2
An Intelligent Control Plane for Security Services Deployment in SDN-based Networks
Maïssa MBAYE1, Omessaad HAMDI2 and Francine KRIEF3
1 Gaston Berger University, Saint-Louis, Senegal
2 IMT Atlantique, Rennes, France
3 ENSEIRB-MATMECA, Bordeaux, France
2.1. Introduction
The software-defined networking (SDN) approach involves the management of a network infrastructure by software applications (Fortes 2013; ONF 2015). These applications may be hosted by one or several servers and enable the control of the (physical or virtual) network components of the infrastructure. This new model of network architecture, relying on the separation between the control plane and the data plane, is increasingly drawing the attention of major players in networking and telecommunications (Open Networking Foundation [ONF], IETF, ITU-T, ETSI) (Kreutz et al. 2015).
The data plane corresponds to network equipment in charge of optimized (at best) data transfer to the destination node. In this plane, the main task involves using a forwarding/flow table for correct data retransmission. In the case of SDN/ OpenFlow-based networks, this table contains the flow transfer rules that match the fields values of common headers (Ethernet, IPv4/v6, MPLS, TCP/UDP, etc.) and deduces from them the action to be taken (retransmit, delete, modify header, etc.). From 2015 onward, the main manufacturers (IBM, Hewlett-Packard, Huawei, Juniper, NEC, etc.) launched SDN/OpenFlow compatible network equipment on the market (Kreutz et al. 2015).
The control plane represents the entire logic enabling the management of the forwarding table content. It has an overall view of the network and includes the protocols enabling the data plane programming depending on the needs of the applications deployed in the network (routing, access control, quality of service [QoS], load balancing, traffic engineering, security, etc.). This control plane is implemented by a software platform that is (logically) centralized in a cloud and is known as controller. This plane offers innovative functionalities, such as network virtualization.
The main benefits of SDN-based networks and network virtualization are that the new generation networks are more flexible, agile and adaptable and highly automated. Indeed, the transition from IPv4 to IPv6 shows that because equipment manufacturers are responsible for the deployment of new protocols and network applications in their products, the time required to launch a product on the market is longer. With this new approach, it is possible for each structure to have new network applications and protocols programmed on the equipment eliminating the need to wait for a newer version of the equipment. Nevertheless, this possibility raises a certain number of challenges for security and scalability.
Security challenges mainly take two forms: SDN-based network security and deployment of security services. SDN-based network security efforts are essentially focused on securing the controller, which is a centralized decision point. Indeed, if the controller is compromised, out of service or disconnected from the data plane, network behavior consistency is no longer guaranteed. The controller may be the target of different kinds of attacks, such as distributed denial of service (DDoS) attacks, unauthorized access and injection in security policies (Shu et al. 2016). The solutions proposed cover a wider range, from firewalls (Wang et al. 2013) to intrusion detection/prevention systems (IDS/IPS) (Gowtham et al. 2018), in order to counteract the threats targeting SDN-based network security.
In SDN-based networks, the deployment of security applications (for example, IDS/IPS) aims to offer security as an SDN-based network service to the customers. The two major challenges of security services deployment are as follows: the dynamic character of SDN-based network control and the large amount of data to be processed by these solutions. This involves the deployment of security services that will offer acceptable response and processing times.
In classical networks, machine learning (ML) and artificial intelligence (AI) have generally proved their effectiveness for security (Das and Nene 2017). Nowadays, AI is increasingly used for solving any type of problem, partly due to the amount of data generated through the Internet. SDN-based network security is also in line with this trend, and several works already approach the SDN-based network security problem, providing solutions that rely on AI tools (Abubakar and Pranggono 2018; Dey et al. 2018; Xie et al. 2019). The ultimate objective would be to have intelligent SDN-based networks with self-protection and self-optimization capabilities.
This chapter aims to approach AI-based intelligent control techniques that enable an intelligent management of security deployment.
As a first step, section 2.2 offers a presentation of SDN-based networks, followed by an approach to the security problem and the description of an architecture for the deployment of security services for SDN-based networks in section 2.3. Section 2.4 presents the various initiatives aimed at making SDN-based networks “intelligent”. Section 2.5 focuses on the contribution of AI to network security, while section 2.6 deals with security in SDN-based networks. We describe our proposal for the deployment of an intelligent service for intrusion prevention in section 2.7. Section 2.8 deals with the main challenges to be addressed in view of the wide use of AI tools for SDN-based network security. Finally, section 2.9 concludes this chapter.
2.2. Software-defined networking
The SDN-based network concept marks a significant development of traditional network architectures. This section presents the main concepts and architectural elements.
2.2.1. General architecture
SDN architecture is mainly composed of three planes (Figure 2.1): the application plane, data plane, and control plane. Separation between the control plane and the data plane is at the core of this architecture (ONF 2015).
The application plane contains both the SDN applications and the network applications. The SDN controller uses an application programming interface (API), known as northbound API, which interacts with the application plane. This plane contains applications enabling the implementation of purely network functionalities, such as QoS and routing. Other SDN applications whose role is to control the SDN-based network logic can also be found here (Bannour et al. 2018).
The data plane is composed of physical or virtual equipment for interconnection with a main task of data forwarding. In fact, in traditional networks, the network equipment contains the control plane and the data plane. With this new approach, the control plane is externalized in order to enhance network equipment’s efficiency. These network elements (mainly switches) contain the forwarding tables and can be remotely controlled via APIs.
The control plane is implemented at the SDN controller level, generally on a physical server or in the cloud. The controller manages the entire “intelligent” logic of the SDN-based network by programming (on-the-fly manipulation) the content of the forwarding tables at the data plane level. The SDN controller manages the infrastructure in its entirety and is able to acquire real-time information on the state and activity of the (physical or virtual) network equipment it controls.
In a routing protocols context, the control plane would correspond to the component whose task it is to find the best paths for the router and set a ready to use routing table for it. It is logically centralized but can be physically distributed between several elements (Bannour et al. 2018). When controllers are physically distributed, they can communicate using East and Westbound API.
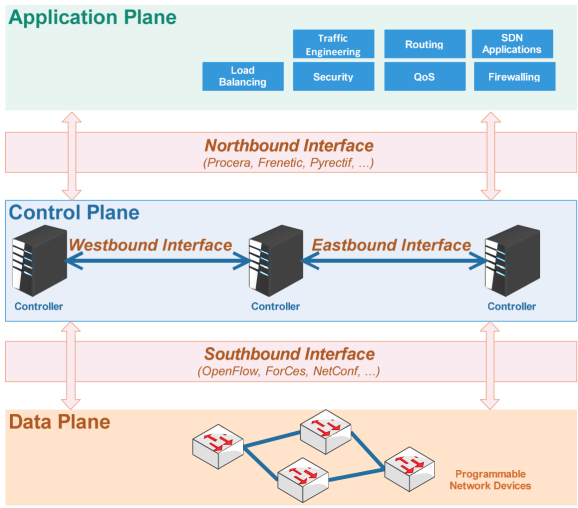
Figure 2.1. Simplified SDN architecture (Zhang et al. 2017)
The control plane and the data plane communicate via a class of protocols known as a Southbound interface. In 2019, the most advanced and commercially available Southbound interface for SDN-based networks was OpenFlow1. There are however other alternatives such as ForCES, SNMP and NetConf of IETF. Furthermore, other approaches to network equipment programming exist, such as P4 (Bosshart et al. 2014; Cordeiro et al. 2017), which are currently under development.
OpenFlow was originally a Stanford University project. Today, it is a standard network protocol, published by the ONF, which serves as a link between the control plane and the data plane. This protocol is composed of instructions (rules) that enable the programming of forwarding tables of network equipment, referred to here as flow tables. The instructions define an action on the traffic (packet transmission, packet rejection, etc.). Various versions of the OpenFlow protocol have been introduced to add more flexibility and reliability including several flow tables, improved correspondence/action capacities, optical ports, group tables, etc.2
Furthermore, many OpenFlow controllers are available, such as POX (Kaur et al. 2014), Beacon (Erickson 2013) and OpenDayLight3.
2.2.2. Logical distribution of SDN control
The physical centralization of the control plane in a single programmable software component known as a “controller” raises a number of problems, particularly in terms of scalability, availability and reliability (Nkosi et al. 2016; Karakus and Durresi 2017). Hence, the higher the number of switches, the higher the load of the SDN controller, and therefore its overload in terms of bandwidth, processing power and memory capacity. The communication delays between the SDN controller and the switches increase also with the network size and extent, which consequently influences the data flow latency (Bannour et al. 2018). The scalability problem can be solved by extending the responsibilities of the data plane in order to lighten the controller load, but this requires a modification of the switches design (Rebecchi et al. 2017).
