivid application domains such as Cognitive Science, Artificial Intelligence, Mobile-first, Blockchain, Biomedical Engineering, Immersive Experience, Zettabyte Era, Micro-service Architecture, Robotic Process, 3D Alteration, Automation, Quantum Computing, etc. These trending technologies are likely to rule the future world in the coming years and make it a must for the industries, and academia. It will arguably change our perception of living by connecting everybody and almost everything placed anywhere in this world. It has recently found its presence in everyday human life connecting a host of home appliances such as the refrigerators, washing machines, microwaves, water taps, clocks, homewares, and even the cooking vessels or pots. It is difficult to imagine things or appliances without the IoT we use today. However, to maintain sustainability, these devices need to be economically viable, ecofriendly, and energy-efficient. This motivates the authors to coin the concept of IoT and its application domains in the current scenario and the way ahead. Some of the major areas of IoT platforms that sensitize the digitized world have been highlighted with special emphasis on the concepts of cloud, fog, edge, and virtual computing.
Keywords: Internet of things, green computing, cloud computing, fog computing, edge computing, virtual computing, semantic IoT
1.1 Introduction
The advents of green computing and green technology make the Internet of Things (IoT) an emerging field of research in recent years. Many vivid application domains such as cognitive science, Artificial Intelligence, biomedical engineering, Micro-service Architecture, Robotic Process, etc. are the outcomes of the IoT technology [1]. Any IoT domain is associated with a set of equipment, devices, machines, home appliances, agricultural or medical instruments, smart vehicles, hardware (servers, monitors, printers, sensors, actuators, etc.), software, and communication network. It is an essential commodity today that finds its footprints in smart homes or smart cities, educational institutes, smart vehicles, agriculture, wearable technologies such as sensors, or wearable devices using remote controls for monitoring and management [2]. The thrust areas of IoT devices are to provide efficient lighting, heating, air conditioning, security, media, and communication, e.g., the provisioning of much needed care and assistance to disabled, sick, or elderly individuals [3]. Some of the major areas of IoT platforms that occupy in the current scenario are shown in Figure 1.1.
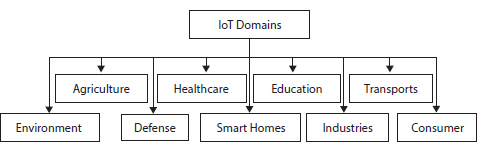
Figure 1.1 Major areas of IoT platform.
1.2 The IoT Scenario
In recent years, the IoT domain has been extended to provide enhanced tags to monitor and control the human affective states. Such attempts can be found useful in the field of criminal investigations, lie detection, an advanced warning to in-car board systems, on-line tutoring, computer games, security, banking, human resource planning, call centers, child psychology, etc. [4–9]. The associated devices and technologies can be effectively utilized in systems such as voice control, pacemakers, advanced hearing aids, Fitbit electronic wristbands, wearable sensors for the people having sight or mobility disabilities. The use of actuators or sensors to cope with an immediate seizure or a sudden fall or similar emergency can help people or patients of all ages in the home and work environment [10]. The additional security devices mounted on the body or its part will alert nearby individuals including the health attendants or medicos at the right time hence can enhance the quality of living being.
An effective IoT framework in commercial applications requires the collection, analyzing, monitoring, and management of input data concerned with healthcare, medical, transportation, building, home automation, vehicles including agriculture. Elaborate research, control, and monitoring of these inputs can lead to new information and insights for channelizing in the desired directions. A reliable system can provide the desired freedom by linking the smart systems or devices, healthcare services, physicians, and medical resources to patients [11]. Another interesting application is to set-up smart beds in healthcare units equipped with actuators and sensors that provide patient information regularly and also to confirm whether a bed is vacated or occupied. These beds fitted with automatic sensors with appropriate supporting and pressure devices can either reduce or eliminate manual assistance to unwell individuals.
The application of IoT in the transportation system requires an efficient framework to communicate, integrate, process, and control information among many sensors and devices connected to such a system and its peripheries. The role of IoT remains vital to interact and coordinate among traffic systems, logistics and packaging systems, vehicle control, parking, toll plaza, security and safety, road assistance, etc. [12]. Similarly, IoT-based smart infra-structure systems that design and develop smart homes or apartments or campuses or a smart city must be able to manage and control the electrical/electronic/mechanical sensors, actuators, devices, and equipment as per a user demand [13]. Further, such a technology finds its place in several service-based industries, infrastructure development, product or manufacturing industries, metropolitan scale development, agriculture, energy management, living laboratories, environmental monitoring, intelligence, and security, etc.
1.3 The IoT Domains
1.3.1 The IoT Policy Domain
The policy-based IoT intends to develop, plan, and implementation of suitable rules, strategies, and policies concerned with IoT devices based on real-time data for future impact and possible environment sustainability. It helps in efficient energy management, data management, resource utilization, and user feedback that benefit the industries as well as the end-user. A few areas of policy-based IoT application are shown in Figure 1.2.
The application of policy-based IoT in smart cities helps to plan for smart healthcare, smart vehicles, smart homes, smart security, smart campuses, smart agriculture, etc. [1]. Due to scare, limited and rapid depleting of resources with an increase in global population, it demands .a smart city environment for the future generation. With the advent of industrialization and the emission of poisonous gas particles, the world becomes unhealthy and suffocated. Further, many environmental hazards such as global warming, climate change, acid rain, soil erosion, etc. tend to threaten the world ecosystem. This has compelled the government agencies, NGOs, and policymakers to find different means or ways to contain the carbon footprints that grow exponentially. To be successful, the policies and strategies must appeal and be conducive to the manufacturers, designers, service providers, as well as the end-users with energy-efficient systems. Such planning, policies, regulations, etc. facilitate the smart environment where people can utilize the air conditioners, computer labs, sensors, and networking systems with desire for economical effectiveness. The IoT application in smart cities provides the provision to many factors such as
- Smart Agriculture: Smart agriculture based on the IoT aims to integrate several heterogeneous devices, objects, equipment such as the wearable sensors, humidity sensors, temperature sensors, mobile phones, etc. with the networking system to remain successful [14].
