This chapter begins with an overview of financial terms and tools used to build a business case for technology usage to aid the business cause. Then this chapter focuses specifically on building a business case for the IP VPN solution by utilizing these financial tools and considering pertinent factors specific to VPN technology. You will see, for example, that part of building the business case is outlining the IP VPN solution requirements and identifying user group characteristics. The chapter also includes a decision tree to help make the build versus buy decision. After making this crucial decision, a whole new phase of the project begins with specific challenges. This chapter concludes with a discussion of how to make the deployment of an IP VPN solution successful so you can make the most of your VPN technology decision.
In today’s business environment, ubiquitous connectivity and maximized use of corporate networked resources can be decisive factors that enable a business to reduce costs, increase productivity, and maintain a competitive edge.
Pressured by limited resources and budgets, IT managers increasingly rely on more cost-effective, flexible, and scalable IP VPNs to streamline their corporate networks and facilitate stronger external relationships with customers, suppliers, and partners. Adding to this challenge is a need to integrate data, voice, and video traffic over economical, scalable, and dependable networks. IP VPNs have emerged as a viable solution for meeting these challenges, and many IT managers are now looking to service providers for value-added, cost-effective, VPN-based services.
The bottom line for a business is to be profitable. In these trying times of slow economic growth, business management teams are “hunkering down in the board room” (Jack Welsh, Former CEO of GE) to identify cost-efficiency tools. It is important to note that information technology has emerged as a key business-enabling tool. However, to utilize IT to solve business issues, management teams look to financial and business analysis tools to equate costs and benefits of IT to the business’s bottom line profit-and-loss sheet.
The team managing the business essentially has to follow these key steps to successfully integrate VPN technology into their business:
Build a business case for having a VPN solution for the business.
Make a decision to build or buy the VPN solution.
Plan a successful deployment of the VPN.
Account for ongoing support for the VPN solution and the users in line with the current business charter.
Linking technology offerings and business values offers an interesting challenge. Here, in the case of VPN, CIAN tenants define what technology brings to you and your business. By defining the impact of each tenant on your business and then relating costs and benefits to that impact, you can discuss the justification for deploying VPN in your business environment. Table 2.1 lists the VPN CIAN tenants and shows potential benefits and impact for a business.
Table 2-1. Business Value Taxonomy
CIAN Tenant | Results | Value Level | Potential Benefits | Impact |
|---|---|---|---|---|
Confidentiality | Encryption ensures privacy of information | Ongoing, added, or new | Reduces risk of unauthorized disclosure | Risk reduction Regulatory compliance |
Integrity | Hashing ensures trustworthiness of the information | Ongoing, added, or new | Reduces risk of data corruption Business processes are not compromised | Risk reduction Regulatory compliance |
Availability | Systems are available | Ongoing | Reduces risk of data corruption Business processes are not compromised | Risk reduction Financial benefits |
Downtime is minimized | Ongoing | Faster reaction to security incidents | Risk reduction | |
Nonrepudiation | Acknowledgments from the information sender | Ongoing, added, or new | Allows proof that the information came from the sender without a dispute | Risk reduction Regulatory compliance |
Risk management is a key to making decisions. For example, when connecting the business to the Internet, it is imperative to protect intellectual property even though it costs significantly more than the Internet connection. Intellectual property residing in documents and records and means of communication such as e-mails must be protected by providing access on a privilege basis to the authorized users as a part of the risk management strategy.
The main business analysis tools, namely cost benefit analysis (CBA), return on investment (ROI), total cost of ownership (TCO), and net present value (NPV), are considered in this section. These tools can be used to analyze VPN investment protection for the business.
CBA is a decision-making approach that allows you to weigh projected costs against envisaged benefits. By carrying out this direct comparison, a business can decide if the quantitative (free cash flows) and qualitative (intangible yet valuable) benefits of the solution are worthwhile compared to costs and disadvantages. In this comparison, if the benefits outweigh the costs, the solution is selected.
ROI provides a framework for identifying costs versus benefits with a balanced view. However, it is advisable to concentrate on hard savings to make the business case with ROI. Qualitative benefits are important to note, but often those augment the foundation of the business case—hard savings reflected in quantitative benefits.
TCO is a tool commonly used to identify the cost of the purchase of an entity as well as all aspects in the operation and associated maintenance expenses. To obtain an accurate financial picture, it is advisable to calculate year-on-year expenses as well. The chief advantage of doing a yearly calculation is that it identifies entities with high operational costs, even when the initial capital costs seem low. Yearly calculation helps in identifying that even with low capital costs, considerable expenses can occur because of ongoing operational costs.
