The Process of an Attack
An attacker can attempt to gain access to or exploit a system in many ways. This system can be as simple as a home computer connected to the Internet through a DSL connection, or a complex corporate network. Regardless of the kind of system an attacker targets, they typically employ the same fundamental steps:
1. Reconnaissance via social engineering or other methods
2. Footprinting/fingerprinting
3. Scanning (passive or active)
4. Enumeration
6. Escalating
7. Creating backdoors and covering tracks (cleanup)
The following sections discuss these steps in detail. You need to understand the concepts of what attackers might do in each step, and their goals, so you can detect and thwart their attacks.
Reconnaissance
Considering the introduction to this chapter, this discussion begins with hacking innocent information, which is also known as social engineering. Hacking innocent information from a person via social engineering is much easier than bypassing a firewall.
Fundamentally, people want to trust and help others, so they are more vulnerable to social engineering; combating this most basic hacking can be one of the biggest challenges to those who are responsible for security.
Although you might not think innocent information is worth protecting, it can be crucial to a social engineer attacker. When an attacker is armed with this information, he can use it to present himself as believable. In reality, this is where the hacker usually begins penetrating a company, by obtaining some document that might seem innocent and commonplace; be careful, however, because it could be useful to others.
Consider the following scenario, which I used once while performing a network assessment. To see what people would be willing to give up to someone who “sounded” official, I called the senior IT engineer, Daniel:
“Hello, this is Tom from WindWing Travel. Your tickets to San Jose are ready; would you like us to deliver them or arrange for you to pick them up as e-tickets at the airport? “
“San Jose?” Daniel says, “I do not have any travel plans there.”
“Is this Daniel Thomas?” I asked.
“Yes, but I do not have any trips scheduled until AppleCon in Las Vegas, later this year.”
“Well,” I chuckle, “are you sure you do not want to go check out San Jose?”
Daniel chuckles as well, responding to a humorous situation and a break in his normal routine by saying, “Sure, I’d be happy to go if you can convince my boss....”
“Sounds like another computer glitch,” I say and, while chuckling, I remark, “I thought computers were supposed to make our lives easier.”
Daniel laughs, too.
“In our travel system, we track travel arrangements under your employee number. Perhaps someone used the wrong number when booking the flight. What is your employee number?”
Daniel knows that several groups within his company have his employee number: security, human resources, his boss, and obviously finance, so why wouldn’t the travel company use a way to identify him that would fit with his company. There is no danger here, is there?
A competent hacker working on social engineering can take this simple piece of information and use it with some rather easily obtained data to take his hack to the next level. Imagine what access he might gain if he had an employee’s number, full name, telephone extension, department, work location, email address, and even his manager’s information. This information is innocent when viewed in pieces, but it paints a scary picture when compiled together.
Clearly, innocent information should be protected, and all employees should be made aware that mishandling information that should never be released to the public could truly endanger both the company and, more importantly, the employee. A strong security awareness program from all corporate employees and by a service-level agreement (SLA) for contractors should be tied and enforced by HR. For example, consider the following example:
“Daniel, I can’t find you by employee number. Let me try another way. What is your Social Security number?”
As you can see, a rapport was quickly established making my claims believable, and ultimately I got around to asking for the information I wanted, his Social Security number. A good rule is that all company data should be considered sensitive and not released unless an individual is explicitly authorized to do so. Remember that all calls and email are corporate property; with the move to IP convergence for voice and data, calls may be recorded for “quality purposes” and email may be archived and read later. The same applies to instant messaging communication. Security should be an enabler to the business, not a roadblock to progress.
For additional information on social engineering and how hackers gather information without ever alerting your network engineers, refer to the following enjoyable and well-written book, The Art of Deception: Controlling the Human Element of Security, by Kevin Mitnick and William Simon. This book also describes techniques and policies that you can use to defend against these types of attacks. I strongly recommend this enjoyable and well-written book.
Footprinting (aka Casing the Joint)
“Intelligence preparation” of the enemy and the battlefield is a military term used to define the methodology employed to reduce uncertainties concerning the enemy, environment, and terrain for all types of military operations. During military actions, this concept has been clearly demonstrated through the use of drone aircraft that enabled military commanders to see the battlefield and thus pick when and, more important, how they engaged the enemy. Understanding the battlefield and subsequently having the ability to choose how you engage the target is analogous to the choices hackers make. In network security terms, this intelligence preparation is known as reconnaissance and footprinting; in Hollywood movies, it is referred to as “casing the joint.” The network resources that security professionals are tasked with securing are analogous to a battlefield, and battlefield intelligence is critical to victory.
Hackers conduct these preparation operations against your company and network they need to understand “where” their target is and how it is put together. Footprinting is a continuous process used throughout all planned and executed operations. The myriad of attackers and intruders from the void are the aggressors who are constantly on the offense. The security professionals are the defenders, entrusted to preserve the confidentiality and integrity of data against these intruders and protect against disclosure, alteration, and destruction (DAD).
In the real world, many criminals perform this step, but they probably have not named it. For example, a criminal might review the security of a convenience store so that he can understand what the security is, where the money is kept, the location of security cameras, possible exits, and any other items that might help him succeed in his crime. As shown in Table 1-1, hackers look to gain information during this phase.