The control plane should therefore be designed as a distributed system in which several SDN controllers are in charge with the overall network management, while maintaining a logically centralized network view. Indeed, this solution provides a better scalability to the network control plane, while reducing the latencies of the control plane. Moreover, the use of several controllers improves reliability by eliminating the problem of the single point of failure.
Several works have focused on distributed control design. In Oktian et al. (2017), the various approaches to how a logically centralized view is provided to several instances of distributed controllers depending on the choice of design implemented have been discussed. They have thus identified two distributed architectures: flat architecture and hierarchical architecture (Figure 2.2). In flat architecture, each controller manages a subnetwork/field of the global network. In hierarchical architecture, local controllers manage the needs of local applications, while the main controller, generally known as the “root”, deals with the needs of applications requiring a global network view.
In Bannour et al. (2018), the authors classified control architectures depending on how knowledge is disseminated between the controller instances. Two architectures are mentioned, the first centralized and the second distributed. This classification enabled them to compare the various SDN controller platforms in terms of upgradability, reliability and performance criteria. The authors prefer the hierarchical organization of the control plane for better upgradability and better performances. Each controller can thus have different responsibilities and make decisions based on a partial view of the network. The highest level acts as a centralized controller, with the problem of a single point of failure.

Figure 2.2. Control plane distribution models
Table 2.1 presents a classification of network information to be exchanged between distributed controllers in order to maintain the global view.
Table 2.1. Classification of shared network information (Oktian et al. 2017)
| Category | Examples |
| State of the local network (static) | Reachability Topology Capacity QoS parameters |
| State of the local network (dynamic) | Flow tables Flow rules Real-time use of bandwidth Flow path |
| Controller event | State of the controller SDN application – specific information |
| Inventory | List of installed SDN applications List of connected switches |
The distribution of SDN control raises a number of challenges, among which the identification of the required number of controllers as well as their appropriate locations with respect to the expected performance and reliability objectives. Hence, the hierarchical organization of the control plane requires a relevant diagram of control distribution taking into account both the organization of SDN control plane and the physical location of SDN controllers (Bannour et al. 2018). Finally, to preserve the logically centralized view, the requirement to share knowledge between controllers may introduce new scalability problems. Indeed, the frequent propagation of state updates can make the network unavailable, which will increase the latency between controller and switches.
Another significant challenge relates to the fault tolerance of the distributed control architecture. Hence, controller coordination strategies should be implemented to reach agreements and also solve the problems related to the competition between updates and state consistency (Bannour et al. 2018). The state consistency of logically centralized SDN controllers is a major design challenge of SDN-based networks, which involves compromises between rule application and network performances. It is indeed very difficult to reach high consistency in an SDN environment subjected to network failures without compromising its availability and without adding to the complexity of the network state management. Recent approaches have introduced the concept of adaptive consistency, according to which the controllers can adjust their consistency level to reach the expected performance level, depending on specific metrics. This consistency should be taken into account when searching for the optimal location of controllers. Indeed, minimizing the distances between controllers is important for system performances; it facilitates the communication between controllers and improves the state consistency of the network. In Canini et al. (2014), the authors dealt with this problem and proposed a robust distributed SDN control plane, known as software transactional networking (STN).
The security of the distributed SDN-based network is a further crucial challenge. Decentralization of SDN control reduces the risk associated with a single point of failure and with attacks (DDoS, for example). However, the integrity of data flows between SDN controllers and switches is not always certain. A plausible scenario would be that of an attacker being able to corrupt a network by acting as an SDN controller.
Finally, it is also difficult to ensure the interoperability of distributed SDN controllers belonging to different SDN domains and using different controller technologies.
Several researches proposed the integration of automated and adaptive approaches in the distributed control plane in order to meet the previously mentioned challenges. Hence, in Ma et al. (2018), the authors use reinforced learning for the automation of the resource management and distribution in a distributed SDN-based network.
2.3. Security in SDN-based networks
Security is one of the factors hindering the deployment of SDN architectures, which are currently mainly centralized. The centralized aspect of the control plane has in fact many advantages, but it also raises a very important security problem, as all the control planes of the switches are located in a single point. Typically, the impact of the denial of service (DoS) attacks becomes very significant, as the control plane is no longer distributed, which represents a risk of compromising the entire network.
This section presents the various attack surfaces of SDN-based networks, before describing an architecture for the deployment of security services for SDN-based networks.
2.3.1. Attack surfaces
In terms of attack identification and response, SDN has two essential advantages, compared to traditional networks (Fortes 2013; Tang et al. 2016):
- – the control plane enables an administrator to separate and block the attacks on any heterogeneous material (no need to individually reconfigure each component);
- – instead of investing in an expensive intrusion detection system, SDN is able to distribute a task between the nodes; moreover, each node can become a firewall, a proxy, etc.
As for the drawbacks, SDN provides an opportunity to attackers when it exposes new interfaces, which means communication between the control plane and the data plane. By compromising the SDN controller, the entire network can be compromised. Consequently, when using SDN to provide intrusion detection systems (IDS) services, the security of the latter should be kept in mind. An impenetrable access control strategy for the SDN controller should therefore be designed and implemented.
Security of the application plane: the application plane includes various types of applications. Some of them play a very important role in the elaboration of flow rules. Attacking these applications may cause a malfunction of the SDN-based network. An attacker may inject a malicious code in the application or may illegally access the SDN-based network. Developing an access control model or a code verification mode is effective approach against this type of attacks (Klaedtke et al. 2014).
Security of controllers: the SDN controller is the most important element. An attacker conducting an attack on the controller may easily gain total control of the network. The vulnerabilities in the control plane may also lead to illegally controlling the controller. Moreover, an attacker may launch a flooding attack using the vulnerabilities of the switch (sending several packets of a compromised switch to a controller may disable it) or of the OpenFlow protocol (an attacker may send packets that do not correspond to the table and therefore the switch is going to send them all to the controller, which may trigger a DoS/DDoS). The controller is the main target of the DoS attacks.
Security of the data plane: the switch is the crucial part of the data plane. It transfers packets, reads the MAC address table and the ARP requests, etc. Several attacks are possible in the data plane, such as the DoS/DDoS. A further attack can be conducted via the size of the flow tables, which can be very significant and can therefore reduce the switching speed, especially when the Southbound interface is compromised.
Security of protocols: SDN protocols are mainly protocols of the Southbound and NorthBound interfaces. OpenFlow is typically a Southbound interface protocol. Despite its wide use, it still has vulnerabilities because there is no identification and access control for the communications between the switch and the SDN controller. Protocols can be secured by adding an access control mechanism to the network resources in the data plane from the control plane.
2.3.2. Example of security services deployment in SDN-based networks: IPSec service
Previous work by Coly and Mbaye (2019) proposes a framework for the deployment of security services in an SDN-based network. IPSec tunnels are taken as a security service example to illustrate the operation of this framework. Internet Protocol Security (IPsec) (Kent and Seo 2005) is a suite of protocols securing the IP layer of the TCP/IP model. This framework can be used to provide a virtual private network (VPN) or establish secure tunnels between two sites. This protocol uses the Internet Key Exchange (IKE) protocol for key negotiation and management.
The main outcomes of this proposal are as follows: design of an architecture for the deployment of security services in SDN-based networks, a new extension of OpenFlow protocol for the management of secured tunnels and, finally, integration of an IPSec-based tunnel mechanism in SDN-based networks as use case.
2.3.2.1. General architecture
The proposed architecture is presented in Figure 2.3. The networks (networks’ costumers) are connected by an SDN core network. The core of the SDN-based network is composed of Border Gateway Switches (BGS) and Core Internal Switches (CIS). These switches communicate with the SDN controller through the OpenFlow Southbound interface. The SDN controller coordinates the deployment of security services in the SDN-based network. In the case of tunnels deployed between different end nodes, the security service is deployed only at BGS ingress and egress. In other cases, the service is deployed in all the CIS systems of the flow path.

Figure 2.3. Architecture of IPSec tunnel service deployment in an SDN-based network
When a client subscribes to a service level agreement (SLA) comprising a security service, the SDN controller is set up according to this contract. The costumer’s flows will henceforth drive the deployment of this service by sending a “SecTrans” message with the security policies to the (ingress/egress) BGS involved in this communication pathway. The remaining transaction is managed by the Southbound extension. As a use case illustrating the operation of this proposal, let us consider the deployment of an IPsec-based secured tunneling service, as SDN security service. For this purpose, we have extended the OpenFlow protocol for establishing an IPsec tunnel and defined an extended structure for the flow tables.
