Exploring Attack Types
There are numerous attack methods and types and countless variations. As attackers have launched new types of attacks, IT security professionals have identified new methods of protection. When one attack method no longer works, attackers develop others. It’s a constant battle between the attackers and security professionals. As long as criminals are able to gain money or achieve other criminal objectives through attacks, expect them to continue.

NOTE Although attackers attack for motives other than money, such as revenge and different types of espionage, money remains a primary motivator. Many of the improvements in attacks and attack methods are driven by criminals using attacks to line their pockets with other people’s money.
The following section outlines many of the common types of attacks. This is by no means a complete list, but it does provide an overview. Also, many current attacks and attack methods are modifications of basic attacks.
DoS
A denial-of-service (DoS) attack attempts to prevent a system from answering legitimate requests from users. The attack often attempts to overwhelm the system by consuming system resources; while the system is busy dealing with the attack, it doesn’t have enough resources to respond to regular requests. The goal is to deprive the organization, or its customers, from the use of their resources.

EXAM TIP A denial-of-service (DoS) attack attempts to disrupt a service. It can do so by taking a system down or by consuming system resources with meaningless requests that overload its ability to respond to legitimate requests. The effect is that valid authorized users are unable to access a system.
As an example, a common DoS attack is a SYN flood attack that initiates, but doesn’t complete, the TCP handshake process. Chapter 3 described the three-way handshake used by TCP. Recall that a normal three-way handshake includes the following three packets:
1. A TCP client sends a packet with the SYN flag sent to a system such as a server.
2. The server responds with a packet with the SYN and ACK flags set.
3. The client then completes the handshake process by sending back a packet with the ACK flag set.
In a SYN flood attack, the attacker withholds the third packet, leaving the half-open session on the server. For example, consider Figure 5-1, which shows the process of a SYN flood attack. The first two packets are sent just like a regular three-way handshake, but the third packet is not sent. Instead, the attacker then sends out another SYN packet.


EXAM TIP In a SYN flood attack (also called a TCP SYN, TCP flood, and TCP half-open attack), the attacker withholds the third packet in the TCP handshake process.
This is similar to one person sticking his or her hand out to shake hands with you, you extending your hand, but then at the last second, the other person pulls his or her hand away. The person sticks his or her hand out again, you extend your hand again, and he or she pulls his or her hand away again. You probably won’t fall for this over and over, but TCP will keep answering with SYN/ACK packets and keep waiting for the third packet to complete the process.

TIP Most intrusion detection systems (IDSs) can detect this type of attack. They will then change the ACL on the firewall or a boundary router to block all traffic from the offending IP address.
If this happens once or twice, it’s no big deal. However, an attacker can initiate hundreds of half-open sessions in a short period of time. If the attack isn’t detected, the server can keep each of these sessions open as it waits for the third packet. Each one of these sessions consumes resources. The attack can slow down the server, and in extreme cases, it can actually crash the server.
The following are some other well-known DoS attacks:
• Ping of death An ICMP ping packet is normally 32 bytes of data, although different operating systems may vary the size. A ping of death attack changes the size of the ping packet to more than 64 KB. These large ping packets have crashed some systems, although most systems recognize the attack today and can avoid it.
• LAND A local area network denial (LAND) attack tricks a system into sending out packets to itself in an endless loop. In other words, the source and destination addresses are set to the attacked system. A LAND attack can shut down a system.
• Smurf ICMP ping packets are broadcast to multiple computers on a network, but the source address is spoofed. Normally, ping sends echo requests packets to a single system and receives echo replies back from the system. If a ping is broadcast, then all systems on the subnet will receive the echo requests and flood the system sending out the broadcast. When the source address is spoofed with a victim’s IP address, all of the pings flood the victim.
• Fraggle This is similar to the smurf attack, but instead of using ICMP packets, it uses UDP echo packets for the attack.

