IN THIS CHAPTER
Security issues plague every operating system, and the Macintosh operating system is not excluded. Hundreds of hacking programs targeting the Macintosh (and for the Macintosh, targeting other systems) exist, so it isn’t hard to see that it has its flaws. Yet many people still believe that security on the Macintosh platform isn’t an issue! Until Mac OS X, Macintosh operating systems offered greater security than many alternative systems, but many of the issues and hacks seen now are the result of modifications to the system and third-party software exploits.
When security issues and hacks began increasing for the Macintosh, many of the Mac OS news sites never reported on any issue that arose for fear of losing readers by reporting such negative issues. Times have changed for these news sites; when one site posts on an issue, the others must follow suit, as security has become such a hot topic and is recognized as a high priority subject. If not for all the competing news sites and concerned readers, some security issues still wouldn’t be reported.
Security issues and hacking topics for the Macintosh formerly could only be found at select sites, most of which specialized on the topic or were underground-related. Sites like mSec (http://www.msec.net), SecureMac.com, and Freaks Macintosh Archives (http://freaky.staticusers.net/, a Mac hacker site) have reported on hacking vulnerabilities since they opened. Macinstein.com was one of the first sites to cover Macintosh security issues openly, and now MacSurfer.com and MacFixIt.com have no fears of discussing or reporting the issues, either.
Apple has also adapted to security publicly by offering a mailing list specific to Macintosh security and has set up a Web site with information at (http://www.apple.com/support/security/). This mailing list will only discuss topics related to the operating system—third-party products won’t be discussed on this list.
The security updates page (http://www.apple.com/support/security/security_updates.html) within Apple’s security site currently only has information on Mac OS X and Mac OS X servers. The details include the affected piece of software the system uses, and any known references.
In the rest of this chapter, I will cover Macintosh security topics ranging from internal desktop security to Internet security, covering both the classic Mac OS (prior to X) and Mac OS X. First off, I would like to explain the differences between Mac OS X and Apple’s previous version of its operating system.
Unlike any of Apple’s other operating systems, Mac OS X is a new breed, created by mixing the Macintosh interface with the advanced technology of Unix underlying the system. Mac OS X is Unix-based, running on what is known as Darwin (http://www.apple.com/darwin/), the core of Apple’s system. The most notable difference is the integration of Mach 3.0’s OS services based on BSD. Apple has brought back many users with the release of Mac OS X by catching the attention of technical users, allowing them to interact with the Unix interface through the Terminal application (see Figure 24.1), providing the best of both worlds.
Figure 24.1. The Mac OS X Terminal console—the gateway into the core of the Unix portion of the system.
The Terminal application allows users access to the Unix built into Mac OS X. With the developers tools installed, many Unix programs can also be compiled and run from the command prompt. This includes many of the security tools available for Unix, as well as hacker’s exploits in C or Perl found on sites such as PacketStorm Security (http://www.packetstormsecurity.org).
In basing OS X on Unix, Apple has introduced the security concerns that exist for the Unix operating system, as well as those of the Macintosh. Mac OS systems prior to OS X were considered more secure because remote administration utilities were not built-in. Additional software was necessary to remotely control or administer the computer; without it, remote attackers had no way into the computer if no services were enabled or server software was installed. Unix offers an advanced multi-user environment—there are dozens of services and programs to be activated or launched to allow remote users access to the system (such as FTP, SSH, Telnet, Web, and backdoors accessible via Telnet).
Mac OS X offers many services that are disabled by default, so unknowing users would not be open to remote connections without activating the services first. Early versions of Mac OS X came with a Telnet service that allowed a user to connect with a Telnet application and navigate and control the system remotely. However, due to insecurities in the protocol, Telnet service was promptly replaced with SSH, a secure non-plain-text encrypted type of Telnet functionality.
Enabling the SSH service (daemon) on a Mac OS X system will allow a user to SSH to the computer, and with the correct authentication password, the remote user can access the computer via the command line (for more on SSH, see Chapter 6, “A Brief TCP/IP Primer”). If you do not intend to access your computer remotely, turn this service off, especially if you have not set up a firewall restricting access to the port SSH runs on (port 22). SSH has had its own security issues as well; running the software without following up on security issues can be hazardous to your system. In short, don’t run it for fun—use it when needed and when the computer is protected properly.
Today, it is common to have Macintosh computers in every environment, and it is becoming more common to see them used as servers. There are many server software packages available, including IRC, FTP, Hotline, Mail, and Web for the Macintosh.
Establishing a Macintosh Internet information server was once a pretty daunting task—not any more. Today, there are many server suites available that will have you up and running in minutes. I list a few in Table 24.1.
Of the server suites listed, I will only go into detail with two of them, WebSTAR and Hotline.
Of the servers mentioned in Table 24.1, the one that has received the most publicity is WebSTAR, mostly for its security features. The first mainstream media attention the software package received occurred when a cash reward was offered for anyone who could penetrate the Web server. Most recently, the U.S. Army decided to switch its Web server platform to the Mac OS and run WebSTAR. Before discussing other vulnerabilities for the Macintosh platform, I want to briefly cover that story.
On September 14, 1999, StarNine (now known as 4D Inc.) announced that the U.S. Army’s main Web site, http://www.army.mil, was being served by WebSTAR Server Suite software on the Mac OS. A Windows NT–based server had previously been serving the Army site when it was hacked in late June 1999 by a 19-year-old Wisconsin man. Perhaps old news, but the Web server is still in place running on a Macintosh using WebSTAR.
NOTE
For more information, refer to http://www.webstar.com/press/press_releases/pr091499.html.
This sudden switchover caught the attention of everyone. WebSTAR’s press release was plastered all over the news, and Apple ran commercials showing Army tanks surrounding the G3 Macintosh.
WebSTAR for Mac OS X allows for the easy configuration of all the services offered in one package. Even though Mac OS X has the Apache Web server built in, the ease of WebSTAR and the added features/security make it a complete server suite. Last time I checked, the Army wasn’t running WebSTAR on Mac OS X—more than likely it hasn’t passed the tests, as the OS is rather new, or the Army prefers Macs without remote administration methods, so it would be ideal to stick to running WebSTAR on an OS prior to Mac OS X.
Hotsprings, Inc., took over the development of Hotline from Hotline Communications, the recent event has put many questions into the picture as to where this program will go. Both the client and server software are available for download on such sites as VersionTracker.com and Download.com from mirrored locations. Grab your client, put in an alternative Hotline server, and connect.
Hotline is not a Web server or email server; you do not use a Web browser to access it. Hotline is its own server and its own client. Anyone can host a server, run the application, and become an administrator capable of sharing files with the world. You can find anything you want to download somewhere on Hotline. Hotline was first made for the Macintosh, and demand was sufficient for a Windows-compatible version, which is now also available. Let’s go through some of the details.
Hotsprings, Inc., made two products: a server that enables users to connect, and a client application that enables users to chat, send messages to each other, download files, stream media, and post news.
The software is free, and with the tracker system, anyone can find a server to fit their needs. The tracker is a list of online servers. You can search the servers’ descriptions or names to find a server that will fit your needs.
To list all the uncensored servers, open the server window and click the Add Tracker button. Enter tracked.group.org for the name and address. Refresh the list, and you now have access to anything you desire.
TIP
For a Macintosh hacking server where you can find all the Hackintosh files, get the Hotline client and connect to the Freaks Macintosh Archives server. The address is fma.nedline.com: 1234, or search for FMA on the tracker or from the Web at http://tracker.staticusers.net/. From there you can talk to Macintosh hackers, programmers, and power users whose ideas exceed most Mac users. Plus you can talk to some of the original Macintosh hackers, like The Weasel, who started the e-zine HackAddict.
For Hotline resources such as news sites, articles, search engines, servers, and trackers, visit http://www.hotspringsinc.com/.
There are two different versions of Mac OS X: the standard package for the client side, and Mac OS X Server, which is intended for use as a server. The difference between the two is that the Server version has added tools and services pre-bundled with it to easily manage a server.
The standard edition of Mac OS X does have the capability to be run as a server. For starters, it comes with an FTP server, Web server and SSH server, and with the right knowledge, additional server functionality can be added. However, the nice, easy-to-use interfaces to configure, set up, and install the server software will be absent, unless third-party developers create them.
The Web server bundled with Mac OS X is the most used and popular Web server in the world—Apache (http://www.apache.org). Adapted to Mac OS X, users can now publish and serve their sites from their own computer with all the functionality of Apache for the Unix platforms. Mixed with PHP and MySQL, the Apache Web server is far from lacking functionality. Mac OS X Server Edition has GUI-based configuration utilities to help manage the Apache Web server. The standard version of Mac OS X doesn’t come with any configuration utilities, so any changes to the server need to be done by command line. Reading the help manual and additional documentation on the Apache Web site will be useful.
Each user has a directory called Sites in his Home Directory where the files are accessible from a Web browser when the Web Service is active. Accessing http://127.0.0.1/~username/ from your Web browser on the local machine will show the files in the users directory. Be aware that files stored within the Sites directory are accessible by anyone if the Web server is active. If you use this directory for only yourself without intending to allow access to anyone else on the Internet, be sure to configure the firewall settings to deny access to whichever post the Web server is running on (generally port 80).
There are Unix variants of Hotline, one of which is called HXD. Mac OS X is capable of running HXD in the background (a daemon) by having the system take care of it; setting up, starting, and stopping the service is done through the Terminal application. HXD is just one example of what is available to run on Mac OS X as server software; Apache is another, and there are still others, such as mail servers and various file sharing servers.
I will now go over some different software vulnerability issues for the Macintosh. I don’t believe that you can understand security fully without understanding what the hacker uses and knows. Some vulnerabilities only affect older versions of the software titles or systems, but you’d be surprised how many people are still using older versions, whether it’s because they were unaware of the update, the security alert wasn’t made public enough (such as just saying it’s an update, instead of advising of a security hole), or the new version had too steep a price tag.