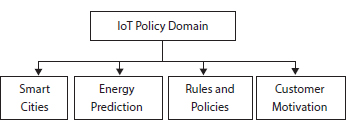
Figure 1.2 Policy-based IoT applications.
- Smart healthcare: It requires a context-aware linking system to be efficient and viable linking the agriculture, healthcare, and environment [15]. The IoT must cater to a remote health monitoring system while managing huge data by applying visualization and data mining. The linking of the IoT green computing to health industries can infuse flexibility, interoperability, and intelligence by information transmission among different modules of the healthcare system. This reduces and simplifies the administrative task.
- Smart security: The world becomes small due to the use of IoT. This makes the people, installations, equipment, etc. vulnerable to cyber-attack. The loss, theft, and exposure of private information become common today due to network interconnectivity. The IoT system must be capable to safeguard from pilferage or leakage of sensitive information by taking preventive measures. This way, it can avoid unwanted threats to national, environmental, social, and personal entities by providing smart security with efficient IoT gateways [16]. It requires the provision of password protection systems, ciphering or cryptographic or jumbling technologies, robust routing mechanism. The security clearance is a must at every level to maintain information integrity, confidentiality, authenticity.
- Smart homes: The IoT-based smart homes help the end-users to cope and deal with their busy schedules by interlinking the sensors, electronic gadgets, etc. with software set up in homes [13]. The equipment such as the computer, mobile phone, air conditioner, lighting, heating mechanism, ventilation, security systems, hardware, etc. connected through networking and sensors benefit from these ends irrespective of time and place.
- Smart vehicles: The IoT-based smart transport system equipped with smart servers can provide e-notification, traffic and weather updates, automated accident detection, etc. to drivers and vehicle owners to save up on their energy and time. It helps to restrict the vehicle speed under adverse weather condition and traffic congestion by estimating the distance traveled the driver reaction time, etc. The associated systems such as the GPRS tracking, emergency prioritization, vehicles, GSM modem, infrared proximity sensors, Xbee, embedded processor are few contributions of smart vehicle systems [12]. Similarly, smart vehicles that can handle and inform human affective states can provide a warning to a passenger or the driver for timely action by alerting the traffic management system in case of emergency [17].
- Smart campus: The resources are scarce and are rapidly depleting with an increase in the global population, hence they are limited. Further, it is not advisable to neglect the environmental effect.
- Climate change, soil erosion, global warming, acid rain, etc. in the exploration of resources on a large scale. It demands awareness among the consumers, manufacturers, designers, service providers, to develop energy-efficient IoT system for smart cities. In this regard the role of NGOs, educational institutions, think tanks, intellectuals remain vital to promoting green residences or campuses. This can be possible by providing automatic monitoring and control of IoT devices focusing on the economy, energy-efficient, reliability, etc. [18].
1.3.2 The IoT Software Domain
A few of the IoT Software domains are shown in Figure 1.3 and have been explained briefly here.
1.3.2.1 IoT in Cloud Computing (CC)
CC aims to deliver the hardware and software services across a parallel and distributed system. It has three important characteristics such as (a) virtual, (b) dynamic provision on-demand, and (c) negotiation. In this scheme, the hardware and software systems are interconnected dynamically and computerized virtually [19]. This way, the scheme reduces the carbon footprints and emissions besides decreasing the energy consumption appreciably. This can be achieved by transferring a few on-premises applications into the cloud. One of the real-life situations where CC finds its use is on-line marketing in which we procure goods and services without our presence in the shop-floor physically. Further, it reduces unnecessary expenditure on transportation and reduction in greenhouse gas emissions by each individual going to the shop-floor separately. As it is possible in CC to use the resources of the service provider rather than buying expensive equipment or systems for a business, it is economical. The reduction in the cost of using CC may be attributed to the following.
- One can include new software, hardware, and system upgrade costs in his/her contract.
- The expert data is found in the cloud, thus need to hire or pay the expert staff.
- Thus, it reduces energy consumption.
- Unnecessary time delays can be avoided.
Some of the other benefits that are offered by CC are security, flexibility, insight, quality control, increased collaboration, disaster recovery, competitive edge, loss prevention, sustainability, etc. The major advantages of CC have been shown in Figure 1.4.
The limitations of CC are briefed below.
- Privacy agreement: The user in the CC platform requires the desired privacy and service level agreement before the commencement of the services. It delegates certain responsibilities on both the service provider and the user which needs to be adhered to by both the parties.
- Security: The protection of data and the security against pilferage, theft, etc. need to be considered beforehand. While it is provided by the service provider in its periphery, the remote users need to weigh the security system before opting for CC.

Figure 1.3 Softwarebased IoT applications.

Figure 1.4 The benefits of CC.
- Vulnerability: Since each component is easily accessible via the internet, it is likely to be attacked by hackers.
- Limited flexibility and control: The uses in CC have limited control over the execution and function of the service provider as per the agreement signed by both parties.
- Platform dependencies: The vendor lock-in or implicit dependency creates deep-rooted differences between the user and the service providers. This sometimes poses difficulties for users to migrate to other service providers at will due to additional cost, security, and privacy issues.
- Cost: for small businesses or on a small scale, CC cost exceeds the cost due to staffing or hardware procurement.
Types of CC
The commonly employed CC services are briefed below.
- Infrastructure as a service (IaS): In this, an external service provider facilitates the user with computer power and disc space via the internet. The users need to have hardware such as CPU, data storage, memory, or network connectivity. Examples of IaS are the Rackspace, Amazon EC2, Windows Azure, etc.
- Software as a service (SaS): In this, the user can access the internet-hosted software by browsing. The service provider maintains and controls the software updates and the user has limited control over the configuration settings and the applications. It is mostly suitable for small businesses.
- Platform as a service (PaS): It is a crossover between SaS and Ias. In this case, the user rents the operating system, hardware, network capacity, storage, etc. to the service provider. Thus, the user has the desired control over the computing setup, technical aspects, customization, etc. as per his/her need.
1.3.2.2 IoT in Edge Computing (EC)
CC is an efficient mechanism to process the data that reduces at the network edge. New software domains have been developed that are more energy-efficient than CC are the Fog or EC [20, 21]. In EC the computation of the enabling technologies is carried out at the edge of the network. At downstream data, this function is performed using cloud services whereas, at upstream data, the IoT services are carried out.