TIP Although many of these attacks will fail on protected systems, they are valuable to understand. Many current attacks are simply variations on attacks that have been successful in the past.
Protecting Systems from Attacks
Many attacks are possible because of vulnerabilities discovered in an operating system. However, once these vulnerabilities are discovered, the vendor develops, tests, and releases patches and updates to plug the security holes. As long as these updates are applied to the systems, the systems are no longer vulnerable to that specific attack. However, if the system is not patched or updated, it remains vulnerable.
Chapter 9 covers countermeasures and controls, including a basic practice of hardening systems. Systems are hardened by taking steps such as keeping the system up to date with current patches, removing or disabling unneeded protocols and services, and enabling software firewalls. IDSs can also detect and prevent successful attacks. Chapter 8 covers different types of IDSs and how they work.
Of course, all of this points to the importance of security. An organization that doesn’t use these basic controls can still be vulnerable to even older attack methods.
DDoS
A distributed denial-of-service (DDoS) attack is similar to a DoS attack except that it comes from multiple attackers at the same time. For example, an attacker may launch a TCP flood attack against a single system from hundreds or even thousands of systems. A key to the success of DDoS attacks is for the attacker first to take control of multiple systems and then use these systems to launch the attacks.

EXAM TIP The first step in a DDoS attack is to compromise as many systems as possible. The attacker then controls these systems to launch the DDoS attack.
Attackers often use botnets to launch DDoS attacks.
Botnets and Zombies
A botnet is a group of computers (called zombies) controlled by an attacker. The term botnet is derived from robot and network. The attacker manages a command control center and the computers in the botnet do the bidding of the attacker, similar to how mindless zombies in movies are controlled by fictional wizards.
Computer users are usually unaware that their computer has become a zombie. Instead, computers are often infected with some type of malware that infects the computer without the user’s knowledge; the attacker then takes control. One way that a system is infected is through a drive-by download, as shown in Figure 5-2. When a user visits an infected or a malicious website, malware is downloaded and installed on the user’s system. Users sometimes unknowingly visit these sites during Internet surfing sessions; other times, a user is tricked into visiting a malicious website through a phishing attack.
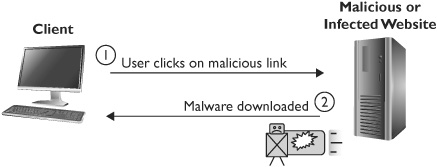
Figure 5-2 Single system infected in drive-by download

TIP Drive-by downloads are any downloads that occur without the user’s knowledge. They can include many different types of malware, including software that joins the computer to a botnet.

TIP Although Figure 5-2 shows a system infected by a drive-by download, it could just as easily get infected by a user being tricked into installing malware, such as a Trojan horse. Chapter 6 covers different types of malicious software, including Trojan horses.
In a phishing attack, the user receives an e-mail that tries to trick the user into either giving up information or simply clicking a link. For example, a common phishing e-mail looks like it comes from a bank and tells the user that suspicious activity has been noted on his or her account. The user is told to click the link to verify his or her account, and if the user doesn’t, the account will be locked out.
If any users click the link, they are taken to the website and the drive-by download starts. Notice that in this case, it doesn’t matter whether a user enters any personal information or not because the attacker really only wanted the user to click the link. If a user does enter information, the attacker can use it to empty the user’s account, in addition to recruiting the user’s computer as a zombie in the botnet.
Figure 5-3 shows a botnet with multiple zombies in it. These zombies regularly check with the attacker’s command and control center, which is hosted on one or more servers controlled by the attacker. Smaller botnets may have a single server hosting the command and control software. Larger botnets may have dozens of servers located around the world.

Figure 5-3 Zombies regularly check in with the command and control center
The commands issued to the zombies in the botnet vary. Zombies can be directed to bombard a server with a DDoS attack, as shown Figure 5-4. Zombies within a botnet can also be directed to take other malicious actions, such as sending unwanted or unsolicited e-mail (including phishing e-mail), spread malware, or launch other types of attacks.

Figure 5-4 Zombies can launch DDoS attacks
Criminals often rent out the botnet to other criminals, and if the botnet is large, they can generate a significant amount of money from these rentals. Many botnets control tens of thousands of computers, and some control more than a million. At its height, the Rustok botnet had more than a million zombies and sent out billions (yes, billions with a b) of spam daily. The Rustok botnet was taken down in March 2011 and IT watchers reported that spam levels immediately plummeted.

