IN THIS CHAPTER
This chapter explains why logs are important, how to create a logging strategy, and how to avoid some of the common pitfalls associated with logging and auditing. We will introduce the tools and techniques that will help you get the most from your logs without losing your mind.
Logs are another set of double-edged swords that lie quietly behind the scenes. They can completely save your butt, or completely overwhelm you, depending on the situation. Their importance, however, is frequently underestimated.
Logs are useful for a number of things. They can help you troubleshoot problems. They can be used for tracking down network anomalies. They can help trace an intruder’s steps, or help solidify your case in a court of law. However, if you don’t have a logging strategy, rest assured you will eventually come to regret it.
If your operating system already supports logging, you might be tempted to forgo additional logging tools. Try to resist that temptation. You can’t always trust your logs. In fact, altering logs to cover one’s tracks is one of the first things crackers learn. The practice has become so common that there are tools that automate the process. A list of the many available tools can be found at http://www.apocalypseonline.com/security/tools/tools.asp?exp_category=Log%20Cleaners, but here are a few of the more well-known ones:
UTClean—. UTClean is a utility that erases any evidence of your presence in
wtmp,wtmpx,utmp,utmpx, andlastlog. Check out UTClean at http://www.kyuzz.org/jaromil/files/exploits/utclean.c.remove—. remove will clean
utmp,wtmp, andlastlog, erasing any evidence of your presence. Check out remove at http://www.kyuzz.org/jaromil/files/exploits/remove.c.marry—. marry is a tool for editing
utmp,wtmp, andlastlogentries. Check out marry at http://www.apocalypseonline.com/security/tools/redirect.asp?red_tool=marry.c.
NOTE
On many Unix systems, wtmp, wtmpx, utmpx, and lastlog record and report user information, including what time a particular user accessed the system. For example, grepping for a last entry on root will produce output like this:
root console Fri Jun 19 17:01 - down (00:01) root console Fri Jun 12 12:26 - down (4+02:16) root console Tue May 19 10:45 - down (01:50) root console Fri May 1 11:23 - down (00:02) root console Fri Apr 24 09:56 - 09:56 (00:00) root console Mon Mar 23 02:53 - down (00:01) root console Mon Mar 23 02:43 - down (00:01)
When an intrusion occurs, system administrators turn to these logs to determine who accessed the machine and when.
TIP
It should also be noted that “rootkits,” packages designed to cover an intruder’s tracks and provide back doors into the system, usually contain log cleansers as well. One of the largest collections of rootkits I’ve seen can be found at http://packetstorm.decepticons.org/UNIX/penetration/rootkits/.
To hedge your bets against crackers tampering with your log entries, you should create a logging strategy that’s difficult to circumvent. The easiest way to achieve this is to write your logs to a one-way write-once device, or to copy your logs to a secured logging server. Some administrators have their Unix machines write their logs to a serial port that is attached to a standalone machine. Although this is certainly quite secure, the model doesn’t scale very well.
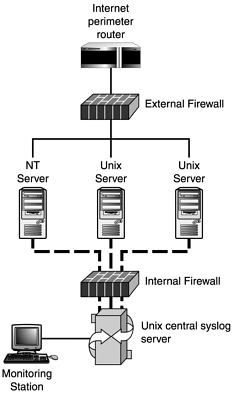
One model that is a little more scalable revolves around using the syslog protocol. syslog is a native service on almost every Unix platform, and recently add-on products have made it available on other platforms (such as Windows NT) as well. Although there are more secure alternatives to syslog, it is now common across most router and firewall products. This ubiquity gives administrators a common denominator with which to centralize all logging. For example, administrators can configure all hosts to log to a protected and centralized syslog-based logging server—giving security teams a single point at which to coordinate log data (see Figure 13.1).
When configured properly, the only traffic allowed to the syslog server is traffic destined for UDP port 514 (the syslog port). By sending system logs to a separate, secure machine, you make it a LOT more difficult for intruders to clean their tracks.
TIP
Adiscon makes a great Windows NT/2000-based utility called Event Reporter that enables you to send the Windows event logs to a syslog-based server. See http://www.eventreporter.com for more information.
TIP
A couple of years ago a program called SRS (Secure Remote Streaming) came onto the scene. SRS was written to replace syslog with security at the core of its design. It’s not as frequently adopted as syslog, but it is certainly worth checking out as a more secure alternative: http://packetstormsecurity.nl/groups/w00w00/SRS/. Another alternative worth checking out that can encrypt data is nsyslogd, available at http://cheops.anu.edu.au/~avalon/nsyslog.html.
In addition to centralizing your logs, you might want to consider using at least one third-party logging or parsing tool. This approach has several advantages. First, although the cracker community is familiar with operating system-based logs, few crackers have the knowledge or the means to circumvent third-party logging software. Second, good third-party software packages derive their logs independently of the operating system logs. You’ll know that intruders have penetrated your system when you compare this information and discover a discrepancy between your third-party logs and your regular logs.
This is especially true if you insulate your third-party logs. For example, suppose you use a third-party logging tool to later verify the integrity of operating system-based logs. Although expensive, writing those third-party logs to write-once media guarantees you one set of reliable logs, and reliability is everything.
Using third-party products is prudent in case your out-of-the-box logging utilities fail. For example, on some versions of Solaris, the tmpx file will truncate incoming hostnames, rendering any data obtained via last erroneous and incomplete.
Coming at this from a different angle, it’s now a pretty common procedure for crackers to kill your logging capabilities prior to launching a real attack. If the target is running an unpatched version of Solaris 2.5.x, for instance, you can kill syslogd simply by sending it an external message from a nonexistent IP address. Similarly, if syslogd accepts remote messages, anyone can make a false entry in the log.