In EC, the network resources are managed and controlled between the path of cloud data found useful in the case of a smartphone which is considered to be an edge between the body things and the cloud. Similarly, a gateway is an edge between campus things and cloud in green computing, or the cloudlet and the microdata center act as an edge between the cloud and the mobile device. While FC is oriented more towards the infrastructure side, EC is focused on the things-side. Hence, the latter remains an emerging technology at par with CC in the current scenario. The EC requires minimum use of refrigeration and maintenance as it needs a small data center for functioning. Ultimately, the technique remains energy efficient with a reduction in e-waste. The use of EC has reduced the response time to 169 ms as compared to 900 ms required by CC [22]. The hierarchy of EC is shown in Figure 1.5.
EC aims to save bandwidth and to reduce the response time by bringing the data storage and the computation closer to the desired location. It has recently been found to be applied in dealer locators, real-time data aggregators, shopping carts, and insertion engines. It is a computing technology that can deliver nearer to a request zone with low latency. As compared to CC that suits big data analysis, EC performs better in real-time processing of data generated by the users or sensors such as ‘instant data’. EC moves the computation away from data centers towards the edge of the network, thus helps smart things or objects such as network gateways or mobile phones to accomplish the desired services or tasks on behalf of the cloud. On account of this shift, it becomes reliable to facilitate service delivery, content catching, IoT management, and storage with reduced response time and efficient transmission and reception of data.
The advantages of EC are as follows and are shown in Figure 1.6.
- A reduction in data volume, as the task is performed at the edge.
- It reduces the consequent traffic and traveling distance of data.
- Low latency and transmission costs.
- It provides computing offloading in real-time applications, such as facial recognition with the low response time.
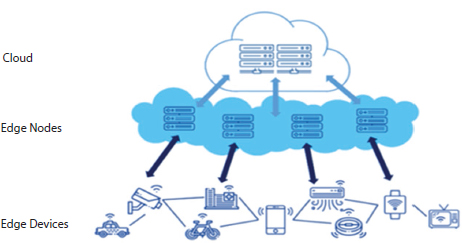
Figure 1.5 The hierarchy of EC.

Figure 1.6 The benefits of EC.
- Instead of using the resource-rich machines such as cloudlets in the vicinity of the mobile users in the case of CC, it is better to offload a few of the tasks at the edge node to reduce the execution time.
- EC optimizes data-driven and management capabilities by efficient facilitation of data gathering, processing, reporting, etc. very nearer to the end-user as possible.
Privacy and security
The distributed paradigm of EC allows data encryption using different mechanisms, hence provide added security. This is because the data can be transferred among several distributed nodes via the internet before arriving at the cloud. This introduces flexibility in security methods to be adopted, thus Edge nodes may suit resource-constrained devices. An eventual shift from centralized top-down cloud infrastructure to a suitable decentralized Edge model helps better the functioning of the network. Further, the edge data allows the shifting ownership of gathered data from service providers to end-users. On the contrary, CC is more vulnerable since all the data is fed to the cloud analyzer and a single attack can disrupt the entire system. As against it, the EC transfers fewer amounts of data that can be accessible to hackers or interceptors. So it helps industries to tackle local compliance, privacy regulations, and data sovereignty issues.
Scalability
In CC, it is essential to forward the data to a centrally located data center. Thus, the modification or expansion of the dedicated data centers remains expensive. On the other hand, the IoT devices can be deployed at the edge with their data management and processing tools in single implantation without waiting on the coordination efforts of personnel placed at multiple sites.
Reliability
In CC, if a crucial system or component fails, it is difficult to make the service alive. As compared to this, in EC using distributed nodes, if a single node fails or unreachable, it is still workable without interruption. Further, there is every possibility of redundant data in CC that may not be useful or have the same value. Hence spending money on these data is not advisable which leads to EC. It allows the categorization of data for the perspective of management. Focusing only on relevant data reduces the bandwidth requirement, hence cost. It optimizes the data flow to maximize the operating cost. It stores the data temporarily which is sent to the cloud for storage at a later stage that causes redundant overload in clouds.
Speed
EC facilitates the availability of analytical computational resources in the vicinity of the end-users, hence can improve the speed of response. The presence of a small amount of data and its management to remote locations reduces the overall loads in the traffic. The reduction in latency can enhance the speed of communication at the user-end.
Efficiency
In EC the end-user remains at the proximity of the computing which allows the application of sophisticated Artificial Intelligence and analytical tools at the edge of a system. Such schemes improve the overall operational efficiency of the system.
Cost Saving
EC has to deal with less data that is relevant to the end-user. Removal of redundant data reduces the cost of data handling, transportation, storage, and management. Further, the bandwidth cost is also reduced as it needs to deal with large data management.
Versatility
EC remains versatile since industries can target the coveted markets with their local cen-ters with fewer infrastructure investments. In this way, the enterprises may allow expert assistance with latency. The efficiency of EC can further increase with the involvement of advanced IoT gadgets without changing the current IT structure.
The Limitations of EC
Table 1.1 shows the limitations of EC.
Table 1.1 The limitations of EC.
| Security | It is often difficult to maintain the desired security in a distributed network such as EC. The security further at risk due to the transfer of data outside the network edge. Further, the infiltration or pilferage of data when a new IoT device is introduced. |
| Incomplete Data | EC can analyze and process limited information and discard the rest of the data. Thus, there is a possibility of valuable information loss which compels the end-user to decide the type and amount of information before opting for such a scheme. |
| Investment Cost | The implementation of an EC infrastructure remains complex and costly and complex since it requires additional resources and equipment. It requires more local hardware for functioning. |
| Maintenance | The EC uses a distributed framework which is decentralized, thus, there are several combinations and variation in network architectures or modes. Hence the maintenance cost increases as compared to that of a centralized network such as CC. |
1.3.2.3 IoT in Fog Computing (FC)
FC reduces the amount of information to be carried into the cloud and improves efficiency by extending the cloud nearer to the data generating device known as the fog nodes. These fog nodes are in the form of controllers, switches, servers, routers, cameras, etc. which provide the desired storage, network connection, and computing features is known as fog node. In general, CC is incapable of handling large data bandwidth as it is subjected to volume and latency that’s leads to the advent of FC. It is found useful in compliance and data security and is a non-trivial extension of CC. It bridges several sensors appearing at the network edge to the core computing structure of the cloud [1, 23]. The system requires the processing to be carried out either on the network edge of a gateway device or router or in the data hub of the mobile device.
