CHAPTER 12
Finding Your Suspect
In this chapter, we will examine techniques you can use to track and, hopefully, locate your suspect. We discussed clustering addresses and following transactions in Chapter 10, “Following the Money,” but how can you identify a resource on a blockchain that is identifiable so that you are able—with the proper legal authorities or using open-source techniques—to obtain information on a suspect? This chapter will teach you about IP address tracing as well as its limitations, tracking to a service provider such as a currency exchange, and searching on the so-called dark web using Tor.
When investigating movement of funds on a cryptocurrency, it is easy to hit a dead end. Even with the techniques discussed in this chapter, there will be times when you will need to be patient and just watch and wait for coins to move to a traceable end point, such as a trader or exchange.
Tracing an IP Address
I sat in a presentation in 2017 where the law enforcement specialist in Bitcoin presented, among other things, a number of possible security vulnerabilities and methods for identifying users on the blockchain. Included in this list was a review of the “traceability of the IP addresses found on the Bitcoin blockchain.” It was one of those uncomfortable moments when you are willing someone to stop talking because they are very wrong in what they are saying, and you feel rather embarrassed for them. Simply put, the Bitcoin blockchain does not record any IP addresses.
His mistake came from a misunderstanding about information that blockchain.info records when it detects trades on the blockchain. Blockchain.info watches a large number of Bitcoin nodes, and when it sees a transaction for the first time, it records the IP address in its database. You can see an example of this in Figure 12-1.

Figure 12-1: Relay address on blockchain.info.
If you would like to browse to this record on blockchain.info, open a browser and go to http://bit.ly/2he4Pbr.
Although much of the data provided here by the website is raw information from the blockchain, the IP address is specific to its own database. Does this IP address relate to the user who sent the transaction? Perhaps, but it is unlikely. Bitcoin uses a peer-to-peer network structure to facilitate the efficient dissemination of transactions to all Bitcoin nodes around the world. When Alice creates a transaction, for example, it is sent to the peers recorded in her Bitcoin wallet software. Those peers transmit the transaction to their peers, and the process continues until every Bitcoin node is aware of the transaction. Blockchain.info watches a large number of nodes, and when one of those nodes transmits a transaction for the first time, it is that IP that is recorded. This is depicted in Figure 12-2.

Figure 12-2: Bitcoin peer-to-peer network.
Alice is using IP address 212.58.21.53 and creates a transaction. This is broadcast to her peers, one of which blockchain.info is monitoring. This relay node is using IP address 172.58.42.44, and this is the IP that blockchain.info records in its database. Hence, in this instance, the IP address recorded is not the originator of the transaction.
However, it is possible that the originator of the transaction was the IP address that blockchain.info saw—the problem is, there is no way of knowing.
Since the erroneous conference, I have seen other work done by researchers and even journalists where they have used the IP address in blockchain.info to “identify” and even expose what they believe to be the user of a particular Bitcoin address. But is this a dead end, or can we get closer to the IP address that generated a transaction and hence connect it to a Bitcoin address?
Back in 2011, security researcher Dan Kaminsky gave a talk at the Black Hat USA conference entitled “Black Ops of TCP/IP.” During that talk, he postulated that if you could scan the Internet for every host with port 8333 open, the Bitcoin Core port, and then watch the transactions flowing from each node in real time, the IP address that first transmitted a transaction would likely be the originator of the transaction. Although this does not take into account thin clients such as Electrum or clients on mobile devices that do not have a full blockchain locally, the reasoning is sound. In fact, even if a person was using a mobile device, the transaction would still be traceable to the server that the client was connected to. In Chapter 13, “Sniffing Cryptocurrency Traffic,” I will show you how to capture all the transactions coming from a full node.
Bitnodes
Using the concept voiced by Dan Kaminsky and others, a researcher named Addy Yeow set up a website named bitnodes.earn.com based on open-source code that he released on GitHub (http://bit.ly/2EHKuVO). The idea was to send getaddr or get address messages, starting from a set of known Bitcoin nodes to recursively map every running Bitcoin node. Bitnodes runs constantly and provides an API (application programming interface) for an investigator to be able to analyze the data. All the data is clustered into timestamps so that you can be very granular in ascertaining what nodes were live at a particular point in time. This means that if you have an IP of a suspect, you are able to use the API to know if it has ever been used as a Bitcoin node at a time in the past, or is currently live. It is also possible to filter IP addresses from a certain ISP or country.
Bitnodes provides a live world map of transactions occurring from IP addresses across the globe (see Figure 12-3). Although this is not exactly a useful investigative tool, it does provide a sense of where Bitcoin is being used. You can find this map by browsing to http://bit.ly/2spitgM.

