Law Investigation, Forensics, and Ethics ◾ 359
© 2011 by Taylor & Francis Group, LLC
service. A trademark (TM is used to represent an unregistered trademark) dieren-
tiates products of the same trade. A service mark (using the symbol SM for an unreg-
istered service mark) dierentiates services of the same trade. A trademark not only
consists of a label, logo, or other identifying symbol, it may also cover the distinctive
packaging belonging to a particular product (e.g., the shape of a Coke bottle).
is is called trade dress. Color pattern, shape, design, arrangement of letters/
words, packaging style, and graphical presentation form a part of trade dress. In
early days, trade dress referred to the way a product was packaged to be launched in
the market, but now even the product design is an inclusion element of trade dress.
Elements of trade dress for a particular product do not aect the way in which the
product is used. Federal law for trademarks applies to trade dress also. ere is no
distinction between trade dress and trademark, as the Lanham Act (also known as
the “Trademark Act of 1946”) does not provide any distinction between the two.
Trademark Eligibility and the Benefits of Registering—Any individual or organ-
ization that wishes to use a unique identier in order to categorize its goods or services
can qualify for a trademark. e trademark needs to be unique and not misleading.
To register a trademark, the application form should be led at the USPTO.
Before the USPTO will accept an application to register a trademark, it must
detail the following:
◾ e applicant’s name
◾ A name and address required for correspondence
◾ An apparent depiction of the mark
◾ A list of the goods or services provided
e applicant must also pay the application-ling fee for one or more sets of goods
or services.
e following points cover the benets of registering a trademark:
◾ It protects an organization’s name/logo.
◾ e registered owner attains exclusive rights of the mark and gains protection
against trademark infringement.
◾ e mark may be used to give more visibility to the product from other prod-
ucts in the same trade.
◾ Following the trademark registration it is updated in the trademark search
database, which aids in the discouraging of other applicants from ling a
comparable variety of trademark.
◾ If a registered trademark is infringed, the title holder of the registered trade-
mark can request that the infringing party pay damages.
◾ It provides a foundation for ling the registration for the specic trademark
in a foreign country.
360 ◾ Official (ISC)
2
® Guide to the ISSMP® CBK®
© 2011 by Taylor & Francis Group, LLC
Trademark Infringement—A trademark infringement refers to the unauthorized
use of a protected trademark or service mark, or the use of something very similar
to a protected mark. e performance of any legal action to discontinue (or injunct)
the infringement is directly related to whether the defendant’s exercise of the mark
has created a likelihood of confusion in the typical consumer. Where the court
comes to a determination that a reasonable consumer would be confused, then the
owner of the original mark can put a stop to the use of the infringing mark by
the other party and may even receive damages. A party that holds the legal rights to
a particular trademark can sue other parties for trademark infringement based on
the standard “likelihood of confusion.” In the United States, the Trademark Act of
1946, statutes § 1114 and § 1125, are specic to trademark infringement.
Patents and Patent Infringement
A patent is dened in common terms to be a right granted for any device, substance,
method, or process that is new, inventive, and useful. It is essentially a monopoly
right over a registered invention or discovery that is enforceable by law and provides
the holder the exclusive right to commercially exploit the invention for the term of
the patent. A patent is not automatic and it must be applied for and registered in each
country in which it is to apply (there is no such thing as an international patent).
Patents give useful protection in the event that an invented new technology will result
in a product, composition, or process with considerable long-term commercial gain.
In the United States, the Patent and Trademark Oce issues patents. Patents
are eective up to 20 years from the date on which the submission is led. In
Australia and many other countries there are two types of patents in operation.
Some countries support alternatives to the full patent process through means
such as an innovation patent. ese are designed to be a comparatively quick, inex-
pensive safeguard that only last to a maximum of 8 years. Patent laws allow for the
granting of a patent on the new article not on the propositions that claim to put
into practice those ideas to make the article. You cannot patent an idea.
