Chapter 17: Implementing and Integrating Security Monitoring
Enterprises go multi-cloud and use cloud services from different cloud providers. These solutions will be secured, but enterprises want an integrated view on the security status on all of their platforms and solutions. This is what solutions such as Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) do.
In this chapter, we will learn why these systems are a necessity in multi-cloud. First, we will discuss the differences between the various systems, and then we will explore the various solutions that are available on the market today. The big question we're going to answer in this chapter is how do we make a choice and, more importantly, how do we implement these complicated solutions?
We're going to cover the following main topics in this chapter:
- Understanding SIEM and SOAR
- Setting up the requirements for integrated security
- Exploring multi-cloud monitoring suites
Understanding SIEM and SOAR
All cloud providers offer native services for security monitoring, such as Azure Security Center, AWS Security Hub, and Security Command Center in Google Cloud. However, companies are going multi-cloud using Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) from different providers. Enterprises want an integrated view of their security in all these solutions. If an enterprise is truly multi-cloud, it will need an integrated security solution with SIEM and SOAR.
Next, the enterprise needs a unit that is able to handle and analyze all the data coming from SIEM and SOAR systems and trigger the appropriate actions in case of security events. Most enterprises have a Security Operations Center (SOC) to take care of this. In this section, we will explain what the differences are between SIEM and SOAR, why an enterprise needs these systems in multi-cloud, and what the role of the SOC is.
Differentiating SIEM and SOAR
Let's start with SIEM. Imagine that workloads – systems and applications – are deployed in Azure and AWS, and the enterprise also uses a number of SaaS services, such as Microsoft Office 365 and Salesforce. All these environments are protected with firewalls in both Azure and AWS, along with on-premises data centers. Traffic is routed through virtual network devices, routing tables, and load balancers. The enterprise might also have implemented intrusion detection and prevention to protect systems in the public clouds and on-premises data centers. All these security systems will produce a vast amount of information on the security status of the enterprise environments.
SIEM systems collect, aggregate, and analyze this information to identify possible threats. Since it collects data from all environments, it's able to correlate the data and recognize patterns that might hint toward attacks. For this, SIEM uses machine learning and specific analytics software. It recognizes abnormal behavior in systems with anomaly detection. A simple example is if user A logs in from an office in London at 9.00 AM and again logs in at 9.30 AM from Singapore, a SIEM system would know that this is impossible and will raise an event or alert. The architecture of a SIEM system is shown in the following diagram:
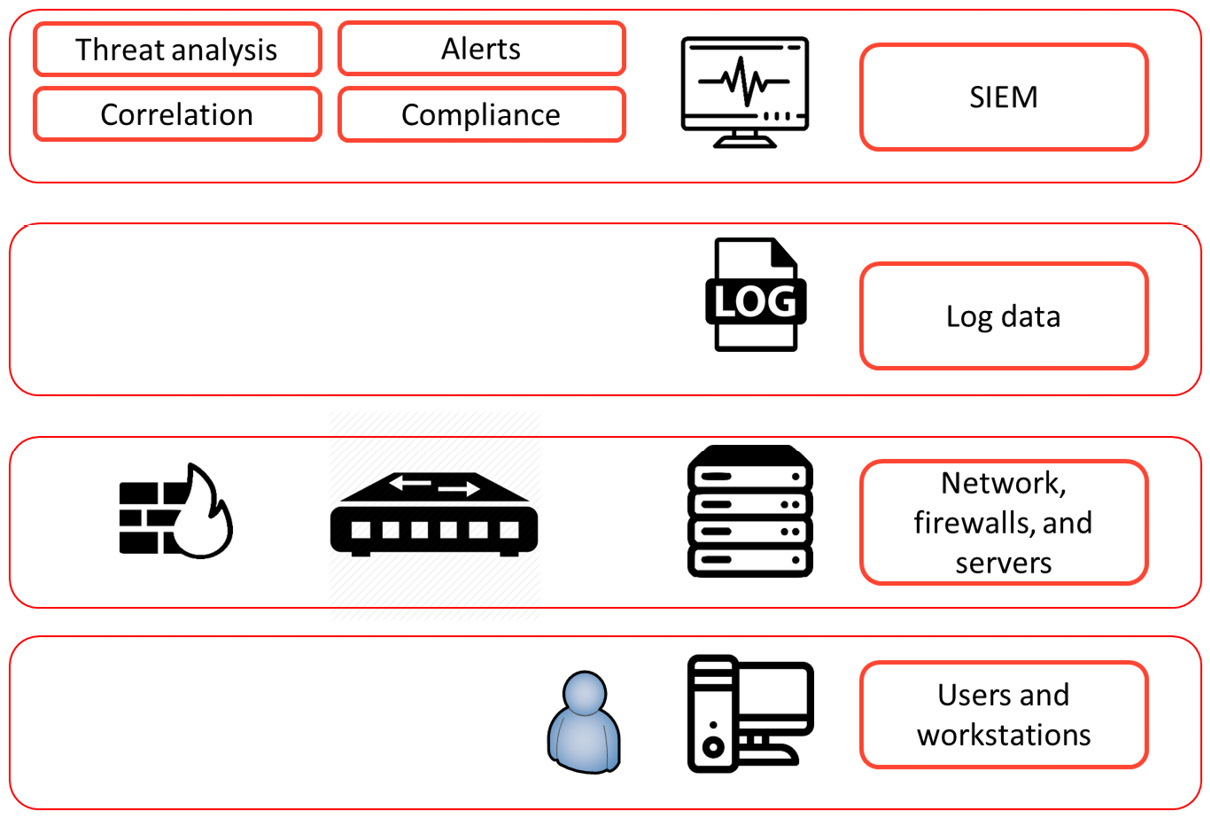
Figure 17.1 – The conceptualized architecture of a SIEM system
SOAR goes beyond SIEM. Like a SIEM system, SOAR collects and analyzes data that it gathers from a lot of different sources, such as the public cloud environments. But the added value of SOAR is in orchestration and automation. In SOAR systems, companies can define automated responses to events, using playbooks that integrate with security solutions in the platforms. If a SOAR system detects a threat in a system, it can immediately remediate it by taking actions such as closing communication ports, blocking IP addresses, or putting systems into quarantine. It does that fully automated, including logging and raising tickets to service management systems. This gives security professionals time to investigate the actual threat, without needing to worry about remediation first. That task is fixed preemptively from them by SOAR.
