Cryptography is an ancient art and science of hiding information to protect sensitive information from the bad guys. It was extensively used even before the computer age. During those times, cryptography was concerned solely with message confidentiality (encryption). Encryption is the process of converting information called plaintext into an unreadable form called cipher-text, and decryption is the opposite where cipher-text is converted back to plaintext. The most basic form of cipher is a transposition cipher, which involves rearranging the order of letters, for example "attack today" will become "tatakc otdya". Substitution cipher is another type of cipher, which replaces letters or group of letters with other letters or group of letters. Several interesting means of hiding information were introduced by imaginative and intelligent people/groups. Cryptography has evolved and modern-day cryptography in general involves three types of cryptographic algorithms: symmetric (secret key) algorithms, asymmetric (public key) algorithms, and hash functions. Symmetric algorithms use a single key for encryption and decryption, asymmetric algorithms uses two keys, one for encryption and the other for decryption, and hash functions are one-way cryptography and since the plaintext is not recoverable they do not require any key.
An application dealing with sensitive data available in memory, stored in a database, file, or any other storage medium is vulnerable to theft. Encryption provides protection from such threats by encrypting data using a key and reconstructs the original data by decrypting it using the same key. Similarly, hashing provides a mechanism through which we can maintain data integrity by creating and comparing the generated hash with the original input, and is generally used to save a password or check for message integrity.
The Cryptography Application Block simplifies implementation of hashing and symmetric encryption functionality in our application. As you might be aware, the .NET Framework provides the Cryptography API as part of the System.Security.Cryptography namespace for this very purpose. The application block takes it a step further by abstracting the application code from the intricacies of specific cryptography providers. It allows us to create and compare hashes, encrypt and decrypt data using the configured hashing and symmetric cryptography providers respectively. Hashing in cryptography is a mechanism through which an input is converted into fixed size string (hash value); this process is generally referred to as one-way hashing function as the hash value cannot be re-converted to the original input. This can be used to perform message integrity checks, store sensitive data such as password that doesn't need to be retrieved, digital signatures, and so on. Encryption in cryptography is a process transforming an input or plain text into an unreadable form called cipher text. This transformation is performed using an algorithm with a key.
The following are the key features of the Cryptography Application Block:
- Provides hashing functionality with a simple API to generate and compare hash values
- Several hash providers are available out of the box for common hashing algorithms
- Extension point to implement custom hash provider
- Provides symmetric cryptography functionality to encrypt/decrypt data
- Several symmetric cryptography providers are available out of the box for common encryption algorithms
- Configuration editor support to configure hashing and cryptography providers
In this chapter, you will:
- Be introduced to the Cryptography Application Block
- Be introduced to Hashing and Hash Providers
- Be introduced to Cryptography and Cryptography Providers
- Learn about referencing the required and optional assemblies
- Learn to set up the initial configuration
- Learn to configure the hash provider
- Learn to generate hash value for a given string
- Learn to compare hash value with a string
- Learn to implement a custom Hash Provider
- Learn to configure the symmetric cryptography provider
- Learn to encrypt data
- Learn to decrypt data
- Learn to implement custom Symmetric Cryptography Provider
Before we leverage and dig deeper into individual features of the Cryptography block, we will create a simple application, which will help us to get up to speed with the basics; in this section we will do the following:
- Reference the Logging block assemblies
- Add Namespaces
- Set up the initial configuration
To complement the concepts and sample code snippet of this book and allow you to gain quick hands-on experience of different features of the Cryptography Application Block, we have created a sample demonstration application that provides implementation of generating and comparing hashes and encrypting/decrypting data.
The following is a screenshot of the sample application:
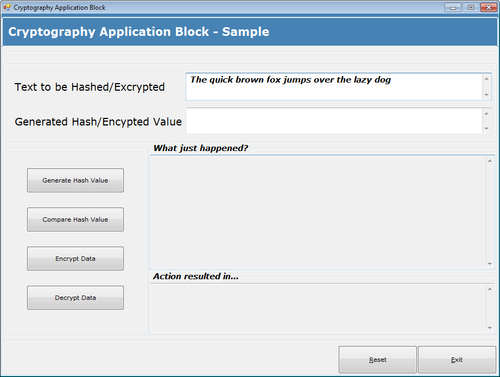
For the purposes of this demonstration, we will be referencing non-strong-named assemblies but based on individual requirements, Microsoft strong-named assemblies or a modified set of custom assemblies can be referenced as well.
The following table lists the required/optional assemblies:
|
Assembly |
Required/Optional |
|---|---|
|
|
Required |
|
|
Required |
|
|
Required |
|
|
Required |
|
|
Required |
|
|
Optional: Used while leveraging SerializationUtility class for serializing and de-serializing objects to and from byte streams |
Instead of fully qualifying the types on every instance of their usage, we can add the namespaces given next to the source code file to use the Cryptography block elements without fully qualifying each reference.
Core Namespace:
Microsoft.Practices.EnterpriseLibrary.Security.Cryptography
Configuration Namespace (Optional): Required while using the EnterpriseLibraryContainer to instantiate objects.
Microsoft.Practices.EnterpriseLibrary.Common.Configuration
Unity Namespace (Optional): Required while instantiating objects using UnityContainer.
System.ConfigurationMicrosoft.Practices.UnityMicrosoft.Practices.Unity.Configuration
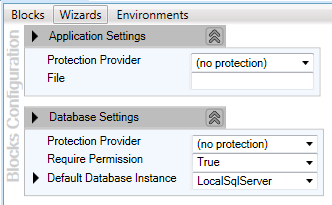
Before we can leverage the features of the Cryptography Application Block, we have to add the initial Cryptography Settings to the configuration. Open the Enterprise Library configuration editor either using the shortcut available in Start | All Programs | Microsoft patterns & practices | Enterprise Library 5.0 | Enterprise Library Configuration or by just right-clicking the configuration file in the Solution Explorer window of Visual Studio IDE and clicking on Edit Enterprise Library V5 Configuration. Initially, we will have a blank configuration file with default Application Settings and Database Settings.
The following screenshot displays the default settings displayed in the configuration editor:
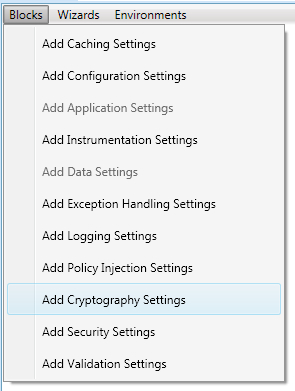
Let us go ahead and add the Cryptography Settings in the configuration file. Select the menu option Blocks, which lists many different settings to be added to the configuration. Click on the Add Cryptography Settings menu item to add the security configuration settings.
The following screenshot shows the menu option Add Cryptography Settings:
Once we click on Add Cryptography Settings, the configuration editor will display the default Cryptography Settings as shown in the following screenshot:
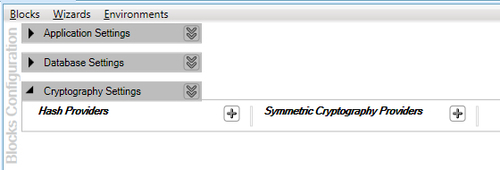
Notice that the setting consists of two sections: Hash Providers and Symmetric Cryptography Providers. We will change the configuration further, but for now, we are in good shape with regards to the initial infrastructure configuration.
