Supplementing Group Policy on Windows Desktops
“Another area of concern is that a user with local administrative privileges can install any application they wish on their desktop. This includes hack tools, virus-ridden applications, vulnerable applications, and non-licensed applications.”
—Derek Melber, MSCE MVP and Author
In spite of an increasingly mobile workforce working flexible hours, the image of a “desktop” sitting on a Formica, faux cedar wood bureau, or workstation in a cubicle persists. But as we know full well, a desktop is not a machine required to be in a fixed location anymore. With technology what it is, that term is synonymous for a person (wherever they may be) that has access and is using Microsoft Windows.
Indeed, people are known to behave differently inside and outside of the office, where the cultures are different. Lines between professional and home life become blurred. People take the suit off at home and log in in their shorts, but that doesn't mean they should take their corporate hat off, as well. But what is the answer? Eliminating administrator rights without allowing for the elevation of certain job-necessary privileges is not the answer. Locking down a system is like asking everyone to raise his or her hand to go to the bathroom—it shows the downside of mistrusting human nature.
Trust is not a value that can be applied in a fixed dose; it has to be measured to meet the needs of the individual's role. Trust is a medicine that has to be applied carefully in prescribed doses based on role, policy, and circumstance. Just as you shouldn't gulp down an entire prescription when leaving the pharmacy assuming it will cure the problem in one go, you also can't just apply blanket privileges to users throughout your organization and expect that to solve your potential insider breach problem.
If you've read the marketing propaganda delivered by most operating system vendors, you have seen that they would like you to believe that their latest version will solve every problem known to exist just short of world hunger and world peace. It therefore behooves you to be aware of many glaring gaps that Windows exposes in privileged identity management (PIM).
Six Things You Should Know Before Migrating to MS Windows 7
Microsoft has done a great deal of exceptional work in improving Windows 7 over its predecessor, Windows Vista. Despite this improvement, glaring gaps in PIM still abound, requiring the security-conscious enterprise to consider Independent Software Vendors (ISVs) to eliminate desktop admin rights. The six things you should know before migrating to Windows 7 include:
- User Access Control (UAC) Security Vulnerability: This exists when a user is logged in as protected administrator, in which case the default is to not notify users when changes are made to Windows settings, allowing users to “silently” elevate certain actions potentially leading to the introduction of malware.
- Registry and File System Virtualization Vulnerability: Applications can write data into a virtual store, whereby other applications that need to use that data will no longer be able to access it.
- Application Compatibility Toolkit (ACT) Limitations: ACT can tell you what applications require admin rights, but can do nothing to elevate rights for use of the applications.
- Virtualization (Med-V & App-V) Vulnerability: Removing admin rights to a user on a PC but allowing them to open a window with admin rights to run a specific application for compatibility purposes will result in opening a security hole on that PC.
- AppLocker Limitations: Requires the administrator to explicitly list every “legal” application, thus controlling what applications a user can use, but still requires admin rights at the user level if that application so requires.
- RunAs Administrator Vulnerability: Only forces a UAC prompt when an application runs but doesn't elevate the rights for the user.
Things You Should Know About MS UAC
Microsoft (UAC) has been touted as the next great thing in desktop security, but does it really satisfy all you need in order to ensure security, compliance, and productivity? The things you should know about UAC include:
- For standard users, UAC is simply a RunAs operation. When prompted with UAC, a standard user is asked for credentials for an administrator account. When these credentials are entered, the application will run under that account and will no longer be able to access remote resources or save data to the correct profile.
- Microsoft does not offer logging or reporting for UAC. Auditing the use of UAC to discover what a user is doing with elevated privileges is a critical part of protecting the computer from unauthorized malware and malicious use.
- UAC has a security vulnerability in Windows 7 for users who log in as protected administrators. This vulnerability can only be mitigated if the user changes the UAC setting to its most secure level, which is the level used in Windows Vista. Alternatively, the vulnerability can be eliminated by removing administrator rights from the user.
