A COMPUTER FORENSICS CRIME SCENE INVESTIGATION should begin with a plan to approach and secure the crime scene. As a forensic specialist, you must identify and collect evidence or potential evidence, and you must process and analyze the evidence so that it has value in court. Forensic specialists must carefully document crime scene activity and all activity related to evidence.
Computer evidence frequently faces challenges in court. Most challenges are related to the evidence's authenticity. The courts want to know whether the data was altered. They also question whether the program that generated the output was reliable. Other challenges in court can involve the forensic analyst. Attorneys sometimes challenge the expertise, methods, or integrity of computer forensics experts who testify.
Whether an investigation is of a corporate, civil, or criminal nature, the approach and processes are similar. Documentation and professionalism are essential in conducting an investigation that will hold up in court. This chapter deals with controlling a computer forensics investigation. It also provides a discussion of the legal aspects of acquiring evidence.
As a system forensics investigator, you may be the first responder to a scene. You must be concerned about destructive processes and devices that the computer's owner may have planted. You must also know how to deal with evidence preservation and collection on mobile devices and monstrous hard drives.
Note
Multiple types of computing devices, bigger hard drives, and increased use of encryption make the job of a digital forensics examiner tougher than ever.
In addition, think about the computer's operating system and applications. You can easily find evidence in typical storage areas, such as spreadsheets, databases, and word processing files. Unfortunately, potential evidence can also reside in file slack, erased files, and the swap file (you'll read more about swap files later in this chapter). This evidence is usually in the form of data fragments. Simply booting the computer or running Microsoft Windows can overwrite it. When Windows starts, it generally creates new files and opens existing ones. These processes can cause erased files to be overwritten and can alter or destroy data previously stored in the swap file. Furthermore, Windows XP, Vista, and 7 have a habit of updating directory entries for files as a normal operating process. File dates are important from an evidence standpoint.
Be careful about running any programs on a subject computer. Criminals can easily modify a computer's operating system to destroy evidence when standard operating system commands are executed. For example, a perpetrator could modify the operating system in such a way that the execution of the DIR command destroys simulated evidence. Or a crafty high-tech criminal could alter standard program names and familiar Windows program icons and tie them to destructive processes.
Even trusted word processing programs, such as Microsoft Word and WordPerfect, can create problems for a forensic investigator. When word-processing files are opened and viewed, the word-processing program creates temporary files. These files overwrite the temporary files that existed previously, and potential evidence stored in those files can be lost forever.
Computer evidence processing is fraught with potential problems. Any loss of crucial evidence or exculpatory material falls on the shoulders of the computer investigator. You can eliminate many of the problems by using tried and proven processing procedures.
Preservation of evidence is the primary element of all criminal investigations, and computer evidence is certainly no exception. You must first secure the subject computer.
You must then make a complete bit stream backup of all computer data before reviewing or processing it. As stated previously, evidence can reside at multiple levels, such as allocated files, file slack, and erased files. It is not enough to do a standard backup of a hard disk drive. Doing so would eliminate the backup of file slack and erased file space. Without backing up evidence in these unique areas, you could damage or destroy evidence.
Bit stream backups are much more thorough than standard backups. They involve the copying of every bit of data on a storage device. The importance of bit stream backups cannot be stressed enough. After you make a backup, you should also create an additional copy of this backup. Then, you should perform any processing on one of the backup copies. As previously recommended, preserve the original evidence at all costs. After all, it is the best evidence.
An investigator must attempt to avoid permanently losing data. Therefore carefully secure the physical evidence. Then you can collect volatile and temporary data. Volatile data is memory that is highly sensitive to system usage, such as registers, memory, and cache. Such data is lost whenever a system is used. It should be collected first to minimize corruption or loss. The following are examples of volatile data:
Central processing unit (CPU) cache and register contents—This data has no forensic value.
Random access memory (RAM) memory dump—This data is important to get, but accessing it changes the contents.
State of network connections—This data is important and easy to get from tables in kernel memory.
State of running processes—This data is important and is in kernel memory.
After collecting volatile data, you collect temporary data—data that an operating system creates and overwrites without the computer user taking a direct action to save this data. The likelihood of corrupting temporary data is less than that of volatile data. But temporary data is just that—temporary—and you must collect it before it is lost. Only after collecting volatile and temporary data should you begin to collect persistent data.
The following sections look at these important principles of computer forensics evidence handling and collection.