Impact: This opens documents with other programs.
Class: Not critical
Fix: Disable the programs that allow this access.
Credit: charlie chuckles
I spoke with charlie chuckles a while ago (in October 2000). He had noticed that no papers had been written on the unusual way of accessing files with AtEase, so he wrote the following:
This is a [problem] for AtEase 5.X…When I say the phrase “AtEase,” it usually implies some sort of inferiority to everything else. But AtEase isn’t really the problem here. It’s the applications and some of their roundabout ways of opening files and the system administrator’s not noticing. So I guess it sort of IS an AtEase problem by not covering every single [strange] way that programs ask for files. That was pretty deep.
The first thing I want to cover in here are the older tricks that have been on the market for a while. Everyone knows about the Web browser trick (type
"file:///drive name/"and read all the files on the drive). That is commonly accessible because all users are given access to some browser in their user folder. There was another trick that I’d seen using Apple Works, but I could never get it to work. I think it’s because the person who wrote it was a failure with a wooden leg and real feet.Now forward! to read/write! Let’s pretend you are in a biosphere. Now let’s pretend your user has access to MS Word. In version 8 (and the equivalent Excel release and probably the rest of Office) there is a find file function. Here’s how to use it:
Launch MS something. File>open. Click the Find button. On the Find Window select the drive you want to search and what you want to search for. If you want all the files list leave the search field empty. It will take a while if there are a lot of files on the drive to be searched (4 minutes for 30,000 on beige g3s). The files will list and you can select what to open with read/write privileges.
I’m pretty sure this works because the method of opening the files was not covered in AtEase. There are other examples of this. In a graphic converter, you can go to file>browse folder and look at the drives with read/write access. Same with Netscape (read only). These are all very [strange] methods of opening and browsing the files. I’m sure there are many other applications that are like them. Keep your peepers on the screen, squire.
If you have a PowerBook 3400 and are thinking about installing At Ease 4.0, do not enable the floppy disk boot security feature. If you do, your disk volume will become permanently corrupted, and you will be unable to access the disk by any conventional means (including boot floppy, SCSI drives, CD-ROMs, or other methods).
Mac OS machines running TCP/IP and System 7.1 or System 7.8 are vulnerable to a denial-of-service (DoS) attack. When these machines are the target of heavy port scanning, they die (7.1 crashes, and 7.8 runs the CPU to 100% utilization). This was reportedly repaired in OpenTransport 1.2.
Besides the systems themselves being affected from the attack, it is common for third-party server software to also have flaws causing denial of service. In case of constant crashing, look over the log files carefully for something suspicious, then put a stop to the insanity! Report your findings to the developers of the application. Be sure to update your software if new versions are available from the vendor, as the issue may have been tackled previously.
Even the security applications themselves can create security problems. DiskGuard, created by ASD Software and now owned by Intego, is a security application that restricts access to folders, files, and disk drives. In a prior version of the software (1.5.2), users who installed the software found that their drives were inaccessible. The company at the time (ASD Software) released a patch upgrading the software to 1.5.3, resolving the issue. Even with the current version, security software that restricts drive access can be very harmful when misconfigured or tampered with by a vicious attacker.
The current owner Intego (http://www.intego.com) has taken further steps to ensure that the software is understandable and well-documented. New versions of DiskGuard don’t have the problem found in version 1.5.2, but there is still the possibility of administrator error causing lockouts to the computer unintentionally.
Be cautious of how the computer is set up—if it is in a high-risk environment, invoke more restrictions and policies. Make sure the administrator is the only one who knows the password used to administrate DiskGuard; in the wrong hands, it could be used to cause lockouts, making it a very time-consuming task for the administrator to regain access to the system.
For example, a user with enough permissions could load and run a program created by mSec called Disengage (http://freaky.staticusers.net/security/fileguard/Disengage.sit), allowing the person running it to see the results after the program decrypts the user information stored in DiskGuard. Once the user had the administrator password, she could log in as the administrator and have full access to the computer or change the permissions.
Users can contact the software developer to voice their concerns. In the end, it’s a cat and mouse game—the developer will change the encryption method the user information is stored in, and crackers will figure out how it was done and create a new program to decrypt it. The best thing to do is watch user activity on the computer and restrict access as much as possible when in a high-risk environment.
In an advisory, Space Rogue explains the problem, the exploit, and the fix: in short, replace the driver for the drive. The hard disks blocking functionality won’t be fully operational, and the data can be accessed.
TIP
The full advisory written by Space Rogue back in 1998 is at http://www.atstake.com/research/advisories/1998/fwb.txt.
Application: MacDNS
Impact: MacDNS is vulnerable to DoS attacks.
Class: Moderate
Credit: Matt Leo
MacDNS provides Domain Name Service lookup for networks and runs on Macintosh Internet servers. Unfortunately, MacDNS will die when bombarded with requests at high speed. (The problem was initially discovered when a firewall tried to resolve forwards on each and every URL requested. This flooded the MacDNS server with thousands of requests.) This has now been confirmed as a bona fide DoS attack that can be reproduced by remote attackers. Leo suggests packet filtering. Otherwise, contact Apple for further information.
NOTE
Apple has released more documentation on the configuration of MacDNS to allow more connections. Full documentation can be found at Apple’s Technical Information site, linked from Apple.com’s support section.
The default password for Network Assistant is “ZYZZY”. Do us all a favor; change the password so it is not the default. For any type of program which has default passwords, documented or not, change the password right away to avoid unauthorized entry.
System: Mac OS 8.0 with PowerBooks 2400 and 3400
Class: Serious
Fix: Find patch at http://til.info.apple.com/techinfo.nsf/artnum/n26056.
Credit: Apple
If you install 8.0 over earlier versions, the Password Control Panel is disabled, and password protection will not work. To remedy this, either install the patch or install 8.0 clean and keep an earlier version with which to boot. Whenever you want to adjust the password settings, boot with the earlier version.
This is a garden-variety DoS vulnerability in early WebSTAR releases, and has nothing to do with Apple. (In fact, this hole can only be reproduced on a server that is also running NetCloak.) Gold found that if you append certain strings to an URL, the WebSTAR server will crash. Macworld ran a story on this hole, and the folks at that magazine did some testing themselves:
…for Mac Webmaster Jeff Gold, frustration turned to alarm when he realized that a mere typo caused his entire Mac-served site to crash. Gold’s crash occurred while he was using StarNine’s WebStar Web server software and the plug-in version of Maxum Development’s NetCloak 2.1, a popular WebStar add-on. Adding certain characters to the end of an URL crashes NetCloak, bringing down the server. To protect the thousands of sites using NetCloak, neither Gold nor Macworld will publicly reveal the character sequence, but it’s one that wouldn’t be too difficult to enter. After further investigation, Macworld discovered that the problem surfaces only when a server runs the plug-in version of NetCloak. When we removed the plug-in and used the NetCloak CGI instead, the Sequence of Death yielded only a benign error message.
TIP
The previous paragraph is excerpted from an article by Jim Heid, titled “How to Crash a Web Server.” (MacWorld 1997)
NetCloak is manufactured by Maxum Development. You can contact Maxum for upgrade information at http://www.maxum.com.
Mac OS X has had more security issues discovered and fixed within the last three months than Mac OS 9 has had in the past two years. This is because Mac OS X runs many programs that are for Unix in general, and as much of it is open source, the developers, hackers, and coders can pick at the code inside and out to find insecurities.
If you were to look at a Unix security mailing list there would be 100 times more posts to it than there would be for a Mac OS 9 list. With past Mac OS releases, nothing has really been open source, so the flaws discovered were generally super-probed in order to find them.
Take a look at Mac OS X’s software vulnerability page (http://www.info.apple.com/usen/security/security_updates.html) and subscribe to their mailing list (http://www.info.apple.com/usen/security/). Within each Security Update you install when you subscribe, you will see what is actually being updated. These titles are being updated for one reason or another because of the lack of security. Many of these programs being updated are Unix distributions, so when a version of the software is found to be vulnerable, Apple will have to evaluate the program and see if a security risk exists on their platform. If the risk exists, Apple will make the update available promptly.
Upon finding a vulnerable item in Mac OS X, you should contact Apple’s security team so they can get right on it, and of course email [email protected] with the details so they can be verified.
For instance, I just received an email from a user named Olivier notifying me of a security risk that was just discovered for OpenSSL. This particular vulnerability would require Apple to update many other packages that utilize OpenSSL functionality. The issue was posted to bugtraq by the people who found it—Olivier is just one of the Mac OS X readers who follow up on security, therefore knowing his system is insecure before Apple even announces it. He told me he applied all the necessary changes detailed in the advisory, and his system is no longer vulnerable.
Mac OS X’s first major security glitch affects all systems that have not upgraded to Mac OS X 10.1. The issue revolves around Setuid root applications allowing root access. This was demonstrated in four easy steps:
Open up the
Terminal.app(located in Applications/Utilities/).Quit
Terminal.app(File Menu, Quit Terminal)Open up NetInfo Manager (Applications/Utilities) and leave it in the foreground.
Launch the
Terminal.appfrom the Recent Items list from the Apple Menu.
If the computer has not been patched, the command prompt will be #, representing root, or the owner of the computer, who can do anything. Apple took this issue very seriously and updated the software fixing the hole. New builds of Mac OS X are not affected in the manner described.
Added additional security measures, such as applying the Open Firmware protection described later in this chapter, will increase local user security—they will not be able to boot from any other drive or media without supplying proper passwords.
Yet another security concern for Macintosh users is permitting file sharing. Notice the word concern is used, because the problem depends on what disks and resources are actually shared, if any. The Macintosh file sharing system is no less extensive (nor much more secure) than that employed by Microsoft Windows versions.
