22.3 Case Study 3: Overview
Since the 9/11 attack on the World Trade Centers, public interest has been focused on our level of national security. This national security concern has concentrated a great deal on airport security. This section identifies some of the vulnerable areas of airport security screening processes that allow a person with a weapon or destructive device to board a plane, causing a life-threatening event. This chapter also specifies other areas in the airport screening process, where packages or luggage containing deadly weapons can pass through security procedures and enter a plane and cause destruction. This study explores the possible ways and avenues that can be taken to improve and increase the reliability of the security screening processes of airports in ensuring a safe working and living environment.
22.3.1 Introduction
The intent of the following aviation risk assessment was to explore the reliability of airport security systems in our national airports and fulfill the requirements of the University of Idaho course ITED 504—aviation, medical, and process risk assessment. The sequence of tasks required to conduct this study consist of the following: identifying airport security processes, developing a list of components used in the security evaluation, and designing a flow diagram of security processes. A software program called Saphire, developed by the Idaho Environmental and Engineering Laboratory for use in probability and risk analysis for the Nuclear Regulatory Commission, was used to develop an event tree and a fault tree for analyzing airport security screening process. Then, a PHA was performed. This PHA identified initiating events and potential consequences that can cause a hazard or failure point within the airport security processes. A human reliability analysis (HRA) was used to determine the relationship of the failures in the security process associated with human error and their event consequences. Minimal cut sets and event sequences exhibited the shortest route from the failure to the consequences. This study concluded by applying mitigations/interventions in determining the actions required to reduce the risk of failure in the airport security screening processes. The purpose of the airport security risk assessment process is to identify vulnerable areas of the airport security screening process and show changes that will improve security screening.
22.3.2 Purpose Statement
The following analysis hopes to identify specific areas within a local airport security screening process that are vulnerable to cause the screening processes to allow a person with a weapon or destructive device to board a plane, causing a life-threatening event. It also hopes to underline areas that need to be considered for improvement and to increase the confidence and reliability of the security screening processes and ensure a safe and secure environment in the airport. Note that not all possible issues were investigated because this was a student analysis and not a thorough study. Changes to the fault tree logic, for instance, might produce different results.
22.3.3 Airport Security Risk Assessment Process
The basic process for the risk assessment involved several steps. The first step was a visit made to the airport and an interview and tour conducted of the airport security screening process with the city police officer acting as the airport security chief. The purpose of the process is to screen out those individuals with weapons or destructive devices from getting on the plane and causing a life-threatening event.
The four parts of the airport security screening process are defined in Table 22.3. The airport security screening process goes through the following basic steps: curbside check-in, where the vehicle is checked visually for compliance; a ticket check-in, where the ticket agent checks for photo ID, national ID, and ask the required bomb questions; a gate check-in, where the security person checks for boarding pass and screen baggage with the X-ray machine; and a wand-portal check, where the security person scans the passengers with the portal and a hand wand. All these checks are designed to screen the passengers and their luggage for life-threatening devices. If the passenger or their luggage fails to pass the screening checks, they are removed and taken to another security area for further screening and evaluation.
Table 22.3 Four Parts of the Airport Security Screening Process and Their Purpose
| Part | Purpose |
| Curbside check-in | Security checks and ensures cars are not of a suspicious nature and are not left unattended |
| Ticket check-in | Ticket agent checks for photo ID, national photo ID, and ask the required bomb questions. There is a baggage search station at this area also |
| Wand–portal check | Security persons check passengers using the portal and a hand wand |
| Gate check-in | Security checks for boarding pass and screen baggage with the X-ray machine |
Nine primary events were identified and an event tree was constructed to graphically represent the process flow. The event tree was analyzed and actions identified, which may cause a failure of the process. Next, a PHA was performed. An analysis of the PHA helped identify the actions that may fail and the way in which they fail. The PHA led to the development of the fault tree. The fault tree allows a computer program to perform a systematic analysis of the actions involved and their effects. The fault tree was used to perform a sensitivity analysis. All the failures or basic events in the fault tree are assigned the same numeric value, indicating the probability of occurrence. A cut set is generated. Three iterations of this analysis are needed to identify a path most sensitive or most likely to alter the outcome if changed.
