The Federal Information Security Modernization Act
The Federal Information Security Modernization Act of 2014 recognized the complex nature of the federal computing environment.11 It also sought to improve oversight of federal information security activities and provide a framework for making sure that information security controls are effective. This is important because the U.S. government anticipates spending over $18 billion on cybersecurity in the fiscal year 2021.12
Purpose and Scope
FISMA defines information security as protecting IT systems to provide confidentiality, integrity, and availability.13 IT systems must be protected from unauthorized use, access, disruption, modification, and destruction.
FISMA has six main provisions. The law:
- Sets forth agency information security responsibilities
- Requires a yearly independent review of agency information security programs
- Authorizes the National Institute of Standards and Technology (NIST) to develop information security standards for IT systems that do not contain unclassified information
- Gives the Office of Management and Budget (OMB) and Department of Homeland Security (DHS) specific oversight responsibilities
- Clarifies that national security systems (NSSs) must be secured using a risk-based approach
- Provides for a central federal security incident response (IR) center
FISMA applies to federal agencies. These agencies fall under the executive branch of the U.S. government and report to the president. Examples of federal agencies include the Federal Aviation Administration, the Social Security Administration, and the Department of Education.
FISMA also applies to contractors who perform services on behalf of a federal agency. For example, researchers at universities who work with federal agencies may have to follow FISMA requirements on their own IT systems because those systems could store federal data.
Main Requirements
FISMA has many requirements. This section will review many of them. First, this section reviews what federal agencies must do to comply with FISMA. Second, it reviews how the NIST helps agencies shape their information security programs. Third, it reviews the federal central IR center. Finally, it reviews how FISMA applies to national security systems (NSSs). NSSs are IT systems that hold military, defense, and intelligence information.
Agency Information Security Programs
FISMA requires each federal agency to create an agency-wide information security program.14 Even agencies with NSSs must create these programs. An agency’s information security program must include:
- Risk assessments—Agencies must perform risk assessments. They must measure the harm that could result from unauthorized access to or use of agency IT systems. Agencies must base their information security programs on the results of these risk assessments.
- Policies and procedures—Agencies must create policies and procedures to reduce risk to an acceptable level. The policies must protect IT systems throughout their life cycle. Agencies also must create configuration management policies.
- Subordinate plans—Agencies must make sure that they have plans for securing networks, facilities, and systems or groups of IT systems. These plans are for technologies or system components that are a part of the larger information security program.
- Security awareness training—Agencies must give training to employees and any other users of their IT systems. This includes contractors. This training must make people aware of potential risks to the agency’s IT systems. It also must make people aware of their duties to protect these systems.
- Testing and evaluation—Agencies must test their security controls at least once a year. They must test management, operational, and technical controls for each IT system.
- Remedial actions—Agencies must have a plan to fix weaknesses in their information security program.
- Incident response—Agencies must have an IR procedure. They must state how the agency detects and mitigates incidents. The procedure must include reporting incidents to the DHS United States Computer Emergency Readiness Team (US-CERT) as needed.
- Continuity of operations—Agencies must have business continuity plans as part of their information security programs.
An agency’s information security program applies to any other organization that uses the agency’s IT systems or data. An agency must protect the IT systems that support the agency’s operations, even if another agency or contractor provides the systems. This can broaden the scope of FISMA, especially because IT systems and functions are often outsourced.
One of the most important parts of a FISMA information security program is that agencies test and evaluate it. FISMA requires each agency to perform “periodic testing and evaluation of the effectiveness of information security policies, procedures, and practices.”15 Agencies must test every IT system at least once a year, and test those with greater risk more often.
Agencies must also review their security controls. Some kinds of security controls are required under FISMA. The NIST has the authority to create these minimum requirements.16 Agencies must follow the standards that NIST creates. An agency must make sure that it implements these controls properly. It must also make sure that the controls work. The yearly testing requirement recognizes that security is an ongoing process. Agencies must always monitor their information security risk. They must monitor the controls put in place to mitigate that risk as well. The head of the agency is responsible for determining the right level of risk for the agency.