The role of SOC
Since the world is moving to digital, companies are increasingly threatened by digital threats. It also seems that hackers are always one step ahead of the companies themselves in protecting their digital assets. It takes a lot of skills to keep up and counter these attacks. Therefore, enterprises rely more and more on specialized groups where security expertise is bundled: the SOC. Enterprises can have these in-house or outsourced to specialized companies.
The SOC is responsible for monitoring and analyzing the security state of an enterprise on a 24/7 basis. A team of security engineers will use different technology solutions, including SIEM and SOAR, to detect, assess, and respond as quickly as possible to security incidents.
In the next section, we will explain how an enterprise can set up a SOC. In the last section of this chapter, we will explore some major SIEM and SOAR solutions that companies can use to protect their systems in multi-cloud environments.
Setting up the requirements for integrated security
Before a company gets into buying licenses for all sorts of security tools, security architects will need to gather requirements. That is done by the following four stages that a security team needs to cover:
- Detect: Most of the security tools focus on detecting vulnerabilities and actual attacks or attempts to breach systems. Some examples are endpoint protection, such as virus scanners and malware detection, and Network Traffic Analyzers (NTA). In multi-cloud, architects need to make sure that detecting systems can operate on all platforms and preferably send information to one integrated dashboard.
- Analyze: This is the next phase. Detection systems will send a lot of data, including false positives. Ideally, security monitoring does a first analysis of events, checking them against known patterns and behavior of systems and users. This is the first filter. The second phase in the analysis is prioritization, which is done by skilled security staff. They have access to knowledge base repositories of providers and security authorities. They have the information that enables them to give priority to potential threats, based on relevant context. Remember one thing: where there's smoke, there's usually a fire. The question is how big the fire is.
- Respond: After a threat is detected and prioritized, the security team needs to respond. First of all, they need to make sure that the attack is stopped and exploited vulnerabilities are identified. The next step is remediation: preventing systems from enacting (further) damage or data breaching. The final step in response is recovery – restoring systems and making sure that the data is safe. Be sure that processes for following up security events are crystal clear. Who needs to be informed, who's mandated to take decisions, and what is the escalation path?
- Prevent: SIEM and SOAR systems can do a lot in detecting, analyzing, and responding to security events. However, security starts with preventing vulnerabilities from being exploited in the first place. Security teams need to have continuous visibility on all the platforms that the enterprise uses and must have access to security reports, assessments, and threat detection scans from the providers. It's also essential that recommendations from Azure, AWS, GCP, VMware, or any other provider are followed up. These providers issue security updates on a regular basis and give recommendations to improve the state of security of environments that are deployed on their platforms. These recommendations should be followed.