Figure 12-3: Live map of Bitcoin trades.
The site provides an interface to be able to search for any IP address and get information as to whether it is a Bitcoin node, its time live, its location, and other information (see Figure 12-4). You can find this interface at http://bit.ly/2GfHSvz.

Figure 12-4: List of current Bitcoin nodes.
You can also extract raw data on whether an IP address is currently live in JSON format. You simply browse using the following URL format:
https://bitnodes.earn.com/api/v1/nodes/<IP-Port>/
For example, the following URL will return the data in Figure 12-5:
https://bitnodes.earn.com/api/v1/nodes/208.118.235.190-8333/

Figure 12-5: Metadata from a Bitcoin node.
This data includes the Bitcoin version in use, the time it was last seen (in UNIX time), the city, the country, and the host it relates to (if available).
Bitnodes performs a regular crawl of the Internet and indexes the IP addresses it finds as timestamps using the UNIX time format. You can use the following URL to list the latest snapshots:
https://bitnodes.earn.com/api/v1/snapshots/?limit=100
Note that the end of the URL is limit=100. This specifies the maximum number of snapshots on a single page, and without this, you would only see 10 snapshots at a time. The snapshots are approximately four minutes apart. At the time of writing, the snapshots on page 1 ran from 1518607945 back to 1518569216, or 14 Feb 2018 11:32 UTC back to 14 Feb 2018 00:46 UTC. Each page of 100 snapshots represents around 11 to 12 hours.
To browse to subsequent pages, you add a page number to the URL such as the following:
https://bitnodes.earn.com/api/v1/snapshots/?limit=100&page=2
At the time of writing, there were 455 pages available of 100 timestamps per page, so it can be a little hit and miss to locate the timestamp you are interested in. However, if you are looking for a timestamp from 30 days ago, and you use 12-hours-per-page as an approximate timespan, this will yield around 60 or so pages, which will get you fairly close to what you need. Once you have the timestamp you are interested in, you can adjust the URL to extract this information. For example, if you want to see the IP addresses live at timestamp 1515855919, you need to browse to:
https://bitnodes.earn.com/api/v1/snapshots/1515855919
This will list all the visible IPs at that time, with metadata including the version of Bitcoin being used, the city, and the ISP that the IP address belongs to (see Figure 12-6).

