CHAPTER 14
Seizing Coins
In this chapter, we will consider when and how to seize cryptocurrency assets. Police forces, government agencies, and private investigation firms are currently debating the correct procedures for seizure either at a live crime scene or later during an investigation. The processes in this chapter represent my recommendations but should not be interpreted as the only way to proceed in what is fundamentally a legal rather than a technical decision.
This entire book has been aimed at a technical investigator, but cryptocurrencies are changing the landscape of a financial investigation. Traditionally, Financial investigators (FI's) are long-time police officers with financial training, or forensic accountants with an eye for the unusual in bank and company account records. To trace the movement of money, investigators work with anti-fraud departments in banks and other financial institutions. They identify, track, and seize proceeds of crime and assets owned by criminals, follow the financial breadcrumbs through complex money-laundering schemes, and monitor the purchase of illegal material.
Financial investigators are a necessary breed of detective, but they are not usually technical. Of course, they will likely be adept with a spreadsheet and understand accounting software, but they are not digital forensics professionals. I was asked by an FI a few months ago how he would produce a seized bitcoin in court. I wasn't sure how to answer, so I spent some time explaining the fundamentals of blockchain technology, and he understood it quickly.
Understanding the blockchain with its inherent cryptography, the ability to carve addresses from computers and phones, and extracting private keys from wallets—all these skills are foreign to the FI. On the flip side, digital forensics professionals tend to have a very particular set of skills but will not necessarily understand financial fraud and money laundering.
For an investigation department to carry out effective cryptocurrency investigations requires a coming together of the FIs and digital forensics departments. In my opinion, this combination needs to include a reasonable level of skill sharing, the FIs need to set aside the traditional mindset of movement of money through banks, and the digital forensics person needs to gain a reasonable understanding of fraud. After a few cases have been completed, the result should be investigators that understand each other, comprehend technical terms, and can effectively apply their skills to this field.
Asset Seizure
Different countries use different terminology for the seizure of assets—some mean the same thing, while others have a variety of connotations. Phrases such as freezing assets, seizing assets, civil forfeiture, assets holding, proceeds of crime appropriation, and cashing out are all terms I hear from different investigators. However, you just need to remember that cryptocurrency is an asset and an asset equals money. Although some specific considerations exist when gaining control of cryptocurrency, there is normally sufficient legislation available in a country's law books to be able to effectively gain access to these assets. For example:
- In the UK, the Proceeds of Crime Act 2002 (POCA), Section 47 (http://bit.ly/2rUpHt8) describes the mechanism for seizure of intangible assets for criminal investigations.
- In the United States, civil forfeiture laws allow police to keep money and other valuables that are “used or intended to be used” to buy or sell property as part of criminal activity.
The same fundamental processes and laws need to apply to the seizure of crypto-assets as they do to standard asset seizure. The differences are only technical.
Cashing Out
One of the biggest concerns about the seizure of cryptocurrency is what to do with the coins once you have control of them. Do you “cash out” and convert the coins into fiat currency or hold them as they are? The issues are significant:
- Secure Storage Unlike traditional currencies where monies can be seized and banked securely, the seized coins remain on the blockchain protected by the new private key or keys. If anyone gains sight of the recovery key or private key string (for example, by taking a photo of it using a smartphone), they could potentially gain access to the funds.
- Insurance Getting an insurance company to insure the assets is extremely difficult because of value fluctuation. What are they insuring and for what value? This is almost impossible to answer with the significant value changes that could exist throughout the duration of an investigation.
- Valuation Fluctuations Investigations and possibly subsequent court cases can last several years. In just over one year, Bitcoin increased from a value of $1000 to around $20,000. Imagine a situation where coins are seized with a value of $20,000, and by the time the suspect is found not guilty, the value has plummeted to $500. Is there a possibility of a lawsuit for the lost value? Who takes responsibility for that?