Sharing files is the act of allowing others to have access to the files. Sharing can be complex, and the choices you make in configuring the file sharing are dependent on the trust relationship in your organization. For example, I will share with you a story of one of my clients—I can assure you this happens a lot, and with networks being used in every environment, security rules must be implemented.
It doesn’t matter how large or small the network may be, when people are grouped together, each group has its own tasks. My client’s office wasn’t the largest setup; however, he had enough computers, and a few extra that weren’t used on a daily basis. Everyone who was a part of the company was trusted—the owner fully believed that each employee loved his company and the business, as well as cherished their jobs.
I was called on to do some security assessment because many of the company’s confidential files and client contact sheets had been distributed to a competing company. The network was composed of both Window and Mac machines sharing resources amongst each other. The computers in the billing department only showed the billing information, and the computers in the lab only showed the users’ shared resources.
Instead of setting up file sharing with permissions for each group of computers, the prior administrator just made it so that a computer in a particular group (for instance, billing) only showed a directory on the desktop, which the user could double-click to access. No restriction whatsoever was implied. The users could hold down the option key and click on the title bar to navigate a directory and see all the other users’ files, with the permissions to copy, delete, and so on.
I set up each user with their own login and password, and they were still able to share files with other users in the department, but now the other departments were restricted from navigating another’s directory.
Log files on the server showed that the files were downloaded from someone on an IP address that was assigned to a unused computer in the billing department. The computer had the exact same setup, but there wasn’t any sort of login authorization upon boot up. The other computers were protected with a screensaver password.
To prevent situations like this from occurring, you should carefully plot out sharing privileges at the time of installation. (And, naturally, if you don’t need file sharing, turn it off. Later in this chapter, I examine programs that can block unauthorized access to folders and control panels, so you can ensure that sharing stays off.) However, perhaps the most important step you can take to keep a Macintosh network secure is this: Educate your users.
Macintosh users are not security fanatics, but that’s no crime. Still, a lot of Unix and Windows NT users ridicule Macintosh users, claiming that they know little about their architecture or operating system. With Apple’s release of Mac OS X in 2001, which is based on the BSD platform, security has changed. Apple is taking security issues very seriously, and reacting to security flaws in a timely manner.
However, most Macintosh users are not very security conscious, and that’s a fact. So, anything you can do to change that is wonderful. At the very least, each user should establish a strong password for himself as the owner of the machine. (Macintosh passwords are subject to attack just the same as any other password on other platforms.) Finally, (and perhaps most importantly), guest access privileges should be set to inactive.
Mac OS 9 offers many more security features, such as voice authentication. One of the more notable features is the capability to encrypt and decrypt files using the built-in File Security program. It doesn’t offer the highest level of encryption, but it is enough to keep people from opening them and still be quick enough to encrypt and decrypt on the fly.
To encrypt your files on the fly, open the Apple File Security program located in the security folder within the Application folder on the hard disk.
Mac OS X offers much more user security than their previous operating systems. The administrator can add, modify, and delete multiple users through the System Preferences Users control pane. Each user’s account has its own home directory. This is a place where the user’s files are stored and protected by default from other users making changes to them without the proper privileges. The permissions used for the files are the same setup as permissions used in Unix.
Using the Terminal application to access the command line, users can learn more about file permissions via the command man chmod. Users can also change the permissions through the graphical user interface (GUI) of Mac OS X by choosing Information on the particular file or folder and selecting Permissions.
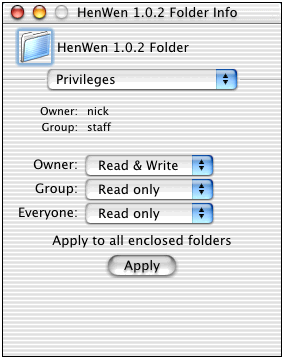
Owner is the person who owns the file/folder. If you’re looking at one of your own, you should be the owner, and Group defines which group you are associated with. Because I logged in with the administrator account, I am part of the group Staff.
If you have a sufficient permission level, you can change the permissions of the files, allowing the owner Read & Write or Read Only access. The group setting allows you to select what the other accounts in your group can do to the file: Read & Write, Read Only, or None.
The Everyone permission is what everyone can do. These are the users who are not a part of the group, or who aren’t the owner of the file. In Mac OS X, your home directory is set to Read Only for Everyone, meaning that everyone can peek through your files. If you want to restrict all the other users, simply get info on your user folder (by clicking the home button and then going up a directory) and select the Privileges option from the pull-down menu and toggle the settings. Once the changes are selected, they are made. There isn’t a choice to save permissions or cancel, so pay attention to what is being done, in case you accidentally or incorrectly select incorrect permissions.
The root user has permission to change any file permission, or to open or delete any file—essentially, whatever she wants. This user should be protected—in Mac OS X, Apple decided it was wise to disable the root user. Those who really want to enable it can do so by following these instructions (this same method can be used to disable the root account, also):
Within the Applications folder on the hard drive is another folder called Utilities with a program called NetInfo Manager—double-click it.
Follow the Domain Menu, Security, then click Authenticate. A dialog will show up asking for the administrators password.
After you’re authenticated, you will be able to click the Menu Domain, Security, Enable Root User.
The Administrator account, which is the first one created when installing Mac OS X, should not be used for everyday normal use. Avoid selecting new users as Administrators when there is no need to do so, and avoid doing everyday tasks as root.
For many, establishing a Web server is a very formidable task, but there is no comparison to actually maintaining one. This is especially true if that Web server is only a small portion of your network, or if numerous people need to be called upon to handle security privileges with different departments or clients.
Handling the management of a server is a very important task; even more important is ensuring that the server remains secure from intruders. Two approaches can be taken to assist with such tasks: You can contract out for custom programming, or you can rely on third-party applications for assistance.
Custom programming is expensive and time-consuming. If you want to throw up a few Web servers and manage them remotely, I recommend using prefabricated tools for the task. If your environment is predominantly Macintosh, the applications that follow are indispensable.
For Unix systems, there have been dozens of applications for security-related research. As Mac OS X is Unix based, we are already seeing ports of many of the popular security analysis tools for Unix to Mac OS X. Currently, many of the programs lack a GUI and must be set up and installed via the command line. If you’re not quite grasping the Unix aspect, search Google.com for Unix tutorials or howto’s—just reading over and trying the commands will familiarize you with it.
The benefit of many of the Unix applications is that they’re open source. This means they’re not compiled applications; instead, they include the source code, and have a cost that’s priceless to end users—free. If you find a program that runs on Unix and the developers have created builds for various flavors of Unix, there is a chance they are developing a version to work flawlessly with Mac OS X, or would be able to if they had access to a Mac OS X computer to debug, compile, and run it on.
After understanding the benefits, take a look at some of the management utilities built into the system. Bring up Mac OS X’s Sharing Preference window to make sure you know what is running and what isn’t. Open the System Preferences window, then click the Sharing icon. Within the window you will see the status of the following options:
File Sharing
Web Sharing
Allow FTP Status
Both File Sharing and Web Sharing have buttons to activate and deactivate the service. When the File Sharing status says File Sharing On, the service is active, and can be turned off by clicking the Stop button. At that point, the status will change. Allowing FTP access by checking that check box is generally not a good idea unless you are aware of the access it grants—any user on your system with an account can FTP in. FTP is also an insecure protocol; by this I mean that the authentication that’s performed when it asks you for a login and password when FTPing into the server is sent in plain text format. Anyone sniffing the network to monitor traffic between you and the destination host can see all the traffic passing by, including the files being transmitted.
Under the Applications tab of the Sharing Preferences is a check box that should be unchecked by default labeled Allow Remote Login. When this option is checked, your computer is running the SSH daemon (SSHd), waiting for connections to be established. Upon correct authentication, users who have an account on the system can operate the computer via the command line as if they were in the Terminal application. By trusting users to connect remotely, you also run the risk that the SSHd running on your computer might be vulnerable to some sort of exploit.
That is why I suggest you follow SecureMac.com for any sort of issue that might occur concerning your Mac’s security. If you aren’t one to compile your own builds of software when new versions come out, keep checking back with Apple’s Software Update, located in Systems Preferences. Check this periodically for new updates that might close any open holes until updates are available. Often, the only route is to disable the affected application containing the holes. If the application is a service that allows for remote users to create a connection remotely to your computer, it might also be wise to disallow access by denying connections to the port from the firewall.
WildPackets, Inc.
Email: [email protected]
WildPackets, Inc., formerly known as AG Group, has the most outstanding network utility around. EtherPeek is a protocol analyzer for Macintosh that supports a wide range of protocols, including but not limited to the following:
IP
AppleTalk
Netware
IPX/SPX
NetBEUI
NetBIOS
DECnet
SMB
OSI TARP
EtherPeek is not your run-of-the-mill protocol analyzer, but a well-designed commercial sniffer. It includes automatic IP-to-MAC translation, multicasts, real-time statistics, and real-time monitoring. EtherPeek also includes integrated support for handling the LAND denial-of-service attack that took down so many servers. If you are in a corporate environment, this would be a wise purchase. Security administrators will love this program for analyzing network activity.
Dartware, LLC
Email: [email protected]
InterMapper is an excellent tool that can save Macintosh system administrators many hours of work. The application monitors your network for possible changes in topology or failures in service. Network management is achieved using the Simple Network Management Protocol (SNMP).
One especially interesting feature is InterMapper’s capability to grab a network snapshot. This is a graphical representation of your network topology. (Network topology is more or less automatically detected, which saves a lot of time.) InterMapper even enables you to distribute snapshots across several monitors for a wider view.