Figure 12-6: IPs and metadata of Bitcoin nodes from a snapshot.
From this list, you can see if your suspect's IP address was live as a Bitcoin node in that time frame.
Using these techniques, you may be able to confirm the following:
- If an IP address is being used as a Bitcoin node
- When the node has been live
- The approximate location of the node either via a lookup on the IP address or via its geolocation metadata
- If an IP address is confirmed as a Bitcoin node, you may be able to use legal means to request user data from the ISP that owns the address
These methods are useful, but Bitnodes provides a different view of the data that can be very useful to an investigator. Having crawled the peer-to-peer network mapping each node it can see, Bitnodes then watches the propagation of blocks and transactions through the network, recording the first 10 IP addresses it has sight of that propagated the transaction or block and then attaching a “first-seen” time to each IP address. This gets you closer to the originator of a transaction.
This capability only works on blocks and transactions over block height 400000 (after Feb 25 2016) and will only work after a block or transaction is more than 8 hours old. The statistics are calculated based on the arrival times formatted as UNIX time in milliseconds from the first 1000 nodes that propagate the data. To use the tool, find the transaction hash (TXID) for the transaction you are interested in. In blockchain.info, that is the long value above the transaction addresses. Copy and paste the TXID into the following URL:
https://bitnodes.earn.com/api/v1/inv/<TX_ID>/
This will list the IP addresses seen propagating the transaction in time order. Try the following URL to return the IP addresses for TX_ID a6350ff0c5a0cebd46518881e0486baa1145ac925fee88450fefd13fa61c31c:
http://bit.ly/2EFoTxn
This returns the following JSON values:
"[2a01:4f8:171:3567::2]:8333",1499717236030],["138.201.33.232:8333",1499717236030],["[2a01:4f8:a0:300a::2]:8333",1499717236036],["88.198.33.138:8333",1499717236036],["23.253.151.73:8333",1499717236041],["148.251.67.240:8333",1499717236061],["73.226.64.145:8333",1499717236065],["52.5.87.242:35131",1499717236069],["52.58.91.193:8333",1499717236075],["68.76.147.138:8333",1499717236081
The first IP address is an IPv6 address, and the second address is an IPv4 address, but both have identical time values with the last four digits being 6030. Although we have looked at UNIX time already in this book, these times are 13 digits long rather than the standard 10 digits and represent the time in milliseconds; hence, you cannot use a standard converter to look up the times. My favorite millisecond converter can be found at http://currentmillis.com. The last four digits represent the seconds and milliseconds and are generally sufficient for network propagation.
These two IPs represent the first nodes to be aware of the transaction, and one of them could be the source of the transaction. Use an IP lookup website to search for the owners of the IPs and the hosts. Try using site-on-ip.com to look up the first IP: 2a01:4f8:171:3567::2. The results show three hosts on this IP:
These sites are tagged as “seeds.” The DNS Seed is a type of DNS server that returns IP addresses of full nodes on the Bitcoin network to enable a new node to find peers to propagate with. Hence, you can discern that this IP is likely not the originator, but an early peer. If you look up the details on the second IP, 138.201.33.232, you find the following hosts:
dnsseed.koin-project.comdnsseed.litecoinpool.orgdnsseed.litecointools.comdnsseed.ltc.xurious.comseed.bitcoinstats.comx9.dnsseed.thrasher.iox9.seed.bitcoin.jonasschnelli.chx9.seed.bitcoin.sipa.bex9.seed.btc.petertodd.org
You cannot help but notice the similarities.
For example, why are some of the same URLs tagged as hosts on the IP address? These are DNS seeds and normal seeds that point to a list of known Bitcoin nodes should the DNS seeds fail for some reason. These seeds are hard-coded into the Bitcoin source code in the file chainparams.cpp. (This source code is available at http://bit.ly/2HgPzmA.) In 2018, the seed values in the source code are
seed.bitcoin.sipa.bednsseed.bluematt.mednsseed.bitcoin.dashjr.orgseed.bitcoinstats.comseed.bitcoin.jonasschelli.chseed.btc.petertodd.org
If you see any of the values listed here, then the IP is a known long-term, reliable Bitcoin node and is a known relay. Of course, it is possible that your suspect may be a long-term relay, but this technique gets you closer to your originator.
Another example can be seen in TX_ID f73ae4a1142a063e78087ae6d9c8dc936f222f2dc8ee477d34d531ffe852790e. The first IP addresses are as follows:
"bitcoinranliixsu.onion:8333",1518391303552"78.129.241.145:8333",1518391303888"171.33.177.9:8333",1518391303889
The first IP is an Onion address from the Tor network: bitcoinranliixsu.onion. If you search for this on the Bitnodes website, you'll discover that Bitnodes knows about it, but it is certainly not a reliable node (see Figure 12-7).

