Security of software applications (or lack of it) has been attracting a lot of importance in the past few years in the industry and the media. It seems that every other day, we hear about an instance or two of malicious hackers causing massive data breaches in software systems in different parts of the world, and causing millions of dollars worth of losses. The victims are either government departments, financial institutions, firms handling sensitive customer data such as passwords, credit cards, and so on.
Software security and secure coding has assumed more importance than ever due to the unprecedented amounts of data being shared across software and hardware systems—the explosion of smart personal technologies such as smart phones, smart watches, smart music players, and other smart systems has aided this immense traffic of data across the Internet in a big way. With the advent of IPv6 and expected large scale adoption of IoT devices (Internet of Things) in the next few years, the amount of data is only going to increase exponentially.
As we discussed in the first chapter, security is an important aspect of software architecture. Apart from architecting systems with secure principles, architects should also try to imbibe their team with secure coding principles to minimize security pitfalls in the code written by them.
In this chapter, we will look at the principles of architecting secure systems, and also look at tips and techniques for writing secure code in Python.
The topics we will be discussing can be summed up in the following list:
- Information security architecture
- Secure coding
- Common security vulnerabilities
- Is Python secure?
- Reading input
- Evaluating arbitrary input
- Overflow errors
- Serializing objects
- Security issues with web applications
- Strategies for Security – Python
- Secure coding strategies
A secure architecture involves creating a system that is able to provide access to data and information to authorized people and systems while preventing any unauthorized access. Creating an architecture for information security for your systems involves the following aspects:
- Confidentiality: A set of rules or procedures that restricts the envelope of access to information in the system. Confidentiality ensures that data is not exposed to unauthorized access or modification.
- Integrity: Integrity is the property of the system which ensures that the information channels are trustworthy and reliable and that the system is free from external manipulations. In other words, integrity ensures the data can be trusted as it flows through the system across its components.
- Availability: Property that the system will ensure a level of service to its authorized users according to its Service Level Agreements (SLAs). Availability ensures that the system will not deny service to its authorized users.
The three aspects of confidentiality, integrity, and availability, often called the CIA triad form the corner stones of building an information security architecture for your system.
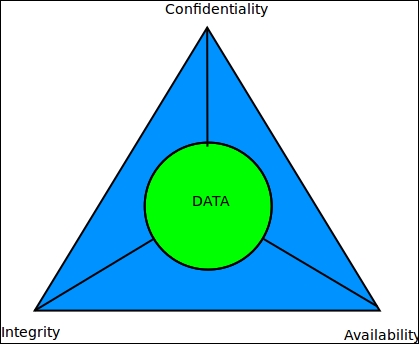
CIA triad of information security architecture
These aspects are aided by other characteristics, such as the following:
- Authentication: This verifies the identity of the participants of a transaction, and ensures that they are actually those who they purport to be. Examples are digital certificates used in e-mail, public keys used to log in to systems, and the like.
- Authorization: This gives rights to a specific user/role to perform a specific task or groups of related tasks. Authorization ensures that certain groups of users are tied to certain roles, which limit their access and modification rights in the system.
- Non-reputability: This refers to security techniques that guarantee that users involved in a transaction cannot later deny that the transaction happened. For example, a sender of an e-mail cannot later deny that they had sent the e-mail; a recipient of a bank funds transfer cannot later deny that they received the money, and so on.
