Reviewing Basic Protocols and Ports
The TCP/IP protocol suite consists of a full range of protocols used to connect computers on the Internet and on most internal networks. An SSCP-certified individual is expected to understand the basic function of many of these protocols. The following section lists some common protocols along with their acronyms and a brief explanation of the protocol.
It’s also important to know the logical port numbers for many of the protocols. The “Mapping Well-Known Ports to Protocols” section later in this chapter describes the use of these ports in more detail and provides a table mapping some well-known ports to protocols. However, I’ve also listed the relevant port numbers in the protocol descriptions in case you turn to only that section for a description of the protocol.
From a security perspective, it’s important to understand some basics about protocols, such as what protocols are required and what protocols are optional. For example, a core step in hardening a server, or making it more secure, is to remove all unneeded protocols and services. Consider a server that is not running the FTP. If an attacker tries to attack this server using a known FTP exploit, it simply won’t work because FTP is not on the server.
On the other hand, consider a server that is running 100 different protocols. It is now susceptible to attacks on each of these protocols. By removing unneeded protocols, you reduce the attack surface of the server. Once you understand some basics about protocols, you can determine whether a protocol is needed or not.
Figure 3-7 identifies the layers of the four-layer TCP/IP and OSI models where several protocols reside. These protocols are listed in the following pages.
Figure 3-7 Mapping protocols to the OSI and TCP/IP models
Address Resolution Protocol
The Address Resolution Protocol (ARP) resolves IP addresses to Media Access Control (MAC) addresses. The MAC address is a 12-hexadecimal number (such as 6C-62-6D-BA-73-6C) assigned to the NIC that uniquely identifies the computer. The MAC is needed to transmit data on the same subnet.
From a big picture perspective, the IP address is used to get traffic from one subnet to another, and once the packet arrives on the destination subnet, the MAC address is used to get the packet to the destination computer. ARP broadcasts a packet onto the subnet essentially asking all the computers on the subnet, “Who has this IP? If it’s you, tell me your MAC.” The computer with that IP address responds with an ARP packet that includes its MAC address.
Reverse Address Resolution Protocol (RARP) works just the opposite of ARP. A client has a MAC address and uses RARP to get an IP address.
Internet Control Message Protocol
The ICMP is used with many diagnostic protocols, such as ping, pathping, and tracert (or traceroute on UNIX systems). For example, if you enter ping and an IP address (such as ping 192.168.1.10) on a Windows system, ping sends four packets to the IP address, and if ICMP is not blocked, the host with that IP address will answer with four ping packets in reply. Other operating systems, such as Linux and UNIX, will continue to send ping requests until the user presses CTRL+C.
ICMP is used with many denial-of-service (DoS) attacks, so it is frequently blocked using a router’s ACL or a firewall. In other words, a server may be operational, but a ping to that server will fail due to a firewall blocking ICMP traffic.
Internet Group Message Protocol
The Internet Group Message Protocol (IGMP) is used for IPv4 multicasting, where data is sent from one computer to multiple computers at the same time. Computers join a multicast group with a multicast address (in the range of 224.0.0.0 through 239.255.255.255). Multicasting is done differently with IPv6. IPv6 uses ICMPv6 messaging instead of IGMP.
You can compare multicasting used with IGMP to unicast and broadcast messages:
• Unicast Traffic is sent from one computer to one other computer.
• Broadcast Traffic is sent from one computer to all other computers on the subnet. Broadcast traffic is not passed by a router.
• Multicast Traffic is sent from one computer to multiple computers in the network. Multicast transmissions use UDP.
Dynamic Host Configuration Protocol
A Dynamic Host Configuration Protocol (DHCP) server uses DHCP to assign TCP/IP configuration information to DHCP clients. This includes IP addresses, a subnet mask, the address of a DNS server, and much more. Many people shorten the definition of DHCP to say that it simply assigns IP addresses, but that is not completely accurate. There are close to 70 different options that a DHCP server can assign. DHCP uses ports 66 and 67.