NOTE Microsoft launched the Microsoft Digital Crimes Unit (DCU) in 2010, and it has been successful in working with other organizations to take down at least two botnets (Waledac and Rustok). You can read about the DCU here: http://www.microsoft.com/presspass/presskits/DCU/.
Spam
Spam is unsolicited commercial e-mail (UCE) and other unwanted electronic messages sent in bulk. It is most often associated with e-mail, but can also be delivered via other means, such as instant messaging. Spam usually includes advertisements, but can also be used in different types of attacks launched from botnets and other attackers. For example, phishing attacks, described later in this chapter, uses spam.
The costs for spammers sending spam are low. A single e-mail can include multiple e-mail addresses, making it relatively easy to send an e-mail to thousands of recipients at a time.
Spammers harvest e-mail addresses using a variety of methods. For example, some programs called web spiders crawl through the web looking for the @ character to identify e-mail addresses. If you post messages on a website with your e-mail address, you can easily be added to a spam list. Other spammers purchase e-mail lists from other companies, and some simply steal these lists.
Sniffing Attack
A protocol analyzer (also called a sniffer or packet sniffer) is capable of capturing and analyzing packets that are transmitted over a network. Network administrators commonly use sniffers for legitimate purposes while troubleshooting networks. However, attackers can also use sniffers for malicious purposes, including data theft. A popular sniffer is Wireshark. It’s available as a free download and runs on most platforms, including Windows, UNIX, Linux, and more.

NOTE You can read more about Wireshark and download a copy from here: http://www.wireshark.org. Wireshark was previously known as Ethereal.
When you run any protocol analyzer, you capture the packets and can then save the captured data as a file (commonly called a capture) and browse them at your leisure. IT professionals use sniffers to troubleshoot and learn details about a network. Similarly, attackers can use a sniffer to capture data and exploit it for personal gain.
If data is sent over the network in clear text, an attacker can easily read it in a sniffer. However, if the data is encrypted, it can’t be read. For example, Chapter 3 mentioned the risks of protocols such as File Transfer Protocol (FTP) and Trivial File Transfer Protocol (TFTP) related to unencrypted transmissions. Both FTP and TFTP send data over the network in clear text if they aren’t encrypted with a protocol such as SSH. An attacker can capture these transmissions and read credential information, such as usernames and passwords, and the actual data.
Figure 5-5 shows a screenshot of Wireshark with a capture. During this capture, I connected to a network drive and opened up a file named passwords.txt. After stopping the capture, I was able to browse through it to locate the packet that held the data, an SMB Read AndX Response command. In the figure, you can see that the packet numbered 1470 is selected in the top pane (arrow 1). The center pane provides details on the packet that you can open as desired. The Read Andx Response section shows that this came from a file named passwords.txt (arrow 2). The bottom pane shows the data in both a hexadecimal and text format. The text data in the passwords.txt file is “Darril Gibson IPa$$edSSCP” (arrow 3).

Figure 5-5 Viewing text data in Wireshark
Sniffers can work in either promiscuous or nonpromiscuous mode. In nonpromiscuous mode, the sniffer will capture only data sent directly to or from the computer’s IP address. It will not capture any packets that do not have the computer’s IP address as either the source or destination address. However, when the sniffer works in promiscuous mode, it will capture all data that reaches the computer regardless of the IP address.

EXAM TIP Promiscuous mode allows a sniffer to capture all data that reaches the sniffer. When the sniffer runs in nonpromiscuous mode, it will capture only data sent directly to or from the system running the sniffer.
One of the ways an organization reduces vulnerabilities from sniffer attacks is to use switches instead of hubs. For example, consider Figure 5-6, which shows both a hub and a switch in action. In the figure, both PC1 and PC3 are sending data to and from each other. When a hub is used, the hub sends the data to all ports and an attacker with a sniffer running on PC2 is able to capture the transmission with a sniffer (as long as the sniffer is running in promiscuous mode).
Figure 5-6 Comparing data sent via a hub and via a switch
However, when a switch is used, data in this transmission is only sent to and from PC1 and PC3. The attacker running a sniffer from PC2 is not able to capture the data because the traffic doesn’t ever reach the switch port for PC2.
It’s worthwhile noting that many switches and routers have maintenance ports. If an attacker can connect directly to the maintenance port of the network device, he will be able to capture all the traffic going through it. This just underscores the importance of physical security. Network devices such as routers and switches must be protected with physical security, such as locking them in server rooms.
Ping Sweep
Attackers often start an attack with a ping sweep. A ping sweep uses ICMP to identify what systems are operational within a range of IP addresses. This is similar to sending a ping to a system and waiting for a response. However, instead of sending a single ping to a single system, the ping sweep sends pings to all the systems within a range of IP addresses.
This part of an overall attack strategy. The ping sweep performs reconnaissance to identify the system. Other tools (such as port scanners) identify details on individual systems in a fingerprinting attack.
Port Scan
The port scan attempts to detect what ports are open on a system as part of an overall fingerprinting attack to gather information on a system. Chapter 3 covered well-known ports. Recall that well-known ports are in the range of 0 to 1023 and are commonly used by specific protocols. For example, SSH uses port 22, SMTP uses port 25, and HTTP uses port 80.

