This practice exam has been written to emulate the types of questions you can expect to see on the SCSP exam. Try to simulate a real testing environment and find a quiet spot where you will not be interrupted. Give yourself 90 minutes to answer all 100 questions.
Once you have answered as many questions as you can in 90 minutes (or are satisfied with your answers if you finish before your 90 minutes are up), go to the “Quick Answer Key” section to score your exam. Review the in-depth answer explanations and references for any answers that were incorrect, and then go to the “Analyzing Your Results” section to review your score.
Questions
1. After configuring storage on a storage array for a host, you find that a technician has moved fiber cables on the fiber switch, causing the assigned LUNs to disappear from the host. What should you do to prevent this from occurring in the future?
A. Utilize WWN zoning.
B. Secure the SFPs to the switch with zip ties.
C. Utilize port zoning.
D. Restrict access to the SAN zoning to storage administrators only.
2. A host connected to an iSCSI SAN is experiencing high CPU utilization. Which option would resolve the issue with the least effort and cost?
A. Replace the CPU with a faster one.
B. Replace the NIC with a NIC with TOE.
C. Upgrade copper cables to fiber.
D. Upgrade Cat5e cables to Cat6a.
3. Which of the following would be considered an initiator? (Choose two.)
A. HBA
B. iSCSI NIC
C. Switch port
D. Storage controller
4. Snapshots are taken every 15 minutes of an e-mail server and then sent to a nearline storage array. The e-mail backups on the nearline storage array are archived to tape at 10 P.M. each day. Restore tests have confirmed that it takes 30 to 45 minutes to restore an e-mail backup from tape and 2 minutes to restore from nearline storage. What is the RPO?
A. 2 minutes
B. 15 minutes
C. 30 minutes
D. 45 minutes
5. You have been tasked with backing up a storage array to tape. The backup window is only a few hours, and all the data must be completely written to tape during the backup window. Which technology should you use to accomplish the objective?
A. Disk to disk
B. Tape autoloader
C. Disk to disk to tape
D. Tape library
6. Users complain about slow access to files on a database server. The database server has its database files stored on an iSCSI SAN. You check the logs on the storage array and switches and see no errors. You then issue a packet capture on the network and find a significant amount of FTP traffic during the times when users have complained. What should you do to improve performance without impacting the speed of FTP transfers?
A. Give iSCSI traffic a higher priority.
B. Give FTP traffic a lower priority.
C. Segment the iSCSI traffic on its own VLAN.
D. Replace NICs with NICs that support TOE.
7. At 2 A.M., your storage vendor calls you to tell you that she is on the way to your data center to replace a failed disk. How did the storage vendor know about the failed disk?
A. Call Home
B. Event logs
C. SSH administrator CLI
D. SNMP traps
8. You are evaluating the price of a new storage array for your company. The company requires the fastest speed but not high capacity. Which disk technology should you look for in the storage array?
A. SCSI
B. SAS
C. SSD
D. SATA
9. Business requirements state that two switches located in different data centers must have the same domain ID. They are part of the same SAN. Which technology will allow you to use the same domain ID on both FC switches?
A. WSAN
B. VSAN
C. Domain ID mirroring
D. Alternate domain IDs
10. A multipathed server connected to a SAN loses access to storage resources after a switch fails. What should you do to correct this?
A. Cable both HBAs to different switches.
B. Install updates to the host’s multipathing software.
C. Configure the ports on the switch to be in the same LAG group.
D. Configure the failover option on the zone.
11. Which component is not configured for high availability in the solution depicted in the illustration?
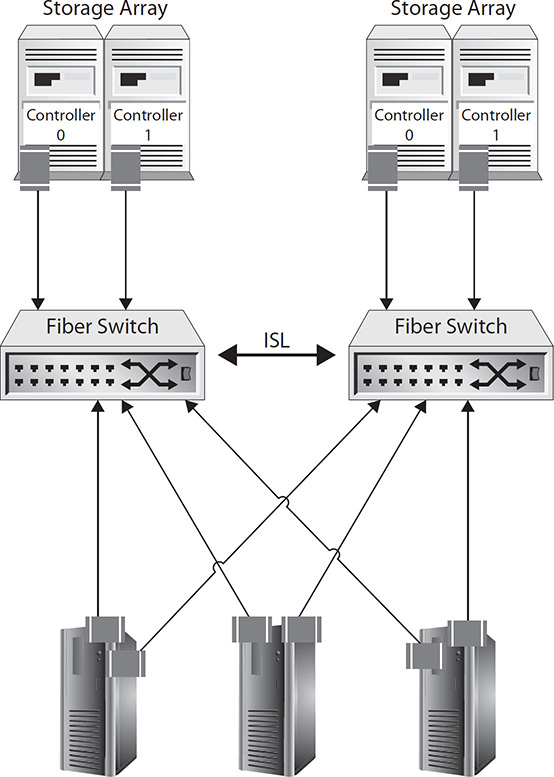
A. Storage array
B. Switches
C. Host
D. ISL
12. Your company would like to move department shares to a central device that will handle access through NFS and CIFS for Windows and Linux machines. Which solution will satisfy the requirements?
A. iSCSI storage array
B. Software as a Service (SaaS)
D. DAS
13. A directory on a file share is running out of space, so the IT director orders several new hard drives. Which of the following options would work to increase the space for the directory when the drives arrive? (Choose all that apply.)
A. Create a RAID set with the drives and a logical volume. Add the volume to the storage pool that the file share resides on and verify that the share is set to autoexpand.
B. Create a RAID set with the drives. Select the volume that is running out of space, choose Extend, and select the unpartitioned space on the new RAID set.
C. Create a RAID set with the drives and a logical volume. Mount the volume in a temporary location and move the files in the directory that is running out of space to the new volume; then unmount and mount the volume in the folder location of the directory that was running out of space.
D. Extend the existing RAID set to include the additional drives.
E. Create a RAID set with the drives and a logical volume. Move the data from the directory that is running out of space to the new logical volume and then share it. Change the name of the old share. Use DFS to create a root share with the name of the old share. Create DFS links to the old and new logical volumes so that the former folder structure is maintained.
14. A storage array is configured with seven 500GB SATA disks, five 300GB SAS 15k disks, and five 400GB SAS 15k disks. At a minimum, how many hot spares will be needed and what type are they?
A. One hot spare consisting of a 500GB SAS 15k disk
B. Two hot spares consisting of a 500GB SATA disk and a 400GB SAS 15k disk
C. Three hot spares consisting of a 500GB SATA disk, a 300GB SAS15k disk, and a 400GB SAS 15k disk
D. One hot spare consisting of a 500GB SSD disk
15. You are setting up a new storage array, and you want to have two RAID groups using RAID 5 and a hot spare. You will need 5TB of available storage, and you have a box of 500GB SAS disks. How many disks would you need?
A. 13
B. 12
C. 11
D. 10
16. Your organization utilizes the following backup schedule: full backups every Saturday at 10 P.M. and incremental backups Sunday through Friday at 10 A.M. and 10 P.M. A large number of files were deleted from the NAS on Wednesday at 5 P.M. Which backups must be restored, and in what order do you restore the files?
A. Full backup and then the 5 P.M. backup on Wednesday
B. Full backup and then the 10 A.M. backup on Wednesday
C. Full backup and then the Sunday 10 A.M., 10 P.M.; Monday 10 A.M., 10 P.M.; Tuesday 10 A.M., 10 P.M.; and Wednesday 10 A.M. backups
D. The Sunday 10 A.M., 10 P.M.; Monday 10 A.M., 10 P.M.; Tuesday 10 A.M., 10 P.M.; and Wednesday 10 A.M. backups
17. How many disks does a RAID 10 array require at the absolute minimum?
A. 1
B. 3
C. 4
D. 5
18. Your team has a series of reports that must be shared between members located all around the world. They want to use a cloud-based solution to host the files. What type of solution should you consider?
A. SaaS
B. PaaS
C. CaaS
D. STaaS
E. IaaS
The following scenario is used for questions 19, 20, and 21:
Nutty Corporation has a clustered e-mail server consisting of four servers (MailNode01, MailNode02, MailNode03, and MailNode04) that connect to an iSCSI SAN for their storage. There are six LUNs assigned to the four clustered servers. They are labeled 001-Quorum, 002-MSDTC, 003-MailDB01, 004-MailDB02, 005PublicFolder, and 006-MailDBArchive. A full backup is performed on LUNs 003, 004, 005, and 006 each night at 8 P.M. using out-of-band backup software. Snapshots are taken of all LUNs assigned to the cluster twice a day at 2 A.M. and 2 P.M. Your manager has informed you that restore operations should be performed in-band whenever possible. The four servers each have four NICs. Two are link aggregated for load balancing and failover for iSCSI traffic, and two are link aggregated for load balancing and failover for use on the LAN. Two VLANs are configured, with one for iSCSI traffic and another for LAN traffic.
19. At 4 P.M., an integrity check detects corrupted data in the public folder. LUN 005PublicFolder is currently mounted on MailNode01. Given the scenario described, what should you do to restore the data with the least data loss?
A. Revert to the 2 P.M. snapshot for LUN 005PublicFolder.
B. Apply the backup from 8 P.M. from the night before and then revert to the 2 P.M. snapshot for LUN 005PublicFolder.
C. Fail over LUN 005PublicFolder to MailNode02 and then reset the integrity error.
D. Take MailNode01 out of the cluster.
20. A junior administrator accidentally deletes LUN 003 from the iSCSI storage array at 9 P.M. Given the scenario described, what should you do to restore the data with the least data loss?
A. Revert to the 2 P.M. snapshot for LUN 003-MailDB01.
B. Apply the backup from 8 P.M. from the night before and then revert to the 2 P.M. snapshot for LUN 003-MailDB01.
C. Create a new LUN 003-MailDB01 with the same size as the old LUN 003-MailDB01 and then restore the backup from 8 P.M. from the night before for LUN 003-MailDB01.
D. Apply the backup from 8 P.M. from the same day for LUN 003-MailDB01.
21. You notice connectivity errors in the log for the second iSCSI NIC in each of the clustered servers. You verify the zone, and it is configured correctly. Given the scenario described, what might be the problem? (Choose all that apply.)
A. The switch for the secondary iSCSI NICs is offline.
B. The iSCSI storage array is in maintenance mode.
C. The second controller on the iSCSI storage array lost its IP address.
D. The iSCSI storage array lost power.
E. The VLAN configuration on the switches is missing.
22. Which of the following is not an advantage of cable management?
A. Cable management improves airflow in the rack.
B. Cable management separates data and power cables to better prevent EMI.
C. Cable management helps prevent cable stretching and snags.
D. Cable management extends the life of rack equipment.
23. Which of the following is a benefit of a high cache hit ratio?
A. Faster storage array response time
B. Lower latency for storage replication
C. Increased utilization of system cache
D. Less storage used because of deduplication
24. Your company expands into a neighboring office space that already has Ethernet cabling installed using Cat5e. The cables terminate in a wiring closet. Your users require 1 Gbps connections to the network, and the wiring closet must support 10GigE to the storage system in your server room. The server room is 75 meters away from the wiring closet. What cabling should you add or replace in this situation? Keep costs to a minimum.
A. Replace the Cat5e cables with Cat6 and add Cat6 cabling from the wiring closet to the server room.
B. Add Cat6 cabling from the wiring closet to the server room.
C. Add multimode fiber between the wiring closet and the server room.
D. Replace the Cat5e cables with Cat6 and multimode fiber from the wiring closet to the server room.
E. Add Cat6a cabling from the wiring closet to the server room.
25. You are a storage administrator responsible for backups on the storage network. Backups must be sent to tape each day using a single tape drive, and the duration of backup jobs on the storage systems must be kept to a minimum. Which backup design would best fit this situation?
A. D2T
B. D2D2T
C. NDMP
D. D2D
26. Which of the following is an advantage of storage tiering?
A. Data is migrated to another site for disaster recovery.
B. Duplicate files are suppressed.
C. Data retention policies are enforced.
D. Most frequently used files can be accessed faster.
27. What is the most frequent backup performed in a GFS rotation?
A. Hourly
B. Daily
C. Incremental
D. Transactional
E. Weekly
28. Which technology encapsulates FC data over Ethernet but does not use IP?
A. iSCSI
B. FCoE
C. FCIP
D. iFCP
29. If you configure seven 400GB drives in a RAID6, how much usable space will you have?
A. 2,800GB
B. 2,400GB
C. 2,000GB
D. 1,600GB
30. Technicians at your company remotely manage the SAN fabric using Telnet. Port 23 is open on the firewall to allow the technicians to connect remotely. What changes should you make to encrypt this traffic?
A. Disallow port 23 on the firewall. Configure an SSL VPN and allow port 443 on the firewall. Instruct technicians to connect to the network using the VPN and then to use Telnet within the VPN.
B. Configure the SAN fabric to use SSH instead. Instruct technicians to connect using SSH rather than Telnet.
C. Enable “require encryption” on the Telnet configuration on the SAN fabric. Instruct technicians to utilize the encryption option when connecting.
D. Disable Telnet and require technicians to use a serial cable to manage the SAN fabric.
31. What is the primary requirement for a system to be considered high availability?
A. 24/7 monitoring
B. Higher SLAs
C. Offsite backups
D. Redundant components
32. How do hot and cold aisles enhance airflow in a data center?
A. Hot and cold aisles keep hot air flowing away from computing equipment and toward cooling equipment while cold air is directed toward computing equipment.
B. Hot aisles and cold aisles allow for high-density racks to be placed where they will receive the most cooling.
C. Hot aisles and cold aisles aid in emergency evacuation.
D. Hot and cold aisles allow for better capacity planning
33. Users in the finance, accounting, and administration departments need access to the quarterly reports. You would like to create a central location to store the files and allow concurrent access to users in the departments. Which protocol would be best suited for the task?
A. SNMP
B. CIFS
C. Telnet
D. iSCSI
E. FC
34. A system that has three LUNs formatted with the EXT3 file system crashes overnight. Web developers need access to the LUNs immediately while the crashed system is being rebuilt. Which type of system should the LUNs be mounted to?
A. Windows 98
B. Windows Server 2008 R2
C. Ubuntu Linux
D. AS/400
E. Apple iOS
35. A multipathed server is connected to a storage array, but it is experiencing higher latency on some traffic and low latency on other traffic. You check the configuration of the HBAs, and they are configured in an active/passive load-balanced team. After analyzing the switches, you find that the ISL between two redundant switches has periods of high utilization that correspond to the higher latency. How might you solve the problem? (Choose the best answer.)
A. Add more links to the ISL between the switches.
B. Map the LUNs to the server using a file-level architecture rather than a block-level architecture.
C. Increase the buffer-to-buffer credits.
D. Configure the multipathed HBAs to be active/active.
36. Which of the following topologies uses optical cables in a logical ring but is configured as a physical star?
A. FC-AL
B. FC-SW
C. P2P
D. Ethernet
37. Which device can make decisions based on information it receives from neighboring devices on where to send traffic most efficiently in a meshed or partially meshed network consisting of multiple potential paths from source to destination?
A. Switch
B. Director
C. Repeater
D. Router
E. Transceiver
38. What role does iSNS play on a SAN?
A. It provides attached devices with information on available storage resources.
B. It notifies administrators when critical events occur on the SAN.
C. It registers new FC addresses when a device connects to the SAN.
D. It load-balances connections between multipathed adapters.
39. Which media would be best suited for archival storage at the lowest cost for 400GB of files on a periodic basis?
A. DVD
B. Flash media
C. Nearline storage
D. Tape
40. How do fiber switches connect to one another?
A. ISLs are created between two switches using E-ports.
B. ISLs are created between two switches using F-ports.
C. Fiber cables are connected to both switches on U-ports.
D. Fiber cables are connected to both switches on F-ports.
41. In a business continuity planning meeting, your manager asks you how the organization would continue business if a fire consumed the equipment in the server room. Which technology would be useful for business continuity in this situation?
