Essentials First: Life in the DMZ
The Demilitarized Zone (DMZ) is a term used in the military to define a buffer area between two enemies. Perhaps the most commonly acknowledged DMZ in the world is the DMZ between North Korea and South Korea, which separates them because they have not yet signed a permanent peace treaty since the Korean War. Perhaps this is an interesting piece of military and political trivia that you did not know, but how does it relate to securing your network and firewalls?
If your company has a self-hosted public website complete with email servers, you might consider using a two-interface (inside and outside) firewall and have the firewall create translation rules that direct the inbound traffic to the correct servers on your private network. Although this might seem like a safe thing to do, it could be disastrous if a talented hacker sets his sights on you. Connecting web, mail, and FTP servers located on the inside of your network to the Internet can be dangerous and, in some cases, simply not recommended. Secure FTP is also an option but the same rules apply.
Well, some smart people got together a long time ago and said, “Hey—let’s put a third interface on the firewall and call it a DMZ.” Sending traffic from the Internet inbound directly to your private network is a bad idea. Adding the third interface to a standard firewall made things both easier and quite a bit safer when deploying Internet accessible servers and services (www, email, and so on). If you were going to sell computers out of your house, you would not want people coming inside your house to buy one, would you? Of course not; you would want to set up a little shop in the garage or on the front porch, thus preventing people that you do not know from wandering all over your house and tampering with your comic book collection or going into your fridge to make a sandwich.
A DMZ is an interface that sits between a trusted network segment (your company’s network) and an untrusted network segment (the Internet), providing physical isolation between the two networks enforced by a series of connectivity rules within the firewall. The physical isolation aspect of a DMZ is important because it enables Internet access only to the servers isolated on the DMZ and not directly into your internal network, as shown in Figure 7-3.
Figure 7-3 DMZ Placement and Function
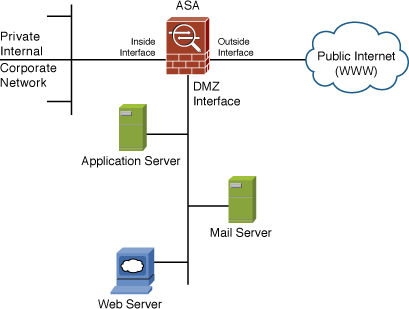
In Figure 7-3, the segment connected to the DMZ interface contains the mail, web, and application servers. Rules applied to the DMZ interface prevent traffic from the Internet from going beyond the segment attached to it.
The biggest benefit to a DMZ is in isolating all unknown Internet requests to the servers on the DMZ and no longer allowing them into your internal network. However, some additional benefits to deploying a firewall with a DMZ can help you better understand what happens in your network and thereby increases security:
• Auditing DMZ traffic
• Locating an IDS on the DMZ
• Limiting routing updates between three interfaces
• Locating DNS on the DMZ
This section discussed what a DMZ is and provided a general example of how to use one. The following case studies examine a requirement for a DMZ and why you should use one in a network given a specific set of criteria.
