Microsoft Vista: The Battle Against Malware Lives On
Introduction
Microsoft’s Vista is by far the most secure version of its client-based operating system (OS) to date. Living by its motto of “Trustworthy Computing,” Microsoft has taken many steps to ensure new levels of security to the Windows Vista base OS. Along with other tools and programs, Microsoft has released Internet Explorer 7, which is the most secure version of the famous browser released to date. Microsoft has also updated and released a plethora of documentation on the company’s main Web site and on TechNet in coordination with the Vista release, to help you harden and prepare your system for use on the Internet or on a corporate network.
With all of these tools, documentation updates, and newly developed forms of technology and security you should be wondering why we still have to deal with so many computer-related issues. The fact is that every time we browse the Internet, we open our doors to danger. It’s also a fact that we may never catch up to quell the growing threat. In the world of IT, the playing field is constantly changing, so as programming code becomes more bloated and newer features are added, consequently more exploits are added. Newly made software and software that has been updated will always have issues that will be resolved only through update installations, hot-fixes, service packs (SPs), and/or complete OS or program upgrades. As this chapter’s title implies, the battle against malware does in fact live on. You do have an option to protect yourself, though.
Security is not only a practice, it’s also a mindset. Those of you who leave your front doors open and unlocked invite danger. This doesn’t mean you will inevitably be a target; it just means you are making it easier to become a target. It’s always better to make sure your assets are secure before inviting danger. You can apply the same way of thinking to your Internet surfing habits. Knowing that you could be a victim every time you venture onto the Web will help you develop a mindset to make sure your doors are locked before you do. By preparing for risk, you will ultimately be more secure. To lessen the risk of attack, you would want to ensure that your OS is secure and hardened and that the Web browser you use will not invite danger. You will also want to make sure you aren’t surfing sites where you may be an even bigger target, such as downloadable warez sites, pornographic content sites, and music download sites. These are generally havens for unwanted malware. With Microsoft’s new tools and more secure software, you are definitely going to be able to lock your doors at night and feel better about your security posture. If you also apply common-sense browsing skills to your Web surfing, you could very well keep your OS malware-free for a long period of time.
With the release of Microsoft’s Vista OS, security has once again been brought to a new level. When Microsoft started to take security extremely seriously (after its federal antitrust case), the biggest area that needed work was its Web browser. From its inception, Internet Explorer has been the target of many exploits. Due to its widespread deployment (it came with the base OS and was one of the first browsers available for use), Internet Explorer became the biggest target of exploit writers. Because of its flawed code and many bugs, exploit writers had no problem creating one exploit after another, with no end in sight. Tie in that the Internet is the main catalyst in an ever-changing world of technology and you can clearly see why Internet Explorer has had so many problems to date. This would also explain why other browsers had not seen as many exploits as Internet Explorer did. They just weren’t as big a target and, to some extent, may have been programmed better.
Ever since Microsoft invested considerable time, money, and resources into securing its software, each release had gotten better and less susceptible to attack and exploit. This obviously doesn’t stop the ongoing plague of exploits that surface each month; it only helps to “stem the tide.” Because malicious software (malware) is an ongoing problem and one that is growing each year, Microsoft has stepped up to the challenge once again with its newest releases of Vista and Internet Explorer Version 7. In this chapter, we will look at how Vista and Internet Explorer make for a safer browsing experience, and how Microsoft is combating problems with malware.
Malware Fundamentals
Intruders, hackers, or attackers who access networks and systems without authorization and with malicious motives can plant various types of programs to cause damage to the network, your system, and your data. These programs—often lumped together under the general term viruses—perform many different functions and are classified under different categories. In this section, we will look at how granular the term malware can actually be. It’s important to have a general understanding of the different classifications of malware, and it’s equally important to understand their general behavior.
Malware is any software product or program that has been created with an intent to cause damage or harm. The word malice is a legal term used to define the intention of one party to harm or cause injury to another party. When applied to computer technology, the word holds equal meaning. A malicious party creates software to cause havoc on any host that downloads and installs it, whether knowingly or unknowingly. When discussing malware, it’s important to classify it. The term malware is generally used to describe a broad spectrum of different types of software, such as computer viruses,Trojans, worms, adware, and spyware. Just about any form of hostile, intrusive, or annoying software or program code can be classified as malware.
Viruses, Worms, and Trojan Horses
Many of the original MS-DOS-based viruses and other types of malware were written as experiments intended to be either harmless or destructive, and many were created as simple and harmless pranks. As time went on, the level of skill used to create such malware grew by leaps and bounds, and the severity of each payload grew exponentially as well. This inevitably caused many software programmers to stop coding, learn security fundamentals, and start coding again while applying those fundamentals. Because it appeared that the exploit writers were outpacing the software developers, this practice became “mandatory” within Microsoft’s own camp.
Young, inexperienced software programmers and script kiddies learning about viruses and the techniques used to write them were getting more advanced as the tools they created or had at their disposal expanded in number. Some of these malware attacks proved to hurt a global economy that now thrived on the use of the Internet. As time went on, a chase seemed to ensue, and it appeared as though the exploit writers were outpacing the product’s legitimate software development teams. As the use of the Internet exploded, it seemed as though malware grew more and more destructive on a daily basis. Newer exploits were coming out rapidly that were designed to destroy files on a hard disk or to corrupt the file system so that it could not be used. Viruses were created to cause traffic flooding to legitimate Web servers, putting them out of business. The list goes on and on. It wasn’t until malware became extremely destructive that action was taken on a grand scale. In 1999, Melissa (a well-known computer virus) really showed us how fast (and far) a virus could spread. It also showed us how vulnerable our systems were to attacks that could hurt a company’s bottom line. Melissa was the first virus to be widely disseminated via e-mail. It is a macro virus, written in Visual Basic for Applications (VBA), and it was embedded in a Microsoft Word 97/2000 document. When the infected document was opened, the macro ran (unless Word was set not to run macros), sending itself to the first 50 entries in every Microsoft Outlook MAPI address book it could find. These included mailing list addresses, which resulted in very rapid propagation of the virus. The virus also made changes to the Normal.dot template, which caused newly created Word documents to be infected. Because of the huge volume of mail it produced, the virus caused a denial of service (DoS) attack on infected e-mail servers.
Viruses
A virus is a malicious program that is commonly installed on a target host with the intent to cause harm or damage. A virus (just like the medical version of the term) infects the host, usually by being installed by the end user of the target host. A virus is almost always executed by the end user without him knowing the true intention of the malware. Viruses are made to perform undesirable actions. Viruses are also created to replicate themselves, infecting other systems by writing themselves to any disk that is used in the computer or sending themselves across a network when activated. Viruses are often distributed as attachments to e-mail or as macros in word processing documents easily sent via e-mail and opened by unsuspecting e-mail users. Some viruses activate immediately on installation, and others lay dormant until a specific date or time, or until a particular system event triggers their payload.
Viruses come in literally thousands of varieties. They can do anything from sending a pop-up message on your desktop to scare you (which is considered a prank), to erasing the entire contents of a computer’s hard disk (which is considered destructive and harmful). The proliferation of computer viruses has also led to the phenomenon of the virus hoax, which is a warning—generally circulated via e-mail or Web sites—about a virus that does not exist or that does not do what the warning claims it will do. The same malicious effect takes place because through the hoax, the end user can cause the same damage to the target system without creating a software tool using programming languages. In the past, some of these hoaxes have prompted computer users to manually delete needed system files, either because they sounded malicious or because the icon image they used by default looked malicious. Real viruses, on the other hand, present a real threat to your network. Companies such as Symantec and McAfee make antivirus software that is aimed at detecting and removing virus programs, and is updated daily to thwart newly created ones, which seem to also come out on a daily basis.
Although viruses come in many varieties, they can be classified into four general categories: e-mail-based, boot sector-based, application-based, and macro-based. The common thread that holds these types together is that they need to be executed on the target host.
■ E-mail viruses E-mail viruses are transmitted via e-mail and contain a payload that is activated when the end user is provoked to activate it, or when something in the e-mail client and how it reads e-mail (and scripts) activates the payload upon delivery or viewing, without opening the e-mail (such as with an automatic reading pane found in most e-mail clients).
■ Boot sector viruses Boot sector viruses are often transmitted via disk. The virus is written to the master boot record on the hard disk, from which it is loaded into the computer’s memory every time the system boots.
■ Application or program viruses Application viruses are executable programs that, when run, infect your system. Viruses can also be attached to other, harmless programs and installed at the same time the desirable program is installed.
■ Macro viruses Macro viruses are embedded in documents (such as Microsoft Word documents) that can use macros, which are small applications or “applets” that automate the performance of some task or sequence. Although Microsoft Office documents are not executable files, they can contain macros. Thus, Office documents should be treated as though they are executables, unless the ability to run macros is disabled in the Office program.
Worms
Worms are ugly, regardless of whether they are dangling from a fish hook or taking down your public Internet connection. Worms can also be very destructive. History has shown us that since its inception, the worm has consistently transferred itself over networks to infect target hosts, whereas common viruses typically infect a single target host only. The worm is then transferred via e-mail or floppy disk to other hosts in hopes that they become infected as well. A worm is written to propagate quickly, and to infect as many target hosts via propagation as possible, thereby causing as much turmoil as possible. Although the line between malware terms such as worm and virus is sometimes blurred, this is the major distinction between the two.
A worm is programmed to “scan” the network from the infected host to find other hosts with open and vulnerable services and ports. As an example, a worm may infect a target host via a network port and then find 30 hosts on the connected subnet with the same open port. Once this criterion is met, the worm then propagates to those 30 hosts, and so on. Examples of this come in the form of the Sasser and Slammer worms. The Sasser worm exploited Transmission Control Protocol (TCP) port 5554. The Slammer worm exploited a known SQL Server vulnerability by sending a single packet to User Datagram Protocol (UDP) port 1434.
The worm first surfaced at the turn of the century. In 2001, worms such as Code Red started to pop up at an alarming rate. This self-propagating worm began to infect Microsoft-based Web servers running Internet Information Server (IIS), and because so many such servers were in use, the virus spread extremely quickly. On various trigger dates, the infected machines would try to connect to TCP port 80 (used for Web services) on computers with randomly selected Internet Protocol (IP) addresses. When successful, the worm attempted to infect any remote system it could find and connect to. Some variations of the worm also defaced Web pages stored on the server as a form of digital graffiti. On other dates, the infected machine would launch a DoS attack against a specific IP address embedded in the code. CERT (www.cert.org) reported that Code Red infected more than 250,000 systems over the course of nine hours on July 19, 2001.
Then came Nimda—a newly created worm used to take advantage of known flaws within the Microsoft OS. In late summer 2001, the Nimda worm infected numerous computers running Windows 95/98/ME, NT, and 2000. The worm made changes to Web documents and executable files on the infected systems and created multiple copies of itself. Nimda spread via e-mail, across network shares, and via infected Web sites. It also exploited vulnerabilities in IIS versions 4 and 5 and spread from client machines to Web servers through the backdoors left by the Code Red II worm. Nimda allowed attackers to then execute arbitrary commands on IIS machines that had not been patched, and denials of service were caused by the worm’s programmed payload.