The NPV of a project represents the potential benefits and costs converted into equivalent value today. This is done by assigning monetary values to the benefits and costs and calculating the sum of the current financial values of the net benefits (revenues minus costs) minus the initial investment.
The calculation of NPV involves three simple, yet nontrivial, steps. The first step is to identify the size and timing of the expected future cash flows generated by the project or investment. The second step is to determine the discount rate or the estimated rate of return for the project. The third step is to calculate the NPV using the provided definition.
Note
Various detailed references for business analysis tools and definitions are available on the web and in print. Given that the scope of this Short Cut is to provide information on making the initial build or buy VPN decision, you are encouraged to educate yourself elsewhere about the details of various general business analysis tools.
To start, definitions for CBA, ROI, TCO, and NPV can be found at
You can find Dr. Jim Metzler’s “Computing the RoI of an IT Investment” at
http://www.webtorials.com/abstracts/MetzlerPresentation1.htm
The case studies in Chapters 4, “Cisco Case Study: Deploying VPN Services for WAN Connectivity and Disaster Recovery,” and 5 “Case Study: Managed VPN Services for Teleworkers Using IPsec Technology,” show the application of some of these tools to VPN deployment scenarios.
Business management teams often struggle to select which business analysis tool to use for making the business case for VPN deployment. Following is a brief comparison with advantages and shortfalls for each tool.
CBA helps build a good theoretical argument for making a business decision, yet it misses out on components such as discounts that are part of any business’s sales structure to cultivate customer relations. As a result, it is more adequate to select a method that considers the time value of monies, as NPV does. CBA also helps identify costs that are tangible, quantified, and financial. However, the benefits can be tangible as well as intangible. A word of caution is to help the decision makers understand tangible and intangible yet valuable benefits. The main way to measure intangible benefits is to establish an operational relationship with measurable components. For example, employee morale is difficult to measure, but rapid response time and courteous service resulting in high customer satisfaction are measurable. By establishing the relationship between customer satisfaction and employee morale, you can understand the value of intangible benefits.
ROI provides a framework for identifying costs versus benefits with a balanced view, whereas TCO provides a metric of the total cost of ownership over a period of time and includes both the acquisition cost and the total cost per year. Both CBA and NPV provide quantitative or hard-savings numbers.
The strength of TCO is providing an understanding of future costs that may not be apparent when an item is initially purchased. However, the metric focuses only on cost, and companies that rely entirely on TCO end up following a strategy that minimizes expenditures rather than maximizes the return for the company. The danger is ending up selecting the least costly security solution but ignoring the solution that provides the greatest impact for the bottom line.
In the case of a VPN solution, TCO must include training costs for operation, support and users, maintenance activities, diminishing performance incidents (for example, if users are kept waiting), security incidents costs, disaster recovery costs, facilities costs (for example, heat ventilation and air-conditioning costs), and other operational expenses in addition to the capital costs incurred at the inception of the project for buying hardware, software, and professional services for design and implementation tasks.
The strength of ROI is that future benefits are considered and included in the cost benefit analysis. The ultimate focus is to maximize benefits from the solution and not focus solely on minimizing the cost of the technology. So ROI entails the following:
A balanced approach to investment justification
A consistent approach for mapping the expected results
Reporting the results
However, it is important to avoid unrealistic expectations regarding returns.
Strategic investments have intangible benefits that often outweigh projected financial benefits. As a result, you can select the business analysis tool or combination of tools to prepare your business case. After it is prepared, the business case must be used in making the decision to deploy a VPN solution.
In today’s fast-paced business climate, increasing market share often depends on unprecedented levels of network access and agility. Businesses are exploring ways to stay competitive, improve revenue, and increase productivity by taking full advantage of e-business initiatives such as workforce optimization, customer care, e-commerce, and corporate communication. Pursuing these initiatives requires complex networking, IT resources that are capable of providing ongoing 24-hour monitoring and management, and cost-effective integrated voice and data services. As a result, businesses are reassessing their corporate networking infrastructures and are seriously considering outsourcing alternatives, such as carrier-managed VPN networking solutions. Service providers offering managed VPN services are helping organizations meet today’s challenges.
Pressured by limited resources and budgets, IT managers increasingly rely on more cost-effective, flexible, and scalable IP VPNs to streamline their corporate networks and facilitate stronger external relationships with customers, suppliers, and partners. Adding to this challenge is a need to integrate data, voice, and video traffic over economical, scalable, and dependable networks. IP VPNs have emerged as a viable solution for meeting these challenges, and increasing numbers of IT managers are now looking to service providers for value added, cost-effective, VPN-based services. High-speed network connectivity, reliability, security, and management make VPNs ideal for supporting a range of enhanced services, such as defense-in-depth security, IP telephony, videoconferencing, e-commerce, and content hosting. Service providers offering managed VPN services present a viable alternative to building your own network solution, and in some cases for businesses to extend corporate resources to mobile workers, small branch locations, and partners.