The network snapshot is extremely detailed, enabling you to quickly identify routers that are down or having problems. You can actually specify how many errors are permissible at the router level—when a particular router exceeds that limit, it is flagged in a different color. Clicking any element (whether machine or router) will bring up information boxes that report the element’s IP address, the traffic it’s had, how many errors it’s had, and so forth. If there has been trouble at a particular node, you will be paged immediately. In all, InterMapper is a very complete network analysis and management suite.
InterMapper provides simultaneous support for both AppleTalk and IP. The software has full Mac OS 9 and Mac OS X support and is ready to run on Apple’s 1U rackmountable XSERVE machines with a plethora of user-contributed plug-ins for added functionality.
Lagoon Software, Inc.
Email: [email protected]
OS: Mac OS 9, Mac OS X
MacAnalysis is one program that belongs in any administrator’s toolbox for security auditing. MacAnalysis includes over 300 vulnerabilities, and retrieves passwords and information in over 200 different manners. It runs from a Mac, but has the information to scan many operating systems for known holes, reporting and analyzing the results, and giving the administrator insight into his network along with tips on fixing the problems.
Besides the security auditing features and the capability to test the results within the program to prevent false alarms, it also has schedulers and instant updates for the newest security holes available for download from their server through the software.
I said it belongs in any Mac administrator’s toolbox, but it isn’t just a security admin’s tool because of the entire built-in network testing and analysis tools:
Traceroute with graphical map locating
Firewall (Mac OS X)
ping
TCP bounce
finger
Port scan
Reverse IP
Brute force pop3/SMTP
DUP broadcast scan
WHOIS
OS fingerprinting
Network info, ICMP logger, news grabber and more…
In only a few seconds, MacAnalysis finds dozens of ways to exploit a system in many protocols, analyzing your network for any open holes, bugs, or tricks you might not be aware of.
Brian Hill
Email: [email protected]
MacSniffer is a graphical front-end for Mac OS X’s built-in tcpdump. With MacSniffer and tcpdump (see Chapter 15, “Sniffers,” for more on tcpdump), you can view Mac OS X’s network traffic to look for network flaws or to analyze traffic.
From the command line, you can access the built-in text-only interface by typing tcpdump , or man tcpdump for instructions. If this screen confuses you, or you just enjoy having the graphic feel to control and change settings, MacSniffer is for you.
MacSniffer’s options include filters to easily sort out traffic, and various view modes for diagnosing the packets being captured. You can choose to view just the headers, or the full ASCII dump of the packet data in real-time.
Alberto Ornaghi and Marco Valleri
In short, ettercap is a sniffer, interceptor, and logger for switched LANs used for multiple purposes. Developed on Unix and adapted to Mac OS X requirements, ettercap is simply one of the neatest network analysis tools on the block.
For a while, many people using Mac OS X had to modify the source before ettercap would compile, but currently ettercap compiles flawlessly on Mac OS X.
The ettercap developers keep adding new features to it on a regular basis. Here are some interesting functions that ettercap can show you while analyzing the network traffic. Many of the features of the program offer the capability of looking into and deciphering what the packets are for, so in the wrong hands this program could be dangerous (it can quickly pick out passwords from packets crossing the network). Many of these features will show you why you need to implement encryption in your everyday use. Even earlier standards on secure connections have been found insecure, such as SSH. Using SSH2 connections is recommended when possible.
Password collection—. BGP, FTP, Half Life, HTTP, ICQ, IMAP 4, IRC, LDAP, MSN, MySQL, Napster, NFS, NNTP, POP, Quake 3, RLOGIN, SMB, SNMP, SOCKS 5, SSH, Telnet, VNC, X11, and YMSG.
Packet filtering—. This feature sets up rules that will filter for a specific string, and there is also support for packet dropping. Packet dropping in ettercap allows for a filter to be enabled that will catch a particular string and replace it with something else.
ettercap also features OS fingerprinting, a connection killer, network scan, and plug-in support. You can find out more on ettercap as well as help forums at its Web site.
Nick Zitzmann
Email: [email protected]
Nick Zitzmann’s HenWen is a application developed to easily set up the popular Unix-based Network Intrusion Detection System (NIDS) Snort (http://www.snort.org) on Mac OS X. HenWen makes it possible for Mac users to interact with Snort without using the command line or having to compile the software. The hardcore geeks will always compile and run their software from the original source, but HenWen reaches out for free.
Snort alone is a network intrusion detection system for analyzing traffic in real-time, capable of handling protocol analysis and content matching to detect attacks and probes. Snort has very flexible rule sets; besides functioning as a straight IDS (intrusion detection system), it also can be used as a packet sniffer, and as a packet logging utility, making it very useful for security administrators. For more on Snort, see Chapter 12, “Intrusion Detection Systems.”
Weedo
StreamEdit is a utility that allows you to modify a stream of TCP or UDP datagrams. The process works by tunneling the data through itself, then allowing you to edit it or apply filters in real time. StreamEdit can be used for many different system administration purposes, but it’s a great application for performing security analysis tests on the network.
The documentation with the application goes over the program step by step in setting up a tunnel for whichever type of stream you wish to analyze or manipulate. StreamEdit is currently on version 1.0b2, but any suggestions or comments should be brought to the attention of the developer, as the program is still in the beta stage.
MCF Software
RADIUS technology is imperative if you run an ISP or any system that takes dial-in connections. Management of user dial-in services can be difficult, confusing, and time-consuming. That’s where RADIUS comes in. Authors of the RADIUS specification describe the problem and solution as follows:
Since modem pools are by definition a link to the outside world, they require careful attention to security, authorization and accounting. This can be best achieved by managing a single “database” of users, which allows for authentication (verifying user name and password) as well as configuration information detailing the type of service to deliver to the user (for example, SLIP, PPP, telnet, rlogin). RADIUS servers are responsible for receiving user connection requests, authenticating the user, and then returning all configuration information necessary for the client to deliver service to the user.
TIP
To learn more about RADIUS you should obtain RFC 2138, which is located at ftp://ftp.isi.edu/in-notes/rfc2138.txt.
In short, RADIUS offers easy management of a centralized database from which all dial-in users are authenticated. RADIUS implementations also support several different file formats, including native Unix passed files. Lastly, RADIUS implementations offer baseline logging, enabling you to determine who logged in, when, and for how long.
If you’ve ever dreamed of having RADIUS functionality for Mac OS, MacRadius is for you. It is a very refined application, offering you the capability to build complex group structures. In this way, adding new users (and having those new users automatically inherit the attributes of other users) is a simple task. And, of course, all of this is packaged in an easy-to-use, graphical environment characteristic of Macintosh applications.
Currently, the only concern with running a MacRadius server is the physical security of the computer. Keep it out of the reach of others, because if anyone were to gain physical sit-down access to the computer or remote control of it as if they were sitting in front of it, they could use a program that decrypts the administrator’s password. The intruder would then have access to change users’ password, or to make other modifications or additions to the server.
MR Mac Software
Download: http://freaky.staticusers.net/network/NetworkSecurityGuard.sit.hqx
Have you ever dreamt about NESSUS for Mac OS? What about a program (HyperCard Stack) that would automatically scan your Mac OS hosts for security vulnerabilities? If so, you need to get Network Security Guard.
Network Security Guard operates over AppleTalk and checks for the following in versions of the Mac OS prior to Mac OS X:
Default passwords
Accounts without passwords
File sharing
File permissions
But wait—there’s more. Network Security Guard has a brute force password cracking utility, so you can test the strength of network passwords, and your reports can be formatted in several ways and forwarded to you over the network. Lastly, you can schedule timed security assessments. All these features make Network Security Guard a great choice. It can save you many hours of work.
The software is unsupported now, as the developer’s site went offline. A more advanced product that is supported and scans for more vulnerabilities is MacAnalysis, which is covered later in this chapter.
Team2600
Email: [email protected]
Oyabun Tools, released by Team2600, is an application you can use to send remote commands to control your Mac. For example, if you notice your Macintosh server is slowing down and you are not at the office to reboot it, you can use the Oyabun Send to restart the machine. This program does not require any installation—just double-click it! Oyabun Tools consists of two products:
Oyabun Send lets you send shutdown/restart/sleep commands over the Internet to other Macs that already have Oyabun Tools Pro installed.
Oyabun Tools Pro lets you send shutdown/restart/sleep commands to other Macs over the Internet. It also lets you set up Macs to receive these commands. This package has everything that comes in the Oyabun Send package.
The Oyabun Send tool was made open source, allowing developers to do whatever they choose with the code as long as it is referenced to Team2600. Currently the software does not run on Mac OS X except under classic mode. Users seeking remote control of a server should look into Mac OS X’s built-in SSH daemon.
Logik
Silo, created by Logik, a Macintosh security guru, is a remote system analysis tool designed for security and administrative evaluation purposes. It features full documentation, remote concept password and file structure generation, network mapping, OS fingerprinting, and remote system, client, administrative, domain, protocol, and network analysis and monitoring.
Logik is said to be working on a new version of Silo that has Mac OS X support, so keep your eyes peeled and his site bookmarked.
Nmap, short for Network Mapper, is an open source utility that allows for network examination, or security auditing, as you learned in Chapter 3, “Hackers and Crackers.” Of all the classic network utilities that exist for Mac OS 9 and below, nothing can compare to the speed and reliability of Nmap. Luckily for Mac OS X users, Nmap can be installed and run from the command line!
Matthew Rothenberg has developed a GUI front-end application for Mac OS X designed to interface with Nmap called NmapFE. Written in Objective-C, the application is available at http://faktory.org/m/software/nmap/.
Nmap can scan a single host or large network very quickly. The program utilizes raw IP packets to determine the status of hosts on a network. Besides the hosts’ status, it will also determine the hosts’ operating systems, and what type of firewalls are in place, along with which services are running on the computer by using known characteristics.
