Children’s Internet Protection Act
The CIPA,16 which was passed in 2000, requires schools and libraries that receive funding from the U.S. government for internet access to filter offensive and sexually explicit online content. The goal of the program is to limit children’s access to offensive and age-inappropriate content on the internet. Under CIPA, a minor is anyone under the age of 17.17 These schools and libraries had until July 1, 2004, to first comply with CIPA.
![]() NOTE
NOTE
Note the differences in ages between CIPA and COPPA. COPPA defines a child as anyone under the age of 13. CIPA defines a minor as anyone under the age of 17.
CIPA was quickly challenged. The American Library Association and the American Civil Liberties Union sued the U.S. government, claiming CIPA violated the free speech rights of adults. They also claimed the law was so broad that it could prevent minors from getting information about topics such as breast cancer. In 2002, the U.S. District Court for the Eastern District of Pennsylvania agreed that CIPA violated First Amendment rights and that the government could not enforce CIPA. The U.S. government appealed that decision.18
![]() NOTE
NOTE
A visual depiction is any picture, image, or graphic image.
The suit went to the U.S. Supreme Court. In United States et al. v. American Library Association, Inc. et al. in 2003, the U.S. Supreme Court overturned the District Court ruling and upheld the law. The Supreme Court said that the law was constitutional because it was conditional. That is, only schools and libraries that chose to receive federal funding to subsidize their internet access costs were required to follow the law. If it wanted to, a school or library could choose not to accept the funding. If that happened, then it did not have to comply with CIPA.
Purpose
The primary purpose of CIPA is to protect minors from accessing offensive content on the internet. Offensive content includes visual depictions of material that is any of the following:
- Obscene
- Child pornography
- Harmful to minors
Under CIPA, obscene and child pornography are defined by referring to other laws. CIPA does specifically define the phrase harmful to minors. It includes any visual content that:
- Taken as a whole and with respect to minors, appeals to a prurient interest in nudity, sex, or excretion
FYI
E-Rate funding provides discounts to schools and libraries for internet access and telecommunications services. This funding is collected as part of the universal services fee paid by consumers to use telecommunications services. The goal of this funding is to help all schools and libraries have affordable internet access. Discounts range from 20 to 90 percent of the service costs depending on the need of the school or library. Part of the E-Rate application requires schools and libraries to state affirmatively that they are complying with CIPA. The E-Rate program provided $4.15 billion in funding in 2019. Learn more at https://www.fcc.gov/consumers/guides/universal-service-program-schools-and-libraries-e-rate.
- Depicts, describes, or represents, in a patently offensive way with respect to what is suitable for minors, an actual or simulated sexual act or sexual contact, actual or simulated normal or perverted sexual acts, or a lewd exhibition of the genitals
- Taken as a whole, lacks serious literary, artistic, political, or scientific value as to minors19
Scope of the Regulation
The E-Rate program provides discounts to most schools and libraries for internet access. Any school or library that receives federal funding from the E-Rate program must comply with CIPA. However, schools and libraries do not have to accept these funds. They can either pay for the internet access with other funds, or choose not to use the internet.
Main Requirements
CIPA has two main requirements. The first is that schools and libraries that accept E-Rate funding must implement technologies that filter offensive visual content so that minors do not access it. The second requirement is that schools implement an internet safety policy.
Content Filtering
The primary requirements of CIPA mandate the filtering of offensive content so that minors do not see it. Although this may seem difficult, there are tools to make the job easier. CIPA’s term for such a tool is technology protection measure (TPM). A TPM is any technology that can block or filter the objectionable content.20 Remember that under CIPA, a TPM must filter visual content.
Consider FIGURE 5-1. This figure shows a proxy server used to filter content. A proxy server accepts internet requests from clients, retrieves the pages, and serves them to the client. Content filters filter out objectionable content. As shown, you would configure the internal clients to access the internet through a proxy server.