Any article, process, or manufacturing technique that asserts a right to a patent
is required to prove its utility. In 35 U.S.C. § 102, U.S. Patent law states that an
invention cannot be patented where
◾ e invention was known or used by others in this country, or patented or
described in a printed publication in this or a foreign country, before the
invention thereof by the applicant for patent, or
◾ e invention was patented or described in a printed publication in this or a
foreign country or in public use or on sale in this country more than one year
prior to the application for patent in the United States or
◾ e inventor has abandoned the invention, or
Law Investigation, Forensics, and Ethics ◾ 361
© 2011 by Taylor & Francis Group, LLC
◾ e invention was rst patented or caused to be patented, or was the subject
of an inventor’s certicate, by the applicant or the applicant’s legal represen-
tatives or assigns property rights to another in a foreign country prior to the
date of the application for patent in this country on an application for a patent
or inventor’s certicate led more than twelve months before the ling of the
application in the United States, or the invention was described in a patent
that has already been granted in the United States.
e primary types of patents include the following:
◾ Utility patents, which are granted to an individual who ascertains or invents
a new instrument, process, useful composition of matter, or manufacture.
Some examples include the following:
− A new process for the fraction distillation of petroleum
− A novel manufacturing method for paper
− A machine such as a motorbike or car
− A previously undiscovered composition of matter including a drug
◾ Design patents are granted to an individual who creates a new, innovative
design for an article of manufacture. It guards the look of an article, for
example, the shape of the Apple iPod.
◾ Plant patents or breeders’ rights are granted to an individual who conceives,
discovers, or asexually reproduces a distinctive variety of plant.
◾ An innovation patent is a fast, inexpensive, but limited protection option.
Document Management
It is an oense to destroy any document that is or may be used as evidence in an
ongoing or potential judicial proceeding in most Western (at least the common law)
jurisdictions. An organization must not destroy documents on the foundation that
the evidence is unfavorable. e penalties for the destruction of documents that are
suspected to possibly be subject to litigation may perhaps end in a charge of obstruc-
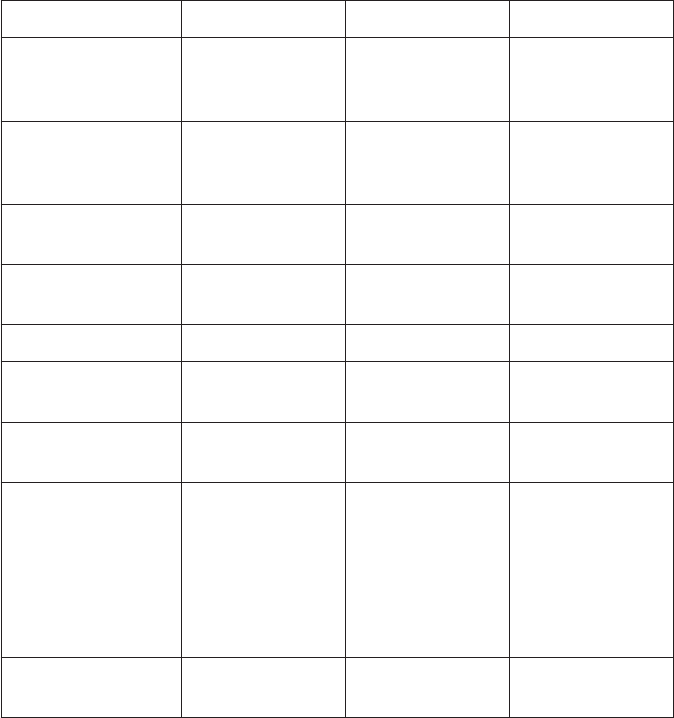
tion of justice (Table5.1).
Electronic Espionage
e United Kingdom diers from the United States in its eorts at codication
through the Restatement and Uniform Trade Secrets Act to introduce a legisla-
tive set of controls preventing electronic espionage. e English law as it relates to
a breach of condential information is exclusively derived from the common law
as it has evolved through the cases. A duty of condence is created when an indi-
vidual obtains condential information through a state of aairs where it would be
inequitable for that knowledge to be divulged to another. is could be a result of
the receiver of the information being on notice, or having an agreement that the
362 ◾ Official (ISC)
2
® Guide to the ISSMP® CBK®
© 2011 by Taylor & Francis Group, LLC
information was to be so handled. e contravention of the duty that can result
is in a civil action for a breach of condence. Actions for the breach of condence
occur in association with the leaking or other dissemination of data that has a com-
mercial value. is includes any personal information regarding an individual such
as credit cards, health information, etc.).