Figure 12-7: Graph of uptime of node.
As you can see, at the time of writing this node is available only 70 percent of the time. It is also not included in the list of “fall-back” nodes available on Tor (which is kept updated at http://bit.ly/2BsRS5E), so although you still can't be sure, it is possible that this could be the originator of the transaction.
The Bitnodes site and API can be very useful to an investigator who has an IP as part of his investigation and wants to know if it was a Bitcoin node as well as for an investigator who wants to know more about a transaction. It is just possible that the IP address could be the originator, and appropriate legal means could be used to obtain location information of the suspect.
Similar sites are available for other cryptocurrencies. For example, litenodes.net (http://bit.ly/2CmkrOW) is an attempt to find the IP addresses of all Litecoin nodes on the network, and ethernodes.org attempts to map all Ethereum nodes. Interestingly, Ethereum has approximately 25,000 nodes in comparison to Bitcoin's 11,000.
Other Areas Where IPs Are Stored
Although it can be difficult to trace an IP address from a transaction, plenty of other places exist where IP addresses can be stored that are related to blockchain activity. Here are some examples:
- Online Stores A suspect may purchase goods or services at an online store and pay using a cryptocurrency. In order to ship goods, the store will have to take personal details, which may include a home address, phone number, and other personal data. This is usually stored in a database and will be related to the cryptocurrency address that was used to purchase. If you can identify the store on the blockchain, you may be able to use legal means to request the release of information about the purchaser. This information should also include access to the weblogs and any other logging or analytics information that could help identify their IP address and also track their movements on the website.
- Exchanges Aside from sites such as localbitcoins.com, which allow the purchasing of coins for cash “on the street,” most purchases of cryptocurrencies will be via exchanges. Exchanges are becoming increasingly regulated and are required to gather significant information on the user, which will include data such as his or her home address as well as financial information such as bank details and credit card details. If an exchange can be identified, then legal means can be used to request the information including any IP address logs that may exist.
- Thin Clients Although I have focused on clients such as Bitcoin Core thus far in this book, many so-called thin clients do not store a complete copy of the blockchain, but instead connect to servers that handle the communication with the blockchain for them. The servers are called SPV (Simplified Payment Verification) servers, which handle the verifications of trades on the blockchain. These servers usually retain the IP address of the user connected to cryptocurrency addresses they use. In fact, the Bitcoin thin client Electrum uploads all the addresses from a user's wallet to the SPV server. Again, significant information can be obtained through legal means.
- Online Wallets Many exchanges also provide online wallets; however, a number of providers just provide secure storage of your private keys in the cloud. Most of these services will retain the IP address of the logged-in user, which can be requested.
Is the Suspect Using Tor?
If you have identified an IP address, it can be useful to ascertain if the address owner is using the Tor network to obfuscate his or her true location. As a concept, Tor has been around for over 20 years; however, the code was only made available publicly by the U.S. Naval Research Lab in 2004. The model is fairly simple—a user connects to one of a large pool of entry nodes, which then bounce your data through various relays before routing to the Internet at large through an exit node. All the nodes are provided by volunteers, although anecdotally, governments are thought to run many of the exit nodes. The system effectively prevents somebody watching your Internet activity and provides a good level of anonymity.
Because it is not supposed to be possible to trace data traffic from an exit node, back through a random series of relays, through an entry node, and back to the originating IP address, the addresses of Tor nodes can be made public. Tor manages a list of all nodes, which is available online and enables you to check the list to see if a suspect's IP is actually a Tor exit node.
Browse to https://torstatus.blutmagie.de. This site maintains a list of all Tor nodes currently active. The onscreen list provides a table of the router name, the hostname, the type of nodes it provides, and other information (see Figure 12-8).

Figure 12-8: List of Tor nodes.
If you look at the top of the web page, you are able to download a series of CSV files of different nodes. One is called “CSV List of ALL Current Tor Server Exit Nodes.” If you download this file, you will see that it contains a list of every current exit node. You can now simply search the list to see if your suspect's IP address exists in the list.
The problem with this is that Tor nodes change all the time, so the IP address you have may not be a live exit node on the day that you download the list. To help with this, Tor maintains a historical list of every exit node that was live during a particular month. This means that if you have an IP address, perhaps one that was used by a suspect at an online store, you can check the date that the IP address accessed the store and then locate the right Tor list and check to see if that address exists.
To find the historical lists, browse to http://bit.ly/2EJZbYE, where you will find monthly lists of exit nodes that stretch back as far as February 2012.
Is the Suspect Using a Proxy or a VPN?
If you obtain an IP address using any of the methods previously described, as with Tor, it can be useful to know if the suspect is using a proxy or a VPN (Virtual Private Network) to access the Internet and hide his or her true IP address.
A proxy is a remote server that acts as a jumping-off point to the Internet. This is usually effective at hiding a user's IP address and can sometimes be encrypted between the user and the proxy. Unless a proxy is run by the user or a trusted third party, public-type proxies should not be trusted as secure. As public proxies are often run by those wishing to hide their traffic and provide the capability to others, it can be difficult to obtain user logs via legal means.
A VPN creates an encrypted tunnel from the user to a remote server before breaking out onto the Internet. A VPN can be set up by a user, but this normally means paying for server space with an ISP and leaving a trail of information that can be requested. Many users will make use of a VPN provider to buy access to VPN jump-off points around the world; however, once again, sign-up procedures and logging of true IPs can mean there is still information that can be requested from the VPN provider.
How can you work out if an IP address belongs to a VPN provider or proxy? My preferred approach is to make use of the services of ipqualityscore.com. The site provides a number of services designed to help prevent fraud, but these can be useful to the investigator. If you click the Proxy Detection link, you are able to try out the service free of charge. Simply enter the IP address of your suspect, and the site will attempt to ascertain whether the IP is from a proxy or VPN server (see Figure 12-9). In my testing, I have found it to be extremely accurate.

Figure 12-9: Lookup of an IP address with and without a VPN.
Ipqualityscore.com also enables you to register for free and gain access to 5000 free lookups per month—in fact, the site is quite reasonably priced at just $50 for 50,000 lookups per month. This enables you do batch lookups of a list of IP addresses. Once you are registered and logged in, browse to http://bit.ly/2o14IAo, and you can then easily upload a CSV file containing a list of IP addresses to check (see Figure 12-10).