Using the failure tree and where applicable, the failure of an action to achieve the desired results will be analyzed. The mode in which the failure occurred, the effects of such a failure, and an attempt to determine just how critical it is to the security process and prevention of a life-threatening event have been analyzed.
Mitigations and interventions have been discussed to determine ways to reduce the risks of failure when performing these actions. These mitigations may provide additional verification at one or all the steps in the process.
From a practical perspective, a class team met and discussed the airport security risk assessment over the course of several class periods with guidance from the instructor. They developed a flow diagram made from notes taken during the interview and tour at the airport, from discussions held in class, from personal experiences of traveling through the airport, and from current news reports commenting on airport security.
To assist the team in determining what activities were most likely to fail and therefore pose the highest risk, a software program called Saphire was made available from the INEEL. An event tree was constructed with this software and a fault tree was extracted from this event tree. A sensitivity analysis was conducted. This produced the same results for all three sensitivity values, 0.01, 0.0025, and 1.0E-6, used. When all failures are the result of human error, there is no redundancy built into the system and all actions have an equal probability for failure. The first two cut sets showed the highest and most equal percentages of failure followed by the next two cut sets in percentage. The first four cut sets at the top are due to human error with no checks or verification built into the system.
The fault tree for the airport security screening process was taken through several exercises to arrive at a fault tree that exhibited various checks and verifications that try to mitigate as many paths for failure as possible in the airport security screening process. Each exercise involved manipulating various gates and basic events and assigning values from the THERP tables to each of the basic events. Table 22.4 shows the cut set values derived from the final input of human error prediction (HEP) values to the basic events of the fault tree. Failure of the ticket agent to check and verify a check for the fake national ID accounts for 87.0% of the failures and the probability of failure is 0.01 or 1 in 100.0 times that the persons with a fake ID will successfully pass through the security screening process. The random baggage search, curbside check-in, and bomb question account for a total of 13.2% of the remaining failures and a total probability of failure of 0.0015 or 1.5 in 1000 times that a person will successfully pass through these steps of the screening process. The results of the cut sets generated are shown in Table 22.5.