The SDN controller is in charge with the generation and transmission of IKE identification information. It is also responsible for the control and enforcement of IPsec SPD. Therefore, it has a centralized view of the network and security policies. The IKE component implemented in the network resource runs to create the IPSec security associations using these identification strategies and information. Figure 2.4 illustrates the tunnel deployment process.
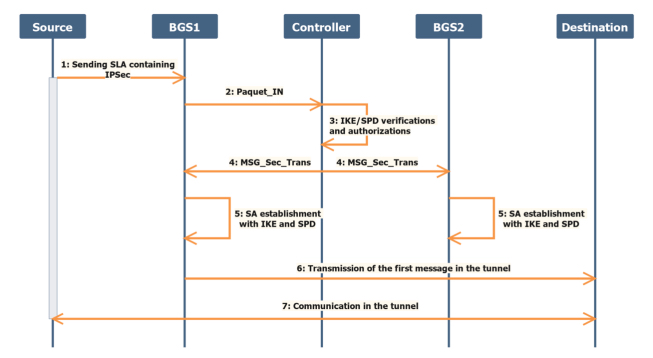
Figure 2.4. Tunnel deployment process
If an end node communicates with another one using an IPsec tunnel, the following procedure unfolds:
- 1) the BGS connected to the source sends a “Packet_In” message (an OpenFlow message) to the controller asking how these packets should be processed;
- 2) if there is a correspondence with the traffic of a service subscriber, the controller generates the IKE identification information and the SPD policies and then sends them to the involved (input and output) BGS in addition to the SecTrans message to allow transmission in the IPsec tunnel; the message adds/modifies a flow with “yes” in the IPsec field;
- 3) the BGS implements the IKE identification information and the SPD strategies to establish security associations before starting transmission.
Once the tunnel is set up, all the messages between these two termination points are transmitted through this tunnel.
2.3.2.2. Deployment performance evaluation
The proposal was evaluated using Mininet4, OpenSwitch and Floodlight5 as SDN controller. Table 2.2 summarizes the node configurations of the test bed.
Table 2.2. System configuration of SDN networks
| Node | Operating system | (Software) Components | CPU | RAM |
| Controller | Debian 8.4 | Floodlight master | (4) @ 3.2 GHz | 4 GB |
| Machine A | Debian 8.4 | Mininet 2.2.2, Racoon, ipsec-tools | (4) @ 3.2 GHz | 4 GB |
| Machine B | Ubuntu 18.04 | Mininet 2.2.2, Racoon, ipsec-tools | (4) @ 2.4 GHz | 4 GB |
| End node A | Ubuntu 18.04 | Racoon, ipsec-tools, iperf, top | (8) @ 4.0 GHz | 8 GB |
| End node B | Ubuntu 14.04 | Racoon, ipsec-tools, iperf, top | (4) @ 3.2 GHz | 8 GB |
The core of SDN-based networks of our test bed contains 10 OpenFlow switches, five on each network (Figure 2.5). These switches are hosted on physical computers interconnected as illustrated in Figure 2.6.
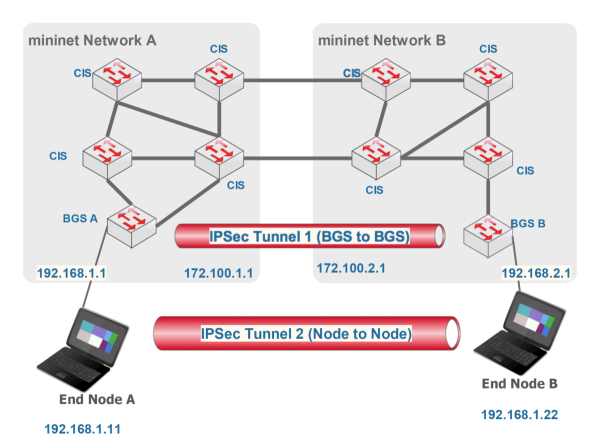
Figure 2.5. Logical topology of the test bed
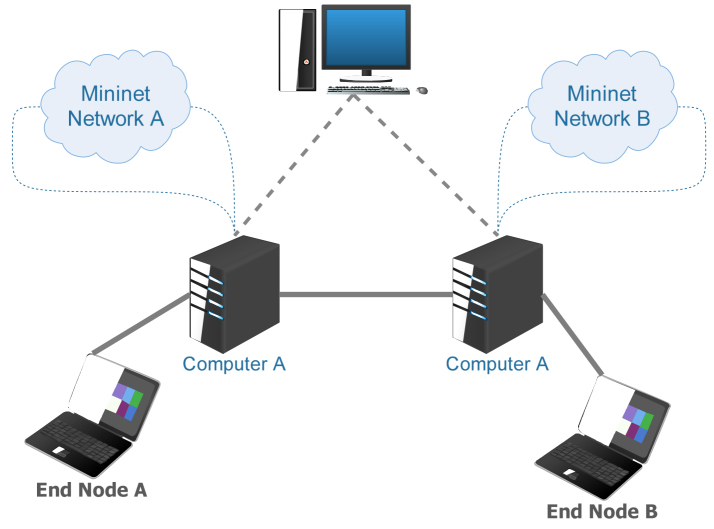
Figure 2.6. Physical topology of the test bed
Performance is evaluated in terms of delay, throughput, jitter and CPU load. During the tests, we compare the performances of an SDN-based network without IPsec with an IPsec tunnel at endpoints, at the client level, and finally in the case of an SDN-based network with an IPsec tunnel between BGS switches.
These results show that, given this configuration, the delay is more significant when the endpoints of the IPsec tunnel are at the level of terminal nodes than between the security gateways represented by BGS (Figure 2.7(A)(a)). We get a similar result if we look at the throughput (Figure 2.7(A)(b)), the jitter (Figure 2.7(B)(c)) and the process load (Figure 2.7(B)(d)).
Although the scope of these results should be confirmed, they can be an argument in favor of deploying security services at gateways (as opposed to terminal nodes). With this type of result, security could be managed as a service at the controller level.
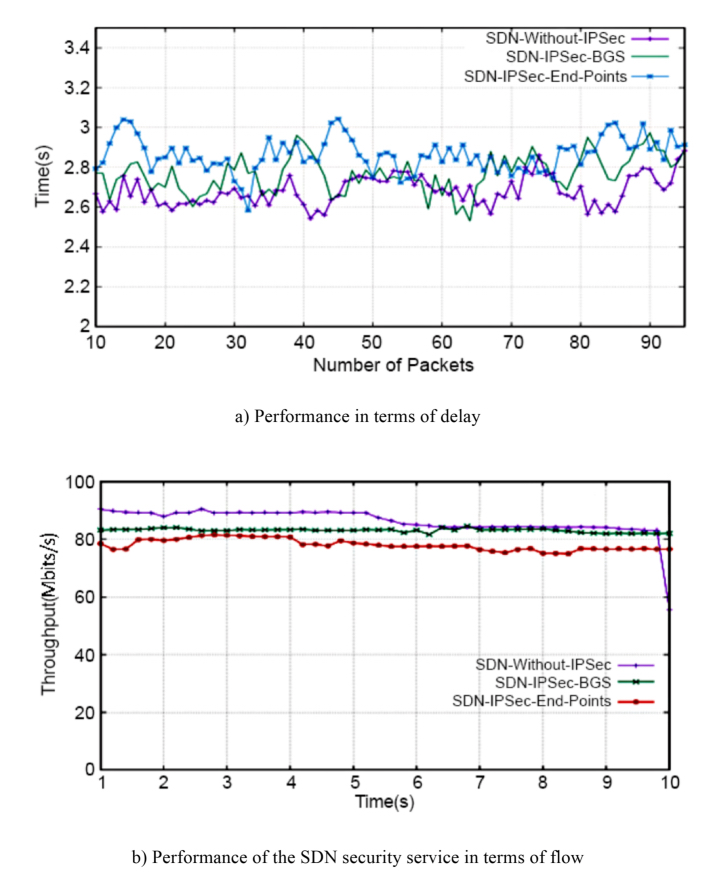
Figure 2.7. (A) Performance of the deployment of IPSec security service on SDN. For a color version of this figure, see www.iste.co.uk/benmammar/network.zip

Figure 2.7. (B) Performance of the deployment of IPSec security service on SDN. For a color version of this figure, see www.iste.co.uk/benmammar/network.zip
2.4. Intelligence in SDN-based networks
Intelligence-oriented design in networks is not new, but it is a challenge with significant stakes. This section starts by presenting the knowledge plane proposed in the 2000s to enable computer networks to make decisions, particularly related to management, in an ”autonomous” manner (Krief 2010). We then introduce the notion of knowledge-defined networking (KDN), which must enable autonomous control and use of SDN-based networks. In the end, we present the very similar notion of intelligence-defined networking (IDN) defined by intelligence or intent-driven networks, a new paradigm brought by Huawei, which is a leader in this market.