Table 1-1 Goals of Reconnaissance and Footprinting
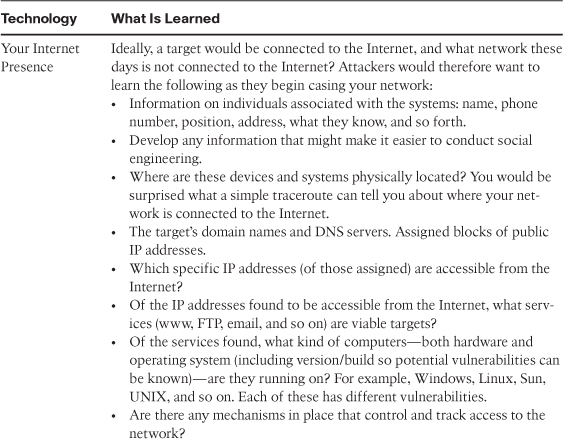

Impressive list, isn’t it? The disturbing aspects of this list are twofold:
• Even the most inept hackers can figure these things out.
• Learning the answers to these questions is free and quite likely you will never know the threat until it’s too late.
Hackers can take a lot of steps to learn about your network without your knowledge. Consider what simply looking at a Domain Name System (DNS) can reveal about your network through the use of a simple (and free) command known as dig (domain information groper), which has replaced nslookup. (See Example 1-1.)
Example 1-1 Using DNS for Passive Reconnaissance via the dig Command
Toms-iMac:~ ccie9360$ dig cisco.com any
; <<>> DiG 9.6.0-APPLE-P2 <<>> cisco.com any
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 25065
;; flags: qr rd ra; QUERY: 1, ANSWER: 12, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;cisco.com. IN ANY
;; ANSWER SECTION:
cisco.com. 85877 IN A 198.133.219.25
cisco.com. 86214 IN MX 15 rtp-mx-01.cisco.com. <- MX =
designates an email server
cisco.com. 86214 IN MX 20 ams-inbound-a.cisco.com.
cisco.com. 86214 IN MX 25 syd-inbound-a.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-a.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-b.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-c.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-d.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-e.cisco.com.
cisco.com. 86214 IN MX 10 sj-inbound-f.cisco.com.
cisco.com. 86360 IN NS ns2.cisco.com. <- NS designates a
DNS server
cisco.com. 86360 IN NS ns1.cisco.com.
;; Query time: 27 msec
;; SERVER: 208.67.222.222#53(208.67.222.222)
;; WHEN: Sat Jul 24 15:52:02 2010
;; MSG SIZE rcvd: 339
Note
The any keyword asks for any DNS record. Many other more specific options are available. You can run the man dig command for the manual, which is the UNIX/Linux way to reference a command’s manual.
As you can see, the output reveals Cisco.com’s email, DNS, and web servers, which you can then use to determine more information. Now traceroute is used to the DNS A record for the domain to figure out where this domain is located on earth:
Toms-iMac:~ ccie9360$ traceroute 198.133.219.25
traceroute to 198.133.219.25 (198.133.219.25), 64 hops max, 52 byte packets
1 172.16.17.1 (172.16.17.1) 1.957 ms 2.033 ms 1.090 ms
<<<Output omitted for my security!>>>
7 te-1-1-0-4-cr01.dallas.tx.ibone.comcast.net (68.86.91.253) 23.208 ms 28.560
ms 34.533 ms
8 pos-0-3-0-0-pe01.1950stemmons.tx.ibone.comcast.net (68.86.86.154) 30.395 ms
26.313 ms 25.119 ms
9 as7018-pe01.1950stemmons.tx.ibone.comcast.net (75.149.231.22) 23.717 ms
29.184 ms 23.887 ms
10 cr2.dlstx.ip.att.net (12.122.195.242) 69.468 ms 70.911 ms 69.258 ms
11 cr2.la2ca.ip.att.net (12.122.28.178) 70.152 ms 72.476 ms 77.454 ms
12 cr2.sffca.ip.att.net (12.122.31.134) 83.423 ms 72.581 ms 70.189 ms
13 gar8.sffca.ip.att.net (12.122.114.65) 69.502 ms 70.041 ms 76.617 ms
14 12.91.205.14 (12.91.205.14) 71.215 ms 69.936 ms 69.898 ms
15 sjc5-dmzbb-gw1-ten4-5.cisco.com (128.107.224.250) 69.791 ms 74.528 ms
69.920 ms
16 sjce-dmzbb-gw1-ten3-3.cisco.com (128.107.224.2) 69.690 ms 71.246 ms 71.310 ms
17 sjck-dmzdc-gw1-gig5-2.cisco.com (128.107.224.69) 69.856 ms 70.424 ms 70.198 ms
18 * * *
19 * * *
20 * * *
^C
The traceroute output shows that this domain lives on the AT&T Internet backbone because it owns the 12.x.x.x class A address range. Because hops 15+ are DMZs, it is likely they are firewalls of some sort with descriptive PUBLIC DNS names. The first three letters are sjc, which must be San Jose California, which you can learn at www.cisco.com is where Cisco is headquartered. This also means that hop 14 must be a router because it is connecting to the Internet on behalf of the firewalls. Also somewhat interesting is hops prior to, consider that Comcast is plainly telling you where its routers are located. AT&T, on the other hand, is abbreviating cities, but its naming convention is apparent: three letters for the city and two letters for the state, thus dlstx is Dallas, TX, which then goes to la2ca, Los Angeles, California. You can learn a lot with what is available freely online, definitely compiling some good intel as you case the joint!