In January 2020, market analyst Gartner issued a report (available on https://swimlane.com/resources/access-selecting-soc-tools-gartner/), which stated that by 2024, 80 percent of all SOCs will have invested in tools using artificial intelligence and machine learning. In that same report, Gartner analysts concluded that these investments will not necessarily bring down the amount team security teams have to spend on investigating security events. So, what would be wise investments in terms of security tools and systems?
First, leverage what providers already have. Azure, AWS, and GCP all have security suites that gather a lot of information on the health and integrity of systems. In almost all cases, it's a matter of ticking the box to enable these security systems, although security engineers will have to set a baseline to which the tools monitor the systems. This was discussed in Chapter 14, Defining Security Policies.
Implementing the security model
A lot of companies already have a multi-cloud setup. For example, they use AWS to host websites and have Office 365 from Microsoft, a SaaS solution. In AWS, security teams will work with AWS Inspector and GuardDuty and for monitoring security. In Office 365, they might use Microsoft Defender and Advanced Threat Protection (MDATP). The challenge for security teams is to have an integrated vision on the full IT environment. How do companies get there?
- Define a target operating model: What does the entire environment look like and who's responsible for all or some of it? Companies must have a clear demarcation model on roles and responsibilities in the management of cloud platforms, services, and systems. The target operating model describes the landscape of components and the owner of these components. Security is an overall component for which the security officer is responsible.
- Define workflows and escalation procedures: This defines the workflow when security events occur. What is the procedure in the case of high-priority events, medium-rated events, and low-risk events? When a high-priority event is detected, it should be raised to the security officer. The security officer decides who needs to be informed and what actions must be taken. These are operational tasks. They may report to the Chief Security Officer (CSO) or the Chief Information and Security Officer (CISO). The CSO or CISO is responsible for strategic security decisions.
- Analyze the capabilities of security tools that are already in place: Evaluate the tools that are in place already. What do these tools cover? How are APIs configured and can they communicate with overlaying systems? What are the default baselines that these tools use?
- Gap analysis: There will always be blind spots. A common example in batch jobs is are these monitored as well from a security perspective? What happens when jobs are stopped? Is communication between systems then halted and is the integrity of systems still safeguarded? In cloud-native environments, companies should also have a good understanding of how containers and serverless solutions are monitored. Not all monitoring tools can handle these native environments yet.
- Make a strategic plan: This is what the CSO or CISO must be concerned with. The first question that must be covered in a strategic plan is the maturity goal of the enterprise. The next question is what the major security concerns are for the enterprise: what are the biggest risks and threats? Hint: it is not always about the loss of money. Reputational damage goes far beyond revenue loss when systems are breached. Finally, the company must be able to identify whether existing tools, processes, and expertise are sufficient and what needs to be done to get to the desired maturity goal.
The following diagram shows a maturity model for security:
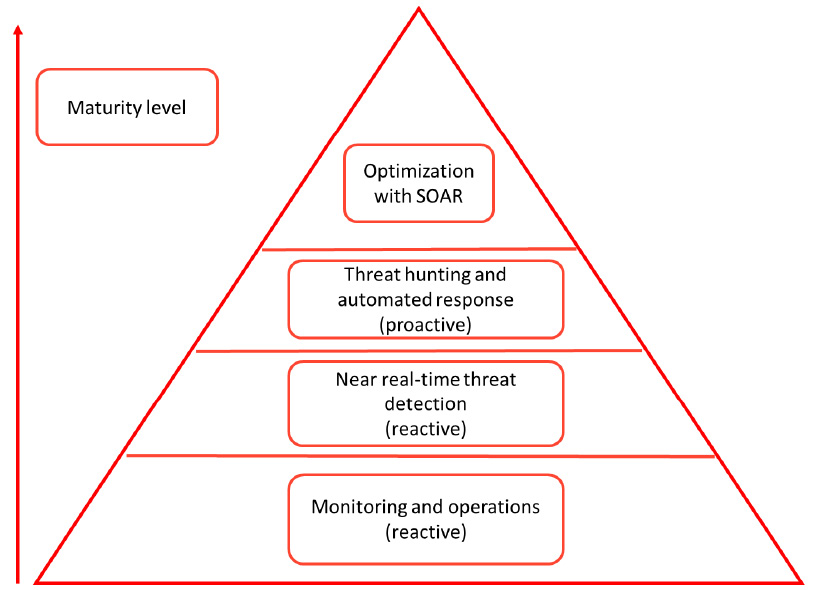
Figure 17.2 – Security maturity model, from reactive monitoring to proactive threat hunting
It's strongly advised to set up a security team or SOC. It's not realistic to have one or two security engineers to watch over multi-cloud environments. The difficult part is how to get there. The best practice is to plan the setup in three stages:
- Stage 1 – get visibility for the business: In this stage, we gather the security policies and align the security processes between business and IT.
