Chapter 6
Security Assessment and Testing (Domain 6)
- During a port scan, Susan discovers a system running services on TCP and UDP 137–139 and TCP 445, as well as TCP 1433. What type of system is she likely to find if she connects to the machine?
- A Linux email server
- A Windows SQL server
- A Linux file server
- A Windows workstation
- Which of the following is a method used to automatically design new software tests and to ensure the quality of tests?
- Code auditing
- Static code analysis
- Regression testing
- Mutation testing
- During a port scan, Naomi found TCP port 443 open on a system. Which tool is best suited to scanning the service that is most likely running on that port?
- zzuf
- Nikto
- Metasploit
- sqlmap
- What message logging standard is commonly used by network devices, Linux and Unix systems, and many other enterprise devices?
- Syslog
- Netlog
- Eventlog
- Remote Log Protocol (RLP)
- Alex wants to use an automated tool to fill web application forms to test for format string vulnerabilities. What type of tool should he use?
- A black box
- A brute-force tool
- A fuzzer
- A static analysis tool
- Susan needs to scan a system for vulnerabilities, and she wants to use an open source tool to test the system remotely. Which of the following tools will meet her requirements and allow vulnerability scanning?
- Nmap
- OpenVAS
- MBSA
- Nessus
- Morgan is implementing a vulnerability management system that uses standards-based components to score and evaluate the vulnerabilities it finds. Which of the following is most commonly used to provide a severity score for vulnerabilities?
- CCE
- CVSS
- CPE
- OVAL
- Jim has been contracted to perform a penetration test of a bank's primary branch. To make the test as real as possible, he has not been given any information about the bank other than its name and address. What type of penetration test has Jim agreed to perform?
- A crystal-box penetration test
- A gray-box penetration test
- A black-box penetration test
- A white-box penetration test
- In a response to a request for proposal, Susan receives an SSAE 18 SOC report. If she wants a report that includes operating effectiveness detail, what should Susan ask for as follow-up and why?
- A SOC 2 Type II report, because Type I does not cover operating effectiveness
- A SOC 1 Type I report, because SOC 2 does not cover operating effectiveness
- A SOC 2 Type I report, because SOC 2 Type II does not cover operating effectiveness
- A SOC 3 report, because SOC 1 and SOC 2 reports are outdated
- During a wireless network penetration test, Susan runs aircrack-ng against the network using a password file. What might cause her to fail in her password-cracking efforts?
- Using WPA2 encryption
- Running WPA2 in Enterprise mode
- Using WEP encryption
- Running WPA2 in PSK mode
- A zero-day vulnerability is announced for the popular Apache web server in the middle of a workday. In Jacob's role as an information security analyst, he needs to quickly scan his network to determine what servers are vulnerable to the issue. What is Jacob's best route to quickly identify vulnerable systems?
- Immediately run Nessus against all of the servers to identify which systems are vulnerable.
- Review the CVE database to find the vulnerability information and patch information.
- Create a custom IDS or IPS signature.
- Identify affected versions and check systems for that version number using an automated scanner.
- What type of testing is used to ensure that separately developed software modules properly exchange data?
- Fuzzing
- Dynamic testing
- Interface testing
- API checksums
- Selah wants to provide security assessment information to customers who want to use her organization's cloud services. Which of the following options should she select to ensure that the greatest number of customers are satisfied with the assessment information?
- Use an internal audit team to self-assess against internal metrics.
- Use a third-party auditor.
- Use internal technical staff who know the systems.
- Use an internal audit team to self-assess against a common standard like COBIT.
- Yasmine has been asked to consider a breach and attack simulation system. What type of system should she look for?
- A ticket and change management system designed to help manage incidents
- A system that runs incident response simulations for blue teams to test their skills
- A system that combines red and blue team techniques with automation
- A security operations and response (SOAR) system
- Monica wants to gather information about security awareness in her organization. What technique is most frequently used to assess security awareness?
- Phishing simulators
- Gamified applications
- Assessment tests
- Surveys
- Jim has been contracted to conduct a gray-box penetration test, and his clients have provided him with the following information about their networks so that he can scan them:
Data center: 10.10.10.0/24
Sales: 10.10.11.0/24
Billing: 10.10.12.0/24
Wireless: 192.168.0.0/16
What problem will Jim encounter if he is contracted to conduct a scan from off-site?
- The IP ranges are too large to scan efficiently.
- The IP addresses provided cannot be scanned.
- The IP ranges overlap and will cause scanning issues.
- The IP addresses provided are RFC 1918 addresses.
- Mark's company has been notified that there is a flaw in their web application. The anonymous individual has notified them that they have two weeks to fix it before the details of the flaw are published along with example exploit code. What industry norm is the individual who contacted Mark's company violating?
- Zero-day reporting
- Ethical disclosure
- Ethical hacking
- The (ISC)2 vulnerability disclosure ethics statement
For questions 18–20, please refer to the following scenario:
The company that Jennifer works for has implemented a central logging infrastructure, as shown in the following image. Use this diagram and your knowledge of logging systems to answer the following questions.