The help screens and documentation included with Nmap are priceless in getting you started. Need help with the installation of Nmap? Install FINK (http://fink.sourceforge.net/). FINK is a project that ports Unix software and ensures its compatible with Mac OS X. Once FINK is installed, read over its documentation to see how to quickly install Nmap.
TIP
Nmap is available for download for free from http://www.insecure.org/nmap/.
Netopia, Inc.
Email: [email protected]
Timbuktu Pro 2000 for Mac OS is a powerful and versatile remote computing application. Although not specifically a security program, Timbuktu Pro is a valuable tool for any Web administrator. Timbuktu Pro currently supports TCP/IP, AppleTalk, IPX, and Open Transport. Through these protocols, you can remotely manage any box (or series of them).
With a simple port scan to an unprotected computer running Timbuktu on port 407, the outsiders have inside knowledge of what is running on your network. Because Timbuktu, along with the other remote control administrative utilities, offers so much control, this is a prime target for attempted intruders.
Also note that the Mac OS X Preview release of Timbuktu included a security risk. Users usually found it by simply clicking the About Timbuktu menu before even being logged in, which granted them access to the computer. Netopia quickly released a fix for the paid version of the preview software, accepting it as a security issue. By now this preview release of the software should NOT be running on your system, as newer versions have been released.
TIP
The Timbuktu Preview release security issue, documentation, and fix can be found at http://www.securemac.com/timubktuosxpreviewhole.php.
No matter which operating system you choose to run, if your computer is connected to the Internet or a network accessible by outsiders, you will want to add firewall protection. Here’s a perfect illustration of why you need firewall protection: You are running Mac OS X, and have FTP or SSH service enabled so you can connect to the computer from home or work. You’re the only one connecting to the computer, and there’s no need for others to access those ports. With the firewall protecting those ports, allowing only your remote IP to connect, your computer is safe from any infiltration attempts.
When using your computer as a server for others to connect to, it’s really easy to configure the firewall in Mac OS X (or any other OS) to restrict all access to any other port except the ones you wish others to connect to. You should become familiar with how the firewall’s filter or rule editor works. Once you have the settings in place, the first thing to do is test that what you put in place actually works. Feeling secure with an improper setup can often be a greater risk than having nothing, because you incorrectly believe that a intruder can’t gain entry.
In the Mac OS X Jaguar release and higher, there is a firewall control setting in the System Preferences with which you’ll construct your firewall settings. Planning out what you want others to have access to on paper, then implementing it into the program works best. If you’re unfamiliar with what ports each software runs on, the port numbers should be included in the documentation for the program. Alternatively, you can simply set the firewall up to deny all access to all ports, then figure out which ports require access and enable them so that either everyone or only specific IP addresses or ranges can access them.
The administrator can type lsof –i from the Terminal application in Mac OS X to see what applications are bound to which ports, and which ports are actively listening or connected. The command netstat -a will also show connection information. More variables like -a can be found by using the man netstat command from the console.
The next firewalls listed are some of the best firewall software for Mac OS 9 and earlier. Not every machine can run Apple’s new latest and greatest system, but no matter how old or new your system is, you should be protected from outsiders.
Sustainable Softworks
Email: [email protected]
IPNetSentry can be downloaded and used immediately, as it is shareware. The developers of this application strongly felt that Mac users should be able to use software first to see if it meets their needs before they dish out the money. Unlike any other firewall for the Macintosh, IPNetSentry does not barricade your computer behind a wall, making it inaccessible from the world. Instead, it works with you, building the rule sets. Of course, you can make your own filters and rules for it to follow. The program watches the type of connections; for instance, if someone port scans your computer, the program notifies you that the attempt has been blocked, and allows you to take the appropriate action.
The developers took this approach because not enough people could configure their firewall properly. Some people were so protected that they didn’t know how to unprotect themselves for a particular port or program—they just took down the firewall completely and forget to put it back online.
IPNetSentry knows when you’re doing something and permits it, as well as alerting you when others are connecting. Indeed, you can test your own firewall by having IPNetSentry’s servers test it and informing you of the outcome. Everything is configurable, and you can be kept apprised of what’s going on with the connections.
Intego
Email: [email protected]
Intego’s NetBarrier is a fully functional firewall for the Mac OS. The GUI of the program is very friendly to use and navigate. With all the gauges and valves going up and down as traffic comes and goes, users can get a real feel for what is happening and at what level.
NetBarrier also protects against ping flooding, SYN flooding, port scans, unknown packets, and features localhost hacking with password protection to protect NetBarrier. It also covers pings of death and many of the well-known webworms.
A Symantec product, Norton Personal Firewall offers a great way to protect your Macintosh from intruders. This program has predefined applications and the ports they run on. For instance, if you know you are running ICQ, you simply select ICQ from the list and allow it. This works the same for many of the popular games or known services.
For those users familiar with OpenDoor Firewall by OpenDoor Network (http://www.opendoor.com/), Norton Personal Firewall is based off that code.
TIP
Norton Personal Firewall will run on both Mac OS and Mac OS X. More information about this product can be found by visiting http://www.symantec.com/sabu/nis/npf_mac/.
Internal security is one of the most important parts of security. Even if your computer is secure from others on the Internet, if someone sits down at your computer for 10 minutes while you are out, your computer is at risk. Or what if someone were to sit down and see your password on a sticky note, or one of your various other hiding places (under the desk, or perhaps under the keyboard)? All your data could be stolen, or your computer could be compromised. You need to take a look at as many utilities as you can to help protect you, and to see what is most commonly used when intruders want to bug your system.
For Macintosh computers running Mac OS X and below, you will find many indispensable programs throughout this section to assist you in running a tight ship. Mac OS X has added security pre-installed that takes just seconds to get running.
I remember many screensavers for Mac OS that just didn’t offer any sort of security, or the ones that did would crash, or could be force quitted in one way or another, disabling the security at hand. One thing to remember about screensaver passwords is that they are meant to protect your computer while you are away for a short period of time. If your computer is set to automatically log in when started, someone could just as easily restart your computer and wait for it to come back up, and the screen would no longer be protected.
I will assume you have multiple users in place, and auto-login disabled when you plan on working in a secure environment (if not, do so!). In the Screen Saver System Preferences window, there is a tab called Activation. You can set the time for the screen to lock automatically. Below that, you have these options:
Do Not Ask for a Password
Use My User Account Password
Upon selecting Use My User Account Password, you will have to enter the same password you use to log in to the system. Without this checked, the screensaver offers no sort of security whatsoever, and is just pretty pixels flying around your screen.
Like Mac OS 9, Mac OS X supports multiple users. This makes it possible to restrict access to your computer by having it protected upon startup, giving the user the option to log out when she is finished without shutting down.
It’s important to note here that there can be only one administrator! Well, there can be more than one administrator, but it’s best to limit it to only one—and don’t get click-happy when creating new users. Granting administrative options by clicking that box when creating a new user will give that user admin privileges to make modifications and changes to the system, including deleting your account, or installing software that could alter the system and allow a backdoor to be put into place. Hope I scared you—be cautious to whom you permit admin privileges. From the command-line view, being an administrator means you’re in the Group Admin.
Create a login and password for each user that’s going to access the system. Advise the users to keep it confidential and private so others do not use it. If the chosen password is weak, it can be cracked very easily. Examples of weak passwords are those that can be found in a dictionary, are short, are the same as the user’s name, or are common knowledge for an insider (friends, family, co-workers). When choosing a password, keep it very private, and do not write it down—just remember it, and don’t use the password to log in to the system as any other password. A good password would be kP@#!3KA, instead of the normal password of your last name or license plate number.
I’d like to recommend that you choose a password up to 18 characters in length, but Mac OS X only stores the first 8 characters for the login password—be sure to mix it with numbers and extended characters. However, in later versions of Mac OS X, this may be fixed. To find out whether this is the case in the version you’re running, set your password for more than eight characters, then log out. When typing your password to log back in, type the first eight characters, then randomly type some other letters—if it works, it’s hasn’t been fixed.
BootLogger is one of the simpler security applications. It basically reads the boot sequence and records startups and shutdowns. It is not a resource-consuming utility. I suggest using this utility first. If evidence of tampering or unauthorized access appears, then I would switch to Super Save (detailed later in this chapter).
TIP
BootLogger is available at http://freaky.staticusers.net/security/BootLogger.sit.hqx.
DiskLocker is a utility that write-protects your local hard disk drive. Disks are managed through a password-protected mechanism. (In other words, you can only unlock the instant disk if you have the password. Be careful not to lock a disk and later lose your password.) The program is shareware (written by Olivier Lebra in Nice, France), and has a licensing fee of $10.
TIP
DiskLocker is available for download from ftp://ftp.amug.org/.
Magna
Email: mailto:[email protected]
Empower offers powerful access control for the Macintosh platform, including the ability to restrict access to both applications and folders.
Ferret is a small application that quickly gathers all important information (logins/ passwords) from a system by descrambling all passwords into plain text. It is meant to be used with a startup disk, or when you only have a few seconds of access to the machine. You can also drag and drop preferences onto it to get the information you want from a particular file (for example, when you are only able to access a preference file, and cannot directly access the machine).
Ferret can gather important information from preference files on any mounted volume, including AppleShare-mounted hard drives. Ferret can discover logins and passwords stored in any of the following applications: FreePPP, MacSLIP, OT/PPP (ARA), Internet Control Panel (Internet Config), Netscape Communicator, Eudora, AIM, ICQ, Gerry’s ICQ, Apple File Sharing Registry (Users & Groups), Carracho Bookmarks/Server Data Files, and Hotline Bookmarks/Server Data Files.
Currently, Ferret works with Mac OS 9 and earlier. Word is, the source code was lost, so future development of the program has been halted. As it currently stands, the application is still very useful.
TIP
Ferret can be downloaded from http://freaky.staticusers.net/hacking-misc/Ferretv0.0.1b4.sit.