In the spring of 2003, Cisco Systems, Inc. contracted with The Yankee Group to identify the drivers and tangible benefits that European enterprises were deriving from IP VPN environments.
Note
The Yankee Group Report “Navigating the IP VPN Market: A Decision-Making Guide for European Businesses” is available at
http://www.cisco.com/application/pdf/en/us/guest/netsol/ns172/c1272/cdccont_0900aecd800d711a.pdf
The Yankee Group looked at the decision-making process behind the range of IP VPN deployments across corporate backbones, which can be categorized into three broad areas:
Network-based IP VPNs fully managed by a service provider. These can be categorized as bought VPNs.
Managed CPE-based IP VPNs, where a service provider installs managed equipment and connectivity. These can be categorized as bought VPNs.
Do-it-yourself IP VPNs, where customers buy equipment from a vendor and connectivity from a service provider. These can be categorized as built VPNs.
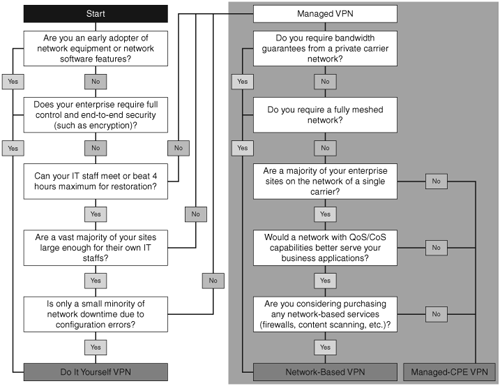
Figure 2-1 shows a decision tree from The Yankee Group report for businesses to make the decision whether to build the IP VPN solution or to buy it. An important point to note is that businesses with an IT department are targeted here. Mainly because of the complexity of the technology, as well as skill levels and resources required to design, deploy, monitor, and maintain a VPN, it is highly recommended that businesses without an established IT department buy the adequate IP VPN solution from their trusted service provider.
Effective VPN solutions are available whether an organization chooses to proceed with in-house deployment or to partner with a service provider. However, to help converge disparate networks, maximize return on investment, and work with constrained resources, IT managers have discovered that selectively outsourcing network implementation and some aspects of the ongoing management of their evolving network to a qualified service provider is a viable alternative that brings distinct cost savings and operational advantages. Outsourcing also can lower implementation as well as ongoing support cost and free valuable resources to focus on strategic IT initiatives.
Some of the factors to consider when building or buying a VPN solution are the following:
Number of customer sites and mobile users—. The higher the number of sites and the larger the number of mobile users, the more costs are incurred in designing, deploying, monitoring, and maintaining the self-built VPN solution. On the other hand, buying the solution would help you negotiate a better overall deal, especially for hard-to-reach sites.
Number of departments of mobile users—. Because the VPN solution design incorporates access to more confidential information maintained by multiple departments, coordinating corporate-level as well as departmental-level security policies would require more efforts. For the buy decision, it becomes imperative to get buy-in from all key stakeholders for the overall VPN solution design and the SLA with the service provider.
Number of hours out of office on sales or other travel—. Understanding this helps define VPN solution usage as well as help desk requirements, which impact the SLA negotiation for the buy decision or support coverage necessities for the build decision.
Number and types of network resources available to mobile users—. At the VPN solution head-end, it is important to identify all necessary resource and application requirements to help make the build or buy decision, as well as decide on the right VPN technology to use.
Percentage of critical business to be performed remotely—. Implications of this factor are reflected in the design of the VPN solution if you are building or the negotiation of the SLA if you are buying the VPN service.
Percentage of increase in user productivity—. This factor provides a metric for business case analysis, but it is also a good metric to track after deploying the VPN solution on an ongoing basis.
Number of remote transactions (sales order, travel expenses, and so on) and the capability of business to understand incoming sales order generating revenues or outgoing expenses—. Business case analysis, especially the quantitative part of the analysis, benefits from collecting information described in this factor. This is an important metric for both the building and buying VPN decisions.
Hourly cost of an engineer—. This is mainly a consideration for building a VPN solution. This is an important factor because a number of engineers will be required to design, build, monitor, and maintain the VPN solution.
Assessment of existing infrastructure to evaluate IP VPN solution readiness on the current device installation base—. This is a very important factor because it allows you to take an inventory of the existing network elements. In the build case, you need to assess what hardware and software upgrades are needed and what you already have that can be leveraged. In the buy case, service providers need an accurate inventory list for maximum cost efficiency. This also helps with identifying deployment requirements, helping the rollout to be as efficient as possible.
