Chapter 6: Staying Secure Online
In This Chapter
![]() Understanding the dangers of going online
Understanding the dangers of going online
![]() Using a firewall
Using a firewall
![]() Avoiding trouble online
Avoiding trouble online
I know that you’ve heard horror stories about hacking: Big corporations and big government installations seem to be as open to hackers as a public library. Often, you read that even entire identities are stolen online. When you consider that your Mac can contain very sensitive and private information in your life — such as your Social Security number and financial information — it’s enough to make you nervous about turning on your computer long enough to check your eBay auctions.
But how much of that is Hollywood? How truly real is the danger, especially to Mac owners? And how can you protect yourself? The good news is that you can easily secure your data from all but the most determined hacker. In fact, depending on the hardware that you’re using to connect to the Internet, you might be well guarded right now without even knowing it.
In this chapter, I continue a quest that I’ve pursued for over two decades now — to make my readers feel comfortable and secure in the online world by explaining the truth about what can happen and telling you how you can protect your system from intrusions.
What Can Happen if I Don’t Take Security Seriously?
Before I begin, I want to offer you a moment of reassurance and a little of my personal background to explain that I’m well qualified to be your guide through this online minefield. (After all, you don’t want Jerry Lewis lecturing you on how to maintain your Internet security. He’s a funny guy, though, convenez-vous?)
![]() I’ve been running and managing all sorts of online systems since the days of the BBS (Bullet1in Board System), the text-based dinosaurs that used to rule the online world in the early ’80s to early ’90s. (In fact, my first book was on this very subject — and it contained a chapter on viruses long before they were the darlings of the techno-media.)
I’ve been running and managing all sorts of online systems since the days of the BBS (Bullet1in Board System), the text-based dinosaurs that used to rule the online world in the early ’80s to early ’90s. (In fact, my first book was on this very subject — and it contained a chapter on viruses long before they were the darlings of the techno-media.)
![]() As a consultant, I run websites and squash virus attacks for a number of companies and organizations.
As a consultant, I run websites and squash virus attacks for a number of companies and organizations.
![]() I run a popular Internet radio station that serves up ’70s hits in CD-quality to anyone with a high-speed DSL or cable Internet connection and a copy of iTunes. (More on this broadcasting revolution in Book III, Chapter 2.)
I run a popular Internet radio station that serves up ’70s hits in CD-quality to anyone with a high-speed DSL or cable Internet connection and a copy of iTunes. (More on this broadcasting revolution in Book III, Chapter 2.)
![]() I keep my own office network of six computers safe from attack while still providing readers all over the world with websites and the aforementioned radio station and BBS.
I keep my own office network of six computers safe from attack while still providing readers all over the world with websites and the aforementioned radio station and BBS.
With that understood, here’s what can happen to you online without the right safeguards, on any computer:
![]() Hackers can access shared information on your network. If you’re running an unguarded network, others can gain access to your documents and applications or wreak havoc on your system.
Hackers can access shared information on your network. If you’re running an unguarded network, others can gain access to your documents and applications or wreak havoc on your system.
![]() Your system could be infected with a virus or dangerous macro. Left to their own devices, these misbehaving programs and macro commands can delete files or turn your entire hard drive into an empty paperweight. (Although Mac viruses are very, very rare as I write this, they’re starting to appear with more frequency (along with their malware brethren). Plus, if you dual-boot your Intel Mac into Windows, you’ve suddenly entered a veritable minefield of PC viruses, malware, and spyware. More on this in a page or two.)
Your system could be infected with a virus or dangerous macro. Left to their own devices, these misbehaving programs and macro commands can delete files or turn your entire hard drive into an empty paperweight. (Although Mac viruses are very, very rare as I write this, they’re starting to appear with more frequency (along with their malware brethren). Plus, if you dual-boot your Intel Mac into Windows, you’ve suddenly entered a veritable minefield of PC viruses, malware, and spyware. More on this in a page or two.)
![]() Unsavory individuals could attempt to contact members of your family. This kind of attack may take place through applications like Messages, through e-mail conversations, or web discussion boards, putting your family’s safety at risk.
Unsavory individuals could attempt to contact members of your family. This kind of attack may take place through applications like Messages, through e-mail conversations, or web discussion boards, putting your family’s safety at risk.

![]() Hackers can use your system to attack others. Your computer can be tricked into helping hackers when they attempt to knock out web servers and public-access File Transfer Protocol (FTP) sites on the Internet. Along the same lines, that innocent web server you put online can be misused by spam-spewing, online “entrepreneurs.” (Cute name, right?)
Hackers can use your system to attack others. Your computer can be tricked into helping hackers when they attempt to knock out web servers and public-access File Transfer Protocol (FTP) sites on the Internet. Along the same lines, that innocent web server you put online can be misused by spam-spewing, online “entrepreneurs.” (Cute name, right?)