Agencies must also follow NIST guidance in performing their annual reviews. If an agency uses a different model to perform its review, that model must include the same elements that NIST does. The important role of NIST is discussed later in this chapter.
Under FISMA, agencies must name a senior official to be in charge of information security.17 In most agencies, this is the chief information security officer (CISO), who is responsible for FISMA compliance. The CISO’s main job duties must focus on information security. Under FISMA, a CISO must have the resources necessary to make sure that the agency can comply with FISMA.
![]() NOTE
NOTE
CISOs must be information security professionals and must have the “professional qualifications, including training and experience, required to administer” FISMA requirements.19
![]() NOTE
NOTE
CyberScope, which was created by the DHS, allows a real-time data feed that helps agencies and the OMB quickly assess the agency’s information security posture.
Agencies have several different reporting requirements under FISMA. For example, agencies must submit monthly electronic data feeds to the DHS through a program known as CyberScope. The purpose of these data feeds is to continuously monitor the security posture of the federal agency’s information systems.
Each agency must report yearly to the OMB on its FISMA compliance activities. An agency also must send a copy of its yearly report to the following:
- House of Representatives Committee on Oversight and Government Reform
- House of Representatives Committee on Homeland Security
- House of Representatives Committee on Science and Technology
- Senate Committee on Homeland Security and Governmental Affairs
- Senate Committee on Commerce, Science, and Transportation
- U.S. Government Accountability Office (GAO)
- The agency’s congressional authorization and appropriations committee18
An agency’s FISMA report is shared widely and must be in unclassified form.22 An agency’s yearly report must review its information security program. Items reviewed must include:
- The adequacy of the program
- A description of each major information security incident experienced by the agency
- The total number of information security incidents experienced by the agency
- A description of any information security incident experienced by the agency that compromised personally identifiable information (PII).
It also must assess the agency’s progress on correcting any weaknesses in the program or security controls. The agency must also respond to a set of questions about its security practices, which are asked in CyberScope. Each year the DHS publishes the questions that will be asked in the following year.
In addition to reporting on their information security activities, agencies must also report on their privacy activities. For example, they have to share information on their privacy training programs and their breach notification policy. They also must give a progress report on their efforts to eliminate the unnecessary use of SSNs and other PII.23
The yearly report also must include the results of an independent evaluation of the agency’s information security program. Some agencies have an inspector general (IG). If an agency has an IG, then the IG may carry out this evaluation. Some agencies do not have an IG. If they do not, the head of the agency must hire an external auditor to perform the evaluation.25
What Is an Inspector General?
An inspector general (IG) is an official who reviews the actions of a federal agency. An IG examines the agency’s activities to make sure that it is operating efficiently and following good governance practices. IGs are independent officials by law. The agency that an IG reports to cannot prevent the IG from performing an audit or investigation.
The Inspector General Act of 1978 defined an IG’s role.20 An IG is responsible for:
- Conducting independent and objective audits, investigations, and inspections
- Preventing and detecting waste, fraud, and abuse
- Promoting economy, effectiveness, and efficiency
- Reviewing pending legislation and regulations
- Keeping the agency head and Congress informed about agency activities21
IGs are appointed to their positions based on their experience in accounting, auditing, law, and investigations. They are not political officials. Some agency heads may appoint and remove their own IGs.
The president nominates IGs for major federal agencies, and the Senate approves them. Only the president can remove these IGs. The president nominates IGs in the Department of Commerce, Department of Justice, and OMB, as well as in some other agencies.