Although, the FC is similar to EC appear similar the key difference lies in the location or the placement of computing power and intelligence. The FC places the intelligence at the local area network to transfer the data from end-users to a gateway for further transmission. On the contrary, EC intends to place the processing power and intelligence in devices such as embedded automation controllers. The concept of cloud, Edge, and FC is shown in Figure 1.7.
Similarly, EC appears directly on the devices where the sensors or controllers are attached or it may appear at the gateway device physically nearer to the sensors. On the other hand, FC carries the edge activities to several processors connected to the LAN physically away from the sensors, controllers, and actuators.
Advantages of FC
- Since in EC the storage and processing of data to take place in LAN, the technique allows the organizations for the aggregation of information from multi-devices to regional stores.
- The data processing capability of Fog architecture is larger than that of Edge as the former allows organizations to gather data from different various devices.
- It improves and helps the real-time processing capabilities of the Edge architecture.
- It is most suitable for structures that have to handle millions of devices sharing information between them.

Figure 1.7 The concept of cloud, edge, and FC.
- It can provide a better quality of services, low latency, security, privacy protection, location awareness, reliability, etc. Hence, it can be efficiently employed in real-time applications than CC.
Disadvantages of FC
- A major drawback of FC is the huge data dimensions it needs to handle with millions of devices.
- It requires a large investment and consequently a large infrastructure to accommodate such volume of data and devices for reliability.
For large sensor data, it is difficult to use the cloud for transmission. Hence, it is essential to move to Fog architecture. Further, the data transmission between the sensors and the cloud or vice versa requires a large bandwidth that makes the CC inefficient. Thus, in the future, it is advisable to replace the CC with FC in the application such as a smart grid, low energy consumption, smart transportation system, smart traffic, management systems, agriculture, and health care system.
1.3.2.4 IoT in Telecommuting
In IoT software domain initiatives, it is possible to implement teleconference or telepresence applications efficiently. It can provide job satisfaction and protect the living being from the effect of greenhouse gas by limiting their traveling. Ultimately, the profit margin of an organization improves as telecommuting reduces the office overhead costs by minimizing office space, lighting, heating, etc. Evidence shows an average annual energy savings of 23 KWh per square foot amounting to 70% of total energy consumed due to air conditioning, heat, and lighting in a U.S. office building [24]. Similar expenditures can be curbed by integrating telecommuting with consulting, hoteling, field service, and sales. The framework of integrating telecommuting to IoT application domain must take care of the following few issues.
- The energy consumption
- Identification of the key energy indices for efficient utilization of different network elements
- Device and network optimization for carrier telecommunication
- Effective management of the link between the environment and the network technology.
- We need to segregate individuals or groups who can work remotely with efficiency and benefit the organization as a whole.
- We need to define the responsibilities, accountability, and expectation standard clearly.
- Describe clear rules and regulations for employees selected for telecommuting.
- Due weightage needs to be given to the career goal of the telecommuting employees.
- Move to cloud as an when required for assistance
1.3.2.5 IoT in Data-Center
Data Centers are the biggest consumer of energy and hence required to be energy efficient. These data centers require a context-aware sensing mechanism to implement selective sensing for minimizing power consumption. An effective energy management architecture can supply power uninterrupted to the dedicated sensor and switches off the idle controllers/sensors/actuators as and when required [25]. Effective data center functioning needs to tackle the following issues.
- A meticulous distribution and evaluation of workload to the dedicated servers.
- Identification and cutting-off of power supply to the ideal servers and redistribution of the workforce and load.
- Maximizing the application of renewable energy sources.
- Efficient and economical use of power and depleted resources.
1.3.2.6 Virtualization-Based IoT (VBIoT)
The VBIoT application aims to reduce the number of hardware resources, hence it consumes less energy. It is a virtual or software-based process to represent things, such as networks, virtual applications, servers, storage, etc. It can reduce IT expenses, boosts flexibility, efficiency, scalability, and agility for many businesses. A saving of 36% energy consumption in IoT devices has been reported by using the Mixed Integer Linear Programming (MILP) in the VBIoT with four-layer architecture [25]. The benefits of VBIoT are:
- It allows managing of data or information with ease and efficiency.
- The continuity and growth in industries can be achieved.
- It is possible to access a true software-oriented data center.
- The resources and applications are made available as and when desired.
- Helps to increase responsiveness, production, efficiency, and agility.
- There is a considerable decline in operating costs and investment in capital.
- The downtime can be minimized or ideally eliminated.
- It optimizes resource allocation by providing better workload distribution, performance enhancement, and automated operations.
VBIoT emphasizes on encapsulation, isolation, partitioning, and hardware independence, thus makes the domain effective. It can be included in many levels of IoT framework such as a server, desktop, network, etc. towards creating a smart world environment.
1.4 Green Computing (GC) in IoT Framework
The benefits and limitations of the GC have been shown in Figure 1.8.
The IoT application to Green Computing (IoTGC) aims to achieve a greener and eco friendly world. The objective is to design, develop, operate, maintain, and control the energy-efficient IoT systems that are economically viable, user friendly, and eco-sustainable.

Figure 1.8 The benefits and limitations of the IoTGC.
Nevertheless, the challenges are many due to a change in global climate, depleted resources, energy crises, environmental issues, etc. [1]. Further, the hardware system must be easily disposable/recyclable and must comprise of handheld and large-scale data centers.
1.5 Semantic IoT (SIoT)
The reflection of heterogeneity on these raw data for meaningful interpretation and detection of events in real-world environments makes the IoT platform more complex. The total number of IoT domains included in 2016 is approximately 450 with an exponential rise in new IoT platforms each year [26]. By the year 2020, the number of IoT devices may reach around 50 billion with numerous heterogeneous services and applications [2]. In this accord, the SIoT concerns to a worldwide network of interconnected devices, things, heterogeneous objects, and services which can be uniquely addressable and accessible using some sort of standard communication protocols.
