In this chapter, you will learn tips in these areas: what assets are, the asset security, protecting assets, privacy, memory and data management, data handling as part of asset security, and the public key infrastructure used to protect assets.
Information and Asset Classification
Tip #12: Learning various levels of data classification
Data classification from public (open) to top secret (only a few can access) levels and the classification procedures (first step to the last).
Domain: Asset Security, Security and Risk Management.
Subdomain: Information and asset classification.
Subject background: Classification of information can be for the government and for the private/public-sector companies. Clearly, the private and public sector companies are not governed by the politicians or the government and thus can have their own classification system and need not conform to any single rule. Moreover, the classification system for private industry can be different from one company to the other.
Levels of Classification per Private Sector
Type | Description |
|---|---|
Sensitive | Strict and limited access to information that needs a high degree of honesty/reliability/job level. Disclosure of this data causes severe damage. Examples: mixing formulas for drinks, patented information. |
Confidential | Restrictive information and disclosure may still cause damage. |
Private | Private information is generally company-owned data like the patient records or the human resources data that has personally identifiable information (PII). It is mandatory for the company to protect this data. |
Proprietary | Proprietary information can be generally given to others on a limited basis but can still cause some problems. Examples: Specifications of a new product, management plans of a new office. |
Public | Public information can be freely disclosed. Examples: information used for marketing, demographics of the company, etc. |
Levels of Classification per US Government Regulations
Type | Description |
|---|---|
Top Secret | Strict and very limited access to information that needs a high degree of honesty/reliability/job level. Disclosure of this data causes “exceptionally grave damage.” |
Secret | Restrictive information and disclosure may still cause “serious damage.” This is the second highest classification. |
Confidential | Low-level classification for data. Disclosure causes damage but can be disclosed with proper authorization. |
Sensitive but Unclassified (SBU) | Some personal information such as medical data. May not cause damage but needs to be kept away from public eyes. Examples: military recruiting numbers, medical PII, etc. |
Unclassified | This is not a classification per se but can be said as information that can be provided to anyone without reservation. Examples: passed budget limits for past years, population data, etc. |
Private or public companies have their own classification schemes to protect data.
The government/military has a set classification that must be adhered to.
Always use caution in disseminating information even if the data is at lowest classification level, which is public or unclassified.
Classification applies to both individuals and the equipment or data.
Information classification is necessary to protect the assets and the company/government/military or the citizens of the country.
The FIRST STEP in data classification is to decide what/how many classification levels a company must have.
The SECOND STEP of data classification is to decide which asset goes to which classification level and who can access that level.
Be clear to put assets in one classification level only. There must be no overlap for any information from one level to another.
When data is being classified, the rules apply to all forms of data—paper, electronic or otherwise (in other words, to all soft or hard copies).
What data is stored, kept, or destroyed is the decision of the data owner.
- A)
Top Secret
- B)
Secret
- C)
Unclassified
- D)
Secret but Unclassified
Analysis: From the verbiage, we note that all the data will always be on the cloud. The cloud data and its privacy are taken care of by the cloud provider. The computer operators do not store anything on computer memory. This means if someone hacks into the computer, they cannot access any data since the data is on the cloud and not on the computer itself. Operators access the cloud with two-point authentication, which makes it difficult for hackers to further dig into the cloud. Thus, the computer used to access the cloud is just a mere instrument and will not store anything. Unless someone decides to access the cloud, this computer can be used for even word processing and checking the news on internet.
Statement: Removing the unnecessary verbiage, the statement can be rephrased as follows:
A government organization decides to migrate to cloud computing. All the data will be stored ONLY on the cloud. The cloud data when disclosed can cause “serious damage” to the country, and its confidentiality is taken care of by the cloud computing provider.
Question: A government organization decides to store data ONLY on the cloud. The operators access data on the cloud via a two-step authentication procedure. What classification levels should these computers BEST belong?
Solution: Option C is the correct answer. Option A is wrong because the Top Secret classification causes grave damage, and it does not fit the statement given. Option B is wrong because the “Secret” data classification, when disclosed, causes “serious damage,” but the data is on the cloud and the secrecy is taken care of by cloud provider. The cloud is also accessed separately from the machine. Option D is wrong in that there is no such known classification in the US government.
Review Questions
- 1.What is the FIRST step in data/information classification process?
- A)
Decide what data needs classification
- B)
Decide who the data owner will be
- C)
Define the classification levels required
- D)
Define the procedures to classify data
Answer: Option C
- A)
- 2.Who is the BEST person to be in charge of the data and its classification?
- A)
The information security officer (ISO)
- B)
The data or information owner (DIO)
- C)
The chief security office (CSO)
- D)
All employees of the information security department
Answer: Option B
- A)
- 3.
Is it possible for an asset to fall into two overriding classification levels?
Answer: No. Each asset should have only one classification level. If an asset fits two levels, the highest level is usually chosen.
- 4.How information is usually classified?
- A)
On sensitivity
- B)
On criticality
- C)
Both A and B
- D)
Neither A nor B
Answer: Option C
- A)
- 5.What type of data is the classification level that is attached to data/information?
- A)
Unclassified data
- B)
Meta data
- C)
Secret data
- D)
Sensitive data
Answer: Option B is correct. The data classification level attached to the data/information item is metadata. The other options are classification level definitions.
- A)
- 6.For data classified as “public,” what type of auditing is required?
- A)
Private and special auditing
- B)
Public special auditing
- C)
Sensitive but unclassified special auditing
- D)
No special auditing required
Answer: Option D
- A)
- 7.A computer purchased by the government comes with a user manual. If the computer is classified as a Top Secret asset for the data it stores, the user manual must be classified as?
- A)
Top Secret
- B)
Secret
- C)
Confidential
- D)
Unclassified
Answer: Option D. Simple computer user manuals are always given the unclassified label. Computers may carry digital data with a Top Secret level, but the generic usual manual about how to operate the computer is an unclassified item.
- A)
- 8.A private organization starting to classify its data and information is conducting a meeting in which the data owner proposes to have only three classification levels at BEST and would even prefer two classification levels. Is this acceptable?
- A)
No, data classification must have at least four levels.
- B)
Yes, private organizations can have their own levels of classification.
- C)
No, data classification must follow state/federal rules.
- D)
Yes, but data owner must also consult with other companies.
Answer: Option B
- A)
- 9.
A doctor’s office stores patients’ medical records in digital form only. What classification level is MOST appropriate for these records?
Answer: Private data classification fits the medical records.
- 10.Data classification rules apply to what form of data?
- A)
Digital data and paper data
- B)
Digital, paper, video, fax, phone, disks, and all data
- C)
Only soft and hard copies of data
- D)
All formats of data except paper data
Answer: Option B. Classification must apply to EVERY FORM of data.