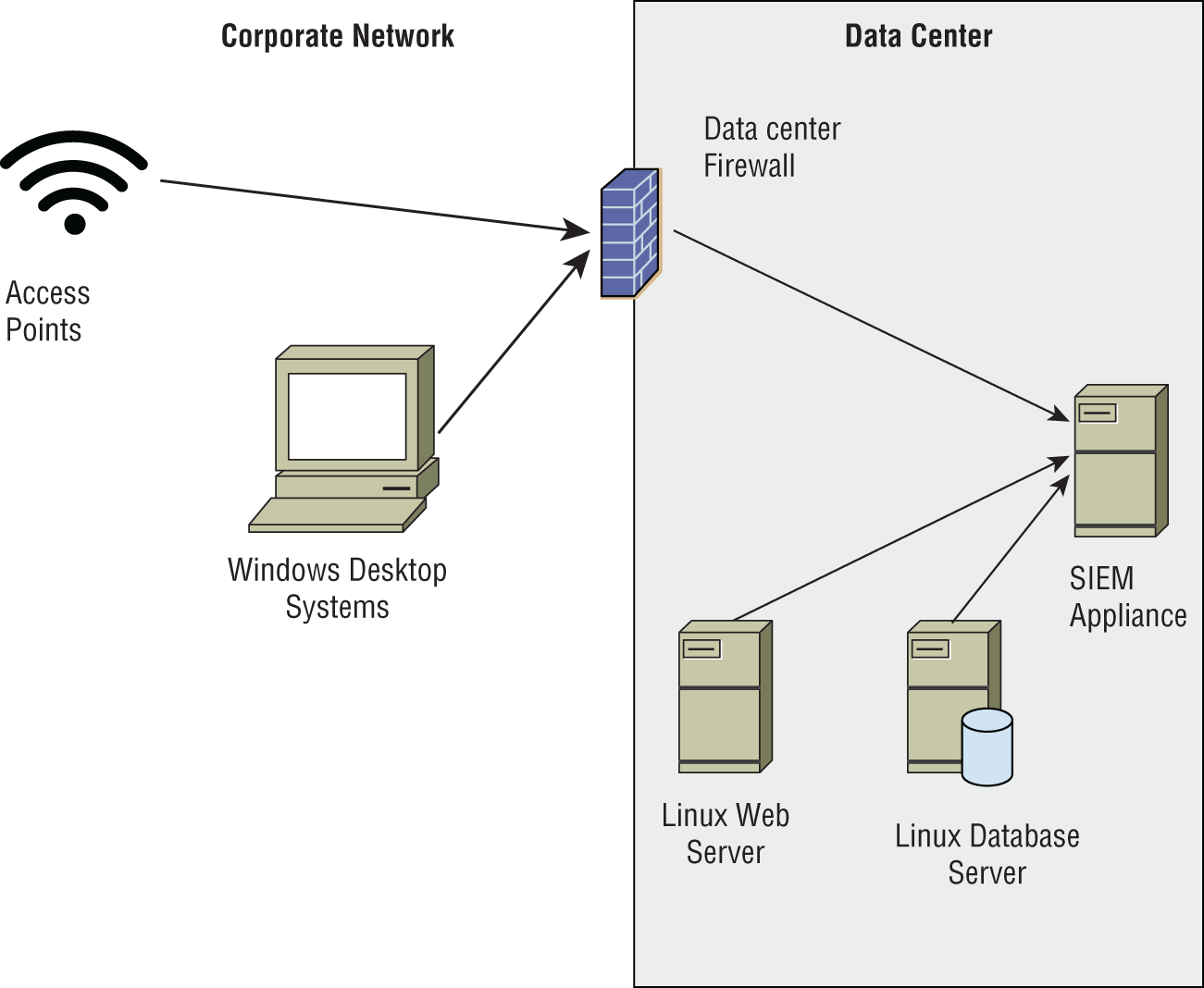
- Jennifer needs to ensure that all Windows systems provide identical logging information to the SIEM. How can she best ensure that all Windows desktops have the same log settings?
- Perform periodic configuration audits.
- Use Group Policy.
- Use Local Policy.
- Deploy a Windows syslog client.
- During normal operations, Jennifer's team uses the SIEM appliance to monitor for exceptions received via syslog. What system shown does not natively have support for syslog events?
- Enterprise wireless access points
- Windows desktop systems
- Linux web servers
- Enterprise firewall devices
- What technology should an organization use for each of the devices shown in the diagram to ensure that logs can be time sequenced across the entire infrastructure?
- Syslog
- NTP
- Logsync
- SNAP
- During a penetration test, Michelle needs to identify systems, but she hasn't gained sufficient access on the system she is using to generate raw packets. What type of scan should she run to verify the most open services?
- A TCP connect scan
- A TCP SYN scan
- A UDP scan
- An ICMP scan
- During a port scan using nmap, Joseph discovers that a system shows two ports open that cause him immediate worry:
21/open
23/open
What services are likely running on those ports?
- SSH and FTP
- FTP and Telnet
- SMTP and Telnet
- POP3 and SMTP
- Aaron wants to validate his compliance with PCI-DSS. His company is a large commercial organization with millions of dollars in transactions a year. What is the most common method of conducting this type of testing for large organizations?
- Self-assessment
- To conduct a thirty-party assessment using COBIT
- To partner with another company and trade assessments between the organizations
- To conduct a third-party assessment using a qualified security assessor
- What method is commonly used to assess how well software testing covered the potential uses of an application?
- A test coverage analysis
- A source code review
- A fuzz analysis
- A code review report
- Testing that is focused on functions that a system should not allow is an example of what type of testing?
- Use case testing
- Manual testing
- Misuse case testing
- Dynamic testing
- What type of monitoring uses simulated traffic to a website to monitor performance?