Filelock is a little more incisive than DiskLocker. This utility will actually write-protect individual files or groups of files or folders. It supports complete drag-and-drop functionality, and will work on both 68KB and PPC architectures. It’s a very handy utility, especially if you share your machine with others in your home or office. It was written by Rocco Moliterno of Italy.
TIP
Filelock is available from http://macinsearch.com/infomac2/disk/filelock-132.html.
Highwinds Trading Company, LLC
Email: [email protected]
Highwinds has been creating security/encryption products since 1999. FullBack is a secure, easy-to-use archiving and backup program for Mac OS 9 and earlier. The deluxe version provides 512-bit, randomly generated encryption keys. Product information is available at http://www.highwinds.com/BackupSystem.html.
Invisible Oasis is a keystroke logger. This application records everything typed into a daily log. The installed extension is invisible, as is the folder where the logs are kept. To see whether you have this extension installed, use a program such as Apple ResEdit and go to Get Info Menu, and navigate to the Preference folder located within the System Folder on the Hard Disk (Hard Disk → System Folder → Preferences). Go into your preference folder, Get Info on the hidden folder and Unhide. You can open the logs with any text-editing program.
TIP
Invisible Oasis will work with systems prior to Mac OS 9. Download it at http://freaky.staticusers.net/security/keyloggers/InvisibleOasis_Installer.sit.
ResEdit can be found by searching for it on http://www.versiontracker.com.
Valid uses have been found for keystroke recorders, such as recovering documents after a crash, even before it was saved, and for development/testing purposes to ensure activities happened in the same manner. TypeRecorder is a shareware-based keystroke recording application, currently only for systems prior to Mac OS X. If you don’t pay the shareware fee, a dialog is displayed upon startup, so the program is not intended to be a sleek, hidden, you-can’t-find-me type of spy software.
TIP
Find TypeRecorder at http://rampellsoft.com/products/typerecorder/.
Blue Globe Software
Email: [email protected]
KeysOff enables you to lock out certain keys, preventing malicious users from accessing the menu bar, using mouse clicks, the power key, or command-key shortcuts. The program also prevents unauthorized users from loading disks. This is one of the most simple, cost-effective, and useful security programs available. Mac OS systems prior to OS 9 have it made when using KeysOff for desktop security—most definitely a favorite for security, and not a favorite of the hackers when all the security is in place, disabling many bypass features.
Maui Software
Email: [email protected]
LockOut, available for both Mac OS 9 and Mac OS X, is an easy-to-use application. It doesn’t pretend to offer a vaulted, secure solution—the documentation states its faults, so users are not fooled by false claims. Another positive aspect to the program is the low price, as Mac computers need some sort of security. Lockout can offer it, and the development staff implement user suggestions with each new version.
Before accessing the Macintosh, a valid password must be entered. While you’re away from the computer and it has been locked out, users may leave messages. If a password is entered incorrectly, LockOut enables the administrator to set up a voice warning to alert the user trying to gain access. When the maximum amount of idle time has been reached, LockOut will reactivate. When the program detects break-in attempts, it can automatically email a address with information about the attempt.
Several security programs use emergency passwords. These are passwords generated by the program in case the admin forgets his password. They usually give the user complete access to a computer.
In theory, you would need all sorts of software registration information for the software vendor to give away the emergency password. In reality, you only need to find the algorithm used to generate the emergency password.
nOGuard is a program that generates emergency passwords for PowerOn Software’s OnGuard 3.1 and 3.3. It was created by mSec.
TIP
The most up-to-date version of nOGuard is available for download at http://freaky.staticusers.net/security/onguard/nOGuard2.sit.
CP3 Software
Email: [email protected]
URL: http://www.cp3.com/
Password Key logs unauthorized access attempts, locks applications, and temporarily suspends all system operations until the correct password is supplied. Password Key is not Mac OS X-ready; it’s only for use on systems up to Mac OS 9 currently— check their site for more current information.
PowerBook users use the Password Security Control Panel to protect their computers. Displaying a dialog box that requests a password every time the hard drive is mounted, Password Security provides a convenient security measure.
As pointed out by a previous advisory, Password Security generates an emergency password every time it displays the password dialog box. This emergency password gives the same access level to the laptop as the owner’s password does.
This is, of course, a huge security breach, allowing anyone who can figure out the emergency password to access the computer, and even to change the owner’s password. The program PassSecGen (created by a member of the Macintosh security group mSec) generates the emergency passwords for the PowerBook security control panel to gain entry without knowing the real administrator password. This does not to appear to be a risk when using Mac OS X as the operating system.
TIP
The most up-to-date version of the Password Security Generator is available for download at http://freaky.staticusers.net/security/powerbook/PassSecGen1.0.sit.
Aladdin Systems
Email: [email protected]
Secure Delete in the past has been a part of the Stuffit Deluxe package for file compression. Secure Delete does exactly what it says—it deletes the files in a secure manner in which they are not recoverable with software such as Norton Utilities. When deleting a file by dragging it to the trash can, the file remains on the hard disk until the data has been overwritten on the areas of the disk where the original data was. Secure Delete overwrites the erased data blocks on the disk numerous times to ensure a safe deletion.
Stuffit Expander has become a part of the Mac compression lifestyle, offering the capability to expand every type of file. Stuffit Expander comes pre-installed with Mac OS X, so Aladdin decided to offer Secure Delete as a stand-alone deal. It can also be obtained with the Stuffit Deluxe package.
SecurityWare, Inc.
Email: [email protected]
SecurityWare offers physical security devices for all makes and models of Macs to prevent theft and tampering. From iMacs to desktops, there is hardware protection to physically protect your computer, including iBooks and PowerBooks.
Having some sort of physical security is always important no matter what environment you’re in. Once that computer is out the door, it’s gone—the only chance you have after that is Stealth Signal.
Stealth Signal, Inc.
Email: [email protected]
You can track lost or stolen laptops with Stealth Signal for a secure recovery. Stealth Signal silently sends information to the tracking servers that are watching your laptop. If for any reason you lose it, simply log on to the Web site and report it stolen. With the help of Stealth Signal, you might be able to recover the computer— although chances are what is on it has more value than the computer itself.
Through their research, the developers at Stealth Signal came to the conclusion that when hardware is stolen, it is usually sold quickly, wiping minimal, if any, amounts of data from the hard disk. This may or may not be the case, depending on who has stolen it. If the computer is connected to the Internet or has a phone line connection, Stealth Signal will make contact with the tracking servers. The computer can be tracked by the IP address used to connect to the Internet. Stealth Signal also has additional security features that they didn’t want me to talk about, but I can assure you that if your computer is stolen and someone is connecting to the Internet with it, they can help recover the hardware.
Stealth Signal is available for Mac OS, Mac OS X and the Windows platform. Connection statistics and other neat information can be viewed from the reporting Web interface.
Single user mode is a startup method you might choose to boot into when in front of the computer. This mode offers root access to the computer without authentication—it exists for emergency cases to fix problems.
To boot into single user mode, during the startup progress hold down the Command + S key. Once you are in and the computer has started up, you will have a black screen (command line) with the # facing you. Before any changes can be made, you must mount the hard disk.
/sbin/fsck –y /sbin/mount –wu /
In single user mode, it’s just you and the machine—no services are started. So, if you need to start services to change information, such as NetInfo, you must load it up.
Full documentation on single user root mode can be found at http://www.securemac.com/macosxsingleuser.php.
For the ultimate paranoiac, Super Save will record every single keystroke forwarded to the console. However, in a thoughtful move, the author chose to include an option with which you can disable this feature whenever passwords are being typed in, thus preventing the possibility of someone else later accessing your logs (through whatever means) and getting that data. Although not expressly designed for security’s sake (more for data crashes and recovery), this utility provides the ultimate in logging. Super Save does not work with Mac OS 9 or Mac OS X, and does not record mouse movement—only keyboard activity.
TIP
Super Save is available at http://wuarchive.wustl.edu/systems/mac/amug/files/system/s/.
SubRosaSoft.com Ltd.
Email: [email protected]
SubRosa Utilities is a set of security applications, two of which are for encryption. The software-suite consists of three pieces of software, all of which are compatible with the Windows OS, Mac OS, and Mac OS X:
SubRosa Encryptor—. Featuring 128-bit encryption with rolling keys, this program will encrypt your files and folders utilizing keys instead of insecure passwords. The files are encrypted in a format that’s Internet-ready; once it has been uploaded, it can be downloaded without being corrupted on both the PC and Mac.
SubRosa Decryptor—. The Decryptor will decrypt the encrypted archives created with the encryption application. Best of all, the entire Decryptor program is free of charge from SubRosa’s Web site, so you can transmit files in a secure manner, and the recipient of the file does not need to purchase any software to decrypt it.
SubRosa Shredder—. If you want a file encrypted in the first place, a potential data thief already knows it has confidential value. After a file has been encrypted, it is suggested that it be securely deleted using the SubRosa Shredder. The settings can be manipulated to specify how many times the file should be overwritten for a secure delete—by default it is set to three; if you feel extra special, raise the number. The higher the number, the more times Shredder manipulates the data, and the harder it is to recover.
Apple Open Firmware (http://bananajr6000.apple.com/) is the firmware used in Macintosh hardware—all specifications and details can be found at the included URL. For our purposes, we will only cover the password feature of the firmware.
Similar to the PC’s BIOS password, the Open Firmware password protects the system in many levels. Mac hackers know that they have many different ways to bypass internal security while sitting in front of the machine. They can try disabling extensions, booting from a media device or SCSI ID, and they’ll be successful in one way or another. Open Firmware puts a stop to bypassing security by disabling the user from bypassing the operating system’s instructions without supplying the proper password.