- A)
Data and System Ownership
Tip #13: Understanding roles in data classification and data management
Differentiate clearly between who classifies data and who implements the business rules, custody, transport, and storage. Other important words are data warehouse, data mart, and data roles used in day-to-day business.
Domain: Asset Security.
Subdomain: Database security, Data roles, Data ownership, Custodians.
Subject background: Data security is paramount, and each stakeholder associated with data needs to have a different and minimally required permission to protect it while handling. Any data leaks will finally have an adverse reaction on the functioning of an organization since 1) data leaks are difficult to detect, 2) data leaks can be internal or external, and 3) there can be natural disasters and unforeseen circumstances that may cause data leaks. Some NIST documents describe data roles and the duty of each role in protecting the data.
Things to Remember
Data Owner: Usually the boss of the organization is called the data owner. The eventual responsibility of the data remains with the data owner, despite the fact that many stakeholders handle the data. Data owners classify data and decide how to handle it.
Data Custodian: They handle data in the day-to-day operations. Data custodians implement rules that are framed by data owners. They protect, store, back up, and retrieve data in the proper format as required by the rules set by the data owners.
System Owner: System owners are people who own the system that processes the data. System owners have to design and guard the security of a system that handles the data. System owners can be typically the same as data owners but can be different too.
Business Owner: These people own business processes. Processes are conducted on the systems and are guarded by system owners. They can be group project managers below the CEO or another C-level manager.
Data Processor: A data processor is a system or a person who processes the data, per the privileges assigned to them.
Data Controller: This is a person or an entity that controls the data. Anyone who is collecting data and passing it around is a controller. How the controlled data is processed is the job of data processor described earlier. Safe Harbor deals with both the data processor and data controller.
Administrators: These are a group of people who decide what data should go to certain people. In other words, they grant permissions on data to the users. Administrators assign privileges to users.
Users: These are end users who utilize the data to complete a task given to them.
Remember that these roles are given to people depending on their “need to know” and their privilege level, with “least privilege” as the norm. Also, the privileges can be escalated or removed as and when people move around in, join, or leave an organization.
Datamart: This is used for a single application or a single department.
Data warehouse: This houses various applications’ data (enterprise-wide depth for data).
- A)
The data owner or the CEO
- B)
The data administrators
- C)
The data custodian
- D)
The data processors who actually classify and process the data
Analysis: Reading the question, it is easy to see that there are several distractors in the question itself. The names of custodians, administrators, controllers, and processors are put in the question to inform the test taker to divert attention. In fact, once the words “data classification” appear in a question, the test taker should immediately remember that the question is directly linked with a “data owner.” It is possible for the question to also ask about other roles of the data, but classification basically is the job of the data owner or the CEO. Remember that the CEO can assign this classification job to another C-level manager (such as a CIO, COO), but the CEO has the ultimate responsibility for breach of data since the CEO remains the owner of the data and decides the classification levels.
Statement: The auditor found the wrong classification of data on various systems. Who should the auditor address the problems encountered during the audit about data classification levels?
Question: Removing the verbiage, we can easily deduce the following cryptic question and quickly find the answer to the question:
Who should the auditor address about data classification levels?
Solution: Data classification is the job of data owner. Whether the data owner is a CEO or another C-level manager, it does not matter. Therefore, the answer is option A.
Data administrators set up passwords, privileges, and controls on the data but do not classify the data. Data custodians follow orders of the data owners and do the daily backup and take care of the day-to-day duties of the data. Data processors only can process data given to them and cannot classify it. Ultimately, it is the CEO who will be held responsible for the data classification and the discrepancies in the audit because the CEO owns the data.
Review Questions
- 1.Who classifies data in an organization? (Or, who is responsible for various classification levels assigned to data in an organization?)
- A)
Data custodian
- B)
Data owner
- C)
System owners
- D)
System controller
Answer: Option B. The data owner assigns classification to data.
- A)
- 2.A new user joining in an organization is given privileges to handle data. Who assigns privileges to the user, and how does the user track the data use?
- A)
The administrator gives privileges and tracks users via audit logs.
- B)
The data owner gives privileges and asks the custodian to track the user.
- C)
The data custodian gives privileges and asks the system owner to track the user.
- D)
The data controller gives privileges and asks the data owner to track the user.
Answer: Option A
- A)
- 3.Who is responsible for the day-to-day storage, backup, and retrieval of data in an organization?
- A)
The day-to-day data processor
- B)
The retrieve and backup programmer
- C)
The data custodian
- D)
The data administrator
Answer: Option C. A data custodian will be the person responsible for the day-to-day handling of data.
- A)
- 4.What is the difference between a data warehouse and data mart?
- A)
The data warehouse is for a single application, but the data mart is for several applications.
- B)
The data warehouse is for many applications, but the data mart is for a single application.
- C)
The data warehouse is the externally funded and provided entity.
- D)
The data mart is an internally housed entity.
Answer: Option B.
- A)
Tip #14: Know the rules and regulations that govern the United States, European Union, and overseas data sharing
Remember the details of Safe Harbor and the GDPR.
Domain: Security and Risk Management.
Subdomain: Security, Overseas data sharing, US and EU data sharing regulations and protection, etc., Data and system ownership.
Subject background: Like the United States has data privacy rules, the European Union has its own privacy laws. Simply stated, Safe Harbor is a paradigm or concept on how US-based companies can comply with the EU privacy laws. In other words, Safe Harbor principles state how a non-European entity or company can comply with a European entity about the privacy of data (belonging to EU citizens, companies, etc.). As of May 2018, Safe Harbor has been replaced by the General Data Protection Regulation (GDPR). GDPR is the most important regulation in data protection in the past 20 years.
Safe Harbor has a set of seven principles: notice, choice, onward transfer, security, data integrity, access, and enforcement.
Safe Harbor basically is an agreement between the US Department of Commerce and the European Union to export and handle the PII of European citizens.
Safe Harbor compliance is a way of building trust.
EU data protection laws allow the PII of EU citizens to be shared if the receiving country can adequately guarantee the PII data is well-protected.
Companies or entities must have a mechanism to safeguard the PII of EU citizens when it is transferred to and within the United States.
GDPR is a regulation and is NOT a directive. It is directly binding and applicable and does not provide flexibility for some aspects to be adjusted for anyone.
In some cases, violators of GDPR can be fined up to 20 million Euros or 4% of the annual worldwide turnover of the preceding financial year.
Under the GDPR, public authorities and businesses whose core activities consist of processing personal data or PII are required to employ a data protection officer (DPO).
- A)
Employ Safe Harbor or GDPR directives
- B)
Implement GDPR regulations and employ a data protection officer (DPO)
- C)
Employ a data protection officer (DPO) but do not implement Safe Harbor/GDPR
- D)
Employ Safe Harbor directives but do not hire a data protection officer (DPO)
Analysis: Any company with a website has to know that the website is accessible from all over the world. Any data collected from EU citizens has to follow the Safe Harbor and GDPR regulations. Even if the data collected is only a small amount of PII, the GDPR rules still apply. This is the main reason why a small pop-up keeps appearing on websites telling the users that the website may store cookies that may contain some personal information of the user, such as the computer location, browsing habits, etc.