A. Offsite tape backups
B. Hierarchical storage management
C. Snapshots
D. Remote replication
42. Users complain of slow performance on a key application. You calculate current performance metrics. What must you compare the metrics to in order to identify which component or system is slow?
A. Alerts
B. Baseline
C. Scope
D. Logs
43. Which technology would ensure that the same data is present on all devices before committing a transaction?
A. Snapshot
B. Replication
C. Consistency group
D. Integrity group
44. Which of the following statements is true?
A. LTO3 tapes have a native capacity of 400GB and a compressed capacity of 800GB.
B. LTO4 tapes have a native capacity of 400GB and a compressed capacity of 800GB.
C. LTO5 tapes have a native capacity of 800GB and a compressed capacity of 1,600GB.
D. LTO2 tapes have a native capacity of 100GB and a compressed capacity of 200GB.
45. Your organization plans to replicate data from a high-performance database in New York to Los Angeles. The link between sites has high latency, and performance must be only minimally impacted. What form of replication would be best suited to this situation?
A. Synchronous replication
B. Direct replication
C. Asynchronous replication
D. Host-based replication
46. A storage array has four front-end ports connected to four servers. A fifth server is added. What should be installed so that this device can connect to the storage array?
A. Director
B. Router
C. Switch
D. Repeater
47. How many heads are in a hard disk drive, and how are they situated?
A. There is a head at the top and bottom of each platter with its own actuator arm.
B. A single head runs between all of the platters on the hard drive.
C. There is a head at the top and bottom of each platter. All heads are attached to the same actuator arm.
D. The head runs along the surface of each disk and is used to read the hard drive.
48. Where is the controller board located, and what job does it perform?
A. A controller board controls the movement of the actuator arm from below the disk.
B. A controller is mounted to the base of the disk and contains an interface for sending and receiving data to a connected device. It controls the movement of the actuator arm and rotation of the spindle.
C. A controller board is mounted to the top of the disk and controls the physical components in the disk.
D. A controller board is attached to the top of the disk and causes the disk to spin.
49. While both solid-state and hard disk drives are used to store data, how do SSD and HDD differ in the way they organize data?
A. SSD organizes data into blocks rather than tracks and selectors.
B. In an HDD, blocks consist of multiple pages made up of 150 bytes.
C. In SSD, pages consist of blocks, which are generally 128 bytes.
D. An HDD uses logical bit addressing to reference a location on a disk, while SSD uses a master table.
50. How does Fibre Channel reference other devices on the network?
A. A simple channel access system (SCAS)
B. A reference ID
C. A twofold security connection number
D. A World Wide Name (WWN)
51. What is Fibre Channel layer 3 known as, and what does it do?
A. It is known as the block layer, and it is the upper-layer protocol mapping. It is responsible for encapsulating upper-layer protocols.
B. (It is the processing layer, and it breaks data into smaller chunks called frames.
C. It is the services layer, and it supports striping, hunt groups, and the spanning of multiple ports.
D. It is the infrastructure layer used to ensure all pathways are planned for data to travel.
52. What is a World Wide Name (WWN)?
A. A 16-bit or 32-bit identifier for a network communication port
B. A computer’s external IP address
C. The main port identifier in a simple channel access system
D. An 8-byte or 16-byte identifier for a network communication port on a Fibre Channel network
53. One of the most basic metrics used in measuring storage performance is called what?
A. File Transfer Protocol
B. System Storage Monitoring
C. Input Output Operations per Second
D. Send Receive Operations per Second
54. How do optical cables transmit data?
A. Optical cables transmit data via long-range frequencies.
B. Optical cables transmit data via light impulses.
C. Optical cables transmit data via electromagnetic waves.
D. Optical cables transmit data via electromagnetic impulses.
55. Which of the following best describes a converged network adapter?
A. A device that connects an iSCSI host to storage
B. A device that can be used for communication with non-storage-related equipment via a network
C. An onboard device that connects two devices via copper cabling
D. A device capable of connecting a host to storage with connections over FC, Ethernet, or twinax connections
56. Which of the following best describes a fiber director?
A. A high-capacity modular switch with two or more hot-swappable power supplies and redundant routing engines, pathways, and processors.
B. A layer 3 device that is used to connect network segments of differing topologies.
C. A device that connects storage segments that traverse a WAN. The director performs encapsulation over the WAN of supported storage protocols and deencapsulation of data on the receiving end.
D. A device that filters storage data at the application layer utilizing a wide array of software. Such devices are typically vendor updatable.
57. The condition known as buffer underrun refers to which of the following?
A. When a disk is rendered unusable because of a failure during the write process
B. When the scratches on a disk have rendered portions of the data unusable
C. When the buffer is emptied during the process of burning information to a disk
D. The condition where a disk drive cannot read a disk at the optimal speed
58. How does the Storage Networking Industry Association (SNIA) define storage virtualization?
A. The application of virtualization to storage services or devices for the purposes of aggregating functions or devices, hiding complexity, or adding new capabilities to lower-level storage resources
B. The abstraction of software and hardware used to provide storage services such that each can operate independently
C. Implementation of standards-based storage products that can be layered upon one another to provide functionality to meet business objectives
D. Utilizing virtualization in storage services to provide differing views to the data based on the level of virtual provisioning used
59. According to the Storage Networking Industry Association Shared Storage Model, what is the job of the file/record layer?
A. This layer organizes the information required by the application and interfaces with the application.
B. This layer uses virtualization to map logical addresses to physical addresses.
C. This layer of virtualization is an abstraction of physical storage to logical partitions independent of storage structure, allowing several physical disks to be accessed through a single virtual/logical interface.
D. This layer stores data on virtualized removable media, including virtual tapes (VTs), virtual tape libraries (VTLs), and tape library virtualization (TLV).
60. Which of the following is not a form of storage provisioning?
A. Privileged provisioning
B. LUN provisioning
C. Thick provisioning
D. Thin provisioning
61. Which of the following is shared by in-band and out-of-band virtualization?
A. Optimization of SAN utilization and performance.
B. Storage management is offloaded from the host.
C. Latency is avoided by separating control functions from the paths where data travels.
D. A consolidated virtual platform for network storage management.
62. Which of the following is not a type of storage virtualization?
A. Disk virtualization
B. Host virtualization
C. Block virtualization
D. Tape virtualization
63. What is a high-speed memory that can be used to service I/O requests faster than accessing the disk?
A. Memory
B. Logical disks
C. Solid-state drives
D. Cache
64. Which of the following best describes the Common Information Model?
A. It is an object-oriented approach to organizing information where objects have attributes, and each is created from a class that describes the format of the object.
B. It is a method used to allow multiple levels of abstraction to exist in the data path and to pool storage under the control of a domain manager.
C. CIM is a method of creating a LU that can grow as needed. The LU appears to the host system as the maximum size it can grow to, but it consumes only the amount of space the host uses on the storage system.
D. CIM is used to set warning and alarm thresholds in storage management tools that then compare the set values against real-time readings from the system.
65. What does it mean if in-band management is used for a storage network?
A. Data as well as management and monitoring information travel over different paths.
B. An appliance is used to manage and monitor data.
C. An appliance is used to monitor data, but transfers occur over the front-end data path.
D. Data as well as management and monitoring information travel over the same path.
66. Appliance-based data migration specifically refers to which of the following?
A. A data migration in which stand-alone network appliances migrate files and volumes, interfacing with storage systems and providing a separate interface for managing the replication
B. Migrating entire applications, referred to as appliances, from one site to another or from one redundant clustered node to another
C. Migrating management data such as logs and configuration settings from network appliances for the purposes of centralized review and business continuity
D. A data migration solution that can be plugged into a rack without additional customization or configuration
67. What amount of space do thick logical units take up? (Choose the best answer.)
A. Only the amount of space consumed by files within the logical unit.
B. The amount of space consumed by files in the logical unit plus 20 percent.
C. Thick logical units are those that exceed 1TB.
D. The same amount of space as is presented to the host operating system.
68. What best defines data integrity?
A. Assurance that data remains unchanged after creating, modifying, copying, completing, or otherwise operating on data.
B. Having a backup of every version of a data set since its creation.
C. Encrypting a file or data set to prevent tampering.
D. The data given is proven factual and is supported by other reports.
69. Which of the following is not a broad classification for the causes of system outages?
A. Human error
B. Intentional error
C. Workflow error
D. Systematic error
70. Which of the following is the primary objective of business continuity planning?
A. Providing a proactive strategy to prevent or limit the impact of system failures and to rapidly restore operations should such events occur
B. Outlining the essential activities required when a disaster occurs
C. Leveraging redundancy in each aspect of the storage and networking environment to be better able to resist a failure of a single component
D. Replicating duties such that the loss of a single employee, role, or division would not impact the ability of the organization to continue doing business
71. If malware infection potentially impacts the business by a loss of three hours of productivity on average and this is expected to happen once every other month, then the cost per year in hours is which of the following?
A. 12 hours of lost productivity
B. 18 hours of lost productivity
C. 24 hours of lost productivity
D. 36 hours of lost productivity
72. What is necessary to determine how much redundancy is needed?
A. Knowing how available a system needs to be
B. Logical block addressing
C. How well the failover system works
D. Whether the system is replicated
73. What does a risk assessment analyze?
A. The threats that could impact the integrity, confidentiality, or availability of business systems
B. The cost that a business could incur because of the exploitation of potential threats and the likelihood of such exploitation occurring
C. Organizational security as a whole
D. Both A and B
74. What does a business impact analysis estimate?
A. The time, cost, and effort to respond to and contain a security incident
B. The cost an organization could incur should systems be unavailable because of incident or disaster
C. The amount of time it would take to bring business operations back to normal
D. The controls required to bring risks below the organization’s risk tolerance level
75. What is the main difference between remote and physical authentication?
A. Remote authentication is used to access a system from offsite, while physical authentication is used to connect from another portion of the onsite network.
B. In remote authentication, passwords are sent via the network, while physical authentication is done on the machine being logged into.
C. Physical authentication is the type of authentication where a certain visual pattern is used, while a remote authentication is used to easily access devices via a network.
D. Remote authentication is used when a system is accessed through another system, while physical authentication is used only to access a remote authentication service.
76. When services are transferred from one component to another in a redundant system, it is called what?
A. Service redundancy
B. Failover
C. Overflow
D. Component transfer
77. What is the name of a system that provides immediate response and high availability?
A. Emergency system processing
B. Online transaction processing
C. Rapid response protocol
D. Systemic fabrication principles
78. Which technology allows multiple N-ports to reside on the same physical N-port?
A. VSAN
B. SCR
C. PLOGI
D. NPIV
79. What is a result of a single configuration, a network, hardware, or software malfunctioning and causing the entire system or process to fail?
A. Large-scale system failure
B. A single point of failure
C. Network failure
D. Server-side power failure
80. What is a secondary risk?
A. Risk caused by another risk response strategy
B. Risk that is moderately likely to occur
C. A risk that can occur when multiple other risks occur
D. A risk computation obtained from an alternate methodology such as quantitative, if qualitative was used for the primary risk
81. Low humidity can create an environment where charges can build up, which can lead to what?
A. Water damage
B. Electrostatic discharge
C. Overheating
D. Electrical failure
82. Fire suppression systems that use gaseous agents remove components that fire needs to exist. Which of the following examples remove heat from fire?
A. FSC-500
B. HFC-125
C. CFN-330
D. HVAC
83. What does rack density refer to?
A. The amount of heat generated by devices in a rack
B. The number of cables running between devices on the rack
C. The number of types of devices on the rack
D. The number of devices in the rack
84. What is a form of storage management where data of varying formats is transferred between hosts or storage systems at periodic intervals?
A. Transfer protocols
B. Replication
C. Data backup
D. System support
85. What presents files and directories as a composite object with a single integrated file interface while optimizing their location?
A. Block management architecture
B. Hierarchical storage management
C. Manual storage tiering
D. Storage management system
86. What purpose does the alias serve on a fiber network?
A. The alias is an alternate WWPN that can be used in case the first WWPN fails.
B. The alias is used to identify ports that belong to a multicast or hunt group.
C. The alias is a descriptive name given to a node so that it can be referred to by it instead of its WWN.
D. The alias was used in FDDI ring implementations, but it is not used in modern fiber networks anymore.
87. What specifies that data potentially relevant to ongoing or expected lawsuits should be preserved?
A. Mandatory preservation
B. Litigation holds
C. Trial backup requirements
D. Litigation preservation
88. A technician notifies you that the tape drive at your data center is making noise. You investigate and find that the drive repeatedly stops, rewinds, and then writes again. What could be causing this issue?
A. The tape drive needs cleaning.
B. The drive is shoe-shining.
C. The cable between the tape drive and the backup server is going bad.
D. The backup system has mounted the tape drive for random reads.
89. Which controller technology breaks files up into segments to be stored on multiple nodes in a process known as encoding?
A. Full mesh
B. Cache
D. Dual
90. Which unit of measurement is used to describe the number of devices data must traverse from source to destination?
A. Jump
B. Hop
C. Latency
D. Ping
91. Which technology is used to prioritize traffic?
A. Class of service
B. Routing
C. Link-level prioritization
D. Switching
92. Your customer would like to implement a SAN over their existing Ethernet network. What solution should you recommend?
A. FC on FC switches
B. FC on the same LAN
C. iSCSI on the same LAN
D. iSCSI with VLANs
93. A server rack in your data center is configured with A/B power. Normal power levels are 25 percent on each link, and peak power is 60 percent. Do you recommend any changes? If so, which changes?
A. No changes are required because the load is less than 80 percent.
B. Reduce the load to bring each link below 50 percent.
C. Add one more circuit and put 30 percent load on it.
D. Two more circuits should be added to bring the load below 40 percent peak for each link.
94. Which of the following devices is not hot pluggable?
A. Hard drive
B. Power supply
C. Switch module
D. Motherboard
95. Which disk type can run at 15,000 rpm? (Choose all that apply.)
A. IDE
B. SCSI
C. SATA
D. SAS
E. FC
96. Which device would be used by a host to connect to a Fiber Channel SAN?
A. HBA
B. NIC
C. Modem
D. TOE
97. Which piece of safety equipment can a person wear to protect against electrostatic discharge?
A. Hard hat
B. Lifting belt
C. Wrist strap
D. Aluminum gloves
98. A user needs to quickly transfer 10GB data from their workstation to a remote office. The user offers to bring the data to the remote office, but they need to store the data on some removable media. Which media would be best suited for transferring the data and be easiest for the user to utilize?
A. DVD
B. Flash drive
C. CD
D. Tape
99. Your company would like to implement a network to connect multiple disk arrays to servers. Which technology should they employ?
A. NAS
B. DAS
C. LAN
D. SAN
100. Which of the following could be used to send e-mails to administrators when storage resources are at or above 80 percent capacity?
A. Baselines
B. Thresholds
C. Alerts
D. Logs
101. Which type of drive would be best suited for a small office NAS with low I/O and utilization?
A. Consumer drive
B. Entry-level drive
C. Midrange drive
D. Enterprise drive
102. Fred is pricing out a new server that will be used to house development virtual machines for a variety of different departments. Each department is on its own VLAN, and developers require a dedicated NIC for their virtual machines. Fred determines that he needs to have 12 Ethernet connections, so he plans to purchase three quad-port Ethernet adapters. Which PCI bus should he utilize for the server and the expansion cards?
