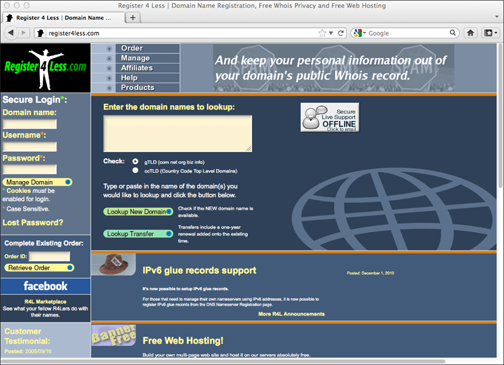
Figure 2-9: Registering your domain at Register4less.
Securing Your Brand’s Accounts
People often set up their brand accounts in a perfunctory fashion, not realizing that the little decisions they make along the way can create problems later on. Since your online reputation management strategy must begin with a secure foundation, I suggest reading through the following sections so that you have a good handle on how to set up your brand’s accounts more securely. The key is to make sure that you have full control over your accounts, not someone who’s working for you at the moment. Protect your interests more fully with these tips.
Registering your domain(s)
One of the most important decisions you will make in connection with having control over your online reputation management is really simple and easy to implement! The flip side of that good news is that if you’re considering entrusting that information to a third-party vendor, such as a site designer, you need to get that party to transfer those rights and responsibilities right back to your organization. It’s a fairly simple process that varies a little bit with each service but is really important to do.
If you haven’t registered your intended domain(s) yet, I strongly advise you to review Chapter 6 before you do. There I show you how to use search engine optimization (SEO) keywords more effectively.
Where you register is important. You will always make a better decision when you consider the Internet in terms of the American Wild West. Wear a cowboy hat and pin a silver star to your shirt as you work, and you’ll have the right frame of mind. There are outlaws there, and the American legal system is at least 15 years from learning how to negotiate online reputation management. Be savvy and be careful in your choice of domain registrars. I use Register4less, although there are many other reputable registrars. Figure 2-9 shows you how easy it is to search on Register4less’s site.
Here are some reputable providers:
![]() Register (
Register (www.register.com
): Clean, easy-to-use interface. Features monthly service bundles and the domain search information you need right at the top of the page.
![]() Register4less (
Register4less (www.register4less.com
): My favorite registrar because of its reputable business practices and ease of use.
![]() Name (
Name (www.name.com
): Cute, hip interface. Features a “domain nabber,” (a feature that claims a domain for you) and some pretty interesting hosting and web-page building tools.
![]() Namecheap (
Namecheap (www.namecheap.com
): Voted best domain registrar by Lifehacker readers. Offers domain registration with free e-mail, URL forwarding, and privacy protection.
Using a professional e-mail address
These days, people expect to see a brand use an official-looking e-mail address, not something like [email protected]. Such an address looks unprofessional, and its function within your organization isn’t clear. After all, it’s best to have different mailboxes for different kinds of correspondence so you won’t waste time tracking down important messages in a catchall e-mail inbox. Here are some tips to get the most out of your e-mail account:
![]() Don’t use your personal e-mail address. I suggest creating your own, like
Don’t use your personal e-mail address. I suggest creating your own, like [email protected]. You can also create a domain with Google’s tools and have it look like [email protected]. Don’t let me catch you using MyDog’[email protected]. People probably won’t take your brand seriously online.
![]() Don’t get too colorful: When I went back to college, I thought it was cool to have
Don’t get too colorful: When I went back to college, I thought it was cool to have nontraditional as my e-mail address — after all, I was something of a nontraditional student. Although I had kids in middle and high school, I had gone back to school and was sharing classrooms with 20-year-olds. I was clearly different. “Nontraditional” may have been accurate, but it wasn’t the most flattering term I could have used. After college, when it was time to create my resume, a trusted advisor counseled me to lose the address because it just didn’t look professional. Sage advice!
![]() Don’t give everyone the same address: Reserve your professional and personal e-mail addresses for people you trust. Direct everything else (product inquiries, newsletters) to a more anonymous e-mail account.
Don’t give everyone the same address: Reserve your professional and personal e-mail addresses for people you trust. Direct everything else (product inquiries, newsletters) to a more anonymous e-mail account.