- Log analysis
- Synthetic monitoring
- Passive monitoring
- Simulated transaction analysis
- Derek wants to ensure that his organization tracks all changes to accounts through their lifecycle. What type of tool should he invest in for his organization?
- A directory service like LDAP
- An IAM system
- An SIEM
- An EDR system
- Jim uses a tool that scans a system for available services and then connects to them to collect banner information to determine what version of the service is running. It then provides a report detailing what it gathers, basing results on service fingerprinting, banner information, and similar details it gathers combined with CVE information. What type of tool is Jim using?
- A port scanner
- A service validator
- A vulnerability scanner
- A patch management tool
- Emily builds a script that sends data to a web application that she is testing. Each time the script runs, it sends a series of transactions with data that fits the expected requirements of the web application to verify that it responds to typical customer behavior. What type of transactions is she using, and what type of test is this?
- Synthetic, passive monitoring
- Synthetic, use case testing
- Actual, dynamic monitoring
- Actual, fuzzing
- What passive monitoring technique records all user interaction with an application or website to ensure quality and performance?
- Client/server testing
- Real user monitoring
- Synthetic user monitoring
- Passive user recording
- Earlier this year, the information security team at Jim's employer identified a vulnerability in the web server that Jim is responsible for maintaining. He immediately applied the patch and is sure that it installed properly, but the vulnerability scanner has continued to incorrectly flag the system as vulnerable. To deal with the issue so that it does not continue to be flagged incorrectly?
- Uninstall and reinstall the patch.
- Ask the information security team to flag the system as patched and not vulnerable to that particular flaw.
- Update the version information in the web server's configuration.
- Review the vulnerability report and use alternate remediation options.
- Angela wants to test a web browser's handling of unexpected data using an automated tool. What tool should she choose?
- Nmap
- zzuf
- Nessus
- Nikto
- STRIDE, which stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege, is useful in what part of application threat modeling?
- Vulnerability assessment
- Misuse case testing
- Threat categorization
- Penetration test planning
- Why should passive scanning be conducted in addition to implementing wireless security technologies like wireless intrusion detection systems?
- It can help identify rogue devices.
- It can test the security of the wireless network via scripted attacks.
- Their short dwell time on each wireless channel can allow them to capture more packets.
- They can help test wireless IDS or IPS systems.
- Paul is reviewing the approval process for a penetration test and wants to ensure that it has appropriate management review. Who should he ensure has approved the request for a penetration test for a business system?
- The change advisory board
- Senior management
- The systems administrator for the system
- The service owner
- What term describes software testing that is intended to uncover new bugs introduced by patches or configuration changes?
- Nonregression testing
- Evolution testing
- Smoke testing
- Regression testing
- Which of the following tools cannot identify a target's operating system for a penetration tester?
- Nmap
- Nessus
- Nikto
- sqlmap
- Susan needs to predict high-risk areas for her organization and wants to use metrics to assess risk trends as they occur. What should she do to handle this?
- Perform yearly risk assessments.
- Hire a penetration testing company to regularly test organizational security.
- Identify and track key risk indicators.
- Monitor logs and events using a SIEM device.
- What major difference separates synthetic and passive monitoring?
- Synthetic monitoring works only after problems have occurred.
- Passive monitoring cannot detect functionality issues.
- Passive monitoring works only after problems have occurred.
- Synthetic monitoring cannot detect functionality issues.
For questions 40–42, please refer to the following scenario. Chris uses the standard penetration testing methodology shown here. Use this methodology and your knowledge of penetration testing to answer questions about tool usage during a penetration test.
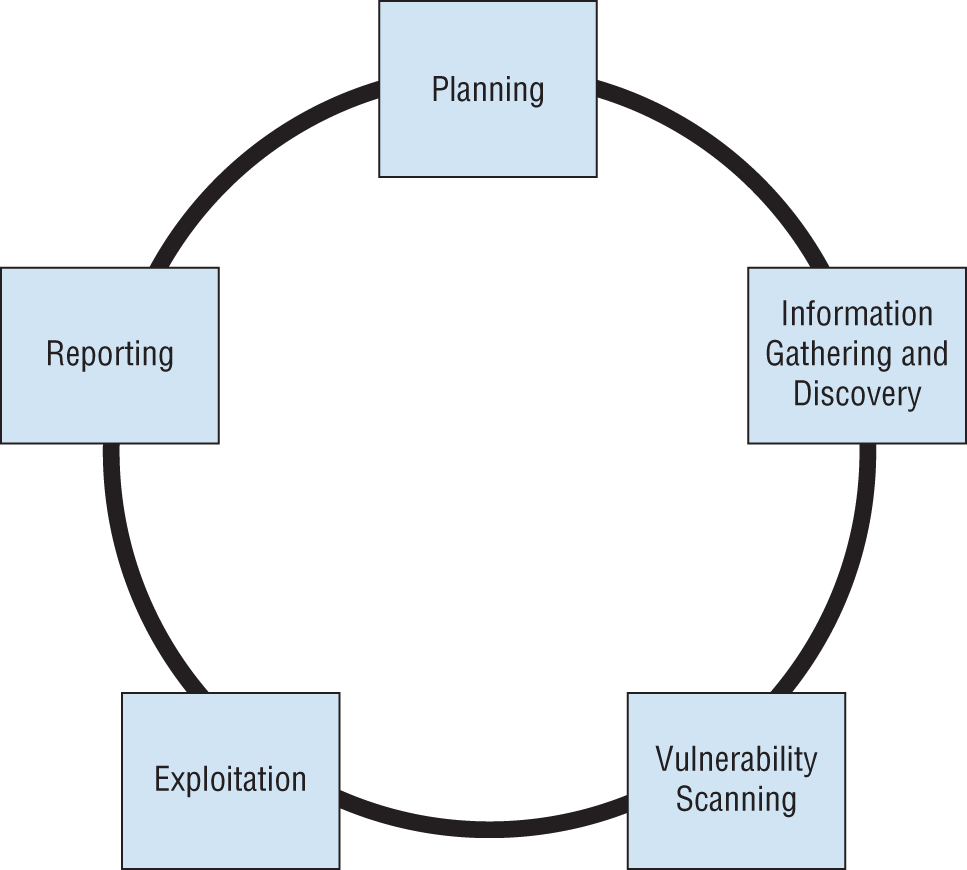
- What task is the most important during Phase 1, Planning?