EXAM TIP A fingerprinting attack attempts to gather information on specific computers, such as what protocols are running on the system or what specific functions the server performs. In contrast, a reconnaissance attack is a broad-based attack that attempts to identify systems on a network. For example, a ping sweep can identify what computers respond to ping requests to identify what computers exist and then follow the ping sweep with a port scan to fingerprint the individual systems.
If a port scan determines that port 80 is open, it is highly likely that the system is servicing the HTTP protocol. Further, if it’s answering HTTP protocol requests, it is probably a web server. It could be an Apache web server running on a Linux system, an Internet Information Services (IIS) web server running on a Microsoft system, or something else. Additional steps beyond the port scan are used to determine exactly what operating system the server is using and what web server software is running.
Port scanning tools may run sequentially through ports. You can detect them by checking firewall logs or by using automated IDSs. For example, if the same source IP addresses checks for responses on ports 20, then 21, then 22, and so on, it’s a clear indication of a port scan. More sophisticated port scanners can randomize the order of the port numbers that they check, such as 22, then 80, then 25, and so on. However, most IDSs are aware of both tactics and can detect a port scan if it’s sequential or randomized.
Salami
In a salami attack, an attacker performs multiple minor actions that can go unnoticed or unreported, but due to the large number of these small actions, they can add up to big gains. Its name comes from a metaphor of slicing small slivers of salami sausage to create enough pieces to create a sandwich.
In one of the classic examples of a salami attack, an attacker shaves a penny off another transaction. If any individual loses a penny, the victim is unlikely to notice or even complain if he or she does notice. However, when the same tactic is used thousands or millions of times, the attacker can gradually pilfer a substantial amount of money. For example, programmers in the movie Office Space realized that they could write a program to shave fractions of pennies from transactions where they work. Unfortunately, they misplaced a decimal and ended up taking too much money, resulting in some comical results.
Salami attacks can also be used to gain information from databases. Instead of getting the entire database at a time, attackers can get small pieces of data and then combine them to reproduce the full picture. Espionage works this way when a spy tries to learn as much as he or she can through as many innocuous sources as possible. Similarly, a social engineer (described later in this chapter) often tries to gather small pieces of data from multiple sources.

TIP Chapter 11 delves into databases a little deeper, including the concept of inference. In an inference attack, an attacker collects multiple pieces of small, seemingly inconsequential information, but is able to put this together to infer or deduce sensitive information.
Man-in-the-Middle
Man-in-the-middle (MITM) attacks perform electronic eavesdropping by placing a system that is able to capture data sent between two other parties. For example, if one computer is exchanging data with a server, an MITM attack can capture all the data between the two systems. The attack is transparent, and neither of the systems is aware of the MITM system.