Now determine whether all the servers that dig reported to you are in the same location. First ping the Cisco DNS server to get its IP address, and then you can traceroute to it:
Toms-iMac:~ ccie9360$ ping ns1.cisco.com
PING ns1.cisco.com (128.107.241.185): 56 data bytes
64 bytes from 128.107.241.185: icmp_seq=0 ttl=111 time=71.388 ms
64 bytes from 128.107.241.185: icmp_seq=1 ttl=111 time=71.445 ms
64 bytes from 128.107.241.185: icmp_seq=2 ttl=111 time=70.924 ms
^C
--- ns1.cisco.com ping statistics ---
3 packets transmitted, 3 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 70.924/71.252/71.445/0.233 ms
Toms-iMac:~ ccie9360$
Toms-iMac:~ ccie9360$ traceroute 128.107.241.185
traceroute to 128.107.241.185 (128.107.241.185), 64 hops max, 52 byte packets
1 172.16.17.1 (172.16.17.1) 1.584 ms 1.403 ms 1.052 ms
<<<Output omitted for my security!>>>
7 te-1-1-0-4-cr01.dallas.tx.ibone.comcast.net (68.86.91.253) 23.504 ms 25.326
ms 23.431 ms
8 pos-0-2-0-0-pe01.1950stemmons.tx.ibone.comcast.net (68.86.86.150) 24.266 ms
28.507 ms 28.004 ms
9 as7018-pe01.1950stemmons.tx.ibone.comcast.net (75.149.230.162) 22.479 ms
28.274 ms 23.051 ms
10 cr2.dlstx.ip.att.net (12.122.195.242) 71.920 ms 69.378 ms 69.901 ms
11 cr2.la2ca.ip.att.net (12.122.28.178) 69.274 ms 69.825 ms 76.966 ms
12 cr2.sffca.ip.att.net (12.122.31.134) 70.084 ms 69.025 ms 69.719 ms
13 gar8.sffca.ip.att.net (12.122.114.65) 69.148 ms 69.967 ms 68.863 ms
14 12.91.205.14 (12.91.205.14) 69.637 ms 72.182 ms 69.718 ms
15 sjc5-dmzbb-gw1-ten4-5.cisco.com (128.107.224.250) 71.831 ms 71.324 ms
69.001 ms
16 sjce-dmzbb-gw1-ten3-3.cisco.com (128.107.224.2) 70.783 ms 73.464 ms
71.846 ms
17 sjck-dmzdc-gw1-gig5-2.cisco.com (128.107.224.69) 71.295 ms 71.022 ms
69.650 ms
18 * * *
^C
Toms-iMac:~ ccie9360$
The traceroute results are identical, so now you know that San Jose holds many important servers for Cisco and that they have at least three different ranges of public IP addresses, specifically the following:
• 198.133.219.25 = DNS A record
• 128.107.224.69 = DMZ firewalls
• 128.107.241.185 = DNS server
All these subnets are in San Jose, CA, the location of the headquarters campus of the target. I know this through confirmation at its website and an Internet search.
Consider that through using just simple and free DNS tools, the attacker can reveal the public IP address of the Cisco website and that of its DNS and email servers. Cisco.com is queried all the time and is, therefore, not alarmed by passive reconnaissance.
Whois is a tool that is again freely available in many applications and on the Internet at the following locations. Try it out on your domain:
• www.networksolutions.com/: Whois web interface
• www.arin.net/: ARIN Whois
• http://whois.ripe.net/: European Whois
• http://whois.apnic.net/: Asia Pacific IP address allocations
• http://whois.nic.mil/: U.S. military
• http://whois.nic.gov/: U.S. government
Do not forget the information available on a company’s website and how useful it is to know the address, main phone number, fax number, mergers, press releases, and members (with bios) of the company’s management team. A target’s corporate website has become a well of useful information from which an attacker can learn quite a lot. The hacker could use this knowledge for social engineering, identity of network systems, system administrators, and so forth. Usenet and Web searches on the system administrators and technical contacts are found when running host queries. By taking the time to track down this information, the attacker might be able to gain greater insight into the target network, plus the attacker knows how to do some social engineering, as key names become known.
If you were a hacker, however, you could begin a more active reconnaissance process to determine what services you could see on these servers through their public IP address.
Unfortunately, most companies are not prepared to detect these types of scans or probes. It is not that they do not have some of the necessary tools; it is simply that the target devices most likely are not logging what is going on—or if they are, no one is looking at the logs. This is one of the problems facing security professionals these days—information overload from device logs!
Consider that one of the next steps could be a simple ping scan using any number of freely available tools on the Internet. Figure 1-1 shows one of the best FREE tools available for black- and white-hat hackers, NMAP. Specifically I used its front end GUI, known as Zenmap, to run a simple scan of a test subnet, 172.16.17.0 /24.