Simple Network Management Protocol
The Simple Network Management Protocol (SNMP) is commonly used to manage network devices (such as routers and layer 3 switches) on a network. SNMP agents on the network devices report management data back to a central server running SNMP management software. Additionally, a server hosting SNMP management software can use SNMP to configure the network devices remotely.
SNMPv1 had several security flaws, but SNMPv2 and SNMPv3 provide significant improvements. For example, client authentication in SNMPv1 was handled with a community string, and the default community was “public.” However, SNMPv2 and SNMPv3 introduced several security enhancements. SNMPv3 uses encryption to achieve confidentiality, verifies the integrity of the packets, and includes authentication to verify that the data is from a known entity. SNMP uses ports 161 and 162.
Hypertext Transfer Protocol and Hypertext Transfer Protocol Secure
HyperText Transfer Protocol (HTTP) is the common protocol used to transfer web pages over the Internet. Most web browsers use HTTP by default. For example, you could type in the address of a site such as mcgraw-hill.com and it will default to http://mcgraw-hill.com. HTTP uses port 80.
HTTPS (HTTP Secure) is an encrypted form of HTTP. HTTPS has historically been encrypted with Secure Sockets Layer (SSL), although it can also be encrypted with Transport Layer Security (TLS). Data encrypted within HTTPS is not readable by anyone who is not involved in the HTTPS session. HTTPS uses port 443.
Domain Name System
A Domain Name System (DNS) server provides name resolution services. More specifically, DNS resolves host names to IP addresses as its primary function. For example, a DNS client can query the DNS server with the host name of a computer and the DNS server replies with the IP address. DNS uses port 53.
DNS servers use different types of records to provide different responses:
• A (host) record Resolves a host name to an IP address.
• PTR (pointer) record Resolves an IP address to a host name.
• MX (mail exchange) record Identifies a mail server.
• CNAME (canonical name or alias) record Allows a system to be known by different names, or aliases. For example, a web server can be named Web1 but also respond to a name of www.
Berkeley Internet Name Domain (BIND) is a version of DNS software that runs on UNIX systems. It is freely available and runs on many DNS servers on the Internet. Microsoft networks running in internal organizations commonly use Microsoft’s version of DNS.
Network File System
Network File System (NFS) allows computers running different operating systems to access and share files over the network. NFS is an open standard created by Sun Microsystems and is commonly used to allow users running UNIX (and UNIX derivatives such as Linux) to access files on Microsoft systems. Similarly, NFS allows users running Microsoft systems to access files on UNIX-based systems.
File Transfer Protocols
The FTP is used to transfer files from one system to another. Some organizations host FTP servers that allow individuals to upload and download data. The FTP server provides a simple storage location for people located in different areas of the world. FTP uses ports 20 and 21.
Trivial FTP (TFTP) was mentioned briefly earlier in the chapter in the UDP section. TFTP is stripped-down version of FTP that provides very basic capabilities and doesn’t even use TCP to establish a session. TFTP uses UDP port 69.

EXAM TIP FTP uses TCP and TFTP uses UDP.
Both FTP and TFTP have significant security issues. Data sent across the network using FTP and TFTP is sent in clear text. Anyone with a sniffer can easily capture the data and read the contents of the FTP packets. This includes the username and password (if used) and also the data.
Secure FTP (SFTP) uses Secure Shell (SSH) to encrypt FTP traffic. Aside from being encrypted with SSH, SFTP works the same as FTP.
Tunneling Protocols
Chapter 4 will explore virtual private networks (VPNs) in greater depth. In general, a VPN provides access to a private network over a public network such as the Internet. Because traffic is sent over the public network, it needs to be protected. A common way of protecting VPN traffic is by encapsulating it in a tunneling protocol and encrypting the encapsulated data.
Two common tunneling protocols are the Point-to-Point Tunneling Protocol (PPTP) and the Layer 2 Tunneling Protocol (L2TP).