Statement: The question's verbiage can be shortened as follows:
A social engineering website that stores the username and passwords, location of the person (resident country and the city), the user’s job, tastes in food, and occasionally personal hobbies was recently reported to the EU that the user’s PII is not well-protected by the site. The company’s legal team argued that the company did not break any laws of Safe Harbor or GDPR.
Question: A social engineering website was recently reported to the European Union that the user’s PII is not well-protected. Is the company violating any laws of PII?
Solution: The simplest answer is yes since any information collected from the user can directly or indirectly lead to the user’s other data, which can ultimately pave the way for finding more information about the user. Option A is wrong since the GDPR is not a directive but a regulation. Option C is wrong because employing a DPO alone is not the solution. Option D is wrong for the same reason since both a DPO and data protection are important. Option B, therefore, is the correct answer.
Review Questions
- 1.What is the full form of the GDPR, which deals with the European Union’s data privacy?
- A)
General Data Privacy Rules
- B)
General Data Protection Regulation
- C)
General Data Privacy Regulation
- D)
General Data Protection Rules
Answer: Option B
- A)
- 2.What is the maximum amount of fine the GDPR can impose?
- A)
A flat fine of 30 million euros
- B)
25 million euros or 5% of the worldwide turnover of the current year
- C)
20 million euros or 4% of the worldwide turnover of the preceding year
- D)
20 million euros or 5% of the worldwide turnover of the current year
Answer: Option C
- A)
- 3.Corporations and public entities dealing with the processing of personal data are supposed to employ or implement who/what?
- A)
Data privacy officer
- B)
Data privacy software and data privacy ownership
- C)
Data ownership and data privacy
- D)
Data protection, privacy, and ownership
Answer: Option A
- A)
- 4.
The GDPR applies within what geographic area?
Answer: It is a regulation within the European Union.
- 5.
How many principles does the Safe Harbor have?
Answer: It has seven principles: notice, choice, onward transfer, security, data integrity, access, and enforcement.
- 6.Safe Harbor is an agreement between what two entities?
- A)
Federation of all US public trading corporations and the European Union
- B)
US Department of Commerce and the European Union
- C)
US Consortium of Internet Companies and the entire Europe continent
- D)
Government of the United States and the European Union
Answer: Option B
- A)
- 7.
How does an entity join the Safe Harbor?
Answer: It is a voluntary process but must comply with requirements and publicly declare as such. The entities also self-certify annually to the US Department of Commerce in writing that the entity agrees and complies with the Safe Harbor requirements.
Protecting Privacy
Tip #15: Know the newly introduced privacy laws of the European Union, European Economic Area, and the related GDPR
General Data Protection Regulation (GDPR) , is a new regulation aimed at protecting the privacy for all individuals under European Union and European Economic Area (EEA). Failure to follow the regulation can have very adverse effect in the form of fines.
Domain: Asset Security, Security Engineering, and Security Operations.
Subdomain: Protecting privacy, Privacy concerns and limitation of use, Data retention, Handling requirements, Protect data in transit, Resource protection techniques.
Subject background: Data protection and privacy for all individuals in the European Union was implemented via the GDPR in May 2018. The GDPR also addresses exporting data from/to the EU and EEA. It basically states that those who control the personally identifiable information (PII) must implement appropriate technical and organizational measures to implement data protection principles. Business processes should implement pseudonymization and anonymization to protect the PII when and where appropriate.
Data processors must clearly indicate how they data is collected, used, and stored. Subjects can request a copy of the data collected by the businesses. Businesses must report data breaches within 72 hours if the breach had any effect on the PII or privacy. Public authorities and core businesses must employ a data protection officer (DPO) .
Things to Remember
The GDPR is a regulation, not a directive. It is directly binding and applicable.
The GDPR consists of 99 articles grouped into 11 chapters.
The GDPR applies if the data controller/processor/subject is in the EU and in some cases outside the EU.
The GDPR does not apply to personal/household activity that has no connection to the professional or commercial processing of data.
The GDPR does not also cover deceased persons, scientific or statistical analysis, lawful interception, national security, military, police, or justice departments.
The right of access (article 15) is a right of the data subject.
The term “data” includes data provided by the subject and the data observed (such as behavior, physical traits, etc.).
Data that is adequately anonymized is excluded from the GDPR regulation.
The GDPR requires that the pseudonymized data and any information used to anonymize or pseudonymize the data should be kept separate from each other.
Data processors must ensure that PII is not processed unless necessary for a specific process or implementation.
Data protection under the GDPR is by design and default. This means privacy settings are always set to the highest level by default.
Data subjects must be informed of their rights on how their data will be used or transferred to a third party if a transfer is required for a business process.
- Data subjects have the right to the following:
- a.
View their PII/access an overview of the PII
- b.
See/request how it is being processed
- c.
Obtain a copy of the stored data
- d.
Erase data under certain circumstances
- e.
Contest the process used by the business
- f.
File a complaint with a data protection authority (DPA)
- a.
Informed consent is used for lawful data processing. Consent must be specific and freely given and with unambiguous words written in plain, simple, and understandable language.
Data subjects have the right to withdraw consent at any time. This opt-out process must not be harder than the process they originally opted in.
- A)
Sue the European Union (EU) for misuse of subject data
- B)
File a complaint with the European Economic Area (EEA)
- C)
Opt in to share data on a particular date and opt out on another date
- D)
Consent only when the subject provides data to a business for the first time
Analysis: Reading the question, it becomes clear that it is asking about GDPR and the rights of a subject under the GDPR regulations. EU and EEA formulated the rules, but it is businesses that have to take care of implementing the GDPR. So, the first sentence of the question is generally a superfluous statement.
Statement: Data protection and privacy for all individuals in the European Union (EU) addresses exporting of data from/to the EU and EEA.
Question: Under the GDPR, which of the following is one of the rights of data subject?
Solution: Clearly, option C is a better fit than rest of the answers given. The EU and EEA are law makers and political bodies that make the laws. One cannot and do not sue those since these organizations do not handle the data. A subject’s data is handled by a business (for example, a credit card company), which has to give option of opt-in and opt-out to a subject. Importantly, opt-in and opt-out are the rights of a subject, and a subject can choose when to opt in and when to opt out at their discretion. Thus, options A and B are wrong. Option D is wrong because consent can be given at any time and taken away at any other time as well, not just at first time. But a subject can always opt in and opt out.
Review Questions
- 1.Under the GDPR, responsibility and accountability to protect data lies with whom?