EXAM TIP A packet sniffer such as Wireshark is used in an MITM attack. The attacker captures packets and then analyzes the data to learn information. If data such as passwords or files is passed over the network in clear text, it’s rather easy for an attacker to gather and read this information.
An active MITM attack can be quite sophisticated. Consider Figure 5-7. A user is using a web browser to connect with a web server over the Internet. The web browser indicates that an SSL session is established with HTTPS in the URL and a lock icon, and in truth, an SSL session is established. However, instead of having a secure SSL session with the web browser, the user has a secure SSL session with the MITM system.
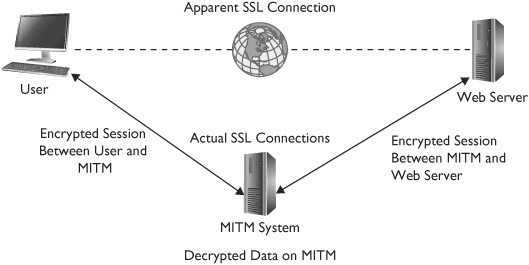
Figure 5-7 MITM attack using SSL
The MITM system establishes two SSL sessions. One session is secure between the user and the MITM system, and the other session is secure between the MITM system and the web server. On the MITM system, all of the data is decrypted and can easily be read.
It’s difficult to set up such an attack without control of either the user’s internal network or the web server’s internal network. Some organizations have set this up internally to track activity of users within the organization. For example, if the MITM system is established internally, internal user’s activity can be fully tracked. Before doing this, an organization would typically let employees know via an acceptable usage policy that their online activity is tracked and that certain activity is prohibited.
If the web server is hosted at a disreputable hosting company, the hosting company may be able to implement an MITM system there. They can then capture user data such as credit card data and then run up charges on these credit cards.

TIP MITM attacks can be active or passive. In an active MITM attack, the attacker tries to capture data from specific systems. In a passive attack, the attacker attempts to capture data from any system.
Session Hijacking
Session hijacking is another sophisticated attack where an attacker captures information from an ongoing TCP/IP session and attempts to take over the session in the place of one of the parties. Such an attack is possible with HTTP sessions where cookies are used. If successful, the attacker may gain access to either of the systems in the original session or launch a DoS attack on one of the systems to take it out of service.
The session hijacking attack often starts with a sniffing attack where the attacker gathers information about an ongoing session. The gathered information includes cookies that are passed back and forth between the web client and the web server.

TIP A cookie is a text file stored on a user’s system. When a user visits a website, the website is able to read the cookie and use it to identify the user. The cookie also includes a session ID used to identify the current session to the web server.
Although session hijacking appeared to be waning, the release of a program called Firesheep (a Firefox extension) was released in 2010 that allows attackers to listen for and exploit session cookies transmitted over a wireless network. For example, an attacker can sit in a public wireless hotspot, capture these session cookies, and use them to hijack HTTP sessions. Although the use of Firesheep to listen in on other conversations breaks many different wiretapping laws, laws aren’t an effective deterrent for many criminals.
Replay
A replay attack starts as an eavesdropping attack where the attacker uses a sniffer to capture the data. However, the replay attack goes a step further and uses the information gathered to impersonate a system involved in the captured session.
For example, two computers may establish a session and exchange authentication information. An attacker will capture this information and use it later to impersonate one of the systems.
Several methods help prevent the success of this type of attack. For example, Kerberos (a network authentication protocol) uses time stamps and requires systems to be within five minutes of each other. These time stamps restrict the time that an attacker can replay captured data. Additionally, session tokens are often used within sessions. For example, CHAP, which was introduced in Chapter 4, uses a nonce (number used once) to create session tokens. These session tokens aren’t reused, so they cannot be reused in a replay attack.
Buffer Overflow Attacks
A buffer overflow occurs when a system receives more data than it expects and it’s unable to handle it gracefully. Programs, or applications, have areas of memory called buffers that they use for temporary data storage. Normally, these buffers are specifically defined areas of memory, and the application is unable to access memory spaces beyond the buffers.
However, there are times when an application gets overwhelmed with the data sent to it, and the resulting error causes it to exceed the defined buffer. In this case, the application causes the buffer to overflow into other areas of memory that are normally protected. If attackers can exploit a buffer overflow error, they are able to write additional data into the overflow area. Attackers often include a large volume of no operation (NOOP) code in an attack. Even if the command is to do nothing, a sufficient volume of NOOPs can cause a buffer overflow.