Figure 1-1 Ping Scan of a Class C Subnet
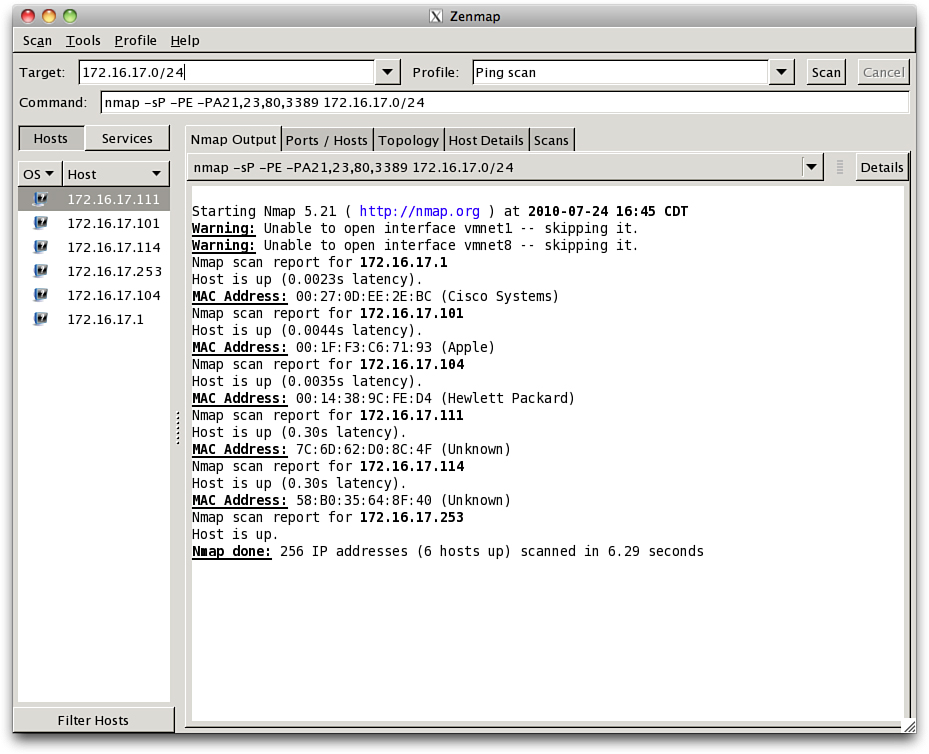
The output of this command also includes some interesting and helpful information. From the results in Figure 1-1, you now know that three known devices on the network exist: Cisco, Apple, and HP. Unfortunately, there are not any Windows machines, so this is going to be a bit tougher; perhaps you should try a different network?
During this phase of an attack, the methods employed involve nonintrusive and standoff methods that hopefully do not enable the attacker’s efforts to be detected. The attacker wants to determine the type of network with which he is dealing, and with whom he is dealing: system, network, and security administrators. Attackers know this and understand that the more active they are, the more likely their activities will be noticed. Attackers can, therefore, start active reconnaissance and allow it to continue until they learn enough information to launch an exploit against that system. If the exploit succeeds, the attackers move on to the next step; if not, they go back and gather more information.
Again, the intent is to develop a network map that uses information gathered during footprinting; the hackers figure out which devices are routers, firewalls, PCs, printers, and so on, and place them on the map, and identify key systems such as mail servers, domain name servers, file servers, and so on. The attackers also want to know where the target gets its Internet access in case they need to try to access the target through its ISP.
Scanning
At this point, the attackers have a good map of the machines on the network, their operating systems, who the system administrators are, any discussions posted to newsgroups, their office locations, and who their upstream intrusion prevention system (IPS) or IDS is. The attackers also know that, from this point forward, everything they do might be logged; at a minimum, they should assume that it is. The attackers have a map of the network and devices and are ready to move on to identifying listening services and open ports. The attackers also determine the acceptable risk. Can they afford to be logged during scanning? Are they behind a series of proxies outside the United States? Is compromise acceptable during the latter stages of the attack? Is concealment of the originating attack location necessary? What about exposure of the sponsor if he is working on behalf of another entity? There is a lot going on in the attacker’s mind. Some attackers sketch things out, and others internalize these considerations as they move from step to step.
In Example 1-2, the attacker has initiated a more active set of scans against a target using NMAP (www.insecure.org), a free tool that both hackers and ethical hackers (good guys) commonly use. Because it is free, you will not find a script kiddie without it! Or better yet, Backtrack 4 (BT4) and its open-source complete compilation of wired, wireless, and forensic tools. Check out the software at www.backtrack-linux.org/.
Example 1-2 Active Port Scan Results
[AppleKick:/Users/topkick] topkick# nmap -sS -O 192.168.254.69
Starting nmap V. 3.00 ( www.insecure.org/nmap/ )
Interesting ports on (192.168.254.69):
(The 1579 ports scanned but not shown below are in state: closed)
Port State Service
7/tcp open echo
9/tcp open discard
13/tcp open daytime
17/tcp open qotd
19/tcp open chargen
25/tcp open smtp
42/tcp open nameserver
53/tcp open domain
80/tcp open http
119/tcp open nntp
135/tcp open loc-srv
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
563/tcp open snews
1025/tcp open NFS-or-IIS
1027/tcp open IIS
1031/tcp open iad2
1033/tcp open netinfo
3372/tcp open msdtc
3389/tcp open ms-term-serv
Remote operating system guess: Windows 2000/XP/ME
Nmap run completed — 1 IP address (1 host up) scanned in 5 seconds
[AppleKick:/Users/topkick] topkick#
If you refer to Figure 1-1, you can see that the ping scan revealed an active host at 192.168.254.69 and that the more detailed scan with NMAP, shown in Example 1-2, provided additional information. You might be wondering how accurate NMAP is. The answer is very accurate; specifically, the device scanned was, in fact, a Windows 2000 server.
For example, Figure 1-2 uses TigerSuite (www.tigertools.net) to see the other services that are accessible on the server. The figure shows that the server is readily identified, as are some extraneous services that are easily exploitable: SMTP, NTP, and FTP. Also notice that the scan revealed the server’s name and domain, which is helpful to users and hackers in a Windows network! Not to mention the highly useable and open NetBIOS ports, typically 135–139 on Windows-based machines.