When seizing computer equipment, before turning off a suspect computer, take the following measures to secure the physical evidence:
Photograph the system setup, wiring, and area.
Tag and bag all cables, cords, and peripheral devices.
Write-protect all storage media.
When transporting, make sure to be grounded and place everything in antistatic bags.
Avoid exposing the items to any heat above 75 degrees and avoid letting any magnetic fields, such as police radios, come near the equipment. Gentle handling is important.
Record the names of individuals who occupy or have access to the area.
Volatile data consists of running processes on a live computer. A computer's system state changes constantly, even if no applications are running. For example, power cycles, timed backups, and logon processes are always running in the background. If a computer is hooked up to a network, more processes are running. Some types of Internet attacks require that the computer be left on for long periods of time.
Tip
If an attack is in progress, don't shut down the computer right away.
Table 6-1. Live analysis school of thought recommendations.
DESCRIPTION | PROGRAM | RESULT |
|---|---|---|
Establish a new shell |
|
|
Record system date/time |
|
|
Determine logon |
|
|
Record open sockets |
|
|
List socket processes |
|
|
List running processes |
|
|
List systems connected |
|
|
Record system time |
|
|
Record steps taken |
|
|
Table 6-2. Safe shutdown school of thought recommendations.
PROCEDURE | |
|---|---|
MS-DOS |
|
UNIX |
|
Mac |
|
Windows |
|
There are two schools of thought on how to handle volatile data in forensic investigations: the live analysis school and the safe shutdown school.
The live analysis school of thought, as its name suggests, recommends leaving a suspect computer turned on and working on it immediately after securing it. This school recommends attaching a Small Computer System Interface (SCSI) device or using an open network connection to get results for the commands shown in Table 6-1.
The safe shutdown school of thought believes that a suspect computer should be carefully shut down immediately after the computer is secured. This school recommends the shutdown procedures shown in Table 6-2.
Large hard drives are becoming less expensive and more popular. Therefore, a forensic investigator must recognize the trade-off between spending resources and duplicating everything. An investigator must consider the suspect's intelligence and how high profile or harmful the incident is. In addition, the investigator should decide whether a low-impact search of the hard drive might suffice instead of a high-impact search that looks for file slack and the like. For example, a sample of evidence might suffice with minor offenders. On the other hand, the jurisdiction, judge, or the other side may demand a printout of everything. If a business or institution is going to handle a case administratively instead of criminally, printing all this evidence is unnecessary.
According to Joseph Sremack, a forensic analyst should perform an investigation quickly to return the affected system to its regular job. The presumption is that quicker data collection results in a quicker investigation. However, this call for speed can result in the collection of insufficient evidence, which is the worst-case scenario for an investigation. If evidence is insufficient, you must once again perform the time-consuming process of data collection. Even worse, the needed data may be volatile and may have been lost during the first attempt at data collection.
The primary goal of most investigations is thoroughness. The main purpose of an investigation is to arrive at a complete understanding of the causes and effects of an incident. Carefully perform the data collection so as not to overlook data that could potentially be useful—even if the data does not directly relate to any of the clues collected from the preparation phase.
The standard method to ensure that you have collected every piece of potentially useful data is to gather all volatile data, logs, and other system-specific information that may not be gatherable at a later time. Collecting this information allows you to begin the investigation without the possibility of losing potentially useful information.
The following are some of the possible approaches to take in duplicating a suspect computer:
Remove the hard drive and attach it to a forensic workstation.
Attach a hard drive to the specimen computer and use it as an imaging system.
Use another computer in the office area as an imaging system.
Use a crossover cable or an Ethernet connector to send the contents to another network computer or the hooked-up forensic workstation.
The best approach depends on the resources available and whether your equipment is compatible with the specimen's network system.
As mentioned earlier in this chapter, make a bit stream backup of all computer data. Then review and process the backup rather than the original disk drive or other media. To create a bit stream backup, you can use programs such as EnCase, SafeBack, Code Blue, Norton Ghost, and the UNIX dd (data dumper) utility.
A bit stream backup is a recording of every bit of data that signals a storage device. It is the electronic version of the radio frequency (RF) stream that a radio receiver picks up. A bit stream backup copies not only working files that a conventional backup utility finds but also hidden, erased, fragmented, corrupted, temporary, and special attribute files. These files are not easily hidden on floppies, but a hard drive is full of them. A temporary file, in particular, contains data from a document that someone worked on but never saved to disk.
