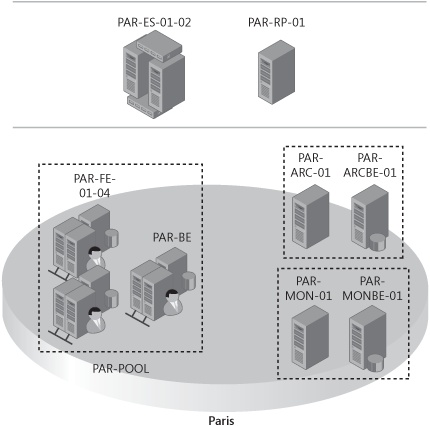
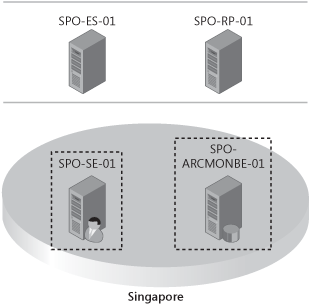
In Chapter 14, we presented a detailed planning process of a fictitious globally distributed company named Litware, Inc. The goal of this chapter is to demonstrate a deployment path for Litware, Inc. The focus is to explain the deployment sequence, starting with the preparatory steps. This chapter doesn’t provide step-by-step instructions to set up individual server roles. These are covered in various Microsoft Office Communications Server 2007 R2 deployment guides located at: http://go.microsoft.com/fwlink/?LinkID=133729.
On the Companion Media
Links to information related to this book are described in the section titled "Additional Resources" at the end of this chapter. These links are provided on this book’s companion CD.
Preparation is the most critical aspect of an Office Communications Server deployment. Certain steps, such as developing a server naming convention, preparing Domain Name System (DNS) entries, creating certificates, and installing and configuring network interface cards (NICs), should be done before proceeding with the actual deployment. This approach saves you from having to come back to the preparation of the environment after each step. The advantage in doing all the server preparation up front is that when you deploy server roles later in your deployment path (for example, when deploying the Edge Server after you have set up the pool), you do not have to ask DNS administrators to create additional entries for them because you already took care of this a few days earlier. In environments where multiple administrators are involved, the deployment process becomes smoother if adequate preparation is done in advance. This chapter demonstrates an example deployment path for large multisite deployments.
At first, it is important to define the naming convention for all servers that Litware, Inc. wants to deploy. It’s essential to choose a naming convention that is easily understandable to all organizations involved in the deployment because doing so decreases the possibility of miscommunication. As Table 15-1 shows, Litware, Inc. chooses a naming convention for its servers that easily identifies each of the Office Communications Server 2007 R2 roles and their locations.
Table 15-1. Litware, Inc.’s Server Naming Convention
NAMING CONVENTION | |
|---|---|
Server name | X-Y-Z |
Server-FQDN (fully qualified domain name) | x-y-z.litwareinc.com |
X | Server locations are abbreviated as follows: CHI = Chicago PAR = Paris SPO = Singapore |
Y | Server roles are abbreviated as follows:
|
Z | Role number (if this is missing, the server is a load balancer) |
Note that some exceptions to this naming convention exist for non–Office Communications Server 2007 R2 roles, such as load balancers.
If you have used Office Communications Server 2007, you will notice that a number of server roles seem to be missing from Table 15-1. The reason for this is that in Office Communications Server 2007 R2, the recommended topology has changed from an expanded Enterprise Edition topology to the collocated Enterprise Edition topology. In the collocated Enterprise Edition topology, all pool services are collocated on every front-end server. This greatly simplifies deployment and management.
Similarly, the recommended Edge Server topology is the collocated Edge Server. In fact, in Office Communications Server 2007 R2, you will not find the setup user interface (UI) to deploy an expanded Enterprise pool or the non-collocated Edge Servers. This option is available only via a command line tool called LcsCmd.exe. For more information, refer to the Office Communications Server 2007 R2 Command Line Reference documentation found at http://go.microsoft.com/fwlink/?LinkID=133728.
Table 15-2 through Table 15-4 show the server names, IP addresses, and FQDNs of the servers for the three Litware, Inc. sites.
Table 15-2. Litware, Inc. Server Names for Chicago
SERVER NAME | IP ADDRESS | SERVER FQDN | |
|---|---|---|---|
Consolidated Enterprise Edition (EE) pool name (load balancer Virtual Internet Protocol (VIP) for the pool) | CHI-POOL | 10.18.10.1 | chi-pool.litwareinc.com |
EE front-end server 1 | CHI-FE-01 | 10.18.10.2 | chi-fe-01.litwareinc.com |
EE front-end server 2 | CHI-FE-02 | 10.18.10.3 | chi-fe-02.litwareinc.com |
EE front-end server 3 | CHI-FE-03 | 10.18.10.4 | chi-fe-03.litwareinc.com |
EE front-end server 4 | CHI-FE-04 | 10.18.10.5 | chi-fe-04.litwareinc.com |
EE front-end server 5 | CHI-FE-05 | 10.18.10.6 | chi-fe-05.litwareinc.com |
EE front-end server 6 | CHI-FE-06 | 10.18.10.7 | chi-fe-06.litwareinc.com |
Back-end SQL cluster name | CHI-BE | 10.18.10.10 | chi-be.litwareinc.com |
Back-end Node 1 | CHI-BE-01 | 10.18.10.11 | chi-be-01.litwareinc.com |
Back-end Node 2 | CHI-BE-02 | 10.18.10.12 | chi-be-02.litwareinc.com |
Archiving Server | CHI-ARC-01 | 10.18.10.20 | chi-arc-01.litwareinc.com |
Archiving Server Back-end SQL | CHI-ARCBE-01 | 10.18.10.21 | chi-arcbe-01.litwareinc.com |
Monitoring Server | CHI-MON-01 | 10.18.10.22 | chi-mon-01.litwareinc.com |
Monitoring Server Back-end SQL | CHI-MONBE-01 | 10.18.10.23 | chi-monbe-01.litwareinc.com |
EE Director pool name (load balancer VIP for EE Director pool) | CHI-DIR | 10.18.10.32 | chi-dir.litwareinc.com |
EE Director front-end server 1 | CHI-DIR-01 | 10.18.10.30 | chi-dir-01.litwareinc.com |
EE Director front-end server 2 | CHI-DIR-02 | 10.18.10.31 | chi-dir-02.litwareinc.com |
Back-end SQL cluster name (for Director pool) | CHI-DIRBE | 10.18.10.40 | chi-dirbe.litwareinc.com |
Back-end Node 1 (for Director pool) | CHI-DIRBE-01 | 10.18.10.41 | chi-dirbe-0l.litwareinc.com |