The steps involved in managing heterogeneous data sources for making SIoT effective are based on SEG 3.0 methodology as shown in Figure 1.9. It supports the SI from the data generation to the end-users.
Due to the involvement of a huge number of things and the services in the future IoT, it remains a challenge to represent, interconnect, store, search, address, and organize relevant information available from different IoT sources. Thus, the involvement of semantics in IoT remains crucial to provide adequate modeling, reach desired solutions for things description, and reason over IoT generated data. With an increase in demand for applications and services using semantic sensor web, the research community, and software developers are designing advanced system architecture to automatically transform data from sensors to semantic expression. The use of data somatization facilitated the end-users to understand and reason on sensor-related human’s activities for effective dynamic environments. The use of SI remains vital for adequate representation and integration of huge amounts of data arrived from different IoT sources for their effective utilization. The information extracted semantically from high-level abstractions or data can provide a potential solution to reduce the heterogeneity in a shared or common IoT platform. The Semantic Interoperability (SI) assisted by the SW to facilitate consolidated technologies, standards, and languages by providing data as well as IoT platform interoperability. With an ever increasing demand in applications and their developments, the use of semantic interoperability in IOT domain remains significant and essential for its success. With many different smart technologies, the SI integration costs are likely to rise and the system becomes complex. Nevertheless, with thousands of potential data sources, application areas, industries, and customers, a smart city can be smarter with the combination, cross-compilation, and re-utilization of data generated by individual applications using SI. The intersection of different IoT visions is shown in Figure 1.10.

Figure 1.9 The steps of SIoT (SEG 3.0 methodology) [27].
A generalized SIoT architecture is shown in Figure 1.11.
It is not enough to gather data but requires an ability to convert or process the available data into fruitful decisions or information that can provide an edge in SI. For instance, if someone was to call an end-user on their phone and speak in London, most users would probably not be able to communicate or achieve a meaningful result. The same issue occurs in communication between things when they use implementation-specific data models.

Figure 1.10 Intersection of different IoT visions [2].
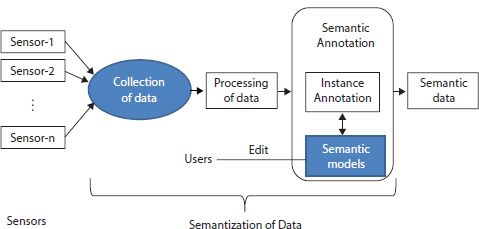
Figure 1.11 A generalized architecture of including semantics.
1.5.1 Standardization Using oneM2M
Many companies are still trying to gain a better understanding of how blending robotics, interconnected devices/systems, and convergent hybrid infrastructure, together with edge and cloud/data center compute, can improve productivity and reduce costs in the long run. Add different vendors’ technology to the mix and a very complicated picture is painted.
Working to reduce this complexity is oneM2M, a global standard that hides technology complexities for IoT application developers through an abstraction layer, and a wide area network perspective. Its areas of expertise extend to the industrial sector, with several completed Technical Reports (TRs) and work in progress dedicated to this area. TR-0018 Industrial Domain Enablement, for example, maps out several use cases relating to Industry 4.0 development and the potential requirements which need to be addressed to ensure M2M communications truly enhance operations. Based on industrial domain research carried out, the document highlights the need to develop an accepted strategy to implement Industry 4.0 as a means of accelerating the update of manufacturing systems that many global organizations have started to invest in. Other completed projects dedicated to tackling the challenges of Industry 4.0 include TR-0027 Data Distribution Services usage in oneM2M and TR-0043 Modbus Interworking. Meanwhile, work is continuing on TR-0049 Industrial Domain Information Mapping & Semantics Support around proximal– distal interworking. Further support for industrial IoT applications is also expected to come when oneM2M publishes Release 3 later this year. OneM2M also collaborates on a wider scale with other industry bodies on a wide range of projects. In its TR-0018 Industrial Domain Enablement report, oneM2M referenced several organizations and industry bodies with relevant activities in the area, including the Industrial Internet Consortium (IIC) and Platform Industrie 4.0 and their respective reference architectures including IIRS and RAMI 4.0. Cooperation with the IIC is already advancing through joint workshops and a oneM2M testbed. Cooperation with Platform Industrie 4.0, the central alliance for the coordination of the digital structural transition in Germany, which includes stakeholders from businesses, associations, trade unions, and academia, is another important alignment of technologies and concepts in the industrial domain, especially as the PI4.0 concept of an Asset Administration shell and the oneM2M CSE are so complementary. OneM2M has incorporated results from Plattform Industrie 4.0’s Reference Architecture Model, Industrie 4.0 (RAMI 4.0), into the TR-0018 Industrial Domain Enablement report. RAMI 4.0 provides a conceptual superstructure for organizational aspects of Industry 4.0, emphasizing collaboration infrastructures, and communication structures. It also introduces the concept of an asset administration shell that incorporates detailed questions on key topics such as semantic standards, technical integration, and security challenges. OneM2M’s joint work with key transformative actors develops and delivers workshops, testbeds, and reports, along with its unique asset. The concept of a service layer on top of a connectivity layer—contributes significantly to the overall Industry 4.0 framework and industrial internet as a whole, ushering in a new wave of digitalization which will mark the beginning of Industry 4.0.
SI has been introduced in the latest specification of oneM2M standard Release 2 [Swetina]. It allows the posting, distribution, and reuse of meta-tagged data through a gateway by providing timely notifications to interested clients or entities available in semantic discovery.
