Route Filtering and Attribute Manipulation
Route filtering and attribute manipulation are the basis of implementing BGP policies. This section describes the following:
-
BGP route maps
-
Prefix lists
-
Identifying and filtering routes based on the NLRI
-
Identifying and filtering routes based on the AS_PATH
In order for new BGP policies such as attribute manipulation or filtering to be applied, a fresh set of the relevant routes must be presented to the Input Policy Engine. This can be accomplished in a number of ways. The brute-force way is to simply reset the BGP session by using the following command:
clear ip bgp [* | address | peer-group][soft [in|out]]
However, soft reconfiguration or BGP Route Refresh provide solutions that are much more elegant. Refer to Chapter 12, "Configuring Effective Internet Routing Policies," for more details.
BGP Route Maps
Route maps are used with BGP to control and modify routing information and to define the conditions by which routes are redistributed between routers and routing processes.
The format of a route map is as follows:
route-map map-tag [permit | deny] [sequence-number]
The map-tag is nothing more than a name that identifies the route map, and the sequence-number indicates the position that an instance of the route map is to have in relation to other instances of the same route map. (Instances are ordered sequentially.)
For example, you might use the commands demonstrated in Example 11-6 to define a route map named MYMAP.
Example 11-6. Route Map MYMAP
route-map MYMAP permit 10 ! First set of conditions goes here. route-map MYMAP permit 20 ! Second set of conditions goes here. |
When BGP applies MYMAP to routing updates, it applies the lowest instance first (in this case, instance 10). If the first set of conditions is not met, the second instance is applied, and so on, until either a set of conditions has been met or there are no more sets of conditions to apply.
The condition portion of a route map is set by using the match and set commands. The match command specifies criteria that must be matched, and the set command specifies an action that is to be taken if the routing update meets the conditions defined by the match command.
The configuration in Example 11-7 demonstrates a simple route map.
Example 11-7. Route Map Configuration
Router bgp 3 Neighbor 1.1.1.1 route-map MYMAP in ! route-map MYMAP permit 10 match ip address 1 set metric 5 ! route-map MYMAP permit 20 set local-preference 200 ! ip access-list 1 permit 1.1.1.0 0.0.0.255 |
The statements in Example 11-7 subject routes learned from neighbor 1.1.1.1 to route map MYMAP. If 1.1.1.0/24 is advertised from neighbor 1.1.1.1, the metric is set to 5 (as specified in sequence 10), and no further action will occur. Any other prefixes received from the neighbor will also be subjected to route map MYMAP sequence 10. However, because they won't match sequence 10, they continue to sequence 20. Because no match statement is present, the LOCAL_PREF attribute for all prefixes presented will be set to 200.
There are two types of access lists—standard and extended. The main difference is that a standard access list is applied to the source IP address, whereas an extended access list is applied to source and destination or source and network mask. The following global command defines a standard access list; the extended access list will be covered in this chapter at the point it is used in context.
access-list access-list-number {deny | permit} source [source-wildcard]
A standard access list is used to match on a particular source IP network or host, to permit or deny a specific route. Consider the standard access list in Example 11-8.
Example 11-8. Standard Access List
Router bgp 3 Neighbor 1.1.1.1 route-map MYMAP in ! route-map MYMAP permit 10 match ip address 1 set metric 5 ! ip access-list 1 permit 1.1.1.0 0.0.0.255 |
In Example 11-8, access list 1 identifies all routes of the form 1.1.1.X. (Note the inverse mask notation 0.0.0.255 versus the explicit 1.1.1.0/24 in the previous example, which permits only that exact prefix length.) A route of the form 1.1.1.X will match the access list and will be propagated (because of the permit keyword) with a metric attribute set to 5. The logic will then break out of the list of route map instances because a match has occurred. Prefix lists are a newer, more intuitive, more efficient way of filtering routes. We'll discuss these in more detail later.