Back-end Node 2 (for Director pool) | CHI-DIRBE-02 | 10.18.10.42 | chi-dirbe-02.litwareinc.com |
Exchange Unified Messaging (UM) Server | CHI-UM-01 | 10.18.10.70 | chi-um-01.contoso.com |
Load balancer VIP for collocated Edge Server (internal) | CHI-ES | 192.168.10.40 | chi-es.litwareinc.com |
Load balancer VIP for collocated Edge Server (external) | — | 64.65.66.1 (Access Edge Service) | sip.litwareinc.com |
64.65.66.2 (Web Conferencing Edge Service) | chi-wcs.litwareinc.com | ||
64.65.66.3 (A/V Edge Service) | chi-ave.litwareinc.com | ||
Edge Server 1 (internal NIC) | CHI-ES-01 | 192.168.10.41 | chi-es-01.litwareinc.com |
Edge Server 1 (external NIC) | — | 64.65.66.11 (Access Edge Service) | — |
64.65.66.21 (Web Conferencing Edge Service) | |||
64.65.66.31 (A/V Edge Service) | |||
Edge Server 2 (internal NIC) | CHI-ES-02 | 192.168.10.42 | chi-es-02.litwareinc.com |
Edge Server 2 (external NIC) | — | 64.65.66.12 (Access Edge Service) | — |
64.65.66.22 (Web Conferencing Edge Service) | |||
64.65.66.32 (A/V Edge Service) | |||
Mediation Server (internal NIC) | CHI-MED-01 | 10.18.10.50 | chi-med-01.litwareinc.com |
Mediation Server (external NIC) | CHI-MED-01 | 10.18.10.51 | chi-med-01.litwareinc.com |
HTTP reverse proxy server (internal NIC) | CHI-RP-01 | 192.168.10.60 | chi-rp-01.litwareinc.com |
HTTP reverse proxy server (external NIC) | — | 64.65.66.30 | chi-rp-01.litwareinc.com |
Table 15-3. Litware, Inc. Server Names for Paris
SERVER ROLE | SERVER NAME | IP ADDRESS | SERVER FQDN |
|---|---|---|---|
Consolidated EE Pool Name (load balancer VIP for the pool) | PARPOOL | 10.17.10.1 | par-pool.litwareinc.com |
EE front-end server 1 | PAR-FE-01 | 10.17.10.2 | par-fe-01.litwareinc.com |
EE front-end server 2 | PAR-FE-02 | 10.17.10.3 | par-fe-02.litwareinc.com |
EE front-end server 3 | PAR-FE-03 | 10.17.10.4 | par-fe-03.litwareinc.com |
EE front-end server 4 | PAR-FE-04 | 10.17.10.5 | par-fe-04.litwareinc.com |
Back-end SQL cluster name | PAR-BE | 10.17.10.10 | par-be.litwareinc.com |
Back-end Node 1 | PAR-BE-01 | 10.17.10.11 | par-be-01.litwareinc.com |
Back-end Node 2 | PAR-BE-02 | 10.17.10.12 | par-be-02.litwareinc.com |
Archiving Server | PAR-ARC-01 | 10.17.10.20 | par-arc-01.litwareinc.com |
Archiving Server Back-end SQL | PAR-ARCBE-01 | 10.17.10.21 | par-arcbe-01.litwareinc.com |
Monitoring Server | PAR-MON-01 | 10.17.10.22 | par-mon-01.litwareinc.com |
Monitoring Server Back-end SQL | PAR-MONBE-01 | 10.17.10.23 | par-monbe-01.litwareinc.com |
Load balancer VIP for collocated Edge Access Server (internal) | PAR-ES | 192.167.10.40 | par-es.litwareinc.com |
Load balancer VIP for collocated Edge Access Server (external) | — | 64.64.66.1 (Access Edge Service) | par-es-ext.litwareinc.com |
64.64.66.2 (Web Conferencing Edge Service) | par-wcs.litwareinc.com | ||
64.64.66.3 (A/V Edge Service) | par-ave.litwareinc.com | ||
Edge Server 1 (internal NIC) | PAR-ES-01 | 192.167.10.41 | par-es-01.litwareinc.com |
Edge Server 1 (external NIC) | — | 64.64.66.11 (Access Edge Service) | — |
64.64.66.21 (Web Conferencing Edge Service) | |||
64.64.66.31 (A/V Edge Service) | |||
Edge Server 2 (internal NIC) | PAR-ES-02 | 192.168.10.42 | par-es-02.litwareinc.com |
Edge Server 2 (external NIC) | — | 64.64.66.12 (Access Edge Service) | — |
64.64.66.22 (Web Conferencing Edge Service) | |||
64.64.66.32 (A/V Edge Service) | |||
HTTP reverse proxy server (internal NIC) | PAR-RP-01 | 192.167.10.60 | par-rp-01.litwareinc.com |
HTTP reverse proxy server (external NIC) | — | 64.64.66.30 | par-rp-01.litwareinc.com |
Table 15-4. Litware, Inc. Server Names for Singapore
SERVER ROLE | SERVER NAME | IP ADDRESS | SERVER FQDN |
|---|---|---|---|
SE Server (with archiving and monitoring servers collocated) | SPO-SE-01 | 10.15.10.1 | spo-se-01.litwareinc.com |
Archiving and Monitoring Server back-end SQL | SPO-ARCMONBE-01 | 10.15.10.21 | spo-arcmonbe-01.litwareinc.com |
Edge Server (internal NIC) | SPO-ES-01 | 192.165.10.41 | spo-ep-01.litwareinc.com |
Edge Server (external NIC) | — | 64.62.66.11 (Access Edge Service) | spo-es-ext.litwareinc.com |
64.62.66.21 (Web Conferencing Edge Service) | spo-wcs.litwareinc.com | ||
64.62.66.31 (A/V Edge Service) | spo-ave.litwareinc.com | ||
HTTP reverse proxy server (internal NIC) | SPO-RP-01 | 192.165.10.60 | spo-rp-01.litwareinc.com |
HTTP Reverse Proxy Server (external NIC) | — | 64.62.66.30 | spo-rp-01.litwareinc.com |
Note
Because some of the users in the Chicago site are enabled for Voice in addition to the regular server roles, the Mediation Server, Session Initiation Protocol (SIP)/Public Switched Telephone Network (PSTN) gateway, and Exchange UM Server are also deployed in this site. Also note that Litware, Inc. decided to go with an Enterprise Edition pool to serve as a Director for higher availability and better performance.
Note
Because the user population at the Singapore site is small, Litware, Inc. decided to go with a Standard Edition server with Archiving and Monitoring Servers collocated on the same physical machine. Also note that for the Singapore site, the external IP addresses for the Edge Server also need an FQDNs assigned. This is because there is no external load balancer in Singapore, and therefore the external IP addresses have to be in the external DNS.
Each Litware, Inc. server role requires dedicated server hardware, as described in the Office Communications Server 2007 R2 Planning Guide. When preparing server hardware for an Office Communications Server 2007 R2 deployment, the required number of NICs in each server should be checked. Table 15-5 through Table 15-19, found later in this chapter, show where Litware, Inc. needs multiple NICs as required by the server roles.