SafeBack and EnCase are two widely used tools for making bit stream backups:
SafeBack—The world's first cybercop, Chuck Guzis, created SafeBack. This tool duplicates anything attached to the controllers on a computer motherboard. It can even handle removable devices, if the appropriate drivers are installed. Built-in utilities can scan ports for other devices. Put the Remote.exe imaging program on a boot compact disk (CD) to boot the specimen computer and use a crossover parallel cable to connect to the forensic workstation. You can then use the Backup, Restore, Verify (checksum), and Copy commands. SafeBack makes its own audit file. To save space, it saves everything it images in a compressed format on the forensic workstation. The process takes anywhere from a few minutes to many hours. For more information on SafeBack, see
http://www.forensics-intl.com/safeback.html.EnCase—EnCase technically produces accurate duplicate files. EnCase uses a Windows interface and focuses on hard drive contents. You add the specimen hard drive to a forensic workstation as hard disk drive 1 or 2. EnCase, a Windows Explorer-like program, does the rest, with Preview, Save, and Output functions. It displays graphics files in thumbnail format. You can even do string searches for text in Preview mode. Imaged files can be compressed or not, but anything saved is in a proprietary, read-only format, so it is tamper-proof. You can control the size of the evidence files, so that they write to CD-ROM for presentation in court, along with any comments and password protection added. For more information on EnCase, see
http://www.guidancesoftware.com.
After making a backup copy, validate that it is an exact mirror copy. Programs such as CrCheck.exe and CRC32 are available to do this. But large storage devices require a mathematical algorithm, such as the "fingerprint checker" Message Digest 5 (MD5), to estimate the probabilities of match and error. All these programs use a checksum or hashing algorithm that holds up in court as verifying an accurate and reliable copy.
The more numerous the files, the more you must make mathematical computations. And the more read errors you get, the more you need a program that uses conventional-style placeholders. Probability theory plays a vital part in the admissibility of most modern forms of evidence, such as DNA, forensic psychology, social science, and computer forensics.
In computer forensics, booting a computer requires special care. A boot process is one that starts an operating system when the user turns on a computer system. Never boot from an evidence drive; instead boot from a DOS startup CD. In addition, get in the habit of bypassing the operating system and going straight to the basic input/output system (BIOS)—by holding down Shift, Ctrl+F1, or Delete, depending on the chipset. Whenever you run Windows, it changes the swap file, bookmarks, histories, and cache. These areas, particularly the swap file, hold valuable data remnants, such as passwords, graphics, and sometimes whole documents. Whenever a BIOS runs, the boot block on the hard drive may change, including file-access timestamps, partition information, registry or configuration files, and essential log files.
Record information that appears on opening screens. These screens should display autoexec devices, config.sys programs, directories, and file allocation table (FAT) and data storage areas. At some point, also document the results of running a program such as SCANDISKor CHKDISK. Document errors and, if appropriate, correct or repair them. The specialist must document any such corrective actions.
To make a system CD, insert a blank CD. Then, at the C: prompt, type format a: /s to write the system files, and only the system files, to the CD. Table 6-3 lists the system files.
After booting up a suspect system, do the following:
Verify the time and data stamp—Verify the time and data stamp stored in the CMOS chip of the specimen computer. This information helps determine the times and dates of other computer files. Many clock settings that record the file date are inaccurate, but the CMOS stamp helps with estimation and might make the all-important connection with ownership and the start of operation. Computers don't commit computer crimes; people do. You must pay attention to dates, times, and alibis.
Visually inspect the hard drives—Visually inspect and document the make, model, and size of all hard drives. The manufacturing specifications tell what the capabilities are and might even provide the best diagnostic utilities for use with a hard drive that is difficult to read.
Table 6-3. System files.
Scan for viruses—Before running any type of diagnostic program or software, ensure that you have not inadvertently introduced any computer virus into the specimen computer. Therefore, document all forensic software as being regularly and recently scanned by a virus utility—and preferably two of them. You can virus-scan the specimen computer and any CDs and, if appropriate, remove any viruses found. Take into account that viruses can hide in compressed files.
List and catalog files—List and catalog all files with their dates and times of creation, update, and last access. Investigative leads come out of cross-referencing these dates and times with other files on the same computer or files on a different computer.
Document forensic tools—Document the forensic tools you have used, along with their purchase. You must also register software with the publisher, and document any upgrade or update history.