Time to perform various deployment steps—. In line with the previous factor of taking inventory of the network, estimating the time to roll out the VPN solution helps with migration of applications in both building and buying scenarios. Determining how quickly you need to deploy your VPN can also impact the build versus buy decision.
Number of help calls—. For the build case, this factor helps with establishing requirements on how the help desk support must be staffed, whereas in the buy case, this factor identifies how to negotiate the SLA for response time required to troubleshoot any issues with the VPN solution during deployment, monitoring, and maintenance phases.
Percentage of traffic between IP VPN nodes—. Depending on the type of VPN deployed, it is possible that bandwidth consumption will be affected. It is imperative to monitor traffic levels on all VPN links and, if required, upgrade the bandwidth capacity to satisfy QoS and SLA requirements for the applications traversing on the links between VPN nodes.
Throughput and capacity utilization—. Ongoing monitoring is essential to successful deployment and maintenance of the VPN solution. User experience associated with utilizing VPN highly depends on VPN monitoring, so in both build or buy cases, throughput and capacity utilization is very important.
As much as possible, assign a cost figure to each of these factors during the business case process. To understand the impact of each of these factors in the building as well as the buying decision, read the case studies in Chapters 4 and 5.
Anytime, anywhere access to the workforce and business promises dramatic gains in productivity and competitive differentiation—not merely tactical gains such as paperwork reduction. Especially, a mobile and telecommuting workforce can be more responsive to customers as well as in their day-to-day duties, because it is able to seize business opportunities on-the-fly, without having to wait for pricing, customer data, product specifications, or other key data stored in the business data center. Nimbleness and agility to detect market changes without delay due to visibility into field operations can compress service cycles and accelerate business processes.
It is essential for the business case to consider user-group benefits and productivity increases. This section includes examples of these benefits for the mobile and telecommuter workforce and covers other cost advantages.
Because a lot of customer interactivity is a key to the mobile workforce’s success, significant competitive advantage is gained by providing mobile information access. The mobile workforce requires the following to operate more efficiently and with high productivity:
Anytime, anywhere availability of the confidential information with ease of use with mobile devices and minimum delay.
Closely linked business processes helping field resources to close the deal. For example, being able to get discounts approved quickly given the size of a customer order allows a significant advantage.
Effective yet scalable mobile access to field resources, leading to productivity gain by allowing quick and secure access to information required to complete the job—for example, making a purchase order entry from the customer site.
Delivery of greater intelligence to the field by extending the reach of critical business processes to the point of action.
The advantages of mobile information access and integrated processes to serve the mobile workforce’s requirements go beyond financial gains:
Growing revenue due to productivity gains because an efficient workforce has access to required applications, information, and resources.
High customer satisfaction due to timeliness of the workforce, which builds customer loyalty and retentions.
High visibility for management, allowing more informed decisions, as business processes integrate mobile workforce operations.
Competitive advantage, because easily accessible information allows the mobile workforce to quickly take advantage of opportunities.
Mobile or teleworker-based organizations can be more competitive, more collaborative, and more agile—not just keeping pace with the competition, but moving a step ahead. According to Gartner, 80% of key business processes will involve the exchange of information among mobile workers. This type of agility requires that information flow both ways: management needs insight into field operations, and mobile workers need access to up-to-date data and applications. Organizations that can move processes and information to the field are more likely to one-up their competitors, close new business deals, and increase revenue from existing clients.
Traditionally, businesses have focused solely on the day-to-day productivity benefits of teleworking. Recent advances, however, point to a smooth transition from the corporate office to the home office in many circumstances, greatly improving the capability to continue operations in the face of disruptions such as inclement weather, health concerns, security alerts, and major traffic impasses. Businesses with teleworking solutions benefit by being able to take advantage of a talent pool with fewer geographic limitations. They can also take advantage of a geographically dispersed employee base that can be closer to the customer base or partners.
Enterprise business continuity plans typically focus on failures in the IT infrastructure. Few plans prepare for loss of employee access to the workplace. Spurred by incidents such as inclement weather, commuter issues, and man-made and natural disasters, more businesses are developing plans to provide secure alternative work arrangements. A distributed workforce requires organizational flexibility and the agility to help ensure operational continuity.
As a result, and combined with the increase in traditional telecommuting, teleworking (or telecommuting) programs are experiencing significant growth. Teleworking enables employees to work effectively at distributed, nontraditional office locations, such as at home, on the move, or in telecenters. The evolution of broadband access services, such as cable and digital subscriber line (DSL), has enabled the creation of cost-effective teleworking programs even for small to midsize businesses.