- UAC dialogs cannot be supplemented with corporate legal text or customized warnings.
UAC has undergone a makeover from its debut in Windows Vista. Microsoft has reduced the number of prompts that UAC presents when a user is logged in to Windows. Microsoft implemented UAC to help prevent unauthorized changes to the operating system. UAC is designed to prompt a user when a task is performed in Windows that requires administrative privileges. For users who are logged in as a protected administrator, the prompt simply asks for consent.
If the protected administrator selects, yes, then the operation is allowed to continue with elevated privileges. The reason the user is called a “protected administrator is because he is actually operating with two tokens—one is a standard user token, the other is an administrator token. All tasks that the user performs are done as a standard user, until the user answers yes to a UAC dialog; once this happens, the user switches to an administrator token, and the task is elevated to administrator status.
Microsoft and security experts all agree that users should avoid operating as an administrator, with a full administrator token all the time, because it leaves the operating system extremely vulnerable to various security problems, including malware and malicious use.
With UAC, the user is notified whenever they elevate themselves to administrator for specific tasks to warn them of the potential for harm. The problem with this approach in corporate environments is that this strategy leaves the security decision up to the end user, which as we have said before, cannot be expected to be a saint or to be competent all of the time. Therefore, it is best to avoid configuring users as protected administrators, and make sure they are configured as standard users. Standard users have a different experience with UAC—instead of a simple prompt for consent, they are asked for a password for an administrative user.
If the standard user has the password for an administrator account, the process or application would run successfully. However, it would be running under a different account, without the security context of the actual end user. Essentially, this is an enhanced RunAs operation. Further, it only works if the user has an administrator password, or if someone else enters the administrator password for the user (over-the-shoulder credentials). Giving users administrator passwords will just lead to abuse, and over-the-shoulder credentials will only increase the load on the help desk.
Since the introduction of Windows Vista, organizations have been asking Microsoft to provide a way to manage a list of applications that would automatically elevate themselves and bypass the UAC prompts. Here is Microsoft's response to this request. According to Mark Russinovich, Technical Fellow at Microsoft; Inside Windows 7 User Account Control on technet.microsoft.com: “End users have been asking for Windows to provide a way to add arbitrary applications to the auto-elevate list since the Windows Vista beta... Windows 7, just like Windows Vista, doesn't provide such a capability.”
Things You Should Know About MS AppLocker
AppLocker is a new and exciting technology in Windows 7 that can drastically improve desktop security in some organizations. AppLocker allows administrators to create a whitelist of all approved applications that are allowed to run on a computer; any other applications or executables would not be allowed to run. On the surface, this appears to be the security silver bullet; however, there are some things to be aware of when looking to AppLocker to help improve your security.
For example, if any of the applications that are on the AppLocker whitelist require administrator privileges, the user will need to be configured as a local administrator or they will, at the very least, still need an administrator password to answer UAC prompts. AppLocker cannot automatically elevate applications that are on the whitelist. If the user is configured as a local administrator, or has a local administrator password, it is easy to circumvent the controls that AppLocker provides.
The easiest way to circumvent the controls is by booting in Safe Mode and disabling the AppID Service. Because the user is an administrator, he would have full control to do this. Thus, removing administrator privileges from the user is critical in preventing the malicious user from circumventing these controls. If the user is not an administrator, AppLocker becomes much more effective, but organizations still need to find a way to deal with the applications that are on the whitelist that require administrator privileges.
There is also the question of the management of the whitelist. In smaller organizations that have relatively static environments, the combination of AppLocker and eliminating administrative rights is viable. Unfortunately, the whitelist scales with the size of the organization. As the company gets bigger, the whitelist gets bigger, and can become completely unmanageable very quickly. In larger organizations, it becomes nearly impossible to quickly react to users who need new applications placed on the whitelist.