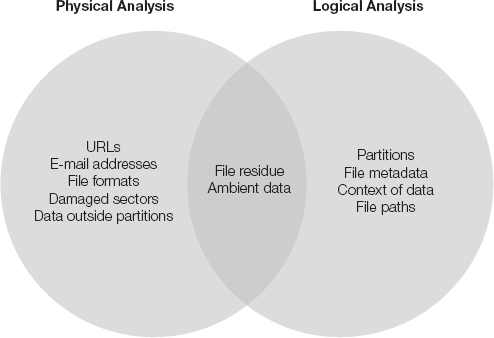
This chapter has so far discussed general preparations involved in the initial seizing, duplication, and finding of digital evidence. There's much more to learn, especially about examining data to find incriminating evidence—evidence that shows, or tends to show, a person's involvement in an act, or evidence that can establish guilt. One of the three techniques of forensic analysis has been covered already—live analysis, which is the recording of any ongoing network processes. The remaining two techniques are physical analysis and logical analysis, which both deal with hard drive structures and file formats.
Physical analysis is offline analysis conducted on an evidence disk or forensic duplicate after booting from a CD or another system. Logical analysis involves using the native operating system, on the evidence disk or a forensic duplicate, to peruse the data. Put another way, physical analysis is looking for things that may have been overlooked, or are invisible, to the user. Logical analysis is looking for things that are visible, known about, and possibly controlled by the user. There is some overlap, as Figure 6-1 indicates.
Two of the easiest things to extract during physical analysis are a list of all Web site URLs and a list of all e-mail addresses on the computer. The user may have attempted to delete these, but you can reconstruct them from various places on the hard drive.
Next, you should index the different kinds of file formats. The file format you start with depends on the type of case. For example, you might want to start with graphics file formats or document formats in a pornography or forgery case. There are lots of other file formats: multimedia, archive, binary, database, font, game, and Internet related. Computers generally save things in file formats beyond the user's control. For example, all graphics files have header information attached. Collectors of pornography usually don't go to the trouble of removing this header information, so it's an easy matter of finding, say, one graphics' header at the beginning of a JPEG file and doing a string search for all other graphics of that type. (This chapter discusses examination of sectors and partitions in the section "Logical Analysis.")
Note
File residue is a broad term for a number of types of data, such as ambient data, file slack, free space, and shadow data. The term ambient data describes data stored in nontraditional computer storage areas and formats. Computer experts often use it to describe data stored in the swap file, unallocated (free) space, or file slack.
The following sections describe some of the places that an investigator must physically analyze.
A swap file is the most important type of ambient data. Windows uses a swap file on each system as a "scratch pad" to write data when additional random access memory (RAM) is needed. A swap file is a virtual memory extension of RAM.
Most computer users are unaware of the existence of swap files. The size of these files can range from 40MB to more than 400MB. Swap files contain remnants of word processing, e-mail, Internet browsing activity, database entries, and almost any other work that has occurred during past Windows sessions. Swap files can be temporary or permanent, depending on the version of Windows installed and the settings selected by the computer user. Permanent swap files are of the greatest forensic value because they hold larger amounts of information for longer periods of time. However, temporary, or dynamic, swap files are more common. These files shrink and expand as necessary. When a dynamic swap file reduces its size close to zero, it sometimes releases the file's content to unallocated space, which you can also forensically examine.
Note
In Windows NT and Windows Server 2003, swap files are called page files.
Unallocated space, or free space, is the area of a hard drive that has never been allocated for file storage, or the leftover area that the computer regards as unallocated after file deletion. It's where the hard disk often sends fragments of files when someone deletes or removes files.
The only way to clean unallocated space is with cleansing devices known as sweepers or scrubbers. However, few commercial products scrub free space to Department of Defense (DoD) standards. The fragments of old files in free space can be anywhere on the disk, even on a different partition, but they tend to fall next to partition headers, file allocation tables (FAT), and the last sectors of a cluster. FAT, clusters, and sectors are defined as follows:
A file allocation table (FAT) stores associations between files and the clusters assigned to them.
Clusters are fixed-length blocks of data—one to 128 sectors—in which DOS- and Windows-based computers store files. Clusters are made up of blocks of sectors.
Sectors are the smallest unit of storage on a computer. They are composed of bits and are generally a power of two bytes in size. A "regular" disk sector is 512 bytes.