2.4.1. Knowledge plane
In 2003, Clark et al. (2003) proposed a new plane enabling knowledge management in a network: the knowledge plane. The main objective of this new plane was to solve the Internet-specific limits, particularly the lack of reliability and adaptation when facing a new situation such as a security attack (Mbaye and Krief 2009). This work has been subsequently integrated in the architectures of autonomous networks. An autonomous network is defined as one with the capacity of management and underlying infrastructure processes to deploy, organize and operate without external aid. The administrator only guides these processes, setting high level objectives (Krief 2010). The knowledge plane plays an essential role in autonomous networks, enabling each autonomous entity to close the network control loop without administrator support. Management tasks can therefore be conducted by the network itself, each autonomous entity being capable of self-configuration, self-optimization, self-protection and self-repair. Movahedi et al. (2012) compared the various architectures of autonomous networks and underlined the role of learning in enabling intelligent adaptation and converging to optimal network operation.
In the context of SDN-based networks, the clear separation between the control and data planes and the centralization of intelligence can positively influence the development of the knowledge plane with new functionalities.
2.4.2. Knowledge-defined networking
Mestres et al. (2017) studied the reasons why AI techniques were not adopted in practice and stated that the expansion of the two recent paradigms, namely the SDN and the network analysis (NA), will facilitate the adoption of these techniques for network control and use. They also proposed a new paradigm, known as KDN, which associates SDN, NA and ML to provide automated network control. In Mestres et al. (2018), they explored the possibility of applying various ML models and techniques for modeling complex network elements, such as the virtual network function (VNF). They also proved that the behavior of various VNFs could be learnt using ML techniques, such as their CPU consumption depending on input traffic.
The ALLIANCE project (Careglio et al. 2018) relies on the new KDN paradigm. Its objective is to design and implement a 5G network infrastructure that is capable of dealing with ubiquitous services, while meeting the performances and commercial demands of multiple stakeholders. This project is expected to propose, compare and interconnect three different prototypes of complete network architecture (from access network to core network), autonomous and 5G oriented. Several network solutions will be studied, such as SDN/NFV, programmable overlay networks and Recursive InterNetwork Architecture (RINA). Each of the retained solutions relies on a KDN orchestrator, which takes advantage of ML techniques for automated network deployment, use, monitoring and repair.
In Hyun and Hong (2017), the authors present an autonomous network architecture combining network telemetry, KDN, SDN and P4 INT. P4 INT (In-band Network Telemetry) enables the gathering of network telemetry data. These data are then used by the KDN to bring intelligence to network management. SDN is then in charge of network management and control depending on the decision made by the knowledge plane. In Hyun et al. (2018), the authors present a first implementation of the network monitoring system.
In Lu et al. (2019), the authors take an interest in the orchestration at KDN level in order to put into operation a hybrid optical/electronic DCN in a high-performance and energy-efficient manner. This orchestration relies on three AI modules based on deep learning, namely the traffic prediction module, the module for the prediction of the virtual machine demand and the module for network reconfiguration. The experimental results show that, besides an improvement in service provision performances, this approach enables better energy efficiency in the system.
2.4.3. Intelligence-defined networks
Intelligence-defined network (IDN) approaches come as a development of SDN by adding a cognitive layer above the control layer. This also enables the introduction of AI in the network management and control. This approach is quite similar to KDN approach, but it is proposed by manufacturers, particularly by Huawei (Jiang 2016; Huawei 2018).
The latter proposed at the Mobile World Congress in 2018 a new offer referred to as an intent-driven network (IDN), aimed at upgrading the SDN-based networks into networks “driven by intent” by the addition of AI, big data and cloud technologies. Emphasis is on the capacity of the control plane to know – or to predict – the type of application/service that a client would want to use and the context in which he/she would want to do it, in order to automatically book for him/her the full bandwidth he/she needs, and provide him/her the best user experience. The network, now centered on the user, is thus capable of accurately identifying the client intent and fulfilling it. It is also capable of detecting in real time the quality of the user experience and conducting a predictive analysis in order to proactively optimize performances (Huang et al. 2018).
2.5. AI contribution to security
This section starts by presenting ML techniques that are most commonly used for security purposes. This is followed by an example of intrusion detection systems as an illustration of AI contribution to the SDN security field.
2.5.1. ML techniques
ML is a subdomain of AI; it can be further divided into four groups:
- 1) supervised learning: given a set of objects, each of which has an associated target value, the system must learn a model that is capable of predicting the proper target value of a new object;
- 2) unsupervised learning: given a set of objects that have no associated target value, the system must learn a model that is capable of extracting regularities in the set of objects in order to understand the data structure;
- 3) semi-supervised learning: given a small set of objects, each of which has an associated target value and a larger set of objects without target value, the system must be capable of solving supervised and/or unsupervised problems;
- 4) reinforcement learning: given a set of decision sequences in a dynamic environment and for each action of a sequence a reward value, the system must learn a model capable of predicting the best decision.
Researches in the field of computer security use mainly supervised and unsupervised learning techniques. These techniques are presented in the next sections.
2.5.1.1. Supervised learning techniques
Supervised learning involves a set of well-established techniques that are used in various domains.
The most commonly used in the security research field are the following:
- 1) decision tree: a decision-aiding tool representing a set of choices in the shape of a tree. The tree has nodes and branches. The nodes are assigned labels by the attributes and the branches are assigned labels by a predicate that applies to the parent node. Decision trees are very successful in solving classification problems. The decision tree can describe a set of data by a tree structure (Negnevitsky 2005). The input and output data can be discrete or continuous. The decision trees can represent all the Boolean functions. A decision tree conducts a sequence of tests, each internal node of the tree corresponding to a test of one of the input attributes (Russell and Norvig 1995). Learning involves recursive tree building by choosing the attribute that assigns the examples in their own classes to the child nodes for each value of the chosen attribute. The decision tree is a tool used in several fields, such as security and data mining;
- 2) Bayesian network: a probabilistic graphical model representing random variables as a graph. This graph represents the relations, which are not deterministic, but probabilistic, causal, between the variables. Bayesian networks involve taking simultaneously into account a priori knowledge (in the graph) and the experience contained in the data;
- 3) genetic algorithm (GA): one of the best known and most commonly used techniques (Holland 1975). Here, the solution to an optimization problem is represented by a chromosome. A set of chromosomes forms the population. The two fundamental but very important operations of this technique are: crossover and mutation. The crossover operation combines previously selected individuals by exchanging some of their parts. On the other hand, mutation introduces a slight uncertainty in the search in order to avoid the local optima problem. The significant factors for the implementation of the whole GA are: the selection strategy and the type of crossover and mutation operators (Boussaid et al. 2013);
- 4) support vector machine (SVM): these are a set of supervised learning techniques intended to solve discrimination and regression problems. SVMs were developed in the 1990s and were adopted due to their capacity to work with large size data. SVMs rely on linear separators that maximize the margin between two different classes in order to provide the best classification. The learning methods can be used to transform the input data into a large size space in order to deal with linearly nonseparable cases (Nguyen and Armitage 2008);
- 5) neural networks: artificial neural networks drew their inspiration mainly from the biological neurons of the human brain (Negnevitsky 2005). Neural networks are widely used because of their capacity to deal with large amounts of information and their stability when exposed to noise. Neural networks are a set of neurons (small processors) working in parallel. These neurons receive data, apply a function known as an “activation function” and send them over to other neurons or to an external source. Neural networks have many advantages. First of all, they can adjust to data without explicitly specifying the function or distribution for the representation of the underlying model (Zhang 2000). Second, neural networks form a universal functional approximator, which can approximate any function (Zhang 2000). Third, neural networks are nonlinear models, which gives them the flexibility needed for the representation and modeling of complex relations (Zhang 2000). MultiLayer Perceptrons (MLP) are the most commonly used systems for neural network classification. MLPs are mainly formed with supervised learning algorithms. Neural networks are subjected to overadjustments when too many parameters are used in the model (Russell and Norvig 1995);
- 6) random forest: this technique belongs to the model aggregations family. It is a particular case of bagging (bootstrap aggregation) applied to decision trees. The principle is to average the predictions of several independent models in order to reduce variance, and therefore the prediction error. To build these various models, several bootstrap samples are selected, in other terms, unrestricted random sampling is performed. Random forests add chance at the variable level, besides the bagging principle. For each tree, a bootstrap sample of individuals must be selected and a tree node is built on a subset of randomly drawn variables;
- 7) K-nearest neighbors (K-NN): a classification algorithm. The idea is to vote the nearest neighbors through an observation x. The class of x is determined based on the majority class among the K-NN of the observation x. The nearest neighbor is determined using a distance function.