For any business, it is important to show what the direct savings are from adopting a new technology. Following is a summary of some savings you can expect from adopting a VPN:
Works with existing cost-effective broadband access networks, including dynamic addressing (does not require static IP address), so multiple client devices can be supported in the home office.
Offers reduced WAN costs with an always-on VPN tunnel to the teleworker and lowers ongoing maintenance and support costs.
Reduces the complexity of support and integration of new applications with a solid, IP-based infrastructure that supports converged applications.
Removes the need for home phone direct dial and offers significant cost reductions on line toll charges for dial-up and long distance. The solution integrates voice services over the single, broadband-based connection, eliminating these charges while delivering superior overall connectivity performance. These savings alone can pay for your initial investment.
Building a do-it-yourself VPN solution provides the following advantages:
Time-to-value for VPN-enabled IT infrastructure is improved by supporting new technology and applications faster across branches, remote offices, mobile workers, partners, and such.
With the built-in capability for convergence, deployment of IP VPN helps businesses with consolidating data, voice, and video traffic onto a single service offering or network, thus reducing costs. Businesses do not need to buy their own WAN equipment and make large capital expenditures.
IP VPN quality of service capabilities can ensure mission-critical applications requiring end-to-end bandwidth guarantees without sending WAN costs through the roof.
IP is ubiquitous, and organizations can reach remote offices, customer, suppliers, and partners anywhere in the world via the Internet. In addition, convergence in the application development world has been occurring so that current applications are being developed around the IP protocol.
Buying, or outsourcing, a VPN solution provides the following advantages:
Allows you to focus on core business objectives and have free time for high-value IT initiatives.
Can meet business pertinent regulatory requirements by generating required audit reports from the monitoring information collected from the deployed VPN solution. As discussed previously, Sarbanes-Oxley, HIPAA, PCI-DSS, Directive 2002/58/EC for EEC, and APEC-OECD for APAC are a set of regulatory requirements in force.
SP provides 24×7×365 help-desk support so that the business IT department experiences reduced day-to-day network management and maintenance workload.
Reduced overhead and unpredictable costs associated with implementing and managing a network in house.
Provides a cost-effective foundation to add other network-based, value-added managed services (such as IP telephony and managed security) and have a positive impact on time to value.
Facilitates MAC (moves, adds, and changes) activities related to business, applications, people, and other changes with ease and lower cost.
Technology changes can be negotiated with the service provider to drive benefits to the core business. Also, other providers can be leveraged to benefit from the latest technology offerings. For example, managed VPN IPsec-based service for site-to-site and remote access solutions can be augmented by adding SSL VPN for certain remote access user requirements.
Overall success of the VPN solution deployment depends very much on a smooth and successful rollout. After making an all-important decision on building or buying a VPN solution, the business has to oversee and ensure that rolling out the VPN solution is done with care and diligence. Stewardship of the VPN solution starts from the point at which a business decides to utilize a VPN solution, whether it is built or bought. The internal IT department will be responsible for deploying if you choose the build option, and a service provider will deploy if you choose the buy option.
Several other aspects should be considered as well. For example, to maximize the investment, it is also important to plan, design, implement, and operate (PDIO) the solution in the right manner. Having a VPN solution integrator ensures that PDIO aspects have received appropriate attention to ensure a successful rollout. Details of how an integrator helps are outlined later in this chapter. Having an integrator adds to the overall cost of the VPN solution, but it is very worthwhile to incur that cost to ensure a successful rollout.
Rolling out IP VPN successfully and in rapid fashion helps all parties involved: the business for improved productivity and cost-cutting and external suppliers for generating revenues as the project completes.
A basic guideline for overseeing a rapid IP VPN rollout is as follows:
Carry out an audit of what technology, applications, and systems are already in place—. This helps you understand what other technologies and systems are in place because of mergers, network audit validity, and such.
Familiarize appropriate parties with IP VPN technology and its usage—. Support organizations as well as users of the IP VPN technology must be trained to use the technology to make a straightforward transition.
Start the IP VPN deployment with a limited pilot—. Identifying an internal or external party to test with under the pilot phase also gives great productionlike exposure in a contained environment.
Select hub locations for optimizing the latency for most users—. Having equally good or better user applications when a change happens is very important; even though support and cost implications are there, hub location plays a crucial role in rollout success.
Plan a phased approach for new applications and services—. Rapid rollout with well-tested key applications is better than migrating all applications and service at the same time.