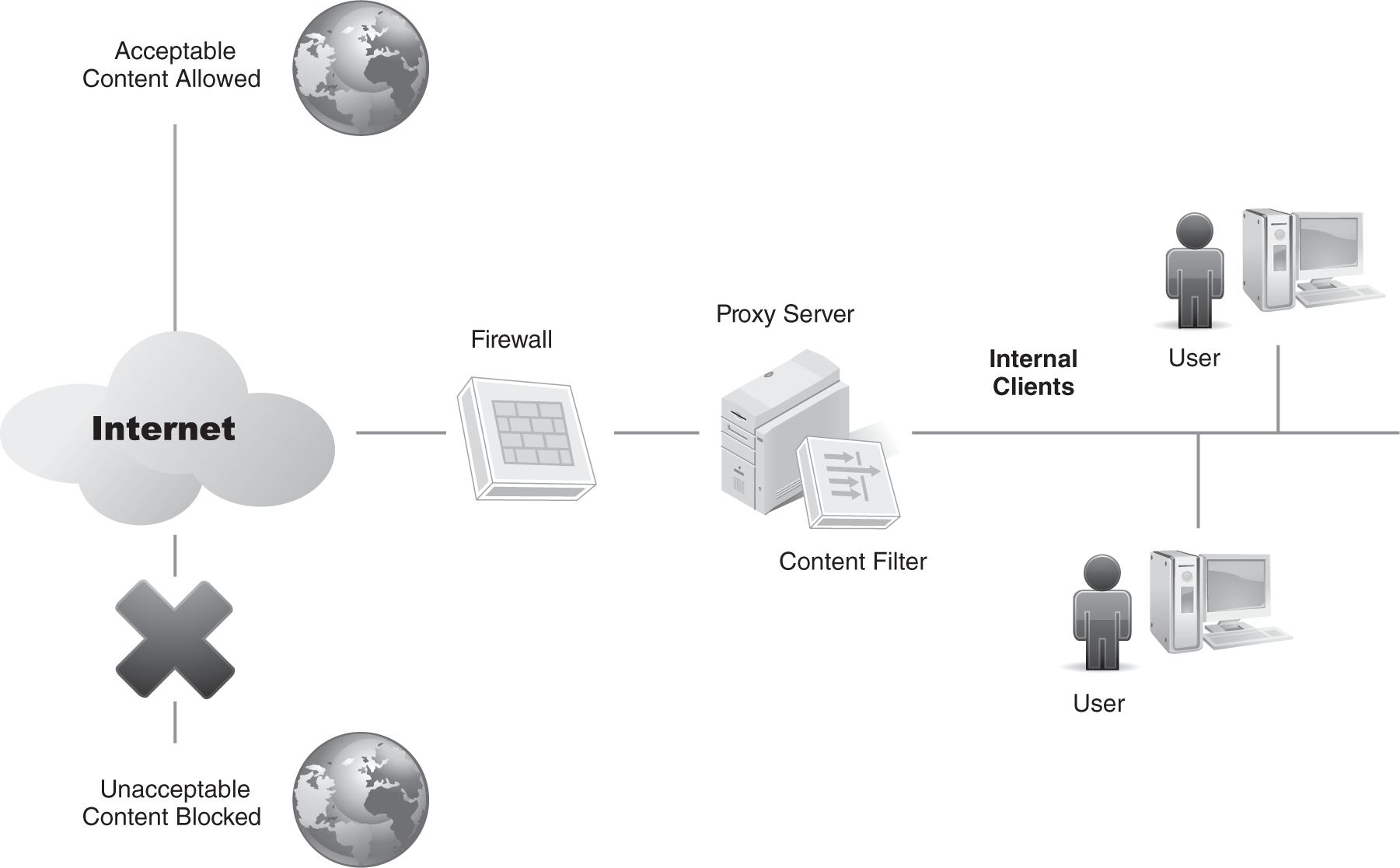
FIGURE 5-1
Proxy server used for content filtering.
The proxy server has a content filter that blocks all content marked as unacceptable. Some filters can also block content to email and instant messaging programs. Similarly, the filter allows all content marked as acceptable based on filter lists.
Third-party companies sell subscriptions to filter lists. These companies constantly search the internet, identify restricted materials, and add it to the filter lists. When a network administrator adds the filter to an organization’s proxy server, the server blocks the prohibited material.