A. PCI
B. PCI-X
C. PCIe
D. PCI-M
103. Juan is the new storage administrator for his company, and he recently found that the company file shares are stored on a single 3TB SATA drive. The server does not have a RAID controller. Juan wants to implement RAID 5 using three identical 2TB drives he already has on hand to replace the current disk. Juan has no budget for other equipment. Which RAID controller should he implement?
A. Host-based controller
B. Software RAID
C. Hardware RAID
D. Software RAID using a hardware controller
104. Which cloud storage method is most vulnerable to latency?
A. Cloud backup
B. Locally mapped cloud storage
C. Cloud synchronization
D. Web-based cloud storage
105. Which of the following is an example of cloud storage?
A. An application writes a transaction to a database, which then replicates to another database in another data center.
B. A user modifies a file on their computer, and that modification is synchronized with another remote third-party source over the Internet and other replica sets that connect to the remote source.
C. A user stores data on a share hosted on a file server, but the share is on a volume mounted through iSCSI to another storage device.
D. An e-mail server stores user mailboxes on a volume that is mapped back to a number of nodes. The data is encoded, and portions of the data are spread across the nodes in the set.
106. Which of the following is an accurate definition of a hybrid cloud?
A. A hybrid cloud is owned and operated by a third party and made available to customers over the Internet.
B. A hybrid cloud is a proprietary system owned and operated by a single organization for its use.
C. A hybrid cloud is a cloud that is owned and operated by a third party or jointly by its members.
D. A hybrid cloud is a combination of a public cloud and a private cloud.
107. Which of the following is not an ITIL service change approach?
A. Phased
B. Push
C. Big bang
D. Core
108. Which information would be useful for properly sizing backup drives? (Choose all that apply.)
A. Current size of backups
B. Growth rates
C. Storage location
D. Backup frequency and retention
Quick Answer Key
1. A
2. B
3. A and B
4. B
5. D
6. C
7. A
8. C
9. B
10. A
11. A
12. C
13. A, C, and E
14. B
15. A
16. C
17. C
18. D
19. A
20. C
21. A and C
22. D
23. A
24. E
25. B
26. D
27. B
28. B
29. C
30. A
31. D
32. A
33. B
34. C
35. D
36. A
37. D
38. A
39. D
40. A
41. D
42. B
43. C
44. A
45. C
46. C
47. C
48. B
49. A
50. D
51. C
52. D
53. C
54. B
55. D
56. A
57. C
58. A
59. A
60. A
61. D
62. B
63. D
64. A
65. D
66. A
67. D
68. A
69. C
70. A
71. B
72. A
73. D
74. B
75. B
76. B
77. B
78. D
79. B
80. A
81. B
82. B
83. D
84. B
85. B
86. B
87. B
88. B
89. C
90. B
91. A
92. D
93. D
94. D
95. B, D, and E
96. A
97. C
98. B
99. D
100. C
101. C
102. C
103. B
104. B
105. B
106. D
107. D
108. A, B, and D
In-Depth Answers
1. ![]() A is the correct answer. Each HBA in a host is assigned a WWN that is unique to it. WWN zoning allows access to LUNs based on the WWN of the device. In this way, it does not matter which port the HBA is plugged into on the switch because the zone will still allow access based on the WWN of the HBA port, which would still reside in the host.
A is the correct answer. Each HBA in a host is assigned a WWN that is unique to it. WWN zoning allows access to LUNs based on the WWN of the device. In this way, it does not matter which port the HBA is plugged into on the switch because the zone will still allow access based on the WWN of the HBA port, which would still reside in the host.
![]() B is incorrect because the SFP is simply a transceiver, and it does not contain port information or an identification number. The SFPs can be changed without impacting the zoning. C is incorrect because port zoning would map LUNs to switch ports, which would not change automatically if a device was moved from one port to another. D is incorrect because this problem did not occur because of a zoning change. Rather, it occurred because a change was made to the physical cable. Arestriction on zoning would not prevent a technician from moving a cable.
B is incorrect because the SFP is simply a transceiver, and it does not contain port information or an identification number. The SFPs can be changed without impacting the zoning. C is incorrect because port zoning would map LUNs to switch ports, which would not change automatically if a device was moved from one port to another. D is incorrect because this problem did not occur because of a zoning change. Rather, it occurred because a change was made to the physical cable. Arestriction on zoning would not prevent a technician from moving a cable.
Chapter 8: Storage Visibility | Zoning SCSP objective 1.3, Identify storage mapping elements
2. ![]() B is the correct answer. TOE is a chip on a NIC that performs TCP/IP processing so that the computer processor does not have to. This would reduce the CPU utilization.
B is the correct answer. TOE is a chip on a NIC that performs TCP/IP processing so that the computer processor does not have to. This would reduce the CPU utilization.
![]() A is incorrect because while it would result in more CPU, it would not do so with the least effort and cost. C is incorrect because fiber cables are not used with iSCSI for host connectivity and the problem is not one that can be solved with cables. D is also incorrect. Faster- or slower-speed cables will still require the CPU to perform TCP/IP computations.
A is incorrect because while it would result in more CPU, it would not do so with the least effort and cost. C is incorrect because fiber cables are not used with iSCSI for host connectivity and the problem is not one that can be solved with cables. D is also incorrect. Faster- or slower-speed cables will still require the CPU to perform TCP/IP computations.
Chapter 4: Storage Networking Devices | NIC | TCP Offload Engine SCSP objective 1.6, Describe how to improve performance for host applications
3. ![]() A and B are the correct answers. Initiators send requests to targets. Targets are storage resources that can be utilized by initiators. An HBA and an iSCSI NIC both function as initiators.
A and B are the correct answers. Initiators send requests to targets. Targets are storage resources that can be utilized by initiators. An HBA and an iSCSI NIC both function as initiators.
![]() C is incorrect because a switch port cannot be a target or an initiator. D is incorrect because astorage controller would most likely host targets, not initiators.
C is incorrect because a switch port cannot be a target or an initiator. D is incorrect because astorage controller would most likely host targets, not initiators.
Chapter 3: iSCSI Storage Network | Initiator SCSP objective 2.3, Identify Ethernet/IP SAN components
4. ![]() B is the correct answer. The RPO is the recovery point objective, and it indicates how current the restore will be. The RPO relates to how much data would be lost. In this case, the RPO is 15 minutes because snapshots are taken every 15 minutes. Any data changed or added in the last 15 minutes would be lost.
B is the correct answer. The RPO is the recovery point objective, and it indicates how current the restore will be. The RPO relates to how much data would be lost. In this case, the RPO is 15 minutes because snapshots are taken every 15 minutes. Any data changed or added in the last 15 minutes would be lost.
![]() A is incorrect. It takes 2 minutes to restore from nearline storage, so 2 minutes is the recovery time objective (RTO) for restoring from nearline storage. C and D are incorrect because 45 minutes is the RTO for restoring from tape and 30 minutes is the shortest amount of time recovery from tape could be completed.
A is incorrect. It takes 2 minutes to restore from nearline storage, so 2 minutes is the recovery time objective (RTO) for restoring from nearline storage. C and D are incorrect because 45 minutes is the RTO for restoring from tape and 30 minutes is the shortest amount of time recovery from tape could be completed.
Chapter 7: Business Continuity Objectives | Recovery Point Objective SCSP objective 4.3, Describe disaster recovery concepts
5. ![]() D is the correct answer. Given the choices provided, you are looking for a choice that increases the speed of transfers to tape. Possible solutions would include using faster tapes or utilizing multiple tapes at the same time. Atape library allows backup software to write to multiple tapes at a time so more data could be backed up in the same backup window.
D is the correct answer. Given the choices provided, you are looking for a choice that increases the speed of transfers to tape. Possible solutions would include using faster tapes or utilizing multiple tapes at the same time. Atape library allows backup software to write to multiple tapes at a time so more data could be backed up in the same backup window.
![]() A is incorrect because a disk-to-disk solution would not archive to tape as required. B is incorrect because a tape autoloader has only one drive. C is incorrect because the same amount of data would still need to be backed up to tape with D2D2T.
A is incorrect because a disk-to-disk solution would not archive to tape as required. B is incorrect because a tape autoloader has only one drive. C is incorrect because the same amount of data would still need to be backed up to tape with D2D2T.
Chapter 4: Removable Storage | Tape Media | Libraries and Autoloaders SCSP objective 4.1, Identify backup technologies
6. ![]() C is the correct answer. The packet capture shows that FTP traffic is traversing the same network as iSCSI traffic. To segment this traffic, a VLAN is needed. The VLAN would allow iSCSI traffic to traverse its own network without impacting FTP traffic, and vice versa.
C is the correct answer. The packet capture shows that FTP traffic is traversing the same network as iSCSI traffic. To segment this traffic, a VLAN is needed. The VLAN would allow iSCSI traffic to traverse its own network without impacting FTP traffic, and vice versa.
![]() A is incorrect because increasing the priority of iSCSI would impact the FTP transfers. B is incorrect because decreasing the FTP priority would also impact FTP transfers. D is incorrect because the problem is not with excessive CPU processing.
A is incorrect because increasing the priority of iSCSI would impact the FTP transfers. B is incorrect because decreasing the FTP priority would also impact FTP transfers. D is incorrect because the problem is not with excessive CPU processing.
Chapter 5: Network Virtualization | Methods | VLAN SCSP objective 1.4, Describe virtualization concepts and techniques
7. ![]() A is the correct answer. Call Home is a feature of computing equipment that allows the device to send relevant alerts to the equipment vendor so that the vendor can respond independently. This allows for quicker response to critical issues because local resources do not have to analyze the logs or contact support with a trouble ticket to begin the process of resolving the issue.
A is the correct answer. Call Home is a feature of computing equipment that allows the device to send relevant alerts to the equipment vendor so that the vendor can respond independently. This allows for quicker response to critical issues because local resources do not have to analyze the logs or contact support with a trouble ticket to begin the process of resolving the issue.
![]() B is incorrect because the storage vendor did not have to review event logs to receive the alert. C is incorrect because the vendor received the alert automatically and did not need to connect to the device to look through the logs. D is incorrect because SNMP traps are used locally and would not be delivered to the storage vendor.
B is incorrect because the storage vendor did not have to review event logs to receive the alert. C is incorrect because the vendor received the alert automatically and did not need to connect to the device to look through the logs. D is incorrect because SNMP traps are used locally and would not be delivered to the storage vendor.
Chapter 6: Storage Monitoring, Alerting, and Reporting | Alerting Methods SCSP objective 5.2, Identify storage management technologies
8. ![]() C is the correct answer. Of the available choices, SSD offers much greater speeds than SCSI, SAS, or SATA, but SSD is not available in as large of a capacity as SATA disks.
C is the correct answer. Of the available choices, SSD offers much greater speeds than SCSI, SAS, or SATA, but SSD is not available in as large of a capacity as SATA disks.
![]() A,B, and D are incorrect because SSD is faster than SCSI, SAS, or SATA.
A,B, and D are incorrect because SSD is faster than SCSI, SAS, or SATA.
Chapter 1: Available Disk Interfaces and Their Characteristics SCSP objective 3.4, Describe disk technologies
9. ![]() B is the correct answer. Domain IDs must be unique on the SAN, so two virtual SANs must be created to allow for the same domain ID.
B is the correct answer. Domain IDs must be unique on the SAN, so two virtual SANs must be created to allow for the same domain ID.
![]() A, C, and D are incorrect; they are all imaginary concepts that sound similar to real concepts.
A, C, and D are incorrect; they are all imaginary concepts that sound similar to real concepts.
Chapter 5: Network Virtualization | Methods | VSAN SCSP objective 1.4, Describe virtualization concepts and techniques
10. ![]() A is the correct answer. The multipathed server has two connections, but they are going to the same switch, and that is why both connections were lost when the switch died. Cabling each HBA to a different switch will guard against single switch failure.
A is the correct answer. The multipathed server has two connections, but they are going to the same switch, and that is why both connections were lost when the switch died. Cabling each HBA to a different switch will guard against single switch failure.
![]() B is incorrect because the software is working fine. This is a physical cabling issue. C is incorrect because the ports should be on different switches, not in a LAG group. D is incorrect because failover is not configured on the zone level.
B is incorrect because the software is working fine. This is a physical cabling issue. C is incorrect because the ports should be on different switches, not in a LAG group. D is incorrect because failover is not configured on the zone level.
Chapter 9: Redundancy | Path/Bus | Multipath SCSP objective 4.3, Describe disaster recovery concepts
11. ![]() A is the correct answer. The figure shows two cables on each storage array, but they are going to one switch each. For the systems to be configured for high availability, the storage arrays should have a connection to both switches to protect against a switch failure.
A is the correct answer. The figure shows two cables on each storage array, but they are going to one switch each. For the systems to be configured for high availability, the storage arrays should have a connection to both switches to protect against a switch failure.
![]() B is incorrect because the switches have an ISL between them. C is incorrect because the hosts have redundant connections to both switches, and D is incorrect because the ISL connects all switches.
B is incorrect because the switches have an ISL between them. C is incorrect because the hosts have redundant connections to both switches, and D is incorrect because the ISL connects all switches.
Chapter 9: Storage Architecture Components | High Availability SCSP objective 4.3, Describe disaster recovery concepts
12. ![]() C is the correct answer. ANAS hosts shares using protocols such as NFS and CIFS.
C is the correct answer. ANAS hosts shares using protocols such as NFS and CIFS.
![]() A is incorrect because iSCSI uses a block-level architecture and the iSCSI protocol, not NFS or CIFS. B is incorrect because SaaS is a cloud-based application, but this would require StaaS, cloud-based storage. D is incorrect because a DAS would provide access only to a locally attached device, and it would not support NFS or CIFS.
A is incorrect because iSCSI uses a block-level architecture and the iSCSI protocol, not NFS or CIFS. B is incorrect because SaaS is a cloud-based application, but this would require StaaS, cloud-based storage. D is incorrect because a DAS would provide access only to a locally attached device, and it would not support NFS or CIFS.
Chapter 2: Network Attached Storage SCSP objective 2.1, Identify NAS components
13. ![]() A, C, and E are the correct answers. Answer A would increase the storage available in the pool, and then the share would expand as necessary to consume the space when it needs it. Answer C would work because this would increase the available space to that individual folder by mounting the extra space as a folder. E would work because it would utilize the same directory structure while pointing the folder that is running out of space to the new disks with available storage.
A, C, and E are the correct answers. Answer A would increase the storage available in the pool, and then the share would expand as necessary to consume the space when it needs it. Answer C would work because this would increase the available space to that individual folder by mounting the extra space as a folder. E would work because it would utilize the same directory structure while pointing the folder that is running out of space to the new disks with available storage.
![]() B is incorrect because extending a volume works only within a single RAID set or storage pool. To extend the volume, both RAID sets would need to belong to the same storage pool. D is incorrect because RAID sets cannot be modified once they are created. To add more disks to a RAID set, the data would need to be migrated to alternate storage, and then the RAID set could be deleted and re-created as a larger RAID set.
B is incorrect because extending a volume works only within a single RAID set or storage pool. To extend the volume, both RAID sets would need to belong to the same storage pool. D is incorrect because RAID sets cannot be modified once they are created. To add more disks to a RAID set, the data would need to be migrated to alternate storage, and then the RAID set could be deleted and re-created as a larger RAID set.
Chapter 1: Hosts Interaction with Disks | File Systems SCSP objective 1.2, Describe host-based functions for storage
14. ![]() B is the correct answer. Two hot spares are needed. One hot spare is needed to cover the 500GB SATA disk because a SAS disk cannot be a hot spare for a SATA, and vice versa. Another disk is needed to cover the SAS disks. A400GB SAS 15k disk can be a hot spare for the 300 or 400GB SAS disk. Please note that a 300GB SAS 15k disk would not be able to function as a hot spare for both because it would not have enough capacity if a 400GB SAS disk failed.