EXAM TIP A buffer overflow problem starts as a programming error. However, if it’s detected, an attacker can launch a buffer overflow attack. Successful buffer overflow attacks allow an attacker to gain elevated privileges and insert malicious code into normally protected memory areas of a system.
As a simple example, a web page may expect a user to enter some specific data, such as a number between 1 and 10. An attacker may try to send different data, such as an escape sequence, to see what happens. If the different data is not expected and programmed for, it can cause an error. If the error is not handled gracefully, the attacker can then try to repeat the error but add additional data. For example, the additional data could be a malicious script that installs itself on the server.
One of the primary ways to prevent buffer overflow attacks is to keep systems updated. When a buffer overflow vulnerability occurs, vendors release patches that fix the problem. If the patch is applied, the system is protected. Of course, if patches are not applied, the system remains vulnerable.

EXAM TIP A key to keeping a system secure is to keep it updated with current patches and fixes. This protects against buffer overflow attacks and many other types of attacks.
Scareware and Ransomware
Scareware or ransomware is malware that describes itself as antivirus software. A user may visit a website and then see a pop-up similar to that shown in Figure 5-8, which indicates that the system is infected with a virus. However, every user who visits the website will see the exact same message. A virus hasn’t been detected; instead, this is an attempt to trick the user into installing malicious software on their system.

Figure 5-8 Scareware pop-up trying to trick a user into installing malware

NOTE Although I created the dialog box shown in this figure, it is similar to some dialog boxes that users may see when visiting a website. There isn’t a Trojan virus named fakemeout.takemymoney. However, the actual scareware that users can download looks extremely realistic, using icons similar to those used in other security programs. Attackers put a lot of time developing the look and feel of the scareware application to make it appear as though it is antivirus software. However, unlike actual antivirus software that truly scans a system looking for malware, scareware does not look for malware.
If the user does click on the Fix Now button, it prompts the user to download and install an application. Scareware applications indicate that the system is infected with a virus even if it isn’t. The application then lets the user know that the free trial edition only scans their system. To remove the supposed virus, the user must pay.
Although the extortion nature of scareware is malicious enough by itself, most scare-ware applications do more. For example, the downloaded application could join the system to a botnet that can be controlled by the attacker. It could download and install a keylogger designed to capture all of their keystrokes and send it off to an attacker to use later. The possibilities are limited only by the imagination and technical abilities of the scareware authors. History shows us that they have a lot of imagination when it comes to stealing money from victims, and their technical abilities continue to increase.
What should a user do when seeing something like this? Close the dialog box and leave the site. If a user doesn’t have antivirus software installed, he or she should go directly to a reputable site to get it, and not try to install it from one of these warnings. There are even some reputable companies that provide free editions of antivirus software to individual users.
Password Attacks
Attackers often try to learn passwords through different methods. If the attacker is able to learn the username and password of an account, the attacker can then impersonate the user by logging on with the user’s credentials. A password cracker is a program that tries to discover, or crack, passwords.
The following list describes some common methods of password attacks:
• Brute-force In a brute-force attack, the attacker tries all possibilities until getting a match. This can be quite time consuming when performed manually, but password crackers automate the attempts. Brute-force efforts generally take the most time and effort. This attack can be beaten by using strong passwords of sufficient length, such as those at least eight characters long. The longer a password is, the harder it is to crack with a brute-force attempt.
• Dictionary A dictionary attack attempts to use all the words in a dictionary or a database of different words. Password dictionaries usually include words from multiple languages in addition to commonly used passwords such as 123456, iloveyou, Qwerty (the first five letters next to the tab key), 7777777, letmein (let me in), trustno1 (trust no one), and qazwsx (the first six letters from top to bottom on the keyboard). A dictionary attack can be beaten by using strong passwords including a mixture of upper- and lowercase letters and symbols.
• Social engineering The simplest way to get a password is simply to ask for it. Although most users won’t just give up their password easily, they can be tricked or conned into giving it up by a skilled social engineer. For example, phishing attacks (described later in this chapter) often ask users for their username and password, and some users respond.