Table 22.4 Revised Cut Set
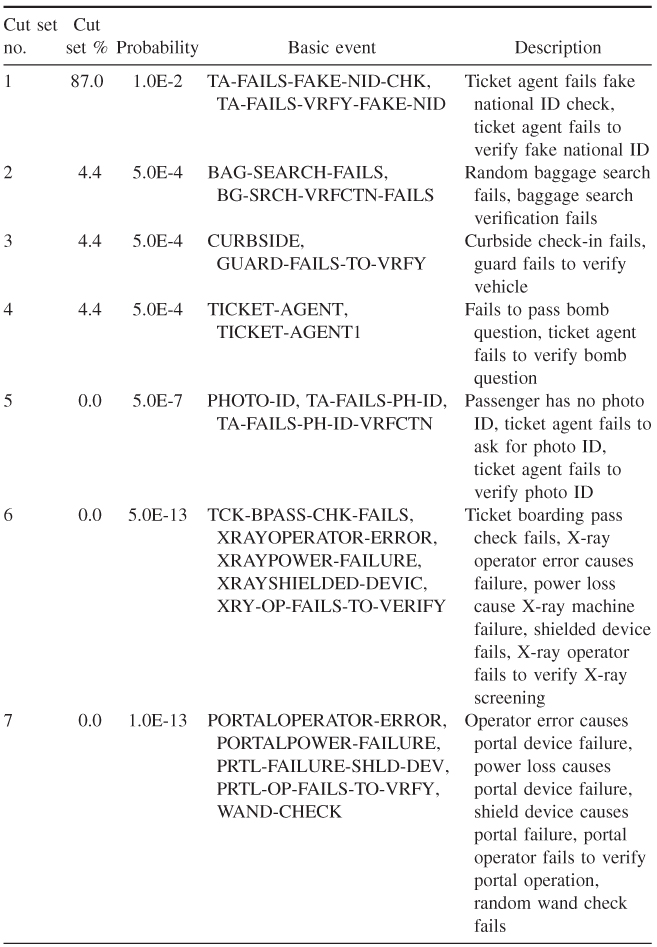
Table 22.5 Cut Sets
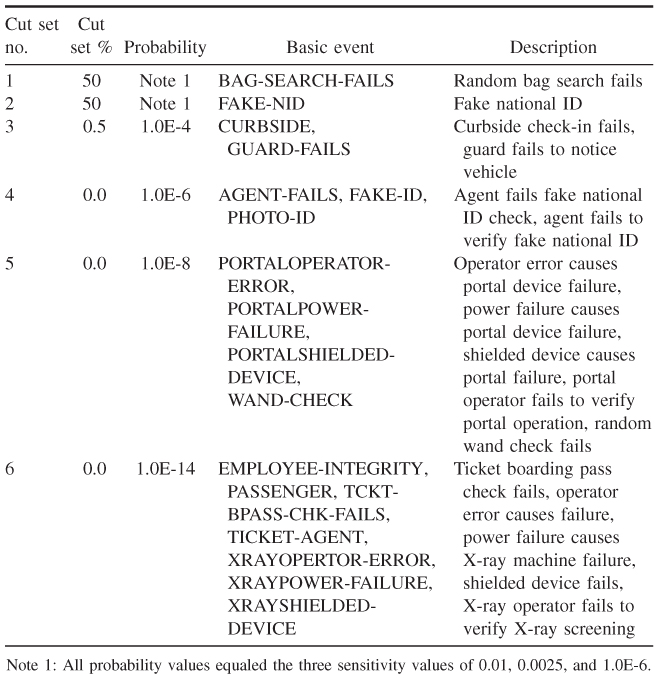
Various risk mitigation measures were recommended during an ongoing review of the fault tree by the analysis team. The method of mitigation chosen was verification and the use of checklists. These were used to help ensure that all the actions required to screen threatening persons were taken.
The verification and checklists are used in the following cut sets:
The use of these verifications and checklists produced a noticeable difference in the probabilities of occurrence and the rearrangement of some of the cut sets.
Table 15.4 showed that the bag search, the fake national ID, and the curbside check-in were the easiest path for a person wanting to pass through the screening process and not get caught. Instituting verifications and checklist switched the easiest paths that a person would take to get through the screening process. Using a checklist, the bag search, curbside check-in, and ticket agent bomb question would fail to detect someone about 4% of the time or 5 in 10,000 times that a person walked through the airport screening. The high probability of failure of the ticket agent to check or successfully check for a fake national ID is the most prevalent, 87% failure rate or 1.0 in 100.0 visual checks of national ID. There is a marked difference in which path or cut set that would show the most failure in the screening process and in the probabilities based on the use of verifications and checklist. Their introduction into the screening process would probably have a low impact on productivity and cost.
22.3.4 Summary
Suggestions and recommendations are presented for ensuring that the airport screening process is designed and operated in a manner that ensures the maximum of safety to passengers and airport security personnel. From the process of risk analysis and the use of the software program from the INEEL, the checklist and verifications are shown to produce the less risk of failure for the different paths of screening process to fail in detecting an individual determined to get through the airport screening and causing a life-threatening event. The process of checking and verifying a fake national ID seems to be the most vulnerable for failure. This may be due to the lack of hard numerical data on national fake IDs, their prevalence in our society, and the ease at which they can be mistaken for the real ID. This risk analysis may warrant further research into this area of national security.
Conclusions
To ensure a level of confidence and reliability in the airport security screening process, the specific areas to focus on is the national identification check and the baggage search process as identified in the risk analysis exercise.