- Building a test lab
- Getting authorization
- Gathering appropriate tools
- Determining if the test is white, black, or gray box
- Which of the following tools is most likely to be used during discovery?
- Nessus
- john
- Nmap
- Nikto
- Which of these concerns is the most important to address during planning to ensure that the reporting phase does not cause problems?
- Which CVE format to use
- How the vulnerability data will be stored and sent
- Which targets are off-limits
- How long the report should be
- What four types of coverage criteria are commonly used when validating the work of a code testing suite?
- Input, statement, branch, and condition coverage
- Function, statement, branch, and condition coverage
- API, branch, bounds, and condition coverage
- Bounds, branch, loop, and condition coverage
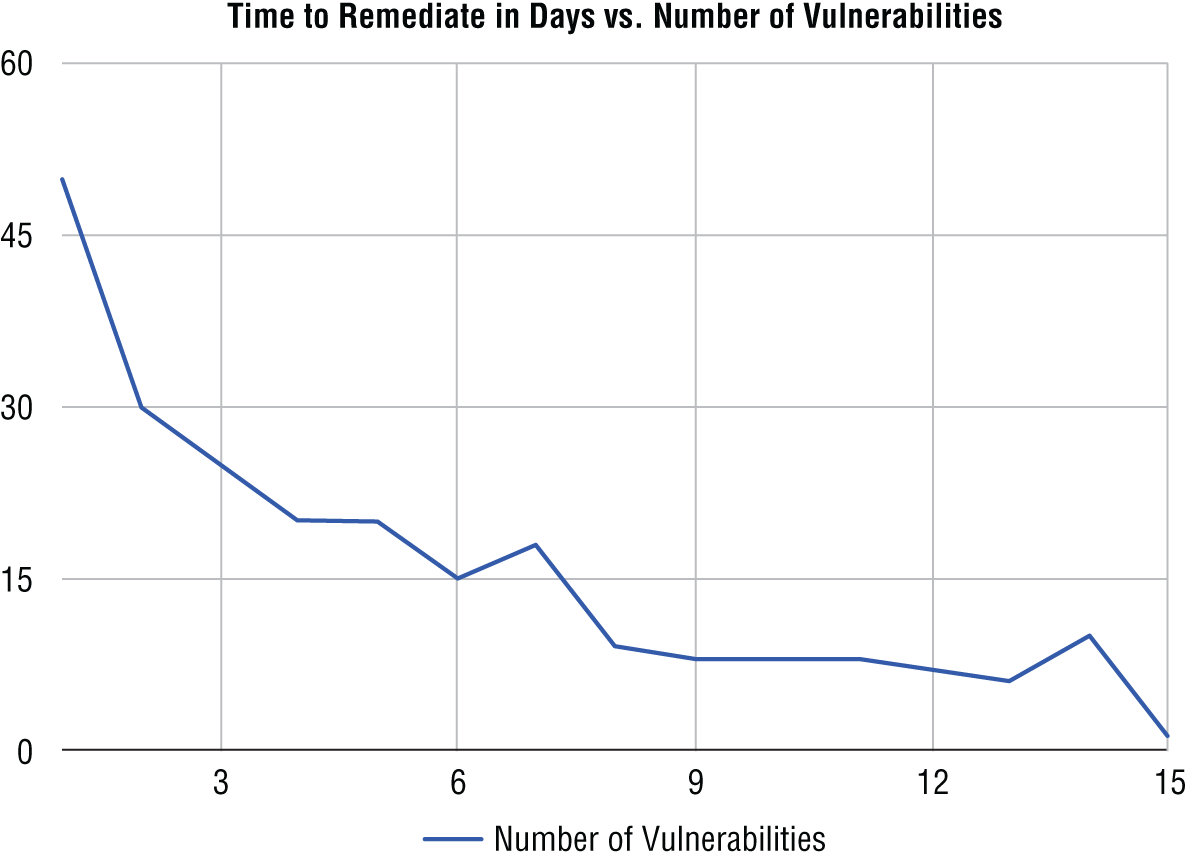
- As part of his role as a security manager, Jacob provides the following chart to his organization's management team. What type of measurement is he providing for them?
- A coverage rate measure
- A key performance indicator
- A time to live metric
- A business criticality indicator
- What does using unique user IDs for all users provide when reviewing logs?
- Confidentiality
- Integrity
- Availability
- Accountability
- Which of the following is not an interface that is typically tested during the software testing process?