With VPN rollout, identify processes that can be automated—. Automation is a key to scalability and faster completion of the rollout. It also helps with making the solution cost effective. For example, new requests from remote branches to connect into the VPN solution can be automated to generate the configuration required and export it to the provisioning systems. That level of automation would help with scaling and cost efficiency because more branches can be connected in a short time and with fewer resource requirements from the security operation center (SOC). Automating any process helps identify glitches in the smooth running of that process. As a result, automation helps with identifying and resolving issues adversely affecting productivity.
According to the Cisco commissioned Yankee Group report “Navigating the IP VPN Market: A Decision-Making Guide for European Businesses,” there will be a bigger cost to enterprises if they do not invest time to audit. Although the report addresses the European market, it is equally true for worldwide markets.
If accurate information about the network architecture, topology, and current configuration is not gathered or provided prior to the VPN solution implementation, the risk is that the network implementation will not be optimally designed. In addition, if the install base inventory is not up-to-date, you might need to return to the negotiating table with a supplier to revisit requirements. So keeping tabs on equipment deployments, network connections, and applications usage is not only good housekeeping, but also good business. However, some suppliers offer this service for organizations that do not think they can do this thoroughly or cost effectively themselves.
Table 2-2 details application utilization by telecommuters of different types. It is important to understand application-based requirements on a user group basis because granting appropriate QoS characteristics helps with defining VPN solution requirements.
Table 2-2. Application Requirements for VPN Solution Users
Application | Occasional Users to Unmanaged VPN Clients | Part-Time/Full-Time and Day Extenders to Enterprise Class Teleworkers |
|---|---|---|
Yes | Yes | |
Web-based application | Yes | Yes |
Mission-critical application | Best effort | Prioritized |
Real-time application | Best effort | Prioritized |
Voice over IP | Best effort | High quality |
Video on Demand or Streaming Media | Unlikely | High quality |
Videoconferencing | Unlikely | High quality |
Remote configuration and management | No | Yes |
Integrated security | Basic | Full |
Resiliency and availability | No | Yes |
Note
The following is an explanation of some of the terms appearing in Table 2-2:
Unmanaged VPN clients—. Self-supporting VPN users building wireless, voice, and other capability in a nonstandard way on business-provided VPN connectivity.
Enterprise class teleworkers—. Business-supported VPN solutions include voice, video, and data connectivity with wireless connectivity on tested small office/home office (SOHO) VPN solutions.
Best effort—. When the VPN solution cannot guarantee meeting the user requirements, but a good faith effort will be made to provide the connectivity service.
Prioritized—. When the VPN solution can identify priority marking on IP packets and meet the user requirements reflected in IP packet marking in the order of importance.
High quality—. When the VPN solution can guarantee meeting the user requirements and deliver end-to-end connectivity requirements to the user’s satisfactory level.
Basic security—. Provided by the VPN solution. For example, IPsec VPN provides security with CIAN tenants.
Full security—. A VPN solution providing firewall, intrusion prevention systems (IPS), and wireless security to adequately protect the telecommuter class VPN.
Note
The information in Table 2-2 comes from Packet magazine, volume 16, number 2 (second quarter 2004).
Conducting a network and traffic management study before implementing a VPN solution ensures that you have a thorough assessment of all the network hardware, including servers, switches, and devices as well as network traffic flow, patterns, and volumes. Understanding the IP addressing structure and device inventory information available from operation support systems (OSS), including end points such as servers and desktops, adds to the thoroughness of the study. The next step is to review the network topology. It is usually less expensive for an enterprise to provide its own network hardware and topology assessment information, instead of asking the equipment supplier, service provider, or integrator to do it. The traffic management study should gauge the level and type of application traffic on the network. As a rule, during peak hours, real-time applications such as IP telephony should account for about 30% of the total bandwidth available.
Because network changes happen on a regular basis, it is important to consider network management tools to monitor the health and performance of LAN and WAN traffic on an ongoing basis. Even though it may seem that more than enough bandwidth is available to support the application load, the bursting nature of data traffic may cause a bandwidth-intensive data application to interfere with a packet-based voice or video call. These management tools are particularly important during the initial implementation of new applications to the network, which will require reengineering. Some service providers have developed these management tools, but the area remains immature.
There are two chief ways of rolling out VPN solutions for either build or buy decisions:
Roll out the solution with internal staff.
Roll out the solution with an integrator partner.
Even though some elements for the preceding rollouts are similar, it is important to note that while dealing with an external integrator partner, even though rollout of VPN solution responsibilities and a successful rollout are contracted out, carrying out close monitoring of the project’s progress and vendor management are still very important.
For a business, an integrator partner may be part of their service provider organization or a separate entity acting on behalf of the service provider that carries out deployment of the VPN solution. An integrator can be chosen by the business if the business is working on other technical or business solutions with the same integrator and the integrator has very good familiarity with the network and security policies of the business.