2.5.1.2. Unsupervised learning techniques
The unsupervised approach also involves a set of well-established algorithms:
- 1) K-means is one of the best known clustering approaches. Its implementation requires knowing the k parameter beforehand, which indicates the number of resulting clusters. Each data point is assigned to the centroid that is closest to each group. K-means minimizes an objective function, which represents the distance between the data points and their corresponding centroids (Khan and Ahmad 2004). Centroids are updated repeatedly, depending on the data points attributed to them until they stay the same or no point changes. K-means mainly depends on the initial set of classes. Consequently, an inappropriate choice of k may lead to mediocre results (Zhang and Xia 2009). Moreover, the fuzzy-C-means (FCM) classification (Pal and Bezdek 1995), also known as “soft K-means”, enables each data point to belong to several classes. In other terms, a data point may belong to all the classes with a different adhesion degree;
- 2) self-organizing map (SOM): used in DoS attacks, the SOM algorithm is also known as the Kohonen algorithm. It is a stochastic classification algorithm that integrates a notion of vicinity between classes.
These various learning techniques are summarized in Table 2.3.
Table 2.3. The most commonly used machine learning techniques for computer security purposes
| ML Algorithm | Problem | Advantages | Drawbacks |
| Decision tree | Classification Regression | Easy to implement Easily understandable decisions Data classification without heavy computation Continuous and discrete data processing | Costly in terms of computation and memory space Instability: a small change in the dataset may drive significant modifications in the model |
| Bayesian network | Classification | Easy to implement Rapid learning phase | Difficulty in managing continuous data |
| Genetic algorithm | Classification | Conclude proper classification rules | Computation cost |
| Support vector machine | Classification Regression | Big data processing | Less effective on a noised dataset Computation costly |
| Neural network | Classification Regression | Rapid prediction phase Works well on large volume of training data | Computation cost Difficult interpretation of the learning model by a human |
| Random Forest | Classification Regression | Works well on big learning data Reduces model instability compared to decision trees | Low training speed |
| K- NN | Classification Regression | Easy to implement | Costly in terms of computation and memory space |
| K-means | Clustering | Easy to implement Easy to interpret results | Cost of linear computation with the size of learning data |
| SOM | Clustering | Manipulation of very large volume data | Computation costly |
2.5.2. Contribution of AI to security service: intrusion detection
The above-mentioned AI techniques have been used to solve many security problems in general, and particularly for intrusion detection (Soheily-Khah et al. 2018).
In Barapatre et al. (2008), an approach with a multilayer perceptron–back propagation (MLP-BP) is proposed. The input to the proposed system has the characteristics of the Knowledge Discovery from Database (KDD)6 dataset and the output the classification of normal packets and suspect packets present in the dataset. The MLP-BP neural network has been shown to detect DoS and “Probe” attacks more accurately than the user to root (U2R) attacks. In Lu et al. (2015), the authors use the radial basis function (RBF) neural networks, which are very practical in intrusion detection systems. They compared RBF and MLP-BP using a KDD dataset that was processed by the conversion of all the chains into figures, thus reducing the size of the dataset. The simulation results showed that the RBF neural network is better than MLP-BP in terms of learning time, accuracy and detection of attacks.
Canbay and Sagiroglu (2015) propose a hybrid approach for attack detection. GA and K-NN were used in combination for attack modeling and detection. K-NN was used for the classification of the attacks and GA for the selection of k neighbors in a sample of attacks. This hybrid system was applied for the first time in the field of intrusion detection. The results showed that the proposed system yields better results in terms of detection accuracy than a single system.
Most researchers used the KDD dataset, which was widely criticized for not being a faithful representation of the network. In Sahu and Mehtre (2015), the authors used a new set of labeled network data, referred to as the “Kyoto 2006+ dataset”. In Kyoto 2006+, each instant is labeled as “normal” (no attack), attack” (known attack) and “unknown attack”. The users used the Decision Tree (J48) algorithm to classify the network packet that could be used for a Network IDS (NIDS). The results showed that the decision tree has a very good classification accuracy and that it also enables the classification of unknown attacks.
As these several work samples prove, the potential of AI has not yet been exhausted in the security field, since a combination of techniques may yield better results.
2.6. AI contribution to security in SDN-based networks
This section takes intrusion detection systems as examples to illustrate the potential of AI in the field of SDN security.
Network administrators implement IDS to avoid intrusion attacks and apply the network security policy. An IDS monitors the traffic and sends intrusion alerts to the administrator console when a suspicious message is detected.
In Tang et al. (2016), the authors propose a deep learning approach for the detection of anomalies in an SDN environment. They built a model of deep neural network (DNN) for an intrusion detection system. They proved that deep learning has a strong use potential for anomaly detection in SDN environments. In Tang et al. (2018), the authors improve the approach presented in Tang et al. (2016). They propose an intrusion detection system that uses Gated Recurrent Unit Recurrent Neural Network (GRUN-RNN) for SDN networks. The proposed approach is tested using a NSL-KDD7 dataset. Experimental results show that the proposed approach has also a strong potential for intrusion detection in SDN environments. Thaseen and Kumar (2013) aimed to evaluate various tree-based classification algorithms that classify the network events in intrusion detection systems. Experiments are conducted on the NSL-KDD dataset. The results show that the RandomTree model has a better accuracy if false positives are minimized.
In Chen and Yu (2016), the authors propose a new collaborative intrusion prevention architecture (CIPA). A CIPA is deployed as virtual network of a neural network on the subnetwork. Taking advantage of the parallel and simple mathematical handling of neurons in a neural network, CIPA can spread its light computation capability to the programmable switches in the subnetwork. Each programmable switch virtualizes one to several neurons. The whole neural network operates as an integrated IDS/IPS. This enables CIPA to detect the attacks distributed in a global view, which does not require extended communication and computation time.
The DDoS attack is one of the most recurrent problems in network security. Despite the fact that DDoS attack mechanisms are widely understood, the problems have recently become increasingly frequent due to the similarity between a DDoS attack and normal traffic. In Nam et al. (2018), the authors propose approaches for the detection of DDoS attacks. The algorithms proposed in the detection architecture are implemented in an SDN environment. The SDN controller enables the rapid compilation of a complex classification and detection algorithm. Experimental results show that these algorithms have a relatively short processing time, while maintaining good accuracy.
In Mihai-Gabriel and Victor-Valeriu (2014), the authors present a way to reduce DDoS attacks in an SDN environment by evaluating the risks using a cyberdefense system based on neural networks.
In Niyaz et al. (2016), the authors propose a multivector DDoS detection system based on deep learning in an SDN environment. They implemented the system as network application above an SDN controller. Deep learning was used to reduce a large number of functionalities derived from the network traffic headers. Using the traffic traces gathered from various scenarios, the authors detected attacks with high accuracy and very few false positives.
Braga et al. (2010) present a light method for DDoS attack detection based on traffic flow characteristics, in which such information is extracted in a relatively short time compared to traditional approaches. This is made possible by the use of the NOX platform, which provides a programming interface facilitating the processing of switch information. The approach has good detection performance and a very low rate of false positives.
In Mehdi et al. (2011), the authors develop algorithms for the detection of significant traffic anomalies that can be implemented in an SDN context using Openflow and NOX compatible switches as controller. They prove that these algorithms are accurate in the identification of malicious activities in domestic networks with respect to Internet service provider (ISP). Moreover, the analysis of efficiency of SDN implementations on a programmable domestic network router indicates that anomaly detectors can operate without affecting the performances of domestic network traffic.
2.7. Deployment of an intrusion prevention service
In the context of signature-based IDS, when a network attack occurs, one of the most difficult tasks for the network administrator or expert is to write an accurate signature describing this new attack.
This section presents the works of Hamdi et al. (2015), who use another AI technique: inductive logical programming (Muggleton 1991) for automated signature generation.