Table 15-5. Summary of Chicago Infrastructure Requirements
SERVER ROLE | NAME | EXTERNAL DNS NAME (IP ADDRESS) | INTERNAL DNS NAME (IP ADDRESS) | EXTERNAL FIREWALL PORT (DIRECTION) | INTERNAL FIREWALL PORT (DIRECTION) |
|---|---|---|---|---|---|
Edge Server—Access Edge Service (load balancer) | CHI-ES | sip.litwareinc.com VIP = (64.65.66.1)_sip._tls. domain (SRV) 443 sip.litwareinc.com_sipfederation-tls._tcp.domain (SRV) 5061 sip.litwareinc.com | chi-es.litwareinc.com VIP = (192.168.10.40) | 443 Transmission Control Protocol (TCP) (inbound) (Internet → Access Edge Service for Remote User Access) 5061 TCP (both) (Internet ↔ Access Edge Service for federation) | 5061 TCP (both) (Office Communications Server 2007 R2 pool ↔ Access Edge Service) |
Edge Server—Web Conferencing Edge Service (load balancer) | CHI-ES | chi-wce.litwareinc.com VIP = (64.65.66.2) | N/A (internal edge of Web Conferencing Service can’t be behind a load balancer | 443 TCP (inbound) (Internet → Web Conferencing Edge Server) | 8057 TCP (outbound) (Office Communications Server 2007 R2 pool → Web Conferencing Edge Service) |
Edge Server—A/V Edge Service (load balancer) | CHI-ES | chi-ave.litwareinc.com VIP = (64.65.66.3) | chi-es.litwareinc.com VIP = (192.168.10.40) | 443 TCP (inbound) (Internet → A/V Edge Service) 3478 User Datagram Protocol (UDP) (inbound) (Internet → A/V Edge Service) 50,000-59,999 TCP & UDP (both) (Internet ↔ A/V Edge Service) | 443 TCP (outbound) (Internal Net [all IPs] → A/V Edge Service) 3478 UDP (outbound) (internal Net [all IPs] → A/V Edge Service) 5062 TCP (outbound) (internal Net [all IPs] → A/V Edge Service) |
NODES (EDGE SERVER) | |||||
Node1 | CHI-ES-01 | N/A (64.65.66.11, 64.65.66.21, 64.65.66.31) | chi-es-01.litwareinc.com (192.168.10.41) | N/A | N/A |
Node2 | CHI-ES-02 | N/A (64.65.66.12, 64.65.66.22, 64.65.66.32) | chi-es-02.litwareinc.com (192.168.10.42) | N/A | N/A |
HTTP reverse proxy server | CHI-RP-01 | chi-rp-0l.litwareinc.com (64.65.66.30) | chi-rp-01.litwareinc.com (192.168.10.60) | 443 TCP (inbound) Internet → HTTP reverse proxy server | 443 TCP (inbound) HTTP reverse proxy server → Office Communications Server 2007 R2 pool |
EE Director pool (load balancer) | CHI-DIR | N/A | chi-dir.litwareinc.com (10.18.10.32) | N/A | 5061 TCP (both) (Access Edge [internal load balancer VIP] ↔ Director) |
EE DIRECTOR FRONT-END NODES | |||||
Node1 | CHI-DIR-01 | N/A | chi-dir-01.litwareinc.com (10.18.10.30) | N/A | N/A |
Node2 | CHI-DIR-02 | N/A | chi-dir-02.litwareinc.com (10.18.10.31) | N/A | N/A |
Back-end SQL Server for Director pool (cluster name) | SQL-DIRBE | N/A | chi-dirbe.litwareinc.com VIP =(10.18.10.40) | N/A | N/A |
BACK-END SQL NODES (FOR DIRECTOR POOL) | |||||
Node 1 | CHI-DIRBE-01 | N/A | chi-dirbe-01.litwareinc.com (10.18.10.41) | N/A | N/A |
Node 2 | CHI-DIRBE-02 | N/A | chi-dirbe-02.litwareinc.com (10.18.10.42) | N/A | N/A |
EE pool (load balancer) | CHI-POOL | N/A | chipool.litwareinc.com VIP = (10.18.10.1)_sipinternal._tcp.domain (SRV) 5061 chi-pool.litwareinc.com_sipinternaltls_tcp.domain (SRV) 5061 chipool.litwareinc.com | N/A | N/A |
EE FRONT ENDS | |||||
Node 1 | CHI-FE-01 | N/A | chi-fe-01.litwareinc.com (10.18.10.2) | N/A | N/A |
Node 2 | CHI-FE-02 | N/A | chi-fe-02.litwareinc.com (10.18.10.3) | N/A | N/A |
Node 3 | CHI-FE-03 | N/A | chi-fe-03.litwareinc.com (10.18.10.4) | N/A | N/A |
Node 4 | CHI-FE-04 | N/A | chi-fe-04.litwareinc.com (10.18.10.5) | N/A | N/A |
Node 5 | CHI-FE-05 | N/A | chi-fe-05.litwareinc.com (10.18.10.6) | N/A | N/A |
Node 6 | CHI-FE-06 | N/A | chi-fe-06.litwareinc.com (10.18.10.7) | N/A | N/A |
Back-end SQL Server (cluster name) | SQL-BE | N/A | chi-be.litwareinc.com VIP = (10.18.10.10) | N/A | N/A |
BACK-END SQL NODES | |||||
Node 1 | CHI-BE-01 | N/A | chi-be-01.litwareinc.com (10.18.10.11) | N/A | N/A |
Node 2 | CHI-BE-02 | N/A | chi-be-02.litwareinc.com (10.18.10.12) | N/A | N/A |
Mediation Server | CHI-MED-01 | chi-med-01.litwareinc.com (10.18.10.51) | chi-med-01.litwareinc.com (10.18.10.50) | N/A | N/A |
Archiving Server | CHI-ARC-01 | N/A | chi-arc-01.litwareinc.com (10.18.10.20) | N/A | N/A |
Archiving Server Back-End SQL Server | CHI-ARCBE-01 | N/A | chi-arcbe-01.litwareinc.com (10.18.10.21) | N/A | N/A |
Monitoring Server | CHI-MON-01 | N/A | chi-mon-01.litwareinc.com (10.18.10.22) | N/A | N/A |
Monitoring Server Back-End SQL Server | CHI-MONBE-01 | N/A | chi-monbe-01.litwareinc.com (10.18.10.23) | N/A | N/A |
Litware, Inc. decided to enable several scenarios with a high level of redundancy for its users. This resulted in a high number of individual servers and server roles needing to be deployed. Figure 15-1 through Figure 15-3 provide a graphical view of the target deployment for each of the Litware, Inc. sites.
Litware, Inc. decided to install the entire Office Communications Server 2007 R2 deployment in a single domain (Litware, Inc.com) because domain controllers are available at each of the sites. The Office Communications Server 2007 R2 Active Directory Guide, found at http://go.microsoft.com/fwlink/?LinkID=133727, explains in detail the steps that have to be taken to prepare Active Directory for an Office Communications Server 2007 R2 deployment.
In the future, Litware, Inc. would like to add Office Communications Servers in a different Active Directory domain at a new site. Because that site doesn’t have good connectivity to the root domain, Litware, Inc. decided to put its global settings in the Configuration Partition rather than in the System container.
Important
Active Directory administrators need to have good control over Active Directory schema updates because these events can affect the entire enterprise’s directory infrastructure. Therefore, you’ll need to coordinate with the Active Directory administrators to prepare Active Directory in an Office Communications Server 2007 R2 deployment. Depending on the enterprise and its business, there can be periods in which an Active Directory schema update is not allowed by company policy and therefore the Office Communications Server 2007 R2 deployment can be delayed. The effects of such policies on the deployment schedule need to be incorporated into the deployment plan.
In large enterprises, the configurations of DNS, certificates, and firewalls are sometimes, from an organizational perspective, separate from the administrators who install and configure Office Communications Servers. Therefore, the administrators responsible for deploying Office Communications Servers must collaborate with other administrators within the company.
As part of Litware, Inc.’s Office Communications Server 2007 R2 planning process, the number of individual server roles has been identified, as shown in Chapter 14. This enables Litware, Inc. to summarize all DNS and firewall port requirements so that the preparation of the surrounding infrastructure can be done at one time before the actual deployment takes place. Table 15-5 through Table 15-19 summarize all preparations that need to be done for Litware, Inc.’s Office Communications Server 2007 R2 deployment. In addition, a detailed view with all the infrastructure requirements—including certificate requirements for Chicago—will be shown later in the chapter.
Table 15-5 provides a summary of Litware, Inc.’s infrastructure requirements for Chicago.