In some cases, investigators have asked a judge to rule on the question of whether to convert coins to a fiat currency. Perhaps the suspect can be asked if he wants the coins to be cashed out at the current value and placed in a bank account, or just transferred to a cryptocurrency address controlled by the investigator and held until the end of the case. Suspects may distance themselves from the coins, alleging that they have nothing to do with them. This may be true or the suspect may just wish to separate himself from what may be determined to be crime. In this instance, the investigator can decide what action to take without fear of any recourse. Of course, a suspect's story can change as the case progresses.
Some investigation teams have suggested that the best course of action is to cash out coins at the point of seizure as it is possible that copies of a suspects private key may be held by others. This could be done during a live response at a suspect's premises or later in the lab, but either way, preparation and processes are needed. If this is to be done live on a suspect's computer, care needs to be taken to ensure that other evidence on the computer or device is not overwritten.
Cashing out either live on-premises or later in the process requires significant preparation. This preparation should include the following:
- Determining which exchange you will use—The investigation team should set up a relationship with a trusted exchange that knows they are dealing with coins involved in an investigation and will expedite the transaction and perhaps agree to lower fees.
- Understanding the exchange's process for cashing out—The investigation team should have authentication on hand and/or addresses to transfer the coins to.
- Setting up a bank account for the exchange of funds—A bank account needs to be in place to receive the funds from the exchange. Some banks are showing resistance to working with some exchanges, and although this is primarily related to purchasing cryptocurrency, the bank needs to understand the needs of the investigator. As soon as the coins are cashed out, this is now a normal situation for an FI, and the retention and management of the funds can be carried out as usual.
If you have decided to cash out live, the process is fairly simple. As long as you have the exchange and bank accounts in place to accept the money, then the following is the recommended procedure. I recommend always working in pairs to ensure procedural accuracy and reduce errors in copying addresses, for example:
If the decision has been made to seize coins by simply transferring them to another address, then the process is almost identical to the cashing-out process in the previous section, but without an exchange being involved. Seizure and storage of coins requires a little more preparation, as involves the following steps: A number of options exist, but I recommend that you use a wallet that enables you to set up multisig addresses. When funds are transferred from the suspect's wallet to a multisig address with two or more signatories, it means that the funds cannot be moved without the keys of the other keyholders of the address. This protects an investigator if coins go missing. Some online wallet providers also offer highly secure storage of keys offline.
Cashing-Out Process
Seizing Coins without Cashing Out
Setting Up a Storage Wallet
To provide an example as to how you would apply the previous instructions, I'll walk you through the process using the Electrum Wallet software for Bitcoin. Electrum is a thin client and does not require the downloading of the full Bitcoin blockchain, so it can be set up quickly. It is also fairly straightforward to create multisig addresses:
- First, create the storage wallet that will receive the suspect's keys.
- Download Electrum from http://bit.ly/2EKtxXI. Run the software and select New/Restore from the File menu. The software will ask you to name the wallet, and it's logical to use the case number or a similar identifier.
- The next screen will ask what type of wallet should be created (see Figure 14-1). Select the Multi-signature Wallet option, and then choose how many cosigners you require.
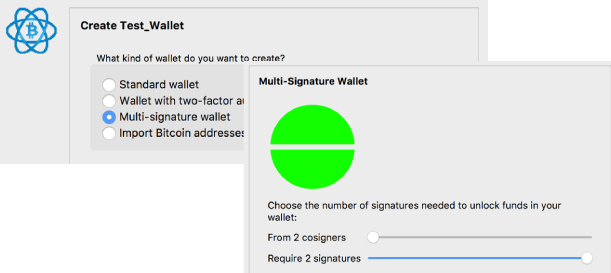
Figure 14-1: Select the Multi-signature Wallet option.
- On the next screen, select the Create A New Seed option, which will generate the 12-word recovery mnemonic code. Electrum then forces you to rekey the code. You cannot copy or paste it here or into any other document—you must manually type it in.
As you can see in Figure 14-2, these steps will generate a Master Public Key that you can give to your cosigners if needed.

Figure 14-2: Seed generation and public key.