TIP Dictionaries are available in multiple languages, so using words from different languages doesn’t make a password more secure.
A rainbow table is a more sophisticated attack used to learn passwords. In short, a rainbow table is a list of hashed passwords used to compare against a captured hashed password. The rainbow table is used for comparative analysis; if a match is found, the password is discovered. To help make this attack more understandable, let’s slow the process down and examine the different steps.
One of the ways that passwords are protected is by hashing them. A hash is simply a number created by executing a hashing algorithm against the password, and the hash will always be the same if the password is the same. For example, if the password is P@ssw0rd, the resulting hash may be 1A2B3C. The actual hash would be more complex, but it’s shortened here for brevity.
Now imagine that an attacker has captured a hashed password either by hacking into a password database or by capturing packets with a sniffer. In either case, the attacker now knows that the hash of a password is 1A2B3C. The attacker can guess a password (such as P@ssw0rd), calculate the hash, and then compare it against the captured hash of 1A2B3C. If it’s the same, the attacker now knows the original password. If it’s not the same, the attacker can guess another password and repeat the process until the password is discovered.
The most time-consuming part of this process is guessing a password and then calculating the hash. However, a rainbow table shortens this time considerably. A rainbow table is a huge database that includes all possible combinations of characters that can be used as a password, along with the hashed version of the password. Several rainbow tables are available using different hashing algorithms and targeted against specific operating systems. Although rainbow tables can be very large (as big as 64 GB), they significantly reduce the time required to crack a password.
If an attacker has a rainbow table, all he needs to do is compare the captured hash against every entry in the rainbow table. When a match is discovered, the matching entry in the rainbow table identifies the actual password used to create the hash.
To beat a rainbow table, you salt the password before hashing it. A salt adds a random number of bits to the hashed password. In other words, an unsalted hash of P@ssw0rd may be 1A2B3C, but when it’s salted, it could be 3602FD or just about any other hexadecimal number.

EXAM TIP Some password crackers use rainbow tables to speed up the process of cracking a password. However, by salting the hashed password, you render the rainbow table ineffective.
Covert Channel
A covert channel is a mechanism used to transmit and receive information between two computers surreptitiously. A covert action is a secret one that is not open or acknowledged, such as a clandestine spy operation. Channel refers to the communications path. A covert channel uses a communication path that isn’t normally used in the same way and can bypass traditional controls such as firewalls and intrusion detection systems.