Note that in Table 15-5, a total of 12 IP addresses are used, which point to the same two physical Edge Servers. Here is a summary to further clarify the addressing scheme for these servers:
One IP address for the Access Edge VIP (externally) = 64.65.66.1
One IP address for the Web Conferencing Edge VIP (externally) = 64.65.66.2
One IP address for the A/V Edge VIP (externally) = 64.65.66.3
One IP address for the Edge Server VIP (internally) shared by the Access Edge and A/V Edge = 192.168.10.40
Two IP addresses for the Access Edge (externally) = 64.65.66.11 and 64.65.66.12 (these addresses are the node addresses, and the VIPs point to them)
Two IP addresses for the Web Conferencing Edge (externally) = 64.65.66.21 and 64.65.66.22 (these addresses are the node addresses, and the VIPs point to them)
Two IP addresses for the A/V Edge (externally) = 64.65.66.31 and 64.65.66.32 (these addresses are the node addresses, and the VIPs point to them)
Two IP addresses for the Edge Server shared by Access Edge, Web Conferencing Edge, and A/V Edge (internally) = 192.168.10.41 and 192.168.10.42
Note that the internal edge of the Web Conferencing Service cannot be behind a load balancer. The individual FQDNs of two Web Conferencing Service boxes (chi-es-01.litwareinc.com and chi-es-02.liwareinc.com) must be addressable by all the Web Conferencing Services in the internal network.
Table 15-6 through Table 15-8 provide detailed views of the infrastructure requirements for the Edge Server arrays in the Chicago perimeter network. An array is a set of servers running the same server roles.
Table 15-6. Details for Chicago External Load Balancer for Co-located Edge Servers
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
LOAD BALANCER | |||
Access Edge | sip.litwareinc.com | Perimeter network | Externally facing hardware load balancer with 3 VIPs |
Web Conferencing Edge | chi-wce.litwareinc.com | Perimeter network | Externally facing hardware load balancer with 3 VIPs |
A/V Edge | chi-ave.litwareinc.com | Perimeter network | Externally facing hardware load balancer with 3 VIPs |
VIPS | |||
Access Edge VIP (external) | (1) 64.65.66.1 | 100-megabit Full | VIP address on the external load balancer for array of Access Edge Services |
Web Conferencing Edge VIP (external) | (1) 64.65.66.2 | 100-megabit Full | VIP address on the external load balancer for array of Web Conferencing Edge Services |
A/V Edge VIP (external) | (1) 64.65.66.3 | 100-megabit Full | VIP address on the external load balancer for array of A/V Edge Services |
PORTS | |||
Firewall (external) | 443 TCP | Inbound | Traffic from Internet → Access Edge Service, Web Conferencing Edge Service, and A/V Edge Service external load balancer VIPs (sip.litwareinc.com, chi-wce.litware.com, and chi-ave.litware.com, respectively) |
5061 TCP | Bi-directional | Traffic to/from Internet ↔ Access Edge Service external load balancer VIP (sip.litwareinc.com) | |
3478 UDP | Inbound | Traffic from Internet → A/V Edge Service external load balancer VIP (chi-ave.litwareinc.com) | |
50,000-59,999 TCP and UDP | Bi-directional | Traffic to/from Internet ↔ A/V Edge Service external load balancer VIP (chi-ave.litwareinc.com); if you don’t want to open the entire range of ports from 50,000 to 59,999, allow 6 ports for each concurrent external user | |
Certificates | |||
Certificate Name (CN)/Subject Name (SN) | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | N/A | N/A | N/A |
DNS (External) | |||
(A) | sip.litwareinc.com | 64.65.66.1 | |
(A) | chi-wce.litwareinc.com | 64.65.66.2 | |
(A) | chi-ave.litware.com | 64.65.66.3 | |
Table 15-7. Details for Chicago—Internal Load Balancer for Co-located Edge Servers
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Load Balancer | |||
Access Edge and A/V Edge (shared) | chi-es.litwareinc.com | Perimeter network | Internally facing hardware load balancer with 1 VIP. Note that the internal edge of the Web Conferencing Edge Services is not load balanced. |
VIPs | |||
Access Edge and A/V Edge VIP (internal) | (1) 192.168.10.40 | 100-megabit Full | Virtual IP address on the internal load balancer for an array of Edge Servers (shared by all Edge Services). |
Ports | |||
Firewall (internal) | 8057 TCP | Outbound | Traffic from Data Conferencing Servers of the EE pool → Web Conferencing Edge Service Node1 (chi-es-01.litwareinc.com) and Node2 (chi-es-02.litware-inc.com). |
5061 TCP | Bi-directional | Traffic to/from Edge Server internal load balancer VIP (chi-es.litwareinc.com) ↔ Director load balancer VIP (chi-dir.litwareinc.com) and to Web Conferencing Servers and A/V Conferencing Servers in EE pool. | |
443 TCP | Outbound | Traffic from Internal Network (all) →A/V Edge Service internal load balancer VIP (chi-es.litwareinc.com). | |
3478 UDP | Outbound | Traffic from internal network (all) →A/V Edge Service internal load balancer VIP (chi-es.litwareinc.com). | |
5062 TCP | Outbound | Traffic from internal network (all) →A/V Edge Service internal load balancer VIP (chi-es.litwareinc.com). Note that the internal firewall rule must enable traffic from any computer on the internal network that will be involved in A/V calls or A/V conferencing to reach the A/V Edge Service internal load balancer VIP over all three ports. | |
Certificates | |||
CN/SN | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | chi-es.litwareinc.com | 192.168.10.40 | N/A |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Table 15-8. Details for Chicago Edge Server Nodes
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
Edge Server (Access Edge Service, Web Conferencing Edge Service, A/V Edge Service) | |||
Node1 | CHI-ES-01 | Perimeter network | Workgroup servers in the perimeter network. Each node is running Access Edge Service, Web Conferencing Edge Service, and A/V Edge Service. |
Node2 | CHI-ES-02 | Perimeter network | |
NICs | |||
Node1 (internal-facing) | (1) 192.168.10.41 | 100-megabit Full | Shared by all Edge Services |
Node2 (internal-facing) | (1) 192.168.10.42 | 100-megabit Full | Shared by all Edge Services |
Node1 (external-facing) | (1/3) 64.65.66.11 | 100-megabit Full | Used by Access Edge Service. Can be behind a Network Address Translation (NAT) or port-forwarding firewall. |
(2/3) 64.65.66.21 | 100-megabit Full | Used by Web Conferencing Edge Service. Can be behind a NAT or port-forwarding firewall. | |
(3/3) 64.65.66.31 | 100-megabit Full | Used by A/V Edge Service. Must be a publicly addressable IP address. Can be behind a port-forwarding firewall but not translated with NAT. Note that the default gateway should be on the external NIC in each node and point to the Internet, or you might not get audio on remote Microsoft Office Communicator 2007 R2/Office Communicator Phone Edition calls. | |
Node2 (external-facing) | (1/3) 64.65.66.12 | 100-megabit Full | Used by Access Edge Service. Can be behind a NAT or port-forwarding firewall. |
(2/3) 64.65.66.22 | 100-megabit Full | Used by Web Conferencing Edge Service. Can be behind a NAT or port-forwarding firewall. | |
(3/3) 64.65.66.32 | 100-megabit Full | Used by A/V Edge Service. Must be a publicly addressable IP address. Can be behind a port-forwarding firewall but not translated with NAT. | |
Ports | |||
Firewall (internal) | N/A | N/A | All Edge Services on the Edge Server array will use ports opened for those services on the internal load balancer VIP (sip-es.litwareinc.com). |
Firewall (external) | N/A | N/A | All Edge Services on the Edge Server array will use ports opened for those services on the external load balancer VIPs (sip.litwareinc.com, chi-wce.litwareinc.com, chi-ave.litwareinc.com). |
Certificates (internal) | |||
Internal certificate shared by all Edge Services (for both nodes) | CN/SN=chi-es.litwareinc.com | Enhanced Key Usage (EKU): Server/Client | Used for client/server Transport Layer Security (TLS)/Mutual Transport Layer Security (MTLS). |
Certificates (external) | |||
External certificate assigned to Access Edge Service (for both nodes) | CN/SN=sip.litware-inc.com | EKU: Server/ Client | First entry in Subject Alternative Name (SAN) must match the CN/SN of certificate. |
SAN=sip.litwareinc.com; sip.additionalSIPDomainName.com | If federation is enabled, the certificate must be issued by a public CA. Same physical certificate must be present on both nodes. The SAN must contain additional entries for each SIP domain that federated partners and/or remote users will access. | ||
External certificate assigned to Web Conferencing Edge Service (for both nodes) | CN/SN=chi-wce.litwareinc.com | EKU: Server/ Client | The same certificate can be applied to both nodes. If federation is enabled, the certificate must be issued by a public CA. |
Authentication certificate assigned to the A/V Edge Service (for both nodes) | CN/SN=chi-ave.litwareinc.com | EKU: Server | A certificate is used to create Media Relay Access Server (MRAS) access tokens. They are not exposed to the client. The same physical certificate must be present on both nodes. |
DNS (Internal) | |||
(A) | chi-es-01.litwareinc.com | 192.168.10.41 | This is the internal FQDN of the Edge Server (Node1). |
(A) | chi-es-02.litwareinc.com | 192.168.10.42 | This is the internal FQDN of the Edge Server (Node2). |
DNS (External) | |||
(A) | N/A | N/A | External NICs in Node1 and Node2 are externally accessible only via the respective load balancer VIPs; use internal IP addresses for managing each node. |
(SRV) | _sip._tls.litwareinc.com _sipfederationtls._tcp.litwareinc.com | _tls for port 443 _tcp for port 5061 | |
Table 15-9 provides a detailed view of the infrastructure requirements for the HTTP reverse proxy server in the Chicago perimeter network.
