Chapter 2. Fundamental concepts in Process Integration 19
Figure 2-2 Inter-enterprise integration
Hence, the lessons learnt from traditional Enterprise Application Integration (EAI)
solutions can be applied to business-to-business (also known as Extended
Enterprise or inter-enterprise) integration. It is important to note, however, that
there would be differences in Quality of Service (QoS) concerns and commercial
considerations that are of particular significance to inter-enterprise integration.
For example, core concerns for inter-enterprise integration include security,
interoperability, and governance (defining the responsibilities of each party).
Nevertheless, we should expect that inter-enterprise solutions can leverage the
majority of the intra-enterprise concepts.
2.1.2 Summary
As integration technologies have evolved, many similarities between the
intra-enterprise and inter-enterprise integration approaches have become
apparent. It should be possible to describe a set of underlying concepts that
apply to both the areas.
2.2 Process Integration concepts and notations
In this section we introduce basic concepts and notations for capturing different
types of interactions encountered in Process Integration.
2.2.1 Collaboration and Interaction
Integration between people, process, and applications can be thought of as
collaboration and interaction between participating entities.
Collaboration
In the most general sense, a collaboration denotes N-to-N activities between
sub-systems within a distributed system. As shown in Figure 2-3, complex
collaborations between sub-systems can be broken down into more basic
interactions. An interaction focuses on 1-to-1 or 1-to-N activities originating from
a single sub-system.
Source
Application
Target
Application
Partner A Partner B

20 Broker Interactions for Intra- and Inter-enterprise
In this way, complex collaborations involving many sub-systems can be
decomposed into simpler interactions that are easier to analyze. Data analysts
use a similar approach when analyzing complex data with many-to-many
relationships. Normalization is used to reduce many-to-many relationships
between data to 1-to-many relationships.
Figure 2-3 Collaboration topologies
Note that we do not show a link from A-to-C on the right of Figure 2-3. This is
because, in breaking the interaction down, we found that A only initiates
interactions with B, D, and E. The C-to-A interaction will be modeled in another
1-to-N interaction.
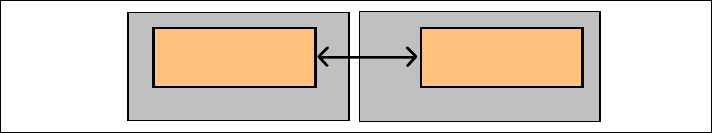
Interaction
As we just saw, an interaction is a collaboration originating from a single
component. Figure 2-4 shows an interaction between a source application and a
target application. The initiating operation is indicated by a small solid circle.
Figure 2-4 Definition of interaction
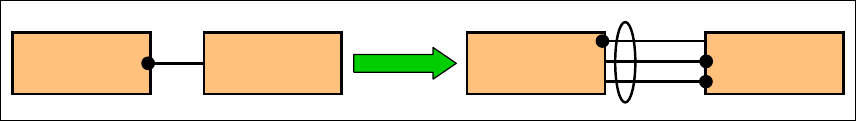
Complex interactions may be decomposed into several simpler interactions to
enhance the level of detail. An example is shown in the Figure 2-5, where a
query for a quote is decomposed in a request step, an acknowledgement step,
and a final reply step.
D
B
A
E
C
N-to-N
A
D
B
E
1-to-N
Source
Application
Target
Application
Chapter 2. Fundamental concepts in Process Integration 21
Figure 2-5 Decomposition of complex interactions
An ellipse spanning one or more basic interactions denotes a shared context
involved in a complex interaction between two or more sub-systems. Examples
of shared contexts are session, security, transaction, process control, and so
forth.
Complex interactions with multiple target applications also can be decomposed
into multiple 1-to-1 interactions, as long as there is one initiating operation within
a source application. The interaction patterns approach can then be applied to
these 1-to-1 interactions.
2.2.2 Connectors and Adapters
The terms connector and adapter are often used interchangeably. This section
defines their use in a Patterns for e-business context.
Connectors
Connectors provide the connectivity between source and target applications. A
connector is always present to facilitate interaction between two sub-systems.