The newer Macintosh hardware models come with Open Firmware capable of setting up password support. Apple has also prepared software for Mac OS X to easily set up the password and enable or disable restrictions. For Mac OS X running Firmware 4.1.7+, use Apple’s application Open Firmware Password available for download at http://www.apple.com/downloads/macosx/apple/openfirmwarepassword.html.
The password protection feature of Open Firmware goes beyond standard Firmware specifications; a notable feature is the anti-brute force password attack methods. This means a user cannot keep on entering the password over and over until he finds the correct one—the Open Firmware will stop the user from making further attempts.
NOTE
Full instructions for enabling Open Firmware Password protection on Mac OS 9 and Mac OS X through Open Firmware can be found at http://www.securemac.com/openfirmwarepasswordprotection.php.
There are two ways to bypass the Open Firmware Password, but the first one doesn’t quite bypass it. Instead, it’s a program that will grab the password if the computer is started up. If you’re locked out already, this program will do you no good, but it’s useful if you need to recover the password. The program name is FWSucker, short for Firmware Password Sucker. Keep in mind that if a user on your system is already at the desktop and has the capability to load/run software, she can obtain the Open Firmware Password and make alterations. You can find out more about FWSucker at http://www.securemac.com/file-library/FWSucker.sit. Keep this out of the reach of children—you wouldn’t want someone to obtain the password and then protect the system and lock you out.
The second method for getting around the Open Firmware password is by resetting it. Without knowing the current password, the only way to gain entry is to reset the password. To do so, you will need to open up the computer and add or remove the necessary RAM so the total amount in the computer is different from its original amount, then ZAP the PRAM three times by holding down Command + Option + P + R during startup. After it has been reset, you can replace the hardware with the original components.
Apple did a good job requiring physical access to the insides of the machine to bypass the security. In a multiuser environment (work, lab, school), the computers would be locked anyhow, and someone wouldn’t be able to open the machine up unnoticed.
The following utilities are popular password crackers or related utilities for use on Macintosh. Some are made specifically to attack Macintosh-oriented files. Others are designed to crack Unix password files. This is not an exhaustive list, but rather a sample of the more interesting tools freely available on the Internet.
NOTE
FileMaker Pro is a database solution from Claris (http://www.claris.com). Although more commonly associated with the Macintosh platform, FileMaker Pro now runs on a variety of systems. It is available for shared database access on Windows NT networks, for example.
Many of the applications that crack FileMaker Pro files are version-specific. There has not been a crack for recent versions of FileMaker Pro in years. If you find an old FMP file on disk and it is protected, the FMP-cracking applications in this section would be useful.
There are also FileMaker Pro Password crackers available for the Windows platform that might cover more than the other software titles mentioned.
FMP Password Viewer Gold 2.0 is another utility for cracking FileMaker Pro files. It offers slightly more functionality (and is certainly newer) than FMProPeeker 1.1.
TIP
FMP Password Viewer Gold 2.0 is available at http://freaky.staticusers.net/cracking/FMP3.0ViewerGold2.0.sit.hqx.
This utility cracks FileMaker Pro files. In any event, FMProPeeker subverts the security of FileMaker Pro files.
TIP
FMProPeeker is available at http://freaky.staticusers.net/cracking/FMProPeeker.sit.hqx.
Grungie
Email: [email protected]
Macintosh Hacker’s Workshop (MHW) is a suite of hacking tools that will run under Mac OS 9 and Mac OS X. The program was developed to beat the performance of the existing graphical user interface password crackers for the Macintosh, and under Mac OS X it did indeed offer quicker speeds and better functionality.
MHW includes a wordlist generator used to test passwords. The cracking can be done using wordlists, or by brute force attacks. Many password crackers exist for Unix, but the advantage of using a Unix-based password cracker is purely in the performance.
John the Ripper is a Unix-based password cracking utility, and as mentioned previously, the advantage of using a Unix-based password cracking utility like this is for the performance. Because of all the system resources the program uses to test and audit the password, there is no need to bog it down with graphical user interfaces. This program must be compiled from the command line via the Terminal application.
To start off, go to the Web site listed here and download the Development release (dev) of the program, which supports Mac OS X. Compilation might require you to become acquainted with the user manual or install instructions.
After compilation is complete, run John the Ripper on a Unix password file, or export the password file stored in Mac OS X by using the following command:
nidump passwd .
The program is well-documented and discussed at the Web site provided. Happy cracking—this has to be one of the quickest password crackers available to run on Mac OS X!
Killer Cracker is a Macintosh port of a password cracker formerly run only on DOS-and Unix-based machines (http://www.hackers.com/html/archive.2.html).
MacKrack is a port of Alec Muffet’s famous Crack 4.1. It is designed to crack Unix passwords. It rarely comes with dictionary files, but still works quite well, and makes cracking Unix /etc/passwd files a cinch. (It has support for both 68KB and PPC.)
TIP
MacKrack is located at http://freaky.staticusers.net/cracking/MasterKrack1.0b14.sit.
Made by System Cowboy of the hacker group Digital-Rebels.org, MagicKey is a password-auditing tool for AppleTalk. The application audits an AppleTalk user’s file for weak passwords or no passwords with the brute force method.
TIP
MagicKey3.2.3a can be downloaded from http://freaky.staticusers.net/security/auditing/MK3.2.3a.sit.
MasterKeyII is yet another FileMaker Pro-cracking utility.
TIP
MasterKeyII is available at the following site http://freaky.staticusers.net/cracking/MasterKeyII1.0b2.sit.hqx.
McAuthority is a password-security application that uses brute force to attack a server to gain access to the password-protected areas. This application was made by nulle, one of the greatest Mac hack programmers.
TIP
McAuthority can be downloaded from http://freaky.staticusers.net/jp/McAuth1.0d6-FAT.sit.
Meltino is a sleekly designed Unix password cracker by the Japanese programmer nulle. This is one of the most popular Macintosh Unix password crackers. This application supports MD5 encryption as well as DES encryption. Meltino also supports the UltraFastCrypt (UFC) algorithm.
TIP
Meltino 2.0.1 can be downloaded at http://freaky.staticusers.net/cracking/Meltino/Meltino2.01_PPC.sit.bin.
Password Killer is designed to circumvent the majority of PowerBook security programs. PowerBooks are the only Apple computers susceptible to the security bypass circumvention, because the security software affected is only installed on PowerBooks.
TIP
Password Killer (also referred to as PowerBook Password Killer) can be found online at http://freaky.staticusers.net/cracking/Passwordkiller.sit.hqx.
Mailbombing is the act of sending a lot of email to a person to flood his mailbox. I do not suggest sending a mailbomb to anyone. Try sending it to yourself to see how it works. If you have ever received a mailbomb, you understand.
Sometimes you have to send anonymous email—things you don’t want people seeing and knowing you sent.
Caem lets you send mail anonymously with attachment support by utilizing proxy servers and certain mail servers. Some of the advanced features included for sending mail are the capability to build custom message headers and to import/export contacts and data.
TIP
Logik, the programmer of Caem, takes his work seriously and updates the program often. You can find his program at his Web site: http://logik.accesscard.org/.
Bomba is another mailbombing application. One of the techniques that the program has to send mail quicker is to connect to several mail servers simultaneously with proxy support for privacy.
Bomba is available for download at http://www.team2600.con or at http://freaky.staticusers.net/attack/mailbombing/bomba.sit.
Another Team2600 development, NailMail works on both Mac OS and Mac OS X, delivering what the group considers their fastest mailbombing application ever. You can be the judge of that by going to http://www.team2600.com and downloading the program free of charge.
Created by a Macintosh developer who goes by the alias of Mancow, this is a very slick, easy-to-use mass emailing program that supports HTML email. Spic & Spam has been built for Mac and Mac OS X. You can download it and see screenshots at http://mancow.forked.net/products/spicnspam/.
A different kind of bulk mailer, ATT Blitz is a application that takes advantage of mobile messenger Web site services for many popular cellular services. The program allows the user to send a certain amount of messages to the target’s phone, hiding their IP address by specifying a proxy.
ATT Blitz has been tested to work with AT&T, Verizon, Nextel, Sprint PCS, VoiceStream, and PrimeCo. Many users do not have free messaging services, thus they are paying per message. Bombing someone’s phone with this program is not recommended, but if it ever happens to you—you are aware the program exists. You can download it at http://mancow.forked.net/products/spicnspam/.
Viruses exist for the Macintosh. However, unlike the widespread Melissa or I Love you Bug viruses, unless the user’s whole network or a majority of its contacts were Macintosh users also, the virus or Trojan wouldn’t make it far. The reason Windows-based viruses/Trojans go so far is that there are more Windows users than Mac users around the world. Each time the virus comes to a Macintosh computer, chances are it has no affect on the system, so it’s a dead bug—you’re not spreading it. Good for you for being a Mac user.
Viruses spread globally on the Macintosh don’t work that well, because once they hit a Windows users computer, chances are it wouldn’t know how to run the Mac program or script. Of course, in due time, one could be set up to work on both systems with the right mind and programming.
Picture an office work network: hundreds of Macintosh computers in one place, an environment in which a worm or virus could easily spread across the network. All it takes is one person and a network that shares resources.
I’ve seen it time and time again: developers who create the software distribute files that are infected. They could be doing so intentionally or unintentionally, but the fact remains that when the programs are put on Internet sites like Download.com, AOL Archives, and VersionTracker.com, millions of Mac users flock to the sites to download the software.
The most widespread event I can reference was an incident in which a CD packaged with an issue of MacAddict magazine was distributed to its subscribers and newsstands. The CD was accidentally infected with the AutoStart worm. The worm was activated when the PowerPC computer’s QuickTime (2.0) control panel was set up to automatically play CDs when inserted.
Users had to download removal tools to get rid of the worm that caused the computer to read the hard disk in intervals of 3, 6, 10, and 30-minute intervals.