Figure 12-10: Uploading a CSV file.
Once you have identified if an IP address comes from a proxy or VPN, there is the possibility of requesting information or logs from the service provider.
Tracking to a Service Provider
Following transactions through the blockchain manually or using visualization tools is a vital skill, but an investigator needs to translate that work into real-world data, a name, IP address, or other identifiable information. Thus far, this chapter has focused on finding or researching IP addresses; however, if you can link transactions to a service provider of some type, then legal measures can be used to request stored information on a customer. When I use the term “service provider,” it should probably be qualified to a legitimate service provider. A store located on the Tor network that sells drug-manufacturing equipment and only takes Bitcoin is unlikely to respond to your request for customer information, but many legitimate providers will often respond positively where a legal approach is made. A service provider could include, but is not limited to the following:
- Exchange
- Coin-mixing company
- Legitimate trader
- Thin-client server administrator
Currency exchanges are an excellent resource for information if you can identify that coins were either purchased from a particular exchange or if coins were cashed out to a fiat currency using an exchange. Getting cryptocurrency coins without leaving a trace has become increasingly difficult, especially Bitcoin, because mining would often be a way of acquiring coins with little or no attribution. However, Bitcoin now requires specialist and expensive hardware to achieve any success. Coins could be acquired by trading in person with an existing coin owner or using sites such as www.localbitcoins.com. Recently, ATMs have appeared that enable you to acquire coins anonymously, but it will be interesting to see if and when countries pass legislation to make acquiring currency without a trace increasingly difficult.
Using a currency exchange to purchase coins is extremely popular, but most of the major exchanges are being regulated and require significant personal and financial information to complete registration and enable purchasing. Some wallet sites now actively recommend localbitcoins.com as their preferred purchasing route.
If you can follow transactions through a blockchain and identify a service provider of some type, then you can use legal means to request data and acquire real-world data to help your investigation. But how do you identify a service provider? It's not possible track “through” an exchange, because the coins that come out of an exchange are different from the ones that are deposited. Imagine taking a $5 bill to a bank and depositing it. If you go back the next day and ask for $5, the teller will not go and get your original bill; instead, she will provide you with the same value from a float. Exchanges and mixers work in a similar way. When a coin is transacted with an exchange, addresses are aggregated, and the majority of coins stored are kept in an offline (cold storage) wallet for safekeeping. The exchange will keep a float in an address, and as people purchase coins, they will transfer the required amount from the float and accept the rest back as change.
By far the best way to identify clusters such as exchanges, mixers, and major online traders is by using a commercial tool such as Elliptic or Chainalysis. A similar task can be achieved manually, but it will likely take longer and require more resources.
The first thing you need to be able to do is cluster addresses so that you know addresses owned by the same user, group, or organization. I discussed these techniques in detail in Chapter 10, but in simple terms, you can infer that the following addresses have the same owner:
- Input addresses belong to same owner
- Input addresses used with other input addresses in other transactions
- When you compare the input and output values of changed addresses:
- Payment from a multisig address starting with a
3has a3change address - Payment to a
3address from a1address has a1address as its change address
- Payment from a multisig address starting with a
Once you are confident with manually clustering addresses, you can make a micro-transaction to the service provider. If you then withdraw the coin value you deposited, most exchanges will expose a large number of input addresses used by the exchange and also expose a change address. You can then use clustering methods to build a picture of the exchange. If you do this regularly and to many of the primary exchanges, you will begin to see repeated addresses and can accurately identify the address as being owned by a particular service provider.
This process is often evident on the blockchain where an exchange has an address with a large float ready to transact coins with users who buy them. For example, let's say the exchange puts 100 bitcoin in an address. A person buys 0.5 bitcoin, and the exchange transacts all 100 bitcoin, with the exchange taking back 99.5 as change. Next, a person buys 1 bitcoin. The exchange uses the change address to send that person the 1 bitcoin and takes 98.5 bitcoin back to another change address. In reality, the transactions will be to multiple customers in a single transaction, but you will still see the large amount sent back as change each time. This process is called unpeeling. You can see a good example of this if you browse to http://bit.ly/2GrxaD1. This will load a record of a transaction with one input of 8892 bitcoin and with 14 outputs. The final output is for 8890 bitcoin. Is this the change address? If you are sharp-eyed, you will notice that this output address is the same as the input address—this alone shows that it is the change address (see Figure 12-11).