OneM2M acts as a software middle layer, by interconnecting devices with their respective application–infrastructure entities (cloud-based), independently from their underlying transport networks. In effect, it creates an abstraction layer that allows application developers to create value from their business and operational applications without having to deal with the technical protocols for connecting to and managing devices. The standard solves the problem of implementation variances for common service functions. Its technical specifications provide a global standard for the basic functions, such as device management, security, registration, and so forth. The use of oneM2M specifications in field-deployed devices ensures data and vendor interoperability. Furthermore, oneM2M provides global standardized APIs on the application-infrastructure side, where customers can interact with their device and/or even their platform. On the device side, oneM2M’s APIs help developers tailor applications for their specific purpose without the need to master technical details about the underlying connectivity networks. To enable end-to-end communication across different verticals, oneM2M provides the tools that enable various interworking possibilities. One approach is to map data models for shop-floor machines and sensors as oneM2M resource structures and vice versa. Since such inter-working definitions are available for other verticals, such as automotive and rail, different verticals can communicate with each other relatively easily. The primary aim of oneM2M is to standardize the common services necessary to deploy and operationally support IoT applications across multiple verticals. This implies a horizontal focus, aiming for a high degree of reuse and cross-silo interoperability. Vertical sector requirements are also important to oneM2M standardization participants. In the manufacturing and industrial sectors, oneM2M established a liaison with the Industrial Internet Consortium. OneM2M is also actively involved with the Open Connectivity Foundation, targeting interworking opportunities for consumer IoT applications. OneM2M’s standardization continues to address new frontiers for interoperability and interworking with the development of its latest specifications, Release 4. Release 4 will encompass industrial, vehicular, and fog/edge architectures. It also lays the groundwork for semantic interoperability and tools to help user adoption.
We all know that SIoT is taking place in modern applications for industries and is developing very fast making analytics crucial to ensure security. Since the SIoT analytics operates using the cloud and electronic instrumentation, it requires programmers to control and access IoT data. IT professionals approaching IoT analytics should capture data via packets in automated workloads, also known as flow. Flow is the sharing of packets with the for example, if you stream a video on the internet, packets are sent from the server to your device. This is flow in action. NetFlow and sFlow are both tools that monitor network traffic. IT pros are still creating methods to capture the flow of data for analysis of IoT data. The number of cloud companies has increased, and as networks continue to grow, it’s very risky to carry down the large visibility gap for capturing data. Because of huge data traffic, many cloud companies have started to send information through their networks via IP Flow, sFlow, and NetFlow. When you start to capture IoT specific data, there are several advantages. The data gets standardized into industry-accepted data, and once the data is observed from the gateway, it can be correlated with traffic data coming out from the data center or cloud services in use. Every cloud environment can create flow by generating and exporting the data. For example, a few IT equipped companies such as Amazon, Google, Microsoft Azure have incorporated these attributes in different applications to facilitate the industries and consumers. Amazon is a popular platform for cloud services which takes into account both the cost and frequency response of the network. It has many features to enhance the IoT platform and can support many devices. This platform uses flow as the mechanism to communicate. The service is handled by the virtual private cloud. It comes across under certain levels such as ports, networks, traffic levels, and some other communication networks. Data gets stored using the CloudWatch logs in JavaScript Object Notation (JSON). Similarly, Google is popular in every technology. Google Cloud IoT Core is a fully managed service that allows you to handle easily and secure the connection with manages and ingests data from millions of globally dispersed devices. The data flow is run by logging the Stack driver. And the performance of the network operates with good latency. It handles large data which works still fine. Similarly, the ‘Microsoft Azure’ flows under a secured network system. The flow logs are work or travel in a flow and stored into Azure storage in the format of JSON. The data from the devices have been stored in a method of real-time data.
For example, the use of some sort of standards to announce each printer and its attributes is one way to elevate such an issue and there are so many such attributes.
Today, each vertical industry comes along with its protocol and specifications bodies to develop their data models. For example, in the industrial automation industry, organizations like OPC are working on data models and objects which can be used on the shop floor. In the automotive industry, ETSI’s Intelligent Transport Systems technical committee is working collaboratively to define messages and data models for communication between cars. Many IoT applications also involve several partners in a distributed value chain. For instance, an intelligent application for an industrial plant might automatically order feedstock from one or more partners for its production line. Supplies are typically ordered and delivered by several partners. It is easy to see how this scenario can end up in up in an “island of things” configuration since different partners in the value chain belong to different verticals, each with their specific data models. It is thus desired to make sure the cross-availability of IoT devices, services, and data for the growth of new business and the emergence of opportunities. This can assist managing data from multiple sources, generate new avenues, and innovate suitable solutions for the existing service providers to scale new markets.
1.5.2 Semantic Interoperability (SI)
The last decade witnessed a many-fold increase in a host of heterogeneous devices, actuators, sensors, etc. with varied applications in the IoT platform. To cope up with the smart environment, an efficient distribution, monitor, support, coordination, control, and communication among these sensors remains essential that gives rise to the term interoperability. The interoperability can be achieved with the following major layers as shown in Figure 1.12.
Technical interoperability is concerned with the communicability among the things or objects in IoT domain using the software and hardware. On achieving the suitable connectivity, the syntactic interoperability deals with the data models, data formats, data encoding, communication protocols, and serialization techniques using certain specified standards. Finally, Semantic interoperability establishes the desired meaning to the content and assists to comprehend of the shared unambiguous meaning of data. The interoperability concept can be better visualized using the five major perspectives and is given in Table 1.2.
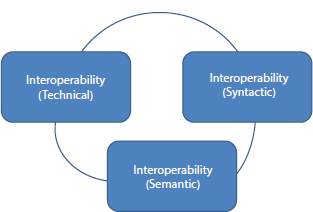
Figure 1.12 Different layers of interoperability.