Table 15-9. Details for Chicago HTTP Reverse Proxy Server
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
HTTP reverse proxy server | CHI-RP-01 | Perimeter network | Workgroup server running Internet Security and Acceleration (ISA) Standard Edition in the perimeter network. |
NICs | |||
Internal | (1) 192.168.10.60 | 100-megabit Full | |
External | (1) 64.65.66.30 | 100-megabit Full | The HTTP Reverse Proxy Server role can be behind a NAT or port-forwarding firewall. |
Ports | |||
Firewall (internal) | 443 TCP | Inbound | Traffic from HTTP reverse proxy server (chi-rp-01.litwareinc.com) → Office Communications Server 2007 R2 Enterprise Edition load balancer VIP (chi-pool.litwareinc.com). |
Firewall (external) | 443 TCP | Inbound | Traffic from Internet HTTP → reverse proxy server (chi-rp-01.litwareinc.com). |
Certificates | |||
Certificate assigned on reverse proxy | CN/SN=chi-rp-01.litwareinc.com | EKU: Server | Exportable Machine certificate: used for client/server TLS/MTLS. |
DNS (Internal) | |||
(A) | chi-rp-01.litwareinc.com | 192.168.10.60 | This is the internal FQDN of the HTTP reverse proxy server. |
DNS (External) | |||
(A) | chi-rp-01.litwareinc.com | 64.65.66.30 | This is the external FQDN of the HTTP reverse proxy server. |
Note
That if internal and external facing Internet Security and Acceleration (ISA) Server NICs reside in the perimeter network, port 443 needs to be open inbound from the ISA Server to the Office Communications Server 2007 R2 Enterprise Edition Load Balancer VIP.
Table 15-10 and Table 15-11 provide detailed views of the infrastructure requirements for the Director servers in Chicago.
Table 15-10. Details for Chicago Load Balancer for Office Communications Server 2007 R2 Enterprise Edition Director Pool
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Load Balancer | |||
Office Communications Server R2 Enterprise Edition pool | chi-dir.litwareinc.com | Internal network | Hardware load balancer with 1 VIP. |
VIPs | |||
EE Director pool VIP (external) | (1) 10.18.10.32 | 100-megabit Full | VIP Address on the load balancer for EE Director pool. |
Ports | |||
Firewall (internal) | 5061 TCP | Bi-directional | Traffic to/from Access Edge Server internal load balancer VIP (chi-es.litwareinc.com) ↔ EE Director pool load balancer VIP (chi-dir.litwareinc.com). |
Firewall (external) | N/A | N/A | N/A |
Certificates | |||
N/A | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | N/A | N/A | N/A |
DNS (External) | |||
(A) | chi-dir.litwareinc.com | 10.18.10.32 | Note that this DNS entry must be made both in the internal corp network as well as the perimeter network so that it is resolvable by internal EE servers as well as the Edge Servers. |
Table 15-11. Details for Chicago EE Director Pool
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
EE Director Pool Front-End Server | |||
Node1 Node2 | CHI-DIR-01 CHI-DIR-02 | Internal network Internal network | Domain members on the internal network. Each node is running a copy of Office Communications Server 2007 R2 Enterprise Edition. |
NICs | |||
Node1 | (1) 10.18.10.30 | 100-megabit Full | |
Node2 | (1) 10.18.10.31 | ||
100-megabit Full | |||
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
Certificate assigned to both front-end nodes | CN/SN=chi-dir.litwareinc.com | EKU: Server | |
DNS (Internal) | |||
(A) | chi-dir-01.litwareinc.com | 10.18.10.30 | This is the internal FQDN of each front-end server in the EE Director pool. |
(A) | chi-dir-02.litwareinc.com | 10.18.10.31 | |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Note that the infrastructure requirements for the back-end SQL cluster for the Director pool are not described in detail. These requirements are the same as the back-end SQL cluster for the EE pool described in Table 15-14.
Table 15-12 and Table 15-13 provide detailed views of the infrastructure requirements for the expanded Office Communications Server 2007 R2 Enterprise Edition pool in Chicago.
Table 15-12. Details for Chicago Load Balancer for Office Communications Server 2007 R2 Enterprise Edition Pool
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Load Balancer | |||
Office Communications Server 2007 R2 Enterprise Edition pool | chi-pool.litwareinc.com | Internal network | Hardware load balancer with 1 VIP; accessed by way of the Director. |
VIPs | |||
EE pool VIP (internal) | (1) 10.18.10.1 | 100-megabit Full | Virtual IP address on the load balancer for the Office Communications Server 2007 R2 Enterprise Edition front-end servers. |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
CN/SN | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | chi-pool.litwareinc.com | 10.18.10.1 | |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Table 15-13. Details for the Chicago Office Communications Server 2007 R2 Enterprise Edition Front-End Servers
QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE | |
|---|---|---|---|
Server | |||
EE Front-End Server | |||
Node1 | chi-fe-01.litwareinc.com | Internal network | Domain member Office Communications Server 2007 R2 Enterprise Edition expanded pool. |
Node2 | chi-fe-02.litwareinc.com | Internal network | |
Node3 | chi-fe-03.litwareinc.com | Internal network | Each front-end server in the pool contains all the server roles that belong to an EE pool (for example, Front End role, Web Conferencing Server role, A/V Conferencing Server role, Web Component Server role) and is configured exactly the same way. The pool name is CHI-POOL. |
Node4 | chi-fe-04.litwareinc.com | Internal network | |
Node5 | chi-fe-05.litwareinc.com | Internal network | |
Node6 | chi-fe-06.litwareinc.com | Internal network | |
NICs | |||
Node1 (internal) | (1) 10.18.10.2 | 100Mb Full | |
Node2 (internal) | (1) 10.18.10.3 | 100Mb Full | |
Node3 (internal) | (1) 10.18.10.4 | 100Mb Full | |
Node4 (internal) | (1) 10.18.10.5 | 100Mb Full | |
Node5 (internal) | (1) 10.18.10.6 | 100Mb Full | |
Node6 (internal) | (1) 10.18.10.7 | 100Mb Full | |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
Certificate assigned to every front-end node | CN/SN = chi-pool.litwareinc.com | EKU: Server | Used for client/server TLS/MTLS. |
SAN = chi-pool.litwareinc.com sip.litwareinc.com | sip.additionalSIPDomainName.com | The first entry in the SAN must match the CN/SN of the certificate. The SAN must contain additional entries for each SIP domain that federated partners and/or remote users will access. | |
DNS (Internal) | |||
(A) | chi-fe-01.litwareinc.com | 10.18.10.2 | This is the internal FQDN of each EE front-end server in the pool. |
(A) | chi-fe-02.litwareinc.com | 10.18.10.3 | |
(A) | chi-fe-03.litwareinc.com | 10.18.10.4 | |
(A) | chi-fe-04.litwareinc.com | 10.18.10.5 | |
(A) | chi-fe-05.litwareinc.com | 10.18.10.6 | |
(A) | chi-fe-06.litwareinc.com | 10.18.10.7 | |
(SRV) | _sipinternal._tcp.litwareinc.com | _tcp for port 5061 | |
_sipinternaltls._tcp.litwareinc.com | _tcp for port 5061 | ||
DNS (External) | |||
(A) | N/A | The Office Communications Server 2007 R2 EE pool is not addressable externally accept via the Access Edge Service/Director pool. | |
Table 15-14 provides a detailed view of the infrastructure requirements for the back-end SQL cluster in the Chicago pool.