- A)
Data controller (DC)
- B)
Data subject (DS)
- C)
Data object (DO)
- D)
Data protection agency (DPA)
Answer: Option A
- A)
- 2.Under the GDPR, businesses have to protect the subject data by:
- A)
Business laws of the European Union (EU)
- B)
Design and default
- C)
Data subject’s consent
- D)
Signing a service level agreement (SLA) with the subject
Answer: Option B
- A)
- 3.When implementing the GDPR, what is the BEST way for an organization anonymizing or pseudonymizing with an encryption key to store data?
- A)
Store anonymized/pseudonymized data and the key together in the same location
- B)
Store anonymized/pseudonymized on-site and the key off-site
- C)
Keep anonymized/pseudonymized and the key on a single RAID 0 type disk
- D)
Keep anonymized/pseudonymized on RAID 0 disk, but do not keep the key at all
Answer: Option B
- A)
- 4.What law or ordinance replaced the Safe Harbor law?
- A)
General Data Provision Rulebooks (GDPR)
- B)
General Document Protection Reviews (GDPR)
- C)
General Data Protection Regulation (GDPR)
- D)
General Document Protection Rules (GDPR)
Answer: Option C
- A)
- 5.The term “data” under the GDPR can be BEST referred to as
- A)
Data provided by the subject and the data collected as observed
- B)
Data provided by the subject only after proper consent
- C)
Data consented by the subject and transferred in and out of EU/EEA only
- D)
Data consented to a business doing business only outside EU/EEA
Answer: Option A
- A)
Tip #16: Remember various levels of protection and the ring structure
Remember the protection rings 0, 1, 2, and 3 and where they operate, what they contain, and what they envelope for IT systems that may include mainframe systems or desktop stand-alone systems.
Domain: Security Engineering, Asset Security.
Subdomain: Trusted processes, CPU and IT system security, Protecting privacy.
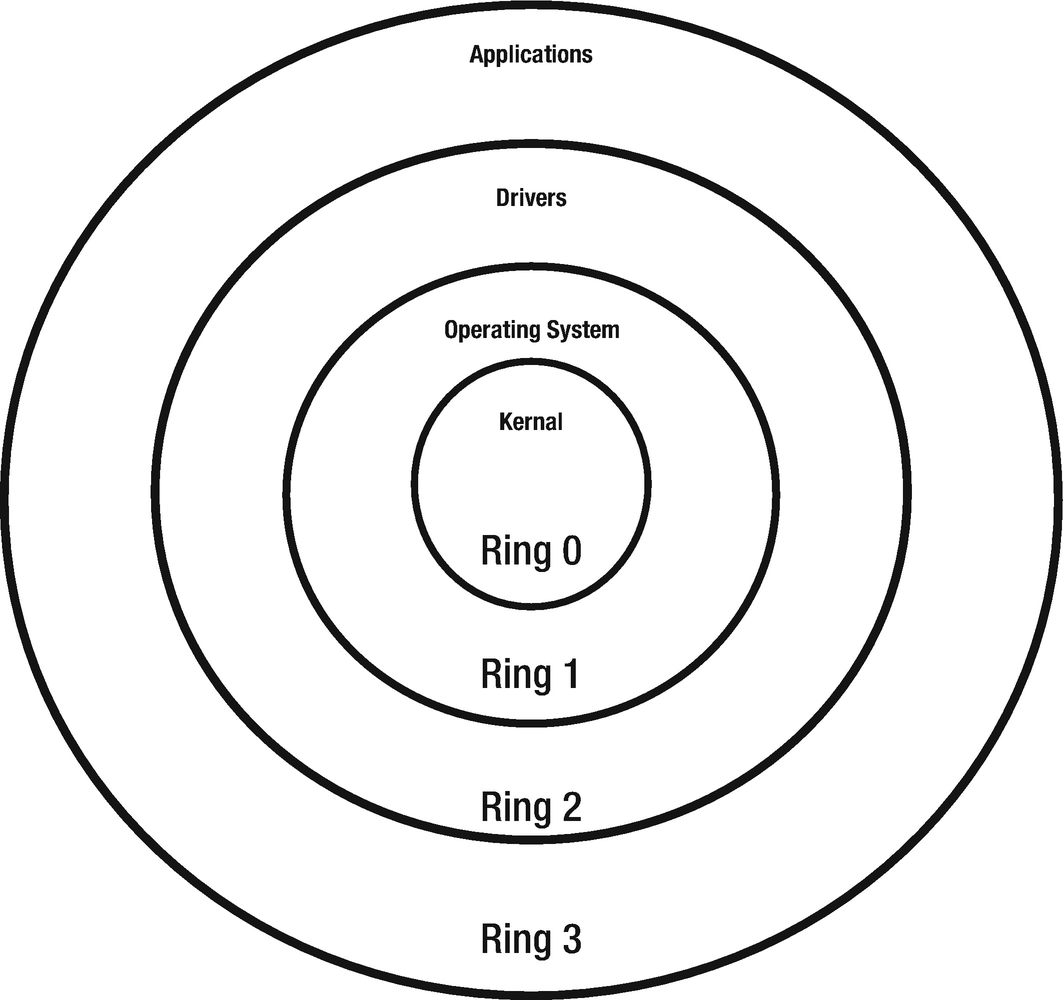
Protection rings
Things to Remember
The protection rings 0 to 3 and what they contain can be remembered with the acronym KODA as follows:
Ring 0 – Kernel (K): Contains the lowest and safest levels of keepings things protected. This includes kernel or the bare-bones file system that keeps the IT system up and running. But the kernel alone cannot contain everything and needs other items to be built around it for a normal user to work and operate.
Ring 1 – Operating system (O): This level is a step above the kernel where somewhat expert users can operate and do restricted work. Disk formatting, file allocation, and permissions go in this ring and help other users.
Ring 2 – Drivers (D): This level stores the device drivers, like the driver files for various applications, hardware, and how they interact with the operating system. Depending on the operating system, the drivers change as well.
Ring 3 – Applications (A): Databases and applications like Microsoft Word, Excel, etc., go in this level. This level is most accessible to a general user, and there is not much protection offered. This is the area where you let users log in and do generic work like checking email or browsing a website to check the daily news.
For rings 0 to 3, the protection goes from most secure (ring 0) to least secure (ring 3).
Simply because ring 0 is the most secure protection level does not mean everything can be stored at that level.
- A)
Ring 3 – Application level
- B)
Ring 2 – Device driver level
- C)
Ring 0 – Kernel level
- D)
Ring 1 – Operating system level
Analysis: We can easily deduce that the situation in the question refers to a DBA accessing the database at the operating system level.
Statement: A lot of verbiage can be removed from the question since most of it is a description of how the DBA is accessing the database and at what level. It can be read as follows:
The database administrator (DBA) can go to the operating system’s command-line interface (CLI) and operate the database securely.
Obviously, the DBA is not accessing the DB at the kernel level or at the device driver level. Thus, options B and C are wrong. The DBA can access the database at ring 3, which is the application level, but note that the question says the DBA is working at the CLI, which falls at the operating system level. So we can easily remove the distractors and come to a conclusion about the correct answer.