Table 1.2 Taxonomy of interoperability: major perspectives.
| Taxonomy of interoperability | Attributes |
| Device interoperability [19] | Involves both the low and high-end devices High-end devices are Raspberry Pi, smartphones, etc. with good computational abilities and resources Low-end devices are low-cost sensors, actuators, RFID tags, Arduino, OpenMote, etc. with resource-crunch, communication, low energy, and processing abilities. It aims for better integration and communication among several heterogeneous devices in advanced IoT platforms. |
| Network interoperability [20] | The network remains is multi-service, multi-vendor, largely distributed and, heterogeneous. It facilitates the better transfer of data among several smart systems using efficient networking systems. It can alleviate issues such as addressing, resource optimization, routing, security, QoS, mobility support, etc. |
| Syntactical interoperability [21] | It allows interoperation of the format and structure of the data during communication among heterogeneous IoT devices, entities, domains, systems, etc. It includes the syntactic set rules in the same or some different grammar It is significant in the case of disparities between the encode and decode rules involving the source and the end-user. |
| Semantic interoperability [22] | It allows the meaningful exchange of knowledge and information among agents, services, and applications. It is significant when the automatic interoperation of IoT information or data models is not materialized due to the difficulties in descriptions and understandings of operational resources or procedures. |
| Platform interoperability [21] | The need arises with the advancement of diverse and versatile operating systems, programming languages, data structures, IoT architectures, access mechanisms, etc. Different mechanisms are developed for efficient data management involving several IoT platforms. Similarly, cross-platform and cross-domain in different heterogeneous domains are addressed. |
1.5.3 Semantic Interoperability (SI) Security
The semantic IoT is considered as a black hole in a nebulous term. It must have a security policy that is comprehensive with expansive visibility. Further, several decades-old IoT technologies require be managing or segmenting effectively along with emerging technologies. For example, the oldest IoT iteration concept is to involve multi-function printers with both copying and scanning abilities. Nevertheless, the security concerned often ignores these which pose a threat to the domain as anybody can easily route or access these from a workplace or other places. The proliferation of security corresponding to smart systems can lead to potential threats to put infrastructure, or an entire city and its traffic, lighting, and power grid systems having millions of IoT users. However, as these smart systems work in the cloud, the organization can develop several usage patterns. The integration and coordination of smart IoT devices such as wired or unwired equipment, cameras, biometric access, gesture or face identification models, keypad, etc. with interoperability, it becomes possible to place the right people at a right place. For example, the huge meshing network structure present in a smart city environment warrants a robust security traffic system, secured wired or wireless sensors, parking meters, to prevent the proliferation of the IoT system. The security system must contain visibility to maintain awareness among both users and hackers. It is thus essential to make policies about IoT security regarding the locations of cameras, conceivable devices, sensors, measuring instruments, or meters to make it effective.
1.5.4 Semantic IoT vs Machine Learning
The Machine Learners (MLs) are essential components in the field of pattern recognition, classification, and regression analysis. Over the years, several MLs have been efficiently applied in the field of power management, speech, and speaker identification, emotion recognition, etc. [28–32]. The integration and coordination of SIoT with MLs has been often discussed in the literature involving pervasive and ubiquitous computing, ambient intelligence, wireless sensor networks, artificial intelligence, human–computer interaction, cognitive science, etc. The multi-layered back-propagating Neural Networks have been effectively utilized to identify human movements such as sitting, walking, running, etc. in smart home applications. Similarly, identification ML models such as the Naive Base Classifiers, Bayesian networks, Support Vector Machines, K-Nearest Neighbor, Hidden Markov Model, etc. have been efficiently applied in the field of context-aware search systems, home automation, navigation systems, etc. in IoT domains.
The Integration and coordination of SIoT and MLs arguably increase the financial health of an industry or business. It requires the choice of specific words or vocabularies to suitably represent a set of concepts. The choice aims to bridge the semantic gap that exists among machines in IoT platform. However, many industries in the existing structure act superficially, thus unable to transform the company into a true profit-oriented entity in reality. For example, the inclusion of Artificial Intelligence in a fast-food chain allows the planning of the diet charts based on the recommendation of user habits. It helps to suggest add-on items based on the current selection, the restaurant traffic, or environmental conditions, weather, or time of a day. The integration of artificial intelligence, SIoT, machine learning, modern analytic models, etc. requires to be embedded with the lifecycle of a customer frequently and completely. For example, the satisfaction level of a customer can be enhanced by displaying his or her name, preferences, frequent visits, etc. on the menu chart makes the client feel proud and special. Efficient handling of a customer’s behaviors, interests, and future intentions can provide many intelligent inputs to the food industry in real-time. Similarly, the AI-powered chat-bouts help the customers with the user-friendly experience to boost revenue due to personalization. It has been observed that most of the consumers are motivated to choose a product of a company that recognizes, remembers, and values his or her association with the product. This way, it is possible to predict a customer’s next move, by upgrading and feeding SI data consistently in an IoT platform. This feedback provides the simulating engines or MLs an edge for new developments in this field with better outcomes. Ultimately, the revenue increases, productivity improves, operational expenses reduced, personalization enhanced at a large scale that leads to better customer experiences. The SI automated IoT embedded machines with intelligence assists millions of smart models functioning concurrently that benefits both the customers and service providers.
1.6 Conclusions
Internet of Things (IoT) application in smart homes or cities, workplace, agriculture, transportation, healthcare, artificial intelligence, Cognitive Science, Blockchain, Micro-service Architecture, Robotic Process, Automation, Quantum Computing are all concepts gaining attention in recent years in public, private, and corporate worlds due to media publicity and efficacy. With its growing interest on everybody and everyday applications, it helps people enjoy self-driving cars, use wearables for efficiency and timely assistance, plan taxi services or business meetings, and so on. The IoT application domains have covered all sectors, industries, and every sphere of life today, thus thrive to boost the financial health of the world. It has begun to shape the future world with a unique perspective never seen before in the history of humanity. With these intuitions, this paper elaborates several factors concerned to IoT world that rule and dominate the world today in the current scenario.
References
1. Das, S.K. and Palo, H.K., Internet of Things (IoT) Application in Green Computing: An Overview, in: Advances in Greener Energy Technologies, pp. 85–102, Springer, Singapore, 2020.
2. Evans, D., The internet of things: How the next evolution of the internet is changing everything, vol. 1, pp. 1–11, CISCO white paper, USA, 2011.
3. Philip, V., Suman, V.K., Menon, V.G., Dhanya, K.A., A review on latest internet of things based healthcare applications. Int. J. Inf. Secur., 15, 1, 248, 2017.
4. Palo, H.K. and Mohanty, M.N., Wavelet-based feature combination for recognition of emotions. Ain Shams Eng. J., 9, 1799–1806, 2018.