Figure 12-11: Large transaction with change address back to itself.
Next, click the View Tree Chart link and follow the output starting 17A16Q by clicking it. If you keep clicking this address, you will witness transaction after transaction as coins are “sold” to customers and the balance returned to itself. This is depicted in Figure 12-12, but I recommend that you try this for yourself if you can because it's more impressive on screen.

Figure 12-12: Unpeeling a transaction tree with a reducing value of the primary address.
When you see patterns like this, you are almost always dealing with an exchange. If you now take the address 17A16Q, you can do a lookup with either www.bitcoinwhoswho.com or www.walletexplorer.com. This will identify the address as belonging to Poloniex.com. You have now identified an address used by the Poloniex exchange. If you are researching a Bitcoin address, and the input to it is 17A16Q …, you will know that the source was the Poloniex exchange, and you can now make a legal request for information.
Also, a large number of addresses in each of the vast number of transactions from 17A16Q contain coins originating with Poloniex. This is a good start in building a database to identify exchanges. Of course, it's a very limited start, but this demonstrates how you can identify an exchange by its pattern and then extract ownership data and addresses belonging to clients reasonably easily.
It can be useful to know what crypto and fiat currencies an exchange supports. An excellent site is www.coinlib.io/exchanges, which details each exchange and the currencies that are supported. Searching for Poloniex shows that they support a wide range of cryptocurrencies but only support U.S. dollars for payment and cashing out (see Figure 12-13).

Figure 12-13: Currencies supported by Poloniex.
Tracking transactions back to a store or trader can sometimes be more complex, but on many occasions, the trader will publish an address. It is then straightforward to do some online open-source research on the address to find out more about it. Once you have an address or addresses used by a trader, you can use clustering techniques to find other addresses and then extract all the inputs to those addresses to begin to identify customers. It is extraordinary how often you can find an address that belongs to a trader. Next, you extract all the input addresses, perhaps using Maltego as described in Chapter 11. Many of the input addresses belong to customers, and a good number of those will be just one hop from an exchange where they bought their bitcoin or other cryptocurrency.
Considering Open-Source Methods
The blockchains of most currencies are by definition open source. Their underlying code is usually publicly available—for example, the Bitcoin code can be obtained by browsing to https://github.com/bitcoin. The open-source nature of the code means that researchers can examine it and find security problems, improve it, or fork it to a new version. But, this isn't the type of open source I'm talking about.
Open-source intelligence gathering is the ability to search publicly available information for both explicit and implicit information about a subject. In Chapter 8, “Detecting the Use of Cryptocurrencies,” you learned how to use HTTrack to download a website and then use a search tool such as Agent Ransack to use a regular expression to find Bitcoin addresses. But, you cannot use regular expressions to search the Internet, so you have to be clever in the way you construct search terms.
I teach a class on advanced open-source intelligence gathering, and one of the first things I tell students is that Google is there to stop you from searching the Internet. This is often met with opposition, but you can test this yourself by browsing to Google and searching for the name of a movie that is currently showing at theaters. Google will generally display the movie times at your local cinema. But what if you were not looking for that? What if you were looking for the movie's cast, where it was filmed, or even showings in another city? Google hasn't ignored these possibilities, but its algorithm has looked at your search, considered where you are geographically, and has given you the information that previous searchers have clicked on recently. It's a bit more complex than that, but it means that when you are searching Google's vast index for a restaurant called “The Eatery,” it somehow manages to give you the information about the café nearest to you rather than one on the other side of the world.
If you are searching as part of an investigation, you need to form searches to acquire the information you actually want rather than what Google thinks you want. To do this, there is a series of search modifiers that you can use. For example, if you know that your suspect has a Facebook page, is called Mario, and accepts bitcoin donations, you can use the modifier site: to just search the site that you want. For example, try the following search in Google:
- site:facebook.com Mario bitcoin donations
This search will only look at pages from Facebook, because you invoked the site: modifier. You should be able to find the page depicted in Figure 12-14.
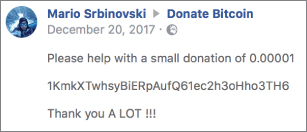
Figure 12-14: Results of searching using the site: modifier.
Here are some other useful modifiers:
intitle:searches for a word in the web page title.allintitle:searches for all search terms in a page title.intext:searches for pages with a single search term.allintext:searches for pages with all of the subsequent search terms.inURL:searches for a word in the URL of the page.allinURL:searches for all the search terms in a page URL.filetype:searches for a specified file type (such as.doc,.pdf,.txt, or whatever file type you specify after the colon).
Using these modifiers, you can get more control over your searches to find information related to your suspect.
Accessing and Searching the Dark Web
The dark web isn't actually dark—it is just the name that journalists have locked onto because it sounds mysterious and dangerous. The so-called dark web has many names such as the deep web, darknet, and although a little inaccurate, often just Tor, which is the primary method of accessing this information. Dark web sites are simply Internet-based resources such as websites, forums, IRC chat channels, and others that are not accessible using a standard browser and cannot be seen using normal search engines.
Being able to access this area of the Internet is vital for an investigator because, although the dark web is not all about criminality, many sites that sell services or products that are illegal or, at best, not mainstream, exist in this space. Many of these traders use Bitcoin and other cryptocurrencies to accept payment; hence, we need to be able to investigate them effectively.
I often speak to investigators that are nervous about getting online and browsing the dark web because they are afraid of viruses, hackers, mistakenly downloading illegal material such as child images, and many other concerns. Unfortunately, they are right to be nervous, but this should not be an excuse to avoid travelling to the online version of the rough side of town.
You can take precautions by using a virtual machine to browse rather than your primary computer and by being very cautious where you click and what you download. Of course, these concerns will differ for a law enforcement officer and a civilian investigator, as laws may apply differently depending on what you are investigating. A law enforcement officer may be looking for illegal images, while a person investigating ransomware may be actively trying to be infected in order to be able to examine the malware.
When it comes to investigating traders, the investigator is primarily looking for what services or products are being offered and any published cryptocurrency addresses. If a shopping-cart type of system is being used, an investigator may want to make a purchase to be able to follow the payment on the blockchain and see where it ends up.
Being able to browse the dark web is very easy. Numerous software tools can help you, but perhaps the easiest method is to download and install the Tor Browser from torproject.org. The URL you need is http://bit.ly/1jdsLFC. Alternatively, you can Google for Tor Browser, and it is generally the first result.
Once you have installed the browser, run it, and you will see that it looks very much like a standard Firefox web browser. On the left side is a small icon that looks like a green onion—click this icon to change security and connection settings for controlling your access to the network (see Figure 12-15).