TIP Although covert channels are difficult to create, they can be used as a secret method to pass information between two entities for malicious purposes.
For example, TCP uses a TCP handshake process to establish a TCP session. The primary piece of information used in these packets, besides the source and destination data, is the SYN and ACK flags. However, there is room elsewhere in the TCP packet, such as in the protocol ID field, to add additional data such as ASCII codes for individual characters. If both systems know the data will be contained within the packet, one system can send the data and the other system can receive it.
The ability to transfer small pieces of data in the protocol ID field is a well-known tactic. Many firewalls and intrusion detection systems are able to check packets for this additional data and identify the covert channel. A successful covert channel uses a technique not known to others.
Cramming
Cramming is the practice of adding additional charges to a phone bill that are unauthorized, deceptive, or misleading. In other words, additional charges are crammed onto the original bill. The goal is often to trick phone customers into paying for services they did not authorize or receive.
For example, your local telephone company, or even a long distance telephone company, can start charging you for services that you haven’t requested or used. These additional charges may be listed as things like “other fees,” “service fee,” or “monthly fee.” If the company has described these fees to you and you agree to them, they are valid. However, if the fees differ from what was described or were never described, you may be a victim of cramming. Cramming is illegal and governed by the Federal Communications Commission’s (FCC) Truth-in-Billing rules.
Zero Day Exploits
Zero day exploits are attacks that take advantage of vulnerabilities that are unpublished and are often unknown by the vendor. The differences between these two are:
• Unpublished and unknown by the vendor, but known by an attacker For example, an attacker may discover a buffer overflow vulnerability and launch an attack using this vulnerability. The attacker may share the knowledge with other attacker friends, and each of these attackers can also launch zero day exploit attacks.
• Known by the vendor, but not published There are many times when a vendor knows about a vulnerability but hasn’t released a patch to fix it yet. For example, an antivirus company could discover an issue with a Microsoft operating system and inform Microsoft. Microsoft will investigate and write a patch to fix it, but its personnel also need to test the patch before releasing it. Any attacks that attempt to exploit the vulnerability before it is published are zero day exploit attacks.
Unpatched Systems and Zero Day Exploits
In some cases, people refer to a zero day exploit as an attack on a system shortly after the patch has been released but before the patch has been applied.
For example, Microsoft releases patches on “Patch Tuesday,” the second Tuesday of every month. However, IT personnel don’t always get their systems patched immediately because they need to test the patch. They may not get their system patched until Wednesday or Thursday, or even later.
Attackers often download these patches as soon as they are available and get as much information on them as they can find. They then reverse engineer the patch to discover the vulnerability the patch is fixing. Once they discover the vulnerability, they develop an attack method to exploit it.
Exploits of the vulnerability between the time when the patch is released and when the system is actually patched is sometimes called a zero day exploit. In this case, attacks on Tuesday or Wednesday after the patch is released may be called a zero day exploit.
Everyone doesn’t agree with this definition of a zero day exploit. Many security professionals say that if a patch is released, exploits against the vulnerability are simply attacks against unpatched systems. However, this does help emphasize the importance of keeping systems patched and up to date. Many successful attacks take advantage of unpatched systems, and these attacks can be prevented by keeping systems up to date.
The danger from zero day exploits also helps to emphasize the importance of a defense in depth strategy. If the vulnerability is unknown to the public and a patch isn’t released, IT personnel won’t know about it and certainly won’t have a patch to apply. However, other security practices can help prevent a successful attack.
For example, one of the basic elements of hardening a system, or making it more secure from the default configuration, is to disable unneeded protocols and services. Imagine that an attacker discovers a zero day vulnerability with the FTP. ServerA does not need FTP, but FTP is running on this server. ServerA is vulnerable to this attack. On the other hand, if ServerA was hardened and FTP was disabled, the server is not vulnerable to the attack.
Advanced Persistent Threat
Years ago, many of the attacks were launched by script kiddies. Script kiddies could have been bored teenagers running scripts and applications that someone else wrote, although they really didn’t understand the underlying details of what they were doing. However, attackers today are much more sophisticated.
Advanced Persistent Threat (APT), a relatively new term, refers to a highly sophisticated group of people who target their attacks. They have both the capability and intent to carry out successful attacks. Many countries reportedly have teams of IT personnel regularly probing the IT systems of organizations and other government networks.
For example, imagine that a country wants to gather intelligence on the United States. The country could put together a team of 100 specialists with a goal of gathering information on government computers in Washington, D.C. IP addresses are issued by geographic location, so the specialists could first identify all the IP addresses issued in Washington. This information is publicly available, so this task isn’t difficult. They can even use a site like geobytes (http://www.geobytes.com/iplocator.htm) to gather additional information on specific IP addresses.
They can then use ping sweeps to identify the IP addresses that are operational and then conduct port scans to identify open ports. Port scans may find that some computers have ports 80 and 443 open, indicating that they are web servers. Many port scan tools such as Nmap include additional capabilities and can actually determine the operating system, the version, and even the patches that have been applied. Instead of just suspecting that a server is a web server, Nmap can verify that it’s a Microsoft Windows server running Internet Information Services (IIS) as a web server. As the attackers in the APT continue, they gather more and more information on the systems. At some point, they will be able to discover which IP addresses are assigned to government computers and which IP addresses are assigned to nongovernment computers, along with specific details on the government computers.
The members of the APT could store all this information in a database and wait until they discover a zero day exploit or until a vulnerability is announced. For example, if they learn about a vulnerability with IIS, they would look in their database to identify any servers running IIS. They then attempt to exploit the vulnerability.
APTs don’t attempt to get all the information immediately. Instead, they are patient and happy to get a little bit of information at a time. However, they are also persistent. When one attack fails, they don’t give up. Instead, they look for other ways to attack and keep going at it until they get some success. Think of a group of firefighters. If they don’t succeed in putting out the fire immediately, they don’t quit and go home. Instead, they attack the fire from a different angle, or perhaps with different tools. People within an APT are just as persistent.
After many successful attacks against computers and networks in the United States, the United States government created the United States Cyber Command (USCYBERCOM), which became operational in 2010. Its mission statement is as follows:
USCYBERCOM plans, coordinates, integrates, synchronizes, and conducts activities to: direct the operations and defense of specified Department of Defense information networks and; prepare to, and when directed, conduct full-spectrum military cyberspace operations in order to enable actions in all domains, ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries.
Many other countries have created similar organizations to combat the threats of cyber warfare.