Table 15-14. Details for Chicago Back-End SQL Cluster
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
SQL Server cluster | chi-be.litwareinc.com | Internal network | This is the virtual name for the SQL Server cluster. |
Node1 | CHI-BE-01 | Internal network | Domain member SQL Server (EE pool back end). |
Node2 | CHI-BE-02 | Internal network | Domain member SQL Server (EE pool back end). |
NICs | |||
Node1 (internal) | (1) 10.18.10.11 | 100-megabit Full | |
Node2 (internal) | (1) 10.18.10.12 | 100-megabit Full | |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
N/A | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | chi-be.litwareinc.com | 10.18.10.10 | This is the internal FQDN of the SQL Server cluster. |
(A) | chi-be-01.litwareinc.com | 10.18.10.11 | |
(A) | chi-be-02.litwareinc.com | 10.18.10.12 | |
DNS (External) | |||
(A) | N/A | The SQL Server is not addressable externally. | |
Table 15-15 provides detailed views of the infrastructure requirements for the Archiving Server in Chicago.
Table 15-15. Details for the Chicago Archiving Server
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
Archiving | CHI-ARC-01 | Internal net-work | Domain member. |
NiCs | |||
Internal | (1) 10.18.10.20 | 100-megabit Full | |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
N/A | N/A | N/A | The Archiving Server doesn’t require a certificate |
DNS (Internal) | |||
(A) | chi-arc-01.litwareinc.com | 10.18.10.20 | |
DNS (External) | |||
(A) | N/A | N/A | N/A |
Table 15-16 provides a detailed view of the infrastructure requirements for the Archiving Server’s back-end SQL Server cluster.
Table 15-16. Details for Chicago Back-End SQL Cluster
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
SQL | CHI-ARCBE-01 | Internal network | Domain member SQL Server. |
NICs | |||
Internal | (1) 10.18.10.21 | 100-megabit Full | |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Certificates | |||
N/A | N/A | N/A | N/A |
DNS (Internal) | |||
(A) | chi-arcbe.litwareinc.com | 10.18.10.21 | This is the internal FQDN of the SQL Server. |
DNS (External) | |||
(A) | N/A | The SQL Server is not addressable externally. | |
Note that the infrastructure requirements for the Monitoring Server and the Monitoring Server back-end SQL are exactly the same as those of the Archiving Server and the Archiving Server back-end SQL.
Table 15-17 provides a detailed view of the infrastructure requirements for the Mediation Server in Chicago.
Table 15-17. Details for the Chicago Mediation Server
ROLE/FEATURE | QUANTITY/VALUE(S) | LOCATION/SETTING | NOTE/EXAMPLE |
|---|---|---|---|
Server | |||
Mediation | chi-med-01.litwareinc.com | Internal network | Domain member running the Office Communications Server 2007 R2 Mediation Server role. |
NICs | |||
Internal | (1) 10.18.10.50 | 100-megabit Full | |
External | (1) 10.18.10.51 | 100-megabit Full | Carries unsecured PSTN traffic to/from the IP/PSTN gateway. Enables 64 Kbps per concurrent PSTN call. |
Ports | |||
Firewall (internal) | N/A | N/A | N/A |
Firewall (gateway network) | N/A | N/A | N/A |
Certificates | |||
Certificate assigned to the Mediation Server | CN/SN =chi-med-01.litwareinc.com | EKU: Server | Used for Server MTLS/ Secure Real-Time Protocol (SRTP). |
DNS (Internal) | |||
(A) | chi-med-01.litwareinc.com | 10.18.10.50 | This is the internal FQDN of the Mediation Server. (Ping resolves to this IP address.) |
(A) | chi-med-01.litwareinc.com | 10.18.10.51 | This is the IP address used for the Mediation Server ↔ SIP/PSTN gateway communication. Considered an external interface by the Mediation Server. |
DNS (External) | |||
(A) | N/A | ||
Table 15-18 contains the summary view of all infrastructure requirements for the deployment in Paris.
Table 15-18. Summary of Paris Infrastructure Requirements
SERVER ROLE | NAME | EXTERNAL DNS NAME (IP ADDRESS) | INTERNAL DNS NAME (IP ADDRESS) | EXTERNAL FIREWALL PORT (DIRECTION) | INTERNAL FIREWALL PORT (DIRECTION) |
|---|---|---|---|---|---|
Edge Server—Access Edge Service (load balancer) | PAR-ES | par-es-ext.litwareinc.com VIP =(64.64.66.1) | par-es.litwareinc.com VIP = (192.167.10.40) | 443 TCP (inbound) (Internet → Access Edge Service for remote access) 5061 TCP (both) (Internet ↔ Access Edge Service for federation) | 5061 TCP (both) (Office Communications Server 2007 R2 pool ↔ Access Edge Service) |
Edge Server—Web Conferencing Edge Service | PAR-ES | par-wce.litwareinc.com VIP = (64.64.66.2) | N/A | 443 TCP (inbound) (Internet → Web Conferencing Edge Server) | 8057 TCP (outbound) (Office Communications Server 2007 R2 pool → Web Conferencing Edge Service) |
Edge Server—A/V Edge Service (load balancer) | PAR-ES | par-ave.litwareinc.com VIP = (64.64.66.3) | par-es.litwareinc.com VIP = (192.167.10.40) | 443 TCP (inbound) (Internet → A/V Edge Service) 3478 UDP (inbound) (Internet → A/V Edge Service) 50,000-59,999 TCP & UDP (both) (Internet ↔ A/V Edge Service) | 443 TCP (outbound) (Internal Net [all IPs] → A/V Edge Service) 3478 UDP (outbound) (internal Net [all IPs] → A/V Edge) 5062 TCP (outbound) (internal Net [all IPs] → A/V Edge Service) |
NODES (EDGE SERVER) | |||||
Node1 | PAR-ES-01 | N/A (64.64.66.11, 64.64.66.21, 64.64.66.31) | par-es-01.litwareinc.com (192.167.10.41) | N/A | N/A |
Node2 | PAR-ES-02 | N/A (64.64.66.12, 64.64.66.22, 64.64.66.32) | par-es-02.litwareinc.com (192.167.10.42) | N/A | N/A |
HTTP reverse proxy server | PAR-RP-01 | par-rp-01.litwareinc.com (64.64.66.30) | par-rp-01.litwareinc.com (192.167.10.60) | 443 TCP (inbound) Internet → HTTP reverse proxy server | 443 TCP (inbound) HTTP reverse proxy server → Office Communications Server 2007 R2 pool |
EE pool (load balancer) | PAR-POOL | N/A | chipool.litwareinc.com VIP = (10.17.10.1) | N/A | N/A |
EE FRONT ENDS | |||||
Node1 | PAR-FE-01 | N/A | par-fe-01.litwareinc.com (10.17.10.2) | N/A | N/A |
Node2 | PAR-FE-02 | N/A | par-fe-02.litwareinc.com (10.17.10.3) | N/A | N/A |
Node3 | PAR-FE-03 | N/A | par-fe-03.litwareinc.com (10.17.10.4) | N/A | N/A |
Node4 | PAR-FE-04 | N/A | par-fe-04.litwareinc.com (10.17.10.5) | N/A | N/A |
Back-end SQL Server (cluster name) | SQL-BE | N/A | par-be.litwareinc.com VIP = (10.17.10.10) | N/A | N/A |
BACK-END SQL NODES | |||||
Node 1 | PAR-BE-01 | N/A | par-be-01.litwareinc.com (10.17.10.11) | N/A | N/A |
Node 2 | PAR-BE-02 | N/A | par-be-02.litwareinc.com (10.17.10.12) | N/A | N/A |
Archiving Server | PAR-ARC-01 | N/A | par-arc-01.litwareinc.com (10.17.10.20) | N/A | N/A |
Archiving Server back-end SQL Server | PAR-ARCBE-01 | N/A | par-arcbe-01.litwareinc.com (10.17.10.21) | N/A | N/A |
Monitoring Server | PAR-MON-01 | N/A | par-mon-01.litwareinc.com (10.17.10.22) | N/A | N/A |
Monitoring Server back-end SQL Server | PAR-MONBE-01 | N/A | par-monbe-01.litwareinc.com (10.17.10.23) | N/A | N/A |
Table 15-19 contains the summary view of all infrastructure requirements for the deployment in Singapore.
