Routing Protocol Security
Any WAN these days runs a dynamic routing protocol; the most common and secure of which is Open Shortest Path First (OSPF). Although an in-depth discussion of how dynamic routing with OSPF works is outside the scope of this book, a brief overview is in order. Dynamic routing provides a means for routers to share knowledge of the networks of which they are aware. OSPF is one of the protocols that can be used for this exchange of information. If attackers were to isolate or inject bogus routing updates into your dynamic routing protocol, they could cause all sorts of issues within your network, resulting in critical data not getting across the network.
To safeguard your network’s routing information within your WAN, you can configure route authentication between routers. This section briefly discusses how route authentication in OSPF is done and how it can benefit the security of your network.
Route authentication enables peer routers to positively identify the source of incoming encrypted dynamic routes. This means that attackers cannot forge erroneous routes or tamper with the exchange of routes without detection.
OSPF Authentication
OSPF is responsible for transmitting routing updates and building a routing table to ensure connectivity across a network. OSPF incorporates security within its function as a routing protocol. The authentication capacity provided in OSPF is sufficient to protect the exchange of routing information.
This section describes OSPF authentication as part of a total security plan and explains what neighbor router authentication is, how it works, and why you should use it to increase your overall network security. Following are several topics of importance about this issue that this section discusses:
• Benefits of neighbor authentication
• Conditions for deploying OSPF neighbor authentication
• How neighbor authentication works
• Configuring neighbor authentication
OSPF is responsible for transmitting routing updates and building a routing table enabling data to flow across a network. OSPF authentication was designed to protect only the integrity of the routing information within an OSPF routing domain; in other words, data is not protected—you need additional encryption to accomplish that. You can prevent any OSPF router from receiving fraudulent route updates by configuring the router to use a type of security known as neighbor router authentication. Following are two design characteristics that truly define how OSPF authentication operates:
• OSPF authentication is activated for an entire network, or in OSPF terminology, an area.
• The authentication key must match for neighboring routers on the same link.
Following are several different ways that you can deploy this type of security within your OSPF network:
• By assigning the same OSPF authentication key throughout the entire OSPF area
• By assigning a different key for every link within the network
Regardless of which technique you decide to use, the passwords used between neighboring routers must match.
Note
This section refers to neighbor router authentication as neighbor authentication. Neighbor router authentication is also sometimes called route authentication. The use of neighbor enables us to be extremely specific in our discussion.
Benefits of OSPF Neighbor Authentication
When configured, neighbor authentication occurs whenever routing updates are exchanged between neighboring OSPF routers within the OSPF area that has authentication activated. This authentication ensures that a router receives reliable routing information from a trusted source (that is, a neighbor router also running OSPF).
Without OSPF authentication, unauthorized or deliberately malicious routing updates could compromise the integrity of your network traffic. A security compromise could occur if an unfriendly party diverts or analyzes your network traffic. The compromise might not be the result of malicious action.
For example, an unauthorized or compromised device could send a fictitious routing update to convince your router to send traffic to an incorrect destination. This diverted traffic could be analyzed to learn confidential information about your organization, or it could merely be used to disrupt your organization’s capability to effectively communicate using the network. OSPF authentication prevents any such fraudulent route updates from being received by your router.
When to Deploy OSPF Neighbor Authentication
You should consider configuring a router for OSPF authentication if that router meets any or all of these conditions:
• It is conceivable that the router might receive a false route update.
• If the router were to receive a false route update, your network might be compromised. This is almost a certainty.
• You deem it necessary as part of your network security architecture.
Remember that if you configure a router for OSPF authentication, you also need to configure the neighboring routers for authentication as well.
How OSPF Authentication Works
When OSPF authentication has been configured on a router, the router authenticates the source of each routing update packet that it receives. This is accomplished by the exchange of an authenticating key (sometimes referred to as a password) that is known to both the sending and the receiving router. Following are two types of OSPF neighbor authentication used:
• Plaintext authentication
• Message Digest Algorithm Version 5 (MD5) authentication
Both forms work in essentially the same way, with the exception being that MD5 sends a message digest instead of the authenticating key itself. The message digest is created using the key and a message, but the key itself is not sent, preventing it from being read while it is being transmitted. Plaintext authentication sends the authenticating key itself over the wire. Plaintext authentication is not recommended for use as part of your security strategy as a means of protecting against malicious attacks. The primary use of plaintext authentication is to avoid accidental changes to the routing infrastructure. Using MD5 authentication, however, is a recommended best practice.
As with all keys, passwords, and other security secrets, you must closely guard the authenticating keys used in neighbor authentication. The security benefits of this feature are reliant upon your keeping all authenticating keys confident.
Plaintext Route Authentication
Each participating neighbor router must share an authenticating key. This key is specified on each router during the configuration of OSPF. You can specify multiple keys with OSPF. For example, you can have a different key for each WAN interface on a router running OSPF. The caveat is that the neighbor router off each interface must have a matching key configured on the receiving interface, as shown in Figure 8-5.
Figure 8-5 OSPF Routing Authentication
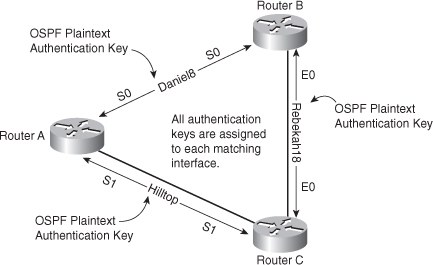
In general, when a routing update is sent, the following authentication sequence occurs:
1. A router sends a routing update with a plaintext authentication key (that is, password).
2. The receiving (neighbor) router checks the received authentication key against the same key stored in its own memory.
3. If the two keys match, the receiving router accepts the routing update packet. If the two keys do not match, the routing update packet is rejected.
MD5 Route Authentication
MD5 authentication works similarly to plaintext authentication, except that the key is never sent over the wire. Instead, the router uses the MD5 algorithm to produce a message digest of the key (also called a hash). The message digest is then sent instead of the key itself. This ensures that nobody can eavesdrop on the line and learn keys during transmission.
One difference between plaintext and MD5 authentication is that MD5 does support defining more than one key per interface (and uses the key number to differentiate the keys). One implication of potentially having more than one key defined is that key management and especially changing keys can be more graceful with MD5 (define a new key on one router [they become out of sync but continue using the old key]; define the new key on the other router [they become in sync and use the new key]; remove the old key from both routers). Contrast this operation to plaintext, where you define a new key on one router, and they become out of sync and terminate the neighbor relationship until the new key is defined on the second router.
Authenticating with Other Dynamic Routing Protocols
Although OSPF is an excellent reliable and secure protocol, it is not the only dynamic routing protocol that you can use. Most modern routing protocols can perform route authentication between neighboring routers to protect the integrity of your network. OSPF was presented as a baseline to introduce the concepts and benefits available to you; if you want to learn more about OSPF, check out the following definitive text on the subject:
OSPF Network Design Solutions, Second Edition
(www.ciscopress.com/bookstore/product.asp?isbn=1587050323)