When an update does not meet the criteria of a route map instance, BGP applies the next instance, and so on, until an action is taken or there are no more route map instances to apply. If the update does not meet any criteria, the update is not redistributed or controlled; it is silently discarded.
The route map can be applied on the incoming (in) or the outgoing (out) BGP updates. Example 11-9 demonstrates the route map MYMAP applied on the outgoing updates toward BGP neighbor 172.16.20.2.
Example 11-9. Route Map MYMAP Applied to Outgoing Updates
router bgp 1 neighbor 172.16.20.2 remote-as 3 neighbor 172.16.20.2 route-map MYMAP out |
Prefix Lists
As discussed in Chapter 6, the prefix list is a newer, more efficient, more intuitive way to identify routes for matching and filtering of routing protocols. Let's take a moment to provide some prefix list configuration guidelines.
In addition to being a much more intuitive interface, and unlike access lists, prefix lists can be updated incrementally. This means that each entry of a prefix list is identified with a sequence number. If you want to add, remove, or modify a given sequence of a prefix list, you only need to specify the sequence number, as discussed in a moment. The primary benefit of this is that, unlike access lists, you need not delete and then reconfigure an entire list in order to make a modification.
Prefix lists are still order-dependent—that is, the first match wins. Like access lists, they allow you to permit or deny the associated prefix. Prefix lists also allow you to filter on both exact matches and ranges of prefixes.
Some configuration guidelines for prefix lists are discussed next. Note that these guidelines should not replace the IOS configuration documentation provided for your specific version(s) of IOS.
Prefix lists can be named by any alphanumeric string and can also be configured with a description. The description is configured like this:
ip prefix-list list-name description text
To add or remove entries from the prefix list, you would use the following syntax:
[no] ip prefix-list list-name seq seq-value deny | permit network/len [ge ge-value][le le-value]
list-name is an alphanumeric string. You could use a standard number scheme, or perhaps something more intuitive:
ip prefix-list CustomerA description <up to 80 characters, spaces permitted>
Table 11-3 documents some examples of filtering specific prefixes.
| Filtering Criteria | Command to Execute |
|---|---|
| Permit exact prefix 192.68.0.0/16 | ip prefix-list sample permit 192.68.0.0/16 |
| Deny a default route | ip prefix-list sample deny 0.0.0.0/0 |
| Permit all | ip prefix-list sample permit 0.0.0.0/0 le 32 |
| Deny all | ip prefix-list sample deny 0.0.0.0/0 le 32 |
| Deny /25+, in all address space | ip prefix-list sample deny 0.0.0.0/0 ge 25 |
| In 192.68.0.0/24, deny /25+ | ip prefix-list sample deny 192.68.0.0/24 ge 25 |
| Permit all addresses from /8 to /24 | ip prefix-list sample permit 0.0.0.0/0 ge 8 le 24 |
Note that sequence numbers are not included in Table 11-3. If you do not specify a sequence number, the initial sequence value will default to 5 and will be incremented by 5 each entry thereafter unless explicitly specified otherwise.
To perform incremental configuration of a prefix list, you simply specify the sequence number of the entry you want to add, remove, or modify. For example, consider the prefix list in Example 11-10.
Example 11-10. Sample Prefix List
ip prefix-list sample seq 5 permit 1.1.1.0/24 ip prefix-list sample seq 10 permit 2.2.2.0/24 ip prefix-list sample seq 15 permit 3.3.3.0/24 ip prefix-list sample seq 20 deny 0.0.0.0/0 le 32 |
The sample prefix list in Example 11-10 permits 1.1.1.0/24, 2.2.2.0/24, and 3.3.3.0/24, and then denies all other routes. Let's assume that you now want to permit 4.4.4.0/24 also. Configuring the following entry would accomplish this:
ip prefix-list sample seq 18 permit 4.4.4.0/24
This entry would result in a prefix list that looks like Example 11-11.