![]() Criminals can attempt to con you out of your credit card or personal information. The Internet is a prime tool used by those trying to steal identities.
Criminals can attempt to con you out of your credit card or personal information. The Internet is a prime tool used by those trying to steal identities.
To be absolutely honest, some danger is indeed present every time you or any user of your Macintosh connects to the Internet. However, here’s the good news. With the right safeguards, it’s literally impossible for most of those worst-case scenarios to happen on your Macintosh, and what remains would be so difficult that even the most die-hard hacker would throw in the towel long before reaching your computer or network.
Using a Macintosh gives you an advantage: Hackers and virus developers (there’s a career for you) are traditionally interested only in “having fun” with PCs running Windows, so the likelihood that Mountain Lion could pick up a virus is far less than it would be if you were using Windows. As I mentioned earlier, if you boot into Windows using Mountain Lion’s dual-boot feature on your Macintosh (which I discuss at length in Book VIII, Chapter 1), you need to pay heed to Windows security — the same warning also applies to those running Windows in a virtual machine (using programs like Parallels Desktop or VMware).
Heck, I even know a couple of fellow Mac owners who feel they just don’t need antivirus protection — but believe me, this is not an area where you want to be lax and lazy, and you still need an antivirus application! (More on antivirus software later in this chapter.)
I also want to point out that virtually everyone reading this book — as well as the guy writing it — really doesn’t have anything that’s worth a malicious hacking campaign. Things like Quicken data files, saved games of Sims 3, and genealogical data might be priceless to us, of course, but most dedicated hackers are after bigger game. Unfortunately, the coverage that the media and Hollywood give to corporate and government attacks can turn even Aunt Harriet more than a little paranoid. Therefore, time for another of Mark’s Maxims:
“Shields Up, Chekov!”
“Okay, Mark, now I know the real story on what can happen to my computer online. So what do I do to safeguard my Macintosh?” You need but two essential tools to protect your hardware (besides a healthy amount of common sense, which I cover in the upcoming section “A Dose of Common Sense: Things Not to Do Online”): a firewall and an antivirus program.
Firewall basics
First, a definition: A firewall is a piece of hardware or software that essentially builds an impermeable barrier between the computers on your side of the wall (meaning your Mac and any other computers on your network) and all external computers on the other side of the wall (meaning the rest of the Internet).
“But wait a second — if other computers can’t reach me and my Mac can’t reach them, how can I use the Internet at all?” Ah, that’s the beauty of today’s firewalls. By using a series of techniques designed to thwart attacks from the outside, a firewall allows you to communicate safely, even monitoring what you send and what you receive for later examination. Figure 6-1 illustrates the basics of a firewall.
Figure 6-1: A firewall, hard at work. (They’re not actually made of brick, though.)
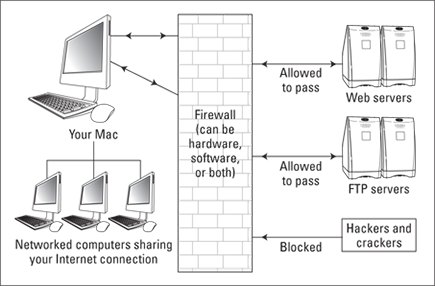
A firewall sounds grand and incredibly complex and highly technical — and sometimes it is — but it can also be incredibly simple. For example:
![]() You can spend anywhere from $50 to thousands of dollars installing sophisticated firewall hardware and/or software.
You can spend anywhere from $50 to thousands of dollars installing sophisticated firewall hardware and/or software.
or
![]() You can “activate” your firewall by disconnecting your Mac’s dialup, digital subscriber line (DSL), or cable modem from the wall socket.
You can “activate” your firewall by disconnecting your Mac’s dialup, digital subscriber line (DSL), or cable modem from the wall socket.
Believe it or not, both of those examples technically involve a firewall. In the first case, the firewall is a physical, tangible presence on the network; in the second case, the lack of a connection to the Internet actually acts as a firewall. (Think of it as the Air Firewall.) I’ve spoken to a number of readers who actually do this; however, if you’re running a website or downloading a file from your company’s FTP site, yanking the connection when you head to bed isn’t an option. Therefore, most of us will install a physical firewall through hardware or software.
Do I already have a firewall?
In some cases, you might already be using a hardware firewall and not even know it. For example, many Internet-sharing devices include a built-in NAT firewall. Network Address Translation (NAT) is the most effective and popular hardware firewall standard in use by consumer devices. If you’re using an Internet sharing hub or router, check its manual to determine whether it offers NAT as a firewall feature — and if so, turn it on if NAT isn’t enabled by default. (See Book VI, Chapter 2 for more on Internet sharing, routers, and firewalls.)