Detecting and preventing viruses and other malicious activity from taking place on your computer is the most important part. Even though you might feel that your computer is safe, you don’t know what viruses other computers have, or what the disk a client has sent you could be infected with. It’s even easier to become infected nowadays from the Internet being so handy. Imagine a hostile employee or enemy that knows you use a Macintosh. He sends you an email with a virus attached—of course, he faked the address, so you don’t think twice about opening it. Your Mac could be gone at this point.
The following are a few popular Macintosh antivirus solutions and resources.
No, its not a .com, . net, or .org—it’s http://www.MacVirus.info/, a site devoted to Macintosh virus education and antivirus solutions. Get the latest antivirus definitions, news, and facts about viruses from this site.
Read comparisons between different antivirus products, vendor facts, and get your questions answered about Mac viruses.
Once known as iTools, but now known as .Mac, this once-free service has moved to a yearly service fee. Along with the [email protected] and Web hosting that iTools offered, .Mac offers antivirus solutions for subscribers. The bundled Apple .Mac service comes with hard disk space on Apple’s server to backup onto, as well as the well-known antivirus software title Virex and updated virus definitions.
The Virex application is developed by McAfee, and is available for both Mac OS and Mac OS X. Virex scans emails for infected attachments, archived formats, and easy drag-and-drop checking. Combined with Mac OS X’s pre-existing security features, .Mac’s backup and Virex make for a great combination.
TIP
.Mac service can be obtained by visiting http://www.mac.com/; free trial accounts are available. Virex for the Macintosh may be obtained from http://www.mcafeeb2b.com/products/virex/.
Symantec Corporation
Symantec has a long history and good reputation for their products. Norton’s Anti-Virus for the Macintosh offers the same level of satisfaction as their other products offer. The features of NAV (Norton Anti-Virus) for the Macintosh compare to the other antivirus vendors in that it scans for viruses, and checks email attachments and archived files for viruses hiding within. A popular yet easily forgettable feature of NAV is that the virus definitions are automatically updated via Symantec’s LiveUpdate technology, so having to remember to download new definitions to be protected is in the past.
The Mac OS X version of NAV is lacking a few features, as developers hurry to adapt to the new technology and standards that Mac OS X offers. As reported on VersionTracker.com and other news sites, the Mac OS X version still has a few memory leaks, and the AutoProtect feature isn’t yet what the Mac OS version offered. It will be worked out in due time, and as of this writing there have not been any Mac OS X-specific viruses released into the wild.
TIP
Norton Anti-Virus product information is located at http://www.symantec.com/nav/nav_mac/. Downloadable demos, and more can also be found at Symantec’s Web site.
Intego
Email: [email protected]
VirusBarrier is Intego’s antivirus solution, available for Mac OS now, and with a planned release for Mac OS X in the third quarter of 2002. The developers have truly created a program that runs itself right out of the box. The features offered grow with every version:
NetUpdate virus definitions (download new viruses instantly)
Log file functions
Drag-and-drop virus scan
Protects against viruses and macro viruses
Stuffit archive scanning
Voice alert and email alert upon locating viruses
Password-protected settings (intruders cannot simply disable the password, but must authenticate first)
This software title can be purchased online or at any authorized Macintosh dealer, or you can download a demo from http://www.intego.com.
Disinfectant definitely has served its purpose, and has been used by thousands of Mac users seeking to detect and remove virus-infected files. The program isn’t Mac OS X ready; in fact, the program has been discontinued completely but can still be found. The program file is small and very quick at doing its job. If you’re running a system prior to Mac OS X, this program is free of charge to use; however, you will want to note that it doesn’t protect against worms, and it doesn’t protect against Microsoft Word macro viruses.
TIP
Because the program’s development has been halted, there is not a centralized homepage to visit. Try the link http://hyperarchive.lcs.mit.edu/HyperArchive/Archive/vir/disinfectant-371.hqx, and if it doesn’t work, simply go to an archive site such as http://www.download.com and perform a search for Disinfectant.
The AutoStart worm affects older Macintosh systems when QuickTime’s AutoPlay feature is enabled in the control panel. In version 2.0 of QuickTime, AutoPlay was enabled by default, so users commonly found themselves with computer problems and errors. After the computers were taken to the shop, it was found that many of them had the AutoStart worm. Users can check to see whether their computer is a victim to the worm and download free removal tools at the following sites:
WormScanner—. http://www.jwwalker.com/pages/worm.html
Worm Gobbler—. http://www.lineaux.com/html/body_autostart.html
Webmasters who have ever viewed their Web logs have seen evidence when their site has been hit with such worms as CodeRed and Nimda, as their requests fill the logs. Hopefully, any request from those two worms show up under File Not Found and Not a Valid Request. Whether they actually affect your system or not, the worm is using bandwidth and filling up log files rapidly by requesting files that could be nonexistent.
The Little Dutch Moose is a program for blocking and stopping these worms and illicit requests from arriving at your Mac OS X Web server (Apache) before they are even processed. The program watches over the connections and notices when connections are made in worm- or virus-like methods, and puts a halt to the requests.
Mac OS X users who are taking advantage of the built-in Apache Web server now have a way to protect and prevent against these type of connections, which could lead to denial of service or other malicious activities.
TIP
Customers of LDM (Little Dutch Moose) receive free updates. The software is shareware-based, so you can try it out by downloading it from the developer’s Web site at http://www.wundermoosen.com/.
As it stands, Mac OS X does not have any viruses designed for it. Before long (or when someone reads this statement), a new virus might be discovered. Viruses have been sparse for the last few years on the Macintosh; for the most part, we only update our monthly virus definitions to protect against Word macro viruses.
Email, software archives, and Web sites are all great ways to catch a virus, simply by downloading software without being protected. Antivirus software does more than just look for known viruses—it watches the system and its resources, looking for tactics that viruses are known to use. Not being protected is just dumb. Getting an infected file is as easy as downloading a movie from the Internet, so be cautious. Use one of the antivirus solution titles listed above and join their mailing lists to stay advised of current viruses in the wild.
Because of Mac OS X’s Unix core, many are concerned that remote users will gain access because of misconfigured or outdated services, and that access will be granted by software unintentionally. The main concern is a Trojan horse that can backdoor the computer, allowing remote access or sending system files without your knowledge. Set up your firewall to deny connections when you are not allowing others to connect to your computer. One of the easiest ways to ensure that you don’t get hacked is to put up a barrier ensuring that intruders can’t get close enough to try.
Besides viruses, Macintosh users have to be aware of spyware. Spyware are programs that run in the background, allowing someone to monitor user activity. This can include Trojan horses, remote administration type utilities, and keystroke loggers.
Keystroke loggers monitor and log everything typed on the keyboard. Hackers use these types of programs to capture user passwords, and others use them to snag confidential information, such as credit card numbers or social security information. These programs are generally undetected, and without the right knowledge of every keystroke logger out there, you can be left in the dark.
Trojan horses for the Macintosh often offer some sort of way back into the system. Once the Trojan has been installed, it remains undetected, just waiting for the remote user to make the connection. Users without a Internet or network connection need not worry about Trojans if in a isolated situation, but those who are in constant movement on the Internet should take extra steps to make sure their computer isn’t a playground for hackers.
Not all remote administration tools are considered Trojan horses. Programs such as Timbuktu and Apple Remote Desktop offer remote control over the computer, but in a commercial way. Usually when connections are established to one of these commercial products, the remote user can see that the user has connected to his computer, but there are some set to work in the background, so the present user need not be interrupted when another remote user is connected. Any of these programs, if installed without knowing what it does or knowing who installed it, can be a security risk—your computer could be waiting for people to connect to, administer, or control your Mac remotely.
You need to detect, isolate, and remove spyware and any unwanted administrator programs that might be plaguing your system without your knowledge. The job of MacScan is simple: Find any sort of software on your computer that can be construed as spyware, and detect any programs that offer remote administration functions you might be unaware of.
MacScan checks the hard drive for all known keyloggers for the Macintosh. It will also isolate any log files created by the keystroke loggers and move them to a secured location. Those log files could have years of your emails, confidential documents, passwords, and other affairs you don’t want recovered.
Ever keep changing your password and feel like someone keeps getting your new passwords every time? If a keystroke logger is installed, all the user has to do is view the log files and search for your old password and look at what follows: chances are, it’s the new password. If someone is capturing every keystroke, you’re no better off than if they knew your password in the first place. They could also be learning the passwords you commonly use for other systems or resources that require your authentication. Before typing in that secret information, make sure someone isn’t snooping on your keystrokes.
Included in the definition of spyware are Trojans and admin utilities. Many Trojans are configured to contact the attacker by email, notifying them of your IP address and other information that lets them know your computer is online and accessible. A firewall can protect intruders from coming in, but you will have to protect your machine to deny access to all ports, because you just can’t tell what port the Trojan may be set up for without analyzing it.
MacScan also detects these known Trojans, offering administrator functions remotely to the computer. Furthermore, when it finds any Trojan, it will notify the administrator of the configured settings, such as email address, passwords, and logins. For example, consider a Trojan horse—if it was set up to email [email protected], you know immediately that the intruder is linked to that email address. You also know what port the Trojan is set to communicate over and the password if any. With a little more research, you can try connecting to your own infected computer, or simply remove the spyware program all together.
Regarding valid system administrator tools such as Apple Remote Desktop and Timbuktu, MacScan does not divulge any passwords, and does not allow the user running the program to remove the admin tools. Instead, it will let the user know the software is running so she can take the appropriate action.
MacScan also has Mac OS X functionality, protecting the system so it is a security resource for everyone interested in keeping their privacy.
TIP
A trial version of MacScan can be downloaded at http://macscan.securemac.com/ and purchased from the same site. Becoming part of the MacScan user base ensures that you will be included in special deals, price cuts, and many free updates as new features are added.