When organizations choose to forgo the implementation of AppLocker for whitelisting, removing administrator privileges becomes even more important. Most applications require administrator privileges to install, and if organizations wish to prevent unknown applications from entering the environment, removing administrator privileges can add significant value.
Microsoft AppLocker has also been touted as the next best thing in desktop security (in addition to UAC), but does it really satisfy all you need in order to ensure security, compliance, and productivity? The things you should know about AppLocker include:
- AppLocker cannot elevate privileges for processes. It is designed to block or allow the execution of explicitly listed applications only.
- AppLocker does not allow organizations to remove administrator privileges. If you have applications that require administrator privileges, and those applications are on the AppLocker whitelist, the users will need to be configured as administrators.
- In order to make AppLocker secure, you must also remove admin rights from end users. If users are administrators, they can easily circumvent AppLocker policies and even disable the AppLocker service.
- AppLocker does not prevent users from accessing protected areas of the file system. If a user is an administrator and AppLocker is delivering a whitelist to the machine, the user can still modify critical areas of the file system.
- Managing an AppLocker whitelist can be difficult and cumbersome. This may not be suitable for large organizations with thousands of line-of-business applications.
Top Ten Reasons to Implement Least Privilege on Windows Desktops
Taking a more tongue-in-cheek approach to highlighting the types of privilege misuse that occurs daily inside most organizations, we thought that a top-ten list approach might appeal to you as well. How many of these have you seen throughout your organization?
#10—Sally in Sales will stop calling the help desk (at $30/call) every time she needs to change the system clock because she traveled to a different time zone and has standard user privileges.
#9—Andy the Auditor can get a full report of who has what entitlements instantly to satisfy compliance successfully, instead of taking weeks of manual effort.
#8—Ted in Tech Support won't have to drop everything to add a print driver to someone's PC if corporate policy actually permits them to do it themselves.
#7—Sid in Development won't be able to download potentially hazardous software onto his PC that in turn could infect the entire corporate network.
#6—Fiona the Secretary won't damage her PC configuration while trying to upgrade an application by accidentally “fat fingering” the wrong IP address.
#5—Bob, the VP of Marketing, won't crater the nightly backups by loading 120GB of music from his iTunes onto his corporate laptop.
#4—Alice in Human Resources will no longer be able to copy and sell private personnel data to supplement her income without the auditors being aware of her activities.
#3—Fred in IT won't be able to install a Trojan on the mission-critical server, bringing it down for four hours and costing the company over $1M in lost transactions, because he was passed over for a big promotion.
#2—Jack in Operations will no longer be permitted to download Active-X controls from online gaming web sites and spend hours of company time knocking over liquor stores in Grand Theft Auto.
#1—Charles Xavier III, the CEO, won't have the ability to screw up his laptop configuration accidently, indirectly, or even intentionally without a full event log being generated for audit, remediation, or recovery.
The “Do-Nothing” Approach
Daren Mar-Elia, Microsoft Group Policy MVP and founder of gpoguy.com and sdmsoftware.com, talks about organizations that try to get away without doing anything and hoping the problem never manifests. “I call this the bury-your-head-in-the-sand strategy. This is clearly one way to address a problem—by not addressing it. I still see a surprisingly large number of IT shops that take it for granted that their users run as administrators on their desktops. If they haven't yet had problems with malware or users wiping out their own systems, they will. Some shops will try to justify it by saying, ‘well we have a lot of developers and they need to be administrators’.”
Developers are indeed a challenge, but we would also argue they are a big risk group because they tend to download anything and everything from the Internet. Suffice it to say that we do not believe the Do-Nothing approach is sustainable in the long run. If Windows 7 and UAC aren't forcing you to address this problem head-on, then sooner or later you will need to confront it. If you need business justification to go to management to make the case for this, try some of these:
- Better security on your desktops and within your organization. If your company is even mildly regulated by a government organization, I can't imagine how you can get away with this for long. It's a PR nightmare waiting to happen!
- Lower Total Cost of Ownership (TCO) around managing your desktops as a result of less user futzing.