Question: If the DBA operates at the command-line interpreter (CLI), what level or protections rings does he access?
Solution: The command-level interpreter (CLI) is the operating system level where a user can access operating system commands over the kernel. This level is not available to all, and if available, it is restricted with limited permissions. Thus, the correct answer is option D.
Review Questions
- 1.What are the correct protection levels in the order of MOST secured to LEAST secured?
- A)
Ring 0, 1, 2, and 3
- B)
Ring 2, 1, and 0
- C)
Ring 3, 2, 1, and 0
- D)
Rings 0, 1, and 2
Answer: Option A
- A)
- 2.At which protection ring layer do the MOST trusted processes operate?
- A)
At the highest-numbered ring level
- B)
At the ring level where device drivers work
- C)
At the lowest-numbered ring level
- D)
At ring levels 3 and 4 only
Answer: Option C. Option D is a clear distractor since there is no protection ring 4.
- A)
- 3.
A network interface card (NIC) is being installed on a computer with the Windows operating system. The NIC comes with a CD that has the driver files. When the NIC is correctly installed, at what protection ring level do the NIC’s driver files reside?
Answer: Driver files always are in ring 2, above the operating system level since the drivers are for that operating system.
- 4.
From an IT system owner’s perspective, who should be allowed to operate at protection ring level 0?
Answer: Only the most trusted people since ring 0 is the most secure level.
- 5.
What is the purpose of layering the IT system into protection levels 0 to 3?
Answer: Layered protection provides a secure self-defense mechanism of an IT system and the operating system.
- 6.
At what level does a user need the MOST privileges for an IT system?
Answer: At the ring 0 protection level since it is the most secure level
Memory Management
Tip #17: Learn to remember the types of disk storage and their mechanisms
Understand different RAID types and their uses.
Domain: Security Operations, Software Security, Network Security.
Subdomain: Memory management, Asset security, Data and system ownership.
Subject background: Redundant Array or Independent Disks (RAID) is a concept for providing memory sufficiently and without fail for IT systems so that the systems align with the security concept of continuous availability. These RAID disks are designed and provided for an IT system to make sure that the asset (whether it is a database, a running program, or a backup) is available without fail. For RAID, a series of physical disks are provided to make sure that the IT system is available continuously. The disks may be placed in the same physical location or dispersed over an area, but the IT system and the user would not know the difference. For a user, whatever level of RAID is used, it will appear as a single disk. When using RAID, data can be written on a single disk, two disks, or several disks with some data on each disk. The front-end user, though, will never know where the data is exactly stored. The front-end user cannot also decide where the data must be stored. It is not even necessary for the user to know how to optimize the disk storage. In other words, how RAID is designed and maintained is a background process a front end user should never have to worry about.
RAID disks are general-purpose simple hard disk drives.
RAID levels and associated data formats are standardized by the Storage Networking Industry Association (SNIA).
RAID networks do NOT provide recovery of data under catastrophes such as fire, flood etc.
RAID provides availability but cannot replace the backup process. Backup is a separate process to save the data of the IT systems.
Parity is a term used for error checks. Parity data is generated for error checks and is added to the original data when transmitting or storing data.
Striping is a process of splitting data evenly or unevenly. Disks can be split evenly to store data or to make drives.
Fault tolerance is a quality of the drive/IT system in which the drive or system will continue to operate normally under a failure.
RAID is generally used where a single point of failure can cause unrecoverable data loss.
RAID levels can be combined to make them as RAID 10 (1+0) or RAID 60 (6+0), etc.
The most commonly used RAID level is RAID 5.
Redundant array of independent tapes (RAIT) uses tapes instead of disks.
A MAID is a massive array of inactive disks that store large to very large data in the order of several terabytes or more.
RAID uses general disks (magnetic) and thus can be said to be a direct access storage device (DASD).
Levels of RAID
Level | Details | Minimum Disks |
|---|---|---|
0 | Block-level striping without parity or mirroring. If one disk fails, all the data may not be available. | 2 |
1 | Mirroring without parity or striping. Data is written independently to two drives. If one fails, the other may be able to provide the required data. | 2 |
2 | Bit-level striping with Hamming code parity for error correction. Currently this is no longer used. | 3 |
3 | Byte-level striping with dedicated parity. Data is striped, but parity data is held on a separate drive. If the actual data fails, it might be reconstructed with parity. | 3 |
4 | Block-level striping with dedicated parity. This is similar to level 3, but parity is now at the block level instead of the byte level. | 3 |
5 | Block-level striping with distributed parity. Data is written to several disks, and parity is also written to all disks. It helps to make sure that there is no single point failure since parity data is available on several disks. | 3 |