Depending on the required level of detail, a connector can be:
? A primitive (or unmodelled) connector, represented by a simple line between
sub-systems
? A component (or modelled) connector, represented by a rectangle on a line
between sub-systems
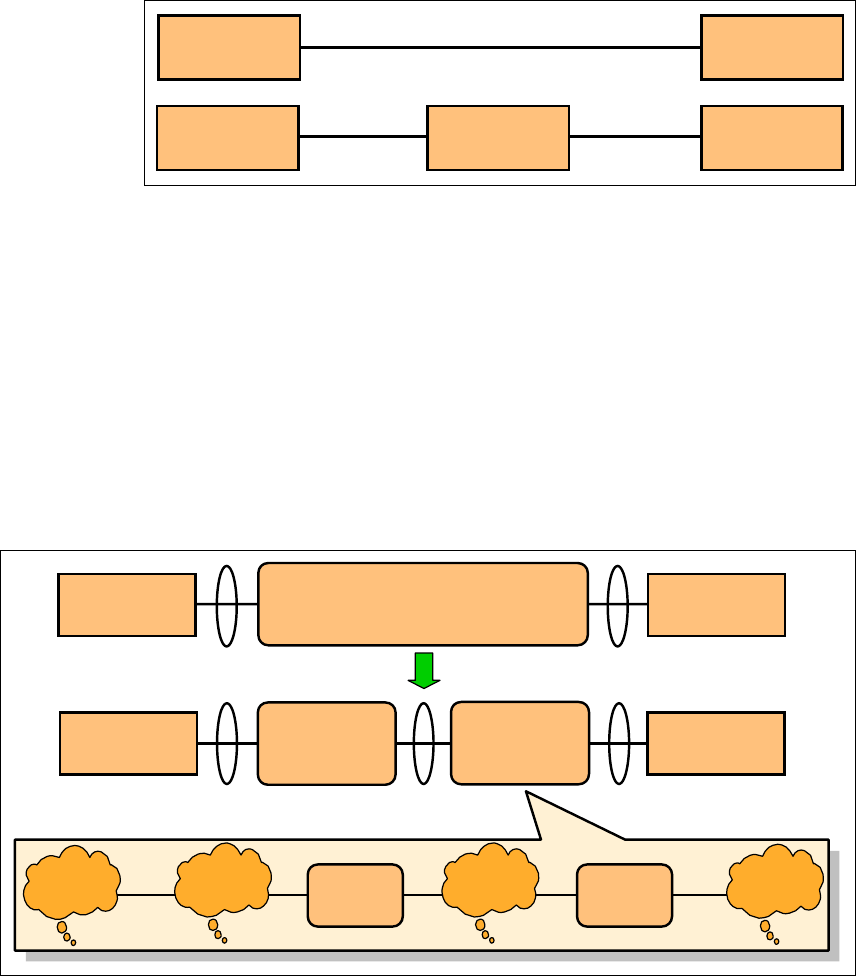
For lower-level modelling, a primitive connector can always be decomposed into
a modelled connector and two adjacent primitive connectors, as shown in
Figure 2-6. This way, connector models can be recursively decomposed until the
correct level of detail is reached.
Source
Application
Source
Application
Target
Application
Req
Ack
Quote
Source
Application
22 Broker Interactions for Intra- and Inter-enterprise
Figure 2-6 Decomposition of connectors
It is useful to distinguish two connector subtypes, as shown in Figure 2-7:
? An
adapter connector is concerned with enabling logical connectivity by
bridging the gap between the context schema and protocols used by the
Source application (S type) and Target application (T type).
? A
path connector is concerned with providing physical connectivity between
Source and Target applications. It may be very complex (for example, the
Internet) or very simple (an area of shared storage).
These connector subtypes are orthogonal, meaning a connector may be both an
adapter connector and a path connector. The relationship between connectors
and adapters is shown in Figure 2-7.
Figure 2-7 Relationship between connectors and adapters
<Connector>
Source
Application
<Connector>
<Connector>
Target
Application
Target
Application
Modeled
Connector
Source
Application
T typeS type
S type T type
Source
Application
Target
Application
Connector
Source
Application
Target
Application
Firewall Firewall
Adapter
Connector
Path
Connector
T type
Dept LAN
Org WAN Internet
DMZ LAN
Chapter 2. Fundamental concepts in Process Integration 23
Adapters
Adapters provide the logical connectivity to an application. Without adapters,
each application would need to implement the specific interface of the target
application.
It is useful to distinguish three types of adapters:
? Control adapters are not concerned with content. They are only concerned
with the activities involved in flow operations:
– Transforming the protocol used between the segments
– Segmenting, batching, and sorting data blocks
– Correctly interacting with the path connector to execute the transport
operation (This includes respecting the protocol rules.)
? View adapters are concerned with transforming content but only in terms of its
technical representation. Examples include:
– Element demarcation schemes, such as delimited, fixed-length, and XML
– Element sequencing schemes, such as keys and collation sequences
– Element encoding schemes, such as character set, number format, and
date format
? Model adapters transform the semantic content and normally require
business input to define correct operational rules. Some examples are:
– Splitting out subsets of data
– Joining external data (augmentation/enrichment)
– Summarization
– Translation of identifiers (key management)
Coupling adapter connectors
Coupling adapter connectors can be used to implement a common integration
protocol such as messaging, RMI/IIOP, SOAP/HTTP, and so on. As shown in
Figure 2-8, the adapter functionality between the source application and the
target application is decomposed into two halves. Each half adapts to and from a
common intermediate protocol.
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