Unallocated space often contains intact files, remnants of files and subdirectories, and temporary files that were transparently created and deleted by computer applications or the operating system. Furthermore, unallocated space contains information resulting from trying to save something to a CD that is too large for it, recently sending something to a printer, trying to repartition or reformat a hard drive, or having a system crash while working on a file.
File slack is the empty space attached to every file. All DOS and Windows programs store files in fixed-length blocks called clusters. Rarely do file sizes exactly match the size of these clusters perfectly. The extra space from the end of the file to the end of the cluster is called file slack.
Cluster sizes vary in length, depending on the operating system and the size of the logical partition. Larger cluster sizes have more forensic value. With normal 512-byte sectors, if there is not enough data in the file to fill the last sector in the cluster, DOS or Windows makes up the difference by padding the remaining space with data from the memory buffers. This means that the file slack is filled with RAM slack that potentially contains information from previous work sessions. If the computer has been left on for several days, the file slack areas contain a tremendous amount of information. RAM slack technically refers to the last sector of a file. If the operating system needs additional sectors to round out the block size for the last cluster, then it creates a different type of slack. Drive slack, unlike RAM slack, which comes from memory, is padded with what was stored on the storage device, not just from previous work sessions.
Swap files, unallocated space, and file slack contain mostly binary information, which is tedious to look at. File slack, in particular, is random in nature, and you might find a logon name or password or might find just fragments of messages and documents. Analysis can be time-consuming. On large hard disk drives, file slack can involve gigabytes of data. File slack also can be found on CDs and other storage media.
Shadow data is fringe data that remains on the physical track of storage media after deletion, sweeping, or scrubbing. Regardless of the storage medium—CD, hard disk, tape, and so on—a mechanical device called a head is used to write the data. The data is stored electronically in magnetic patterns of 1s and 0s. These patterns are in the form of sectors, which are written consecutively in concentric rings called tracks. However, head alignment is just a little bit different each time an attempt is made to erase data, and data remnants sometimes bleed over the tracks. Recovering shadow data is not an easy task. You need specialized equipment to retrieve it. There is no guarantee that one scrubbing will have completely eliminated shadow data. Therefore, government agencies require multiple scrubs or burning for media that have held sensitive or classified data.
You must examine the logical file and directory structure to reconstruct what the user was doing with his or her computer. Rarely does an investigator run across a signed confession in the My Documents folder. Most perpetrators are smarter than that.
They use various tactics to hide what they've been doing. For example, perpetrators often use unusual file paths. In addition, many try to thwart investigators by using encryption such as Pretty Good Privacy (PGP). They may also use steganography to hide data in graphics or other files. Or they may use metadata to combine different file formats into one format. You can also expect to find lots of deleted, professionally scrubbed, data.
An investigator hopes to trace the uses that a suspect computer has been set up for. Certain types of criminals optimize their system for different uses. For example, a programmer optimizes for speed, a pornographer for storage, and a stalker for messaging. You must go about logical analysis methodically. Divide the data on the hard drive into layers and try to find evidentiary information at each layer. Look for peculiarities on each layer and then choose the right extraction tool. Table 6-4 shows the location of evidence at each layer.
Table 6-4. Logical analysis layers of evidence.
APPLICATION STORAGE | WINDOWS FILES | UNIX FILES |
|---|---|---|
Physical | Absolute sectors | Absolute sectors |
Data Classification | Partition | Partitions |
Blocking Format | Clusters | Blocks |
Storage Space Allocation | FAT | Inode and data bitmaps |
Information Classification | Directories and folders | Directories |
Proceed through the logical analysis layers of evidence as follows:
Physical layer—Starting at the Physical layer, look for how the hard drive is set up to read and write in blocks and sectors. Intel chips allow the user to adjust the cylinder/head/sector (C/H/S) settings through the BIOS. Anything different from the standard default 512-byte absolute sector size means that the machine is set up to buffer large amounts of data to and from the hard drive. Certain types of hackers do this.
Data Classification layer—At the Data Classification layer, look at the partition tables. Using partition is a way of splitting up the hard drive into separate areas, usually for different operating systems. Windows assigns separate drive letters and tables to FAT and NTFS (NT File System) partitions. UNIX, on the other hand, uses hybrid tables that represent all partitions. This is because UNIX is more flexible and integrates with other operating systems. Evidence could easily be hidden in the UNIX tables.