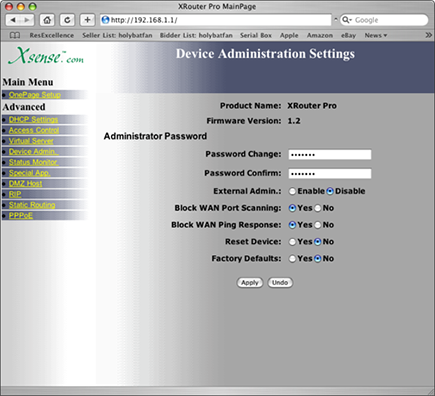
For instance, Figure 6-2 illustrates the configuration screen for my Internet router. Note the options to disable port scanning and ping responses, which are two tricks that hackers often use to detect what’s often called a “hot computer” — meaning that the computer can be identified and is accessible to attack. Wireless networks are notoriously hot. For more information on securing your wireless connections, visit Book VI, Chapter 4.
Figure 6-2: My Internet router is set to be downright rude to hackers.
Using the internal OS X firewall
OS X includes a powerful internal firewall, which Mountain Lion makes very simple to use. Most Mac owners will be perfectly satisfied with this built-in firewall, which is configured through System Preferences. Find more information on setting up your firewall in Book VI, Chapter 2.
Using a commercial software firewall
You’ll also find a number of popular alternatives to Mountain Lion’s built-in firewall on the market that offer more control over individual applications and more configuration options than your OS X firewall. For example, consider these commercial software firewall applications:
![]() Symantec, Norton Internet Security for Mac, $80 per year (
Symantec, Norton Internet Security for Mac, $80 per year (www.symantec.com
): Frequent updates and top-of-the-line technical support ensure that your firewall stays current and that you can get help when you need it.
![]() Intego, Internet Security Barrier X6, $80 per year (
Intego, Internet Security Barrier X6, $80 per year (www.intego.com
): Along with antispam and antiphishing features, Internet Security Barrier X6 comes with a number of preset configurations that allow you to choose a basic firewall for your network environment with a single click.
Antivirus basics
Next, consider your antivirus protection (both under Mountain Lion and Windows XP/Vista/7/8, if you’re running Boot Camp on an Intel-based Mac). Viruses are typically transmitted through applications. You run a program, and the virus is activated. Although they don’t meet the traditional definition of a virus, both scripts and macros can be used to take control of your system and cause trouble, as well. Therefore, you need to closely monitor what I call The Big Three:
![]() Web downloads: Consider every file that you receive from the Internet as a possible viral threat.
Web downloads: Consider every file that you receive from the Internet as a possible viral threat.
![]() Removable media: Viruses can be stored on everything from CD-ROMs and DVD-ROMs to USB flash drives.
Removable media: Viruses can be stored on everything from CD-ROMs and DVD-ROMs to USB flash drives.
![]() E-mail file attachments: A Trojan Horse or “worm” application sent to you as an e-mail attachment is an easy doorway to your system.
E-mail file attachments: A Trojan Horse or “worm” application sent to you as an e-mail attachment is an easy doorway to your system.
Horrors! OS X has no built-in antivirus support. (Then again, neither does Windows.) However, a good antivirus program will take care of any application that’s carrying a virus. Some even handle destructive macros within documents. Make sure that the antivirus program you choose offers real-time scanning, which operates when you download or open a file. Periodic scanning of your entire system is important, too, but only a real-time scanning application such as VirusBarrier X6 can immediately ensure that the StuffIt and Zip archives or the application you just received in your e-mail Inbox is actually free from viruses. (Oh, and don’t forget that many of the Software Updates released by Apple for Mountain Lion will plug security holes in our favorite operating system.)
I heartily recommend both ClamXav 2 (free for personal use at www.clamxav.com
) and Intego’s VirusBarrier X6 for Mac (which is included as part of the Internet Security Barrier X6 suite I mention earlier) for antivirus protection. Both programs include automatic updates delivered while you’re online to make sure that you’re covered against the latest viruses.
A Dose of Common Sense: Things Not to Do Online
One more powerful weapon that you can use to make sure that your Mac stays safe from unlawful intrusion is this: Practicing common sense on the Internet is just as important as adding a firewall and an antivirus application to your Mac.
With this in mind, here’s a checklist of things that you should never do while you’re online:
![]() Never download a file from a site you don’t trust. And make sure that your antivirus software is configured to check downloaded files before you open them.
Never download a file from a site you don’t trust. And make sure that your antivirus software is configured to check downloaded files before you open them.
![]() Never open an e-mail attachment until it has been checked. Don’t give in to temptation, even if the person who sent the message is someone you trust. (Many macro viruses actually replicate themselves by sending copies to the addresses found through the victim’s e-mail program. Of course, this problem crops up regularly in the Windows world, but it’s been known to happen in the Macintosh community as well.)