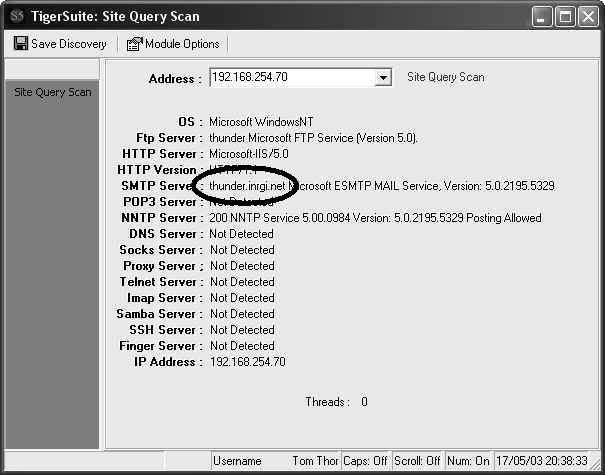
Being somewhat concerned about these services, I immediately shut them off and disabled them from starting again; they can also be audited and turned up and secured when applications call critical services. This is a relatively new server, and I was more concerned about getting it functioning for my users than securing it. In their hearts, most OS vendors felt the need to be helpful and reduce the number of expensive (for them) technical support phone calls turning on every service and function from the beginning. Clearly, they were not thinking of security in this decision—only money. Apparently, they want their CEO to be the richest man in the world. Regardless of their irresponsible motives, Figure 1-3 shows that it does not take the IT professional long to correct this situation. As you can see by the circled server name, the scan has revealed whom they are and what the hacker found.
Figure 1-3 Secured Server Scan Results

You can Telnet to an open port 80 and do a simple get command, but SSH (22) should always be the default out of band (OOB) management option. The result should be a “banner,” which identifies web server type (IIS, Apache, and so on) and other interesting facts, as shown in Example 1-3.
Example 1-3 Telnet to Mail Server, Doing Some Reconnaissance
[AppleKick:~] topkick% telnet 192.168.254.69 80
Trying 192.168.254.69...
Connected to 192.168.254.69.
Escape character is '^]'.
get
HTTP/1.1 400 Bad Request
Server: Microsoft-IIS/5.0
Date: Tue, 20 May 2011 00:43:14 GMT
Content-Type: text/html
Content-Length: 87
<html><head><title>Error</title></head><body>The parameter is incorrect. </body></html>Connection closed by foreign host.
[AppleKick:~] topkick%
The first thing to do is to open a connection from your computer to your mail server. For some odd reason, newer versions of Windows no longer have Telnet enabled by default (annoying Microsoft), so you need to manually enable it. Also, some email providers use content-aware firewalls to block Telnet, Cisco, and Hotmail, for example. In this example, we are going to find an executive’s email address because we are going to fool the email server that we are trying to send a real email:
telnet mail.domain.ext 25
You should receive a reply like this from the email server:
Trying <mail.servers.public.ip.address>Connected to <mail.domain.ext>.Escape
character is '^]'.
220 mail.domain.ext Microsoft ESMTP MAIL Service, Version: 6.0.3790.4675 ready at
Sun, 25 Jul 2010 15:31:21 -0400
You then need to tell the email server where you are sending the email from:
HELO www.hackerdomain.com
In this case, we are making up a domain because we do not want to tell anyone who we are or where we are coming from. In the real world, although you really should use your exact fully qualified domain name as seen by the outside world, the mail server has no choice but to take your word for it because those are the rules defined in RFC822 through RFC1123. Also, some email servers accept EHLO in place of HELO. The email server should reply as follows:
250 mail.domain.ext Hello [YOUR.ip.address], pleased to meet you!
Now give your email address; on many mailservers the space after the : is required rather that optional.
MAIL FROM: [email protected]
The email server should reply as follows:
250 2.1.0 [email protected] OK
Now give the recipient’s address:
RCPT TO: [email protected]
When you discover the valid and real email address of the CEO, the email server responds as follows:
250 2.1.0 [email protected]... Recipient ok
To start composing your message, issue this command:
DATA
The email server should reply as follows:
354 Start mail input; end with <CRLF>.<CRLF>
If you want a subject for your email, type the following:
Subject: <type.subject.here>
Then press Enter twice (these are needed to conform to RFC 882); you will not see this reflected on the screen but do it anyway. You can now proceed to type the body of your message:
Hello CEO, there is some really important invoices for you to review please click
here to ensure they are correct. You are being whaled so will need all account
numbers for us to hack, thank you.
Note
After phishing comes whaling, a sneaky attempt by scammers to hijack the personal computers of top-ranking business execs.
To tell the mail server that you have completed the message, press Enter a couple times; then enter a single “.” on a line on its own and press Enter. The mail server should reply with the following:
250 2.0.0 ???????? Message accepted for delivery
You can close the connection by issuing the following command:
QUIT
The mailserver should reply with something like:
220 2.0.0 <mail.domain.ext> Service closing transmission channel
Connection closed by foreign host.
Note
Telnetting to target IP addresses on various port numbers can sometimes yield surprising results. Try Telnetting to some of the more commonly known ports (such as port 80) to see what kind of results you get. You will be surprised at the information readily available to you.
Another type of scanning, known as vulnerability scanning, is typically done from the Internet to find out how well a system is protected. This type of scanning and some of the tools available are discussed in Chapter 12; until then, you can search online to find many scanners, and yes, many are free! As you have seen, each technique in the reconnaissance phase has value, but the true value (for the attacker) is gained when multiple techniques are combined to gain a complete picture of the target network or device. Nessus and Kismet are good examples of open-source tools in BackTrack4 that enable through vulnerability scanning.