Routing Protocols
As mentioned previously, routing occurs at the network layer. Routers identify the best path for a packet to take based on information it knows about the network. It’s possible to enter routing information manually in a smaller network, but for larger networks, the routers communicate to each other using a routing protocol. The two primary routing protocols used on internal networks are Routing Information Protocol version 2 (RIPv2) and Open Shortest Path First (OSPF).
Although RIPv2 works well, it can generate a lot of traffic and doesn’t scale well. In general, RIPv2 is good for smaller networks while OSPF is used for larger networks. RIPv2 is very easy to enable and configure on routers, while OSPF takes a little more effort.
Telnet
Telnet is a basic protocol used to interact with a remote system using text-based commands. For example, a Telnet server will accept connections from a system running a Telnet client. When the client connects, the user is presented with a Telnet command prompt. The user can then enter Telnet commands at the command prompt.
Although Telnet used to be much more popular, especially in UNIX and UNIX derivatives such as Linux, it isn’t used that often today. One of the challenges with Telnet is that data is passed across the network in clear text and can be captured with a sniffer. However, Telnet can be encrypted with SSH.
A risk when Telnet is running is that an attacker can use it to launch other attacks. A report from Akamai Technologies reported that 10 percent of attacks from mobile networks in the third quarter of 2010 were directed at the Telnet port (port 23). Because Telnet is not used so much, this makes me wonder whether Telnet is being left enabled on these systems even though it’s not needed.
Secure Shell
SSH is a basic encryption protocol that can create a secure session between two computers. It is used to encrypt other protocol traffic such as FTP (called SFTP) and Telnet traffic. Aside from encrypting the traffic as it passes over the network, the underlying protocol works the same. SSH uses port 22.
Internet protocol Security
Internet Protocol security (IPsec) provides security for IP traffic traveling over a network. It is used to encrypt data and/or to provide authentication of systems that are transferring data between each other. IPsec has two primary components:
• Authentication Header (AH) AH provides authentication between the systems and verifies the integrity of the packets, but it does not encrypt the data. The AH is created from a hash of the packet with additional authentication data, and this hash is then encrypted to prevent tampering. The hash provides integrity. Packets protected with AH are identified with protocol ID 51.
• Encapsulating Security Protocol (ESP) ESP encrypts the data and also provides the same authentication services provided from AH. Data encrypted with ESP cannot be read if captured with a sniffer. Packets protected with ESP are identified with protocol ID 50.

EXAM TIP Note that AH and ESP are identified with protocol IDs (not port numbers). The IP header includes the protocol ID field. Other protocol ID values are as follows: ICMP is 1, IGMP is 2, TCP is 6, and UDP is 17.
Secure Sockets Layer and Transport Layer Security
Secure Sockets Layer (SSL) is a popular encryption protocol used to encrypt different types of traffic. You most often see SSL used to encrypt HTTP traffic (as HTTPS). However, SSL is used in other implementations. For example, SSL is also used as tunneling protocol for some VPN traffic.
Transport Layer Security (TLS) has been designated as the replacement of SSL. It is based on SSL and is formally defined in RFC 5246. Although the acronym HTTPS historically has meant that an HTTP session is encrypted with SSL, some HTTPS sessions today are encrypted with TLS.
E-mail Protocols
The Simple Mail Transfer Protocol (SMTP), Post Office Protocol version 3 (POP3), and Internet Message Access Protocol version 4 (IMAP4) are three protocols commonly used for e-mail.
From a client perspective, SMTP is used to send e-mail from e-mail clients to an e-mail server. POP3 is used to receive e-mail from a POP3 server. IMAP4 is used to store e-mail on an e-mail server and allow clients to access it, and even organize the e-mail in folders. One advantage of IMAP4 over POP3 is that users are able to screen some of the e-mail before downloading it to their system. In contrast, POP3 sends the entire contents to the client as soon as the client connects.

TIP Clients use SMTP to send e-mail to an SMTP server, and e-mail servers use SMTP to both send and receive e-mail between other SMTP servers.