Using an integrator with your internal staff or the managed VPN provider has significant advantages:
Knowledge of the VPN technology because the integrator has real-world experience of VPN solution rollouts.
Experience with VPN design, implementation, and the maintenance of the technology of a VPN solution that the business is deploying.
Extra bandwidth for internal IT resources as the integrator assumes the responsible for VPN solution deployment.
Cost considerations for utilizing a VPN integrator must be made as a part of preparing the business case. However, the cost of a VPN integrator may be treated as buying an insurance policy for the success of the VPN rollout.
The following is the process for selecting an integrator:
Put together a cross-functional team from all departments involved, and solicit input about their needs for an integrator. In the cross-functional teams, include IT staff, accounting, business operations, human resources, and sales and marketing.
Issue a request for information (RFI). An RFI is generally used to collect written information from various suppliers who provide business-requested information in a standard format. As a result, a comparative analysis can be made by the business to understand the integrator’s size, project management process, know-how to deploy VPN solution, and such.
Identify a list of integrators and interview them for evaluation. Prepare a checklist for internal parties involved and distribute that in advance so that all the questions are answered and everyone’s feedback is gathered.
Reduce the list of integrators and provide them with a request for proposal (RFP). An RFP is an invitation for suppliers, through a bidding process, to bid on a specific product or service. An RFP is usually part of a complex sales process, also known as enterprise sales. RFP helps identify timetables of the projects, teams if subcontractors are involved, work processes, pricing, and other details. Also important is to have the integrators sign a nondisclosure agreement (NDA).
Note
You can find a sample RFI template at http://www.omg.org/cgi-bin/doc?rfi-template.pdf.
You can find a sample RFP template at http://www.omg.org/cgi-bin/doc?rfp-template.pdf.
Carry out reference checking for the integrator. This is an important step because it adds further validity to the integrator decision.
Add qualitative feedback from internal teams to the RFI and RFP.
Identify an exit strategy. With details gathered in the RFI and RFP, a comprehensive scope of the IP VPN rollout project can be built that has a clear beginning and end so that no additional scope-creep occurs, resulting in adversely affecting time to value.
With a successful rollout of the IP VPN solution, you should commence monitoring and maintenance of the IP VPN network and its resources. This includes the following, each of which is covered in more detail in this section:
VPN resource management
Capacity planning
Monitoring and reporting frameworks
Metrics
Granularity
With the establishment of a jointly working NOC and SOC, it is important to carry out health monitoring as well as security incident monitoring. Carrying out health monitoring as well as monitoring for security events actually provides a great wealth of information that a business’s IT department can use to generate comprehensive reports. From managed VPN services, it is prudent to negotiate monitoring for network health, availability, and capacity utilization, as well as information that is pertinent to security detection.
Gaining visibility with network telemetry allows the IT department to control the network utilization as well as project bandwidth purchase, thereby controlling IT budget spending to match with applications’ requirements of the network bandwidth.
The general perception is that if an Internet connection already exists, configuring IPsec VPN on the capable Internet router accomplishes the task of moving to a VPN solution. Capacity planning for a VPN solution is very important, and it is imperative to consider both endpoints of the VPN solution. If both endpoints have large Internet ports, and the amount of traffic that will be carried on the VPN does not have a noticeable effect on performance at either site, then VPN does not increase capital cost during the rollout or soon after rollout when more traffic is generated from the site users. If, in the assessment preceding the rollout, small or overutilized Internet ports were not discovered, maintaining acceptable VPN performance will require an expensive bandwidth upgrade. When the VPN connection is problematic—for example, when the two endpoints are handled by different service providers and especially when Internet service at one endpoint is provided by a smaller or less experienced SP, internal troubleshooting and management costs can increase. These costs are often hidden until after the VPN connection has been established. Careful planning based on expected traffic requirements, availability requirements, and the SP available at each site gives prospective VPN users a better idea of what their cost of ownership will be for their VPN connections.
Latency fluctuations often indicate capacity issues unless the connectivity itself is over satellite or similar high-latency-prone technology.
Capacity planning is one of the most significant advantages of opting for a managed VPN service rather than building your own. With comprehensive reporting being part of the SP’s value offering, a business can design a process to review the delay, jitter, and loss measurements and application-carrying capacity planning with great ease.
Businesses utilize more applications to accommodate new requirements or increase productivity. At times, some applications can start utilizing more bandwidth on the WAN connection given the number of users utilizing it. Hence, it is prudent to create a guideline on bandwidth usage:
Establish bandwidth requirement guidelines as a part of the pre-rollout assessment.