As the IT community repaired systems at a feverish rate to recover from Code Red and Nimda, Klez reared its ugly head. In late 2001 and early 2002, the Klez worm spread throughout the Internet, primarily via e-mail. It propagated through email mass mailings and exploited vulnerabilities in the unpatched versions of Outlook and Outlook Express mail clients, attempting to run when the message containing it was viewed or previewed in the preview pane. When Klez runs, it copies itself to the System or System32 folder in the system root directory, and modifies a Registry key to cause it to be executed when Windows is started. It also tries to disable any virus scanners and sends copies of itself to addresses in the Windows address book, in the form of a random filename with a double extension (for example, file.doc.exe). As though this wasn’t harmful enough, the worm had a secret payload, which executed on the thirteenth day of every other month, starting with January, resulting in files on local and mapped drives being set to 0 bytes in length.
Worm outbreaks have become a cyclical plague for both home users and businesses, and have been eclipsed only recently in terms of damage by spyware. As they were from inception, today most worms are commonly written for the Windows OS, although a small number are also written for Linux and UNIX systems, such as 2005’s Lupper, which was aimed at the growing use of Linux Web servers in the marketplace.
Trojan Horses
For a malicious program to accomplish its goals, it must be able to do so without being shut down by the user or administrator of the computer on which it’s running. Concealment is a major goal of a malware creator. When a malicious program is disguised as something innocuous or desirable, users may be tempted to install it without knowing what it does. When reflecting on history, the documented first use of the Trojan horse was when the Greeks gave their enemies (the Trojans) a gift during the Trojan War. The gift (a gigantic wooden horse) was given in peace so that the Trojans would bring it into their stronghold, but at night, when the city slept, the Greek soldiers snuck out of the back of the horse and attacked and then captured the city of Troy.
This is how the Trojan horse exploit performs. The Trojan horse will appear harmless enough for the recipient to install, because it hides its true intention, which is based on malicious activity. The Trojan horse conceals a harmful or malicious payload within its seemingly harmless shell. The payload may take effect immediately and can lead to many undesirable effects, such as deleting all of the user’s files, or more commonly, installing further harmful software on the user’s system for future payloads.
Trojans can be very cleverly disguised as innocuous programs, utilities, or screensavers. A Trojan can also be installed by an executable script (JavaScript, a Java applet, ActiveX control, etc.) on a Web site. Accessing the site can initiate the program’s installation if the Web browser is configured to allow scripts to run automatically. Trojans can use the default behavior of Windows to disguise their true nature. Because the file extension (the characters that appear after the last dot in a filename) are hidden by default, a hacker can name a file something such as harmless.jpg.exe and it will appear in Windows Explorer as harmless.jpg, seeming to be an innocent graphics file, when it is really an executable program. Of course, double-clicking it to open the “harmless picture” will run the program. Trojans that are designed to allow hackers to gain unauthorized access across a network, such as Back Orifice and NetBus, are sometimes called remote access Trojans (RATs). Back Orifice, Back Orifice 2000, NetBus, and SubSeven were the most commonly used Trojans of their time, although literally hundreds exist. Newer Trojan horses, such as Xombe and Dloader-L, both of which arrive as an executable attachment in spam e-mail messages claiming to come from [email protected], are meant to wreak havoc by fooling you into thinking that the attachment legitimately came from Microsoft. Because the spoofed e-mail address “seemed” legitimate, many were fooled into executing the attachment, which can be thought of as any system administrator’s nightmare.
Trojan horses known as droppers are used to initiate a worm outbreak, by injecting the worm into users’ local networks. Spyware is commonly distributed as a Trojan horse, bundled with a piece of desirable software that the user downloads from the Web, or from a peer-to-peer file-sharing network such as LimeWire (www.limewire.com). When the user installs the software, the spyware is installed alongside it. Spyware authors who attempt to act legally may include an End User License Agreement (EULA) which states the behavior of the spyware in loose terms, but with the knowledge that users are unlikely to read or understand it.
Spyware and Adware
Somewhere along the malware timeline, virus and exploit writers started to shift gears from attacking with a purpose, such as harm and damage, to just getting paid. Spyware and adware have become lucrative business ventures for those who have tried it and were successful at it. Spyware programs are designed to monitor users’ Web browsing habits and then market relevant advertisements to these users based on their browsing history. Some spyware programs display unsolicited advertisements and then trick or force the user to click on them. Some are even self-activated. Other forms of spyware are intelligent enough to redirect affiliated marketing revenues to the spyware creator.
Spyware programs do not spread like viruses do; they are generally installed by exploiting known security holes or are packaged with software that the end user downloads and installs onto the target host. Spyware programs are usually installed as Trojan horses, meaning you believe you are installing software that does a specific function, but in the background, other functions are taking place. Spyware differs from standard viruses in that their creators present themselves openly as businesses, whether legitimate or not.
Spyware exploits are also used to obtain user information. Similar to how cookies help to aid your browsing experience, spyware does the same by analyzing what sites you go to and what your browsing habits are. However, it then invades your privacy further by not only using that information to market products to you, but also avoiding deletion or removal so that you cannot remove it. A cookie, on the other hand, is generally pretty easy to deny or delete, especially with Internet Explorer 7.
Some spyware can trick you by changing your search engine results to paid advertisements that benefit the spyware creator. Others change the affiliate marking codes so that all revenue goes to the spyware creator instead of to you. This is sometimes called stealware.
You can use spyware detection programs such as third-party vendor tools (e.g., Ad-Aware; www.lavasoftusa.com), or you can use Microsoft Defender in conjunction with SpyNet to help stop your spyware woes.
Similar to antivirus software, spyware removal programs compare a list of known spyware with files on your computer and then remove any that it detects. Antispyware programs can combat spyware from being installed, but the best strategy is to carefully examine and analyze what you choose to download and install.
Botnets
Much like the DDoS attack, the botnet is a program that will facilitate an attack from coordinated systems. Software robots (or bots, for short) are controlled via a botnet.
In a botnet, the malware logs on to an Internet Relay Chat (IRC) channel or other chat-based system. The attacker can then give instructions to all the infected systems simultaneously. Botnets can also be used to push upgraded malware to the infected systems, keeping them resistant to antivirus and antispyware software or other security measures.
Prevention and Response
Before we get into how Microsoft’s new products can help you reduce the threat of malware, it makes sense to discuss prevention and response first. As mentioned earlier, staying secure is a two-step dance. You need good software that protects you, and the mindset to protect your surfing habits. Protecting systems and networks from the damage caused by Trojans, viruses, and worms is mostly a matter of common sense. It’s up to you to prevent harm by being aware of it, and then being able to respond to it and make the systems (or network) operational without any downtime, if possible. Although there are many ways to protect yourself and your system using Microsoft’s tools, it always helps to practice some of the following general security practices as well:
■ Periodically update every piece of software you install on your system, as well as the OS itself, which also needs to be updated periodically. You can do this by installing the latest updates, hotfixes, security patches, and SPs that are available for your software. Keep on top of when new patches come out, and try to test and then install the current patches to keep your system at its best.
■ When you are using your e-mail client, pay close attention to “who” is sending you e-mail and “where” the e-mail originates. Because e-mail can be spoofed, you may not always be able to do this, but in most cases, a spam filter can quickly identify unspoofed e-mail and send it right to the trash or automatically remove it.
■ If you receive files from sources that you do not recognize, it’s wise not to execute them. Instead, delete them. In other words, if someone sends you a file such as harmless.jpg.exe, it’s a good idea to delete the file and not execute it because it seems to fall into the characteristic of a typical malware hoax intended on getting you to launch it.
■ When using your e-mail client, make sure you turn off any preview pane functionality so that you do not open and, therefore, execute any attached scripts simply by opening your Inbox.
■ To prevent macro viruses, ensure that macro security is enabled in Office so that if you open a Word document, you won’t necessarily run a malicious script that may also be contained within it.
■ Do not use floppy disks from untrusted sources. Also, pay attention to any file that enters your system from any source, whether it is a CD or DVD-ROM, USB flash device, or something similar.
■ Use host-based instruction detection/prevention (IDS/IPS) software if possible, as well as firewall software, antivirus software, and spyware removal software such as Microsoft Defender.
■ Harden your systems and disable unneeded or unwanted services.
■ Use a strong password policy. If malware does attempt to try to steal your credentials, having a strong password policy in place will help you if your system does become infected.
■ Configure your Web browser (such as Internet Explorer 7) to ignore or warn for cookies, and disable JavaScript and ActiveX, two commonly exploited scripting languages. Keep a close eye on sites that are not trusted and try to block sites that you know are malware-infected.
You may also want to make sure your network is also secure. Some more advanced practices include the following:
■ Configure your routers, switches, and other adjoining network hardware to be secure, which means locking down services, keeping the router or switch OS updated, and applying any security measures such as disabling broadcasts on certain interfaces, applying access control lists (ACLs), and so on.
■ Disable the Simple Network Management Protocol (SNMP) and any other services that you do not need.
■ Make sure any e-mail relays in use are protected and aren’t being used to send spam.
■ Use application gateway firewalls to protect against large-scale attacks.
■ Apply defense in depth. Using a firewall alone is almost meaningless. You need to ensure that you have multiple levels of security in place, such as desktop policies, a firewall, and an IDS.
■ Use a security policy and keep it updated. Security is upheld only when it’s supposed to be, so make sure your company has a policy in place that dictates what needs to be secured and how it needs to be secured.
■ Make sure you have an incident response plan ready, with detailed steps and a team that can carry it out. Your goal should be to prevent a crisis if you can, but your real responsibility when dealing with incident response concerns the response; in other words, taking care of the issue either while it is happening or after it has happened.
Incident Response
Recognizing the presence of malicious code should be your first response step if the system does get infected. Administrators and users need to be on the alert for common indications that a virus might be present, such as missing files or programs; unexplained changes to the system’s configuration; unexpected and unexplained displays, messages, or sounds; new files or programs that suddenly appear with no explanation; memory “leaks” (less available system memory than normal) or unexplained use of disk space; and any other odd behavior of programs or the OS. If a virus is suspected, a good antivirus program should be installed and run to scan the system for viruses and attempt to remove or quarantine any that are found. Finally, all mission-critical or irreplaceable data should be backed up on a regular basis in case all of these measures fail.
Remember that virus writers are a creative and persistent bunch and will continue to come up with new ways to do the “impossible,” so computer users should never assume that any particular file type or OS is immune to malicious code. There is only one way to completely protect yourself against a virus, and that is to power down the computer and leave it turned off entirely.
