Two-Factor Authentication/Multifactor Authentication
As we have shown when reviewing RADIUS and TACACS, they are a means to securely authenticate to access a secure device. Those authentication methods relied on the user knowing a secret codeword or password, typically things the user knows. Although they are efficient, they are single layers in the defense of your network; additional layers, for defense in depth, are provided by using two-factor authentication. Two-factor authentication is when there are two independent and separate methods of authentication that the user must pass to gain access. Usually one of the two methods is something the user has that must be applied as part of the authentication process. You might think that this is a new concept, but you have likely have been engaging in two-factor authentication for quite awhile without realizing it. Accessing an ATM or paying with a bank card is two-factor authentication, the first authentication is “having the card,” and the second authentication is “knowing the PIN.”
Perhaps you have access with a token card that is synced to generate a unique code that when applied together enables you to gain access to your company’s network via a VPN. Two-factor authentication is becoming more and more common these days; your kids are likely using it if they play the online game World of Warcraft. As shown in Figure 5-12, you gain access to the game by “knowing” your username/password and “having” your token to generate an authentication code.
Figure 5-12 Warcraft Authenticator Code Is Two-Factor Authentication
IEEE 802.1x: Network Access Control (NAC)
Organizations continue to embrace mobility for their users by expanding wireless LANs (WLAN) for PCs and a whole range of mobile devices. Wireless networks are attractive because they are much easier to deploy and use than wired networks and cheaper, making them a better solution in many offices. However, security is a big concern because the open nature of wireless LANs brings a whole slew of concerns about user and corporate data being pulled from the air. Also increasing is the concern for the security of wireless networks with all sorts of new threats emerging, as discussed, and the bleed to wired networks. Organizations require security mechanisms that ensure that when credentials are transmitted, they remain secure and enable organizations to ensure that users trying to connect are whom they claim to be.
Enter 802.1X, a standard for port-based network access control, developed by the Institute of Electrical and Electronics Engineers (IEEE). 802.1X was originally designed for use in wired networks but was adapted to address WLAN security concerns because of its robust, extensible security framework and powerful authentication and data privacy capabilities. The 802.1X standard also defines the encapsulation methodologies for the transport of EAP over PPP or Ethernet. The 802.1X standard delivers powerful authentication, and security enables you to enforce port-based network access control when devices attempt to access the network. The 802.1X standard has three main components:
• Supplicant: Software that resides on the user’s machine or device and is used to request access to a wired or wireless network
• Authenticator: Devices, such as switches or wireless access points, that sit between the supplicant and the authentication server
• Authentication server: A server that receives authentication messages which in turn takes the request and validates against a back-end data store such as Active Directory, eDirectory, or LDAP
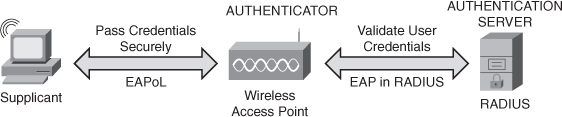
802.1x has become popular in wireless and wired networks in large part because its operation is secure and straightforward. When attempting to access an 802.1X-enabled network, instead of the user or device simply being granted Layer 3 access, it is challenged for its identity. If the user’s device is not configured for use in an 802.1X-based network, that is, it does not have a running supplicant, it will be denied network access. If the user’s device is configured with an operational supplicant, it will respond to the challenge for its identity and start the 802.1X authentication process. The supplicant passes network credentials (user and/or device identification information) to the authenticator, which verifies the connection to the network and passes the identification information on to the authentication server to determine access. Figure 5-13 demonstrates how 802.1X would work in a wireless network.
Figure 5-13 802.1x Authentication Process Flow
In a wired network, switches can use IEEE 802.1X to perform user authentication, rather than the types of device authentication performed by many of the other features described in this section. User authentication requires the user to supply a username and password, verified by a RADIUS server, before the switch can enable the switch port for normal user traffic. Requiring a username and password prevents the attacker from simply using someone else’s PC to attack the network without first breaking the 802.1X authentication username and password.
Cisco has a comprehensive identity management solution based on 802.1X called TrustSec. TrustSec is an integrated solution that uses Cisco products that offer authentication, access control, and user policies to secure network connectivity and resources. These products include the following:
• Cisco Catalyst family of switches
• Wireless LAN access points and controllers
• Cisco Secure ACS
• Cisco Secure Services Client
Additional and optional components include X.509 public key infrastructure (PKI) certificate architecture. You can find detailed TrustSec information including configuration and deployment guidelines at www.cisco.com/go/trustsec.
Information on how the TrustSec and 802.1x solution is integrated into Cisco NAC is covered in the following section.