You should consider an alternative logging system for all these reasons. The next section briefly covers several good ones.
The following tools not only report data from logs, they also collect data from diverse sources. Note that some of these tools are starting to tread pretty close to the intrusion detection space, which we covered in detail in Chapter 12, “Intrusion Detection Systems.” It will be interesting to see whether the two types of utilities will interoperate over time.
The authors wrote SWATCH to supplement the logging capabilities of out-of-the-box Unix systems. SWATCH, consequently, has logging capabilities that far exceed your run-of-the-mill syslog. SWATCH provides real-time monitoring, logging, and reporting. Because SWATCH is written in Perl, it’s both portable and extensible.
SWATCH has several unique features:
A “backfinger” utility that attempts to grab finger information from an attacking host.
Support for instant paging so you can receive up-to-the-minute reports.
Conditional execution of commands. (If this condition is found in a log file, do this.)
Lastly, SWATCH relies on local configuration files. Conveniently, multiple configuration files can exist on the same machine. Therefore, although originally intended only for system administrators, any local user with adequate privileges can use SWATCH.
Platform: Unix (Perl is required)
Kenneth Ingham developed Watcher while at the University of New Mexico Computing Center. He explains that the Computing Center was being expanded at the time, so the logging process they were using was no longer adequate. Ingham was looking for a way to automate log scanning, and Watcher was the result of his labors.
Watcher analyzes various logs and processes, looking for radically abnormal activity. The author sufficiently fine-tuned this process so that Watcher can interpret the widely variable output of commands such as ps without setting off alarms.
Watcher runs on Unix systems and requires a C compiler.
Author: Kenneth Ingham
Email: [email protected]
lsof version 4 traces not only open files (including network connections, pipes, streams, and so on), but the processes that own them. lsof runs on many Unix systems, including but not limited to the following:
AIX
BSDI BSD/OS
NetBSD 1.[23] for Intel and SPARC-based systems
FreeBSD
Digital Unix (DEC OSF/1)
HP-UX
IRIX
Linux
NEXTSTEP 3.1 for NEXTSTEP architectures
SCO UnixWare
Solaris and SUN OS
Platform: Unix
Private-I has two primary functions. First, it serves as a back-end log archiver for Cisco IOS-based routers, PIX and Checkpoint firewalls, and SonicWall VPN devices. Second, it is capable of generating real-time alerts based on known firewall and IOS event codes. Because Private-I has been designed to process the vendor-specific event codes piped to it via syslog, it can alert administrators of problems in real-time, as well as produce informative reports.
OpenSystems.com
Though WebSense is best known for its screening capabilities, the product also has powerful logging capabilities. (These have recently been enhanced, as the product has been designed to work closely with firewalls from many vendors.)
WebSense, Inc.
Email: [email protected]
Win-Log is a very simple utility for Windows NT. It logs when, how often, and how long Windows NT is used. You can use this utility to ascertain whether someone has been rebooting your box, even if they somehow circumvent Event Logger.
iNFINITY Software
Email: [email protected]
The following tools examine log files, extract the data, and generate reports.
NetTracker analyzes both wall and proxy files. It has extensive filtering and reporting, and can export data to Excel and Access file formats. NetTracker can also analyze general access logs and format custom reports suitable for graphing. NetTracker runs on Windows; a 30-day evaluation is available on the Web.
Sane Solutions, LLC
Email: [email protected]
LogSurfer is a comprehensive log analysis tool. The program examines plain text log files and can perform various actions based on what it finds (and the rules you provide). These might include creating an alert, executing an external program, or even taking portions of the log data and feeding that to external commands or processes. LogSurfer requires a C compiler.
Univ. of Hamburg, Dept. of Computer Science
DFN-CERT
WebTrends for Firewalls and VPNs combines Web link, usage, and traffic analysis with log analysis for more than 20 firewalls.
WebTrends can pull some very impressive statistics, and writes to a wide variety of database report formats. (This product runs on Windows.)
Analog is probably the only truly cross-platform log file analyzer. Analog currently runs on most operating systems.
Not only is Analog cross-platform, it also has built-in support for a wide variety of languages, including English, Portuguese, French, German, Swedish, Czech, Slovak, Slovene, Romanian, and Hungarian.
Analog also does reverse DNS lookups (slowly), has a built-in scripting language (similar to the shell languages), and has at least minimal support for AppleScript.
Lastly, Analog supports most of the well-known Web server log formats, including Apache, NCSA, WebStar, IIS, W3 Extended, Netscape/iPlanet, and Netpresenz.
Author: Stephen Turner
Never underestimate the importance of keeping detailed logs. Not only are logs essential when you’re investigating a network intrusion, they’re also a requisite for bringing charges against an attacker. Sparse logs simply won’t do.
In recent years, many criminal cracking cases have ended in plea bargains. One of the primary reasons for this is because perpetrators were often kids—kids who were just “having a little fun.” However, plea bargains are becoming less prevalent as real criminal elements migrate to the Net. Real criminals know that proving a case before a judge or jury is very difficult (especially if the prosecution has little Internet experience). When judges and jurors are asked to send a human being to prison, they need substantial proof. The only way you can offer substantial proof is by having several fail-safe methods of logging.
Crimes perpetrated over the Internet are unlike most other crimes. For example, in a robbery case, crooks are placed in a lineup so the victim can identify the culprit. In burglary cases, fingerprints will generally reveal the identity of the perpetrator. On the Internet, however, you have neither a physical description nor fingerprints. Therefore, without logs, making a case against a cracker is almost impossible.