Microsoft Vista and Security
The battle for malware wages on, but new weapons have been pushed to the front line. For Windows Vista, many new security features (as well as some updated ones) help to protect computer systems from past, present, and future malware threats of any class.
Vista includes many new features that help to thwart malware threats. Behind the actual making of the software was a major plan to shift the way Microsoft does business in the security sector. Now, making a secure, private, and reliable computing experience has become the company’s top priority and has been dubbed “Trustworthy Computing.”To preserve data confidentiality, integrity, and availability (CIA), Windows Vista brings a new level of confidence to computing through improved security, reliability, and management. It achieves this by establishing innovative engineering, applying best practices, and creating a system where the OS can be updated and maintained consistently to avoid intrusion or exploitation.
New features include:
■ Windows Service Hardening (WSH) Windows Service Hardening limits the amount of damage an attacker can do if a service is compromised.
■ Network Access Protection (NAP) Network Access Protection is used to prevent clients from connecting to the network if they are infected with malware.
■ Internet Explorer 7 Internet Explorer 7 comes with Windows Vista by default as the built-in Web browser. It includes many security enhancements that protect users from malware attacks such as phishing and spoofing, and it uses a new mode, called Protected Mode, to further secure the user’s browsing experience.
■ Updated Windows Firewall The new outbound filtering feature in the personal firewall helps to apply more granular control over traffic traversing it.
■ User Account Control (UAC) This feature will allow a user to change computer settings while running as a standard user, instead of requiring administrator privileges to perform most tasks.
■ Windows Defender The Windows Defender utility detects malware on your system and, when used in conjunction with SpyNet, can help to eliminate most spyware attacks and exploits.
Other features within Vista help to secure the system; however, these relate to the battle against malware.
Windows Service Hardening (WSH)
For a long time, malware seemed to be connected to Windows-based services. Because Windows services have always been an open door for malware creators, Microsoft took steps to ensure that this doesn’t continue to be a problem. In the past, there has been a major issue with the number of critical services running as System, which basically gave an open door to anyone who could bypass the minimal security in place. The Sasser, Blaster, Slammer, and Code Red exploits targeted unprotected and easily exploited services. WSH is a new service released with Microsoft Vista that allows you to harden the security posture of your host system. It’s not realistic to leave a PC powered down and not in use, because this goes against what a computer was originally designed to do, which is to help you be more productive. The computer was not meant to act as a 150-pound paperweight. Microsoft has raised the bar on system service hardening by releasing WSH.
A system service is normally a background process that runs to support specific functions, such as the Messenger service that is used to send and receive messages throughout the system. In the past, services have been able to be exploited because once they were breached they basically opened the door to the system for the malware creator. Now, WSH focuses on using the least-privileged account—for example, LocalService. To further understand how this works consider that the hardened service would be protected via service SID access via ACLs. The service would use an SID, an ACL, and a “write-restricted token” to further harden and protect the system from exploitation.
Microsoft’s system services have been the base for many attacks because of the high level of privileges these services run with. If exploited, some services can give unfettered access to the entire system. The malware can then run with the highest possible system privileges, or LocalSystem privileges. Once the system has been exploited, the attacker can run exploits on the system with administrator privileges. Worms such as Slammer exploited known system service holes. System services are kept secure with Windows Vista through the use of restricted services. This is done by running the services used with the “least privilege” needed, which reduces the risk of a threat. Using restricted services minimizes the number of exploitable services that are running and helps to secure the ones that do run. Windows services are run under service profiles that help to classify the service further so that the Vista OS has full control over its own services, further limiting malware exploitation.
Used in conjunction with the newly updated Windows Firewall, inbound and outbound network ports that the services are allowed to use are now under Vista’s control. If a system service attempts to send and receive network data on a specific port, the firewall will block access. The commonly exploited Remote Procedure Call (RPC) service is an example. When RPC is needed, it will be loaded and “restricted” to doing only certain things. No longer can it be used to replace system files and other data, modify the system Registry, and so on.
WSH is important to Vista’s overall security because even if you cannot prevent your system from being infected by malware, at least now you have a good feeling that if the system does get infected, the payload will not be as extreme as it used to be with older versions of the Windows OS. WSH also opens the door for independent software vendors (ISVs) to develop components and programs that are secure and will not cause issues for Windows Vista.
WSH (in conjunction with other new security features) provides an additional layer of protection which builds on the defense in depth principle. Defense in depth is a general security term that means applying many levels of security to enhance your security posture. Do not rely on one form of security, such as a firewall, to protect you. Incorporate other forms of security so that you do not have all your eggs in one basket. With WSH, Vista adds another layer of security to the system, which can help thwart future attacks and exploits even further.
Network Access Protection (NAP)
NAP is used to prevent clients from connecting to the network if they are infected with malware. NAP is a policy enforcement platform incorporated into Windows Vista as well as Windows Server 2007 (codenamed Longhorn). By enforcing compliance with very specific system health requirements, Vista is able to help prevent malware from accessing the rest of the network and attached systems.
NAP can help verify that each computer connected to the network is malwarefree; if it is not, it will not be allowed to connect to the network and further infect other systems. Until the system checks out as malware-free, it will not be allowed to use the network or its services.
Improvements in Internet Explorer 7
With the release of Windows Vista, you can expect to use the newest and most secure version of Microsoft’s Web browser to date. New features in Internet Explorer 7 help to prevent the inception and spread of malware. To help protect a user’s personal information and the security of Vista in general, Internet Explorer 7 comes with many new advances in security and tools to help prevent or limit damage from an attack. One simple change is with the Secure Sockets Layer (SSL) protection offered when using the browser. Commonly, a padlock icon will show up in the bottom of the browser indicating that you are entering a “secure” site that uses encryption technologies. Now, the new security status bar helps by showing you in clearer terms that a site you are visiting is safe. The padlock also appears closer to the top of the browser and is highlight blue when safe. This is but one very simple example of things that have changed to make your browsing experience easier and safer.
Basic Browser Behavior
When surfing the Internet, it’s easy to visit sites that you think are safe, but are not. These sites can introduce malware when you click on the site itself, when you download a file from the site manually and install it, or worse, when you are conned into believing that the site you’re visiting is a real site, but in fact is nothing more than a fake used to garner your personal information.
Browser Exploits
Web browsers are client software programs, such as Internet Explorer, Netscape, and Opera, that connect to servers running Web server software (such as IIS or Apache) and request Web pages via a URL, which is a “friendly” address that represents an IP address and particular files on the server at that address. The browser receives files that are encoded (usually in Hypertext Markup Language [HTML]) and must interpret the code or “markup” that determines how the page will be displayed on the user’s monitor. Browsers are open to a number of attack types. The embedded scripts (and even some of the markup language) can be used to exploit your browser. With Internet Explorer 7, new tools such as the Phishing Filter help to thwart these attacks.
Early browser programs were fairly simple and could be exploited by using minimal techniques. Today’s browsers are highly complex, signaling the need to secure them even further. These newer browsers are capable of not only displaying text and graphics, but also playing sound files and movies and running executable code. The browser software also usually stores information about the computer on which it is installed, as well as the user (via data stored as cookies on the local hard disk), which can be uploaded to Web servers—either deliberately by the user, or in response to code on a Web site. These characteristics serve useful purposes. Support for running code (as “active content” such as Java, JavaScript, and ActiveX) allows Web designers to create pages that interact with users in sophisticated ways. Cookies allow users to set preferences on sites that will be retained the next time they visit the site.
However, hackers and attackers can exploit these characteristics in many ways. For example, an attacker can program a Web site to run code that transfers a virus to the client computer through the browser, erases key system files, or plants a “backdoor” program that then allows the hacker to take control of the user’s system.
Web Spoofing
Web spoofing is a means by which an attacker is able to see and even make changes to Web pages that are transmitted to or from another computer (the target machine). These pages include confidential information such as credit card numbers entered into online commerce forms and passwords that are used to access restricted Web sites. JavaScript can be used to route Web pages and information through the attacker’s computer, which impersonates the destination Web server. The attacker can send e-mail to the victim that contains a link to the forged page, or put a link into a popular search engine. SSL doesn’t necessarily prevent this sort of “man in the middle” attack; the connection appears to the victim to be secure, because it is secure. The problem is that the secure connection is to a different site than the one the victim thinks he is connecting to. Hyperlink spoofing exploits the fact that SSL doesn’t verify hyperlinks that the user follows, so if a user gets to a site by following a link, he can be sent to a spoofed site that appears to be legitimate.
Web spoofing is a high-tech form of con artistry. The point of the scam is to fool the user into giving confidential information such as credit card numbers, bank account numbers, or Social Security numbers (SSNs) to an entity that the user thinks is legitimate, and then using that information for criminal purposes such as identity theft or credit card fraud. The only difference between this and the “real- world” con artist who knocks on a victim’s door and pretends to be from the bank, requiring account information, is in the technology used to pull it off.
Certain clues may tip off an observant victim that a Web site is not what it appears to be, such as the URL or status line of the browser. You may think you are going to a Web site simply because it’s listed in the URL field, while in another location on the browser, it’s indicated that you are going to a different URL. An attacker can also use JavaScript to cover his or her tracks by modifying these elements from your view. An attacker can even go so far as to use JavaScript to replace the browser’s menu bar with one that looks the same but replaces functions that provide clues to the invalidity of the page, such as display of the page’s source code. Later versions of browser software have been modified to make Web spoofing more difficult. Older browsers are highly vulnerable to this type of attack. Improvements in Internet Explorer thwart spoofing attacks, because now you can check the validity of each site you visit.
Configuring Internet Explorer Securely
Now that you have a clear understanding of the types of malware in existence and the steps Microsoft has taken to prevent you from being exploited, let’s discuss how to configure and use these tools and settings. With Internet Explorer 7, there are many ways to improve security. Internet Explorer 7 in Windows Vista represents a major step forward in browser security and privacy protection. All of Internet Explorer 7’s security features revolve around making your computer and Web browsing experience all that it can—and should—be.
Protected Mode
Internet Explorer 7 has a new mode, called Protected Mode. When in Protected Mode, the browser will run without fear of malware taking over with elevated privileges. In addition to providing a more secure architecture in which to work, Protected Mode also assists with handling and verifying any scripted or automated action that would move data around the system, such as from the Temporary Internet Files folder, a haven for malware. Figure 2.1 shows the browser with Protected Mode enabled (or on) by default.

ActiveX Opt-In
Internet Explorer 7 allows for tighter control and security when working with ActiveX components. Many attacks have exploited ActiveX in the past. ActiveX components can handle file download and installation for the computer user. Although this is handy, malware takes full advantage of it whenever it can. ActiveX runs only on Microsoft-based systems, as it is made and updated by Microsoft in a proprietary fashion.
A new feature called ActiveX Opt-In will disable all ActiveX controls that haven’t been prescreened. In other words, if an ISV does not preset the control to work with Vista and Internet Explorer 7, it will not work. In fact, the security status information bar in Internet Explorer 7 will give you the option to work with each ActiveX control on a case-by-case basis. This allows the user to know exactly what each control is doing, what’s being installed, and so on.