6 | Block-level striping with double distributed parity. This is similar to level 5, but parity data is written TWICE to drives. | 4 |
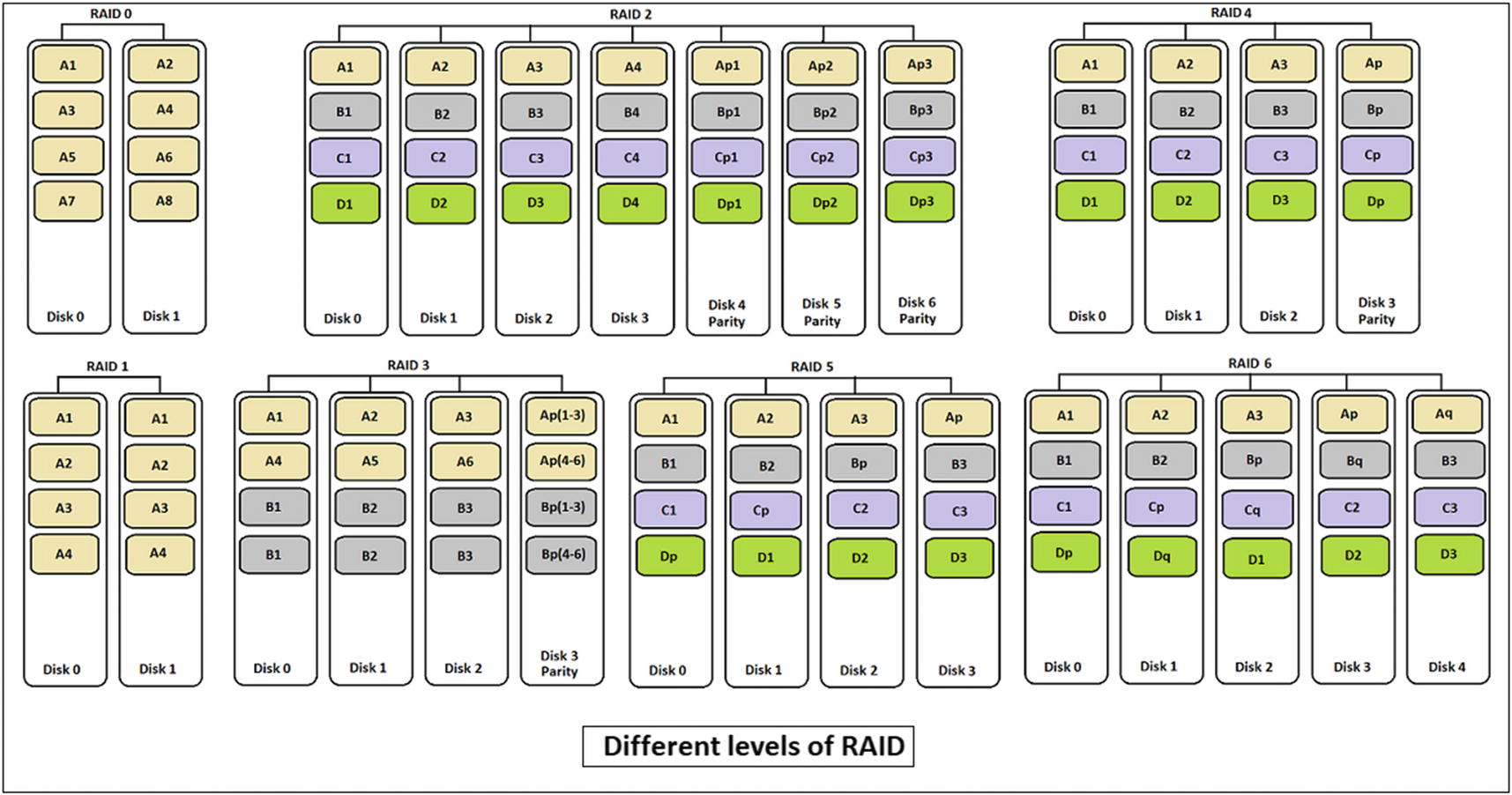
Different levels of RAID
- A)
No additional cost to pay and no additional advantage
- B)
No additional cost to pay but has a second parity data storage advantage
- C)
One additional disk cost to pay and has a second parity data storage advantage
- D)
One additional disk cost to pay and no additional advantage
Analysis: Reading the question, it may appear challenging, but in reality it is a simple statement of what the organization has decided to do. The organization has decided to pick RAID 6 as their choice over RAID 5. All we need to know now are the advantages of RAID 6 over RAID 5 and if there is an additional disk cost involved.
Statement: Notice that when we read the verbiage, it becomes clear that none of the first few sentences was required to ask the actual question. All the question asks is the advantage of RAID 6 over RAID 5.
Question: Which of the following options BEST describes the additional price the organization has to pay for the RAID 6 over RAID 5, and what advantage will the organization get for selecting RAID 6?
Solution: From Table 2-3, we note that RAID 6 uses parity data twice in two different disks. Thus, to store a second parity, we need an additional disk. Other than the second parity block, RAID 5 and RAID 6 are essentially the same. The advantage of adding a second parity is that if the first parity block data is corrupted or lost, we will still be able to recover data from the second parity block. Option D is obviously wrong since we will not buy an additional disk without getting any advantage from it. Likewise, option A is wrong since RAID 5 and RAID 6 do differ. Option B is slightly tricky since we do not have an additional disk, and it may be possible to create a partition on existing disk for second parity. But the question, like most of the CISSP questions, is asking for the BEST answer from the given four choices.
Thus, the correct answer is option C.
Review Questions
- 1.What RAID level uses block-level striping with parity data written twice?
- A)
RAID 2
- B)
RAID 11
- C)
RAID 60
- D)
RAID 6
Answer: Option D
- A)
- 2.
What is the exact purpose of parity in storing data in RAID level 3?
Answer: Parity is used for error check.
- 3.Which of the following RAID levels uses hamming code parity?
- A)
RAID level 60
- B)
RAID level 6
- C)
RAID level 2
- D)
RAID level 1
Answer: Option C
- A)
- 4.Which RAID level uses a minimum of two disks and has no mirroring or parity associated with it?
- A)
RAID 10
- B)
RAID 11
- C)
RAID 1
- D)
RAID 0
Answer: Option D
- A)
- 5.Which of the following BEST describes RAID?
- A)
Reduced and accomplished independent disks
- B)
Redundant array of independent disks
- C)
Redundant array of inexpensive disks
- D)
Reduced array of inexpensive disks
Answer: Option B
- A)
- 6.
Which successive levels of RAID that improve over the earlier ones have the same type of block-level striping?
Answer: Level 4, level 5, and level 6. Note that level 0 uses block-level striping, but the successive levels (levels 1, 2) do not.
- 7.
Which is the only level of RAID that uses bit-level striping?
Answer: Level 2
- 8.
What disks are used for creating a RAID?
Answer: RAID disks are general-purpose simple hard disk drives.
- 9.Who decides the standards of RAID levels and associated data formats?
- A)
They are standardized by the in-house database manager.
- B)
They are standardized by the Storage Networking Industry Association.
- C)
They are standardized by storage area networking standards.
- D)
They are standardized by hardware and networking vendors.
Answer: Option B
- A)
- 10.
RAID networks do NOT provide recovery of data under which circumstances?
Answer: Catastrophes such as fire, flood, etc.
- 11.
Which part of the CIA security triangle concept/objective does RAID adhere to?
Answer: The security objective is availability.
- 12.Which of the following BEST describes fault tolerance?
- A)
It is a quality of the drive/IT system in which the drive or system will continue to operate normally under a failure.
- B)
In the case of corrupted data, fault tolerance provides a clean backup copy.
- C)
If data is entered with errors, it corrects data automatically.
- D)
If data is saved in two or more disks, fault tolerance can automatically combine data and supply it to the user effortlessly.
Answer: Option A
- A)
- 13.What is the difference between RAID and RAIT?
- A)
RAID uses data, and RAIT uses the timing of the IT systems.
- B)
RAID uses databases, and RAIT uses tracks on disk.
- C)
RAID uses disks, and RAIT uses tapes.
- D)
RAID uses disks, but RAIT is not related to IT systems.
Answer: Option C
- A)
- 14.Which of the following BEST matches the definition of MAID?
- A)
Massive array of inactive disks
- B)
Massive array of independent disks
- C)
Managed array of inactive disks
- D)
Managed array of independent disks
Answer: Option A
- A)
Tip #18: Understand different types of computer memory addressing schemes (machine level)
Different types of memory addressing schemes such as direct, base, indexed, etc., make memory access easy when doing programming at machine level. The addressing schemes allow accessing the memory directly or with an indirect method without knowing the data stored at a location. These addressing schemes are useful at machine level coding and at processor level.
Domain: Security and Risk Management, Asset Security, Security Engineering.
Subdomain: Memory protection, Types of addressing in memory.