5. Palo, H.K. and Behera, D., Analysis of Speaker’s Age Using Clustering Approaches with Emotionally Dependent Speech Features, in: Critical Approaches to Information Retrieval Research, pp. 172–197, IGI Global, USA, 2020.
6. Palo, H.K. and Sagar, S., Characterization and Classification of Speech Emotion with Spectrograms, in: 2018 IEEE 8th International Advance Computing Conference (IACC), IEEE, pp. 309–313, 2018.
7. Palo, H.K., Mohanty, J., Mohanty, M.N., Suresh, L.P., Comparison of similarity among sub-categories of angry speech emotion, in: 2016 International Conference on Emerging Technological Trends (ICETT), IEEE, pp. 1–6, 2016.
8. Palo, H.K., Spectral prosodic and hybrid features for emotion recognition, PhD thesis, Siksha ‘O’ Anusandhan (Deemed to be University), Bhubaneswar, Odisha, India, 2018.
9. Palo, H.K., Pattanaik, N., Sahu, B.N., Real-Time Detection of Human Speech Emotion Using ATMEGA. Int. J. Adv. Sci. Technol., 29, 12s, 1995–1301, 2020.
10. Chui, M., Löffler, M., Roberts, R., The internet of things. McKinsey Q., 2, 1–9, 2010.
11. He, W., Yan, G., Da Xu, L., Developing vehicular data cloud services in the IoT environment. IEEE Trans. Industr. Inform., 10, 2, 1587–1595, 2014.
12. Keerti Kumar, M., Shubham, M., Banakar, R.M., Evolution of IoT in smart vehicles: An overview, in: IEEE International Conference on Green Computing and Internet of Things (ICGCIoT), pp. 804–809, 2015.
13. Galinina, O., Mikhaylov, K., Andreev, S., Turlikov, A., Koucheryavy, Y., Smart home gateway system over Bluetooth low energy with wireless energy transfer capability. EURASIP J. Wirel. Comm., 178, 1–18, 2015.
14. Nandyala., C.S. and Kim., H.K., Green IoT agriculture and healthcare application (GAHA). Int. J. Smart Home, 10, 4, 289–300, 2016.
15. Wang, K., Wang, Y., Sun, Y., Guo, S., Wu, J., Green industrial internet of things architecture: An energy-efficient perspective. IEEE Commun. Mag., 54, 12, 48–54, 2016.
16. Gou, Q., Yan, L., Liu, Y., Li, Y., Construction and Strategies in IoT Security System, in: IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, pp. 1129–1132, 2013.
17. Palo, H.K. and Sarangi, L., Overview of Machine Learners in Classifying of Speech Signals, in: Handbook of Research on Emerging Trends and Applications of Machine Learning, pp. 461–489, IGI Global, USA, 2020.
18. Wang, H.I., Constructing the green campus within the internet of things architecture. Int. J. Distrib. Sens. N., 10, 3, 1–8, 2014.
19. Curry, E., Guyon, B., Sheridan, C., Donnellan, B., Developing a sustainable IT capability: Lessons from Intel’s Journey. MIS Q. Exec., 11, 2, 61–74, 2012.
20. Shi, W., Cao, J., Zhang, Q., Li, Y., Xu, L., EC: Vision and Challenges. IEEE Internet Things J., 3, 5, 637–646, 2016.
21. Sun, X. and Ansari, N., Edge IoT: Mobile EC for the Internet of Things. IEEE Commun. Mag., 54, 12, 22–29, 2016.
22. EPA Office Building Energy Use Profile (PDF), National Action Plan for Energy Efficiency Sector Collaborative on Energy Efficiency Office Building Energy Use Profile, http://www.epa.gov/cleanenergy/documents/sector-meeting/4bi_officebuilding.pdf, pp. 1-4, August 15, 2007, archived from the original (PDF) on 6 Mar 2009.
23. Stojmenovic, I. and Wen, S., The FC paradigm: Scenarios and security issues, in: 2014 IEEE Federated Conference on Computer Science and Information Systems, pp. 1–8, 2014.
24. Visalakshi, P., Paul, S., Mandal, M., Green Computing, International Journal of Modern Engineering Research (IJMER), in: Proceedings of the National Conference on Architecture, Software systems and Green computing (NCASG), Paiyanoor (India), pp. 63–69, 2013.
25. Arshad, R., Zahoor, S., Shah, M.A., Wahid, A., Yu, H., Green IoT: An investigation on energy saving practices for 2020 and beyond. IEEE Access, 5, 667–681, 2017.
26. Ganzha, M., Paprzycki, M., Pawłowski, W., Szmeja, P., Wasielewska, K., Alignment-based semantic translation of geospatial data, in: 3rd IEEE International Conference on Advances in Computing, Communication & Automation (ICACCA)(Fall), pp. 1–8, 2017.
27. Gyrard, A. and Serrano, M., Connected smart cities: Interoperability with seg 3.0 for the internet of things, in: 30th IEEE International Conference on Advanced Information Networking and Applications Workshops (WAINA), pp. 796–802, 2016.
28. Palo, H.K. and Mohanty, M.N., Analysis of Speech Emotions Using Dynamics of Prosodic Parameters, in: Cognitive Informatics and Soft Computing, pp. 333–340, Springer, Singapore, 2020.
29. Palo, H.K., Behera, D., Rout, B.C., Comparison of Classifiers for Speech Emotion Recognition (SER) with Discriminative Spectral Features, in: Advances in Intelligent Computing and Communication, pp. 78–85, Springer, Singapore, 2020.
30. Palo, H.K., Chandra, M., Mohanty, M.N., Recognition of Human Speech Emotion Using Variants of Mel-Frequency Cepstral Coefficients, in: Advances in Systems, Control and Automation, Lecture Notes in Electrical Engineering, vol. 442, pp. 491–498, Springer Nature Singapore, 2018.
31. Palo, H.K., Kumar, P., Mohanty, M.N., Emotional Speech Recognition using Optimized Features. Int. J. Res. Electr. Comput. Eng., 5, 4, 4–9, 2017.
32. Mohanty, M.N. and Palo, H.K., Child emotion recognition using probabilistic neural network with effective features. Measurement, Elsevier, 152, 107369, 2020.
- *Corresponding author: [email protected]