Blocking Format layer—The Blocking Format layer contains customizations that only the system administrator in UNIX and administrator in Windows can make. More sophisticated users may optimize their block sizes for the size of their disk or partition. They do so because the machine doesn't have to search thousands of allocation units each time a file is written or updated. Other users want to have lots of allocation units per block. These people have lots of wasted space and slack to examine.
Storage Space Allocation layer—The Storage Space Allocation layer is the FAT system, where the allocation tables are located. Each partition has at last two FATS, located at the starting sector of each partition. Sometimes you can find hundreds of allocation tables spread throughout the drive, especially in UNIX. Computer systems automatically run validity checks on these tables all the time, but many of them are corrupted. You can rebuild these tables to their original state by using simple recovery tools. In this way, you may be able to re-create what the computer looked like in the past.
Information Classification and Application Storage layers—The Information Classification and Application Storage layers contain both active and deleted files. Every file system has a method for chaining together lists of files. Sometimes, the more unlinked the file, the more important it is. File date and timestamps are the most valuable pieces of information in reconstructing who accessed what, when, and where.
In the case of federal investigations, after a court has issued a search warrant, specially trained analysts typically perform forensic analysis at government laboratories. Weeks or months may pass before system forensics investigators have collected all the evidence. In most cases, investigators seize the computer and associated hardware, and then they look through the computer files at a police station or a laboratory. State and local investigations may vary from this approach. They're likely to involve less seizure of equipment and instead involve a copy-and-scan approach. These investigations generally involve analysis at the police station. In civil cases, the litigants typically hire private companies to perform forensic analysis.
Tip
Some states require that forensic professionals be licensed as private investigators. These requirements vary by state. As more states move toward requiring licensing for forensic investigators, it's a good idea to keep informed of your state's requirements.
An important consideration in computer forensics is the Fourth Amendment to the U.S. Constitution. This amendment guards against unreasonable searches and seizures. The amendment specifically requires that search and arrest warrants be judicially sanctioned and supported by probable cause. A number of issues in system forensics raise questions about Fourth Amendment rules:
In computer seizure, when exactly does the search occur? The Fourth Amendment was set up to address physically entering a home. With digital forensics, computers are not exactly "entered" or physically "observed." Nothing is physically moved inside them, and they basically contain 1s and 0s. The notion of seizure is tied to the concepts of physicality and invasiveness. Digital information becomes physical when it can be readily observed by ordinary human perception.
Who actually owns a suspect computer and the data it contains? Computers in the home typically involve a complex status of ownership and possession. A home computer may very well be the "family" computer, with several users. An employer typically owns work data and equipment and has authority to search corporate data systems.
If forensic investigators work with images and do their analysis in labs, how does the Fourth Amendment apply? A computer forensics analyst usually works from a bit stream copy of the hard drive. So it's not the actual computer that the analyst is searching but a copy of the actual. In addition, the search may occur on government property, not private property. Under current Fourth Amendment interpretation, copying something does not constitute seizing it.
Does a user's attempt to delete things constitute an attempt at privacy or an attempt at cover-up? When is a forensic expert allowed to attempt recovery of "deleted" files? Hidden files, files with renamed extensions, and encrypted files generally trigger extra law enforcement effort.
Where does one computer search end and another begin? Due to the vast amount of information computers hold, it is increasingly difficult to determine this. Law enforcement analysts cannot go on a "fishing expedition." For example, if they are looking for evidence of drug sales but find an image of child pornography, they can't abandon the original search and begin looking for more evidence of child pornography. Plain view doctrine, on the other hand, allows police to follow up on things when the incriminating nature of the evidence discovered is immediately apparent.
Note
Individuals may lose their right to privacy when they transfer data to a third party. The right to privacy does not extend to searches that are conducted by private parties who are not acting for the government. For example, if a person takes a computer to a repair shop and the technician notices child pornography on the computer, the repair shop must notify the authorities.
For evidence to be admissible in court, you should follow at least one of these three criminal evidence rules:
Authentication appears to be the most commonly used of these rules. However, experts disagree about which is the most essential, or most correct, element of this in practice. Some say it's documentation of what has been done. Others say preservation—or integrity of the original. Still others say authenticity—that is, the evidence is what the investigator says it is. Good arguments could be made for the centrality of each, or all, as the standard in computer forensics law. The following sections provide further discussion.
If your documentation is poor, it will look as if your processing procedures were poor. Without a good written record, your testimony in court will look ridiculous.