- Next, enter the public keys of the cosigners to the address. This will then generate addresses that begin with
3to indicate that they are a multisig address (see Figure 14-3).

Figure 14-3: Enter cosigner address and key generation.
Once these steps are completed, you have an address ready to receive seized coins.
Importing a Suspect's Private Key
You have two ways to move the coins from a suspect's wallet into your new multisig address. The first is very easy using Electrum. From your multisig wallet, select Wallet ![]() Private Keys
Private Keys ![]() Sweep. From this window, you can enter the private key or keys of the suspect, and all the funds managed by the suspect will be moved into your new multisig address (see Figure 14-4).
Sweep. From this window, you can enter the private key or keys of the suspect, and all the funds managed by the suspect will be moved into your new multisig address (see Figure 14-4).

Figure 14-4: Enter private keys to Sweep coins.
This method is quick and efficient but only works if you have been able to acquire the raw private key from the suspect or by dumping it from his wallet. If you have a recovery seed, then a different approach is needed.
You can use the Electrum software wallet again to simply set up a new wallet based on a recovered or seized private key seed from a suspect. It is very important that wallets are kept separate for the obvious reasons of keeping evidence separated so as to avoid any contamination of the evidence or, even worse, assigning coins to the wrong investigation. Electrum can manage multiple wallets, but it is vital to ensure that they are named well to prevent confusion.
Set up another wallet, but this time, choose the I Already Have A Seed option. You will be prompted to enter the recovery words, and the wallet will then complete its set up, contact the blockchain, and provide you with the balance and used addresses. Next, send the entire wallet to your multisig address using the Max button as shown in Figure 14-5. Remember to double-check the address you are sending to and have it checked by another person on the investigative team.

Figure 14-5: Sending the coins to your multisig account.
It is worth remembering that any transaction on the Bitcoin network can take a while to complete. Each block takes around 10 minutes, and to a fair extent, the fee will control the next block that the transaction will be included in. The Fee slider bar can help you decide how much to pay and provides the following options for the transaction blocks to be included:
- Within 25 blocks
- Within 10 blocks
- Within 5 blocks
- Within 2 blocks
- The next block
If you are doing a cash-out at the suspect's computer, you will want to wait until the transaction has confirmed at least one block before leaving. In this case, it may be worth paying the extra fee to have the transaction included in the next block. However, there will be a cost for this that may have to be repaid to the suspect in the event that the assets are returned.
Storage and Security
Assuming that you have decided not to cash out to a fiat currency and allow a bank to care for the funds, you now have to decide how best to secure the storage of the funds. Of course, you cannot actually store cryptocurrency coins because they exist only on the blockchain, but the secure storage of the private key that controls the coins is absolutely paramount. Here are some best practices to follow:
- Each signatory to the multisig address should export the recovery seed by copying the words to a file. Do not save the file.
Remember that the computer you use should be secure because the document could be recovered forensically at a later date. Not saving the document helps, but the temporary file could still be cached to disk or in computer memory.
- Print the document twice.
The printer should be in a secure location because the printed document could be recovered from most modern printers.
- Each document should be stored in a separate safe in different locations.
- Do not store the keys from all multisig accounts together.
To create a backup recovery seed with Electrum, select Seed from the Wallet menu, copy the values, and secure them as described previously (see Figure 14-6).

Figure 14-6: Seed values to copy.
Alternatively, you can electronically store the seed in a file by copying the seed to a document, saving the document, writing to two encrypted hard drives, and storing them separately. I am not a fan of this method, because the saved file can be recovered easily from the computer, even if it's deleted, and hard drives have a horrible tendency of failing just when you need them. In addition, many computers have live snapshots or real-time backups, so even if the file containing the seed was deleted from the primary computer, there is the risk that it will be available on backups. You may feel that this level of security in a police station or secure lab is not needed; however, the lure of easy access to perhaps millions of dollars of hard-to-trace cryptocurrency may be a significant temptation to some.