B is the correct answer. Two hot spares are needed. One hot spare is needed to cover the 500GB SATA disk because a SAS disk cannot be a hot spare for a SATA, and vice versa. Another disk is needed to cover the SAS disks. A400GB SAS 15k disk can be a hot spare for the 300 or 400GB SAS disk. Please note that a 300GB SAS 15k disk would not be able to function as a hot spare for both because it would not have enough capacity if a 400GB SAS disk failed.
![]() A is incorrect because a SAS disk cannot be used as a hot spare to a SATA disk. C is incorrect because a single SAS disk of at least 400GB can be used as a spare for all the SAS disks. D is incorrect because SSD cannot be used as a hot spare for SAS or SATA.
A is incorrect because a SAS disk cannot be used as a hot spare to a SATA disk. C is incorrect because a single SAS disk of at least 400GB can be used as a spare for all the SAS disks. D is incorrect because SSD cannot be used as a hot spare for SAS or SATA.
Chapter 1: Multiple Disks for Larger Storage and Fault Tolerance | RAID Levels SCSP objective 3.3, Describe the different RAID levels
15. ![]() A is the correct answer. Each RAID 5 group will require one drive for parity, and the solution requires a drive for a hot spare, so that is three drives. To get 5TB of space using 500GB drives, 10 drives are required, so the solution requires 13 drives. This would be two 5+1 RAID sets and a hot spare.
A is the correct answer. Each RAID 5 group will require one drive for parity, and the solution requires a drive for a hot spare, so that is three drives. To get 5TB of space using 500GB drives, 10 drives are required, so the solution requires 13 drives. This would be two 5+1 RAID sets and a hot spare.
![]() B is incorrect because this does not include the hot spare. C might seem right if you forgot that both RAID sets need a parity disk, but it is incorrect. D might seem right if you forgot that both RAID sets need a parity disk and that the solution requires a hot spare.
B is incorrect because this does not include the hot spare. C might seem right if you forgot that both RAID sets need a parity disk, but it is incorrect. D might seem right if you forgot that both RAID sets need a parity disk and that the solution requires a hot spare.
Chapter 1: Multiple Disks for Larger Storage and Fault Tolerance | RAID Levels SCSP objective 3.3, Describe the different RAID levels
16. ![]() C is the correct answer. You would need to start with the full backup. Since the scenario is using incremental backups, you need to restore all incrementals since the last full backup, so this includes the Sunday 10 A.M., 10 P.M.; Monday 10 A.M., 10 P.M.; Tuesday 10 A.M., 10 P.M.; and Wednesday 10 A.M. backups.
C is the correct answer. You would need to start with the full backup. Since the scenario is using incremental backups, you need to restore all incrementals since the last full backup, so this includes the Sunday 10 A.M., 10 P.M.; Monday 10 A.M., 10 P.M.; Tuesday 10 A.M., 10 P.M.; and Wednesday 10 A.M. backups.
![]() A is incorrect because a backup was not taken at 5 P.M. B is incorrect because incremental backups require that each incremental following the full backup be restored in sequence. This choice restores only the latest incremental, so it would not work. D is incorrect because a full backup needs to be restored before the incremental backups can be restored.
A is incorrect because a backup was not taken at 5 P.M. B is incorrect because incremental backups require that each incremental following the full backup be restored in sequence. This choice restores only the latest incremental, so it would not work. D is incorrect because a full backup needs to be restored before the incremental backups can be restored.
Chapter 7: Backup Reliability | Backup and Restore Methods | Incremental SCSP objective 4.2, Describe backup types
17. ![]() C is the correct answer. ARAID 10 is a stripe of mirrors. The smallest stripe requires two sets, and each mirror set requires two drives. The math is 2 × 2 = 4, so you need four drives at minimum. RAID 10 sets will always have an even number of drives.
C is the correct answer. ARAID 10 is a stripe of mirrors. The smallest stripe requires two sets, and each mirror set requires two drives. The math is 2 × 2 = 4, so you need four drives at minimum. RAID 10 sets will always have an even number of drives.
![]() A is incorrect because a single drive cannot make any of the RAID sets. B is incorrect because a RAID 10 is a stripe of mirrors, so it requires multiple mirrors, each consisting of two drives. This means that a RAID 10 set will be an even number. This also eliminates choice D.
A is incorrect because a single drive cannot make any of the RAID sets. B is incorrect because a RAID 10 is a stripe of mirrors, so it requires multiple mirrors, each consisting of two drives. This means that a RAID 10 set will be an even number. This also eliminates choice D.
Chapter 1: Multiple Disks for Larger Storage and Fault Tolerance | RAID Levels SCSP objective 3.3, Describe the different RAID levels
18. ![]() D is the correct answer. Storage as a Service would present the files to users, but the files would be stored in the cloud.
D is the correct answer. Storage as a Service would present the files to users, but the files would be stored in the cloud.
![]() A is incorrect because SaaS is a cloud-based application. B is incorrect because PaaS is a cloud-based system and database. C is incorrect because CaaS is not a cloud solution. E is incorrect because IaaS is a cloud-based system with networking and computing resources.
A is incorrect because SaaS is a cloud-based application. B is incorrect because PaaS is a cloud-based system and database. C is incorrect because CaaS is not a cloud solution. E is incorrect because IaaS is a cloud-based system with networking and computing resources.
Chapter 9: Storage Architecture Components | Cloud Services | Storage as a Service SCSP objective 6.2, Identify cloud storage types
19. ![]() A is the correct answer. The 2 P.M. snapshot offers the latest backup, and it can be recovered quickly.
A is the correct answer. The 2 P.M. snapshot offers the latest backup, and it can be recovered quickly.
![]() B is incorrect because the snapshot can be applied without first applying other backups. C is incorrect because resetting the integrity error will not solve the problem. It will remove the error from sight only until it appears again. D is incorrect because taking the node out of the cluster would move the resource to another node, which would also report an integrity error.
B is incorrect because the snapshot can be applied without first applying other backups. C is incorrect because resetting the integrity error will not solve the problem. It will remove the error from sight only until it appears again. D is incorrect because taking the node out of the cluster would move the resource to another node, which would also report an integrity error.
Chapter 7: Backup Locations | Array-Based Backups | Snapshot SCSP objective 4.2, Describe backup types
20. ![]() C is the correct answer. Since the LUN was deleted, the snapshot will not work since the snapshot stored only files that changed. Anew LUN will need to be created, and then the full backup can be restored to it.
C is the correct answer. Since the LUN was deleted, the snapshot will not work since the snapshot stored only files that changed. Anew LUN will need to be created, and then the full backup can be restored to it.
![]() A is incorrect because the snapshot would not work since it holds changes only to the LUN and the entire LUN has been deleted. B is incorrect because there is no LUN to restore to. Also, the snapshot is associated with a LUN, so the snapshot would be lost when the LUN was removed. D is incorrect because the LUN is not available to restore to.
A is incorrect because the snapshot would not work since it holds changes only to the LUN and the entire LUN has been deleted. B is incorrect because there is no LUN to restore to. Also, the snapshot is associated with a LUN, so the snapshot would be lost when the LUN was removed. D is incorrect because the LUN is not available to restore to.
Chapter 7: Backup Reliability | Backup and Restore Methods SCSP objective 4.2, Describe backup types
21. ![]() A and C are the correct answers. Traffic that is directed on the second NIC is not going through because either the switch is offline or the second controller is not configured properly.
A and C are the correct answers. Traffic that is directed on the second NIC is not going through because either the switch is offline or the second controller is not configured properly.
![]() B is incorrect because maintenance mode would restrict access to the unit entirely. D is incorrect because lost power would cause the entire unit to be unavailable. E is incorrect because a lack of VLAN configuration would result in the same experience on both switches if the solution worked at all. It would not result in the connectivity errors for just one NIC.
B is incorrect because maintenance mode would restrict access to the unit entirely. D is incorrect because lost power would cause the entire unit to be unavailable. E is incorrect because a lack of VLAN configuration would result in the same experience on both switches if the solution worked at all. It would not result in the connectivity errors for just one NIC.
Chapter 12: Network Troubleshooting SCSP objective 2.1, Identify NAS components
22. ![]() D is the correct answer. Cable management does not extend the life of rack equipment.
D is the correct answer. Cable management does not extend the life of rack equipment.
![]() A is incorrect because cable management can keep cables away from air intake and exhaust vents. B is incorrect because bundled data cables can be routed away from bundled power cables with cable management. C is incorrect because cable management keeps the cables together so that they are not easily bumped or pulled on. It is much more difficult to stretch a set of bundled cables that are attached to supporting structures than it would be to stretch a single cable hanging loose from the back of a rack.
A is incorrect because cable management can keep cables away from air intake and exhaust vents. B is incorrect because bundled data cables can be routed away from bundled power cables with cable management. C is incorrect because cable management keeps the cables together so that they are not easily bumped or pulled on. It is much more difficult to stretch a set of bundled cables that are attached to supporting structures than it would be to stretch a single cable hanging loose from the back of a rack.
Chapter 10: Facilities | Cable Management SCSP objective 1.5, Describe data storage planning for various business applications
23. ![]() A is the correct answer. Ahigh cache hit ratio means that more data is being returned directly from cache instead of having to seek from disk first.
A is the correct answer. Ahigh cache hit ratio means that more data is being returned directly from cache instead of having to seek from disk first.
![]() B is incorrect because latency is related to distance, so a high cache hit ratio would not impact this. C is incorrect because simple utilization of system cache is not an advantage. D is incorrect because deduplication is not performed in cache hits.
B is incorrect because latency is related to distance, so a high cache hit ratio would not impact this. C is incorrect because simple utilization of system cache is not an advantage. D is incorrect because deduplication is not performed in cache hits.
Chapter 12: Optimize Performance | Cache | Cache Hit and Miss SCSP objective 1.6, Describe how to improve performance for host applications
24. ![]() E is the correct answer. The scenario requires 10GigE spanning 75 meters. Cat6a is the only solution that can meet both requirements.
E is the correct answer. The scenario requires 10GigE spanning 75 meters. Cat6a is the only solution that can meet both requirements.
![]() A is incorrect because the cables from the wiring closet to the rest of the office can handle the required 1Gbps, and Cat6 cables from the wiring closet to the server room would not provide the 10GigE connectivity because Cat6 only provides 10GigE at up to 55 meters. B is incorrect because Cat6 only provides 10GigE at up to 55 meters. C is incorrect because fiber cabling would not be able to provide Ethernet. D is incorrect because the Cat5e cables do not need to be replaced and fiber would not support Ethernet.
A is incorrect because the cables from the wiring closet to the rest of the office can handle the required 1Gbps, and Cat6 cables from the wiring closet to the server room would not provide the 10GigE connectivity because Cat6 only provides 10GigE at up to 55 meters. B is incorrect because Cat6 only provides 10GigE at up to 55 meters. C is incorrect because fiber cabling would not be able to provide Ethernet. D is incorrect because the Cat5e cables do not need to be replaced and fiber would not support Ethernet.
Chapter 4: Cables | Copper Cables | Cat6a SCSP objective 1.1, Identify host connectivity components used in a support matrix
25. ![]() B is the correct answer. Adisk-to-disk-to-tape solution allows for backups to be quickly written from the storage device to another disk, minimizing the duration of the backup job on the storage system. The data is then written to tape without impacting the production environment.
B is the correct answer. Adisk-to-disk-to-tape solution allows for backups to be quickly written from the storage device to another disk, minimizing the duration of the backup job on the storage system. The data is then written to tape without impacting the production environment.
![]() A is incorrect because directly writing to tape would impact the storage systems for a longer period than writing to disk would. C is incorrect because NDMP would allow the storage devices to talk to the backup tapes directly, but this solution does not specify what else would be used to reduce the backup window. D is incorrect because disk to disk would not result in the data being archived to tape.
A is incorrect because directly writing to tape would impact the storage systems for a longer period than writing to disk would. C is incorrect because NDMP would allow the storage devices to talk to the backup tapes directly, but this solution does not specify what else would be used to reduce the backup window. D is incorrect because disk to disk would not result in the data being archived to tape.
Chapter 7: Backup Locations | Disk-to-Disk-to-Tape SCSP objective 4.2, Describe backup types
26. ![]() D is the correct answer. With storage tiers, the data that is most frequently used is placed on the fastest disks.
D is the correct answer. With storage tiers, the data that is most frequently used is placed on the fastest disks.
![]() A is incorrect because storage tiering does not replicate to other sites. B is incorrect because storage tiering does not remove duplicates. Duplicates would be removed with deduplication software. C is incorrect because storage tiering does not necessarily implement or enforce retention policies. Retention policies would need to be enforced through additional software controls, but they could utilize archival tiers to store some data.
A is incorrect because storage tiering does not replicate to other sites. B is incorrect because storage tiering does not remove duplicates. Duplicates would be removed with deduplication software. C is incorrect because storage tiering does not necessarily implement or enforce retention policies. Retention policies would need to be enforced through additional software controls, but they could utilize archival tiers to store some data.
Chapter 11: Information Lifecycle Management | Storage Tiers SCSP objective 5.2, Identify storage management technologies
27. ![]() B is the correct answer. GFS backup schedules use daily, weekly, and monthly backups. Daily backups are the sons, weekly the fathers, and monthly the grandfathers, so daily is the correct answer.
B is the correct answer. GFS backup schedules use daily, weekly, and monthly backups. Daily backups are the sons, weekly the fathers, and monthly the grandfathers, so daily is the correct answer.
![]() A is incorrect because GFS backup schedules do not include hourly backups. C and D are incorrect because GFS specifies the backup intervals, not type. E is incorrect because daily backups occur more frequently than weekly backups.
A is incorrect because GFS backup schedules do not include hourly backups. C and D are incorrect because GFS specifies the backup intervals, not type. E is incorrect because daily backups occur more frequently than weekly backups.
Chapter 7: Backup Frequency | Rotation Schemes SCSP objective 4.3, Describe disaster recovery concepts
28. ![]() B is the correct answer. FCoE uses Ethernet at layer 2, but higher layers are implemented with the FC protocol stack.
B is the correct answer. FCoE uses Ethernet at layer 2, but higher layers are implemented with the FC protocol stack.
![]() A is incorrect because iSCSI does not utilize FC at any layer. C is incorrect because while FCIP does use Ethernet, it also uses IP. D is incorrect because it also uses IP.
A is incorrect because iSCSI does not utilize FC at any layer. C is incorrect because while FCIP does use Ethernet, it also uses IP. D is incorrect because it also uses IP.
Chapter 3: Fibre Channel Storage Network | Protocols | FCoE SCSP objective 2.2, Identify Fibre Channel SAN components
29. ![]() C is the correct answer. If seven drives are in a RAID 6 (5 + 2), two drives are used for parity, and five are available for data: 5 × 400 = 2,000.
C is the correct answer. If seven drives are in a RAID 6 (5 + 2), two drives are used for parity, and five are available for data: 5 × 400 = 2,000.
![]() A is incorrect because this assumes that all seven drives are used for data, but two are required for parity. B would be the right answer if this question asked about RAID 4, which uses only one drive for parity, but this question is using RAID 6. D is incorrect because only two drives are required for parity. The solution in choiceDuses three drives for parity.
A is incorrect because this assumes that all seven drives are used for data, but two are required for parity. B would be the right answer if this question asked about RAID 4, which uses only one drive for parity, but this question is using RAID 6. D is incorrect because only two drives are required for parity. The solution in choiceDuses three drives for parity.