Finally, we present a proposal for advancing this work, by enabling the “intelligent” deployment of such a security service for SDN-based networks.
2.7.1. Attack signature learning as cloud service
The proposal in Hamdi et al. (2015) is to provide attack signature learning as a Cloud service. The service is deployed in the cloud with a client/server architecture. Clients have access to the service via secured VPN.
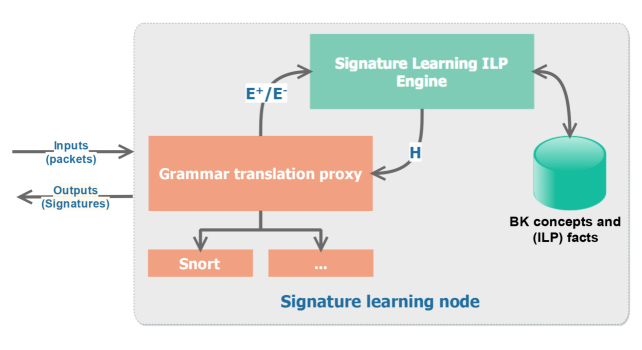
The learning service is provided by learning nodes (LN) containing inductive logic programming (ILP) modules. The LNs receive as input malicious and normal traffics in standard formats (for example, PCAP). The system replies with a Prolog rule (signature) that can be translated into any specific target grammar.

Insiden an LN there is an ILP engine, a facts base and a grammar translator proxy (GTP). This proxy is a component of data mediation between the ILP engine and the client. It translates the input data from the client into predicates corresponding to ILP engine parameters:
- – malicious traffic
 positive examples (E+);
positive examples (E+); - – normal traffic
 negative examples (E−).
negative examples (E−).
The ILP engine learns the rules corresponding to the attack signatures presented to it. This engine needs a facts base composed of background knowledge (BK) and examples that correspond to traffics classified as malicious.
Once the ILP engine learns the rules, GTP transforms these rules of Prolog grammar into the target IDS-specific grammar.
For the time being, only the grammar for IDS SNORT rules is taken charge of by the proposal. Let the learnt signature be C ⊨ P1 …Pn, where C is the concept at the clause heading and P1 …Pn are predicates of BK. The transformation of the SNORT signature rule involves two stages.
Stage 1: build the rule heading based on the Prolog signature by extracting the source and destination IP addresses, the port numbers in the learnt signature. The BK predicates that can be in the signature rule body are: Pi=ip_src(packet), Pj=ip_dst(packet), Pk=src_port(packet), dst_port(packet), Pl=proto(X,tcp). Table 2.4 gives an idea of the transformation done.
Table 2.4. Construction of rule heading
| (Prolog) Signature | SNORT signature |
| ip_src(192.168.0.1) ; ip_dst(10.0.0.1),proto(P,tcp) ; dst_port(X),src_port(Y) | alert tcp 192.168.0.1:ANY > 10.0.0.1:ANY |
| ip_src(X),dst_ip(10.0.0.1), proto(P,icmp) | alert icmp ANY > 10.0.0.1 |
Stage 2: build the body of rules. In the SNORT body, C is transformed into (msg: some_text_id). The body predicates Pn …Pn are transformed in the closest SNORT filter F1, F2, F3, etc. For example, syn_tcp_actif (packet) could be translated into the SNORT filter flow: (…, Flow:Established,…). The final body of the SNORT rule is: (F1, F2,…). Finally, the signature is sent to the client to feed their signature base.
Aleph (A Learning Engine for Proposing Hypotheses) (Srinivasan 2000) was used as ILP engine to realize this solution. This approach was shown to be very effective in DoS attacks. The main advantage of this solution is that the complex task of writing the signature based on network logs can now be accomplished by the cloud service.
This approach is of great interest for the design of SDN-based networks, which already integrates the principle of delocalization of network intelligence in a logically centralized controller. The next section presents the proposals on the architectural plane to enable the deployment of such services in SDN-based networks.
2.7.2. Deployment of an intrusion prevention service in SDN-based networks
One of the first challenges encountered when deploying an IDS architecture that learns the signatures on-the-fly and deploys them is the acceptable response time. The language filter systems of IDS are traditionally much richer than Southbound API in SDN networks. It is therefore a challenge to implement an intrusion prevention system (IPS) with an acceptable response time.
The objective of the proposed architecture is to provide a self-managed IPS for SDN networks. The IPS enables the extension of the security functions from one SDN controller through a P4 interface (Bosshart et al. 2014) because of AI. In fact, the controller’s task is to transfer the retransmission rules or ACL (Access Lists) to switches supporting OpenFLow inside the network. Nevertheless, it is not designed to analyze and detect the attacks inside the network. IDS and IPS are the tools dedicated to this task. The implementation of these tools is a real challenge, given the large amount of data circulating in the SDN domain and the performance constraints related to virtualization. This architecture approaches this challenge by means of three operating blocks: a signature-based intrusion detection and prevention system, a system for on-the-fly learning of attack signatures based on ILP and deep learning, and a P4 interface enabling the deployment of new detection rules in the network.
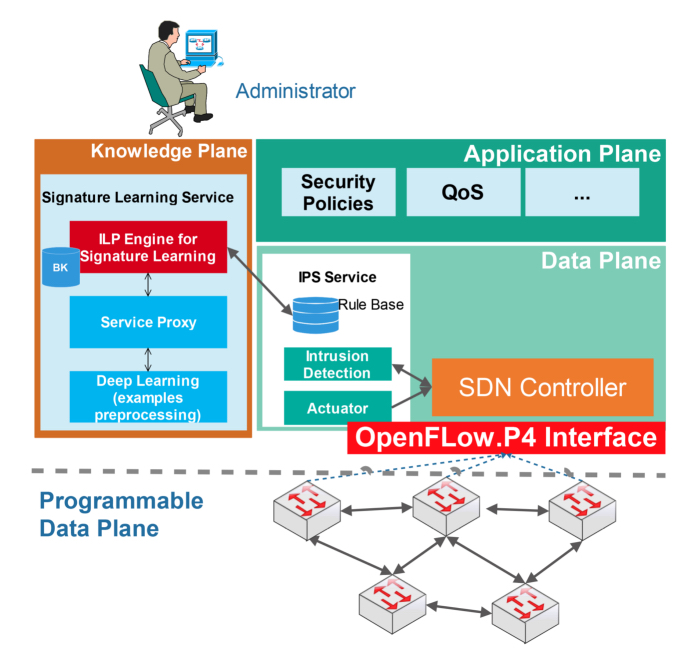
Figure 2.10. Architecture of an intelligent SDN with IDS
The system (Figure 2.10) operates as a processing chain that is self-optimizing with the occasional intervention of the administrator as oracle when needed. The data plane has a classical role in this architecture; on the other hand, the control plane demonstrates more intelligent activity through the knowledge plane.
In SDN-based networks, the knowledge plane manages the whole knowledge in order to improve/optimize the controller operation to ensure the security functions (policy optimization, intrusion prevention, detection of malicious operation of a switch, etc.), routing (route optimization, self-healing of disappeared routes, prediction of load distribution, etc.) and QoS.

Figure 2.11. Interactions between components of data architecture
The knowledge plane makes it possible to have a local intelligent loop for the management of a signature-based IPS service. The loop is described in Figure 2.11. In this loop, there are two learning tools with connected roles:
- – the main learning tool relies on ILP. ILP makes it possible to learn a hypothesis from examples of malicious packets as indicated in Hamdi et al. (2015);
- – the deep learning module that, based on examples of a reference dataset such as NSL-KDD, builds a BK that makes it possible to consider only those concepts that are relevant for learning an attack:
where Δ is the deep learning function that takes as parameter a dataset (such as NLS_KDD) and positive examples of the attack. The output of this function must be the set of p properties that are relevant for BK. Relevance is represented by the function Π(p, Dset) > 0. This formula expresses the fact that the system will use a training base to determine the fields of parameters that are potentially relevant to appear in the attack signature. Indeed, the BK of ILP module generally contains predicates that can be used to describe the attack. The choice of BK content is crucial for having the most accurate possible rules. To add bias to BK design, we use deep learning in order to determine for each attack the properties that are most susceptible to appear in BK. The deep learning module uses the bases of training traces, in our case NSL-KDD, to optimize the BK content. This optimization involves mainly the reduction of the size that enables the upstream filtering of the most relevant parameters for an attack description, and therefore the reduction of the research space of the ILP engine.
A P4 interface makes it possible to transform the filters and actions of the intrusion detection system into programs that can be deployed in programmable switches.