- APIs
- Network interfaces
- UIs
- Physical interfaces
- Alan's organization uses the Security Content Automation Protocol (SCAP) to standardize its vulnerability management program. Which component of SCAP can Alan use to reconcile the identity of vulnerabilities generated by different security assessment tools?
- OVAL
- XCCDF
- CVE
- SCE
- Susan is reviewing software testing coverage data and sees the information shown in the following figure. What can she determine about this testing process? (Select all answers that apply.)

- The testing does not have full coverage.
- Test 4 completed with no failures.
- Test 2 failed to run successfully.
- The testing needs to be run a fifth time.
- Which of the following strategies is not a reasonable approach for remediating a vulnerability identified by a vulnerability scanner?
- Install a patch.
- Use a workaround fix.
- Update the banner or version number.
- Use an application layer firewall or IPS to prevent attacks against the identified vulnerability.
- During a penetration test, Selah calls her target's help desk claiming to be the senior assistant to an officer of the company. She requests that the help desk reset the officer's password because of an issue with his laptop while traveling and persuades them to do so. What type of attack has she successfully completed?
- Zero knowledge
- Help desk spoofing
- Social engineering
- Black box
- In this image, what issue may occur due to the log handling settings?
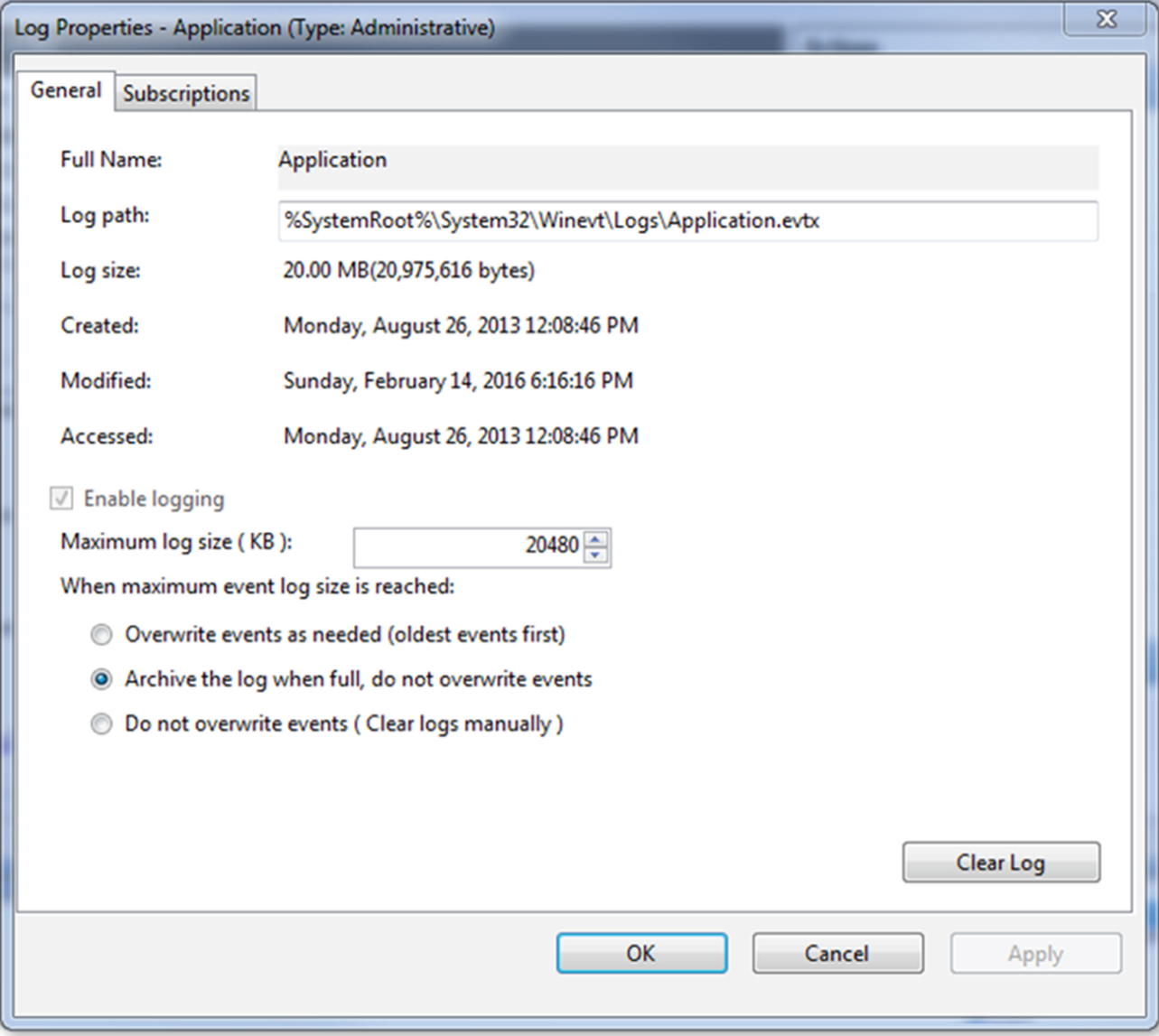
- Log data may be lost when the log is archived.
- Log data may be overwritten.
- Log data may not include needed information.
- Log data may fill the system disk.
- Which of the following is not a hazard associated with penetration testing?
- Application crashes
- Denial of service
- Blackouts
- Data corruption
- Which NIST special publication covers the assessment of security and privacy controls?