Chapter 1: Multiple Disks for Larger Storage and Fault Tolerance | RAID Levels SCSP objective 3.3, Describe the different RAID levels
30. ![]() A is the correct answer. Telnet transmits data in plain text, so another solution is needed to encrypt the traffic. The first step is to remove access to Telnet by disabling port 23 on the firewall. Next, a VPN would allow for the Telnet traffic to be encapsulated in an encrypted channel.
A is the correct answer. Telnet transmits data in plain text, so another solution is needed to encrypt the traffic. The first step is to remove access to Telnet by disabling port 23 on the firewall. Next, a VPN would allow for the Telnet traffic to be encapsulated in an encrypted channel.
![]() B is incorrect because the question states that Telnet must be used, not SSH. C is incorrect because Telnet does not support encryption. D is incorrect because a locally attached serial cable would require local access, not remote access.
B is incorrect because the question states that Telnet must be used, not SSH. C is incorrect because Telnet does not support encryption. D is incorrect because a locally attached serial cable would require local access, not remote access.
Chapter 6: Storage Administration | CLI | Telnet Chapter 8: Encryption | Data in Motion | VPN SCSP objective 5.1, Describe storage security methods
31. ![]() D is the correct answer. High availability must be able to support the loss of a single component, so redundancy is necessary.
D is the correct answer. High availability must be able to support the loss of a single component, so redundancy is necessary.
![]() A is incorrect because monitoring can alert staff to a failure but not prevent it. B is incorrect because a higher SLA just increases the burden on the organization but does nothing to implement high availability. C is incorrect because offsite backups offer business continuity but not high availability. The backups would need to be restored, and this would take time, during which the system would be unavailable.
A is incorrect because monitoring can alert staff to a failure but not prevent it. B is incorrect because a higher SLA just increases the burden on the organization but does nothing to implement high availability. C is incorrect because offsite backups offer business continuity but not high availability. The backups would need to be restored, and this would take time, during which the system would be unavailable.
Chapter 9: Storage Architecture Components | High Availability SCSP objective 4.3, Describe disaster recovery concepts
32. ![]() A is the correct answer. Hot aisles are areas where hot air from computing equipment is expelled and directed back to cooling equipment, while computing equipment draws cool air from cold aisles.
A is the correct answer. Hot aisles are areas where hot air from computing equipment is expelled and directed back to cooling equipment, while computing equipment draws cool air from cold aisles.
![]() B is incorrect because high-density racks and low-density racks both would need to be directed so that their hot air flows into hot aisles. C and D are incorrect because hot and cold aisles do not aid in emergency evacuations, and neither do they aid in capacity planning.
B is incorrect because high-density racks and low-density racks both would need to be directed so that their hot air flows into hot aisles. C and D are incorrect because hot and cold aisles do not aid in emergency evacuations, and neither do they aid in capacity planning.
Chapter 10: Facilities | Cooling SCSP objective 1.5, Describe data storage planning for various business applications
33. ![]() B is the correct answer. To provide concurrent access, a share must be created so the CIFS or NFS protocols could be used.
B is the correct answer. To provide concurrent access, a share must be created so the CIFS or NFS protocols could be used.
![]() A is incorrect because SNMP is a monitoring protocol, not a file access protocol. C is incorrect because Telnet is a management protocol, not a file access protocol. D and E are incorrect because iSCSI and FC provide block-level access, and this would allow only one machine to access the storage at a time, and the solution requires for many users to have concurrent access.
A is incorrect because SNMP is a monitoring protocol, not a file access protocol. C is incorrect because Telnet is a management protocol, not a file access protocol. D and E are incorrect because iSCSI and FC provide block-level access, and this would allow only one machine to access the storage at a time, and the solution requires for many users to have concurrent access.
Chapter 2: Network Attached Storage | NAS File System Protocols | CIFS SCSP objective 2.1, Identify NAS components
34. ![]() C is the correct answer. The EXT3 file system is used on Linux.
C is the correct answer. The EXT3 file system is used on Linux.
![]() A is incorrect because Windows 98 supports only FAT16 and FAT32. B is incorrect because it supports only FAT and NTFS. D is incorrect because it uses the integrated file system, not EXT3. E is incorrect because Apple iOS uses the HFSX file system. Please note that the AS/400 and Apple iOS were not discussed in this book and will not be on the SCSP exam.
A is incorrect because Windows 98 supports only FAT16 and FAT32. B is incorrect because it supports only FAT and NTFS. D is incorrect because it uses the integrated file system, not EXT3. E is incorrect because Apple iOS uses the HFSX file system. Please note that the AS/400 and Apple iOS were not discussed in this book and will not be on the SCSP exam.
Chapter 1: Hosts Interaction with Disks | File Systems SCSP objective 1.2, Describe host-based functions for storage
35. ![]() D is the correct answer. The storage array is configured for active/active, but the HBAs are active/passive. When the storage array sends data on the active connection that is sent to the passive connection on the host, the traffic must traverse the ISL and then be delivered to the active port. If you are using active/active in one place, try to use active/active everywhere else.
D is the correct answer. The storage array is configured for active/active, but the HBAs are active/passive. When the storage array sends data on the active connection that is sent to the passive connection on the host, the traffic must traverse the ISL and then be delivered to the active port. If you are using active/active in one place, try to use active/active everywhere else.
![]() A is incorrect because adding more ISLs solves the symptom, not the root issue. B is incorrect because a file-level architecture cannot be used to map LUNs. C is incorrect because buffer-to-buffer credits only need to be changed on links that extend over a long distance.
A is incorrect because adding more ISLs solves the symptom, not the root issue. B is incorrect because a file-level architecture cannot be used to map LUNs. C is incorrect because buffer-to-buffer credits only need to be changed on links that extend over a long distance.
Chapter 9: Redundancy | Clustering | Active-Active SCSP objective 4.3, Describe disaster recovery concepts
36. ![]() A is the correct answer. Fibre Channel Arbitrated Loop (FC-AL) is a loop or ring, but devices are connected to hubs that implement the loop inside them. The hubs are central devices that appear like a star configuration.
A is the correct answer. Fibre Channel Arbitrated Loop (FC-AL) is a loop or ring, but devices are connected to hubs that implement the loop inside them. The hubs are central devices that appear like a star configuration.
![]() B is incorrect because FC-SW, switch fabric, is not a logical ring. It is a logical star. C is incorrect because P2P is not a physical star. It is a bus. D is incorrect because Ethernet is not a topology.
B is incorrect because FC-SW, switch fabric, is not a logical ring. It is a logical star. C is incorrect because P2P is not a physical star. It is a bus. D is incorrect because Ethernet is not a topology.
Chapter 3: Fibre Channel Storage Network | Topologies | Arbitrated Loop SCSP objective 2.2, Identify Fibre Channel SAN components
37. ![]() D is the correct answer. Arouter receives information from its neighbors on the networks that each device manages and on how many hops it takes to get to the destination through a device. If a connection fails, the routers update the number of hops to compensate so that they maintain accurate information on how to route packets through a network.
D is the correct answer. Arouter receives information from its neighbors on the networks that each device manages and on how many hops it takes to get to the destination through a device. If a connection fails, the routers update the number of hops to compensate so that they maintain accurate information on how to route packets through a network.
![]() A is incorrect because a switch does not receive information from its neighbors to make such decisions. It maintains a bridging table that it builds itself and makes only decisions on how to send data to local devices. B is incorrect because a director is just an upgraded switch. C is incorrect because a repeater just takes a signal and rebroadcasts it. It does not make a routing or forwarding decision. E is incorrect because transceivers convert one signal type to another but do not make routing or forwarding decisions.
A is incorrect because a switch does not receive information from its neighbors to make such decisions. It maintains a bridging table that it builds itself and makes only decisions on how to send data to local devices. B is incorrect because a director is just an upgraded switch. C is incorrect because a repeater just takes a signal and rebroadcasts it. It does not make a routing or forwarding decision. E is incorrect because transceivers convert one signal type to another but do not make routing or forwarding decisions.
Chapter 4: Storage Networking Devices | Router SCSP objective 3.1, Identify host to SAN components
38. ![]() A is the correct answer. ISNS is a database of targets that can be queried by initiators.
A is the correct answer. ISNS is a database of targets that can be queried by initiators.
![]() B is incorrect because iSNS does not perform monitoring or alerting functions. C is incorrect because FC addresses are registered by one of the FC services, not iSNS. D is incorrect because iSNS does not have any understanding of load balancing, nor can it configure it.
B is incorrect because iSNS does not perform monitoring or alerting functions. C is incorrect because FC addresses are registered by one of the FC services, not iSNS. D is incorrect because iSNS does not have any understanding of load balancing, nor can it configure it.
Chapter 8: Storage Visibility | iSCSI Security | iSCSI and iSNS Security SCSP objective 1.3, Identify storage mapping elements
39. ![]() D is the correct answer. Tape is an inexpensive way to archive data, and it comes in large capacities.
D is the correct answer. Tape is an inexpensive way to archive data, and it comes in large capacities.
![]() A is incorrect because it would take many DVDs to back up 400GB of data. B is incorrect because it would take many flash drives to archive this much data. C is incorrect because nearline storage is more expensive than tape.
A is incorrect because it would take many DVDs to back up 400GB of data. B is incorrect because it would take many flash drives to archive this much data. C is incorrect because nearline storage is more expensive than tape.
Chapter 4: Removable Storage SCSP objective 4.1, Identify backup technologies
40. ![]() A is the correct answer. ISLs link fiber switches together, and expansion ports (e-ports) are used to connect to other switches.
A is the correct answer. ISLs link fiber switches together, and expansion ports (e-ports) are used to connect to other switches.
![]() B is incorrect because F-ports connect to N-ports on nodes. C is incorrect because an ISL is required. D is incorrect because an ISL is required and F-ports are not used for ISLs.
B is incorrect because F-ports connect to N-ports on nodes. C is incorrect because an ISL is required. D is incorrect because an ISL is required and F-ports are not used for ISLs.
Chapter 3: Fibre Channel Storage Network | ISL SCSP objective 2.2, Identify Fibre Channel SAN components
41. ![]() D is the correct answer. Remote replication would store the data at another site, and the data could be used there if the first site becomes unavailable.
D is the correct answer. Remote replication would store the data at another site, and the data could be used there if the first site becomes unavailable.
![]() A is incorrect because offsite tapes would have to be restored to equipment, but the equipment in the scenario was consumed by the fire. B is incorrect because HSM organizes data into tiers but does not protect it against site loss. C is incorrect because snapshots are used within a storage array, and they would be lost along with the array in the fire.
A is incorrect because offsite tapes would have to be restored to equipment, but the equipment in the scenario was consumed by the fire. B is incorrect because HSM organizes data into tiers but does not protect it against site loss. C is incorrect because snapshots are used within a storage array, and they would be lost along with the array in the fire.
Chapter 9: Replication | Scope | Remote SCSP objective 1.5, Describe data storage planning for various business applications
42. ![]() B is the correct answer. Abaseline is a record of metrics under normal load. Comparing current data to the baseline will help identify items that are slower than the baseline.
B is the correct answer. Abaseline is a record of metrics under normal load. Comparing current data to the baseline will help identify items that are slower than the baseline.
![]() A is incorrect because an alert would notify of an item that is in an error condition or exceeding a threshold, but it would not be compared to the current metrics. C is incorrect because the scope defines the area affected but could not be used to compare against current metrics. D is incorrect because the logs would contain a large amount of data that would not match up to the collected metrics.
A is incorrect because an alert would notify of an item that is in an error condition or exceeding a threshold, but it would not be compared to the current metrics. C is incorrect because the scope defines the area affected but could not be used to compare against current metrics. D is incorrect because the logs would contain a large amount of data that would not match up to the collected metrics.
Chapter 6: Storage Monitoring, Alerting, and Reporting | Recording a Baseline SCSP objective 5.2, Identify storage management technologies
43. ![]() C is the correct answer. Aconsistency group ensures that a set of writes is performed on each member of the group. Items in a consistency group retain the same data, and writes that occur to one member of the group will not be fully committed until they have been implemented across all members of the consistency group.
C is the correct answer. Aconsistency group ensures that a set of writes is performed on each member of the group. Items in a consistency group retain the same data, and writes that occur to one member of the group will not be fully committed until they have been implemented across all members of the consistency group.
![]() A is incorrect because a snapshot would track changes to data from a point in time. B is incorrect because replication alone would not ensure consistency because some data may not have been replicated yet. D is incorrect because integrity groups were not discussed and are not related to replication or transaction commitment.
A is incorrect because a snapshot would track changes to data from a point in time. B is incorrect because replication alone would not ensure consistency because some data may not have been replicated yet. D is incorrect because integrity groups were not discussed and are not related to replication or transaction commitment.
Chapter 7: Backup Locations | Array-Based Backups | Consistency Group SCSP objective 4.2, Describe backup types
44. ![]() A is the correct answer. LTO3 tapes have a native capacity of 400GB and a compressed capacity of 800GB.
A is the correct answer. LTO3 tapes have a native capacity of 400GB and a compressed capacity of 800GB.
![]() B is incorrect because this is the capacity of an LTO3 tape, not an LTO4 tape. C is incorrect because this is the capacity of an LTO4 tape, not an LTO5 tape. D is incorrect because LTO2 tapes have a native capacity of 200GB and a compressed capacity of 400GB.
B is incorrect because this is the capacity of an LTO3 tape, not an LTO4 tape. C is incorrect because this is the capacity of an LTO4 tape, not an LTO5 tape. D is incorrect because LTO2 tapes have a native capacity of 200GB and a compressed capacity of 400GB.
Chapter 4: Removable Storage | Tape Media | LTO Versions SCSP objective 4.1, Identify backup technologies
45. ![]() C is the correct answer. Asynchronous replication would send data to the remote site when possible and would not wait to commit new transactions if data had not been replicated yet.
C is the correct answer. Asynchronous replication would send data to the remote site when possible and would not wait to commit new transactions if data had not been replicated yet.
![]() A is incorrect because synchronous replication would make the main database wait to commit transactions until they had been committed at the remote site as well. Since the link between sites is high latency, this would reduce performance considerably. B is incorrect because direct replication is not a form of replication. D is incorrect because the question is concerned with consistency between sites and the impact this has on production, not on where the replication is managed.
A is incorrect because synchronous replication would make the main database wait to commit transactions until they had been committed at the remote site as well. Since the link between sites is high latency, this would reduce performance considerably. B is incorrect because direct replication is not a form of replication. D is incorrect because the question is concerned with consistency between sites and the impact this has on production, not on where the replication is managed.
Chapter 9: Replication | Continuous Replication SCSP objective 1.5, Describe data storage planning for various business applications
46. ![]() C is the correct answer. Aswitch would connect the four front-end ports and the five host ports and allow communication between them.
C is the correct answer. Aswitch would connect the four front-end ports and the five host ports and allow communication between them.
![]() A is incorrect because a director is not needed in this simple situation. B is incorrect because a router would be needed only if the storage array was on a different network. D is incorrect because a repeater would only rebroadcast a signal, not allow additional connectivity.
A is incorrect because a director is not needed in this simple situation. B is incorrect because a router would be needed only if the storage array was on a different network. D is incorrect because a repeater would only rebroadcast a signal, not allow additional connectivity.
Chapter 4: Storage Networking Devices SCSP objective 3.1, Identify host to SAN components
47. ![]() C is the correct answer. There is a head at the top and bottom of each platter. All heads are attached to the same actuator arm.
C is the correct answer. There is a head at the top and bottom of each platter. All heads are attached to the same actuator arm.
![]() A is incorrect because each head does not have its own actuator arm. They are all on the same arm. B is incorrect because each head can read data only from a single platter. D is incorrect because it references disks, not platters. There is a head for each platter, not disk.