Problems in the documentation area arise when an investigator tries to take shortcuts or doesn't have adequate time, equipment, and resources. In general, the condition of all evidence must be documented. For example, it has to be photographed, weighed, and sketched. Then a laboratory worker should figure out which tests are appropriate, decide on which part of the evidence to examine first, dissect or copy the part to be tested, and prepare the testing ground. In addition, the worker must document each of these steps. Only then does any testing begin—and that's heavily documented with bench notes, which are subject to discovery and review by experts from the other side.
Collecting and transporting evidence gives rise to numerous possibilities for error in the form of destruction, mishandling, and contamination. Problems in the preservation area have implications for the integrity of law enforcement and crime labs. The basic chain of custody, for example, involves at least three initial potential sources of error:
Evidence has to be discovered.
It has to be collected.
It has to be packaged, labeled, and transported to the lab.
When evidence gets to the lab, it has to be logged in. For each piece of evidence, someone must assign an identification number, place it in storage, and keep it from intermingling with other evidence. All workplaces must be clean and contamination free. Some workplaces are required to meet the standards of professional accrediting organizations. Written policies must be in place. The quality assurance policy, for example, must act as a check on quality control.
If your authenticity is poor, then you, your agency, and the prosecutor will look like inexperienced rookies. Computer evidence, like computer simulations, hasn't fared well under the more rigorous standards of admissibility for scientific evidence. Case law varies by jurisdiction. The following are some of the relevant scientific evidence standards:
Relevancy test (Federal Rules of Evidence 401, 402, 403)—The relevancy test is embodied in the Federal Rules of Evidence and some state rules of evidence. These rules liberally allow anything that materially assists the trier of fact to be deemed relevant by the trier of law.
Frye standard (Frye v. U.S., 1923)—For the results of a scientific technique to be admissible, the technique must be sufficiently established to have gained general acceptance in its particular field. This is referred to as a general acceptance test.
Coppolino standard (Coppolino v. State, 1968)—Even if the profession as a whole isn't familiar with a new test or new science on a particular problem, the court allows it if an adequate foundation can be laid.
Marx standard (People v. Marx, 1975)—The court is satisfied if it does not have to sacrifice its common sense in understanding and evaluating the scientific expertise put before it. This is a common sense or no scientific jargon test.
Daubert standard (Daubert v. Merrell Dow, 1993)—This rigorous test requires special pretrial hearings for scientific evidence and special discovery procedures. The rules on validity, reliability, benchmarking, algorithms, and error rates are laid out beforehand.
The federal courts were the first to recognize that files on computers are similar to and dissimilar to files kept on paper. In recent years, the best evidence rule has also seen the growth of a standard known as representational accuracy, which means it's not necessary to present all the originals. Therefore, a modern clause in the Federal Rules of Evidence (FRE 1001-3) states, "If data are stored by computer or similar device, any printout or other output readable by sight, shown to reflect the data accurately, is an original." This exception to the best evidence rule has found a mostly welcome reception in state courts.
Many argue that it's more appropriate to consider digital evidence as demonstrative rather than documentary. The history of computers in the courtroom ties in with demonstrative standards, and computer forensics, after all, is about reconstructing the crime, or criminalistics. Computer forensics specialists and technicians work from a copy, duplicate, mirror, replica, or exemplar of the original evidence. Digital evidence is easily lost; there's nothing else in criminal justice more easily damaged, corrupted, or erased.
Perhaps one of the most crucial points of a case lies hidden in a computer. The digital evidence collection process allows you to not only locate that key evidence but also maintain the integrity and reliability of that evidence. Timing during this digital evidence collection process is of the essence. Any delay or continuous use of the suspect computer may overwrite data before a forensic specialist can analyze it, resulting in destruction of critical evidence.
The following are some helpful tips for preserving data for future computer forensics examination:
Do not turn on or attempt to examine the suspect computer. Doing so could result in destruction of evidence.
Identify all devices that may contain evidence, including the following:
Workstation computers
Offsite computers, such as laptops, home computers, senders and recipients of e-mail, and personal digital assistants (PDAs)
Removable storage devices, such as external hard drives, flash drives, and CDs
Network storage devices, such as servers, tapes, storage area networks (SANs), and network-attached storage (NAS)
Quarantine all in-house computers, following these protocols:
Do not permit anyone to use the computers.
Secure all removable media.
Turn off the computers.
Disconnect the computers from the network.
Consider the need for court orders to preserve and secure the digital evidence on third-party computers and storage media.