The Role of NIST
FISMA requires the Department of Commerce to create information security standards and guidelines. The Commerce Department delegated this responsibility to NIST, an agency of the Department of Commerce. Under FISMA, NIST must create:
![]() NOTE
NOTE
Before CyberScope, the FISMA reporting process was time- and paper-intensive. For example, in 6 years, the Department of State produced 95,000 pages of paper to meet its FISMA reporting requirements. It spent $133 million to create these reports.24
- Standards that all federal agencies use to categorize their data and IT systems
- Guidelines recommending the types of data and IT systems to be included in each category
- Minimum information security controls for IT systems
![]() NOTE
NOTE
In general, a standard states mandatory actions that an organization must take to protect its IT systems. A guideline states recommended actions that an organization should follow.
The OMB has stated that agencies must follow NIST standards and guidelines for non-NSSs. These standards and guidelines help agencies meet their FISMA obligations. NIST creates two different types of documents: Federal Information Processing Standards (FIPS) and Special Publications (SPs). FIPS are standards, whereas SPs are guidelines.
Federal agencies must follow FIPS. They must comply with new FIPS within 1 year of their publication date. FIPS do not apply to NSSs.
NIST creates FIPS when there is a compelling reason to do so. It creates a FIPS if there is no acceptable industry standard or solution for the underlying information security issue. As of this writing, there are 11 FIPS for information security. You can view them at https://csrc.nist.gov/publications/fips.
NIST uses procedures described in the Administrative Procedures Act (APA) to create FIPS. The APA states formal procedures for creating rules and regulations. This formal process ensures due process and makes sure that all interested agencies have a chance to comment on draft FIPS. NIST publishes a proposed FIPS in the Federal Register, which is available for public review for 30 to 90 days. The Department of Commerce must approve FIPS before they can be finalized.26
What Is FedRAMP?
In 2011, the United States adopted a "Cloud First" strategy as part of the Federal Government IT Modernization Act. That strategy advocated that federal agencies evaluate using cloud computing solutions for IT operations. In 2018, the U.S. federal government released its "Cloud Smart" strategy. Cloud Smart provides guidance surrounding the information security and workforce skills needed to adopt cloud computing models.27
The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program developed by NIST, the U.S. General Services Administration, DHS, and the Department of Defense.28 NIST also advises the FedRAMP program on FISMA compliance.
Any cloud computing services that store federal data must be FedRAMP approved. The FedRAMP program has a list of cloud computing providers that hold a FedRAMP designation. Federal agencies can purchase cloud computing services more quickly from vendors that have those designations.
FedRAMP outlines a standard approach to assess the security of cloud products and services. The FedRAMP security assessment framework is based on the NIST risk management framework (RMF). FedRAMP defines the minimum information security controls needed to safeguard cloud computing systems storing, accessing, and using federal data. Those controls are based on NIST SP 800-53, as revised.
To learn more about FedRAMP, visit https://www.fedramp.gov/.
U.S. Office of Management and Budget, “Federal Cloud Computing Strategy.” Undated, https://cloud.cio.gov/strategy/ (accessed May 16, 2020); Federal Risk and Authorization Management Program, “FedRAMP Security Assessment Framework.” November 15, 2017, https://www.fedramp.gov/assets/resources/documents/FedRAMP_Security_Assessment_Framework.pdf (accessed May 16, 2020).
SPs are computer security guidelines that are more general than FIPS. NIST creates SPs in collaboration with industry, government, and academic information security experts. NIST does not use the very formal FIPS drafting process to create these documents.
Federal agencies have some flexibility in using the SPs for guidance. They help guide federal agencies in strengthening their IT systems. The OMB understands that this may lead to different results among federal agencies. It acknowledges that different results are expected. Agencies have no flexibility in implementing FIPS, as they are mandatory.
NIST uses a RMF approach to FISMA compliance. This framework is outlined in “SP 800-37, Revision 2, Risk Management Framework for Information Systems and Organizations.”29 This approach helps protect IT systems during their whole life cycle. Federal agencies must use the RMF provided by NIST to assess the information security and privacy risks to their IT systems.
The NIST RMF outlines six steps to protect federal IT systems. They are:
![]() NOTE
NOTE
You can view the information security SPs at https://csrc.nist.gov/publications/sp800.
- Categorize IT systems.
- Select minimum security controls.