A is incorrect because each head does not have its own actuator arm. They are all on the same arm. B is incorrect because each head can read data only from a single platter. D is incorrect because it references disks, not platters. There is a head for each platter, not disk.
Chapter 1: How Disk Storage Systems Work | Physical Components | Head SCSP objective 1.1, Identify host connectivity components used in a support matrix
48. ![]() B is the correct answer. Acontroller is mounted to the base of the disk and contains an interface for sending and receiving data to a connected device.
B is the correct answer. Acontroller is mounted to the base of the disk and contains an interface for sending and receiving data to a connected device.
![]() A is incorrect because it is incomplete. The controller board operates more than just the movement of the actuator arm. C and D are incorrect because the controller board is not mounted to the top of the disk.
A is incorrect because it is incomplete. The controller board operates more than just the movement of the actuator arm. C and D are incorrect because the controller board is not mounted to the top of the disk.
Chapter 1: How Disk Storage Systems Work | Physical Components | Controller Board SCSP objective 1.1, Identify host connectivity components used in a support matrix
49. ![]() A is the correct answer. Solid state organizes data into blocks rather than tracks and selectors.
A is the correct answer. Solid state organizes data into blocks rather than tracks and selectors.
![]() B is incorrect because SSD consists of blocks made up of pages, not HDD. C is incorrect because SSD blocks are not 128 bytes. D is incorrect because logical bit addressing is not an addressing method, and SSDs do not use a master table.
B is incorrect because SSD consists of blocks made up of pages, not HDD. C is incorrect because SSD blocks are not 128 bytes. D is incorrect because logical bit addressing is not an addressing method, and SSDs do not use a master table.
Chapter 1: How Disk Storage Systems Work | Solid-State Drive SCSP objective 1.1, Identify host connectivity components used in a support matrix
50. ![]() D is the correct answer. Fibre Channel references other devices on the network by using a World Wide Name (WWN).
D is the correct answer. Fibre Channel references other devices on the network by using a World Wide Name (WWN).
![]() A is incorrect because SCAS is not a method of referencing other devices. B is incorrect because Fibre Channel does not use a reference ID. C is incorrect because a twofold security connection number is not an element of FC.
A is incorrect because SCAS is not a method of referencing other devices. B is incorrect because Fibre Channel does not use a reference ID. C is incorrect because a twofold security connection number is not an element of FC.
Chapter 3: Fibre Channel Storage Network | Components | World Wide Name SCSP objective 2.1, Identify NAS components
51. ![]() C is the correct answer. Fibre Channel layer 3 is the services layer. This layer supports striping, hunt groups, and the spanning of multiple ports.
C is the correct answer. Fibre Channel layer 3 is the services layer. This layer supports striping, hunt groups, and the spanning of multiple ports.
![]() A is incorrect because layer 3 is the services layer, not the block layer. B is incorrect because FC does not use frames, and layer 3 is the services layer, not the processing layer. D is incorrect because layer 3 is not the infrastructure layer.
A is incorrect because layer 3 is the services layer, not the block layer. B is incorrect because FC does not use frames, and layer 3 is the services layer, not the processing layer. D is incorrect because layer 3 is not the infrastructure layer.
Chapter 3: Fibre Channel Storage Network | Protocols | FCP SCSP objective 2.2, Identify Fibre Channel SAN components
52. ![]() D is the correct answer. AWWN is an 8-byte or 16-byte identifier for a network communication port on a Fibre Channel network.
D is the correct answer. AWWN is an 8-byte or 16-byte identifier for a network communication port on a Fibre Channel network.
![]() A is incorrect because a WWN is 8 or 16 bytes, not 16 or 32 bytes. B is incorrect because WWNs are used on an FC network while IP addresses are used on an IP network. C is incorrect because WWNs are used in Fibre Channel, not simple channel access.
A is incorrect because a WWN is 8 or 16 bytes, not 16 or 32 bytes. B is incorrect because WWNs are used on an FC network while IP addresses are used on an IP network. C is incorrect because WWNs are used in Fibre Channel, not simple channel access.
Chapter 3: Fibre Channel Storage Network | Components | World Wide Name SCSP objective 2.2, Identify Fibre Channel SAN components
53. ![]() C is the correct answer. Input/output operations per second (IOPS) is one of the most basic metrics used in measuring storage performance.
C is the correct answer. Input/output operations per second (IOPS) is one of the most basic metrics used in measuring storage performance.
![]() A is incorrect because FTP is used for sending and receiving files and is not a performance metric measurement method. B is incorrect because system storage monitoring is not a specific metric. D is incorrect because send receive operations per second is not a metric that is used.
A is incorrect because FTP is used for sending and receiving files and is not a performance metric measurement method. B is incorrect because system storage monitoring is not a specific metric. D is incorrect because send receive operations per second is not a metric that is used.
Chapter 12: Optimize Performance | Necessary IOPS SCSP objective 1.6, Describe how to improve performance for host applications
54. ![]() B is the correct answer. Optical cables transmit data via light impulses.
B is the correct answer. Optical cables transmit data via light impulses.
![]() A is incorrect because optical cables transmit data via light, not long-range frequencies. C and D are incorrect because optical cables use light instead of electromagnetic waves or impulses. Copper cables conduct electromagnetic waves.
A is incorrect because optical cables transmit data via light, not long-range frequencies. C and D are incorrect because optical cables use light instead of electromagnetic waves or impulses. Copper cables conduct electromagnetic waves.
Chapter 4: Cables | Optical Cables SCSP objective 1.1, Identify host connectivity components used in a support matrix
55. ![]() D is the correct answer. Aconverged network adapter (CNA) is a device capable of connecting a host to storage with connections over FC, Ethernet, or twinax connections.
D is the correct answer. Aconverged network adapter (CNA) is a device capable of connecting a host to storage with connections over FC, Ethernet, or twinax connections.
![]() A is incorrect because CNAs are not used with iSCSI. B is incorrect because it is incomplete. This is only one thing that a CNA can do. C is incorrect because a CNA is a card that is added to a host rather than being built onboard.
A is incorrect because CNAs are not used with iSCSI. B is incorrect because it is incomplete. This is only one thing that a CNA can do. C is incorrect because a CNA is a card that is added to a host rather than being built onboard.
Chapter 4: Storage Networking Devices | CNA SCSP objective 2.2, Identify Fibre Channel SAN components
56. ![]() A is the correct answer. Afiber director is a high-capacity modular switch with two or more hot-swappable power supplies and redundant routing engines, pathways, and processors.
A is the correct answer. Afiber director is a high-capacity modular switch with two or more hot-swappable power supplies and redundant routing engines, pathways, and processors.
![]() B is incorrect because a director is not a layer 3 device. C is incorrect because a director is not used for WAN connections. D is incorrect because a director does not perform filtering.
B is incorrect because a director is not a layer 3 device. C is incorrect because a director is not used for WAN connections. D is incorrect because a director does not perform filtering.
Chapter 4: Storage Networking Devices | Director SCSP objective 2.2, Identify Fibre Channel SAN components
57. ![]() C is the correct answer. Buffer underrun is a condition where the buffer is emptied during the process of burning information to a disk.
C is the correct answer. Buffer underrun is a condition where the buffer is emptied during the process of burning information to a disk.
![]() A is incorrect because the buffer underrun is a specific failure when the buffer is empty during the burn process. There are many errors from the write process that would not be considered buffer underrun. B is incorrect because buffer underrun is not related to scratches on the disk. D is incorrect because a drive that cannot read a disk at the optimal speed is a speed mismatch, and this choice is related to reads rather than writes.
A is incorrect because the buffer underrun is a specific failure when the buffer is empty during the burn process. There are many errors from the write process that would not be considered buffer underrun. B is incorrect because buffer underrun is not related to scratches on the disk. D is incorrect because a drive that cannot read a disk at the optimal speed is a speed mismatch, and this choice is related to reads rather than writes.
Chapter 4: Removable Storage | Optical Media SCSP objective 4.1, Identify backup technologies
58. ![]() A is the correct answer. SNIA describes storage virtualization as the application of virtualization to storage services or devices for the purposes of aggregating functions or devices, hiding complexity, or adding new capabilities to lower-level storage resources.
A is the correct answer. SNIA describes storage virtualization as the application of virtualization to storage services or devices for the purposes of aggregating functions or devices, hiding complexity, or adding new capabilities to lower-level storage resources.
![]() B is incorrect because storage virtualization virtualizes storage resources, not software. C is incorrect because with storage virtualization there are proprietary storage virtualization technologies that do not offer interoperability. D is incorrect because storage virtualization is not used to limit data access.
B is incorrect because storage virtualization virtualizes storage resources, not software. C is incorrect because with storage virtualization there are proprietary storage virtualization technologies that do not offer interoperability. D is incorrect because storage virtualization is not used to limit data access.
Chapter 5: Types of Storage Virtualization SCSP objective 1.4, Describe virtualization concepts and techniques
59. ![]() A is the correct answer. The file/record layer is the layer that organizes the information required by the application and interfaces with the application.
A is the correct answer. The file/record layer is the layer that organizes the information required by the application and interfaces with the application.
![]() B is incorrect because the mapping of logical addresses to physical addresses is how disks use virtualization. C is incorrect because this choice describes block virtualization. D is incorrect because this describes tape virtualization.
B is incorrect because the mapping of logical addresses to physical addresses is how disks use virtualization. C is incorrect because this choice describes block virtualization. D is incorrect because this describes tape virtualization.
Chapter 5: Types of Storage Virtualization SCSP objective 1.4, Describe virtualization concepts and techniques
60. ![]() A is the correct answer. Privileged provisioning is not a form of storage provisioning.
A is the correct answer. Privileged provisioning is not a form of storage provisioning.
![]() B is incorrect because LUN provisioning is a form of provisioning of logical units. C is incorrect because thick provisioning creates a logical unit of a specified size. D is also incorrect because thin provisioning creates a logical unit that is variable in size.
B is incorrect because LUN provisioning is a form of provisioning of logical units. C is incorrect because thick provisioning creates a logical unit of a specified size. D is also incorrect because thin provisioning creates a logical unit that is variable in size.
Chapter 6: Storage Provisioning SCSP objective 1.3, Identify storage mapping elements
61. ![]() D is the correct answer. In-band or out-of-band virtualization can consolidate the virtual platform for network storage management.
D is the correct answer. In-band or out-of-band virtualization can consolidate the virtual platform for network storage management.
![]() A is incorrect because only out-of-band virtualization optimizes SAN utilization and performance. B is incorrect because only out-of-band virtualization offloads storage management from the host since the management device exists outside the host-to-SAN relationship. C is incorrect because only out-of-band virtualization avoids latency.
A is incorrect because only out-of-band virtualization optimizes SAN utilization and performance. B is incorrect because only out-of-band virtualization offloads storage management from the host since the management device exists outside the host-to-SAN relationship. C is incorrect because only out-of-band virtualization avoids latency.
Chapter 5: Types of Storage Virtualization SCSP objective 1.4, Describe virtualization concepts and techniques
62. ![]() B is the correct answer. Host virtualization is not a type of storage virtualization.
B is the correct answer. Host virtualization is not a type of storage virtualization.
![]() A, C, and D are incorrect because disk, block, and tape virtualization are all types of storage virtualization.
A, C, and D are incorrect because disk, block, and tape virtualization are all types of storage virtualization.
Chapter 5: Types of Storage Virtualization SCSP objective 1.4, Describe virtualization concepts and techniques
63. ![]() D is the correct answer. Cache is high-speed memory that can be used to service I/O requests faster than accessing the disk.
D is the correct answer. Cache is high-speed memory that can be used to service I/O requests faster than accessing the disk.
![]() A is incorrect. While memory is faster than disk, it is not used to service I/O requests. B is incorrect because logical disks are not faster than physical disks. C is incorrect because SSD is a form of physical disk.
A is incorrect. While memory is faster than disk, it is not used to service I/O requests. B is incorrect because logical disks are not faster than physical disks. C is incorrect because SSD is a form of physical disk.
Chapter 12: Optimize Performance | Cache SCSP objective 1.6, Describe how to improve performance for host applications
64. ![]() A is the correct answer. The Common Information Model is an object-oriented approach to organizing information where objects have attributes and each is created from a class that describes the format of the object.
A is the correct answer. The Common Information Model is an object-oriented approach to organizing information where objects have attributes and each is created from a class that describes the format of the object.
![]() B is incorrect because this describes in-band management. C is incorrect because it describes thin provisioning. D is incorrect because it describes setting thresholds.
B is incorrect because this describes in-band management. C is incorrect because it describes thin provisioning. D is incorrect because it describes setting thresholds.
Chapter 6: Management Protocols | WBEM SCSP objective 5.2, Identify storage management technologies
65. ![]() D is the correct answer. When in-band storage management is utilized, data as well as management and monitoring information travel over the same path.
D is the correct answer. When in-band storage management is utilized, data as well as management and monitoring information travel over the same path.
![]() A is incorrect because it describes out-of-band management. B is incorrect because in-band management is concerned with the path the data uses, not whether it is an appliance. Also, this answer has the management and monitoring of data occurring on the appliance, but the transfer of data is not mentioned. C is incorrect because this separates the data from the management and monitoring, as would be performed in out-of-band management.
A is incorrect because it describes out-of-band management. B is incorrect because in-band management is concerned with the path the data uses, not whether it is an appliance. Also, this answer has the management and monitoring of data occurring on the appliance, but the transfer of data is not mentioned. C is incorrect because this separates the data from the management and monitoring, as would be performed in out-of-band management.
Chapter 6: Management Protocols | In-Band vs. Out-of-Band Management SCSP objective 5.2, Identify storage management technologies
66. ![]() A is the correct answer. Appliance-based data migration is data migration in which stand-alone network appliances migrate files and volumes, interfacing with storage systems and providing a separate interface for managing the replication.
A is the correct answer. Appliance-based data migration is data migration in which stand-alone network appliances migrate files and volumes, interfacing with storage systems and providing a separate interface for managing the replication.
![]() B is incorrect because appliance-based migration can operate on data or applications. It is not what is being moved, but how it is being moved that this question is concerned with. C is incorrect because the data on the appliances themselves is not being migrated in this situation. D is incorrect because an appliance would require configuration and possibly some customization for it to work.
B is incorrect because appliance-based migration can operate on data or applications. It is not what is being moved, but how it is being moved that this question is concerned with. C is incorrect because the data on the appliances themselves is not being migrated in this situation. D is incorrect because an appliance would require configuration and possibly some customization for it to work.
Chapter 11: Deduplication and Compression | Deduplication Software and Appliances SCSP objective 5.3, Describe data reduction techniques
67. ![]() D is the correct answer. Thick logical units take up the same amount of space as is presented to the host operating system.
D is the correct answer. Thick logical units take up the same amount of space as is presented to the host operating system.
![]() A is incorrect because thick logical units take up the assigned amount of space, so if 100GB is allocated, the logical unit will be 100GB even if only 20GB is stored in it. B is incorrect because thick logical units do not allocate additional space beyond what is assigned. C is incorrect because thick logical units can be any size.
A is incorrect because thick logical units take up the assigned amount of space, so if 100GB is allocated, the logical unit will be 100GB even if only 20GB is stored in it. B is incorrect because thick logical units do not allocate additional space beyond what is assigned. C is incorrect because thick logical units can be any size.
Chapter 6: Storage Provisioning | Thick Provisioning SCSP objective 1.3, Identify storage mapping elements
68. ![]() A is the correct answer. Data integrity is assurance that data remains unchanged after creating, modifying, copying, completing, or otherwise operating on data.
A is the correct answer. Data integrity is assurance that data remains unchanged after creating, modifying, copying, completing, or otherwise operating on data.
