There are a number of tasks that require network configuration to be completed. As the installer of the SOA Suite does not necessarily have network administrator privileges, it is a good idea to get all the tasks that require administrator privileges completed before starting the installation and configuration of the SOA Suite.
The following figure shows the hostnames associated with our cluster. Note that hostnames associated with floating IP addresses (may migrate between machines) are given in italics and all the names on the load balancer refer to virtual IP addresses.
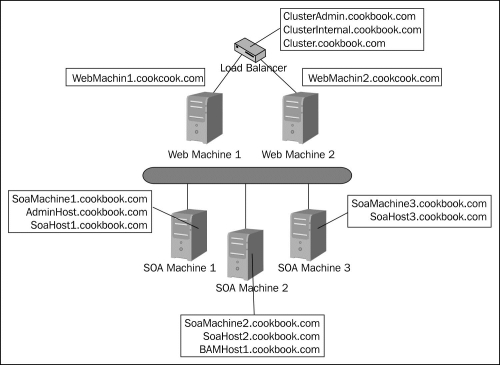
- Collect managed server hostnames and IP addresses.
The Admin server, each SOA managed server, and one of the BAM managed servers will require a unique hostname and IP address that must be routable across the cluster. These IP addresses are separate from the IP addresses of the machines hosting the managed servers. Enter the server type (Admin, SOA, or BAM) and WebLogic server name in a worksheet similar to the one shown next. The server name is the name used within WebLogic to refer to this server. Then have the network administrator complete the table by allocating hostnames and IP addresses for the servers. These hostname/IP address pairs should be put into an internal DNS.
Server type
Server name
Hostname
IP address
Admin
AdminServerAdminHost10.2.0.121SOA
WLS_SOA1SOAHost110.2.0.131SOA
WLS_SOA2SOAHost210.2.0.132SOA
WLS_SOA3SOAHost310.2.0.133BAM
WLS_BAM1BAMHost110.2.0.141 - Get frontend details for the load balancer.
The SOA Suite cluster will have at least one, and usually two or three, virtual hostnames for use by the load balancer. Create a table listing those requirements and get the network administrator to complete the hostname, port number, and protocol details.
Role
Virtual hostname
Port
Protocol
Admin access
ClusterAdmin.cookbook.com443HTTPS
Internal access
ClusterInternal.cookbook.com80HTTP
External access
Cluster.cookbook.com443HTTPS
- Configure the load balancer to listen on all the virtual hostnames and ports identified in step 2 and load balance across all the web server hostnames and ports identified in the Gathering configuration information recipe.
The load balancer is used to distribute requests across the two web servers. The web servers form a routing pool (or multiple routing pools if listening on multiple protocols). The load balancer presents a single address to SOA Suite clients to access the cluster via HTTP and HTTPS.
The web servers will be configured by the EDG to load balance across the WSM cluster using the hostnames of the physical servers running OWSM. They will distribute the load across the BAM cluster using the name of the physical servers running the BAM web interfaces and the virtual hostname of the BAM server itself. The web servers use the virtual hostnames of the SOA servers to distribute the load across the cluster. Finally, the virtual hostname of the Admin server is used to route requests to whichever physical machine is hosting the Admin server at the time of the request.
Using virtual hostnames for the SOA managed servers, the BAM server and the Admin server allows these managed servers to move across physical machines without requiring reconfiguration of the load balancers.
The node managers are dedicated to physical machines and so, like the WSM managed servers, they are able to use the physical hostname of the server on which they run.
Note that although the SOA cluster may not receive SOAP requests, the load balancer may still be required to support access to web-based portions of the SOA Suite such as human workflow, the B2B console, and the SOA composer application. If the only HTTP access to the SOA environment is to the consoles for management purposes, then it may be possible to remove the load balancer and web servers from the installation. In case that no load balancer or web servers are used, EJB clients may access the managed servers directly using a T3 protocol which supports load balancing. Similarly, adapters do not require the load balancer.
The three frontend addresses mentioned are recommended in the EDG, but it is possible to collapse the internal and external access into a single role. It is recommended to keep a separate Admin access role to reduce exposure to hacking.
Although we have shown only a single network interface for both the SOA layer and web layer machines, it is good practice to have two physical network adapters in these layers to provide physical isolation of the networks to increase security. Multiple adapters can also be used to reduce the risk of network outages impacting on the cluster.
- The Enterprise Deployment Guide, Chapter 3, Preparing the Network for an Enterprise Deployment, Section 3.4, About IPs and Virtual IPs (http://docs.oracle.com/cd/E23943_01/core.1111/e12036/net.htm)