- Stage 2 – integrate IT security operations with business security: This is the stage where security operations enable security monitoring and onboard the security baselines – as defined with the business in stage 1 – in the monitoring systems. Part of this stage is also the risk assessment on the platforms. It's recommended to do an assessment on the security baselines of the cloud providers and analyze whether these baselines concur with the security principles of the enterprise.
- Stage 3 – optimize: This is the stage where the true integrated view is created, using one dashboard that covers the entire security state of the IT landscape.
The stages are shown in the following diagram:
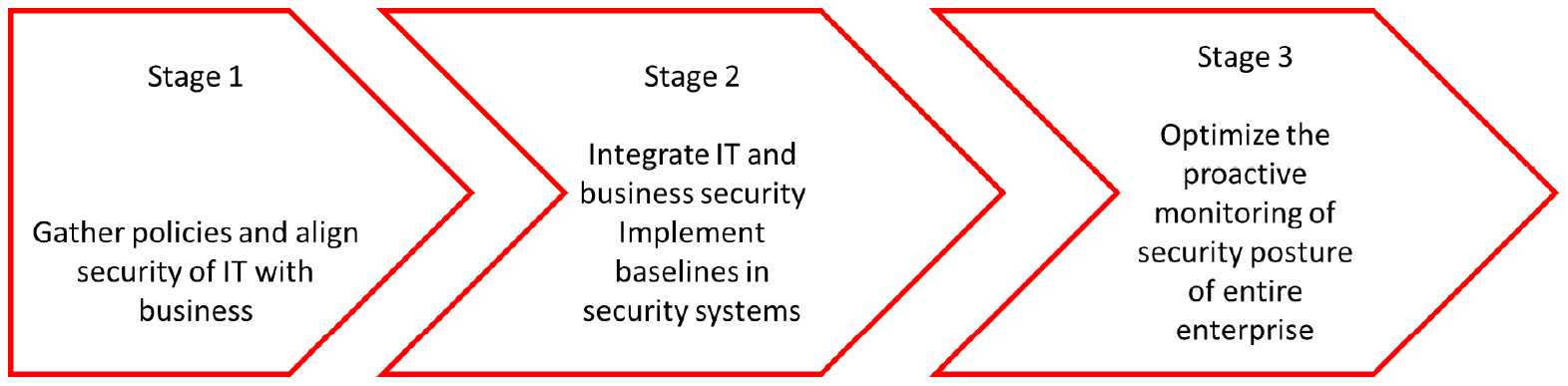
Figure 17.3 – Three stages of security onboarding
Integrated security means that a company has a clear model of processes, tools, and expertise. In multi-cloud, this also means that cloud providers are part of these processes, tools, and certainly expertise. The security architect will have the task of getting this defined, designed, and modeled. SIEM and SOAR tools can help to get an integrated view of the entire security state – or posture – of an enterprise. In the next section, we will discuss popular solutions for this in multi-cloud.
Exploring multi-cloud monitoring suites
Companies have a wide variety of choices when they're looking for a SIEM solution. In the next sections, some popular solutions are discussed.
Exploring SIEM solutions from Splunk, LogRythm, and Rapid7
Each year, market analyst Gartner publishes a list of leading solutions in different IT domains. For a number of years, Splunk, LogRythm, and Rapid7 have been named as leading products for SIEM by Gartner. These solutions can work with all major cloud providers using REST APIs. REST stands for REpresentational State Transfer.
A REST API is a programmable interface that connects to the service in the cloud and enables that data from that service to be captured and sent to an application. In this case, the SIEM suite uses an API to get security data such as alerts from the cloud and transfers it to the dashboard of the SIEM solution. Splunk, LogRythm, and Rapid7 have APIs for Azure and AWS. Splunk and LogRythm integrate with Azure Monitoring using Azure Log Integration (AzLog). In AWS, these tools work with AWS Config, CloudTrail, and CloudWatch to collect data.