![]() B is incorrect because having backups does not mean you will know when to use them or when data has been changed or corrupted. C is incorrect because data tampering is only one way data integrity could be lost. Encryption is primarily used to protect confidentiality, not integrity. D is incorrect because integrity is not concerned with how the data is used, just that it remains unchanged in between authorized changes.
B is incorrect because having backups does not mean you will know when to use them or when data has been changed or corrupted. C is incorrect because data tampering is only one way data integrity could be lost. Encryption is primarily used to protect confidentiality, not integrity. D is incorrect because integrity is not concerned with how the data is used, just that it remains unchanged in between authorized changes.
Chapter 7: Backup Reliability | Backup Reliability Methods | Data Integrity SCSP objective 4.2, Describe backup types
69. ![]() C is the correct answer. Workflow error is much too specific to be considered a broad classification for a cause of system outages.
C is the correct answer. Workflow error is much too specific to be considered a broad classification for a cause of system outages.
![]() A, B, and D are incorrect because human error, intentional error, and systematic error can all be considered a broad classification for the cause of system outages.
A, B, and D are incorrect because human error, intentional error, and systematic error can all be considered a broad classification for the cause of system outages.
Chapter 9: Storage Architecture Components | High Availability SCSP objective 4.3, Describe disaster recovery concepts
70. ![]() A is the correct answer. The primary objective of business continuity planning is to provide a proactive strategy to prevent or limit the impact of system failures and to rapidly restore operations should such events occur.
A is the correct answer. The primary objective of business continuity planning is to provide a proactive strategy to prevent or limit the impact of system failures and to rapidly restore operations should such events occur.
![]() B is incorrect because this describes disaster recovery. C and D are incorrect because these address only part of business continuity.
B is incorrect because this describes disaster recovery. C and D are incorrect because these address only part of business continuity.
Chapter 7: Business Continuity Objectives SCSP objective 4.3, Describe disaster recovery concepts
71. ![]() B is the correct answer. The cost per year in this case is 18 hours of lost productivity. Every other month means six times per year, and the loss is three hours per month: 6 × 3 = 18.
B is the correct answer. The cost per year in this case is 18 hours of lost productivity. Every other month means six times per year, and the loss is three hours per month: 6 × 3 = 18.
![]() A, C, and D are incorrect because 6 months × 3 hours = 18 hours of lost productivity, not 12, 24, or 36.
A, C, and D are incorrect because 6 months × 3 hours = 18 hours of lost productivity, not 12, 24, or 36.
Chapter 7: Business Continuity Objectives | Data Value and Risk SCSP objective 4.3, Describe disaster recovery concepts
72. ![]() A is the correct answer. You must first know how available the system should be in order to determine how much redundancy should be put in place to achieve that availability. This availability measurement is usually expressed as a percentage of uptime such as 99.9 percent.
A is the correct answer. You must first know how available the system should be in order to determine how much redundancy should be put in place to achieve that availability. This availability measurement is usually expressed as a percentage of uptime such as 99.9 percent.
![]() B is incorrect because logical block addressing will help locate data on disk, not identify how much redundancy is needed. C is incorrect because the failover system is a component of redundancy that might be put in place, but it is not a factor to determine what is needed. D is incorrect because replication is a method for achieving redundancy, so it should not be used to determine whether redundancy should be put in place. The decision should be based on a business decision on the required uptime.
B is incorrect because logical block addressing will help locate data on disk, not identify how much redundancy is needed. C is incorrect because the failover system is a component of redundancy that might be put in place, but it is not a factor to determine what is needed. D is incorrect because replication is a method for achieving redundancy, so it should not be used to determine whether redundancy should be put in place. The decision should be based on a business decision on the required uptime.
Chapter 9: Storage Architecture Components | High Availability SCSP objective 4.3, Describe disaster recovery concepts
73. ![]() D is the correct answer. Arisk assessment analyzes the factors that could impact the integrity, confidentiality, or availability of business systems and their expected damage/likelihood.
D is the correct answer. Arisk assessment analyzes the factors that could impact the integrity, confidentiality, or availability of business systems and their expected damage/likelihood.
![]() A is incorrect because it is incomplete. The threats alone do not provide enough information to make a decision on the security controls to implement. B is also incorrect because it is incomplete. Choice Bis the other part that is required to make a decision. Both the threats and the damage/impact are used to calculate risk. C is incorrect because organizational security as a whole is too broad a scope for a risk assessment.
A is incorrect because it is incomplete. The threats alone do not provide enough information to make a decision on the security controls to implement. B is also incorrect because it is incomplete. Choice Bis the other part that is required to make a decision. Both the threats and the damage/impact are used to calculate risk. C is incorrect because organizational security as a whole is too broad a scope for a risk assessment.
Chapter 7: Business Continuity Objectives | Data Value and Risk SCSP objective 4.3, Describe disaster recovery concepts
74. ![]() B is the correct answer. Abusiness impact analysis estimates the cost an organization could incur should systems be unavailable because of incident or disaster.
B is the correct answer. Abusiness impact analysis estimates the cost an organization could incur should systems be unavailable because of incident or disaster.
![]() A is incorrect because the BIA is also concerned with the cost to the business’s image, sales, and competitive advantage, to name a few costs. C is incorrect because the BIA may include time as an input to the cost, but that is not the main concern. D is incorrect because the controls required to bring risks below the organization’s risk tolerance level is part of the risk assessment.
A is incorrect because the BIA is also concerned with the cost to the business’s image, sales, and competitive advantage, to name a few costs. C is incorrect because the BIA may include time as an input to the cost, but that is not the main concern. D is incorrect because the controls required to bring risks below the organization’s risk tolerance level is part of the risk assessment.
Chapter 7: Business Continuity Objectives SCSP objective 4.3, Describe disaster recovery concepts
75. ![]() B is the correct answer. In remote authentication, passwords are sent via the network, while physical authentication is done on the machine being logged into.
B is the correct answer. In remote authentication, passwords are sent via the network, while physical authentication is done on the machine being logged into.
![]() A is incorrect because remote authentication could be used to connect to computers at the same site. C is incorrect because visual patterns are not used in authentication, and there are many types of physical authentication, even if this were an option. D is incorrect because physical authentication is used for devices you are directly interfacing with, not remote authenticators.
A is incorrect because remote authentication could be used to connect to computers at the same site. C is incorrect because visual patterns are not used in authentication, and there are many types of physical authentication, even if this were an option. D is incorrect because physical authentication is used for devices you are directly interfacing with, not remote authenticators.
Chapter 8: Access Control | Authentication | Physical Authentication SCSP objective 5.1, Describe storage security methods
76. ![]() B is the correct answer. Failover is the transfer of services in a redundant system from one device to another.
B is the correct answer. Failover is the transfer of services in a redundant system from one device to another.
![]() A is incorrect because service redundancy can be achieved with or without failover. C and D are incorrect because overflow and component transfer are not storage concepts.
A is incorrect because service redundancy can be achieved with or without failover. C and D are incorrect because overflow and component transfer are not storage concepts.
Chapter 9: Storage Architecture Components | High Availability | Failover SCSP objective 4.3, Describe disaster recovery concepts
77. ![]() B is the correct answer. OLTP provides immediate response and high availability.
B is the correct answer. OLTP provides immediate response and high availability.
![]() A, C, and D are incorrect because these are made-up terms.
A, C, and D are incorrect because these are made-up terms.
Chapter 9: Storage Architecture Components | Online Transaction Processing SCSP Objective 1.5, Describe data storage planning for various business applications
78. ![]() D is the correct answer. N-port virtualization allows multiple N-ports to reside on the same physical N-port.
D is the correct answer. N-port virtualization allows multiple N-ports to reside on the same physical N-port.
![]() A is incorrect because a VSAN is a way to logically partition a SAN into an isolated virtual storage area where network communication is restricted to a virtual domain. B is incorrect because state change notifications are used to inform fiber devices about the presence of devices on the fiber network. C is incorrect because PLOGI is a port logon.
A is incorrect because a VSAN is a way to logically partition a SAN into an isolated virtual storage area where network communication is restricted to a virtual domain. B is incorrect because state change notifications are used to inform fiber devices about the presence of devices on the fiber network. C is incorrect because PLOGI is a port logon.
Chapter 3: Fibre Channel Storage Network | Components | Addressing SCSP objective 2.2, Identify Fibre Channel SAN components
79. ![]() B is the correct answer. Asingle point of failure is a single configuration, a network, hardware, or software malfunctioning and causing the entire system or process to fail.
B is the correct answer. Asingle point of failure is a single configuration, a network, hardware, or software malfunctioning and causing the entire system or process to fail.
![]() A is incorrect because a large-scale system failure indicates more than a single failure or a catastrophic failure, which may not be the case in all instances of a single device failure. C is incorrect because a network failure does not necessarily indicate a failure of a single component. D is incorrect because a server-side power failure is only one example of a component that could fail.
A is incorrect because a large-scale system failure indicates more than a single failure or a catastrophic failure, which may not be the case in all instances of a single device failure. C is incorrect because a network failure does not necessarily indicate a failure of a single component. D is incorrect because a server-side power failure is only one example of a component that could fail.
Chapter 9: Storage Architecture Components | High Availability | Single Point of Failure SCSP objective 4.3, Describe disaster recovery concepts
80. ![]() A is the correct answer. Secondary risk is risk caused by another risk response strategy.
A is the correct answer. Secondary risk is risk caused by another risk response strategy.
![]() B is incorrect because a risk that is moderately likely to occur is something risk managers would need to evaluate against the potential impact to determine reasonable controls. C is incorrect because a risk that can occur when multiple other risks occur is part of the impact of the risk. D is incorrect because the secondary risk is not a second opinion.
B is incorrect because a risk that is moderately likely to occur is something risk managers would need to evaluate against the potential impact to determine reasonable controls. C is incorrect because a risk that can occur when multiple other risks occur is part of the impact of the risk. D is incorrect because the secondary risk is not a second opinion.
Chapter 7: Business Continuity Objectives | Data Value and Risk SCSP objective 4.3, Describe disaster recovery concepts
81. ![]() B is the correct answer. Low humidity can lead to electrostatic discharge.
B is the correct answer. Low humidity can lead to electrostatic discharge.
![]() A is incorrect because a charge does not create water damage. C is incorrect because the buildup of charge would not be sufficient enough to cause overheating. D is incorrect because electrical failure would be a byproduct of another failure.
A is incorrect because a charge does not create water damage. C is incorrect because the buildup of charge would not be sufficient enough to cause overheating. D is incorrect because electrical failure would be a byproduct of another failure.
Chapter 10: Facilities | Humidity Control SCSP objective 1.5, Describe data storage planning for various business applications control
82. ![]() B is the correct answer. HFC-125 removes heat from fire. Other agents that remove heat from fire include FM-200 and HFC-237ea.
B is the correct answer. HFC-125 removes heat from fire. Other agents that remove heat from fire include FM-200 and HFC-237ea.
![]() A and C are incorrect because they are not real gaseous agents. D is incorrect because HVAC is the heating and cooling systems in place in an organization.
A and C are incorrect because they are not real gaseous agents. D is incorrect because HVAC is the heating and cooling systems in place in an organization.
Chapter 10: Facilities | Fire Suppression SCSP objective 1.5, Describe data storage planning for various business applications
83. ![]() D is the correct answer. Rack density refers to the number of devices in the rack.
D is the correct answer. Rack density refers to the number of devices in the rack.
![]() A is incorrect because heat is measured in BTUs. B is incorrect because cables do not have an impact on how dense the rack is. C is incorrect because the type of device is not a factor in determining density.
A is incorrect because heat is measured in BTUs. B is incorrect because cables do not have an impact on how dense the rack is. C is incorrect because the type of device is not a factor in determining density.
Chapter 10: Safety | Weight Considerations | Floor and Rack Loading SCSP objective 1.5, Describe data storage planning for various business applications
84. ![]() B is the correct answer. Replication transfers data between hosts or storage systems.
B is the correct answer. Replication transfers data between hosts or storage systems.
![]() A is incorrect because a transfer protocol can be used for many data transmissions that are not periodic. C is incorrect because backups do not always occur between hosts or storage systems. D is incorrect because system support is the ongoing maintenance of a system, not the transference of data at periodic intervals.
A is incorrect because a transfer protocol can be used for many data transmissions that are not periodic. C is incorrect because backups do not always occur between hosts or storage systems. D is incorrect because system support is the ongoing maintenance of a system, not the transference of data at periodic intervals.
Chapter 9: Replication SCSP objective 1.5, Describe data storage planning for various business applications
85. ![]() B is the correct answer. Hierarchical storage management presents files and directories as a composite object with a single integrated file interface.
B is the correct answer. Hierarchical storage management presents files and directories as a composite object with a single integrated file interface.
![]() A is incorrect because a block management architecture does not exist. Ablock-level architecture exists, but it is not concerned with files but rather the blocks that make up logical units. Files may or may not reside in these blocks. C is incorrect because manual storage tiering requires intervention to optimize the location of data. D is incorrect because a storage management system is much too broad a system to be described as presenting a composite object with a single integrated file interface.
A is incorrect because a block management architecture does not exist. Ablock-level architecture exists, but it is not concerned with files but rather the blocks that make up logical units. Files may or may not reside in these blocks. C is incorrect because manual storage tiering requires intervention to optimize the location of data. D is incorrect because a storage management system is much too broad a system to be described as presenting a composite object with a single integrated file interface.
Chapter 11: Information Lifecycle Management | HSM SCSP objective 5.2, Identify storage management technologies
86. ![]() B is the correct answer. The alias directs traffic to a group of N-ports that are part of a multicast or hunt group.
B is the correct answer. The alias directs traffic to a group of N-ports that are part of a multicast or hunt group.
![]() A is incorrect because the alias is not used for failover. C is incorrect because the alias is not a descriptive name. D is incorrect because the alias has not been removed from the FC protocol and it is still in use.
A is incorrect because the alias is not used for failover. C is incorrect because the alias is not a descriptive name. D is incorrect because the alias has not been removed from the FC protocol and it is still in use.
Chapter 3: Fibre Channel Storage Network | Components | Addressing SCSP objective 2.2, Identify Fibre Channel SAN components
87. ![]() B is the correct answer. Litigation holds specify the data that should be preserved for potential or ongoing litigation.
B is the correct answer. Litigation holds specify the data that should be preserved for potential or ongoing litigation.
![]() A is incorrect because a mandatory preservation is simply a requirement to preserve data but not necessarily related to lawsuits. C is incorrect because trial backup requirements is a made-up term. D is incorrect because the term is litigation hold, not litigation preservation.
A is incorrect because a mandatory preservation is simply a requirement to preserve data but not necessarily related to lawsuits. C is incorrect because trial backup requirements is a made-up term. D is incorrect because the term is litigation hold, not litigation preservation.
Chapter 11: Compliance | Preservation and Litigation Holds SCSP objective 1.5, Describe data storage planning for various business applications
88. ![]() B is the correct answer. Shoe-shining occurs when the device sending data to the tape does not send data fast enough so the tape has to stop and rewind so that the data will be written sequentially.
B is the correct answer. Shoe-shining occurs when the device sending data to the tape does not send data fast enough so the tape has to stop and rewind so that the data will be written sequentially.
![]() A is incorrect because a dirty drive will cause data read and write errors. C is incorrect because a cable problem would result in communication loss or errors. D is incorrect because mounting a tape for random reads would not issue writes to the drive.
A is incorrect because a dirty drive will cause data read and write errors. C is incorrect because a cable problem would result in communication loss or errors. D is incorrect because mounting a tape for random reads would not issue writes to the drive.