Figure 12-15: Options on the Tor Browser.
One of the largest search engines on the dark web is called Torch (see Figure 12-16). You can access it by typing http://xmh57jrzrnw6insl.onion into the address bar of your Tor Browser.
Figure 12-16: Torch search engine.
Try searching for Laundry or Mixer to find Tor-based services that will offer to store and “launder” your coins by joining and splitting them. A good example is OnionWallet, which you can browse to at http://laundryfju74rt34.onion/, or EasyCoin at http://walletbjvdecnjgp.onion/l/login.php.
It's a good idea to get used to working in this environment. It can feel very different from the standard web—sites are often down, connections fail, and the sites feel very basic and not dissimilar to the Internet of the 1990s. However, once you have spent some time browsing the environment, it will quickly feel like home. I suggest that you spend some time searching for the following items:
- Bitcoin addresses
- Aliases
- Sites
- Forums
- Chat sites
A great resource for knowing what sites are available on the dark web is www.hunch.ly. In addition to the Hunchly software sold at the site (which is excellent OSI-management software) the site provides a daily spreadsheet of what dark web sites are live, what is new, and what is currently down (see Figure 12-17). I highly recommend it. If you browse to https://darkweb.hunch.ly, you can request the daily e-mail from there.

Figure 12-17: Dark web spreadsheet at hunch.ly.
Investigators need to be able to confidently search and browse on the dark web in order to follow traders and services that exist in that online space.
Getting real-world information on a trader on the dark web or a customer using its services is certainly difficult. There have been some successes by using the following techniques:
- Using OSI techniques to search on the standard Internet for names and aliases used by traders on the dark web
The same aliases as are found in the dark web often crop up on World Wide Web–based forums, gambling sites, and other web resources that may provide an easier path to identifying the person.
- Monitoring addresses
Traders may advertise their cryptocurrency address on their dark web site. Monitoring the address for payments made to other addresses or traders may lead you to a legitimate trader or service such as an exchange that may enable a legal request for information.
- A law enforcement department or team with appropriate legal warrants exploiting vulnerabilities in the code of a dark web site to extract information
This could include exposing standard IP addresses, downloading databases, or providing remote access to the server.
- Purchasing goods from a dark web site to reveal other information
One trader even put a return address on a package containing the ordered goods.
- Using false identities to join and engage with dark web forums and chat groups to become trusted
This may eventually result in real-world information being shared. This takes skill, planning, and care.
Detecting and Reading Micromessages
The first transaction done by Satoshi Nakamoto on Bitcoin carried a message hidden in the code of the transaction that read, “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.” This demonstrated an ability to carry micromessages within the structure of a transaction and could be useful in identifying the owner of an address.
Due to the high fees of Bitcoin at the present time, sending these types of messages is not sustainable as a widely used messaging system. However, any message encoded in a transaction exists on the blockchain forever and hence is a sound way of making a statement that literally lasts until Bitcoin is no more. Although Bitcoin is too expensive as a communication tool, other cryptocurrencies with lower transaction fees could appear as a viable solution—perhaps as a blockchain-based Twitter-type tool.
In fact, because we can encode anything into hexadecimal and inject it into a transaction, it is possible to place any type of file, whether a document or an image, onto the blockchain, and it can never be removed. Good examples of this are files from Wikileaks. Although they're not easy to extract, if you browse to transaction ID 6c53cd987119ef797d5adccd76241247988a0a5ef783572a9972e7371c5fb0cc or via http://bit.ly/2Hh73zj, you will note a series of outputs that cannot be decoded. This forms code for a download tool that can then be used to extract the raw Wikileaks files from the blockchain (see Figure 12-18).