The intrusion detection service presented in this section is deployed by means of a single SDN controller. To allow for scalability, we recommend the existence of physically distributed but logically centralized controllers, as well as a flat model, a solution that seems to be widely accepted at present. For exchanges between controllers in order to maintain the global view, and in the absence of standardized Eastbound/Westbound API, the Pub/Sub approach should also be retained, as it makes it possible to keep a controller informed only during a change of state.
2.8. Stakes
The stakes of using AI and ML tools for security management in SDN-based networks are very high. This is true not only in technical terms, but also from a societal perspective. Indeed, computer security has today an impact on everyday life, especially with the coming 5G. This technology will significantly impact several domains such as medicine, health, road safety, etc.
First of all, with the advent of big data and big analytics, the devices that enable the study of system vulnerabilities are increasingly effective (Terzi et al. 2017; Hajizadeh et al. 2018; Hoon et al. 2018). If such devices start to identify security vulnerabilities that are intrinsic to the design of SDN, and no protection is possible, the potential consequence is to simply give up this technology. It is therefore important that SDN controllers feature an intelligence and autonomy enabling them to get reprogrammed and reprogram the data plane in an adapted manner.
On the other hand, intelligent attack systems may lead to the appearance of vulnerabilities at the limit of normality in intrusion detection systems based on traditional anomalies, which can generate many false positives and negatives. But given a large number of false positives, the administrators may be tempted to slightly relax the security or to integrate exceptions for actual attacks. Indeed, when faced with intelligent attacks, the most adapted defense is another AI that is able to support the administrators in making the proper decisions.
The coming of 5G highlights the use of AI in security tools even more. Indeed, the large amount of data cannot be analyzed with classical technologies and tools. On the one hand, the security tools may be unable to provide a response within acceptable time: an attack might be successful while the detection system provides a response. On the other hand, these tools may create bottlenecks if the system operates in paranoid mode examining all the packets. The AI/ML tools may enable the limitation of analysis to traffics that are relevant for analysis. If this amount of data could have a linear behavior with respect to the traffic increase, security services could be deployed while ensuring scalability.
2.9. Conclusion
The concept of an SDN-based network was created in order to meet the challenges related to network development. The basic principles of SDN-based networks are as follows: introduction of transmission equipment programmability via standard and open Southbound interfaces; decoupling the control plane and the data plane and the global view of the network by a logical centralization of “network intelligence”.
With this new approach, the elements of the data plane are programmable and very effective in packet transmission, as they conduct less complex tasks. The components of the control plane are implemented on a controller that concentrates the network driving activities due to its global view.
Nevertheless, the security question is an important stake in the development of SDN-based networks. Indeed, the weak points represented by the controller and the securing of programmable network equipment in an environment generating large amount of data are the main challenges to be met.
2.10. References
Abubakar, A. and Pranggono, B. (2017). Machine learning based intrusion detection system for software defined networks. Seventh IEEE International Conference on Emerging Security Technologies (EST). 6–8 September 2017, Canterbury, UK, 138–143.
Bannour, F., Souihi, S., and Mellouk, A. (2018). Distributed SDN control: Survey, taxonomy, and challenges. IEEE Communications Surveys & Tutorials, 20(1), 333–354.
Barapatre, P., Tarapore, N.Z., Pukale, S.G., and Dhore, M.L. (2008). Training MLP neural network to reduce false alerts in IDS. International Conference on Communication and Networking, 1–7.
Bi, J., Zhang, K., and Cheng, X. (2009). Intrusion detection based on RBF neural network. International Symposium on Information Engineering and Electronic Commerce, 357–360.
Boussaid, I., Lepagnot, J., and Siarry, P. (2013). A survey on optimization meta-heuristics. Information Sciences, 237, 82–117.
Braga, R., Mota, E., and Passito, A. (2010). Lightweight DDoS flooding attack detection using NOX/OpenFlow. 35th Conference on Local Computer Networks (LCN), 408–415.
Canbay, Y. and Sagiroglu, S. (2015). A hybrid method for intrusion detection. 14th International Conference on Machine Learning and Applications (ICMLA), 156–161.
Canini, M., De Cicco, D., Kuznetsov, P., Levin, D., Schmid, S., and Vissicchio, S. (2014). STN: A robust and distributed SDN control plane. Proceedings of Open Networking Summit (ONS’14). March 2–4 2014, Santa Clara, CA, USA, 1–2.
Careglio, D., Spadaro, S., Cabellos, A., Lazaro, J.A., Perelló, J., Barlet, P., Gené, J.M., and Paillissé, J. (2018). ALLIANCE Project: Architecting a knowledge-defined 5G-enabled network infrastructure. 20th International Conference on Transparent Optical Networks (ICTON).
Chen, X.F. and Yu, S.Z. (2016). CIPA: A collaborative intrusion prevention architecture for programmable network and SDN. Computers & Security, 58, 1–19.
Chung, S.P. and Mok, A.K. (2006). Allergy attack against automatic signature generation. 9th International Conference on Recent Advances in Intrusion Detection.
Clark, D.D., Partridge, C., Ramming, J.C., and Wroclawski, J.T. (2003). A Knowledge plane for Internet. Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, 3–10.
Coly, A. and Mbaye, M. (2019). S-SDS: A framework for security deployment as service in software defined networks. Third EAI International Conference.
Cordeiro, W.L.D.C., Marques, J.A., and Gaspary, L.P. (2017). Data plane programmability beyond openflow: Opportunities and challenges for network and service operations and management. Journal of Network and Systems Management, 25(4), 784–818.
Das, S. and Nene, M.J. (2017). A survey on types of machine learning techniques in intrusion prevention systems. International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), 2296–2299.
Dey, S.K., Rahman, M.M., and Uddin, M.R. (2018). Detection of flow based anomaly in OpenFlow controller: Machine learning approach in software defined networking. 4th International Conference on Electrical Engineering and Information & Communication Technology.
Erickson, D. (2013). The beacon openflow controller. Proceedings of the Second ACM SIGCOMM Workshop on Hot Topics in Software Defined Networking.
Fortes, J. (2013). Cloud computing security: What changes with software-defined networking? ARO Workshop on Cloud Security.
Gowtham, V.N., Baratheraja, R.N., Jayabarathi, G., and Vetriselvi, V. (2018). Collaborative intrusion detection system in SDN using game theory. In Proceedings of the International Conference on Computing and Communication Systems, Mandal, J., Saha, G., Kandar, D., and Maji, A. (eds). Springer, Singapore.
Hajizadeh, M., Phan, T.V., and Bauschert, T. (2018). Probability analysis of successful cyber attacks in SDN-based networks. Conference on Network Function Virtualization and Software Defined Networks (NFV-SDN), 1–6.
Hamdi, O., Mbaye, M., and Krief, F. (2015). A cloud-based architecture for network attack signature learning. Conference on New Technologies Network and Security.
Holland, J.H. (1975). Adaption in Natural and Artificial Systems. University of Michigan Press, Ann Arbor.
Hoon, K.S., Yeo, K.C., Azam, S., Shunmugam, B., and De Boer, F. (2018). Critical review of machine learning approaches to apply big data analytics in DDoS forensics. International Conference on Computer Communication and Informatics, 1–5.
Huang, C.H., Lee, T.H., Chang, L.H., Lin, J.R., and Horng, G. (2018). Adversarial attacks on SDN-based deep learning IDS system. International Conference on Mobile and Wireless Technology, 181–191.
Huawei (2018). Roads to a better future. Mobile World Congress.
Hyun, J. and Hong, J.W.K. (2017). Knowledge-defined networking using in-band network telemetry. 19th Asia-Pacific Network Operations and Management Symposium.
Hyun, J., Van Tu, N., and Hong, J.W.K. (2018). Towards knowledge-defined networking using in-band network telemetry. IEEE/IFIP Network Operations and Management Symposium.
Jiang, S. (2016). Intelligence Defined Network IDN. IETF 97.
Karakus, M. and Durresi, A. (2017). A survey: Control plane scalability issues and approaches in software-defined networking (SDN). Computer Networks, 112, 279–293.
Kaur, S., Singh, J., and Singh Ghumman, N. (2014). Network programmability using POX controller. International Conference on Communication, Computing and Systems.
Kent, S. and Seo, K. (2005). Security Architecture for the Internet Protocol. Memo, Network Working Group, Obsoletes 2401.
Khan, S.S. and Ahmad, A. (2004). Cluster center initialization algorithm for K-means clustering. Pattern Recognition Letters, 25(11), 1293–1302.