- More reliable end-user experience since installing untested, non-standard software and making user-driven tweaks can seriously impact desktop reliability.
Impact on the Help Desk
What's interesting here is that without exception, IT admins and help desk personnel, in organizations of all sizes, say they spend more than 1/4 of their time fixing problems caused by over-privileged users. In fact, in our conversations with organizations throughout the world, the average amount of time spent fixing these problems was 29% of all activities they are required to do. That means almost a third of their time is spent fixing problems, whether they be accidental errors (the so-called fat-fingered key stroke) or unintended errors, whereby simple actions such as downloading apps from the internet leaves the desktop susceptible to malware that can assume the user's administrator rights and use them to access the whole network.
According the Gartner, Inc.'s report, The Cost of Removing Administrative Rights for the Wrong Users (T. Cosgrove/April 2011), the primary difference between the two management profiles, “moderately managed” and “locked and well-managed,” is user rights. The moderately managed profile assumes administrative rights are granted, while the locked and well-managed profile has them removed. The cost difference between the two profiles is $653 annually. Interestingly, 90% of the cost savings associated with the locked-down user is realized by the user, not IT. The user will spend less time fixing his or her system and doing other administrative tasks, because the PC is better managed.
They'd much prefer to be doing other things. Indeed, an overwhelming 90% of all our respondents to a survey of over 200 IT admins said they'd much rather automate the process of elevating privileges, and use the money they would save on either training staff or upgrading software. In essence, the experience of IT administrators and help desk operatives are legion; they want to spend more time improving user experience, with better training and software, and less time fighting fires (see Figure 4-1).
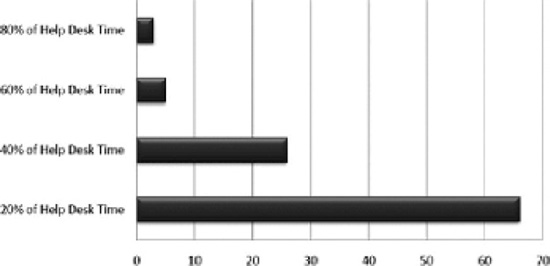
Figure 4-1. Most effective use of automated elevation of privileges
Fortunately, the fault is not the legacy applications. Businesses need not give up the applications they need to run business as usual. The fault is the lack of awareness of just how easy it is to automate the elevation of privilege user access at a granular level, based on the role definition of each employee. But let's not also forget that Windows itself can be a legacy app—as developers will have developed legacy apps based on older versions of Windows—at a time when knowledge of insider threat is great, and also the way MS vulnerabilities provide a back-door key to the network.
Microsoft Published Vulnerabilities
Microsoft and its partners regularly identify new security vulnerabilities in Microsoft software. In 2010, Microsoft published over 100 security bulletins documenting and providing patches for 256 vulnerabilities. In April 2011, BeyondTrust examined and analyzed all of the published Microsoft vulnerabilities in 2010 and all of the published Windows 7 vulnerabilities to date, allowing this report to accurately quantify the continued effectiveness of removing administrator rights at mitigating vulnerabilities in Microsoft software.
Key findings from this report show that removing administrator rights will better protect companies against the exploitation of:
- 75% of critical Windows 7 vulnerabilities reported by Microsoft to date
- 100% of Microsoft Office vulnerabilities reported in 2010
- 100% of Internet Explorer and IE 8 vulnerabilities reported in 2010
- 64% of all Microsoft vulnerabilities reported in 2010
Microsoft is to be lauded for releasing patches to known vulnerabilities each month. Vulnerabilities, however, take time to identify. Patches can take even longer to apply. During this down period, threats can damage a corporate network and gain access to sensitive information. A PIM solution that eliminates administrator rights from desktop users will substantially reduce the severity and/or prevent the exploitation of undiscovered or unpatched vulnerabilities. Enterprises should ensure that while administrative rights are removed to protect desktops from these vulnerabilities, users can also continue to operate effectively and with access to required applications.