Figure 12-18: Wikileaks files downloaded from Bitcoin.
I have included this section in this chapter about finding your suspect, because micromessages from addresses you have identified could contain information that will be useful in helping you make a real-world identification. For example, there could be a message starting with a real name (for example, “Hi Mike”) or containing a credit card number, or myriad other possibilities.
A number of different ways exist to embed a message into a transaction, but I will cover just one primary method here. Creating a message to embed into a transaction can be done very easily by following these steps:
- Construct a message that is less than 20 characters long.
- Encode the message into hexadecimal. You can use the tool available at http://bit.ly/2nqHKBM.
- Convert the resulting hex string into a Bitcoin address. You can use the tool found at https://blockchain.info/q/hashtoaddress/<Your_Hex_Value>.
- Insert the hex value you created at the end of the URL.This will generate a Bitcoin address. Send a few satoshis to the address, and the transaction will appear on the blockchain with your message to the world encoded in it.
To see a good example of this, browse to http://bit.ly/2BDI0lT. This transaction has many very small inputs with all but the change address unspent. This is a clue that this may be a micromessage. Scroll down to the Output Scripts at the bottom of the page as shown in Figure 12-19.

Figure 12-19: Output scripts containing a message.
Copy each block of hex between the square brackets from each output script into the hex box in the tool at http://bit.ly/2nqHKBM. Figure 12-19 shows the hex you need to copy with the first block starting 22339. Once copied into the hex editor it reveals the start of the message “There is not.” Work your way through each hex block to eventually reveal the entire message.
If you would like to watch messages and images being encoded to the Bitcoin blockchain in near real time, browse to Cryptograffiti at http://bit.ly/1mn8H5h. You can see some of my recent favorites in Figure 12-20.

Figure 12-20: Messages on the blockchain.
If you see a transaction where the outputs are very small values and all but one of them are unspent, it is a possible micromessage.
Ethereum has an add-on called a Dapp in alpha stage that allows encrypted peer-to-peer chat over the Ethereum blockchain. It is interesting in that it enables features such as messages that expire after a period of time, and users that only exist as a non-attributable hash provide completely anonymous communications. For example, a journalist could anonymously publish a hash for a whistle-blower to communicate with. Both sides would remain anonymous and protected.
If you can identify messages used by a suspect, and you see odd transactions such as previously described, this may be a message that contains useful information.
Summary
In this chapter, we have looked at ways by which you can take cryptocurrency addresses and use that data to try to locate your suspect in the real world. We have considered methods where you can use IP addresses to try to find the source of a transaction, learned ways you can track transactions to or from a service provider, and how you can find information using open-source methods including on the dark web.
Finding a suspect in the real world from blockchain transactions can be very challenging, and unless you are able to make legal requests for information from service providers, it can be almost impossible. However, the techniques you learned in this chapter can help you to make sense of the data on the blockchain and try to relate it to real-world services.
You also learned about micromessages. Although they're not widely used at present, you can use them to send and receive attributable messages.
Some of these techniques are complex and need to be practiced. Take your time and document everything.