Never open an e-mail attachment until it has been checked. Don’t give in to temptation, even if the person who sent the message is someone you trust. (Many macro viruses actually replicate themselves by sending copies to the addresses found through the victim’s e-mail program. Of course, this problem crops up regularly in the Windows world, but it’s been known to happen in the Macintosh community as well.)
![]() Never enter any personal information in an e-mail message unless you know the recipient. Sure, I send my mailing address to friends and family, but no one else. In fact, e-mail can be intercepted by a determined hacker, so if you’re sending something truly important like personal or company data, use an encryption application, such as PGP Personal Desktop (
Never enter any personal information in an e-mail message unless you know the recipient. Sure, I send my mailing address to friends and family, but no one else. In fact, e-mail can be intercepted by a determined hacker, so if you’re sending something truly important like personal or company data, use an encryption application, such as PGP Personal Desktop (www.pgp.com
).
![]() Never enter any personal information on a website provided as a link in an e-mail message. Don’t fall prey to phishing expeditions. Some of these e-mail message/website combinations look authentic enough to fool anyone! No reputable online company or store will demand or solicit your personal information through e-mail or through a linked website. In fact, feel free to contact the company through its real website and report the phishing attempt!
Never enter any personal information on a website provided as a link in an e-mail message. Don’t fall prey to phishing expeditions. Some of these e-mail message/website combinations look authentic enough to fool anyone! No reputable online company or store will demand or solicit your personal information through e-mail or through a linked website. In fact, feel free to contact the company through its real website and report the phishing attempt!
![]() Never include any personal information in an Internet newsgroup post. In case you’re not familiar with the term, newsgroups are public Internet message bases, often called Usenet groups. Many ISPs offer a selection of newsgroups that you can access. Newsgroup posts can be viewed by anyone, so there’s no such thing as privacy in a newsgroup. (For a glimpse of just how long one of these posts can linger in the great Internet continuum, visit
Never include any personal information in an Internet newsgroup post. In case you’re not familiar with the term, newsgroups are public Internet message bases, often called Usenet groups. Many ISPs offer a selection of newsgroups that you can access. Newsgroup posts can be viewed by anyone, so there’s no such thing as privacy in a newsgroup. (For a glimpse of just how long one of these posts can linger in the great Internet continuum, visit www.google.com
, click the Groups button, and search for your name. I can pull up newsgroup messages that I posted back in 1995!)
![]() Never buy from an online store that doesn’t offer a secure, encrypted connection when you’re prompted for your personal information and credit card number. If you’re using Apple’s Safari browser, the padlock icon appears next to the site name in the title bar. When the padlock icon appears in the title bar, the connection is encrypted and secure — you’ll also note that the web address begins with
Never buy from an online store that doesn’t offer a secure, encrypted connection when you’re prompted for your personal information and credit card number. If you’re using Apple’s Safari browser, the padlock icon appears next to the site name in the title bar. When the padlock icon appears in the title bar, the connection is encrypted and secure — you’ll also note that the web address begins with https: rather than http:.
![]() Never divulge personal information to others over a Messages connection.
Never divulge personal information to others over a Messages connection.
![]() Never use the same password for all your electronic business. Use different passwords that include both letters and numbers, change them often, and never divulge them to anyone else.
Never use the same password for all your electronic business. Use different passwords that include both letters and numbers, change them often, and never divulge them to anyone else.
![]() Never give anyone else administrative access to your web server.
Never give anyone else administrative access to your web server.
![]() Never allow any type of remote access (such as sharing screens) to your Macintosh or your network without testing that access first. It’s very important to restrict remote access to visitors whom you trust.
Never allow any type of remote access (such as sharing screens) to your Macintosh or your network without testing that access first. It’s very important to restrict remote access to visitors whom you trust.
Find more details on securing your network from intrusion — including Internet hacker attacks — in Book VI. In Book II, I cover System Preferences that can affect the security of your system.

 Because this is a book that focuses on OS X Mountain Lion, I won’t be spending much time covering Windows. If you’d like a comprehensive guide to Windows 7 and the PC world, however, I can heartily recommend the sister volume to this book,
Because this is a book that focuses on OS X Mountain Lion, I won’t be spending much time covering Windows. If you’d like a comprehensive guide to Windows 7 and the PC world, however, I can heartily recommend the sister volume to this book, 
 Virus technology continues to evolve over time, just as more beneficial application development does. For example, viruses have been developed that are actually contained in both JPEG image files and e-books (electronic books). Nasty business, indeed. With a good antivirus application that offers regular updates, you’ll continue to keep your system safe from viral attack.
Virus technology continues to evolve over time, just as more beneficial application development does. For example, viruses have been developed that are actually contained in both JPEG image files and e-books (electronic books). Nasty business, indeed. With a good antivirus application that offers regular updates, you’ll continue to keep your system safe from viral attack.