It is also possible to export the raw private keys, although again, these are written to a file, so I would not recommend this approach for the reasons previously detailed. To export the keys in Electrum select Seed from the Wallet menu, and you can then save each key pair to a CSV file for storage (see Figure 14-7).

Figure 14-7: Exporting the raw private keys.
Again, I do not recommend using stored electronic media to retain these seeds or keys. Cold storage, on paper, stored in several locations is a much better solution. Remember this saying as it pertains to backups: “Two is one and one is none!”
The last thing you should do to maximize security is delete the wallet from the computer you have been using. Of course, you should not delete the suspect's wallet from his computer or any forensic image—which is considered evidence tampering and changing data—instead, you delete the storage wallets you just made. In my “Cryptocurency for Investigators” class, I've had students who were really worried about this step. Deleting anything is generally a bad idea in an investigation, but if the wallets remain on computers, then the possibility exists that someone could exploit that weakness and transfer the coins. However, the students have a good reason to be hesitant—an investigator never wants to lose control of the keys, so double-checking everything first is vital.
The principles are the same for the seizure of other currencies using different software wallets. Although not all of them support seed code words, most enable the dumping of the private key, so you can follow the same basic steps and end up with cold storage of the private keys or backup seeds.
Seizure from an Online Wallet
Many companies offer online wallets, including specialist high-security storage companies and exchanges that offer wallet services. The blockchain.info site that has been referred to a significant amount of times in this book is one of these companies.
Seizure of funds can be achieved in the following ways:
- Make a legal approach to the company requesting either the release of cryptocurrency funds or access to the suspect's account. Some companies say that they have no way of accessing an account, and the only solution is to go through a password-recovery process. However, a password-recovery process usually includes an e-mail verification step, and you should have access to the suspect's e-mail in many cases. This may also involve security questions, but my experience is that the exchanges often store the answers in the clear on their customer databases. Either way, access should be achievable.
- Locate the user name and password for the account. This can be easier than you may think. Here are some possible ways to get this information:
- Ask the suspect for his password. (This actually works sometimes.)
- Carry out a forensic analysis on the suspect's computer, looking for passwords to other resources. If you find one of the suspect's passwords, try derivatives of it to gain access elsewhere. Most people use variations of just three base passwords or phrases.
Once you have access to the online account, just transfer the funds to your storage wallet as previously outlined, and store it appropriately.
Practice, Practice, Practice
These steps may seem daunting and, to be honest, the first time I had to move coins from a suspect's live wallet to my storage wallet and then out to paper, I was really nervous! The only way to get comfortable with the process is to practice and practice some more.
Set up a training environment in your lab or office, and train the key people so that the steps become second nature. Purchase a small amount of cryptocurrency, and then role-play different types of seizures using different wallets. You may want to re-create some of the suggestions in Chapter 8, “Detecting the Use of Cryptocurrencies,” to find addresses hidden in a room, or use forensic means to search a computer for public and private keys or backup seeds. Then go through the motions of cashing out, or seizing to your storage address.
Once you have copied a backup seed to paper and then deleted the storage account, use the seed to re-create the wallet. It will really help boost your confidence in the process when you see all the coins return once the seed is imported.
After you're done following the steps to move and back up the practice coins, the storage wallet can become the pretend suspect's wallet, and you can repeat the training over and over, just losing small amounts in fees during the transactions.
Summary
Everything that was covered in previous chapters of this book leads to this chapter. If you can understand cryptocurrencies, locate private key backups, track money though the blockchain, and locate service providers, it is still all for nothing if you cannot seize the assets once they are located.
Aside from the processes described in this chapter, try to get digital forensics and financial investigators to work together and share their knowledge rather than working in silos of information and abilities. This small step can mean the difference between technical solutions being ignored or successfully exploited and financial tricks overlooked or investigated.
The methods described in this chapter are not meant to be the only ones that you can use to gain control of cryptocurrency assets. They are just the methods and processes that have worked for me and the people I work with and train.
And don't forget to practice, practice, and then practice some more!