Table 15-19. Summary of Singapore Infrastructure Requirements
SERVER ROLE | NAME | EXTERNAL DNS NAME (IP ADDRESS) | INTERNAL DNS NAME (IP ADDRESS) | EXTERNAL FIREWALL PORT (DIRECTION) | INTERNAL FIREWALL PORT (DIRECTION) |
|---|---|---|---|---|---|
Edge Server—Access Edge Service | SPO-ES-01 | spo-es-ext.litwareinc.com (64.62.66.11) | spo-es.litwareinc.com (192.165.10.41) | 443 TCP (inbound) (Internet → Access Edge Service for remote access) 5061 TCP (both) (Internet ↔ Access Edge Service for federation) | 5061 TCP (both) (Office Communications Server 2007 R2 pool ↔ Access Edge Service) |
Edge Server—Web Conferencing Edge Service | SPO-ES-01 | spo-wce.litwareinc.com (64.62.66.21) | spo-es.litwareinc.com (192.165.10.41) | 443 TCP (inbound) (Internet → Web Conferencing Edge Server) | 8057 TCP (outbound) (Office Communications Server 2007 R2 pool → Web Conferencing Edge Service) |
Edge Server—A/V Edge Service (load balancer) | SPO-ES-01 | spo-ave.litwareinc.com (64.62.66.31) | spo-es.litwareinc.com (192.168.10.41) | 443 TCP (inbound) (Internet → A/V Edge Service) 3478 UDP (inbound) (Internet → A/V Edge Service) 50,000-59,999 TCP & UDP (both) (Internet ↔ A/V Edge Service) | 443 TCP (outbound) (Internal Net [all IPs] → A/V Edge Service) 3478 UDP (outbound) (Internal Net [all IPs] → A/V Edge) 5062 TCP (outbound) (Internal Net [all IPs] → A/V Edge Service) |
HTTP reverse proxy server | SPO-RP-01 | spo-rp-01.litwareinc.com (64.62.66.30) | spo-rp-01.litwareinc.com (192.165.10.60) | 443 TCP (inbound) Internet → HTTP reverse proxy server | 443 TCP (inbound) HTTP reverse proxy server → Office Communications Server 2007 R2 pool |
SE Server (with archiving and monitoring servers collocated) | SPO-SE-01 | N/A | spo-se-01.litwareinc.com (10.15.10.1) | N/A | N/A |
Archiving Server and Monitoring Server back-end SQL Server | SPO-ARC-MONBE-01 | N/A | spo-arcmonbe-01.litwareinc.com (10.15.10.21) | N/A | N/A |
After preparing the server hardware and surrounding infrastructure—such as DNS and firewall configuration—Litware, Inc. can begin its Office Communications Server 2007 R2 deployment. Litware, Inc. decides to start with the deployment in the Chicago headquarters and follows the deployment path presented in Table 15-20. For each server role deployment, Litware, Inc. reads the information in the corresponding Office Communications Server 2007 R2 Deployment Guides at http://go.microsoft.com/fwlink/?LinkID=133726.
Table 15-20. Deployment Path for Chicago
STEP | SERVER | ACTION |
|---|---|---|
1 | CHI-BE | Install SQL cluster. |
2 | CHI-BE-01 | Install SQL back end. |
3 | CHI-BE-02 | Install SQL back end. |
4 | Create Enterprise Edition pool by using the Create Pool step from the Office Communications Server 2007 R2 setup program on the installation media (point to CHI-BE when prompted for a SQL Server). | |
5 | CHI-POOL | Install and configure the pool load balancer |
6 | CHI-FE-01 | Install the first front-end server. Install and assign the certificate on the server. |
7 | CHI-FE-02 | Install the second front-end server. Install and assign the certificate on the server. |
8 | CHI-FE-03 | Install the third front-end server. Install and assign the certificate on the server. |
9 | CHI-FE-04 | Install the fourth front-end server. Install and assign the certificate on the server. |
10 | CHI-FE-05 | Install the fifth front-end server. Install and assign the certificate on the server. |
11 | CHI-FE-06 | Install the sixth front-end server. Install and assign the certificate on the server. |
12 | Test basic IM/presence functionality: Create two test user accounts and home them on the new pool. Test Office Communicator 2007 R2 client IM access first with one or more front-end servers offline and then with all of them online. Test the client with both manual and automatic configuration options. Sign in using two clients. | |
13 | Test Web Access: Test Office Communicator 2007 R2 client Group Expansion and Global Address List download first with one IIS (installed on the front-end servers) offline and then with both online. | |
14 | Test Web Conferencing: Install two Microsoft Office Meeting 2007 R2 clients to test Web Conferencing first with one or more Web Conferencing Services (installed on the front-end box) offline and then with all of them online. | |
15 | Test A/V: Test Office Live Meeting 2007 R2 and Office Communicator 2007 R2 A/V Conferencing first with one or more A/V Conferencing Services (installed on the front-end box) offline and then with all of them online. | |
16 | CHI-ARCBE-01 | Install SQL Server for the Archiving back end. |
17 | CHI-ARC-01 | Install Archiving Server (point to CHI-ARCBE-01 when prompted to specify a SQL Server). |
18 | Test IM archiving: Use Office Communicator 2007 R2 clients to send test messages and ensure the messages are being archived in the archiving database on the CHI-ARCBE-01 server. | |
19 | CHI-MONBE-01 | Install SQL Server for the Monitoring back end. |
20 | CHI-MON-01 | Install the Monitoring Server (point to CHI-MONBE-01 when prompted to specify a SQL server). |
21 | Test Call Detail Record: Use Office Communicator 2007 R2 clients to send instant messages and Live Meeting clients to do A/V and Web Conferencing. Ensure these sessions are being recorded in the monitoring database on CHI-MONBE-01 server. | |
22 | CHI-DIRBE | Install the SQL cluster for the Director pool. |
23 | CHI-DIRBE-01 | Install the SQL back end. |
24 | CHI-DIRBE-02 | Install the SQL back end. |
25 | Create Enterprise Edition Director pool by using the Create Pool step from the Office Communications Server 2007 R2 setup program (point to CHI-DIRBE when prompted for a SQL Server). | |
26 | CHI-DIR | Install and configure the Director pool load balancer. |
27 | CHI-DIR-01 | Install the first front-end server for the Director pool. Install and assign the certificate on the server. |
28 | CHI-DIR-02 | Install the second front-end server for the Director pool. Install and assign the certificate on the server. |
29 | Test Office Communicator 2007 R2 client IM access first with one front-end server of the Director offline and then with both of them online. To ensure that the Office Communicator client hits the Director, manually configure Office Communicator to point to the Director pool. | |
30 | CHI-ES | Install load balancers for the internal and external edges of the Edge Server. |
31 | CHI-ES-01 | Install the first Edge Server. Install and assign the appropriate certificates. Configure the Edge Server to point to the Director pool. |
32 | CHI-ES-02 | Install the second Edge Server. Install and assign the appropriate certificates. Configure the Edge Server to point to the Director pool. |