The Wild West
Whenever we hear the phrase “Wild West,” the first words that come to mind are old, insecure, and vulnerable. Any old western featuring Clint Eastwood or John Wayne depicts all of these descriptions.
And coincidentally, “Wild West” provides the perfect analogy for the way an enterprise's remaining legacy infrastructure interfaces with a Windows desktop environment. Though often overlooked, every IT administrator must face the challenge of managing legacy applications that simply will not run unless individual desktops are configured for administrator access. This remains a challenge in an enterprise Windows desktop environment, whether a company has 100 or 10,000 seats.
As we have detailed elsewhere, currently there are two options available to administrators:
- Option 1: Adopt best practice of removing administrative rights. Result: Overwhelms help desk with support calls and hampers productivity.
- Option 2: Grant users administrative privileges. Result: Can provide access points for malware, hackers, insider threats, and the less reported though still equally damaging fat-fingered unintentional error.
However, what has not been clear until now is that IT administrators and help desk operatives who choose Option 2 for the sake of productivity, and thus leave their desktop environment unnecessarily exposed, are not being cavalier or necessarily neglectful. The fact is they are left with no other choice because without their legacy applications running efficiently, productivity would come to a halt.
Survey Results Validate Problem
The conclusions of our recent survey of 185 IT administrators and help desk operatives who are collectively responsible for over 250,000 individual Windows desktops in Europe, the Middle East, Africa, and North America, which BeyondTrust published in May 2011 in a report titled Legacy Applications and Least Privilege Access Management, validate this problem. The results were revealing:
- Looking closer at the data, we found that in larger organizations with more than 2,500 active desktops, it was in-house custom applications (51% of respondents) and a range of ‘other legacy apps’ (40%) that force IT admins to elevate privileges to administrator or super user status.
- However, in organizations with fewer than 2,500 active desktops, it was the popular payroll software suite, Intuit QuickBooks (33% of respondents), and again ‘other legacy apps’ (50%), which most often forced IT administrators to elevate network access privileges to the more risky administrator or super user status.
- Survey respondents were invited to name which legacy app they were nominating when selecting Other, resulting in over 50 different apps nominated, with a number of respondents citing “too many to mention.”
- This offers a revealing insight into the state of desktops today; namely, they are littered with applications, each requiring different configuration settings for different users, making effective access management practically impossible.
What we can conclude from this is that while the legacy apps may be different, the experience of all IT administrators and help desk operatives is uniform. Legacy applications make their lives difficult and consume a disproportionate amount of their time, regardless of the size of the organization.
This points to the ubiquity of Windows and its inherent problems in elevating privileged access based on company policy rather than the requirements of individual applications.
Perhaps the most revealing insight from our survey was that while we knew such legacy apps as Sage and QuickBooks caused problems for IT admins with over-privileged users, we hadn't anticipated just how many others there were. The types of legacy applications survey respondents identified ranged from the understandable to the completely absurd (company doesn't need it to run its business, and would violate compliance requirements if found with it.) and revealed over 50 different applications
Notable examples include:
- Old mainframe applications
- Software used for running an office (printer drivers) or the desktop itself (defragmenter)
- Third-party point-of-sale software provided to retailers
- Adobe and Flash software
- Technical applications, often used only by a handful of employees in oil, automotive, and chemical organizations, that still require the entire desktop to be set to administrator or super user status
- Applications downloaded by individual employees from the Web to help them do their job better, such as financial trading software, for example
- Applications downloaded and installed by employees for their own entertainment, such as iPhone applications, and in one instance, a Golf Course Game Application
Indeed, this paints a revealing picture of enterprise desktop environments today: they are littered with applications, each of which requires different configuration settings for different users, and makes effective access management practically impossible.
