Remote-Access VPN Security Considerations
Worms, viruses, spyware, hacking, data theft, and application abuse are considered among the greatest security challenges in today’s networks. Remote-access and remote-office VPN connectivity are common points of entry for such threats because of how VPNs are designed and deployed. For both new and existing IPsec and SSL VPN installations, VPNs are often deployed without proper endpoint and network security. Unprotected or incomplete VPN security can lead to the following network threats:
• Enables remote-user VPN sessions to bring malware into the main office network, causing virus outbreaks that infect other users and network servers.
• Enables users to generate unwanted application traffic, such as peer-to-peer file sharing, into the main office network causing slow network traffic conditions and unnecessary consumption of expensive WAN bandwidth.
• Enables theft of sensitive information, such as downloaded customer data, from a VPN user desktop.
• Enables hackers to hijack remote-access VPN sessions, providing the hacker access to the network as if they were a legitimate user.
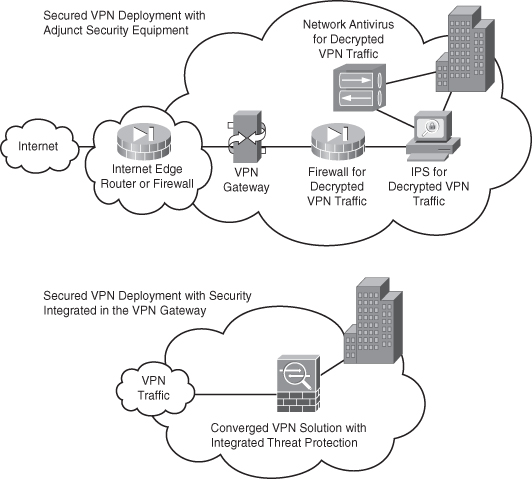
To combat these threats, the user desktop and the VPN gateway to which the user connects must be properly secured as part of the VPN deployment. User desktops should have endpoint security measures such as data security for data and files generated or downloaded during the VPN session, antispyware, antivirus, and personal firewall. The VPN gateway should offer integrated firewall, antivirus, antispyware, and intrusion prevention. Alternatively, if the VPN gateway does not provide these security functions, separate security equipment can be deployed adjacent to the VPN gateway to provide appropriate protection. It’s your responsibility as a security professional to educate your end users through good, consistent user awareness training.
Cisco remote-access VPN solutions offer threat-protected VPN services with full firewall, antivirus, antispyware, intrusion prevention, application control, and full endpoint security capabilities. These security services are integrated into the VPN platform, delivering a threat-protected VPN solution without any additional equipment, design, deployment, or operational complexity.
Steps to Securing the Remote-Access VPN
Technologies required for mitigating malware such as worms, viruses, and spyware and for preventing application abuse, data theft, and hacking exist in the security infrastructure of many organizations’ networks. In most cases, however, they are not deployed in such a way that they can protect the remote-access VPN because of the native encryption of VPN traffic. Although additional security equipment may be purchased and installed to protect the VPN, the most cost-effective and operationally efficient method of securing remote-access VPN traffic is to look for VPN gateways that offer native malware mitigation and application firewall services as an integrated part of the product, as shown in Figure 9-13.
Figure 9-13 Securely Deploying VPNs
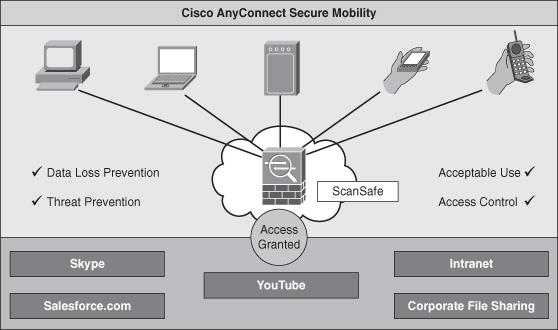
Cisco AnyConnect VPN Secure Mobility Solution
End users want the flexibility to choose how, when, and where to access both personal and professional information to be productive without being inconvenienced by security checks. The IT support staff, on the other hand, wants to allow access for end users while ensuring that the corporate network and the access remains secure. Employees using their own devices to access the corporate network introduce an additional burden to an organization’s IT department. When business data makes its way onto an employee-owned device, it can be a challenge for the enterprise to control its spread or use. To support the increasing number of mobile workers, corporate security administrators must provide context-aware security and policy enforcement, regardless of the end user’s location, what device they use, and where the information they access is located. Administrators must also be able to support a heterogeneous set of laptops and mobile devices to encourage choice for their clients—the end users. And finally, they must provide this security unobtrusively to minimize end-user concerns. The Cisco AnyConnect Secure Mobility Solution provides the following:
• Security policy enforcement that is context-aware, comprehensive, and preemptive
• A connectivity experience that is intelligent, seamless, and always on
• Secure mobility across today’s proliferating managed and unmanaged mobile devices
Cisco AnyConnect with Cisco ASA 5500 Series Adaptive Security Appliances at the head end provides the remote-access connectivity portion of Cisco AnyConnect Secure Mobility. This AnyConnect VPN is becoming more powerful and flexible with the capability now for it to support any mobile operating system such as Apple’s IOS, Android, and the Cisco CIUS platform.
Both the user and device must be authenticated and validated prior to being provided access to the network. After the user is authenticated, the Cisco AnyConnect Secure Mobility Solution can decide which applications and resources the user should have access to. Ideally, this authentication would be transparent to the user. For devices to be authenticated, they must comply with corporate policies and have up-to-date security in place.
The Cisco AnyConnect Secure Mobility Solution enables the connection to simply work and be reliably connected without the user needing to juggle where and how to best connect and persist, even when roaming between networks. As mobile workers roam to different locations, the always-on intelligent VPN in the AnyConnect Secure Mobility client automatically selects the most optimal network access point and adapts its tunneling protocol to the most efficient method.
Mobility changes everything. It changes how and where people work—and it creates new IT security challenges. The Cisco AnyConnect Secure Mobility Solution provides comprehensive and secure remote access. Mobile users can enjoy persistent connectivity back to their corporations, and IT administrators can enable smart, context-aware security policies to protect corporate assets. Figure 9-14 illustrates how AnyConnect VPNs can be successfully deployed within your organization.
Figure 9-14 AnyConnect Deployment Considerations