The OSI Model
The Open Systems Interconnection (OSI) Model was developed by the International Organization for Standardization (ISO) and includes seven layers. It is used to describe a framework for connecting multiple computers to each other. Each layer is focused on a set of specific tasks or functions.
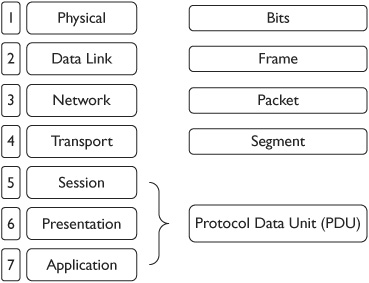
Data is packaged, or encapsulated, at each layer with additional data that the layer requires. For example, at the lowest layer (the physical layer), data arrives as bits (ones and zeros). The next layer (the data link layer) adds additional data and packages the data into frames. Figure 3-1 shows a diagram of the OSI Model identifying the layers and the data encapsulation names. The following subsections describe these different layers.

TIP Many people memorize the layers of the OSI Model with a mnemonic. For example, All People Seem To Need Data Processing (for Application, Presentation, Session, Transport, Network, Data link, and Physical) is one, and Please Do Not Throw Sausage Pizza Away (for Physical, Data link, Network, Transport, Session, Presentation, and Application) is another.
For the SSCP exam, you don’t need to know the OSI Model as in-depth as you would for a networking certification such as Cisco’s CCNA or CompTIA’s Network+. However, you should have a basic understanding of the model and what occurs at each layer. This section provides a brief introduction to the OSI Model. Later in this chapter, relevant protocols will be mapped to the different layers.
The Physical Layer (Layer 1)
The physical layer provides a direct connection to the network. It defines how data is passed on to the network, including the transmission method, such as via wired or wireless techniques. The physical layer includes physical items such as the cabling, hubs and repeaters, and wireless radio waves required to provide a connection to the network.
Security at this layer is focused on protecting access to the network connections. If attackers are able to connect a protocol analyzer or sniffer via unprotected cabling, they can intercept data going across the network.

TIP A sniffer can capture and analyze packets sent over both wired and wireless networks. If data is sent in an unencrypted (clear) text form, an attacker can capture the data and read it. If credentials such as a username and password are sent in clear text, the attacker can learn the credentials by capturing and analyzing the traffic.
The following are the different types of media used for data transmissions:
• Coaxial cable This is an older technology that is rarely used today even though it supports a higher bandwidth and longer cable lengths than twisted pair. It is relatively easy for an attacker to tap into a coaxial cable connection.
• Twisted pair This is the most commonly media used today for data transmissions. Unshielded twisted pair does not have shielding and is susceptible to electromagnetic interference (EMI) and radio-frequency interference (RFI). Shielded twisted pair provides protection against EMI and RFI. It is relatively easy for an attacker to tap into a twisted pair connection.
• Fiber-optic cabling Fiber provides the highest bandwidth and can support cable runs up to 40 kilometers. Although more expensive than copper cable such as twisted pair, fiber is becoming more and more popular. It is free from EMI and RFI issues and it is harder to tap into than wireless, twisted pair, and coaxial.
• Wireless transmissions Wireless transmissions use radio-frequency waves to transmit the signals over the air. Because they travel over the air, they are the easiest to intercept.

EXAM TIP Know what media is the easiest to intercept (wireless) and what transmissions are the most difficult to tap into (fiber connections).
Data traveling on the physical layer is packaged and transmitted as bits (ones and zeros) and bit streams. The physical layer converts the ones and zeros from the media and passes a bit stream to the data link layer, which packages the data as a frame.
The Data Link Layer (Layer 2)
The data link layer provides reliable delivery of data across the network and provides a means to transfer data between devices on the network. The Media Access Control (MAC) address (or physical address) is used here.
Although the MAC is assigned to network interface cards (NICs), it’s worth noting that it’s possible to assign a different MAC address to a NIC. This allows an attacker to spoof the source MAC address so that traffic appears as though it’s coming from a different source.
Basic layer 2 switches work at this layer. As traffic comes into a switch on a physical port, the switch identifies the MAC address of the computer sending the data. It then creates a table mapping the MAC address to the port. When unicast traffic must be sent to that computer, the switch sends the data to that physical port only.
Data traveling on the data link layer is packaged and transmitted as frames.
The Network Layer (Layer 3)
The network layer provides routing for data across a network by analyzing the IP address and determining the best route to the destination computer. The flow of data across the network is controlled at this layer.
Routers and layer 3 switches are the primary hardware devices used at this layer. Routers use access control lists (ACLs) for basic packet filtering to control what traffic is routed on the network. An ACL can block or allow traffic based on IP addresses, logical ports, and even some protocols.