As you move on to the next step in the attack process, remember that the scanning of a target allows the attacker to focus her efforts and attention on the most promising avenues of entry into your network. Attackers expect your IT professionals to be watching, but they doubt they will be seen; that assumption is subject to change, however, if you get involved and make a difference.
Enumeration
Defining the network environment involves footprinting, scanning, and enumeration as the hacker learns and prepares for the attack. Footprinting enables the attackers to limit the scope of their activities to those systems that are potentially the most promising targets to vulnerabilities they plan on running against the server. Scanning told the attackers what ports are open and what services are running.
Enumeration is the extraction of valid account information and exported resources. The key difference between the preceding scanning and footprinting techniques is that enumeration involves active connections to specific systems and directed requests to connect to these specific systems. Enumeration is succinctly defined at Wikipedia as follows:
Network enumerating is a computing activity in which user names, and info on groups, shares and services of networked computers are retrieved. It should not be confused with Network mapping, which only retrieves information about which servers are connected to a specific network and what operating system is run on them.
Note
The previous section concluded by saying that attackers expect to be seen but ignored while they are footprinting. However, when enumeration begins, the attackers’ attempts must be stopped or, at the minimum, logged and acted upon!
Like all steps in the attack, pulling the results together makes the difference in the success of the attack. Following are the four main categories within a network:
• Network resources and open shares
• Users and groups
• Applications
• Device logon banners and message of the day (MOTD) on network devices
As you can tell, the presence of each of these categories differs on every operating system. Consider that every major operating system enables shares, but each—Mac OS, Windows, Linux, and Novell—handles them in a different way. This means that, from an attacker’s perspective, each operating system must be handled differently.
The earlier example of a layered approach becomes apparent here because, through the use of NMAP, you have a good idea of what operating systems you are trying to enumerate and thus ultimately attack.
Enumerating Windows
As the industry leader in computer operating systems, Microsoft Windows is perhaps the most widely discussed; therefore, it makes sense to spend some time on it first. Windows operating systems still depend heavily on the use of NetBIOS (UDP Port 137), and many of the tools an attacker might use to learn more about a Windows-based network are built in to the operating system itself, as you see in the text that follows.
Example 1-4 shows the results of issuing a net view command from the command line of a Windows machine. In this case, the domain was known, so including it in the command revealed all the machines in that domain. Had the domain been omitted, all the LAN’s domains would have been displayed.
Example 1-4 Using Windows Net View
C:>net view
Server Name Remark
---------------------------------------------
\APPLEKICK Toms MAC
\LIGHTNING
\THUNDER
\TOPKICK
The command completed successfully.
C:>
This enumeration technique is even more useful when you combine it with the results of the earlier ping scan. You can use IP addresses and NetBIOS names interchangeably; so for example with NetBIOS, you might access another computer using \COMPUTER-NAME. You can also use \192.168.254.69. Attackers know this and modify their systems so that their machines “automatically” cache the NetBIOS names.
Another great built-in Windows tool is nbtstat, which enables you to query another computer for its NetBIOS name table. This means an attacker can query a server for its table, as shown in Example 1-5.
C:>nbtstat -A 192.168.254.70
Local Area Connection:
Node IpAddress: [192.168.254.69] Scope Id: []
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
THUNDER <00> UNIQUE Registered
THUNDER <20> UNIQUE Registered
INRGI <00> GROUP Registered
INet~Services <1C> GROUP Registered
IS~THUNDER.....<00> UNIQUE Registered
INRGI <1E> GROUP Registered
INRGI <1D> UNIQUE Registered
..__MSBROWSE__.<01> GROUP Registered
MAC Address = 00-C0-9F-20-E4-F0
C:>
In addition, if you do not know the IP address of the machine you have your sights set on, you can issue the command nbtstat -c; you are then provided with a listing of the NetBIOS names (in your cache) and their corresponding IP addresses, as demonstrated in Example 1-6. Don’t you just love friendly operating systems that are eager to freely tell you about themselves?
Example 1-6 Using nbtstat -c to Display NetBIOS Names
E:>nbtstat -c
Local Area Connection:
Node IpAddress: [192.168.1.101] Scope Id: []
NetBIOS Remote Cache Name Table
Name Type Host Address Life [sec]
PRO200 <20> UNIQUE 192.168.1.100 587
PRO200 <00> UNIQUE 192.168.1.100 95
The best way to stop an attacker from learning this kind of information from your network is to ensure that your router and firewall are blocking the entry and exit of NetBIOS packets. Block at both points to prevent a layered approach to security. Specifically, block the following:
• TCP and UDP on ports 135 through 139
• TCP and UDP 445 for Windows 2000
Blocking these ports does not stop NetBIOS; it simply prevents it from entering your network. Ways exist to disable NetBIOS on a Windows PC; however, this might not be an option. Table 1-2 shows some of the common tasks and tools that attackers use.
Table 1-2 Attacker Tasks, Tools, and Techniques
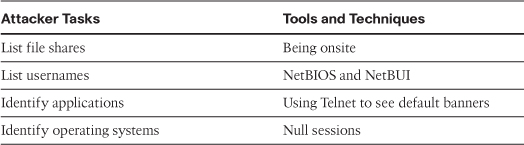
As discussed at the beginning of this section, each operating system has associated techniques that enumerate against it. You have looked at a couple techniques that are just for Windows, and there are many more. Later in this chapter, you will see some recommended titles that discuss more about the other enumeration possibilities.