Subject background: Machine-level and assembly-level languages use the format of “opcode {operand} {operand}….{operand}” to run instructions. These operands can be registers, memory locations, data, or anything the assembly language can allow. When data is being read from or loaded into the memory, it can be addressed in a variety of ways. These ways are called addressing modes/schemes of the memory.
Things to Remember
Immediate addressing usually has the letter “I” in the opcode. It looks for the data in the operand, as in MVI C 40x. Here the instruction is to “move data immediately into register C.” And the data to move into the register C is 40 hexadecimal. Since the data is immediately following the instruction/opcode, this is called immediate addressing.
Let’s consider now that the data 40x is in another memory location, say at the “4389 7623” address. This is the address of the memory where our data 40x is stored. To load this data into a register, we use an instruction like “MOV C, “memory address” or in this case “MOV C, [4389 7623].” So the data 40x stored at the location specified [4389 7623] will be moved to register C. Since we are indirectly giving the data location (rather than the data itself), this called indirect addressing . Moving data from a location into the register is sometimes called register indirect addressing. If a memory location is used instead of a register, then it is simple indirect addressing.
Offset addressing is where an offset value is added to the existing address. The resulting address is from where data will be obtained. An example is illustrated here:
MVI reg1 “4389 7623” means move the address 4389 7623 into register1.
MV reg2 reg1 34 means add 34 offset to the address in reg1 and move the data from the resulting address into register 2. This means we get data from location “4389 7657” (which is 4389 7623 + 34) into register 2. Also note that in this example the first instruction is immediate addressing and the second instruction is offset addressing. This is sometimes also called displacement or relative addressing.
Register direct addressing is when the contents of one register are added/modified/loaded to another. We do not know the contents of either register, but when we want to add those contents, we use register addressing. An example is ADD B, C. The contents of register C are added to register B.
Indexed addressing happens when an address is specified relative to an address that is in an index register. The index register basically contains the base address, and any offset is added to the index to fetch data from the resulting (index + off set) address. An example instruction looks like this:
MOV Reg1, [Reg2+Reg3]
Reg 2 usually has the fixed base address. Reg 3 has the offset. Thus, by giving the offset value only, we can move the data from the resulting address to register 1. This is useful when arrays are used. Let’s assume we have an array with 100 elements and we know the starting address of the array (base address). When we want to move the 79th array element, what we can do is give the instruction as MOV reg1, [reg2+79]. Since reg2 already contains the base address (whatever it is), the data from the resulting address of [base address plus 79 offset] will be moved to register 1.
Auto-increment addressing happens when data is moved/added from one location to another and the second location is incremented “after” the data is moved/added/modified otherwise. The following example illustrates the process:
MOV reg1, [reg2]+d
The content of register 2 is an address. That address holds some data (say 40x). The data 40x is moved into register 1, and after the move, the contents of the address are incremented by one (default) or a value specified (d). If a value is not specified, the default is 1.
Auto-decrement addressing is similar to auto-increment except that the data is decremented before the data is moved/added/modified otherwise. An example is MOV reg1, [reg2]-d.
Note that both auto-increment and auto-decrement can be used before and after, as follows:
MOV reg1, +[reg2]+d means increment the value AFTER moving.
MOV reg1, -[reg2]-d means decrement BEFORE moving. Notice that the placement of + or – before or after the operand to decide whether increment or decrement happens before or after.
Note that when we execute an instruction “ADD R1, R2” the movement of data is always from right to the left. It means contents of register R2 are added to contents of register R1. This results in changes to contents of R1. But contents of R2 will remain the same after the instruction is executed.
- A)
MOV reg1, [reg2+d(32)]
- B)
MOV reg1, [reg2+reg3]
- C)
MOV reg1, [reg2+32]
- D)
MOV reg1, [48+47+32]
Analysis: Note that the verbiage is giving details of where the base address for the index and offset are stored. When all these are stored in registers, there is really no point in using any number or address locations directly. If we can remember that point, we can directly come to a conclusion and pick the correct answer.
Statement: The base index address of the array is in register 2. The value of the 32nd array member d(4*8) is required to be loaded into register 1 using offset 32 stored in register 3.
Question: With the base index address in register 2, if the value of the 32nd array member is required to be loaded into register 1 using offset 32 stored in register 3, what instruction correctly can do this using indexed addressing?
Solution: Note that the correct answer is option B. Options A, C, and D are wrong because they are using a value in the operand, but the verbiage states that the operands and offset are all stored in registers.
Review Questions
- 1.
Register 2 contains the address “4356 9878.” If the data in address [4356 9878] is 54, what will the data be after the following instruction is executed under auto-decrement addressing? Assume opcode ADD is used for addition.
ADD reg1, [reg2]-- A)
54
- B)
55
- C)
53
- D)
51
Answer: When no increment or decrement value is specified, the default is 1. Thus, the correct answer is option C.
- A)
- 2.
Hexadecimal data “3A4C” is moved to register 1 with the instruction “MOVE register1, 3040.” What addressing does the instruction follow?
Answer: When data is mentioned directly in the instruction, it is immediate addressing.
- 3.In the register addressing, the instruction “SUB R1, R2” was executed where “SUB” stands for subtract and R1 and R2 are register names. After the instruction execution, what data will the registers R1 and R2 contain? Assume {R1} or {R2} are contents of registers R1 or R2 and data movement is right to left.
- A)
R1 contains {R1}, and R2 contains {R1}-{R2}.
- B)
R1 contains {R1}-{R2}, and R2 contains {R2}.
- C)
R1 contains {R1}, and R2 contains {R2}+{R1}-{R2}.
- D)
R1 contains {R1}+{R2}-{R1}, and R2 contains {R2}.
Answer: Option B
- A)
Data Retention
Tip #19: Two options of choosing to stay in or stay out have a very subtle difference
Clearly understand the difference between opt-in and opt-out options.
Domains: Security Engineering and Asset Security.
Subdomains: Data retention, Data security controls, Data handling requirements, Security architectures, Designs, etc.
Subject background: It is a common practice for organizations to collect information from users when the user orders a product either via a website or in person. The data collected can be public or private, and depending on what is collected, the organization is responsible for handling the information collected. Several laws and regulations - either private or public, kick in once data is collected. These include but are not limited to state, federal, and the newly introduced European Union’s GDPR. While some organizations collect data before asking the consumers’ permission to use it, others collect data and assume they can use it by default unless otherwise the customer objects to its use. Opt-in is a way of a consumer to choose whether they want to allow the organization to use the data collected. In opt-in, an organization cannot use the data collected for any use without the consumer opting in. Opt-out is a way organizations assume the data collected from consumer is free to use unless the customer tells the organization that they no longer want the organization to use their data. In short, opt-in is consumer-driven, whereas opt-out is organization-driven.