Breach of condence is complex. It enlarges to “reect changes in society, tech-
nology and business practice.” Furthermore, the right to privacy in the EU is incor-
porated in Article 8 of the European Convention on Human Rights. is expands
the available actions connected with a breach of condence to include safeguarding
against the misuse of private information. Under the common law, it is generally
required that the plainti prove three things in order to succeed in an action for a
breach of condence:
Table5.1 Minimum Document Retention Guidelines
Australia/NZ United States United Kingdom
Basic commercial
contracts
6 years after
discharge or
completion
4 years after
discharge or
completion
6 years after
discharge or
completion
Deeds 12 years after
discharge
A minimum of
6 years after
discharge
12 years after
discharge
Land contracts 12 years after
discharge
6 years after
discharge
12 years after
discharge
Product liability A minimum of
7 years
Permanent A minimum of
10 years
Patent deeds 20 years 25 years 20 years
Trademarks Life of trademark
plus 6 years
Life of trademark
plus 25 years
Life of trademark
plus 6 years
Copyright 75 years after
author’s death
120 years after
author’s death
50 years after
author’s death
Contracts and
agreements
(government
construction,
partnership,
employment,
labor, etc.)
A minimum of
6 years
Permanent A minimum of
7 years
Capital stock and
bond records
7 years after
discharge
Permanent 12 years after
discharge
Law Investigation, Forensics, and Ethics ◾ 363
© 2011 by Taylor & Francis Group, LLC
1. e information must be condential without being seen as trivial.
2. e information was presented in a circumstance that required a commit-
ment toward maintaining condence.
3. An unauthorized use or exposure of the secret information must have
occurred with a risk of damage occurring if action does not occur to stop the
incident.
e jurisdictional basis in most common law countries of the action for breach
of condence is unclear. e foundation most regularly relied upon is contract.
Frequently the parties will have incorporated express terms relating to con-
dentiality, but the courts have also commonly acted on the basis of an implied
condentiality provision in an existing contractual relationship. e courts have
also created an equitable obligation of condentiality autonomous of any contrac-
tual relationship. is obligation applies to the initial beneciary of the information
and to third parties who receive unauthorized disclosures of condential informa-
tion. is has also been used in addition to a contractual obligation, and at times
in substitution for a contractual obligation.
e duty that condence need be conserved may be overshadowed through a
variety of other civic causes. ese call for disclosure in the public interest. Either
the world at large or the appropriate authorities should be informed. It is generally
necessary for a court to seek equilibrium for the protection of the public interest.
is balance is judged in placing condentiality against a use or disclosure that
favors society and creates quantiable gains. Protections over the disclosure of pri-
vate data will not be reserved in the event that there is a just cause or excuse for
disclosing it.
An ISP or company that hosts information on the Internet needs to consider
the need to protect data against the needs of data protection and that of the public
interest. A failure to safeguard the interests of clients places the intermediary in
damage of civil actions. is issue is a particular concern for organizations that
host data (who have some obligation unless explicitly excluded in contract) and par-
ticularly service providers specializing in the provision of security services. ese
providers are contracted to ensure that the security of their clients is maintained
and are open to actions in both contract and negligence if they fail in their duties.
One of the greatest diculties comes to pass as a consequence of the ISP or
content hosting provider not having a contract with the owner of the condential
information to protect or monitor that data. e equitable doctrine, imposing a
responsibility of condentiality in respect of data that the recipient knows or should
have known was condential, and further that was proered under conditions that
involve the condentiality of data, may be appropriate in selected circumstances.
Nevertheless, it is clear that there remains a substantial dilemma for the plainti in
proving that such a responsibility exists. is would be predominantly true where
an organization declares unawareness of what content was on the site.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