In addition to filtering with lists such as the previously described ones, TPMs can also include monitoring technologies that track a child’s online activities. They can also limit the amount of time that a child can spend on the internet. In addition, TPMs include age-verification systems that restrict online access to adults.
The Federal Communications Commission (FCC) recognizes that a TPM cannot be 100 percent effective.21 However, neither CIPA nor the FCC defines what level is acceptable. A third-party company may claim its filter is CIPA compliant. However, there is no certification process to verify that a filter is CIPA compliant. The FCC has stated that local authorities should determine which measures are most effective for their community. The FCC rules specifically state that the U.S. federal government may not establish the criteria for making this determination and that it must be handled at the local level.22
Although a proxy server is a common method of filtering, CIPA does not specify where to filter the content. An internet service provider (ISP) may be able to filter it, or you may be able to purchase software to install on individual computers for filtering purposes. CIPA states what must be filtered but not how to filter it.
Proxy Servers in Any Company
Many companies use proxy servers. Their use is not restricted to CIPA compliance. Many companies choose to restrict employees’ access to different internet websites. For example, a company may want to prevent employees from accessing gambling sites. To do so, it can purchase a subscription to lists of gambling sites from one of the third-party sites that provide filter lists. The company can then install this filter on its proxy server.
When the user tries to access the prohibited site, the proxy server can instead show a different page. For example, the server could redirect the user to a web page that states, “Access is restricted.” This page also could show the company’s acceptable usage policy. Additionally, many proxy servers log all activities. Administrators are able to view the logs to determine which employees are trying to access restricted sites.
Internet Safety Policy
To comply with CIPA, schools and libraries must adopt and enforce an internet safety policy that must be made available to all users of the facility. The policy must address the following items:
- Access by minors to inappropriate matter on the internet
- The safety and security of minors when using electronic mail, chatrooms, and other forms of direct electronic communication
- Unauthorized access, such as “hacking,” and other unlawful activities
- Unauthorized disclosure, use, and dissemination of a minor’s personal information
- The measures designed to restrict minors’ access to harmful materials
An internet safety policy must educate minors about appropriate online behavior. This includes how to use social networking websites and chatrooms safely. The policy must include information on how to recognize cyberbullying, as well as how minors should respond to it.23
Exceptions
One of the main criticisms of CIPA is that schools and libraries are not implementing it properly. CIPA requires schools and libraries to filter visual depictions that may be harmful to minors. This means that images must be censored. However, sometimes access to text and entire websites are inadvertently blocked. In addition, sometimes the TPMs used by libraries may not work correctly and may actually allow minors access to obscene materials. Finally, often TPMs deny access by both adults and children to constitutionally protected content.
According to CIPA, a school or library must be able to disable the TPM for any adult who has a need to view content for a research or other lawful purpose. An adult is anyone over the age of 17. If a school or library refuses to disable a TPM for an adult that requests it, then the school or library is potentially infringing on the First Amendment rights of that adult. This is because they are censoring adult access to protected content. Under CIPA, an adult does not have to state why he or she wants the TPM disabled.
The United States et al. v. American Library Association, Inc. et al. Supreme Court ruling in 2003 explicitly mentioned this point. One of the reasons that the Supreme Court held that the law was constitutional is because a TPM could be disabled for any adult that requests it.
Libraries can use any method to disable the TPM that works best for their location. For example, library personnel could label some computers as “adult only.” Librarians would then have to monitor and prevent minors from using these computers. Librarians also could log onto a program designed to disable the TPM. Only personnel with the proper credentials could disable the TPM. Another method is to require an administrator to disable the TPM. Upon request by a patron, the librarian could contact an administrator to disable the TPM.
Oversight
The FCC has oversight for CIPA. However, little oversight action is required. When a public school or library requests E-Rate funding, it must certify that they will comply with CIPA. This certification is usually all that is required.
If a TPM fails, the school or library is expected to take steps to resolve the failure. Patrons may complain to the library for specific instances such as a TPM blocking too much content or not enough content. If the library does not resolve patron complaints, then the patron can file a complaint with the FCC, which may investigate those complaints. Any school or library that fails to comply with CIPA must refund any E-Rate funds or discounts that it received. Depending on the situation, other criminal laws such as laws against providing false statements to the government could apply to CIPA violations.