- Implement security controls in IT systems.
- Assess security controls for effectiveness.
- Authorize the IT system for processing.
- Continuously monitor security controls.
NIST’s RMF recommends a continuous process of categorization, assessment, and monitoring. FIGURE 8-1 shows this process.
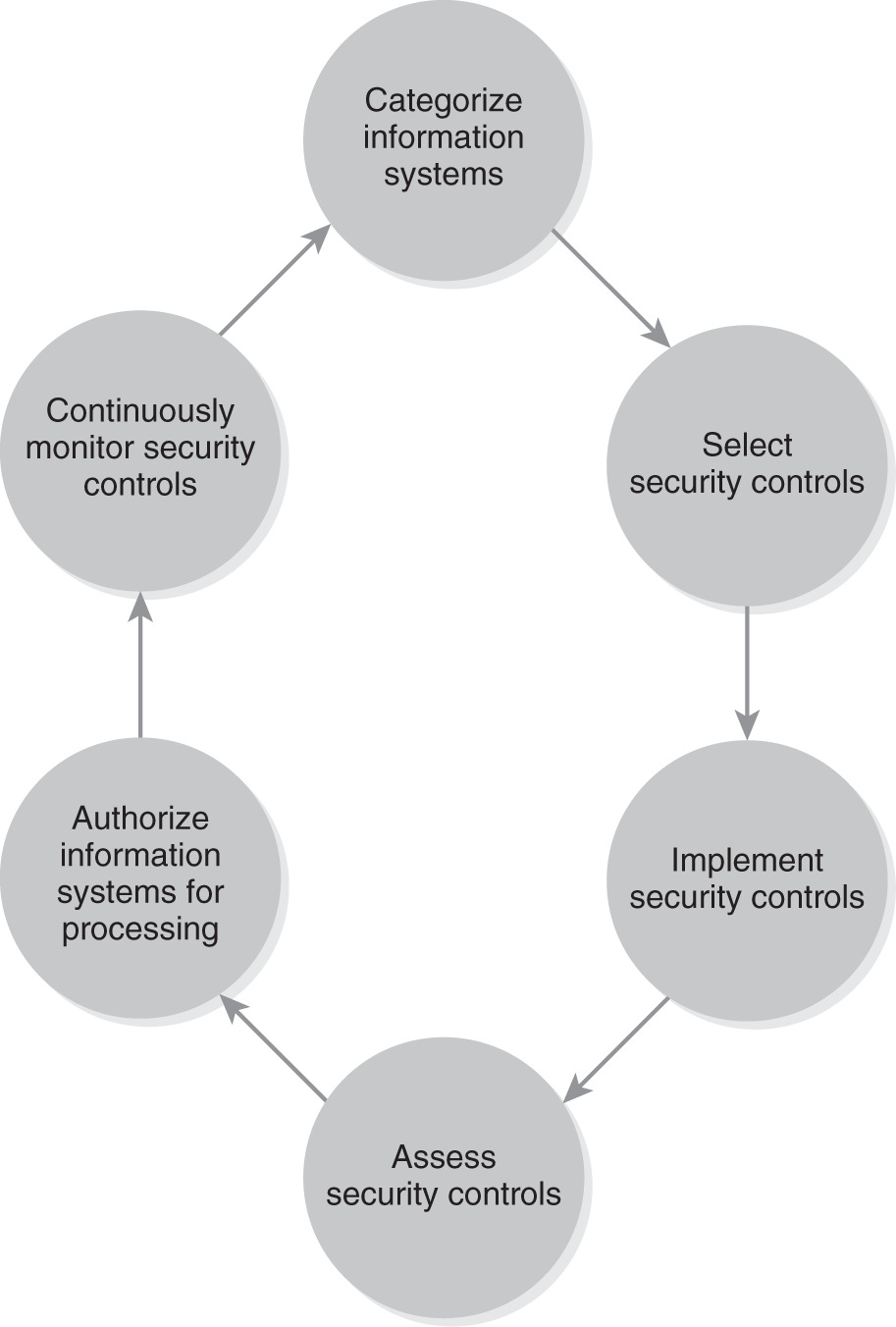
FIGURE 8-1
Risk management framework process.