With the overwhelming amount of spam and phishing attacks, IMAP4 is an appealing alternative and is being used by many e-mail servers on the Internet. Users can often tell by the sender e-mail address or the subject line whether they want to open the e-mail or just delete it. For example, I’d love to actually win $1,500,000 just because I have a gmail account, but when I see the subject line saying, “Your e-mail ID has won $1,500,000,” I know it’s a phishing attempt and I simply delete the message to eliminate the risk.
SMTP uses port 25, POP3 uses port 110, and IMAP4 uses port 143.
Network News Transfer Protocol
The Network News Transfer Protocol (NNTP) is used with newsgroups. Users are able to subscribe to a newsgroup with a newsreader application and then each time anyone in the newsgroup posts a message, all the subscribers receive it. Newsgroups were much more popular years ago, but HTTP forums, or groups, have overtaken them in popularity. Additionally, the use of newsgroups via NNTP is blocked by many organizations. NNTP uses port 119.
Electronic Data Interchange
Electronic Data Interchange (EDI) is the transfer of structured data from one computer to another without human intervention. Currently, there are several different EDI standards in use. The Federal Information Processing Standards (FIPS) Publication 161-2 states that a long-term goal is to create a single universally used family of EDI standards. An EDI standard defines the following:
• Syntax used to compose messages and separate parts of the message
• Types and definitions of application data elements
• Messages types
• Definition and sequence of control data elements in the message headers and trailers
Mapping Well-Known Ports to Protocols
There are a total of 65,536 TCP ports and 65,536 UDP ports. They are divided into three sections:
• Well-known ports (0 to 1023) These ports are assigned to widely used protocols by the Internet Assigned Numbers Authority (IANA).
• Registered ports (1024 to 49,151) These ports are also assigned by IANA, although most are not as widely used as the well-known ports.
• Dynamic (49,152 to 65,535) These ports are assigned dynamically by internal systems.
As an example of how ports are used, consider Figure 3-8. The client is using a web browser to connect to an organization’s internal web server. When the user clicks a link to connect to a web server, several things happen to retrieve a web page. To begin, the client creates a packet and sends it to the web server.

Figure 3-8 Using IP addresses and ports
The packet is built with information about the source and destination of the packet. A web server uses port 80 for HTTP, so the destination port is port 80. The client adds its IP address as the source IP address and then identifies an unused port in the dynamic range and assigns it as the source port for this traffic. This source port is mapped to the user’s web browser application.
TCP/IP is used to get the packet to the server using the destination IP address. Once the packet reaches the server, the destination port is used to get it to the protocol, service, or application that is servicing that port. In this example, the destination is port 80, the well-known port for HTTP. The packet is sent to the web server application servicing HTTP.
The web server then creates the web page and puts the data together to return the web page to the client. Because the source of the original packet was 192.168.1.20 with a port of 49,152, this now becomes the destination. Again, TCP/IP is used to get the packet to the client computer.
When the client receives the packet, it identifies the destination port (49,152), which is mapped to the web browser application. The operating system sends the data to the web browser, which then displays it.
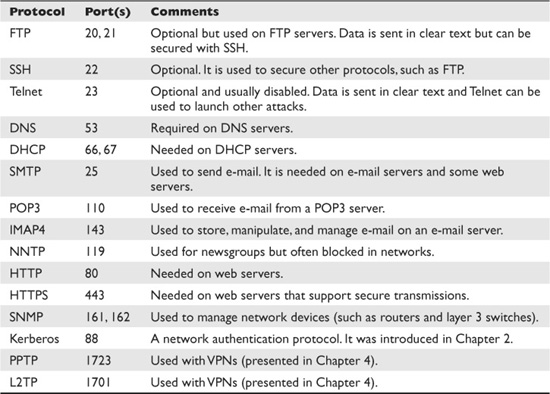
Table 3-1 lists many common protocols and ports, along with some basic comments about the protocol.