Fix My Settings
Nothing could be easier than pressing one button to accomplish multiple tasks. Toward that end, Internet Explorer 7 has a new feature called Fix My Settings, which allows you to adjust the browser’s default settings with just a single click. Used with the Security Status Bar, Fix My Settings helps users quickly determine whether a Web site is authentic and whether changes to their settings by a site are appropriate, and will even suggest settings for the user.
Figure 2.2 shows the Fix My Settings feature in action. If you visit a Web site that is questionable and Internet Explorer believes you may be at risk, the Security Status Bar will warn you of danger and give you options to fix or avert the danger. Here, you can see the Fix Settings for Me option, which will walk you through adjusting your settings so that you are not exploited.
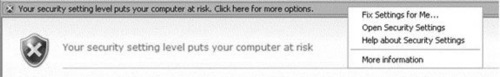
If you have issues with your browser, you can always reset it from within the Internet Options settings found in Internet Explorer, by going to the Tools menu and selecting either the Security tab (which will allow you to reset the zone directly) or the Advanced tab (where you can choose the Restore advanced settings option). Then, you can turn your browser back to the manufacturer’s settings, as shown in Figure 2.3.

Security Status Bar
As mentioned earlier, the new Security Status Bar used with Internet Explorer 7 keeps an eye out for you as you browse, and makes suggestions based on your browsing habits. In other words, if Internet Explorer feels you are at risk, it will warn you and suggest a way to protect yourself from the possible threat. The Security Status Bar operates by alerting you to issues that it believes may harm your system, and gives you options to help you navigate a potential issue. Users can now very quickly be warned about Web sites that are either authentic or spoofed/malicious in nature. By enhancing access to digital certificate information, which in turn helps validate the trustworthiness of e-commerce Web sites, you can now shop online with more confidence.
Windows Defender
Windows Defender enhances security and privacy protections when used with Internet Explorer 7. Although we will cover Windows Defender in more depth later in this chapter, it’s important to know how it works with Internet Explorer 7 to secure your browsing experience.
Windows Defender is Microsoft’s new spyware destroyer. When used with Internet Explorer 7, Windows Defender can help to scan all data traversing the browser for malware signatures. If it finds such a signature, it will work with Internet Explorer 7 and help you rid yourself of it. Defender will also keep an eye on spyware that is attached to (piggybacking onto) legitimate software which tries to install without your knowledge.
Setting Internet Zones
One of the most important features of Internet Explorer 7 is the ability to configure zones. When you open Internet Explorer’s properties, you will find the Security tab, which houses the Internet, Local intranet, Trusted sites, and Restricted sites zones (see Figure 2.4). You can configure these zones to allow for tighter security, or less-restrictive security, based on your browsing habits. For example, if you access the Internet and your local intranet simultaneously, you may need to configure security differently in each zone.
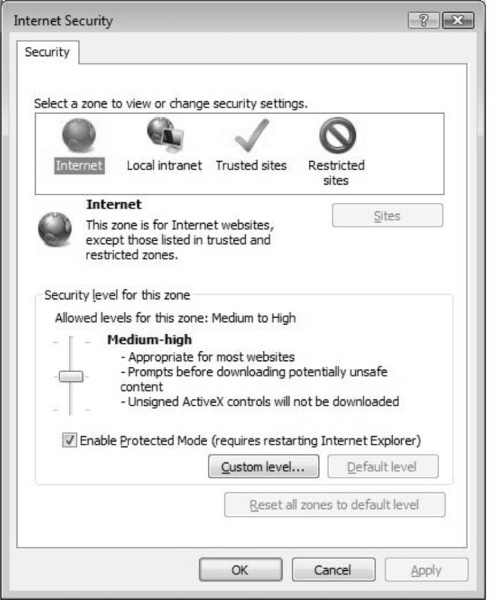
As you can see in Figure 2.4, you can set each zone to the specific level of security you need. For instance, you may want to set the Internet zone to a very high level to avoid malware attacks (for the most part), even though it will reduce your browsing functionality severely, or you may want to set the Internet zone to a very low level so that you can do anything you want to do with your browser. You also can enable Protected Mode within this dialog.
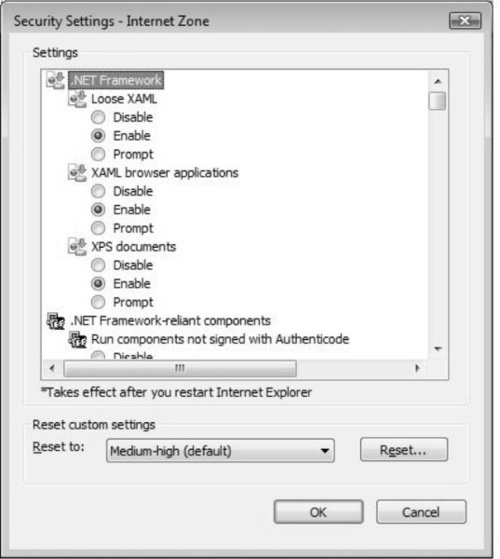
If you need to configure more granular security, you can click on the Custom level button, which will open the Security Settings dialog for the zone you have selected. So, if you want to configure more granular levels of security on the Internet zone, select that zone and select Custom level, which will open the settings for that particular zone. Figure 2.5 shows advanced settings in which you can adjust for the Internet zone to include advanced cookies.
Configuring Privacy
The next tab you can configure within Internet Options is your privacy level. In the Internet Options dialog box, select the Privacy tab. In the Privacy tab, you will find many settings to help secure your browser further. For example, you can select privacy settings based on a specific zone. In Figure 2.6, you can see privacy settings for the Internet zone. When configured correctly, you can either raise or lower the privacy settings you want based on your browsing habits. In Figure 2.6, the Internet zone is configured with a medium privacy rating. This makes sure that all third-party cookies are blocked from doing things you may not want them to do.
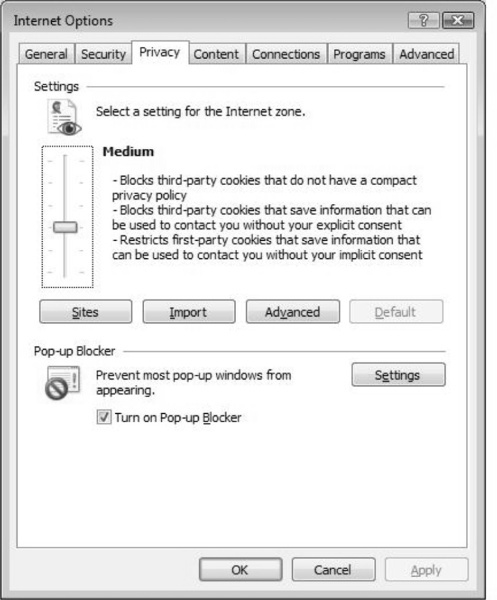
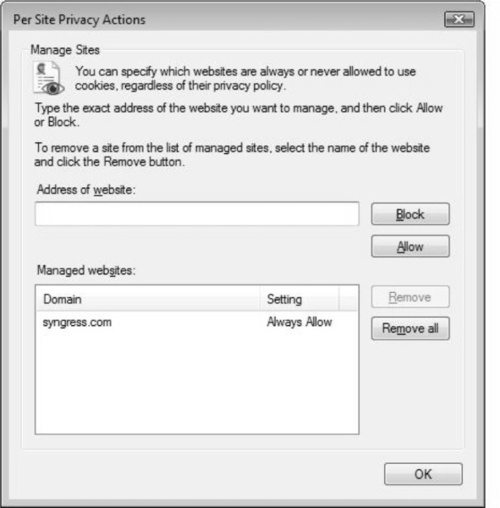
You can also select the Sites button, which will allow you to configure specific sites that you will either allow or not allow to use cookies, regardless of the privacy policy you select. In Figure 2.7, you can see that Internet Explorer 7 is always set to “allow” cookies from www.syngress.com. Although the privacy settings may disallow cookies altogether, this setting allows you to manually override Internet Explorer’s privacy settings to allow any site you feel is not a threat.
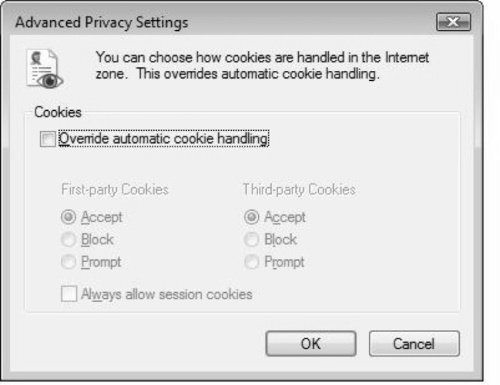
You can also use the Advanced button on the Privacy tab to specify how cookies should be handled in a particular zone. For the Internet zone, you can configure to override automatic cookie handling, and specify more granular settings, as shown in Figure 2.8.
Internet Explorer 7 also provides settings that allow you to control your security. On the bottom of the Privacy tab dialog you will find the Pop-up Blocker. Here, you can enable the Pop-up Blocker to block any pop up (or warn of a pop up) whenever you surf the Internet. By clicking on the Settings button, you can further control the Pop-up Blocker. You also can specify sites from which you will allow pop ups without the need to be prompted (see Figure 2.9), in case you visit sites often that have pop ups which are generally benign in nature.
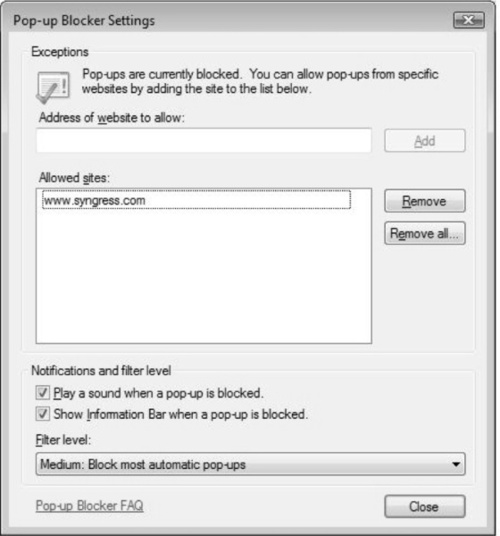
Other settings include a filter level, which can help you select a filtering level that makes sense for your browsing habits, as well as information bar settings and notifications such as sounds that will play when a problem occurs.
Advanced Security Settings
The last tab in the Internet Options dialog is the Advanced tab, as seen in Figure 2.10. Within this tab, you will find more than 100 settings that you can adjust. The best way to see what you can do is to scroll through all the options and read them one at a time, as they are very self-explanatory. In Figure 2.10, you can see a few settings that are crucial to applying security to Internet Explorer 7 and should not be overlooked.