33 | Test Office Communicator 2007 R2 client IM external access first with one of the Access Edge Services offline and then with both online. | |
34 | Test Live Meeting 2007 R2 client external Web Conferencing Edge Service access first with one of the Web Conferencing Edge Services offline and then with both online. | |
35 | Test Office Communicator 2007 R2 client A/V Edge Service external access first with one of the A/V Edge Services offline and then with both online. | |
36 | Test Live Meeting 2007 R2 client external A/V Edge Service access first with one or more A/V Edge Services offline and then with all of them online. | |
37 | Install the SIP/PSTN gateway and connect it to the PSTN network. | |
CHI-MED-01 | Install the Mediation Server. Install and assign certificates. Configure the Mediation Server to point to the Director pool (or EE pool) on the internal side and to an existing SIP/PSTN gateway on the external side. | |
39 | Enable users for Voice and configure normalization rules, phone routes, and location profiles (refer to Chapter 11, for more details). | |
40 | Test the Office Communicator 2007 R2 client by placing and receiving PSTN calls. |
The next location to be configured after the Chicago deployment in Litware, Inc.’s Office Communications Server 2007 R2 deployment is Paris. Litware, Inc. decides to deploy in the order described in Table 15-21.
Table 15-21. Deployment Path for Paris
STEP | SERVER | ACTION |
|---|---|---|
1 | PAR-BE | Install the SQL cluster. |
2 | PAR-BE-01 | Install the SQL back end. |
3 | PAR-BE-02 | Install the SQL back end. |
4 | Create the Enterprise Edition pool by following the "Create Pool" step from the Office Communications Server 2007 R2 setup program (point to PAR-BE when prompted for a SQL server). | |
5 | PAR-POOL | Install and configure the pool load balancer. |
6 | PAR-FE-01 | Install the first front-end server. Install and assign the certificate on the server. |
7 | PAR-FE-02 | Install the second front-end server. Install and assign the certificate on the server. |
8 | PAR-FE-03 | Install the third front-end server. Install and assign the certificate on the server. |
9 | PAR-FE-04 | Install the fourth front-end server. Install and assign the certificate on the server. |
10 | Test basic IM/presence functionality: Create two test user accounts and home them on the new pool. Test Office Communicator 2007 R2 client IM access first with one or more front-end servers offline and then with all of them online. Test the client with both manual and automatic configuration options. Sign in using two clients. | |
11 | Test Web Access: Test the Office Communicator 2007 R2 client Group Expansion and Global Address List download first with one IIS (installed on the Front End Servers) offline and then with both online. | |
12 | Test Web Conferencing: Install two Live Meeting 2007 R2 clients to test Web Conferencing first with one or more Web Conferencing Services (installed on the front-end box) offline and then with all of them online. | |
13 | Test A/V: Test Live Meeting 2007 R2 and Office Communicator 2007 R2 A/V Conferencing first with one or more A/V Conferencing Services (installed on the front-end box) offline and then with all of them online. | |
14 | PAR-ARCBE-01 | Install the SQL Server for the Archiving back end. |
15 | PAR-ARC-01 | Install the Archiving Server (point to PAR-ARCBE-01 when prompted to specify a SQL Server). |
16 | Test IM Archiving: Use Office Communicator 2007 R2 clients to send test messages and ensure the messages are being archived in the archiving database on the PAR-ARCBE-01 server. | |
17 | PAR-MONBE-01 | Install the SQL Server for the Monitoring back end. |
18 | PAR-MON-01 | Install the Monitoring Server (point to PAR-MONBE-01 when prompted to specify a SQL Server). |
19 | Test Call Detail Record: Use Office Communicator 2007 R2 Clients to send instant messages and Live Meeting clients to do A/V and Web Conferencing. Ensure these sessions are being recorded in the monitoring database on PAR-MONBE-01 server. | |
21 | PAR-ES | Install internal and external load balancers Edge Server. |
22 | PAR-ES-01 | Install the first Edge Server. Install and assign the appropriate certificates. Configure the Edge Server to point to the Director pool (in Chicago). |
23 | PAR-ES-02 | Install the second Edge Server. Install and assign the appropriate certificates. Configure the Edge Server to point to the Director pool (in Chicago). |
24 | Test Office Communicator 2007 R2 client IM external access first with one or more Access Edge Services offline and then with all of them online. | |
25 | Test Live Meeting 2007 R2 client external Web Conferencing Edge Service access first with one or more Web Conferencing Edge Services offline and then with all of them online. | |
26 | Test Office Communicator 2007 R2 client A/V Edge Service external access first with one or more A/V Edge Services offline and then with all of them online. | |
27 | Test Live Meeting 2007 R2 client external A/V Edge Service access first with one or more A/V Edge Services offline and then with all of them online. |
The last pool location for Litware, Inc.’s Office Communications Server 2007 R2 deployment is Singapore. Litware, Inc. decides to deploy Office Communications Server 2007 R2 server roles in the order described in Table 15-22.
Table 15-22. Deployment Path for Singapore
STEP | SERVER | ACTION |
|---|---|---|
1 | SPO-SE-01 | Install the Standard Edition Server. Install and set up certificates. |
2 | SPO-ARCMONBE-01 | Install the SQL Server that will be shared by the Archiving and Monitoring back end. |
3 | SPO-SE-01 | Install the Archiving and Monitoring Servers on the Standard Edition Server machine. |
4 | Test basic IM/presence functionality: Create two test user accounts and home them on the Standard Edition Server. Test Office Communicator 2007 R2 client IM access. Test the client with both manual and automatic configuration options. Sign in using two clients. | |
5 | Test Web Access: Test the Office Communicator 2007 R2 client Group Expansion and Global Address List download. | |
6 | Test Web Conferencing: Install two Live Meeting 2007 R2 clients to test Web Conferencing. | |
7 | Test A/V: Test Live Meeting 2007 R2 and Office Communicator 2007 R2 A/V Conferencing. | |
8 | SPO-ES-01 | Install the Edge Server. Install and assign the appropriate certificates. Configure the Edge Server to point to the Director pool (in Chicago). |
9 | Test Office Communicator 2007 R2 client IM external access. | |
10 | Test Live Meeting 2007 R2 client external Web Conferencing Edge Service access. | |
11 | Test Office Communicator 2007 R2 client A/V Edge Service external access. | |
12 | Test Live Meeting 2007 R2 client external A/V Edge Service access. |