NIST guides agencies at each RMF step. “FIPS 199, Standards for Security Categorization of Federal Information and Information Systems,” helps them categorize their IT systems.30 It serves as the starting point for an agency’s information security program and helps them separate their IT systems into categories based on risk. Agencies then apply security controls to their IT system based upon their category.
Under FIPS 199, agencies must first assess the impact on IT systems because of a loss of confidentiality, integrity, or availability. The security category expresses that impact. FIPS defines three security categories. They are:
- Low—The loss of confidentiality, integrity, or availability has a limited adverse effect on the agency, its information assets, or people. A low impact event results in minor damage to assets.
- Moderate—The loss of confidentiality, integrity, or availability has a serious adverse effect on the agency, its information assets, or people. A moderate impact event results in significant damage to assets.
- High—The loss of confidentiality, integrity, or availability has a severe or catastrophic adverse effect on the agency, its information assets, or people. A high impact event results in major damage to assets.
After the agency determines the security category, it must decide which controls to use. NIST created two documents to help with this task. They are “FIPS 200, Minimum Security Requirements for Federal Information and Information Systems”31 and “SP 800-53, Revision 4, Security and Privacy Controls for Federal Information Systems and Organizations.”32 The OMB requires that agencies use these documents to make their security control decisions.
![]() NOTE
NOTE
At the time of this writing, NIST had released a final public draft of NIST SP 800-53, Revision 5. This revision includes major enhancements to information security and privacy controls. It is anticipated that the final version of SP 800-53, Rev. 5 will be released in late 2020 or early 2021.
These documents require agencies to specify controls in 17 areas. FIPS 200 lists these areas. They are:
- Access control
- Awareness and training
- Audit and accountability
- Certification, accreditation, and security assessments
- Configuration management
- Contingency planning
- Identification and authentication
- Incident response
- Maintenance
- Media protection
- Physical and environmental protection
- Planning
- Personnel security
- Risk assessment
- System and services acquisition
- System and communications protection
- System and information integrity
Agencies must apply the right security controls. They must tailor controls to the level of impact. SP 800-53 defines the minimum thresholds, or baselines, for each category. For example, agencies must use low-impact security controls in IT systems where an adverse event has a low impact. It must follow a similar practice for moderate and high impacts.
TABLE 8-1 shows an example of how FIPS 200 and SP 800-53 work together. The example shows the different baselines for wireless access in the access control area.
TABLE 8-1 SP 800-53 Access Control Baselines for Wireless Access

Agencies can use other NIST guidelines to help them improve their security controls. For example, NIST has created an SP for protecting the confidentiality of PII.33 An agency could use this SP to strengthen its access control baseline for employees that access PII. Once a federal agency has implemented security controls, it must test them.
The OMB requires federal agencies to test their security controls. “NIST SP 800-53A, Revision 4, Assessing Security and Privacy Controls in Federal Information Systems and Organizations: Building Effective Assessment Plans” walks agencies through security control assessments.34 These assessments are performed throughout the RMF stages.
NIST’s RMF requires agencies to authorize their IT system for processing. This means that an agency must test its systems and approve its operation. This process is based on a review of the risk of operating the system. An agency must specifically accept the risks of operation before allowing an IT system to operate.
Finally, agencies must continuously monitor their security controls and make sure that they are effective. They also must document any changes to their IT systems and assess them for new risks.
Central Incident Response Center
Under FISMA, the government must have a federal IR center, which must:
- Give technical support to agencies about handling information security incidents.
- Compile and analyze data about information security incidents.
- Inform agencies about current and potential threats and vulnerabilities.
- Inform agencies about threats, vulnerabilities, and incidents to be considered as part of the agencies’ risk assessment process.