Klaedtke, F., Karame, G.O., Bifulco, R., and Cui, H. (2014). Access control for SDN controllers. Proceedings of the 3rd Workshop on Hot Topics in Software Defined Networking, 219–220.
Kreutz, D., Ramos, F.M.V., Veríssimo, P.E., Rothenberg, C.E., Azodolmolky, S., and Uhlig, S. (2015). Software-defined networking: A comprehensive survey. Proceedings of the IEEE, 103(1), 14–76.
Krief, F. (ed.) (2010). Communicating Embedded Networks: Network Applications. ISTE Ltd, London and Wiley, New York.
Lu, J., Hongping, H., and Yanping, B. (2015). Generalized radial basis function neural network based on an improved dynamic particle swarm optimization and AdaBoost algorithm. Neurocomputing, 152, 305–315.
Lu, W., Liang, L., Kong, B., Li, B., and Zhu, Z. (2020). AI-assisted knowledge-defined network orchestration for energy-efficient datacenter networks. IEEE Communications Magazine. IEEE, 58(1), 86–92.
Ma, L., Zhang, Z., Ko, B., Srivatsa, M., and Leung, K.K. (2018). Resource management in distributed SDN using reinforcement learning. SPIE Defense + Security, April 15–19.
MacQueen, J.B. (1967). Some methods for classification and analysis of multivariate observations. Proceedings of the 5th Berkeley Symposium on Mathematical Statistics and Probability, 281–297.
Mbaye, M. and Krief, F. (2009). A collaborative knowledge plane for autonomic networks. In Autonomic Communication, Vasilakos, A.V., Parashar, M., Karnouskos, S., and Pedrycz, W. (eds). Springer, Boston, 60–90.
Mehdi, S.A., Khalid, J., and Khayam, S.A. (2011). Revisiting traffic anomaly detection using software defined networking. International Workshop on Recent Advances in Intrusion Detection, 161–180.
Mestres, A., Alarcón, E., and Cabellos, A. (2018). A machine learning-based approach for virtual network function modeling. IEEE Wireless Communications and Networking Conference Workshops (WCNCW).
Mestres, A., Rodriguez-Natal, A., Carner, J. et al. (2017). Knowledge-defined networking. ACM SIGCOMM Computer Communication Review, 47(3), 2–10.
Mihai-Gabriel, I. and Victor-Valeriu, P. (2014). Achieving DDoS resiliency in a software defined network by intelligent risk assessment based on neural networks and danger theory. 15th International Symposium on Computational Intelligence and Informatics (CINTI), 319–324.
Movahedi, Z., Ayari, M., Langar, R., and Pujolle, G. (2012). Survey of autonomic network architectures and evaluation criteria. IEEE Communications Surveys & Tutorials. IEEE publisher, 14(2), 464–490.
Muggleton, S. (1991). Inductive logic programming. New Generation Computing, 8, 295–318.
Nam, T.M., Phong, P.H., Khoa, T.D. et al. (2018). Self-organizing map-based approaches in DDoS flooding detection using SDN. International Conference on Information Networking (ICOIN), 249–254.
Negnevitsky, M. (2005). Artificial: A Guide to Intelligent Systems. Addison-Wesley, Boston, MA.
Newsome, J., Karp, B., and Song, D. (2006). Paragraph: Thwarting signature learning by training maliciously. Proceedings of the 9th International Conference on Recent Advances in Intrusion Detection, 81–105.
Nguyen, T.T. and Armitage, G. (2008). A survey of techniques for internet traffic classification using machine learning. IEEE Communications Surveys & Tutorials. IEEE publisher, 10(4), 56–76.
Niyaz, Q., Sun, W., and Javaid, A.Y. (2016). A deep learning-based DDoS detection system in software-defined networking (SDN) [Online]. Available at: arXiv:1611.07400.
Nkosi, M., Lysko, A., Ravhuanzwo, L., Nandeni, L., and Engelberencht, A. (2016). Classification of SDN distributed controller approaches: A brief overview. International Conference on Advances in Computing and Communication Engineering (ICACCE).
Oktian, Y.E., Lee, S., Lee, H., and Lam, J. (2017). Distributed SDN controller system: A survey on design choice. Computer Networks, 121, 100–111.
ONF (2015). Software-defined networking: The new norm for networks [Online]. White paper. Available at: https://www.opennetworking.org/images/stories/downloads/sdn-resources/white-papers/wp-sdn-newnorm.pdf, [Accessed February 2019].
Pal, N.R. and Bezdek, J.C. (1995). On cluster validity for the fuzzy c-means model. IEEE Transactions on Fuzzy Systems, 3(3), 370–379.
Pat, B., Dan, D., Glen, G., Martin, I., Nick McKeown, Jennifer, R., Cole, S., Dan, T., Amin, V., George, V., and David, W. (2014). P4: Programming protocol-independent packet processors. ACM SIGCOMM Computer Communication Review. ACM publisher, 44(3), 87–95.
Rebecchi, F., Boite, J., Nardin, P.-A., Bouet, M., and Conan, V. (2017). Traffic monitoring and DDoS detection using stateful SDN. Conference on Network Softwarization (NetSoft), 1–2.
Russell, S. and Norvig, P. (1995). Artificial Intelligence (A Modern Approach). Prentice Hall, Upper Saddle River.
Sahu, S. and Mehtre, B.M. (2015). Network intrusion detection system using J48 decision tree. International Conference on Advances in Computing, Communications and Informatics (ICACCI), 2023–2026.
Shu, Z., Wan, J., Li, D., Lin, J., Vasilakos, A.V., and Imran, M. (2016). Security in software-defined networking: Threats and countermeasures. Mobile Networks and Applications, 21(5), 764–776.
Soheily-Khah, S., Marteau, P.F., and Béchet, N. (2018). Intrusion detection in network systems through hybrid supervised and unsupervised machine learning process: A case study on the ISCX dataset. 1st International Conference on Data Intelligence and Security (ICDIS), 219–226.
Srinivasan, A. (2000). The aleph manual. Technical Report, Oxford University, Oxford.
Tang, T.A., Mhamdi, L., McLernon, D., Zaidi, S.A.R., and Ghogho, M. (2016). Deep learning approach for network intrusion detection in software defined networking. International Conference on Wireless Networks and Mobile Communications (WINCOM), 258–263.
Tang, T.A., Mhamdi, L., McLernon, D., Zaidi, S.A.R., and Ghogho, M. (2018). Deep recurrent neural network for intrusion detection in SDN-based networks. 4th Conference on Network Softwarization and Workshops (NetSoft), 202–206.
Terzi, D.S., Terzi, R., and Sagiroglu, S. (2017). Big data analytics for network anomaly detection from netflow data. International Conference on Computer Science and Engineering (UBMK), 592–597.
Thaseen, S. and Kumar, C.A. (2013). An analysis of supervised tree-based classifiers for intrusion detection system. International Conference on Pattern recognition, informatics and mobile engineering (PRIME), 294–299.
Wang, J., Wang, Y., Hu, H., Sun, Q., Shi, H., and Zeng, L. (2013). Towards a securityenhanced firewall application for openflow networks. In Cyberspace Safety and Security. Lecture Notes in Computer Science, Wang, G., Ray, I., Feng, D., and Rajarajan, M. (eds). Springer, Basel.
Xie, J., Yu, F.R., Huang, T., Xie, R. et al. (2019). A survey of machine learning techniques applied to software defined networking (SDN): Research issues and challenges. IEEE Communications Surveys and Tutorials, 21(1), 393–430.
Zhang, C. and Xia, S. (2009). K-means clustering algorithm with improved initial center. Second International Workshop on Knowledge Discovery and Data Mining, 790–792.
Zhang, G.P. (2000). Neural networks for classification: A survey. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 30(4), 451–462.
Zhang, Y., Cui, L., Wang, W., and Zhang, Y. (2017). A survey on software defined networking with multiple controllers. Journal of Network and Computer Applications, 103, 101–118.
- 1 Available at: www.opennetworking.org/software-defined-standards/specifications/.
- 2 For further details on the various versions of the OpenFlow specification, please refer to: www.opennetworking.org/software-defined-standards/specifications/.
- 3 Available at: http://www.opendaylight.org/.
- 4 Available at: http://www.mininet.org.
- 5 Floodlight OpenFlow Controller – Project Floodlight, Big switch network, available at: http://www.projectfloodlight.org/floodlight/.
- 6 Available at: http://nsl.cs.unb.ca/NSL-KDD/.
- 7 Available at: http://nsl.cs.unb.ca/NSL-KDD/.