- 800-12
- 800-53A
- 800-34
- 800-86
- Michelle is conducting a quantitative business impact assessment and wants to collect data to determine the dollar cost of downtime. What information would she need from outages during the previous year to calculate the cost of those outages to the business? (Select all that apply.)
- The total amount of time the business was down
- The number of personnel hours worked to recover from the outage
- The business lost during the outage per hour in dollars
- The average employee wage per hour
- If Kara's primary concern is preventing eavesdropping attacks, which port should she block?
- 22
- 80
- 443
- 1433
- If Kara's primary concern is preventing administrative connections to the server, which port should she block?
- 22
- 80
- 443
- 1433
- During a third-party audit, Jim's company receives a finding that states, “The administrator should review backup success and failure logs on a daily basis and take action in a timely manner to resolve reported exceptions.” What potential problem does this finding indicate?
- Administrators will not know if the backups succeeded or failed.
- The backups may not be properly logged.
- The backups may not be usable.
- The backup logs may not be properly reviewed.
- Jim is helping his organization decide on audit standards for use throughout their international organization. Which of the following is not an IT standard that Jim's organization is likely to use as part of its audits?
- COBIT
- SSAE-18
- ITIL
- ISO 27001
- Nicole wants to conduct a standards-based audit of her organization. Which of the following is commonly used to describe common requirements for information systems?
- IEC
- COBIT
- FISA
- DMCA
- Kelly's team conducts regression testing on each patch that they release. What key performance measure should they maintain to measure the effectiveness of their testing?
- Time to remediate vulnerabilities
- A measure of the rate of defect recurrence
- A weighted risk trend
- A measure of the specific coverage of their testing
- Which of the following types of code review is not typically performed by a human?
- Software inspections
- Pair programming
- Static program analysis
- Software walk-throughs
For questions 62–64, please refer to the following scenario:
Susan is the lead of a quality assurance team at her company. The team has been tasked with the testing for a major release of their company's core software product.
- Susan's team of software testers are required to test every code path, including those that will only be used when an error condition occurs. What type of testing environment does her team need to ensure complete code coverage?
- White box
- Gray box
- Black box
- Dynamic
- As part of the continued testing of their new application, Susan's quality assurance team has designed a set of test cases for a series of black-box tests. These functional tests are then run, and a report is prepared explaining what has occurred. What type of report is typically generated during this testing to indicate test metrics?
- A test coverage report
- A penetration test report
- A code coverage report
- A line coverage report
- As part of their code coverage testing, Susan's team runs the analysis in a nonproduction environment using logging and tracing tools. Which of the following types of code issues is most likely to be missed during testing due to this change in the operating environment?
- Improper bounds checking
- Input validation
- A race condition
- Pointer manipulation
- Robin recently conducted a vulnerability scan and found a critical vulnerability on a server that handles sensitive information. What should Robin do next?
- Patching
- Reporting
- Remediation
- Validation
- The automated code testing and integration that Andrea ran as part of her organization's CI/CD pipeline errored out. What should Andrea do with the code if the company needs the code to go live immediately?
- Manually bypass the test.
- Review error logs to identify the problem.
- Rerun the test to see if it works.
- Send the code back to the developer for a fix.
- Michelle wants to compare vulnerabilities she has discovered in her data center based on how exploitable they are, if exploit code exists, and how hard they are to remediate. What scoring system should she use to compare vulnerability metrics like these?
- CSV
- NVD
- VSS
- CVSS
- During a port scan of his network, Alex finds that a number of hosts respond on TCP ports 80, 443, 515, and 9100 in offices throughout his organization. What type of devices is Alex likely discovering?
- Web servers
- File servers
- Wireless access points
- Printers
- Nikto, Burp Suite, and Wapiti are all examples of what type of tool?
- Web application vulnerability scanners
- Code review tools
- Vulnerability scanners
- Port scanners
- Frank's team is testing a new API that his company's developers have built for their application infrastructure. Which of the following is not a common API issue that you would expect Frank's team to find?
- Improper encryption
- Object-level authorization issues
- User authentication issues
- Lack of rate limiting
- Jim is working with a penetration testing contractor who proposes using Metasploit as part of her penetration testing effort. What should Jim expect to occur when Metasploit is used?
- Systems will be scanned for vulnerabilities.
- Systems will have known vulnerabilities exploited.
- Services will be probed for buffer overflow and other unknown flaws.
- Systems will be tested for zero-day exploits.
- Susan needs to ensure that the interactions between the components of her e-commerce application are all handled properly. She intends to verify communications, error handling, and session management capabilities throughout her infrastructure. What type of testing is she planning to conduct?
- Misuse case testing
- Fuzzing
- Regression testing
- Interface testing
- Jim is designing his organization's log management systems and knows that he needs to carefully plan to handle the organization's log data. Which of the following is not a factor that Jim should be concerned with?
- The volume of log data
- A lack of sufficient log sources
- Data storage security requirements
- Network bandwidth
- Ryan's organization wants to ensure that proper account management is occurring but does not have a central identity and access management tool in place. Ryan has a limited amount of time to do his verification process. What is his best option to test the account management process as part of an internal audit?
- Validate all accounts changed in the past 90 days.
- Select high-value administrative accounts for validation.
- Validate all account changes in the past 180 days.
- Validate a random sample of accounts.
- When a Windows system is rebooted, what type of log is generated?