Splunk also offers integration with GCP. Rapid7 was already available from the marketplaces in Azure and AWS but did not have an API for Google Cloud. Since a growing number of enterprises are expanding cloud services in all major clouds, Rapid7 acknowledged that a multi-cloud security solution needed to integrate with GCP too. For that reason, they acquired DivvyCloud in spring 2020, a multi-cloud security and compliancy tool.
Implementing SecOps with VMware and ServiceNow
Over the last 5 years, the market for enterprise IT has seen an enormous growth in security monitoring tools, including companies that didn't have security as their main focus, but invested heavily in developing or acquiring security products. It's a logical move when you realizes how fast cybercrime is growing. Good examples of companies that made big investments in security are VMware and ServiceNow.
VMware transformed itself from a company that virtualized server environments into a company that can perform a central role in managing multi-cloud. In 2019, it introduced Intrinsic Security, which consists of several products, including VMware Secure State. Secure State, or CloudHealth, as it was originally called, is a SOAR system. It analyzes misconfigurations of systems and threats, and detects changes that are applied to systems. It calculates the security risk of these systems and is able to automate remediating actions when systems are at risk. In order to do so, security engineers need to load baselines into Secure State to which the tool measures compliance of systems. Secure State is multi-cloud and can be used as a single tool on top of Azure, AWS, GCP, and hybrid platforms that hold both public and private clouds. The latter does not necessarily have to be built with VMware, but can also run, for example, Hyper-V or OpenStack.
In ServiceNow, enterprises can configure the same functionality using SecOps and Governance, Risk, and Compliance (GRC). GRC can be seen as the repository that holds the security policies and compliance baselines of an enterprise. Next, GRC continuously monitors the compliance of systems, analyzes the business impact of risks, and collects audit data. SecOps is the SOAR module of the ServiceNow suite; it continuously monitors the security posture of the entire IT environment and can automatically mitigate security issues, based on security incident response scenarios that are defined as workflows in SecOps.
A workflow can, for example, be that a system is suspended when SecOps detects that software has not been checked for patches in more than 3 months. If the enterprise has a compliance rule that states that software needs to be checked for patches at least once every 3 months, an automated workflow could trigger the action to suspend the use of the software.
Introducing cloud-native SIEM with Azure Sentinel
One final product that is reviewed here is Azure Sentinel, the native SIEM and SOAR solution for Azure. Sentinel does what all SIEM and SOAR solutions do: collect data, check it against compliancy baselines that have been defined in Azure, and respond to threats and vulnerabilities with automated workflows. It also uses artificial intelligence to detect and analyze possible attacks, by learning the behavior of systems and users. With Sentinel, Microsoft has a very extensive suite of security solutions in the cloud with MDATP, Cloud App security, and Azure Security Center. Although Sentinel is based in Azure, enterprises can also connect AWS CloudTrail to Sentinel. At the time of writing, an integration with GCP is not available.
This list of tools and suites is not exhaustive. Enterprise architects and security specialists should together start with gathering requirements from the business, define the needed security level of systems against compliance frameworks, agree to the security processes between business and IT, and then decide what sort of security tools would best fit the requirements. SIEM and SOAR solutions are complex. These solutions can add a lot of value to safeguard the security posture of the IT environment, but need careful consideration and evaluation of the business case.
Summary
Enterprises use a wide and growing variety of cloud solutions. Cloud platforms, systems, software, and data need to be protected from threats and attacks. Likely, a company will also have a variety of security solutions. To create one integrated view of the security of the entire IT environment, companies will have to implement security tooling that enables this single point of view. In this chapter, we looked at SIEM and SOAR systems, tools that can collect data from many different sources and analyze this data against security baselines. Ideally, these tools can also trigger automated responses to threats, after calculating the risks and the business impact.
The functionality and differences between SIEM and SOAR have been explained. After this chapter, you should have a good understanding of how these systems can integrate with cloud platforms.
In the last section of this chapter, leading SIEM and SOAR solutions were discussed. The chapter concludes this section of our book about security operations, or SecOps. There are two more ops-concepts that must be discussed: DevOps and AIOps (operations using artificial intelligence). The next chapters will be about DevOps and AIOps.
Questions
- What is a SOC?
- What is a common technology to integrate SIEM and SOAR systems into cloud platforms?
- Monitoring and operations are the first level in the security maturity model. Rate the following statement true or false: the reason for this is that monitoring and operations are reactive.
Further reading
Enterprise Cloud Security and Governance, by Zeal Vora, Packt Publishing