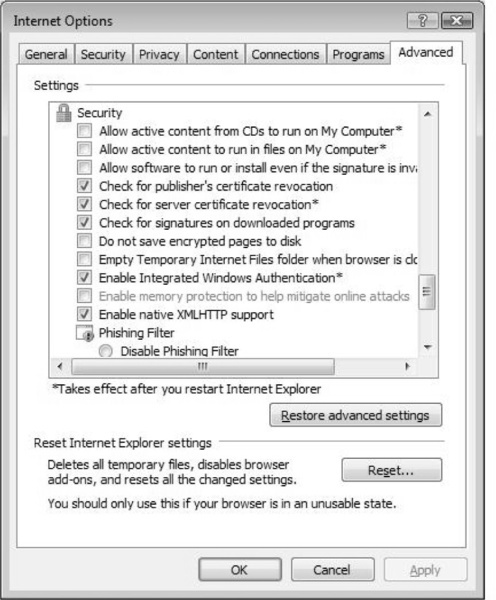
For example, you can set more advanced security settings within the Security branch of the Advanced tab. Here you can adjust Internet Explorer’s behavior by further controlling what it can and cannot do. For example, you can select to Allow software to run or install, even if the signature is invalid. Obviously, you would want to leave this unchecked because an invalid signature could lead to an exploited browser, depending on the nature of the site visited.
Figure 2.11 specifies more settings you can adjust to control Internet Explorer 7. Here you can adjust how the Phishing Filter behaves, as well as use of the SSL and Transport Layer Security (TLS) protocols.
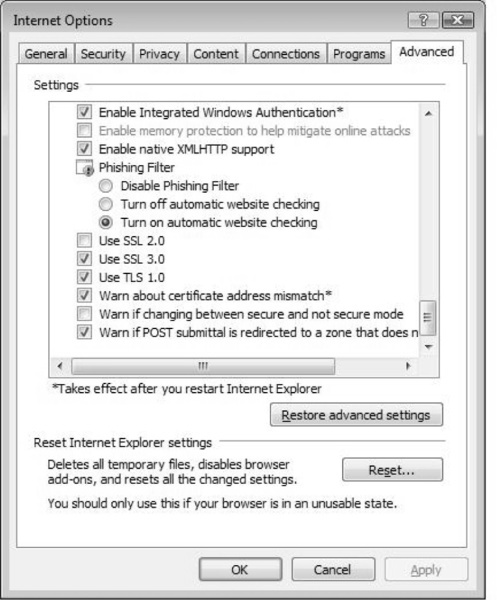
Once you have completed setting your Advanced security options, click on OK to close the dialog box. Some changes may require you to restart Internet Explorer. Simply close the browser and reopen it to continue working with your new settings.
Configuring the Microsoft Phishing Filter
The Microsoft Phishing Filter is new to Internet Explorer 7. It protects you from phishing attacks while you’re surfing the Internet. Phishing is a technique that attackers use to trick you into giving up personal data, credentials, or other information by posing as legitimate businesses or operations. Phishing attacks are not new. For example, clever attackers in the past have spammed AOL users with spoofed email purporting to be AOL. Many users were tricked into giving up their account information because they had no idea that a Web site operator could trick them into doing so with nothing but a similar-looking Web site that claimed to be something it wasn’t. It wasn’t until the end-user community started learning about spoofed Web sites and other ways attackers were getting people’s personal information (sometimes without them even knowing about it) that AOL began to warn users against giving up their personal account information to anybody other than AOL, and to practice due diligence in checking for signs of phishing attacks by examining the URL to ensure that they were being approached by AOL and not by a spoofed site.
Phishing is the exploit hackers use to obtain personal information from unsuspecting users. It continues today, and you can find examples on the wildly popular site MySpace (www.myspace.com). MySpace has suffered from the same issues AOL worked through—malicious Web site operators pretended they were from MySpace when they were really gathering legitimate users’ credentials and, inevitability, their personal information. MySpace owners posted the same types of warnings that AOL did years ago.
To take the security responsibility out of end users’ hands, Microsoft designed and implemented the Phishing Filter into Internet Explorer 7. Now, if the end user wants to stay secure and not have to worry about checking his browser for clues that the site he is visiting is the real deal, he can simply turn on the Phishing Filter and it will ensure through verification steps that the site the end user is visiting is, in fact, legitimate.
When the Phishing Filter is turned on, it performs a few steps every time you visit a Web site. First, it verifies against a locally stored list that the Web sites you are trying to visit are not fraudulent. It will also analyze visited sites for suspicious behavior that is commonly associated with Phishing Web sites. Then, it will connect to an online service that constantly updates it with phishing attack sites that have been found and blacklisted.
You can adjust the Phishing Filter’s settings from within Internet Explorer. When you open Internet Explorer 7, click on Tools and then Phishing Filter. Here you can turn the filter on or off (see Figure 2.12). Microsoft recommends that you used the filter at all times, as this will provide you with the highest level of security.
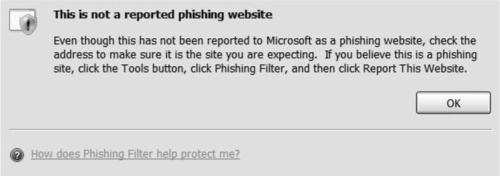
To see the Phishing Filter at work, you can manually run a check on a suspicious Web site. To verify the validity of a site, click on Tools, then Phishing Filter, and then Check This Website. If the site is safe and legitimate, as in Figure 2.13, the Phishing Filter will report as such.
Internet Explorer 7 is the most secure version of the browser to date, and strides in programming to make it safer have been successful. In the next section, we will take a look at the Windows Security Center (WSC), which is used to keep your system’s security centralized.
Windows Security Center
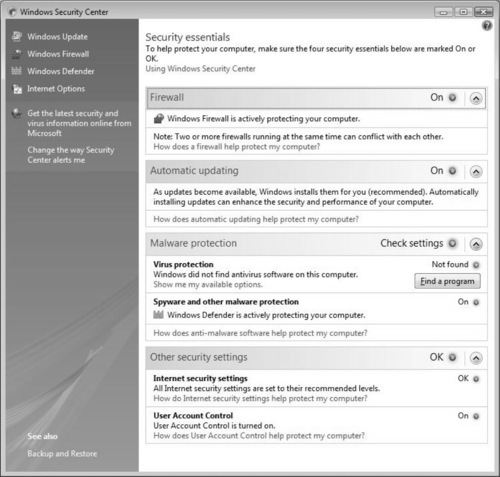
The Windows Security Center (WSC) is the brain and nervous system for Vista when it comes to security. The WSC, which debuted in Windows XP SP2, has been updated with new features, new tools, and more functionality. Through the WSC (see Figure 2.14), you can make sure that the four security essentials—the firewall, automatic updating, malware protection, and other security settings—are enabled to keep the system secure.
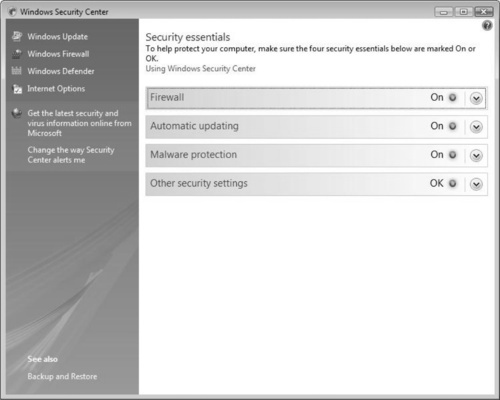
You can reach the WSC in several ways when you first load Windows Vista. By default, the Welcome Center will load when Vista first boots. In the Welcome Center, you can select Control Panel in the Get started with Windows section. Or you can open the Control Panel from the Start menu. In the Control Panel, you can select Security and then Security Center, or if you’re in Classic View, you can select the Security Center Control Panel applet.
Once you open the WSC, you will be given options to configure Windows Firewall settings, Windows Update settings, malware protection, and advanced Internet Explorer settings. In Figure 2.14, Windows Vista is operating with a configured firewall, is configured for automatic updates, is running spyware software, and is using an updated antivirus software product. Any issues within any of these areas will result in the WSC alerting you to the issue, as well as recommending a possible solution.
Configuring a Firewall
To configure the firewall to allow or disallow specified traffic, first open the Windows Firewall settings by going to the Control Panel, selecting Network and Internet, and then clicking on Windows Firewall.
Here, you can turn the firewall on or off, as shown in Figure 2.15. It’s recommend that you leave it on, especially if you do not have a third-party firewall application you would like to use in its place. Having multiple firewall products on one system is usually more of a configuration headache than it’s worth. To further configure the Windows Firewall, click on the Change settings link within the Windows Firewall dialog box.
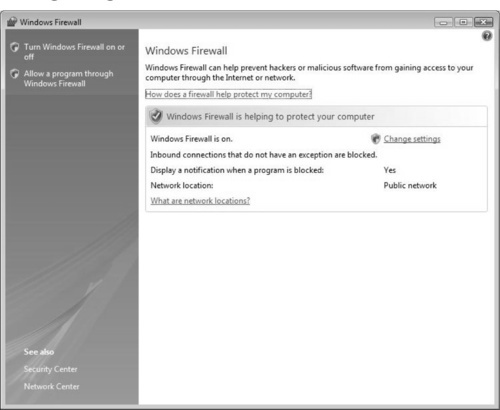
Here, you can adjust other settings, such as allowing or disallowing application- specific traffic to and from intended sources and destinations. In Figure 2.16, the General tab is selected. From here, you can turn the firewall on or off, as well as block all incoming connections if needed.
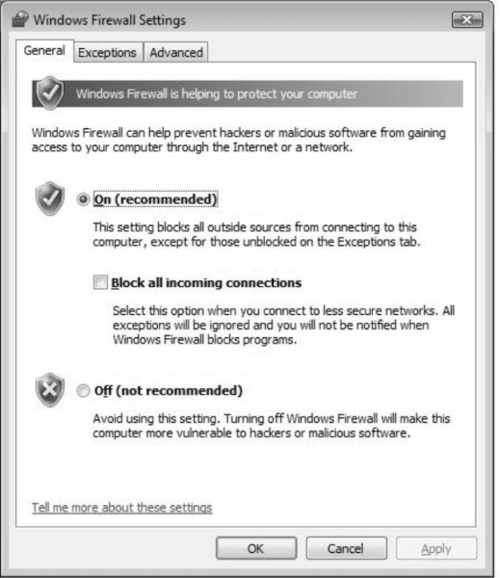
Click on the Exceptions tab, and you can configure how programs will communicate through the Windows Firewall. As shown in Figure 2.17, you can select a program that you want to block or unblock by its name or port number designation. Click on Add program to add a specific program you want to control access to, or use Add port to specify the application’s port number. For instance, you could allow Secure Shell (SSH) and not Telnet for remote access. You can also specify the program (SSH or Telnet) or specify what ports to use (which in this case would be 22 and 21, respectively).