Not surprisingly, many respondents said they had too many legacy applications to mention. Indeed, is it any wonder that today's IT admins consider desktops the “Wild West,” not just because of the overwhelm of managing access to multiple applications, but also because they never know what they're going to encounter on a user's workstation. One desktop manager reported: “We have limited control on what the end user can install and change on a desktop, and in many cases we have limited awareness of changes being made. In most cases, it's too late if a user installs malware and adware, leaving our desktop resources left fire-fighting problems.”
Legacy applications architected before the concept of fine-graned privilege access can't be blamed in a wholesale manner for this problem though. Organizations need these applications to run business as usual, so implementing a least privilege solution is the best way to stem the requirement to completely rearchitect these applications.
Least Privilege, Architecturally Speaking
We've talked about least privilege throughout this book, but why should a desktop user care? Ultimately, a user needs admin rights on the desktop to:
- Run system tasks
- Install software (even active X controls from the Web)
- Run existing applications built to require admin privileges
An effective least privilege solution implemented for desktops will transparently plug into Active Directory and Group Policy in order to manage the elevation of privileges based on role and policy. This is what is called least privilege because you get the minimum amount of privilege in order to do a specific task only when it is needed. If the user has no privilege, then every attempt to do these tasks will be met with a UAC prompt asking for more privilege; if the user already has admin rights, then they are at risk for intentional, accidental, or indirect damage to their data (see Figure 4-2).
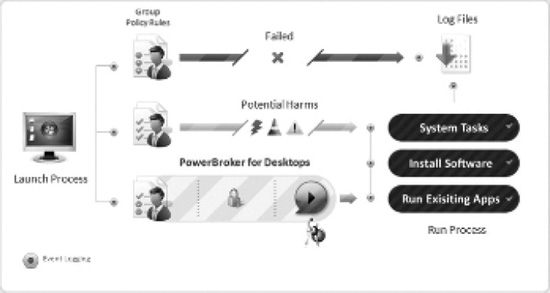
Figure 4-2. Architecture of least privilege.
Putting Least Privilege into Practice
Sometimes the best way to understand a conept as complex as least privilege for desktops is to examine a couple of real-word examples. Let's take a look at what one healthacare company and one university did to eliminate desktop admin rights and implement a least privilege solution.
Desktop Least Privilege in Production
Quintiles Transnational is a company that helps improve healthcare worldwide by providing a broad range of professional services, information, and partnering solutions to the pharmaceutical, biotechnology, and healthcare industries. Headquartered near Research Triangle Park, North Carolina, and with offices in more than 40 countries, Quintiles is a leading global pharmaceutical services organization and a member of the Fortune 1000.
As far as their IT environment goes, Quintiles Transnational manages over 13,000 end-user computers. The company wanted to remove the local administrative privileges from all their end-user accounts and run a least privilege user environment. The goal was to prevent employees from performing installations on their own, as well as running whatever software and applications they wanted. Unfortunately, Quintiles had a difficult time identifying a workaround that would allow applications requiring administrator privileges to run without the significant workload of writing custom install scripts or frequently visiting individual desktops to install software.
With Windows Active Directory installed and 13,000 computers running Windows XP, their least privilege solution was the perfect fit for the issues facing Quintiles. Security, compliance, and productivity were at the forefront of the company's needs, and this solution would enable them to create the least privilege environment they required while increasing end-user productivity. Quintiles continues to use it to elevate the permission level for the users who need to run authorized third-party applications, in addition to homegrown software, that require higher privileges than those to which the user is normally entitled.
Unpredictable Environments
Ian Short, Applications Infrastructure Manager for the University of Winchester, is part of the IT management team responsible for the operation of the IT environment across the university campus. The university predominantly runs a Microsoft site. All of the backend servers run Windows Server 2003 and 2008 within an Active Directory domain. Ian's department also supports over 1,500 Windows desktops on campus (all running Windows XP) that include over 7,000 user accounts. Many of these desktops include laptops used by remote employees in various locations. In addition, Ian and his team are responsible for 120+ applications, with a number of extra locally installed applications.