- Error
- Warning
- Information
- Failure audit
- During a review of access logs, Alex notices that Michelle logged into her workstation in New York at 8 a.m. daily but that she was recorded as logging into her department's main web application shortly after 3 a.m. daily. What common logging issue has Alex likely encountered?
- Inconsistent log formatting
- Modified logs
- Inconsistent timestamps
- Multiple log sources
- What type of vulnerability scan accesses configuration information from the systems it is run against as well as information that can be accessed via services available via the network?
- Authenticated scans
- Web application scans
- Unauthenticated scans
- Port scans
For questions 78–80, please refer to the following scenario:
Ben's organization has begun to use STRIDE to assess its software and has identified threat agents and the business impacts that these threats could have. Now they are working to identify appropriate controls for the issues they have identified.
- Ben's development team needs to address an authorization issue, resulting in an elevation of privilege threat. Which of the following controls is most appropriate to this type of issue?
- Auditing and logging are enabled.
- Role-based access control is used for specific operations.
- Data type and format checks are enabled.
- User input is tested against a whitelist.
- Ben's team is attempting to categorize a transaction identification issue that is caused by use of a symmetric key shared by multiple servers. What STRIDE category should this fall into?
- Information disclosure
- Denial of service
- Tampering
- Repudiation
- Ben wants to use a third-party service to help assess denial-of-service attack vulnerabilities due the amount of traffic during denial-of-service attacks. What type of engagement should he suggest to his organization?
- A social engineering engagement
- A penetration test
- Load or stress testing
- Testing using a fuzzer
- Chris is troubleshooting an issue with his organization's SIEM reporting. After analyzing the issue, he believes that the timestamps on log entries from different systems are inconsistent. What protocol can he use to resolve this issue?
- SSH
- FTP
- TLS
- NTP
- Ryan is considering the use of fuzz testing in his web application testing program. Which one of the following statements about fuzz testing should Ryan consider when making his decision?
- Fuzzers only find complex faults.
- Testers must manually generate input.
- Fuzzers may not fully cover the code.
- Fuzzers can't reproduce errors.
- Ken is designing a testing process for software developed by his team. He is designing a test that verifies that every line of code was executed during the test. What type of analysis is Ken performing?
- Branch coverage
- Condition coverage
- Function coverage
- Statement coverage
For questions 84–86, please refer to the following scenario. During a port scan, Ben uses nmap's default settings and sees the following results.
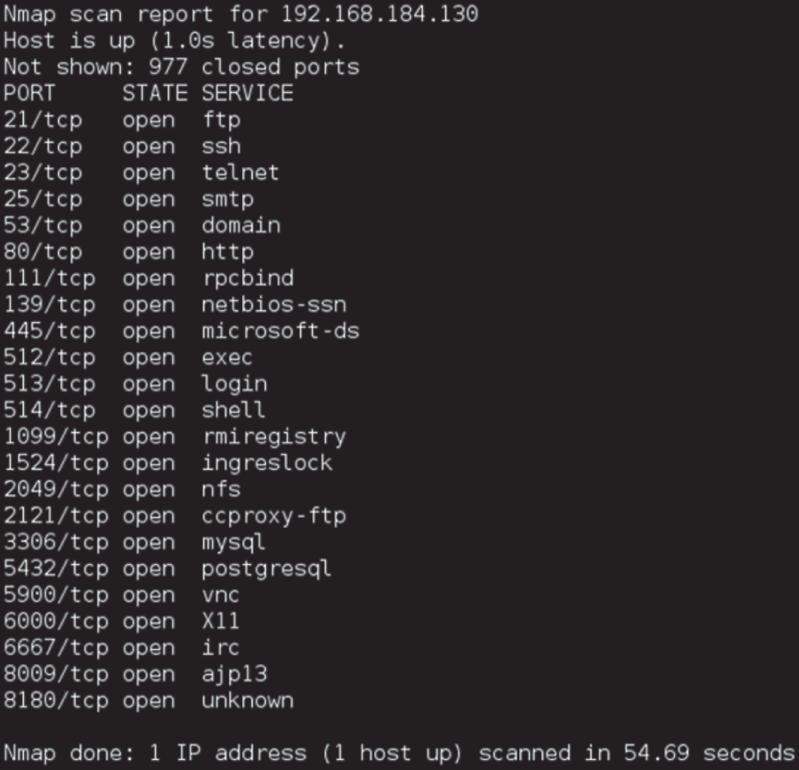
- If Ben is conducting a penetration test, what should his next step be after receiving these results?
- Connect to the web server using a web browser.
- Connect via Telnet to test for vulnerable accounts.
- Identify interesting ports for further scanning.
- Use sqlmap against the open databases.
- Based on the scan results, what operating system (OS) was the system that was scanned most likely running?
- Windows Desktop
- Linux
- Network device
- Windows Server
- Ben's manager expresses concern about the coverage of his scan. Why might his manager have this concern?
- Ben did not test UDP services.
- Ben did not discover ports outside the “well-known ports.”
- Ben did not perform OS fingerprinting.
- Ben tested only a limited number of ports.
- Lucca is reviewing his organization's disaster recovery process data and notes that the MTD for the business's main website is two hours. What does he know about the RTO for the site when he does testing and validation?
- It needs to be less than two hours.
- It needs to be at least two hours.
- The MTD is too short and needs to be longer.
- The RTO is too short and needs to be longer.
- Diana has engaged third-party auditors and wants to release an audit attestation to third parties without including details of the audit. What type of SSAE 18 SOC report should she request?
