QARK (short for Quick Android Review Kit) is another interesting tool. This is a command line tool and performs static analysis of Android apps by decompiling the APK files using various tools and then analyzing the source code for specific patterns.
QARK has been developed by LinkedIn's in house security team and can be downloaded from the following link:
https://github.com/linkedin/qarkInstructions to setup QARK have been shown in Chapter 1, Setting Up the Lab. Let's see how QARK can be used to perform static analysis of Android apps.
QARK works in the following modes:
- Interactive mode
- Seamless mode
We can launch the QARK tool in interactive mode using the following command:
python qark.py
Running the previous command will launch QARK in interactive mode as shown in the following figure:
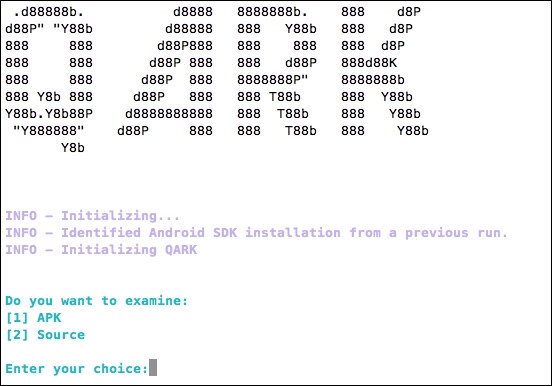
As we can see in the preceding figure, we can use QARK to analyze the APK files as well as the source code. Let's go with the APK file by choosing 1 and then we need to select the path of the APK file as shown in the following screenshot:
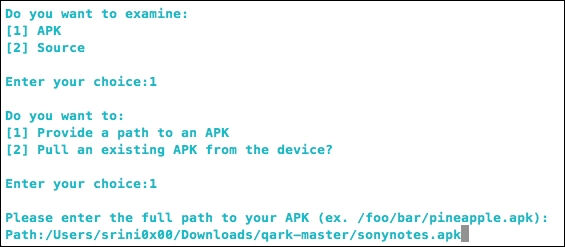
The previous screenshot shows the path of the Sony notes app that we have seen earlier. Hit Enter and follow the onscreen instructions to begin analyzing the application.
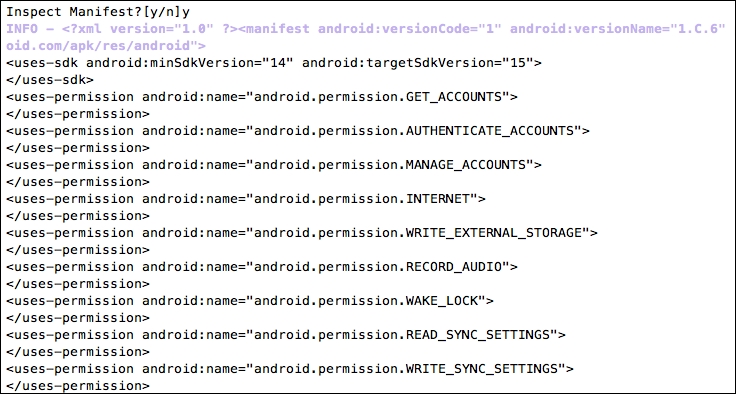
The following figure shows the AndroidManifest.xml file that QARK has retrieved from the target application:
The following screenshot shows the static analysis process being done by QARK:
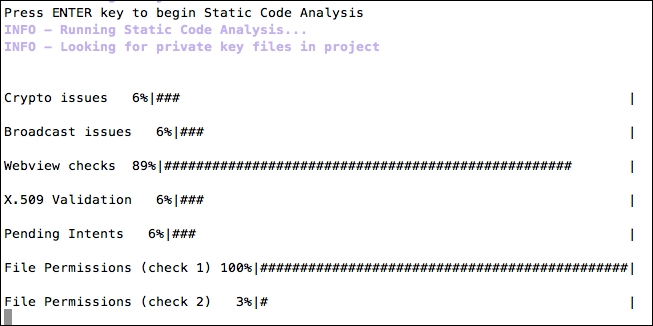
Once QARK completes its analysis, it will generate the report in a folder called output within QARK's directory. If you wish to create a POC, QARK will also create a POC application for demonstrating how to exploit the vulnerabilities reported.
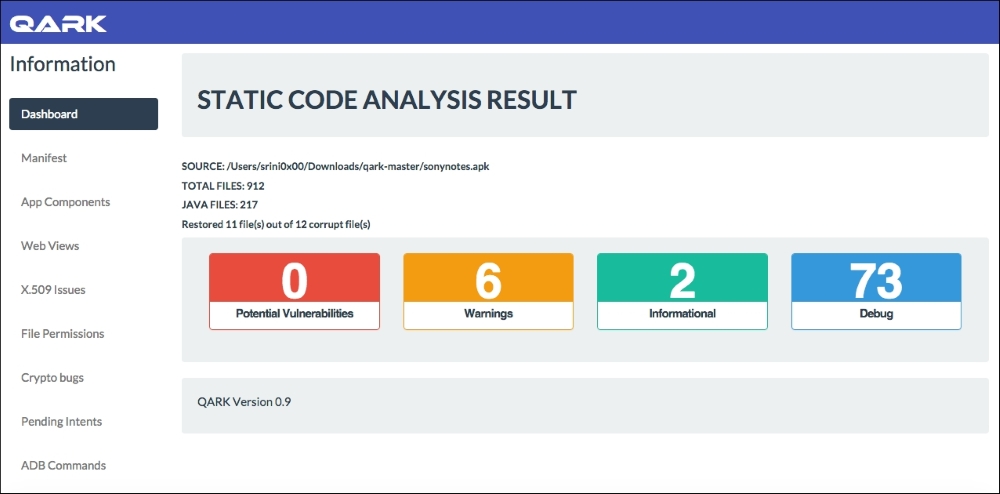
We can look into the details of each vulnerability reported by clicking on the tabs available in the left hand side of the page.
As already mentioned, QARK can also be run in the seamless mode where user intervention is not required.
python qark.py --source 1 --pathtoapk ../testapp.apk --exploit 0 --install 0
The previous command gives the same effect of what we have seen in the interactive mode.
Lets go through the explanation of the previous command.
--source 1represents that we are using APK file as input--pathtoapkis to specify the input APK file--exploit 0tells QARK not to create a POC APK file--install 0tells QARK not to install the POC file on a device