Example 11-11. Prefix List After Permitting 4.4.4.0/24
ip prefix-list sample seq 5 permit 1.1.1.0/24 ip prefix-list sample seq 10 permit 2.2.2.0/24 ip prefix-list sample seq 15 permit 3.3.3.0/24 ip prefix-list sample seq 18 permit 4.4.4.0/24 ip prefix-list sample seq 20 deny 0.0.0.0/0 le 32 |
Now let's assume that you want to deny the 4.4.4.0/24 as well. The following command would accomplish this:
no ip prefix-list sample seq 18
The prefix list would look like Example 11-12.
Example 11-12. Prefix List After Denying 4.4.4.0/24
ip prefix-list sample seq 5 permit 1.1.1.0/24 ip prefix-list sample seq 10 permit 2.2.2.0/24 ip prefix-list sample seq 15 permit 3.3.3.0/24 ip prefix-list sample seq 20 deny 0.0.0.0/0 le 32 |
As you can see, the incremental update capabilities of prefix lists provide a significant advantage over traditional access lists. Although most of the examples in the remainder of this chapter will continue to use access lists versus prefix lists, real-world examples of prefix lists will be supplied in the next chapter.
Identifying and Filtering Routes Based on the NLRI
To restrict the routing information that the router learns or advertises, you can filter based on routing updates to or from a particular neighbor. The filter consists of a prefix list (or access list) that is applied to updates to or from a neighbor. In Figure 11-2, RTD in AS2 is originating network 192.68.10.0/24 and is sending it to RTF. RTF will pass the update to RTA via IBGP, which in turn will propagate it to AS1. By doing so, AS3 could become a transit AS, advertising reachability of network 192.68.10.0/24.
Figure 11-2. Identifying and Filtering Prefixes
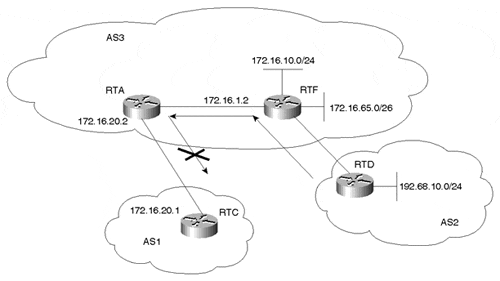
To prevent this situation, RTA will configure a filter to prevent prefix 192.68.10.0/24 from propagating to AS1. Example 11-13 demonstrates the following configuration for RTA to prevent prefix 192.68.10.0/24 from propagating to AS1.
Example 11-13. RTA Prefix Filter
router bgp 3 no synchronization neighbor 172.16.1.2 remote-as 3 neighbor 172.16.20.1 remote-as 1 neighbor 172.16.20.1 prefix-list 1 out no auto-summary ! ip prefix-list 1 seq 5 deny 192.68.10.0/24 ip prefix-list 1 seq 10 permit 0.0.0.0/0 le 32 |
In Example 11-13, the combination of the neighbor prefix-list router configuration command and prefix list 1 prevents RTA from propagating prefix 192.68.10.0/24 to AS1. The prefix list portion of the configuration identifies the prefixes, and when used in conjunction with the BGP neighbor subcommand, it applies the filtering on the outgoing updates associated with the specified neighbor (note the out keyword). Note that prefix list 1 ends with a logic that permits all updates (permit 0.0.0.0/0 le 32). When you use prefix lists or access lists for filtering, if no action is specified at the end of the access list statements, the logic of "deny everything else" applies implicitly. This means that anything that did not match any of the preceding instances will be denied. This is why it is important to specify the default action; in this example, 192.68.10.0/24 will be denied, and everything else will be allowed. For this reason, explicitly configuring the "deny everything else" – if you actually intend to– could save you some headaches down the road.
Although it isn't demonstrated here, the best current practice (if possible) is to supply a list of routes that will be permitted and then configure an explicit deny. This assures that you won't accept routing information from a peer if it's not included in the filter. Of course, this might not be practical if a large number of routes are learned from the peer.