Framing your positive publicity
You will never find a better way to turbo boost your brand online than via social media. It’s probably the most common reason people want to master their online reputation management, and it makes a very worthy goal to add to your strategy if you have the extra time and resources. I tell you everything you need to get started with a winning strategy in Chapter 9.
When one well-known speaker (a frequent Morton’s customer) tweeted that he’d love nothing better than a Morton’s steak when he got off the plane, he found a steamy, fragrant steak with all the trimmings waiting for him in the airport just after he arrived at baggage claim. Now that’s customer service!
This hasn’t happened to me just yet, but I have experienced phenomenal customer service via Twitter, such as the time I tweeted about visiting New York City for a speaking engagement. Somebody from my favorite hotel there sent me a direct message offering me a press discount and a fancy room with a gorgeous view. You can bet I feel really special just remembering that event, and I now refer people to that hotel every chance I get.
I have friends whose computer problems were solved through amazing customer service from Dell via Twitter. (I tell you a lot more about Dell’s super sophisticated setup in Chapter 3.)
I guess the big story is to use Twitter for customer service!
Taking control of your password security
It’s easy to dismiss password security. In a casual moment, it’s easy to think that a goofy or simple password suffices and that nothing bad can come from setting the name of your favorite football team as your Facebook password.
Lots of people do this. Two of the most common passwords used online today:
![]() ncc1701: The ship number for the Starship Enterprise (You’d think geeks would know better!)
ncc1701: The ship number for the Starship Enterprise (You’d think geeks would know better!)
![]() 8675309: The number mentioned in the 1982 Tommy Tutone song. The song supposedly caused an epidemic of people dialing 867-5309 and asking for “Jenny.”
8675309: The number mentioned in the 1982 Tommy Tutone song. The song supposedly caused an epidemic of people dialing 867-5309 and asking for “Jenny.”
Having a weak password is like using a screen door to prevent break-ins. For any number of unsavory reasons, dishonest people all over the world spend lots of time creating bots that roam the web and look for weak passwords. Odds are high that you or a friend have had your Facebook profile hacked. Maybe you got creepy messages from him. (Never click on these, by the way. They vary, but they’re never good for you. Avoid them and inform your friend that she’s been hacked.)
If this happens to you, Facebook has a recovery process you can use to attempt to get control back over your good name, er, profile, but your best defense is to have a first-class, bulletproof password. And in this section, I show you a fast, easy, thoroughly awesome way to always have a great password. It’s probably the most important thing you can do to preserve your reputation online.
![]() password
password
![]() 123456
123456
![]() 12345678
12345678
![]() qwerty
qwerty
![]() abc123
abc123
![]() monkey
monkey
![]() 1234567
1234567
![]() letmein
letmein
![]() trustno1
trustno1
![]() dragon
dragon
Creating super-safe passwords
There are two issues to remember about creating the very best passwords:
![]() They must be easy for you to remember.
They must be easy for you to remember.
![]() They must protect you from hackers.
They must protect you from hackers.
Here’s how you do it:
1. Brainstorm for a minute on a sentence or phrase that has some special meaning to you.
(However, try not to choose one that’s really popular right now.) For example:
• A favorite song lyric
• A line of poetry
• A movie quote (my favorite)
Let’s use “All we are is dust in the wind” as an example.
2. Convert your phrase into an acronym.
We’re using “All we are is dust in the wind,” so the acronym is “awaidinw.” It’s just the first letter of each word.
3. Substitute at least one letter with a number.
With “awaidinw,” it may look like this:
• awa1d1nw (the letter i is replaced with the number 1)
4. Substitute at least one letter with an upper-case letter.
Our password in progress could look like this:
• awa1d1nW (the last letter, w, gets capitalized)
5. Substitute at least one letter with a symbol.
Our password in progress could look like this:
• @wa1d1nW (the first letter, a, is replaced with @)
Congratulations! You’ve just created a password that’s 1.34 tresvigintillion more times, or 1.34 trillion trillion trillion trillion trillion trillion times stronger than your chance of winning the lottery.
Storing your passwords safely and conveniently
After you create the world’s best password, no matter how easy to remember it may be, you should record it somewhere, just to be safe. However, what’s the safest way to store password information? The first step in creating a password storage system that’s going to make your life easier and more secure is to consider the following:
![]() Who needs to be able to get her hands on these passwords?
