In simple terms, the cross-site scripting attack allows the attacker to execute malicious JavaScript in another user's browser. The malicious script is delivered to the client via the website that is vulnerable to XSS. On the client, the web browser sees the scripts as a legitimate part of the website and executes it. When it runs in the victim's browser, the script can force the browser to perform actions similar to the ones done by the user could do. The script can also make the browser execute fraudulent transactions, steal cookies, or redirect the browser to another website.
An XSS attack typically involves the following participants:
- The attacker who is executing the attack
- The vulnerable web application
- The victim using a web browser
- A third-party website to which the attacker wants to redirect the browser or attack through the victim
Let's look at an example of an attacker executing a XSS attack:
- The attacker first tests the various input fields for the XSS flaw using legitimate data. Input fields that reflect the data back to the browser could be candidate for a XSS flaw. An example is shown in the following screenshot; the website passes the input using the
GETmethod and displays it back to the browser: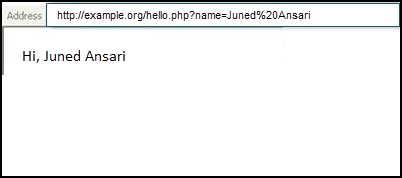
- Once the attacker finds a parameter to inject on which insufficient input validation is done, they will have to devise a way to deliver the malicious URL containing the JavaScript to the victim. The attacker could use an e-mail as a delivery mechanism, or entice the victim into viewing the e-mail by using a phishing attack.
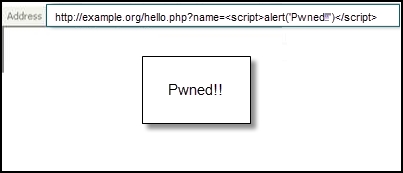
- The e-mail would contain a URL to the vulnerable web application along with the injected JavaScript. When the victim clicks on it, the browser parses the URL and also sends the JavaScript to the website. The input in the form of JavaScript is reflected to browser. As an example, I am using a benign JavaScript:
<script>alert('Pwned!!')</script>.The complete URL is as follows:
http://example.org/hello.php?name=<script>alert('Pwned!!')</script> - The
alertmethod is often used for demonstration purpose and to test if the application is vulnerable. In the later section of the chapter, we would explore other JavaScript methods that attackers often use. - If the web application is vulnerable, a dialog box will pop up on the victim's browser, as shown in the following screenshot:
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