Chapter 4: Removable Storage | Tape Media | Shoe Shining/Backhitching SCSP objective 4.1, Identify backup technologies
89. ![]() C is the correct answer. Agrid breaks up files into segments, or it can store an entire file on a node in the grid. Files or segments are often replicated to other nodes for redundancy.
C is the correct answer. Agrid breaks up files into segments, or it can store an entire file on a node in the grid. Files or segments are often replicated to other nodes for redundancy.
![]() A is incorrect because a full mesh controller does not exist. B is incorrect because the cache is used to store files that are waiting to be written to disk or that may be read from the array. D is incorrect because dual controllers do not break files into segments and they operate on only one node.
A is incorrect because a full mesh controller does not exist. B is incorrect because the cache is used to store files that are waiting to be written to disk or that may be read from the array. D is incorrect because dual controllers do not break files into segments and they operate on only one node.
Chapter 2: Storage Arrays | Controller Head SCSP objective 3.4, Describe disk technologies
90. ![]() B is the correct answer. Ahop measures how many devices are traversed between source and destination.
B is the correct answer. Ahop measures how many devices are traversed between source and destination.
![]() A is incorrect because a jump is not a networking term. C is incorrect because latency measures the time from source to destination. D is incorrect because ping measures whether connectivity exists.
A is incorrect because a jump is not a networking term. C is incorrect because latency measures the time from source to destination. D is incorrect because ping measures whether connectivity exists.
Chapter 12: Performance Metrics and Tools | Switch | Hops SCSP objective 1.6, Describe how to improve performance for host applications
91. ![]() A is the correct answer. Class of service is used to prioritize traffic.
A is the correct answer. Class of service is used to prioritize traffic.
![]() B is incorrect because routing delivers packets across networks. C is incorrect because this is a made-up term. D is incorrect because switching delivers frames to ports based on MAC addresses.
B is incorrect because routing delivers packets across networks. C is incorrect because this is a made-up term. D is incorrect because switching delivers frames to ports based on MAC addresses.
Chapter 3: iSCSI Storage Network | Ethernet Features | Class of Service SCSP objective 2.3, Identify Ethernet/IP SAN components
92. ![]() D is the correct answer. iSCSI would take advantage of the Ethernet network, and VLANs would segment the iSCSI traffic from the normal LAN traffic.
D is the correct answer. iSCSI would take advantage of the Ethernet network, and VLANs would segment the iSCSI traffic from the normal LAN traffic.
![]() A and B are incorrect because FC would not utilize the Ethernet network. C is incorrect because it is better to segment the iSCSI traffic from the LAN traffic with VLANs.
A and B are incorrect because FC would not utilize the Ethernet network. C is incorrect because it is better to segment the iSCSI traffic from the LAN traffic with VLANs.
Chapter 3: iSCSI Storage Network SCSP objective 2.3, Identify Ethernet/IP SAN components
93. ![]() D is the correct answer. Since the power is A/B, each circuit must be able to handle the entire load. Since the peak load is 60 percent, this would translate to 120 percent in failover mode when 80 percent is the max recommended.
D is the correct answer. Since the power is A/B, each circuit must be able to handle the entire load. Since the peak load is 60 percent, this would translate to 120 percent in failover mode when 80 percent is the max recommended.
![]() A is incorrect because a single circuit could not handle the entire load if one circuit fails. B is incorrect because circuits do not always provide 100 percent of their available power, and reducing both links to 50 percent could result in a load that the circuit could not handle in failover. C is incorrect because a third circuit would not be on A/B power.
A is incorrect because a single circuit could not handle the entire load if one circuit fails. B is incorrect because circuits do not always provide 100 percent of their available power, and reducing both links to 50 percent could result in a load that the circuit could not handle in failover. C is incorrect because a third circuit would not be on A/B power.
Chapter 10: Storage Power Requirements | Sufficient Capacity SCSP objective 1.5, Describe data storage planning for various business applications
94. ![]() D is the correct answer. Amotherboard is not hot swappable.
D is the correct answer. Amotherboard is not hot swappable.
![]() A, B, and C are incorrect because they are all hot swappable.
A, B, and C are incorrect because they are all hot swappable.
Chapter 4: Storage Networking Devices | Hot-Swappable Network Components SCSP objective 2.2, Identify Fibre Channel SAN components
95. ![]() B, D, and E are the correct answers. SCSI, SAS, and FC disks can all run at 15,000 rpm.
B, D, and E are the correct answers. SCSI, SAS, and FC disks can all run at 15,000 rpm.
![]() A and C are incorrect because IDE and SATA have a maximum rpm of 7,200.
A and C are incorrect because IDE and SATA have a maximum rpm of 7,200.
Chapter 1: Available Disk Interfaces and Their Characteristics SCSP objective 3.4, Describe disk technologies
96. ![]() A is the correct answer. Ahost bus adapter is used to connect to a Fibre Channel SAN.
A is the correct answer. Ahost bus adapter is used to connect to a Fibre Channel SAN.
![]() B is incorrect because a NIC is used to connect to an Ethernet network or iSCSI SAN. C is incorrect because a modem is used to create a dial-up connection. D is incorrect because TOE is a function of a NIC that offloads the processing of TCP/IP to the NIC.
B is incorrect because a NIC is used to connect to an Ethernet network or iSCSI SAN. C is incorrect because a modem is used to create a dial-up connection. D is incorrect because TOE is a function of a NIC that offloads the processing of TCP/IP to the NIC.
Chapter 4: Storage Networking Devices | HBA SCSP objective 2.2, Identify Fibre Channel SAN components
97. ![]() C is the correct answer. Awrist strap can take excess electrostatic charge and direct it to a ground instead of sensitive components.
C is the correct answer. Awrist strap can take excess electrostatic charge and direct it to a ground instead of sensitive components.
![]() A is incorrect because a hard hat protects against head injury. B is incorrect because a lifting belt protects against back injury. D is incorrect because aluminum is a conductor of electricity and could increase the chance of electrostatic discharge.
A is incorrect because a hard hat protects against head injury. B is incorrect because a lifting belt protects against back injury. D is incorrect because aluminum is a conductor of electricity and could increase the chance of electrostatic discharge.
Chapter 10: Safety | Antistatic Devices SCSP objective 1.1, Identify host connectivity components used in a support matrix
98. ![]() B is the correct answer. Many modern flash drives can hold 10GB of data, and they are easy to use.
B is the correct answer. Many modern flash drives can hold 10GB of data, and they are easy to use.
![]() A and C are incorrect because a DVD or CD would not be able to hold 10GB of data. D is incorrect because a tape would require a tape drive capable of reading the tape at the user’s desk and the remote office.
A and C are incorrect because a DVD or CD would not be able to hold 10GB of data. D is incorrect because a tape would require a tape drive capable of reading the tape at the user’s desk and the remote office.
Chapter 10: Safety | Antistatic Devices SCSP objective 1.1, Identify host connectivity components used in a support matrix
99. ![]() D is the correct answer. Astorage area network (SAN) connects disk arrays, tape drives, and other storage components to servers and hosts.
D is the correct answer. Astorage area network (SAN) connects disk arrays, tape drives, and other storage components to servers and hosts.
![]() A is incorrect because a NAS connects servers to network shares. B is incorrect because a DAS can only connect to devices directly attached to it. C is incorrect because a LAN is used for communication between hosts and servers.
A is incorrect because a NAS connects servers to network shares. B is incorrect because a DAS can only connect to devices directly attached to it. C is incorrect because a LAN is used for communication between hosts and servers.
Chapter 2: Storage Area Networks SCSP objective 3.1, Identify host to SAN components
100. ![]() C is the correct answer. Alerts can send e-mails or notify administrators in other ways when certain conditions are met.
C is the correct answer. Alerts can send e-mails or notify administrators in other ways when certain conditions are met.
![]() A is incorrect because a baseline is a measurement of normal activity. B is incorrect because a threshold is a limit that defines an error condition. D is incorrect because logs record activities performed on a device.
A is incorrect because a baseline is a measurement of normal activity. B is incorrect because a threshold is a limit that defines an error condition. D is incorrect because logs record activities performed on a device.
Chapter 6: Storage Monitoring, Alerting, and Reporting | Setting Alerts SCSP objective 5.2, Identify storage management technologies
101. ![]() C is the correct answer. A midrange drive is ideal for business situations with low I/O requirements. Since this is a NAS device, somewhat higher reliability is needed than what an entry-level or consumer drive could offer.
C is the correct answer. A midrange drive is ideal for business situations with low I/O requirements. Since this is a NAS device, somewhat higher reliability is needed than what an entry-level or consumer drive could offer.
![]() A is incorrect because a consumer drive does not offer the reliability needed for a business NAS. B is incorrect because this is just another name for a consumer drive. D is incorrect because an enterprise drive is best for high I/O requirements, and this is a low I/O situation.
A is incorrect because a consumer drive does not offer the reliability needed for a business NAS. B is incorrect because this is just another name for a consumer drive. D is incorrect because an enterprise drive is best for high I/O requirements, and this is a low I/O situation.
Chapter 1: How Disk Storage Systems Work | Electrical and Mechanical Differences SCSP objective 1.1, Identify host connectivity components used in a support matrix
102. ![]() C is the correct answer. Each of the quad-port Ethernet adapters will utilize a significant amount of bandwidth. PCIe is the only bus that can deliver dedicated bandwidth for each of the three cards.
C is the correct answer. Each of the quad-port Ethernet adapters will utilize a significant amount of bandwidth. PCIe is the only bus that can deliver dedicated bandwidth for each of the three cards.
![]() A is incorrect because PCI would not have sufficient bandwidth to support a quad-port Ethernet card. It is also a shared bus, so the cards would contend for bandwidth. B is incorrect as well. PCI-X would support a quad-port Fast Ethernet adapter, but it is a shard bus, so a single quad-port card would consume most of the bandwidth, leaving little for the other cards. D is incorrect because PCI-M is not a bus type.
A is incorrect because PCI would not have sufficient bandwidth to support a quad-port Ethernet card. It is also a shared bus, so the cards would contend for bandwidth. B is incorrect as well. PCI-X would support a quad-port Fast Ethernet adapter, but it is a shard bus, so a single quad-port card would consume most of the bandwidth, leaving little for the other cards. D is incorrect because PCI-M is not a bus type.
Chapter 1: Available Disk Interfaces and Their Characteristics | PCI Versions | PCI SCSP objective 3.4, Describe disk technologies
103. ![]() B is the correct answer. Juan wants to implement RAID 5, but he does not have other equipment besides the three 2TB SATA drives. The server does not have a RAID controller either. His only option is to use software RAID. This will provide the redundancy needed to protect the data, but the server processor will see increased utilization for parity computations.
B is the correct answer. Juan wants to implement RAID 5, but he does not have other equipment besides the three 2TB SATA drives. The server does not have a RAID controller either. His only option is to use software RAID. This will provide the redundancy needed to protect the data, but the server processor will see increased utilization for parity computations.
![]() A and C are incorrect because there is no RAID controller available in the system. D is incorrect because software RAID is not configured in this way.
A and C are incorrect because there is no RAID controller available in the system. D is incorrect because software RAID is not configured in this way.
Chapter 1: Multiple Disks for Larger Storage and Fault Tolerance | Hardware, Host-Based, and Software Implementations SCSP objective 3.3, Describe the different RAID levels
104. ![]() B is the correct answer. Cloud storage may be located far away from the user, in which case data transfers would need to traverse through many hops to reach the destination. This increases the latency for disk writes unless local caching is used. However, with local caching, there is risk of data loss if adequate redundancies have not been placed on local cache.
B is the correct answer. Cloud storage may be located far away from the user, in which case data transfers would need to traverse through many hops to reach the destination. This increases the latency for disk writes unless local caching is used. However, with local caching, there is risk of data loss if adequate redundancies have not been placed on local cache.
![]() A is incorrect. Latency could make a backup job take longer to run, but backup windows usually have a greater tolerance for fluctuations in backup times than production applications do. C is incorrect because cloud synchronization occurs behind the scenes while the user still works with their local copy of the data. D is incorrect because web-based cloud storage does not operate behind the scenes like other cloud storage methods. The user of a web-based cloud storage system knows when a transfer starts and when it ends. Also, only the file selected is downloaded, not all files on the storage system. Only information on the remaining files is displayed so latency can affect it much like it would other systems. The fact that the user is aware of the time it takes to transfer files and that those transfers are minimized makes latency less of an issue for web-based cloud storage.
A is incorrect. Latency could make a backup job take longer to run, but backup windows usually have a greater tolerance for fluctuations in backup times than production applications do. C is incorrect because cloud synchronization occurs behind the scenes while the user still works with their local copy of the data. D is incorrect because web-based cloud storage does not operate behind the scenes like other cloud storage methods. The user of a web-based cloud storage system knows when a transfer starts and when it ends. Also, only the file selected is downloaded, not all files on the storage system. Only information on the remaining files is displayed so latency can affect it much like it would other systems. The fact that the user is aware of the time it takes to transfer files and that those transfers are minimized makes latency less of an issue for web-based cloud storage.
Chapter 2: Cloud Storage | Cloud Storage Methods SCSP objective 6.1, Identify cloud storage methods
105. ![]() B is the correct answer. This is an example of cloud synchronization. The Internet resource is owned by a third party, which describes a cloud resource.
B is the correct answer. This is an example of cloud synchronization. The Internet resource is owned by a third party, which describes a cloud resource.
![]() A is incorrect because this is an example of database replication. C is incorrect because this is an example of an iSCSI volume mount. D is incorrect because this is an example of a grid storage array.
A is incorrect because this is an example of database replication. C is incorrect because this is an example of an iSCSI volume mount. D is incorrect because this is an example of a grid storage array.
Chapter 2: Cloud Storage | Cloud Storage Methods SCSP objective 6.1, Identify cloud storage methods
106. ![]() D is the correct answer. A hybrid cloud combines elements of the public and private cloud models.
D is the correct answer. A hybrid cloud combines elements of the public and private cloud models.
![]() A is incorrect because this definition describes a public cloud. B is incorrect because this definition describes a private cloud. C is incorrect because this describes a community cloud.
A is incorrect because this definition describes a public cloud. B is incorrect because this definition describes a private cloud. C is incorrect because this describes a community cloud.
Chapter 2: Cloud Storage | Cloud Storage Types SCSP objective 6.2, Identify cloud storage types
107. ![]() D is the correct answer. Core is not an ITIL service change approach. The ITIL change approaches are big bang, phased, push, and pull.
D is the correct answer. Core is not an ITIL service change approach. The ITIL change approaches are big bang, phased, push, and pull.
![]() A, B, and C are incorrect because they are ITIL service change approaches.
A, B, and C are incorrect because they are ITIL service change approaches.
Chapter 6: Configuration Management | Information Technology Infrastructure Library SCSP objective 5.2, Identify storage management technologies
108. ![]() A, B, and D are the correct answers. The current backup size can be used to establish the baseline. The growth rate allows the administrator to determine how much will be needed in the near future so that the backup drives do not have to be immediately replaced. It is also important to know the backup frequency and retention because each of these copies will consume space.
A, B, and D are the correct answers. The current backup size can be used to establish the baseline. The growth rate allows the administrator to determine how much will be needed in the near future so that the backup drives do not have to be immediately replaced. It is also important to know the backup frequency and retention because each of these copies will consume space.
![]() C is incorrect because the backups will need to be an appropriate size no matter where they are stored.
C is incorrect because the backups will need to be an appropriate size no matter where they are stored.
Chapter 12: Backup Troubleshooting | Space Limitations SCSP objective 4.1, Identify backup technologies
Analyzing Your Results
Now that you’re done, let’s analyze your results! First you will need to tally up the number of questions you answered correctly. With this information in hand, please consult the following table:

