When we visit the site of the identified IP address, we see that it is the Damn Vulnerable Web Application (DVWA). We also see that it has appended the details of the default landing page to our initial request. This means that we start from the http://192.168.195.145/dvwa/login.php site as shown in the following screenshot:

We now have a starting location to test from, and using these details, we can look for hidden directories and files. Let's modify our last script to automatically look for hidden files or directories.
The best way to do this is to start within the base directory of the site we are in. You can go up levels, but in environments where multiple websites are housed, you may end up jumping out of the scope. So, know your environment before proceeding to attack in that manner. As you can see, the script runs through a file of directories and filenames, which appends them to the target site. We are then reported whether they were valid or not:
#!/usr/bin/env python
import urllib2, argparse, sys
defhost_test(filename, host):
file = "headrequests.log"
bufsize = 0
e = open(file, 'a', bufsize)
print("[*] Reading file %s") % (file)
with open(filename) as f:
locations = f.readlines()
for item in locations:
target = host + "/" + item
try:
request = urllib2.Request(target)
request.get_method = lambda : 'GET'
response = urllib2.urlopen(request)
except:
print("[-] %s is invalid") % (str(target.rstrip('
')))
response = None
if response != None:
print("[+] %s is valid") % (str(target.rstrip('
')))
details = response.info()
e.write(str(details))
e.close()Knowing this, we can load up four of the most common hidden or unlinked locations that websites house. These are admin, dashboard, robots.txt, and config. Using this data, when we run the script, we identify two viable locations, as shown in the following screenshot. Robots.txt is good, but config usually means we can find usernames and passwords if the permissions are incorrect or if the file is not in use by the web server.

As you can see here, we get a listing of the directory's contents:
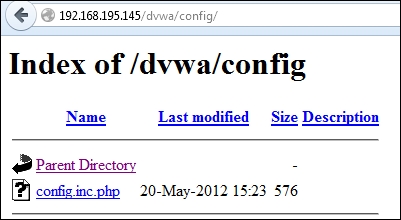
Unfortunately, when you open the config.inc.php file, as shown in this screenshot, nothing is displayed:
Administrators and support personnel do not always understand the impact of some of their actions. When backups are made from config files, if they are not actively being used, or if the permissions are not correctly set, you can often read them through a browser. A backup file on a Linux system is denoted by a trailing ~. We know that it is a Linux system because of the previous HEAD request, which showed that it was an Ubuntu host.
As you can see in the following screenshot, the request opens up a config file that provides us the details required to access a database server, from which we can extract critical data:

As a penetration tester, you have to be efficient with your time as mentioned previously it is one of the obstacles of a successful penetration test. This means that when we research the contents of a database, we can also set up some automated tools. A simple test would be to use Burp Suite using Intruder.
Note
The full version of the dirtester.py script can be found at https://raw.githubusercontent.com/funkandwagnalls/pythonpentest/master/dirtester.py.