The challenge of managing user privileges in an environment full of students is complicated enough, but the dilemma only increases when you account for required applications. The team universally understood that they needed to eliminate administrator rights in order to decrease malware attacks and increase security. However, they also knew they couldn't lock down the entire network because of the 120+ applications they manage. “It became clear that in our environment something needed to be done,” said Ian. “We were noticing a worrying growth in security risks and so managing user access became a priority.”
With a least privilege solution, the University of Winchester has completely removed administrator rights among their users, while simultaneously providing adequate rights to perform the tasks that students and staff need. Some of the key uses include elevating privileges for 8 multimedia packages in their multimedia center, 24 applications on their desktops, and around half a dozen Windows functions, significantly decreasing the amount of time Ian and his team spend on support issues, which has significantly reduced cost as well.
Weighing In
Personal computers have proliferated beyond just the desktop, and with that has come an incredible management challenge. We've seen how too much privilege can potentially cause intentional accidental and/or indirect harm to the local data and possibly surrounding network. We've also discussed how too little privilege can cause sever help desk costs and declines in personal productivity. A least privilege solution is the only way to map personal privileges delegated by policy for compliance and governance satisfaction. But let's see what our insider heroes have to say
Secure Sam:
Least privilege, as we've talked about in this book before, is a simple and innately fundamental concept. It transcends every platform, making IT infrastructures secure in servers, databases, and desktops alike. In Windows desktops, least privilege makes particular sense as so many things can go wrong when users run with administrator rights. Too many times, however, least privilege is thought to be too complicated, and it gets ignored, brushed aside, or justified away. The reality of the situation is that this concept of allowing users to only access the IT resources that they absolutely need is worth whatever complications may arise. Especially on Windows desktops. Microsoft is constantly on the hunt for vulnerabilities to patch in their software, but the fact that there were over 250 in 2010 makes any additional security measures worth it in my eyes. When you take into account that removing administrator rights (or in other words, taking users to a least privilege model) mitigates the majority of Microsoft exploitations, the question shifts from “do I have to? It's so complicated!” to “how long does it take to get least privilege implemented.” And rightly so—with 75% of critical Windows vulnerabilities and 100% of Microsoft Office vulnerabilities fixed by running users in standard user mode, IT decision makers are bypassing a significant amount of potentially devastating exploitations.
Least Privilege Lucy:
When weighing in on the principle of least privilege on Windows desktops, I can't help but focus on the impact such an effort has on the help desk. The help desk tends, in some cases, to be an expensive fix for problems that have no business existing at all. Users that have access to administrator privileges are scary because of all the ways those privileges can create gaping holes in an enterprises' security program. Whether it's if someone hijacks those credentials and steals information, or malware is unintentionally downloaded onto the desktop, or even if software was accidentally downloaded—these things all create messes that require the help desk to amend. It's an expensive way to handle the consequences of letting users run with whatever privileges are most convenient.
Compliance Carl:
The concept of trust with regard to an IT environment is kind of a strange thing. On the one hand, you can't base administrative rights on trust. On the other hand, you have to. While that may seem contradictory, the kind of trust I'm talking about is different in both cases. When someone is hired, an IT administrator can't just trust that he deserves a user account with admin privileges because HR performed a background check. Yes, he passed… but so what? The point is that trust as an emotion is useless in any IT environment. The kind of trust that does hold merit in your organization is a different kind of trust entirely… one that is founded in something bigger than emotion. The kind I was referring to in the second instance is the trust that comes carefully through policies, roles, and circumstances. It's the kind of trust that allows you to have administrator rights because you require them, not because I think you should have them. With the second kind of trust also must come follow-up. Monitoring privileges is a necessary part of trusting employees with them. Everyone must be accountable, and transparent insights into all activities while using those rights is a way for that trust to be further solidified. Roles must be continually evaluated, and adjustments must be made in order for least privilege to work on desktops.