Gaining Access
Many people mistakenly believe that an attacker wants to take control of a target device and that is the ultimate goal of an attack. This is not entirely true. What is more likely is that an attacker wants to “only” gain access to a target PC. After enumeration identifies promising avenues of entry, more intrusive probing can begin as valid user accounts and poorly protected resource shares are exploited to gain access.
Ultimately, attackers must gain access to a system through some aspect of that system. There are typically four major types of exploits that reflect different aspects of a system that attackers target:
• Broader DoS or DDoS attacks that might include the preceding attacks
Within these different aspects of an attack, an attacker can proceed in two ways:
• Automated attacks: These types of attacks target one or more aspects of the target and are usually opportunistic by design. Automated attacks are opportunistic in the sense that they scan an entire block of IP addresses to look for vulnerability. For example, an automated attack might scan every IP address in a Class C block on port 80 looking for a known vulnerability that affects web servers. If the scan is successful, the attack proceeds; if not, the scan continues looking.
• Targeted attacks: These types of attacks might be more dangerous than automated attacks because your organization has been singled out for an attack; a good example is a government organization—local, state, or federal. In other words, attackers know that you have something they want, or that by succeeding in their attack on you, they can achieve a goal. Increasingly, the latter force drives attacks by using politics or social agenda as a rational for an attack. Fortunately, targeted attacks seem to make up the minority of Internet activity. However, the bad news is that if you are targeted, the more skilled the attacker, the less likely you are to “see” or detect the attack.
Remember these two ways an attack might occur as you consider how an attack can affect the different aspects of a system.
Operating System Attacks
An operating system is designed to support what a user would like to accomplish and, in the context of this discussion, the operating system must enable networking to some degree. The more networking enabled on a system, the more services are activated to support these needs. This results in more open ports and active services being available and visible. Therefore, attackers have more opportunities to select an attack, thereby resulting in the access they want. Remember, other than financial motivation, one of the largest differences between the black and white hats is time. The black hats have all the time in the world to get their tasks at hand accomplished—you and I do not.
In addition, users and administrators often think that the job is finished when a server has its OS installed and its services configured. Alas, this is a mistake that results in a perfect target for attackers. Consider being a hacker and finding a server that has the original operating system installed without patches and with all default services activated. That server will be compromised within the hour! There should be a corporate template for OS hardening supported by an application security policy with an exact procedure for the team to follow to keep this consistent and up to date.
Application Attacks
I once worked in a business unit that wrote networking software for one of its products. The company was a large, international company with a strong history in telecommunications. I explain this background because with all the software being written these days, you would think that this company would take advantage of its understanding of the technology and security.
Alas, that was not the case; software programmers were under amazingly tight deadlines and were always asked for new features. I knew many of them—they inherently wanted to do the right thing, but outside factors drove their activities in many ways. Essentially, software was not being tested as it should have been. Add in its increasing level of functionality, and you have opportunities for attackers. This is all terrible, but consumers did not care about security several years ago—only whether the software had the features they wanted. Perhaps if consumers change what they spend money on, secure software will become more of a pressing issue.
Misconfiguration Attacks
Sometimes, system administrators work on the system when trying to secure a system or ensure that it provides the functionality users need. Usually, this means turning on several options, and the wanted feature starts working when you press the right option.
Did you clean up those options after yourself? Likely not. The problem is that the system administrator does not go back and research what fixed her issue and deactivate the unneeded options. This is perplexing because verifying that a system is not misconfigured is an easy precaution to ensure that your system is functioning correctly. A good rule of thumb is to turn unnecessary services off and concentrate on correctly securing and configuring those that are needed.
Keep a written record of what services and options you enable or disable; in the heat of the moment (especially when it is 3:00 a.m. and you are wondering what you did to deserve being hacked), the written record can help you reverse what you might have done earlier.
Another issue that fits under the misconfiguration umbrella is deploying a device and not changing the default administrator username and password programmed into the device. If you are wondering what I am referring to, look at the manual that came with your shiny, new firewall device that has all the blinky lights and whiz-bang security features. Have you looked at the “quick startup” section that almost all manuals have nowadays? Somewhere among those pages is a section about logging in for the first time and setting up the device. Most security devices either have no password, or the username/password combination is something such as “admin/admin.” Guess what? Hackers read manuals, too, and they are aware that default passwords are still active on routers, firewalls, and other Internet devices.
Note
Your next step is to consider device configuration templates, automated deployment tools with role based access control (RBAC), and staging before deployment should be configured to reduce misconfiguration exposure for a corporation.
Scripted Attacks
UNIX, BSD, and Linux are undoubtedly the systems for which attackers will find scripts susceptible to their activities. Many of these operating systems come with sample scripts and programs available for use. These are a blessing in disguise and, if left activated or unchecked, they can result in successful attacks against your system.
Attackers try to execute some of the following attacks against your system during this phase of the attack:
• Buffer memory overflows: The information has to go somewhere, and the attacker can direct it to compromise a system. When the Buffer In Question (BIQ) blows, the OS might do things that the developer never intended.
• Brute force guess passwords: The attacker starts a program that tries every word in a dictionary. Webster’s is fine, but it could also be a dictionary of names, movies, or sports teams/lingo, and so on. Tools such as John the Ripper are effective for dictionary and brute force attacks on passwords.