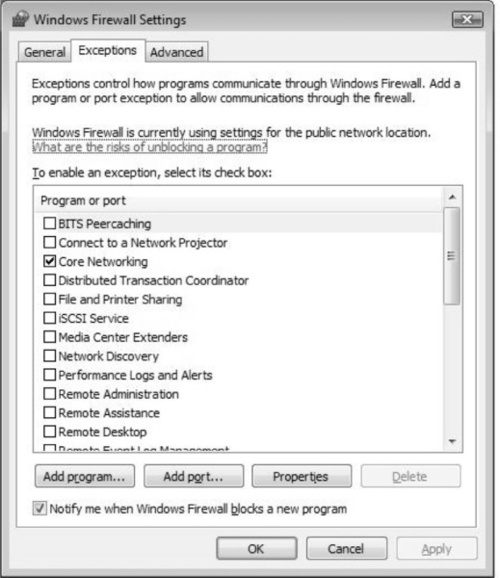
The Advanced tab gives you options for selecting to which network connections you want to apply the firewall’s security. It’s recommended that if you are going to use a firewall, you protect all possible entry points into the system. Figure 2.18 shows how you can select a local area connection as well as a wireless network connection.
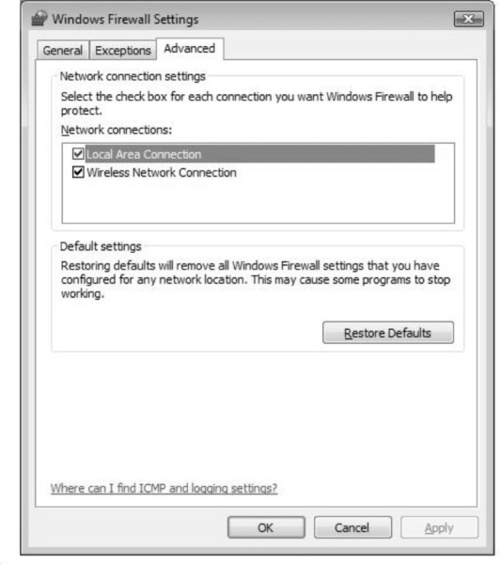
You can also set the Windows Firewall back to its default settings, by clicking on the Restore Defaults button.
Once your firewall is configured, you need to update it only if you want to restrict or allow access to new programs, or if you want to change settings. Otherwise, your firewall will alert you if any issues arise, and the WSC will alert you if there are any issues with your firewall.
Using Windows Update
Windows Update has been evolving every year since the late 1990s. When Microsoft first released its software offerings many hotfixes and service packs followed. At one time, you had to visit Microsoft’s Web site, find the download you needed from the Downloads section, and then install it. Now, a centralized Web service hosted by Microsoft will work as the server-side function listening for the client side to contact it with its needs.
Updating Microsoft Windows and many other Microsoft programs (such as Microsoft Office products, Internet Explorer, and so on) is now quick and almost seamless. Also, now you don’t have to visit Microsoft’s Web site to get downloads, because once you turn on Automatic Updates, updates will be downloaded to your client at a specified time and will be ready for you to confirm and install the next time you are at your PC.
You can turn on Automatic Updates in the WSC or in the Control Panel. Once enabled, Automatic Updates will find and install updates for all of the Microsoft products you have installed.
To run Windows Update, click on the Windows Update link in the WSC on the top left-hand side of the dialog box. By clicking on this link, you will open the Windows Update Wizard seen in Figure 2.19. Once launched, the wizard will quickly scan your system’s logs to verify what you have installed and what you currently need. Internet Explorer will work with Windows Update at Microsoft.com to produce a list of what you need to install and guide you through the install process.
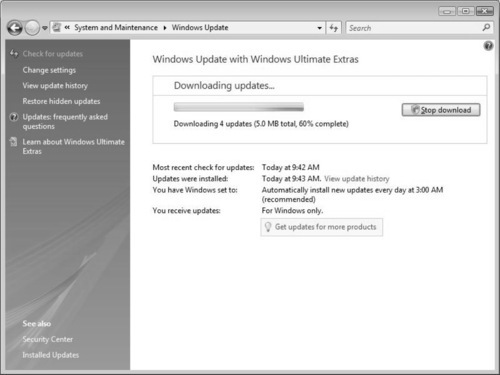
Figure 2.20 shows the available updates you can install on Vista. Here you can see the updates specific to Windows Vista (such as drivers, etc.) as well as the applications, such as Windows Defender. Click on Install to install the updates you would like to install. You can uncheck any update you do not want to install.

Using the Malicious Software Removal Tool
When running Windows Update, you will commonly find a download for the Malicious Software Removal Tool. This is a tool that will help to remove malware from your OS. Since January 2005, this tool has been run more than 3.2 billion times, on more than 270 million computers each month, to combat the spread and flood of malicious software over the Internet. Every month, Microsoft releases a new version of the tool through Microsoft Update, Windows Update, and the Microsoft Download Center.
The Malicious Software Removal Tool will also verify that your system is malware-free before you upgrade from, say, Windows XP to Windows Vista.
Configuring Malware Protection
When working within the WSC, you can configure Malware Protection so that your PC proactively looks out for exploits against which it is currently configured to guard. The WSC will periodically check to ensure that your system is kept updated. It does this by checking that your antivirus software is on, is not damaged, and is updated with signatures and definitions, and by checking your spyware software to make sure is it updated and in working order as well. If nothing is installed, you will be warned that this is not recommended.
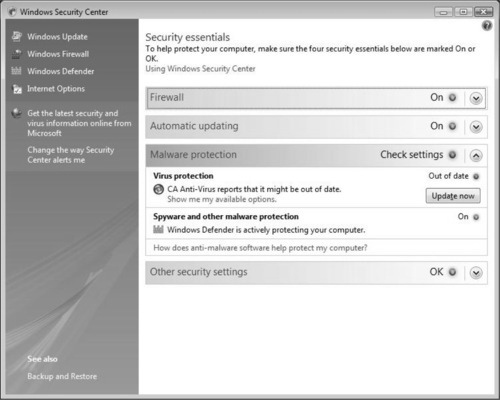
Figure 2.21 shows the WSC indicating that it couldn’t find a valid antivirus application located on the system. Because this will most likely lead to infection or exploitation, it is flagged as an issue for you to resolve. The Check settings indicator (also colored yellow) indicates that no program is installed and/or that it is damaged.
Be aware that if your antivirus software is installed but is out-of-date, you will be given a different indicator. You will still be asked to Check settings, but the indicator will be colored red (see Figure 2.22).
It is imperative that you keep your antivirus signatures, definitions, and engine updated; if you don’t, the WSC will report a problem. In Figure 2.23, the WSC is reporting that malware protection is on and up-to-date.
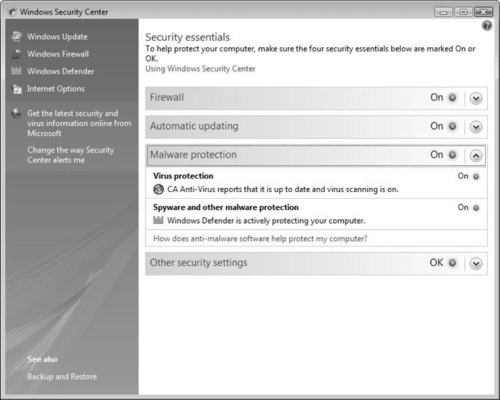
Once you resolve all issues, the Malware Protection section of the WSC will return to its green indication status. This means your system is now ready to do battle with malware because it is completely updated and healthy, and is running optimally.
Microsoft Windows Vista is a brand-new product on the market so its important to consider your older software applications may not run on it at first., Third party vendor software generally do not have full version releases of heir software tested and ready to go, so its important to do some research on what is supported before you upgrade to Windows Vista.
Other Security Settings
In the WSC, you have a fourth area of configuration, called Other security settings. Here, you can check Internet Explorer’s security settings, as well as use User Account Control (UAC).
User Account Control
User Account Control (UAC) UAC is a new tool used with Windows Vista for preventing unauthorized changes. UAC is another level of security applied to the defense in depth model. UAC (known in earlier Windows versions as Least-Privilege User Account [LUA]) is responsible for warning you whenever Windows needs your permission to continue with the use of a program or other application. LUA followed the concept that if the LUA account was jeopardized, it would not cause a serious issue because it did not have administrator privileges. If the account was compromised, there wasn’t much you could do with it.
When a user now logs on to a Windows Vista computer, she is logged on by default as a standard user. If she needs to perform a task in which administrator privileges are required, Vista (with the help of UAC) will prompt her for specific permission to perform the task. This helps to make sure that malware cannot manipulate her account if jeopardized.
When an administrator needs to use her administrator privileges, she doesn’t have to use Run As, because Windows Vista can automatically prompt her for the required credentials, as shown in Figure 2.24. In the past, accounts for standard users contained too many available permissions. Now, standard user accounts are locked down to allow for only the privileges that are needed; anything that requires administrator privileges (such as installing software on the system) will require that the user log on with an administrator account. Because UAC is enabled by default, it will be invoked whenever administrator logon is required. In past versions of Windows, such as XP, you needed to use Run As to log on with administrator rights, although if the user account had been jeopardized, it wouldn’t matter anyway. UAC is a major development in terms of giving only those privileges that users need to do their jobs. As a result, if their accounts are compromised, the risk is lessened.
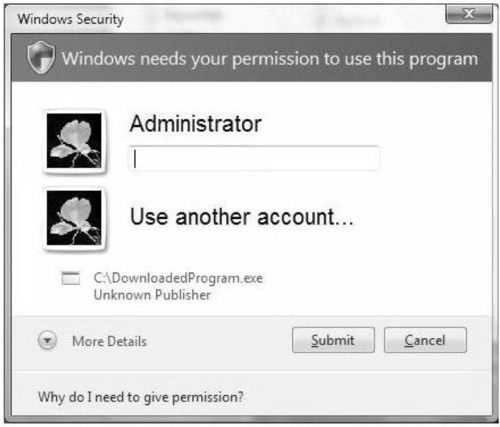
Windows Vista automatically prompts you for administrator credentials when an application requests them. This way, another level of security is implemented to help ensure that the user isn’t manipulated or that malware running silently doesn’t infiltrate the system.
Windows Defender
In December 2004, Microsoft acquired the Windows Defender security technology from GIANT Company Software, Inc. Windows Defender provides continuous security against malware, and if it detects anything suspicious, it will alert you of what it finds. It does this by using three specific tools:
■ Internet agents Internet agents are used to monitor changes to Internet access settings, as well as to stop unauthorized connection attempts via the network.
■ System agents System agents are used to monitor changes to your system’s settings, such as passwords and permissions.
■ Application agents Application agents are used to monitor changes to applications installed on your OS, such as Internet Explorer being modified by downloadable toolbar applications.