TIP Well-known ports are logical numbers matched to specific protocols. For example, HyperText Transfer Protocol (HTTP) uses the well-known port of 80. By blocking port 80, the router’s ACL blocks HTTP traffic that is using port 80. The port number is embedded in the packet.
Spoofing is when a person or device impersonates or masquerades as another. It is usually done for malicious purposes. There are different types of spoofing, but in each case, the attacker makes it appear as though data is coming from a different source.
MAC address spoofing occurs when an attacker changes the source MAC address to another MAC address. An attacker may do this to bypass a MAC filter on a wireless network. The wireless filter allows only specific MAC addresses, but by spoofing an allowed MAC address, the attacker easily bypasses the security.
Internet Protocol (IP) address spoofing happens when an attacker changes the source IP address. For example, an attacker may change the IP address so that traffic appears as though it’s coming from a trusted source, such the IP address of trusted computer.
E-mail spoofing occurs when an attacker changes the From field of an e-mail to make it appear as though it’s been sent from somewhere else. This is commonly done with spam and especially phishing attacks. For example, a phishing e-mail may look like it’s coming from someone at a bank, but it’s actually coming from an attacker. The phishing e-mail often tries to trick a user into clicking a link and providing private information such as the user’s logon credentials.
IP is the protocol used for addressing. Currently both IPv4 and IPv6 addresses are being used on the Internet and in many internal networks. An IPv4 address is made up of 32 bits and is commonly expressed in dotted decimal format (such as 192.168.1.1). An IPv6 address is made up of 128 bits and is expressed with 32 hexadecimal characters, in eight groups of four hexadecimal (such as fe80:0000:0000:0000:045d:2376: b95f:77f5).

TIP There are other ways to express an IPv6 address. The example could also be expressed as fe80::45d: 2376:b95f:77f5 using zero compression. Notice the string of zeros is replaced with two colons (::).
Data traveling on the network layer is packaged and transmitted as packets.
The Transport Layer (Layer 4)
The transport layer provides reliable end-to-end communication services for applications, and includes error detection and recovery mechanisms. Data traveling on the transport layer is packaged and transmitted as segments. Many of the port assignments for upper-layer protocols (such as port 80 for HTTP) occur on this layer.
Two primary protocols used at this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP
TCP is a connection-oriented protocol that provides guaranteed, reliable communication for devices on a network. It uses packet sequencing and the destination acknowledges every packet that it receives. A three-way handshake establishes a TCP connection, as shown in Figure 3-2.

Figure 3-2 TCP three-way handshake
In Figure 3-2, a client is establishing a TCP session with a server. In the first step, the client sends a packet with the synchronize (SYN) flag set. The server responds with both the acknowledge (ACK) and SYN flags set. Last, the client sends back a packet with the ACK flag set. At this point, the session is established.

EXAM TIP In a common attack known as a SYN flood attack, the client withholds the third packet. The server is left with a half-open session consuming system resources while it waits for the third packet. However, instead of sending the third packet, the attacker floods the system with more SYN packets.
If another protocol requires guaranteed delivery, it uses TCP, because IP (the other part of TCP/IP) does not guarantee delivery.
UDP
UDP is a connectionless protocol. Instead of checking to see whether a connection exists with another system before sending data, it simply sends it. Another way of thinking of this is that UDP gives a “best effort” to send the data without verification. This could be like you sending a friend an e-mail to pass on some information. You’re pretty sure your friend will receive it, but you don’t have any verification.
UDP is commonly used with diagnostic protocols because the overhead of establishing a session is not needed when performing diagnostics tests. You’ll see UDP used in simpler protocols such as Trivial File Transfer Protocol (TFTP, a simple, streamlined version of File Transfer Protocol [FTP]), which is used to send small files from one system to another. FTP uses TCP, but TFTP uses UDP. UDP is also common with streaming data such as streaming audio or video. With streaming data, it’s acceptable to lose some bits occasionally here and there. For example, a steaming video file may hiccup occasionally when some bits are lost, but the overall file still plays.

TIP The terms connection-oriented and connectionless have nothing to do with a wired or wireless connection. Instead, they refer to the logical nature of a connection. TCP ensures both sides can communicate before starting a session. UDP simply sends the data without checking to see whether a logical connection exists.
The Session Layer (Layer 5)
The session layer establishes and maintains sessions between applications or software processes on the local and remote systems. It keeps the session information for one application separate from the session information from other applications.
Data traveling on the application, presentation, and session layers is referred to as protocol data units (PDUs).
The Presentation Layer (Layer 6)
The presentation layer standardizes data presentation for the application layer. It translates data using standards such as American Standard Code for Information Interchange (ASCII), Extended Binary Coded Decimal Interchange Code (EBCDIC), Joint Photographic Experts Group (JPEG), Moving Picture Experts Group (MPEG), and so on. Some data encryption and decryption occurs at this layer. Additionally, data can be compressed and decompressed at this layer for better network performance.
The Application Layer (Layer 7)
Network applications use the application layer to implement specific user applications. The layer provides the services needed for applications that communicate across a network.
From a security perspective, many additional features can be implemented at the application layer. These include authentication, access control with mechanisms such as permissions, encryption for confidentiality, hashing for integrity, and the use of digital signatures for non-repudiation.

TIP Encryption, hashing, and digital signatures are explored in more depth in Chapter 14.