Forensically image all suspect media.
Protecting an organization from outside threats is clearly important. Protecting an organization from internal threats is also important. Corporations and government agencies now provide Internet access to their employees. Providing this access opens a Pandora's box. Workers can easily spend countless hours online every day, entertaining themselves at their employer's expense. In addition, employee use of Internet pornography can create a hostile workplace environment and potentially expose an organization to civil liability.
According to the 2008 Computer Crime and Security Survey conducted by the Computer Security Institute and the Federal Bureau of Investigation (FBI), 72 percent of the respondents reported unauthorized access to information by persons inside the organization, compared with just 47 percent who reported intrusions by outsiders. More than 27 percent reported theft of proprietary information, and 85 percent reported theft of laptop computers. Ninety-seven percent reported virus contamination, and a staggering 99 percent reported systems abuse—pornography, pirated software, inappropriate e-mail usage, and so on—by insiders. According to SexTracker, an organization that tracks the online pornography trade, 87 percent of online pornography viewing occurs during the 9-to-5 workday.
Note
Countless organizations use comprehensive and effective computer forensics policies. These organizations include banks, insurance companies, law firms, local governments, retailers, technology firms, educational institutions, charitable organizations, manufacturers, and distributors.
Detailed policies on the use of computers within an organization are an ever-increasing necessity. Regulations are increasing.
A computer forensics policy manual should address all manner of computer-related policy needs. The content should be based on the corporation's experience in employment-related investigations, computer crime investigations, civil litigation, and criminal prosecutions.
Approximately half of the manual should consist of detailed discussions on each of the policy topic areas. The other half should be sample policies that can be readily customized by parts of an organization. The discussions should include topics such as why policies are needed, potential liability, employee productivity considerations, and civil litigation. The manual should discuss in detail safeguarding critical and confidential information. The policies should directly address the problems that would typically occur in an organization of this size and type.
Computer forensics is a field that demands precision. Every investigation is critical, so a computer forensics specialist must be precise and control every investigation. A computer forensics crime scene investigation starts with a plan to approach and secure the crime scene. You must be able to document crime scene activity, engage in discovery and identification of evidence or potential evidence, collect and retrieve such material, and process or analyze it as evidence. You must understand how to control a computer forensics investigation and understand the legal aspects of acquiring evidence.
Batch file
Bit stream backup
Boot process
Cluster
File allocation table (FAT)
Fourth Amendment to the U.S. Constitution
Imaging
Incriminating evidence
Live analysis school of thought
Logical analysis
Physical analysis
Safe shutdown school of thought
Sector
Shadow data
Temporary data
Volatile data
What type of data is lost whenever a system is used and should therefore be collected first to minimize corruption or loss?
Bit stream data
Forensic data
Temporary data
Volatile data
The _________, as its name suggests, recommends leaving a suspect computer turned on and working on it immediately after securing it.
Why is it important to create a bit stream copy of a disk drive or another type of storage media?
A bit stream copy can be created very quickly.
A bit stream copy exactly replicates all sectors on the storage device, including all files and ambient data storage areas.
The Department of Defense requires bit stream copies in all investigations.
It's not. Standard file backups and network server backups are sufficient in most cases.
You should always work on the suspect hard drive rather than a backup, a duplicate, a copy, or an image.
True
False
In a forensic investigation, speed is more important than thoroughness.
True
False
Which of the following is a batch file that handles drivers for all the devices hooked up to the controllers and ports?
AUTOEXEC.BAT
COMMAND.COM
CONFIG.SYS
DRVSPACE.BI
Which techniques of forensic analysis are discussed in this chapter? (Select three.)
Live analysis
Volatile analysis
Physical analysis
Logical analysis
Which of the following does Windows use on a system as a "scratch pad" to write data when additional RAM is needed?
Batch file
Swap file
File residue
Unallocated space
Which of the following is the smallest unit of storage on a computer?
File allocation table (FAT)
Cluster
Sector
File
_________ is the area of a hard drive that has never been allocated for file storage, or the leftover area that the computer regards as unallocated after file deletion.
One of the first questions that can be asked in computer seizure law is when exactly the search occurs. The _________ Amendment to the U.S. Constitution deals with search and seizure.
Which of the following is not a best practice in preserving data for future computer forensics examination?
Immediately turn on and attempt to examine the suspect computer.
Identify all devices that may contain evidence.
Quarantine all in-house computers.
Forensically image all suspect media.