Network Admission Control
Network Admission Control (NAC) is a multipart solution that validates the security posture of an endpoint system before entering the network. With NAC, you can also define what resources the endpoint has access to, based on the results of its security posture. NAC is a key part of the Cisco Self-Defending Network Initiative (SDNI). The SDNI mission is to dramatically improve the capability of the network to identify, prevent, and adapt to threats.
NAC Appliance or Cisco Clean Access (CCA) enables an organization to enforce security policies by blocking, quarantining, and performing remediation of noncompliant systems. Remediation occurs at the discretion of the administrator. The policies and requirements enforced by the Cisco NAC Appliance include checks for latest antivirus software, operating system (OS) patches, and security patches. The Cisco NAC Appliance can also perform vulnerability scanning on the end-user machine in addition to role-based authentication on users attempting to connect to the network. The NAC Appliance solution can restrict what resources these users can access, based on their role. All these policies and configurations are done in the Clean Access Manager (CAM). The Cisco NAC Appliance has three major components:
• Clean Access Server (CAS): Acts as a network control device
• Clean Access Manager (CAM): Manages one or more servers
• Clean Access Agent (optional): Serves as an endpoint lightweight client for device-based registry scans in unmanaged environments
Cisco TrustSec
The traditional network and physical perimeter is no longer the only border where information must be defended. Collaboration, IT consumerization, mobility, and new computing technologies are increasing productivity while presenting new security requirements. There is greater pressure on IT to meet the demands of a dynamic workforce—both in terms of service delivery and security challenges. New solutions are needed to protect borderless networks and to help further improve business efficiencies in the mean time. Cisco TrustSec is such a solution.
Solution Overview
Cisco TrustSec enables organizations to secure their networks and services through identity-based access control to anyone, anywhere, anytime. The solution also offers data integrity and confidentiality services, policy-based governance, and centralized monitoring, troubleshooting, and reporting services. TrustSec can be combined with personalized, professional service offerings to simplify solution deployment and management, and is a foundational security component to Cisco Borderless Networks.
The Cisco TrustSec solution offers the following benefits to customers:
• Compliance support: Expands real-time access visibility and audit trails across an increasingly complex network to address mandated monitoring, auditing, and reporting requirements
• Strengthened security: Extends security across the borderless network by enforcing consistent security policy, ensuring endpoint health, and delivering a secure network fabric
• Increased efficiency: Reduces IT overhead through centralized identity services, integrated policy enforcement, a consistent user experience, and dynamic assignment of user and device access
The core Cisco TrustSec functional areas follow:
• Identity-aware user and device access: Dynamically provides role-based access. Noncompliant devices can be quarantined, remediated, or denied access.
• Guest user access and lifecycle management: Sponsored guests receive restricted access to specific resources (Internet, printers, and so on) through a customized web portal. Internal network access is blocked and activity is tracked and reported.
• Nonuser device discovery: Nonuser devices (printers, cameras, phones, and so on) are centrally discovered. Access is provided based on policy, and device behavior is monitored and audited to prevent spoofing.
• Data integrity and confidentiality: Data paths can be encrypted via MACsec, from the endpoint client to the network core, while allowing critical tools (firewalls, IPSs, content inspection, QoS, and so on) to retain visibility into data streams.
• Monitoring, management, and troubleshooting: Centralized, policy-based corporate governance and compliance includes centralized monitoring and tracking of users and devices to maintain policy compliance. Provides sophisticated troubleshooting, detailed auditing, and historical and real-time reporting.
• Professional services: TrustSec services provide policy review, analysis, and design expertise to prepare a network to deploy a TrustSec solution.
Figure 5-14 illustrates the mechanics of how Cisco TrustSec works.
Figure 5-14 How Cisco TrustSec Works
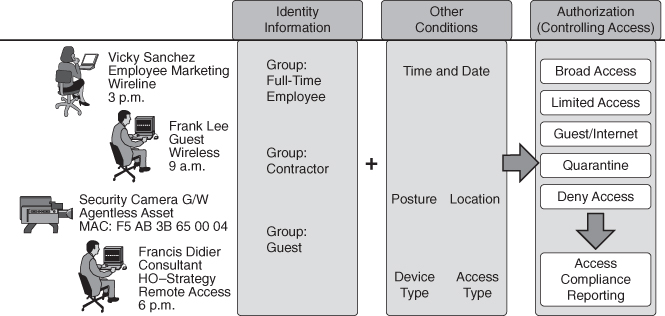
Network users are authenticated with flexible authentication mechanisms to support different device types, operating systems, and access methods.