Route maps (which reference access lists or prefix lists, and perhaps other policies) could have been used to filter updates in the previous example. The direct prefix list method was chosen to give you different options for filtering.
Using access lists to filter supernets or ranges of updates is trickier. Assume, for example, that RTF in Figure 11-2 has different subnets of 172.16.X.X, and you want to advertise an aggregate of the form 172.16.0.0/16 only. The following standard access list:
access-list 1 permit 172.16.0.0 0.0.255.255
would not work because it permits more than is desired. The standard access list looks at the source IP address only and cannot check the length of the network mask. The preceding access list will permit 172.16.0.0/16, 172.16.0.0/17, 172.16.0.0/18, 172.16.1.0/24, and so on.
To restrict the update to 172.16.0.0/16 only, you have to use an extended access list of this form:
access-list access-list-number {deny | permit} protocol source source-wildcard destination destination-wildcard | mask mask-wildcard
This defines an extended access list that matches on a source destination or a source mask tuple to permit or deny a specific routing update. The access list number falls between 100 and 199. In the case where the protocol is IP and you are checking on a source/mask tuple, this would translate into the following:
access-list access-list-number permit ip network-number network-do-not-care-bits mask mask-do-not-care-bits
For example:
access-list 101 permit ip 172.16.0.0 0.0.255.255 255.255.0.0 0.0.0.0
A 0 is an exact match bit, and a 1 is a do-not-care bit.
The preceding extended access list indicates that aggregate 172.16.0.0/16 is to be sent only because you have indicated that the mask should match 255.255.0.0 exactly. An update of the form 172.16.0.0/17 will not be allowed.
You could also accomplish this a couple of other ways. For example:
access-list 101 permit ip host 172.16.0.0 host 255.255.0.0
Or you could use a prefix list:
ip prefix-list 1 seq 5 permit 172.16.0.0/16
Remember that an ending implicit deny is assumed unless it is explicitly overridden.
Identifying and Filtering Routes Based on the AS_PATH
Filtering routes based on AS_PATH information becomes handy when filtering is needed for all routes of the same or multiple ASs. It is an efficient alternative to listing hundreds of routes one-by-one, as might be required when filtering on a prefix basis. You can also specify a filter list on both incoming and outgoing updates based on the value of the AS_PATH attribute.
Looking again at Figure 11-2, if AS3 wanted to prevent itself from becoming a transit AS for other ASs, AS3 could configure its border routers RTA and RTF to advertise only local networks. Local networks are networks originated from the AS itself. This can be accomplished with the RTA configuration in Example 11-14; RTF will be configured in the same manner.
Example 11-14. Preventing AS3 from Becoming a Transit AS for Other ASs: RTA Configuration
router bgp 3 no synchronization neighbor 172.16.1.2 remote-as 3 neighbor 172.16.20.1 remote-as 1 neighbor 172.16.20.1 filter-list 1 out no auto-summary ip as-path access-list 1 permit ^$ |
In Example 11-14, the AS_PATH access list 1 identifies only updates that originate from AS3. The filter list works in conjunction with the AS_PATH access list to filter the updates. In this example, the filter list is applied on the outgoing updates (note the out keyword). The regular expression ^$ indicates an AS_PATH that is empty. The caret symbol (^) indicates the beginning of the AS_PATH, and the $ symbol indicates the end of the AS_PATH. Because all networks originating from AS3 have an empty AS_PATH list (recall that the local AS number is not attached to the path until the route is passed to an EBGP peer), they will be advertised. All other prefixes will be denied.
If you want to verify that your regular expression works as intended, use the following EXEC command:
show ip bgp regexp regular-expression
The router displays all the paths that match the specified regular expression. Refer to Table 6-4 in Chapter 6 for a list of regular expression characters with special meanings.
Note
Route maps (referencing AS_PATH access lists) also could have been used to filter updates in the previous example. The filter list was chosen to give you a different option for filtering.