Windows Defender protects against and removes malware as well as provides control over modifications to software installed on the system. Windows Defender provides real-time monitoring functionality, which means it will always run and keep you protected while you’re using your Windows Vista system. The Windows Vista version of Windows Defender features an updated scanning engine, simplified alerting functionality, multiple-language support, and other enhancements.
Windows Defender provides top-notch spyware detection and removal, and it is connected to an online service that will keep it updated and on top of the latest threat trends. Because malware constantly evolves, so does Windows Defender and its support team.
Using Windows Defender
You can find Windows Defender by opening the WSC and selecting the Windows Defender link. This will invoke the Windows Defender application, as shown in Figure 2.26. If your system is already up-to-date, Windows Defender will report that there is no harmful or unwanted software on your system and that your computer is running normally. If you have not run a scan yet, or your last scan was a while ago, you will be prompted with scan options.
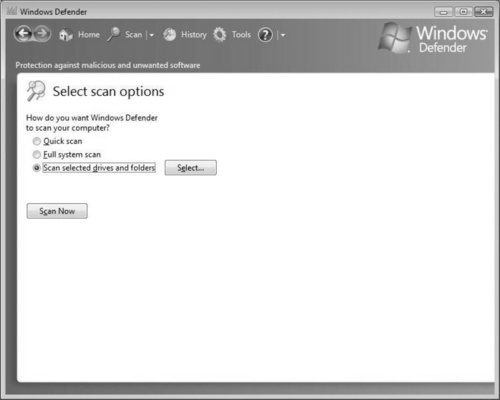
Select the scan option that best suits what you want to do. If you want to perform a quick scan of the most common areas within your system affected by malware, check the Quick scan radio button. If you want to check your entire system, check the Full system scan radio button (note that a full system scan will take far longer to perform than a quick scan). You can also specify which drives or areas of your system you want Windows Defender to scan.
Figure 2.27 shows Windows Defender prompting you to begin a scan. Click on Scan Now to begin the scan.
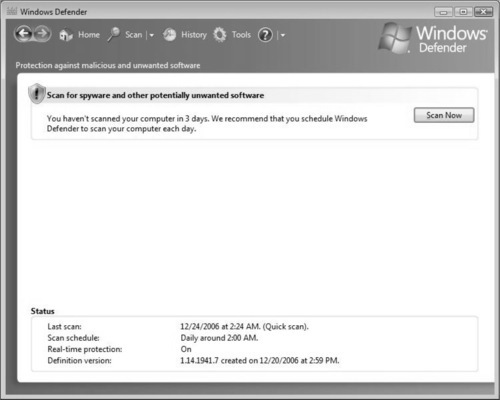
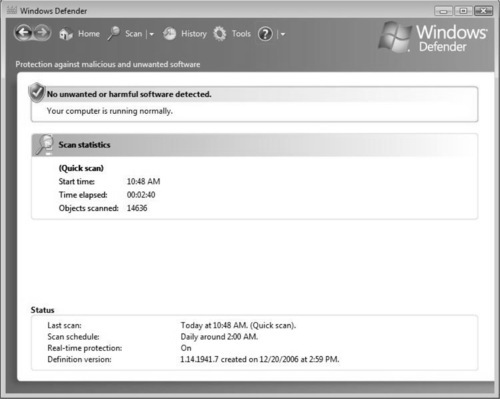
Once the scan is complete, you can view the report. If anything malicious is found, you will be asked how you want to handle it. Figure 2.28 shows Windows Defender completing a quick scan and not finding any malware on the system. (Because this was a quick scan, there still may be an issue with this system, however; a full system scan should be run to verify that the system is in fact free of malicious software.)
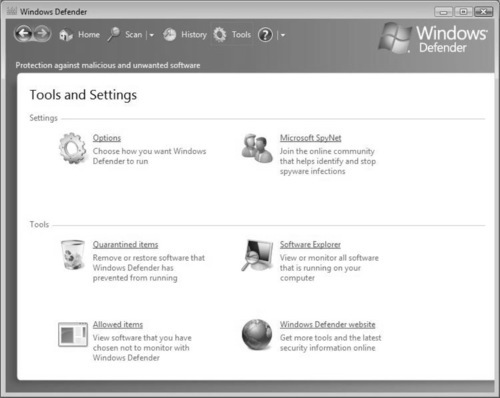
By clicking on Tools on top of the Windows Defender dialog box, you can adjust the settings for Windows Defender and select other tools to further secure your system. As shown in Figure 2.29, once you open the Tools and Settings configuration within Windows Defender, you can change the settings, use Microsoft SpyNet, view quarantined items, use the Windows Defender Software Explorer, set allowed items, and visit and use the Microsoft Windows Defender public Web site.
How to Use the Windows Defender Software Explorer
One of the newest and most helpful tools Microsoft has added to Vista and Windows Defender is Software Explorer. Software Explorer provides you with an unfettered view of the software that is currently running on your computer, along with details of each piece. It also helps you monitor programs that are set to start when the computer boots, programs that run in the background or as background processes, and programs that are used to perform low-level network functions (i.e., Winsock service providers).
Using Software Explorer
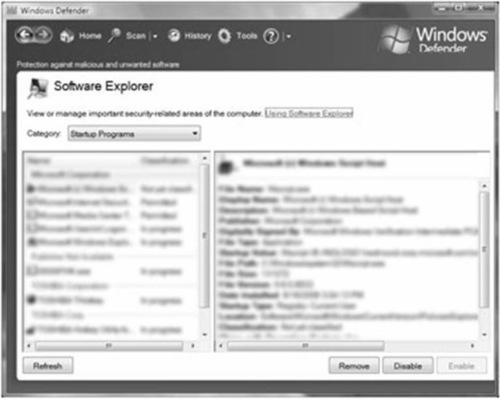
Changing how a program runs on your computer, such as blocking Internet or network connections and ending processes, can cause problems with Windows and other programs that you use. Use Software Explorer to change how a program runs on your computer only if you are certain the program is causing a problem. Once you open Software Explorer, you can select which category of programs you want to view or adjust. For example, in Figure 2.30, you can see Software Explorer in use. Here, the Startup Programs category is shown but blurred out to protect the identity of the system in use.
Other Related Tools
In the Tools and Settings dialog of Microsoft Defender, you can find links to more tools and settings. Here you will find SpyNet, a very useful Web site that helps you find information on malware as well as information on combating it and protecting yourself and your system from its threat of damage.
Using Microsoft SpyNet
Microsoft SpyNet is the network of Windows Defender users that helps determine which programs are classified as spyware. Because the face of malware constantly evolves, so does SpyNet and its hardworking team of security enthusiasts.
SpyNet works to build known signature files for commonly seen malware and to find malware that is new to the scene. It is recommended that you visit SpyNet to get acclimated with the site and the benefits it offers, and that you check back often for updates.
If you commonly surf the Internet and are worried about the effects of malware on your system, visiting SpyNet can give you an advantage, as you will be better educated on what can happen to your system, what is currently happening to others, and how you can support and better secure your OS, your browser, your identity, and your personal data.
Summary
Malware is a threat to computer systems, networks, and the public Internet. With the release of Windows Vista, Microsoft has developed new weapons in the battle against malware. Windows Vista, Internet Explorer 7, and associated software are hardened and ready for war.
Malware is any software product or program created with an intent to cause damage or harm. The most common forms of malware are viruses, Trojans, and worms. Viruses are malicious programs that are commonly installed on a target host with the intent to cause harm or damage. Common virus types include e-mail viruses, boot sector viruses, application viruses, and macro viruses. Worms are a form of malware that will propagate from host to host in order to spread and replicate across a network. A Trojan will appear harmless to the recipient, but actually contains a malicious payload. Trojans that contain a virus as a payload are called droppers. Spyware is the biggest malware issue to date. Spyware exploits include malicious scripts that do everything from rewriting browsers to perform malicious functions, to forcing payment for legitimate revenue streams to a secondary source (usually that of the attacker).
Windows Vista and Internet Explorer 7 were developed to thwart many common exploits and build a foundation in which new ones can be mitigated. New to Vista and Internet Explorer 7 is an updated Windows Firewall. The new outbound filtering feature in the personal firewall helps to apply more granular control over traffic traversing it, and is more flexible than previous versions. The new Phishing Filter is used to verify the validity of the sites you visit so that your personal information and data are not compromised. User Account Control (UAC) allows a user to change computer settings while running as a standard user, instead of requiring administrator privileges to perform most tasks. The updated Windows Defender utility detects malware on your system and, when used in conjunction with SpyNet, can help to eliminate most spyware attacks and exploits. The new Windows Security Center (WSC) is full of configurable options and tools to help you build a strong security posture so that you can safely surf the Internet without constantly worrying about your system. As you can see, there are many ways you can apply defense in depth for a more secure infrastructure.
Malware is definitely a threat, but these new tools and features help to provide a more secure experience. Microsoft Vista takes steps to ensure that the base OS is not jeopardized, and Internet Explorer 7 provides a secure framework in which to operate. Although the battle against malware continues, at least with Vista and Internet Explorer 7 you are well armed to fight that battle.
Solutions Fast Track
Malware Fundamentals
☑ Malware is any software product or program created with the intent to cause damage or harm. The most common types of malware are viruses, Trojans, and worms.
☑ A virus is a malicious program that is commonly installed on a target host with the intent to cause harm or damage. A virus (just like the medical version of the term) infects the host, usually by being installed by the end user of the target host. A virus is almost always executed by the end user without him knowing the true intention of the malware.
☑ An e-mail virus is transmitted via e-mail and contains a payload that is activated when the end user is provoked to activate it, or when something in the e-mail client and how it reads e-mail (and scripts) activates the payload upon delivery or viewing, without opening the e-mail (such as with an automatic reading pane found in most e-mail clients).
☑ Boot sector viruses are often transmitted via disk and are written to the master boot record on the hard disk. Application viruses are executable programs that infect your system when you run them, and macro viruses are commonly embedded in documents (such as Microsoft Word documents).
☑ Worms will propagate. They are programmed to “scan” the network from the infected target host to find other hosts with open and vulnerable services and ports.
☑ A Trojan horse will appear harmless enough for the recipient to install, but it contains a secret payload that usually is a virus or other form of malware.
☑ Malware can be very nasty, especially when it and its payload are concealed. For instance, consider the use of rootkits, backdoors, and keyloggers, all of which are secretly placed on your system for a future attack.
☑ Spyware exploits are also used to obtain user information. Spyware analyzes what sites you visit and what your browsing habits are, and then invades your privacy further by using that information to market products to you, as well as by preventing you from removing the spyware.
☑ You should periodically update every piece of software you install on your system. You can do this by installing the latest updates, hotfixes, security patches, and service packs. Keep on top of when new patches come out, and try to test and install them to keep your system at its best.
☑ Windows Service Hardening (WSH) limits the amount of damage an attacker can do if a service is compromised.
☑ Network Access Protection (NAP) is used to prevent clients from connecting to the network if they are infected with malware.