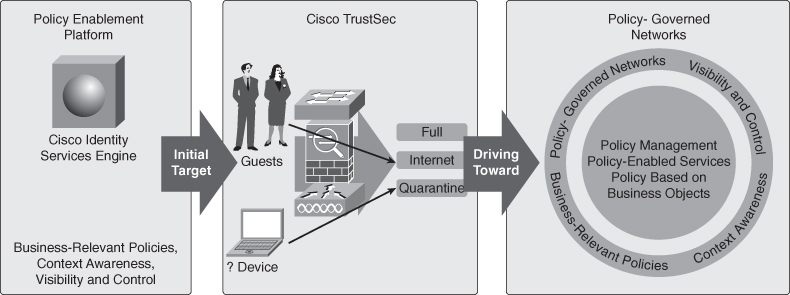
Cisco Identity Services Engine
Traditional corporate network boundaries and siloed services are a thing of the past. Today’s networks must accommodate an ever-growing array of consumer IT devices while providing user-centric policy and enabling global collaboration. The Cisco TrustSec architecture addresses this shift by using identity-based access policies to tell you who and what is connecting to your network, allowing IT to enable appropriate services without sacrificing control.
The first release of ISE focuses on the pervasive service enablement of TrustSec for Borderless Networks. Cisco Identity Services Engine (ISE) delivers all the necessary services required by enterprise networks (AAA, profiling, posture, and guest management) in a single appliance platform. In the future, the same ISE platform can be used to propagate consistent service policies throughout the borderless network, from any endpoint to the video delivery optimization, branch service personalization, and data center server and service agility.
As part of the Cisco TrustSec solution and the Cisco SecureX architecture for Borderless Networks, the Cisco ISE provides a centralized policy engine for business-relevant policy definition and enforcement. ISE complements global contextual information offered by Cisco Security Intelligence Operations (SIO) with localized context awareness for effective access policy enforcement.
• Security: Secures your network by providing real-time visibility into and control over all users and devices on your network.
• Compliance: Enables effective corporate governance by creating consistent policy across an infrastructure.
• Efficiency: Helps increase IT and network staff productivity by automating traditionally labor-intensive tasks and streamlining service delivery.
• Business-relevant policies: Enables centralized, coordinated policy creation and consistent policy enforcement across the entire corporate infrastructure, from head office to branch office.
• Systemwide operational visibility: Discovers, assesses, and monitors users and endpoints and employs advanced troubleshooting capabilities to give IT teams complete visibility into who and what is on the corporate network.
• Context-aware enforcement: Gathers information from users, devices, infrastructure, and network services to enable organizations to enforce contextual-based business policies across the network. Cisco ISE acts as the “single source of truth” for contextually rich identity attributes, including connection status, user and device identity, location, time, and endpoint health.
• Flexible services architecture: Combines AAA, posture, profiling, and guest management capabilities into a single appliance platform. Cisco ISE can be deployed across the enterprise infrastructure, applying the appropriate services supporting 802.1x wired, wireless, and VPN networks. Figure 5-15 demonstrates these aspects of ISE.
Figure 5-15 ISE-Based TrustSec LAN Deployment
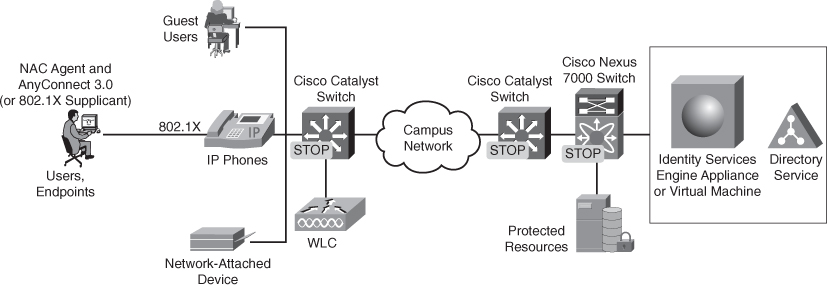
The Cisco ISE is part of an infrastructure-based Cisco TrustSec deployment using Cisco network devices to extend access enforcement throughout a network. Additional deployment components include Cisco NAC Agent and Cisco AnyConnect (or a 802.1x supplicant) on the endpoint; Cisco Catalyst switches and Cisco wireless LAN controllers acting as policy enforcement points for the LAN; and Cisco Adaptive Security Appliances for secure remote access. Cisco ISE also integrates with directory services such as Microsoft Active Directory and Sun ONE Directory Server as policy information points.
Putting Cisco TrustSec and ISE together is a layered solution, as shown in Figure 5-16.