• Try and sniff a password: Everyone has to log in, and if the attacker can “see” a user’s password, he is in! Can you imagine the number of captured passwords that could be seen in the morning when everyone is logging in to your network? Many passwords are plain and clear text to be uncovered with an open-source sniffer.
• Capture the password: In this case, the attacker wants to capture the password file, which can then be decrypted and cracked at the attacker’s leisure and most likely not on the system that was compromised. In other words, the attacker copies this file and cracks it at his leisure (that is, sleeping or at his day job) so that the information it contains is useful.
The techniques, tools, and procedures vary according to the attacker’s level of expertise and ability to code custom scripts and programs. Either way, a plethora of free open-source tools is available for use; the attacker will more than likely make use of some, if not all the following:
• NMAP: www.insecure.org/
• NESSUS: www.nessus.org
• SATAN: www.porcupine.org/satan/
• ETTERCAP: http://ettercap.sourceforge.net/
Do not discount the fact that commercial products are also available and can be used by hackers as well:
• GFI LANGuard: www.gfi.com/
• SAINT: www.saintcorporation.com/
• METASPLOIT PRO: www.rapid7.com
• CORE IMPACT: www.coresecurity.com/
The following section discusses how attackers work on escalating how much they are allowed to do (that is, privilege) after accessing a system.
Escalating Privilege
At this point in a hack, attackers might have gained access to a system. Perhaps the attackers learned/guessed/hacked a user’s password because it was something simple, like the user’s favorite sports team or movie. A regular user, however, might not have the privileges the attackers need for their goal. Thus, in this phase of the hack, the attackers must begin escalating their privilege level. They now understand the system a bit more, so they likely look for the following:
• Being “in” the system, the attackers can run the appropriate exploit code against the system to gain more privileges.
• Try to crack passwords using the many freely available password crack tools.
• Look for passwords that are not encrypted (that is, clear text).
• Evaluate the trusts that exist between the hacked system and others within the network. Perhaps there is another opportunity?
• Perhaps file or share permissions are incorrectly set.
These are the types of steps attackers take after they have gained rudimentary access. They would not likely go through all the risk and trouble to stop without ensuring that they can do whatever it is they intend to do.
If all else fails, or if the attackers want to implement a denial of service (DoS) attack, they use specialized tools called exploit code to disable a system. The use of these exploits is operating system–specific and can also depend on the patch level of the system state. Specifically, this means that system X is vulnerable to exploit 666, but if it has been patched with service patch 5, it is not vulnerable. Some of the exploits that could be used are SYN flood, ICMP techniques, overlapping fragments/offset bugs, and out of buffer. Again, the effectiveness largely depends on the system’s patch level. The attackers knows that when an exploit becomes public it can quickly become useless against systems where the system administrators stay on top of things; however, attackers also know that new exploits are found daily, and that research and experimentation are required to find the most effective tools and techniques.
The remaining steps are rather straightforward and obvious. After the hackers gain administrator/root access (that is, ownership), they complete the reason behind the attack, begin concealing their activities, and almost always leave a way for the hackers to get back into the system now that it is compromised.
Covering Tracks
After the attackers accomplish ownership of the target system, they must hide this fact from the system administrator and blend in if they intend to stay a while and siphon off information. This is one of the most fundamental rules of hacking; however, it is also one of the hardest for attackers to accomplish. For Windows-based systems, event log and registry entries are cleared/cleaned. For a UNIX-based system, attackers clear the history file and execute a log wiper to clean entries from UTMP, WTMP, and Lastlog.
Note
The attackers clear the logs—not delete them. When log files are deleted or cleared, a notification occurs that might draw attention to the fact that the system was compromised.
If the attackers want to maintain access to the system after achieving initial access, they create backdoors for future access. The methodology, tools, and techniques are system-dependent, but the intent is to create accounts, schedule batch/cron jobs, infect startup files, enable remote control services/software, and replace legitimate applications and services with Trojans. Possible tools include the following:
• Netcat: A simple UNIX utility that uses TCP or UDP protocol to read and write data across network connections (http://nmap.org/ncat/).
• VNC (Virtual Network Computing): A remote display system that enables you to view a system’s desktop environment—not only on the machine where it is running but also from anywhere on the Internet and from a wide variety of machine architectures. Many programs do this—VNC just happens to be free and rather popular. Plus, it works on Windows, Linux, and UNIX (www.uk.research.att.com/vnc/).
• Keystroke loggers: Hundreds are available on the Internet, and they can be either hardware- or software-based. Keystroke loggers record every keystroke pressed for a computer and can even email you what they record—anywhere—including all your or your company’s banking transactions.
• Customized programs: Add them to the Windows startup folder or configuration files (system.ini, win.ini, autoexec.bat, config.sys, and so on). For UNIX-based systems, you can employ entries in the /etc/rc.d directory. A good example of this would be ZEUS as a massive botnet with a command and control screen for easy management and deployment.
Note
Zeus is perhaps one of the largest botnets in the world, and it’s an interesting read: http://en.wikipedia.org/wiki/Zeus_(trojan_horse).
There are cases when the attacker does not want to have a backdoor placed in the target system. Usually, this is in the case of corporate espionage, in which an attacker gains access to acquire a certain piece of information and leaves. In a situation involving corporate espionage, the attackers know what they want and have no interest in regaining access to the system at a later time. In these types of attacks, the attackers’ main goal is to cover their tracks so that no one will ever know what happened.