- Consult with NIST and agencies with NSSs about information security incidents.35
Agencies must report all information security incidents to the National Cybersecurity and Communications Integration Center (NCCIC). The federal IR center is also known as the US-CERT. Under FISMA, an incident is an event that
![]() NOTE
NOTE
In 2018, 31 percent of the incidents reported to NCCIC/US-CERT involved employee violations of a federal agency’s acceptable use policy.36
- “actually or imminently jeopardizes the integrity, confidentiality, or availability of information or an information system” or
- “constitutes a violation or imminent threat of violation of law, security policies, security procedures, or acceptable use policies.”37
When an agency reports an incident, it must share as much information about the incident as possible. They must make reports to the NCCIC/US-CERT within 1 hour of discovering an incident that potentially compromises the confidentiality, integrity, or availability of a federal IT system.38 An agency must share the following information about an incident when it makes a report:
- The impact the incident has had on the agency
- Whether any information has been lost, compromised, or corrupted
- The estimated amount of time and resources that are needed to recover from the incident
- When the incident was first detected
- The number of systems, records, and users impacted
- The network location of the incident
- Contact information if the NCCIC/US-CERT needs more information
The NCCIC/US-CERT coordinates IR across the U.S. government, shares information to help the government respond to threats, and also provides information security tips to the public. You can learn more at https://www.cisa.gov/securing-federal-networks.
National Security Systems
FISMA requires federal agencies to secure NSSs using a risk-based approach. An NSS includes systems that are for:
- Intelligence activities
- Command and control of military forces
- Weapons or weapons-control equipment
- Use cryptography to protect national security
- Critical to military or intelligence missions
- Must be kept classified for national defense or foreign policy39
FYI
FISMA does not apply to classified information. Classified information, which is protected by presidential executive order, is information that is labeled Confidential, Secret, or Top Secret. Its label is based upon its national security importance. This data must be protected to meet national security goals.
The Committee on National Security Systems (CNSS) oversees FISMA activities for NSSs. The CNSS has 21 voting members. They include officials from the National Security Administration (NSA), Central Intelligence Agency (CIA), and Department of Defense (DoD). A DoD member leads the committee. The CNSS also includes several subcommittees and panels. You can learn about the CNSS at www.cnss.gov.
Federal agencies with NSSs must follow CNSS policies. Today, CNSS policies favor following NIST guidelines and processes whenever possible.40 However, it was not always this way. Before 2012, the CNSS often had information security policies and procedures for NSSs that were either similar to NIST guidance or very different from NIST guidance. Many commentators thought that practice caused unnecessary complexity. Today, CNSS adopts NIST guidance whenever it makes sense to do so. It only issues separate guidance when NIST guidance does not meet the information security needs of NSSs.
FISMA permits the directors of the DoD and CIA to develop additional information security policies for NSSs within their own agencies. The OMB must report to Congress on FISMA compliance for NSSs. It also makes sure that agencies with an NSS are meeting FISMA’s legal requirements. The OMB makes sure that agencies with an NSS create an information security program and test it each year.
Oversight
The OMB and the DHS share responsibility for FISMA compliance. The OMB oversees FISMA-related budgetary issues. It can also withhold funding from agencies that fail to follow FISMA. In addition, the OMB must continue to issue a report to Congress each year on the government’s FISMA compliance. This report details how federal agencies are complying with FISMA. It also identifies problem areas.
The DHS has had the power to ensure that agencies are meeting their FISMA obligations. It can also create rules and other guidance that these agencies must follow. These rules are called binding operational directives. The DHS also keeps track of how all federal agencies are complying with FISMA and annually reviews their cybersecurity programs. DHS also has responsibilities for governmental IR activities.
FYI
The FY2018 FISMA annual report noted that the U.S. federal government continues to have security deficiencies.41 The top deficiencies were:
- Lack of data protection
- Lack of network segmentation
- Inconsistent patch management practices
- Lack of strong authentication
- Lack of continuous monitoring, audit, and logging capacities.