Identify and utilize bandwidth measurement metrics.
Create a process to review bandwidth utilization and capacity planning guidelines.
If a capacity planning rule kicks in, start a bandwidth utilization investigation. For example, a capacity planning rule be necessary if bandwidth utilization reaches 80% of capacity for three consecutive days in one week’s monitoring cycle. An NOC-mandated bandwidth utilization investigation might then look if it sustains there for periods of 60/120/180 minutes in a single shift.
If, as a result of a bandwidth utilization investigation, it is projected that the usage of bandwidth as well as other resources has increased, start an upgrade process. This upgrade process may include bandwidth as well as hardware upgrades on one or multiple sites.
An IT department becomes a service provider for the businesses that have built their VPN connection. This is in contrast to a service provider’s ability to offer SLAs—essential to attracting and retaining customers in certain situations. Basic SLAs for IP-based VPN services guarantee performance metrics for network availability, packet loss, delay, delay variation (jitter), and throughput. By refining these SLAs, service providers are generating incremental revenue from premium service levels, increasing customer retention, and gaining an edge in attracting new customers. Cisco offers four techniques that service providers can use to improve their SLA service offerings:
Improved network-performance metrics
Finer granularity by offering different metrics for different traffic
Measurement from customer site to customer site
Visibility into network performance through management tools
Figure 2-2 gives more details about these four techniques.
In the case of the business building a VPN solution, the IT department assumes the SLA-related responsibilities.
Service providers gain a competitive edge by guaranteeing a higher level of network performance—for example, a higher percentage of uptime, lower mean time to repair (MTTR), or a lower latency versus their competitors.
Cisco offers two technologies that service providers can use to improve availability of their Layer 3 VPN services:
Bandwidth protection in the core network
Dial backup in the access network
SLAs with higher network availability boost customer retention and help attract new customers.
Bandwidth protection for Layer 3 VPNs is analogous to automatic protection switching (APS) for SONET. In an MPLS network, the enabling technology is Fast Reroute, part of the traffic-engineering capabilities of the Cisco IOS Software. If a link or node anywhere in the network should fail, the Fast Reroute feature routes traffic to another path within 50 milliseconds, practically eliminating the downtime.
Here is a link providing information on SONET APS and Fast Reroute:
http://www.cisco.com/en/US/tech/tk482/tk607/technologies_white_paper09186a0080094baa.shtml
Dial backup is a design technique that improves availability in the access network. If the primary connection becomes unavailable, enterprise customers can continue to access the VPN via an ISDN dial backup connection. Service providers generally charge a premium for dial backup.
Basic service provider SLAs stipulate the same network-performance metrics for all traffic traveling across the network, regardless of the traffic type or destination. With more granular SLA measurements that take into account the type of traffic or its origination and destination, the service provider can further differentiate its service. QoS uses classification, marking, queuing, policing, and shaping of the network traffic to allow a provider to create different classes of service (CoS) with different latency, jitter, and packet loss characteristics. Voice, for example, requires very low latency and jitter, whereas an additional half-second delay for e-mail is inconsequential. Service providers typically offer three tiered service classes:
Real-time applications such as Voice over IP
Business-critical applications such as enterprise resource, planning, ordering, and financial transactions
Best-effort services such as e-mail
Controlling costs during the rollout is essential, but managing costs of the VPN solution does not stop there. Here are the metrics to monitor ongoing costs associated with a VPN solution:
Connectivity costs, via Internet, for the number of customer sites and mobile users
Internet bandwidth requirement for the number of departments of mobile users
Availability requirements, resulting in a higher-than-basic SLA, deemed from the percentage of critical business to be performed remotely
Hourly cost of an IT engineer required on site or to manage a number of VPN sites
Time to perform various deployment steps, subsequent to migration, because of changed applications and use of resource requirements
Number of help-desk calls
Building a business case with the right business analysis tool is the first step in deploying a VPN solution to address the business’s operational requirements. A combined result of qualitative analysis and quantitative analysis carried out by tools such as cost benefit analysis, return on investment, total cost of ownership, and net present value help put together a comprehensive business case.
Subsequent to preparing a business case, businesses have to make a key decision of building or buying the VPN solution.
Regardless of whether the decision is to do-it-yourself (build) or outsource (buy), it is crucial for businesses to carry out a successful deployment of the VPN solution.
Finally, businesses must establish a VPN solution support structure that considers help desk support, the hardware vendor relationship including risk management, monitoring for faults as well as capacity for required traffic, and managing costs for continued cost efficiency.
Having an integrator during the deployment helps businesses achieve rapid time-to-value for a VPN solution; it is worth the additional cost to ensure a successful rollout of the VPN solution.