Improvements in Internet Explorer 7
☑ Internet Explorer 7 comes with Windows Vista by default as the built-in Web browser. New features in Internet Explorer 7 help to prevent the inception and spread of malware. To help protect a user’s personal information and the security of Vista in general, Internet Explorer 7 comes with many advances in security, as well as tools that protect users from such malware attacks as phishing and spoofing. It also includes a new Protected Mode to further secure a user’s browsing experience.
☑ The new outbound filtering feature in the Windows Firewall helps users to apply more granular control over traffic traversing the firewall.
☑ User Account Control allows a user to change computer settings while running as a standard user.
☑ The Windows Defender utility detects malware on your system and, when used in conjunction with SpyNet, can help to eliminate most spyware attacks and exploits.
☑ Phishing is the exploit that hackers use to obtain personal information from unsuspecting users. The Microsoft Phishing Filter is new to Internet Explorer 7. It protects you from phishing attacks while you surf the Internet.
Windows Security Center
☑ The Windows Security Center (WSC) is the brain and nervous system for Vista when it comes to security. Here, you can configure most (if not all) security functionality for the client system. In addition, it monitors your running systems and recommends ways to help mitigate risk and solve security-related issues.
☑ The WSC, which debuted in Windows XP SP2, has been updated with new features, tools, and functionality. With it, you can centrally control a personal firewall application, and make sure the OS and your antivirus software are up-to-date.
☑ In the WSC, you can configure four main security areas: the Windows Firewall, Automatic Updates, Windows malware protection, and other security settings, including Internet Explorer security settings.
☑ The updated Windows Firewall now scans traffic bidirectionally. Previous versions scanned in only a single direction.
☑ Once your firewall is configured, you need to update it only if you want to restrict or allow access to new programs, or if you want to change settings.
☑ You can turn on automatic updating in the WSC, which will allow Windows to monitor and download updates for you.
☑ The Malicious Software Removal Tool can help you to remove malware from your OS and is usually downloaded via Windows Update.
☑ User Account Control prevents unauthorized changes from taking place. Another level of security applied to the defense in depth model, UAC will warn you whenever Windows needs your permission to continue with the use of a program or other application.
☑ The Microsoft Baseline Security Analyzer (MBSA) is a freely downloadable tool from Microsoft. It is designed for IT professionals who need to check the security settings on host computers.
Windows Defender
☑ Windows Defender provides continuous security against malware. If it detects anything suspicious, it will alert you of what it finds.
☑ Windows Defender is composed of three separate agents. Internet agents are used to monitor changes to Internet access settings, as well as to stop unauthorized connection attempts via the network. System agents are used to monitor changes to your system’s settings, such as passwords and permissions. Application agents are used to monitor changes to applications installed on your OS, such as Internet Explorer being modified by downloadable toolbar applications.
☑ Windows Defender is used locally to protect an end user’s Web browsing experience. Windows Defender does not include enterprise management tools.
☑ Windows Defender features an updated scanning engine, simplified alerting functionality, multiple-language support, and other enhancements.
☑ Changing how a program runs on your computer, such as blocking Internet or network connections and ending processes, can cause problems with Windows and other programs that you use. Use Software Explorer to change how a program runs on your computer only if you are certain the program is causing a problem. Once you open Software Explorer, you can select which category of programs you want to view or adjust.
☑ Microsoft SpyNet is the network of Windows Defender users that helps determine which programs are classified as spyware.
☑ SpyNet builds known signature files for commonly seen malware and finds malware that is new to the scene. It is recommended that you visit SpyNet to get acclimated with the site and the benefits it offers, and that you check back often for updates.
Frequently Asked Questions
The following Frequently Asked Questions, answered by the authors of this book, are designed to both measure your understanding of the concepts presented in this chapter and to assist you with real-life implementation of these concepts. To have your questions about this chapter answered by the author, browse to www.syngress.com/solutions and click on the “Ask the Author” form.
Q: If a company has a good firewall installed, won’t that protect it from all these attacks?
A: No. Firewall products are very useful for controlling what comes into or goes out of a network. But a firewall is like a computer (in many cases, a firewall is a specialized computer); it does only what the person who configures it tells it to do. Firewalls can recognize and stop some types of attacks, but certain attacks exploit the characteristics of the protocols commonly used for legitimate network communications, and a packet might appear to be nothing more than a benign bit of data destined for a computer on the internal network. Trojans, viruses, and worms piggyback into the network as e-mail attachments or through remote file sharing. Firewalls won’t catch them, but a good antivirus program, frequently updated and set to scan all incoming e-mail, might be able to. Many companies seem to operate under the assumption that installing a firewall is akin to invoking a magic spell that casts a force field of protection around their networks, rendering them completely immune to attack. Even the best firewall won’t protect against social engineering attacks, nor will it do any good against internal attackers who have physical access to the network. Studies have shown that a large number of network-related crimes are actually “inside jobs.” Be sure to read Chapter 3, where we discuss how firewalls work, so that you understand why they are not the “cure-all” solution to network security that they’re sometimes made out to be.
Q: I think I understand the differences between a virus, a Trojan, and a worm. But what are all these other types of viruses I hear about: stealth viruses, polymorphic viruses, armored viruses, and cavity viruses?
A: Stealth viruses are able to conceal the changes they make to files, boot records, and the like from antivirus programs. They do so by forging the results of a program’s attempt to read the infected files. A polymorphic virus makes copies of itself to spread, like other viruses, but the copies are not exactly like the original. The virus “morphs” into something slightly different in an effort to avoid detection by antivirus software that might not have definitions for all the variations. Viruses can use a “mutation engine” to create these variations on themselves. An armored virus uses a technique that makes it difficult to understand the virus code. A cavity virus is able to overwrite part of the infected (host) file while not increasing the length of the file, which would be a tip-off that a virus had infected the file.
Q: Can a rootkit be used for a good purpose, or is it always classified as malware?
A: The term rootkit was developed as a hacker term, although rootkits can also be used for what some vendors consider valid purposes. For example, if Digital Rights Management (DRM) software is installed and kept hidden, it can control the use of licensed, copyrighted material and prevent the user from removing the hidden enforcement program. However, such usage is no more welcomed than a rootkit that does damage or allows spyware to thrive without detection.
Q: I have an infected system and I cannot figure out what is wrong. Where can I look to find further information on the Internet?
A: Information about specific viruses and instructions on how to clean an infected system is available at www.symantec.com and www.mcafee.com. Both antivirus vendors provide detailed databases that list and describe known viruses. For more information on viruses, worms, and Trojans, see the article “How Computer Viruses Work,” at www.howstuffworks.com/virus.htm.
Q: What are cookies and spyware? How are they different? Do some Web sites use cookies to exploit user information?
A: A cookie is just a bit of text in a file on your computer, containing a small amount of information that identifies you to a particular Web site, and whatever information that site wanted to retain about you when you were visiting. Cookies are a legitimate tool that many Web sites use to track visitor information. For example, you might go to an online computer store and place an item in your basket, but decide not to buy it right away because you want to compare prices. The store can choose to put the information about what products you put into your basket in a cookie stored on your computer. This is an example of a good use of cookies to help the user experience. The only Web sites that are supposed to be able to retrieve the information stored in a cookie are the Web sites that wrote the information in that particular cookie. This should ensure your privacy by stopping any site other than the one you are visiting from being able to read any cookies left by that site. Some Web sites do use cookies to exploit user information, however. Some also may deceive users or omit their policies. For example, they may track your Web surfing habits across many different Web sites without informing you, and then use this data to customize the advertisements you see on Web sites, which typically is considered an invasion of privacy. It is difficult to identify this and other forms of “cookie abuse,” which makes it difficult to decide whether, when, and how to block them from your system. In addition, the acceptable level of shared information varies among users, so it is difficult to create an “anticookie” program to meet everyone’s needs.
Q: Can spyware send tracked information to other people?
A: Some forms of spyware monitor a target’s Web use or even general computer use and send this information back to the spyware program’s authors for use as they see fit. To fight this kind of problem, a spyware removal tool is obviously helpful, as is a firewall that monitors outgoing connections from your computer. Other forms of spyware take over parts of your Web browsing interface, forcing you to use their own search engines, where they can track your browsing habits and send pop-up advertisements to you at will. The biggest concern regarding spyware is that most spyware is poorly written or designed. Many people first realize their computer is running spyware when it noticeably slows down or stops responding, especially when performing certain tasks such as browsing Web sites or retrieving e-mail. In addition, poorly written spyware can often cause your computer to function incorrectly even after it has been removed.
Q: Malware has completely taken over my PC and I cannot do anything to fix it. What is the best next step?
A: You used to be able to clean up most malware infections using various kinds of specialized antivirus and antimalware software. Sadly, this is no longer the case. Once upon a time, malware was written by amateurs and teenagers. But now, many very skilled programmers work on malware, because it is now a moneymaking business. Malware has become so insidious that it is often impossible to remove without expert or professional help.
You should first attempt to remove an infection with automated tools. If that fails (and most likely it will), there are two classes of antimalware software that you should use. The first is traditional antivirus software, which is very good at handling viruses and worms and not so great at handling newer styles of mal- ware. The other kind of software is antispyware software, which is good at the newer sort of malware but not so good at the old kind. When attempting to clean up an infected system, you should run at least one of each. If you were running antivirus software when you became infected, you should see whether it was keeping itself up-to-date, or try running a different program. Proven antivirus software companies include Symantec (a.k.a. Norton), McAfee, Panda Software, Trend Micro, F-Secure, Eset (maker of NOD32), and Kaspersky Labs. Many of these companies have free Web-based scanners (ironically based on ActiveX) or downloadable tryout versions.
Antispyware software is a little more difficult. The various antivirus companies have been in business a long time, but antispyware is a new kind of software that was born at the same time as the modern age of malware. Therefore, many antispyware software companies are either incompetent or outright frauds.
It’s been discovered that malware is very quickly outgrowing the capability for automated software to clean it. The automated tools you try may not work, even if you try multiple ones. Therefore, you will probably end up having to get help. Many local computer repair companies can clean infected computers. You may know an expert who is willing to help you. Sometimes the experts will tell you that the best or only way to take care of a really bad infection is to back up your personal data, clean out the computer completely, and start from scratch. They are not lying. Attempting to eradicate an infection by hand can be extremely time-consuming and is often unsuccessful, even for experts.
Q: Do I need additional antimalware and spyware tools, now that Vista and Internet Explorer are supposedly more secure and provide them?
A: With Windows Vista and Internet Explorer 7, you are definitely more secure than you were using older versions of the OS and Web browser. The fact is that you now get these applications with the base OS instead of having to pay for or download a third-party vendor’s utility. Vista does not come with antivirus software, so you will need to acquire that separately. What Vista does have is a built- in spyware tool that helps prevent “some” malware exploits from taking place. Vista also has a built-in host-based firewall. Make sure that you add antivirus software for full protection.