- SOC 1
- SOC 2
- SOC 3
- SOC 4
- While reviewing the software testing output for her organization's new application, Madhuri notices that the application has produced errors that included directory and file information shown to the web application tester. What issue should she include in her report about the application?
- It does not perform proper exception handling.
- The software does not handle misuse case testing properly.
- Debugging statements need to be removed.
- The code was not fully tested due to errors.
- What is the first step that should occur before a penetration test is performed?
- Data gathering
- Port scanning
- Getting permission
- Planning
- The president of Josh's company is concerned about a significant increase in cryptographic malware that is impacting other companies in their industry. She has asked John to ensure that the company's data will be recoverable if malware strikes and encrypts their production systems. What process does Josh need to undertake to be able to tell her that the company is covered?
- Encrypt all sensitive data.
- Hash all of the organization's data to detect cryptographic malware.
- Perform backup verification.
- Use anti-encryption technology to prevent the malware from encrypting drives.
- Joanna is her organization's CISO, and in her security operations oversight role she wants to ensure that management oversight is happening for security-related changes. What system should she focus on to track this type of data in most organizations?
- The SIEM system
- The IPS system
- The CMS tool
- The ITSM tool
- Henry wants to validate that his backups are working. Which of the following options is the best way for him to ensure that the backups will be useful in a true disaster recovery scenario?
- Periodically restore a random file to ensure that the backups are working.
- Review configurations and settings on a regular schedule to validate backup settings.
- Review the backup logs to ensure no errors are occurring.
- Regularly perform full restores from backups to validate their success.
- What type of vulnerabilities will not be found by a vulnerability scanner?
- Local vulnerabilities
- Service vulnerabilities
- Zero-day vulnerabilities
- Vulnerabilities that require authentication
- Jacinda wants to measure the effectiveness of her security training as one of her security metrics. Which of the following measures are the most useful for assessing the effectiveness of security awareness training? (Select all that apply.)
- How many people took the training
- The level of security awareness before and after the training
- The length of the training in hours
- The number of training events each individual attended this year
- Elaine has discovered a previously unknown critical vulnerability in a product that her organization uses. Her organization has a strong commitment to ethical disclosure, and Elaine wants to follow common ethical disclosure practices. What should she do first?
- Build an in-house remediation or control and then publicly disclosure the vulnerability to prompt the vendor to patch it quickly.
- Build an in-house remediation or control and then notify the vendor of the issue.
- Notify the vendor and give them a reasonable amount of time to fix the issue.
- Publicly disclose the vulnerability so that the vendor will patch it in an appropriate amount of time.
For questions 97–99, please refer to the following scenario. NIST Special Publication 800-115, the Technical Guide to Information Security Testing and Assessment, provides NIST's process for penetration testing. Use this image as well as your knowledge of penetration testing to answer the questions.
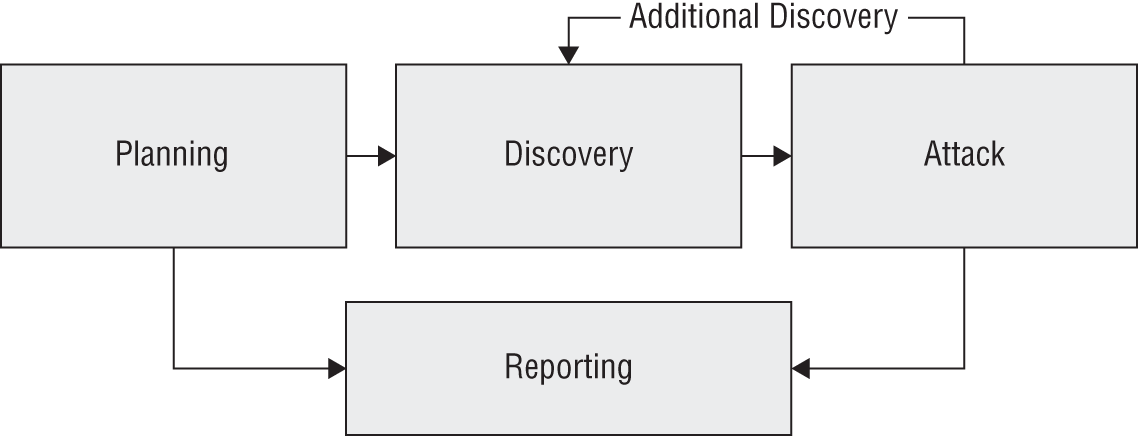
Source: NIST SP 800-115.
- Which of the following is not a part of the discovery phase?
- Hostname and IP address information gathering
- Service information capture
- Dumpster diving
- Privilege escalation
- NIST specifies four attack phase steps: gaining access, escalating privileges, system browsing, and installing additional tools. Once attackers install additional tools, what phase will a penetration tester typically return to?
- Discovery
- Gaining access
- Escalating privileges
- System browsing
- Which of the following is not a typical part of a penetration test report?
- A list of identified vulnerabilities
- All sensitive data that was gathered during the test
- Risk ratings for each issue discovered
- Mitigation guidance for issues identified
- Alex is using nmap to perform port scanning of a system, and he receives three different port status messages in the results. Match each of the numbered status messages with the appropriate lettered description. You should use each item exactly once.
Status message
- Open
- Closed
- Filtered
Description
- The port is accessible on the remote system, but no application is accepting connections on that port.
- The port is not accessible on the remote system.
- The port is accessible on the remote system, and an application is accepting connections on that port.