Who needs to be able to get her hands on these passwords?
![]() Where do these passwords need to be accessed most often?
Where do these passwords need to be accessed most often?
• Desktop at office
• Desktop at home
• Laptop
• Mobile device
If you’re a solo entrepreneur and you only work from your desktop at home, you may be able to get away with a dedicated, locked Rolodex, but even that can cause irritating problems if you start using a smartphone or tablet device to check in with your adoring fans online and discover you need to re-enter your password.
If you’re working with a team, everybody needs a unique login so that you all can track who is saying what, and when they say it. It keeps your communication records squeaky clean. I love clarity, don’t you? (For more on building your team, see Chapter 3.)
Here are two proven password storage options:
![]() Good: Store your passwords in “the cloud.” Create a spreadsheet with your login information and encrypt it. This function is built in to Excel and some other spreadsheet programs. Setting it up on a PC depends on the version you’re using, but a good place to start is to
Good: Store your passwords in “the cloud.” Create a spreadsheet with your login information and encrypt it. This function is built in to Excel and some other spreadsheet programs. Setting it up on a PC depends on the version you’re using, but a good place to start is to
1. Start Excel and open the workbook or spreadsheet you want to encrypt.
2. Open the File menu, select Info from the tab on the left. Click Protect Workbook and then Encrypt with Password.
3. Enter your password and then re-enter it.
 Use a different password for your spreadsheet encryption than the one that you use for your computer. It’s the first password that somebody will try to get in to your password document.
Use a different password for your spreadsheet encryption than the one that you use for your computer. It’s the first password that somebody will try to get in to your password document.
4. Write down your password and save it somewhere else that’s secure.
Your passwords are now encrypted and ready to go. If you store your passwords file online via a service like Dropbox, it will be available on all devices when you need your passwords on the run. (See Figure 2-10.) Please don’t name your file “passwords,” however! Name it something meaningful to you, not something obvious to somebody snooping around.
 You will get much more secure encryption when you use the 2003 or newer version of Excel.
You will get much more secure encryption when you use the 2003 or newer version of Excel.
Figure 2-10: Drop in on Dropbox, a free service for password storage.
 Open your document with the same application you use to create it. For example, if you use MS Excel to encrypt, you want to use an MS Excel mobile version to de-encrypt it.
Open your document with the same application you use to create it. For example, if you use MS Excel to encrypt, you want to use an MS Excel mobile version to de-encrypt it.
![]() Better: Sign in via Google, Facebook, or Twitter as an “Identity Service Provider.” Don’t trust some small site like SocialNetworkingforCrossStitchers.net to adequately protect your password information. Many small social networks enable you to sign in using your login from more popular sites such as Google or Facebook. (See Figure 2-11.) Use this option whenever it’s available. These developers work 24/7 to keep your login information secure.
Better: Sign in via Google, Facebook, or Twitter as an “Identity Service Provider.” Don’t trust some small site like SocialNetworkingforCrossStitchers.net to adequately protect your password information. Many small social networks enable you to sign in using your login from more popular sites such as Google or Facebook. (See Figure 2-11.) Use this option whenever it’s available. These developers work 24/7 to keep your login information secure.
Switching your super passwords
If hackers and dishonest people would only take a vacation, you and I would not have to switch our passwords periodically. But until somebody figures out how to talk them all into taking up another avocation, I want you to assume that somebody is trying to get into your accounts and that it’s only a matter of time before they do by one means or another.
Figure 2-11: The Pinterest Identity Service Provider login.

One of those ways is by hacking their way into getting lists of e-mails and passwords. In 2012 more than 6.5 million LinkedIn accounts were compromised and had to change their passwords. I have one of those accounts and experienced lovely peace of mind because I do the following
1. Create super-safe passwords.
2. Use a unique one for each major profile and account.
3. Replace with fresh super-safe passwords periodically.

 Here’s the Top Ten Hall of Shame for commonly hacked passwords. If you’re using one of these, particularly for your bank account, I insist that you stop reading (after I show you how to create super-safe passwords, of course) and change your password to something that should help you to sleep better at night:
Here’s the Top Ten Hall of Shame for commonly hacked passwords. If you’re using one of these, particularly for your bank account, I insist that you stop reading (after I show you how to create super-safe passwords, of course) and change your password to something that should help you to sleep better at night: