In this recipe, we will demonstrate how to configure Active Directory (AD) as an alternative authentication provider for WebLogic.
Ensure that you have an instance of Active Directory installed and configured and has the group administrator defined. For the purpose of following this recipe, create the demo user and add it to the Administrators group.
You will also need to have installed and configured an instance of Oracle SOA Suite running on Oracle WebLogic.
- Log in to Oracle Weblogic Server Admin Console (
http://host:port/console) with the user that has an administrator privilege, such as weblogic.Once logged in, within the Domain Structure select Security Realms; this will list the currently defined security realms.
- Next, select myrealm. This will display the settings for myrealm.
Next, click on Lock&Edit to edit the session. Then select the Providers tab, and within that, select the Authentication tab. This will list the authentication providers currently defined for myrealm.
- Click on the New button to create a new authentication provider. This will open the authentication provider configuration page.
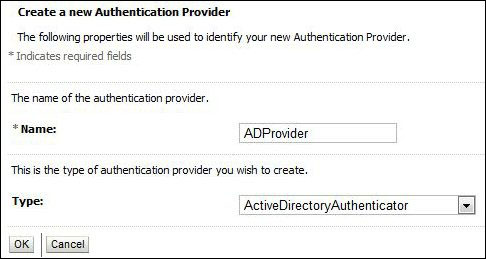
Enter a name, such as
ADProvider, and select Type as ActiveDirectoryAuthenticator as the authentication provider type and click on OK. - The authentication providers are listed in the order in which they will be called. We need to move ADProvider to the top of the list.
To do this, click on Reorder, ensure ADProvider is selected; then click on the up arrow to move it to the top of the list and then click on OK.
- Now we need to configure our ADProvider to connect to our instances of AD; select ADProvider from the authentication provider list, and click on the Configuration tab. From here, select the Provider Specific tab.
Here, we need to provide our Active Directory specific connection details, as well as the location of our users and groups within the identity store, as detailed in the following table:
Field
Description
Host
The host of the machine hosting Active Directory.
Port
The port number on which AD is listening (6501 is the default).
Principal
The Distinguished Name of the LDAP user that WebLogic server should use to connect to Active Directory.
Credential
The credential (password) used to connect Active Directory.
User Base DN
The base Distinguished Name of the tree in the
ADdirectory that contains users.Group Base DN
The base Distinguished Name of the tree in the
ADdirectory that contains groups.Next select the Common tab, and set Control Flag to SUFFICIENT and click on Save.
- Finally, we need to set Control Flag to SUFFICIENT for our default authenticator.
Select Default Authenticator from the authentication provider list, click on the Configuration tab, and then select the Common tab. From here, set Control Flag to SUFFICIENT and click on Save.
- The final step is to put our changes into effect. In the Change Center, click on Activate Changes.
Next, shutdown and restart the Oracle WebLogic Admin Server and related managed servers.
We have defined two authentication providers, the first being Active Directory authentication provider with control flag SUFFICIENT, and the second being the default authenticator defined against the embedded LDAP.
When we log in as the demo user, WebLogic will attempt to authenticate the user against AD. Assuming the password is correct the authentication will be successful and the user will be logged in to the application.
When we log in as weblogic, authentication will fail against AD, but because the OID authentication provider is defined as SUFFICIENT, WebLogic will attempt to authenticate the user against the embedded LDAP at the point at which it succeeds and the user will be logged in to the application.