Things to Remember
Opt-in and opt-out usually are encountered by the consumers while creating an account on a website or while filling forms at a retail store where the user has to either check a box or uncheck a box. In opt-in, the user has to physically check a box and give consent telling the organization that using his data for uses other than collected is OK. In opt-out, a user may have to 1) uncheck a box that was automatically checked by the company by default (the company assumes the consumer is OK with this), 2) send a personal email to the organization telling them to stop using the consumer’s data and stop the marketing blitz of their data and/or stop sending junk emails, or 3) go to the organization’s designated website and inform the organization to stop using data or unsubscribe. For opt-out, some organizations make it easy to get out, but others make it difficult by asking several questions, directing the user to a couple of websites and so on.
- A)
The user has opted in to other services provided by the website to get the free email account.
- B)
The user has opted out of the email service provided by the website to get the free email account.
- C)
The user cannot register for the email account because the checkbox is disabled.
- D)
The user may opt out later but has to register with the default opt-in to get the free email account.
Analysis: A checked box, whether enabled or disabled, is an indication of automatic opt-in. This means that the user is giving automatic permission for the company to share the information. If the box is disabled, it also means that the company will NOT provide email account to the user unless otherwise the opt-in is granted to the organization. That’s how the “Register” button is programmed to work. If the user does not want to give the automatic option, for this particular website, there may not be any other way to provide free email service. The option that “may” work later is to call the company or email them to indicate that the user is opting out. That may take several days. In this case, the button indicates that the user must opt-in and may opt-out later in other ways.
Statement: While registering for a free email account, a user is required to enter a username; password (twice); and personal information such as age, date of birth, and gender. Before clicking the “Register” button at the bottom of the page, the user notices a checkbox that is automatically checked and disabled.
Question: What does the checked and disabled box MOST appropriately indicate to the user, directly or otherwise?
Solution: The answer is option D. Option A is not correct since the user did not purposefully check the opt-in box. Option B is not correct because the user did not send an email or uncheck a box. Option C is not correct too since one can register for email with the checkbox showing as checked and disabled. Note the wording in the question “MOST appropriately.” There could be more than one correct answer, but the test taker has to pick the most accurate answer.
Review Questions
- 1.
If the “Register” button is not enabled until the checkbox is checked, what does it mean?
Answer: In this case, the user is being forced to opt in to give free email access. Since there is no free lunch literally, the user has to opt in by checking the box, which will enable the Register button. This means, though, that the company has forced the user to check the box, and the user understands the risks of sharing their data with the company to get the free email account and access for email.
- 2.
A website selling prescription medicine does not show any checkbox for opt-in or opt-out but shows a lengthy document in PDF in a text box. Before registering the account to order prescription medicine, the user has to read the document and agree to it before clicking the Order button. What kind of permission is the user giving the website?
Answer: Once the document mentions (anywhere in the myriad of pages displayed in PDF) that the user agrees to the terms, it is an automatic opt-in.
- 3.
After registering for an account on the Internet, David gets daily email about the products the website sells. He also receives weekly emails and annual emails about the stock value of the organization and a report. In every email there is a line that says, “If you do not want any emails from us further, please click here to unsubscribe.” David clicks that link and goes to a website and unchecks “unsubscribe me from all emails and reports.” What did David do?
Answer: David opted out of the marketing and data sharing of the organization. He is opting out since he physically unchecked the box and has earlier already been on the mailing list. It is his option to stop all the email he has been receiving.
- 4.
While talking to his pastor at church, Ozzie Ozone learned that he can subscribe to a daily email that gives uplifting thoughts on God and religion. Ozzie signed up for the daily email on the church’s website and checked the box that said, “Yes, please send me daily email.” What did Ozzie pick?
Answer: Ozzie Ozone picked to opt in since he wanted the email about religion and God in his mailbox daily. If he did not want an email, he should have never ticked the checkbox. In a way, opt-in is the choice of user to join. Likewise, opt-out is his choice of getting out from a list.
Tip #20: Learn to distinguish various types of memories and their use in a computer
Understand different memory types such as SRAM, DRAM, EPROM, EEPROM, Flash HDD, CD-ROM, ROM, and RAM.
Domain: Asset Security, Security Engineering.
Subdomain: Data retention, Types of memory, Backup and restore, Common system components, Security vulnerabilities, Threats.
Subject background: Memory in the computer systems of any IT system can be of two types: volatile memory or permanent memory. Volatile memory is also called random access memory (RAM), which is accessible for read and write and works at high speeds. RAM works as storage for programs to run when the processor needs. Therefore, to run more programs, usually more RAM is necessary. But when the power goes out, all the data in RAM is erased, which is why it gets the name as volatile memory.
ROM or read-only memory is the other type of memory that can hold the data for a long time or permanently. DVDs and CD-ROMs are examples of ROM. They are written once but read many times. But small flash drives or thumb drives that can be written and read many times are also considered partly as ROMs since they can retain data for a longer time without having to refresh with an active power connection.
SRAM: This is “static” RAM. It is made of digital flip-flops, each of which stores bits of information (true or false/ 1 or 0). Since more circuitry is needed for flip-flops, typically the costs for SRAM are higher as storage increses.
DRAM: This is “dynamic” RAM. It consists of capacitors that store energy. Since the capacitors can “leak” and lose energy, to maintain the memory the DRAM needs power that refreshes it regularly. DRAM is cheaper than SRAM. The refresh process in DRAM is internal to the RAM and the processor.
PROM: This is programmable ROM. Data can be inserted into this kind of chip (or integrated circuit) once by a program and cannot be erased.
EPROM: This is erasable programmable ROM. This kind of memory chip has a window on top through which ultraviolet light can be passed to erase any data. It can also be programmed electrically. Note that exposing an EPROM chip to ultraviolet rays in a closed enclosure (a small unit similar to a microwave) erases the entire memory; there is no facility to erase only a part of the memory. Likewise, programming is done in its entirety to store data, not in parts.
EEPROM: These chips are electrically erasable, programmable memories. They are generally used in IT systems for the firmware that needs updating (cars, desktop computers, microcontroller, keyless systems, smart cards, etc.). The flash drives or the USB thumb drives also come with EEPROM.
CD-ROM/DVD/BluRay: These come both in writable form and in write-once-read-many-times forms. They can store large amount of data and are common to pass around for storage, backup, and restore.
HDD: Hard disk drives (HDDs) are more common in laptop and desktop computers that store the operating system, programs to be installed, and user data. They are cheap and come in gigabytes of memory. A typical 2.5” HDD can hold several gigabytes to terabytes of data.
TAPE: Tape backups and storage are considered sequential memories, since to get some data out of the tape, it has to run to a location sequentially from the current location, either in forward or backward motion. Tapes also can store large amounts of data and are used for backup and restore of the entire IT system infrastructure software.
SRAM and DRAM also come in a variety of other formats such as video RAM. They can be installed on the motherboard or in an extended slot reserved for memory, also known as memory slots.
Computer specifications usually list HDD, RAM, and a backup drive such as CD/DVD ROM when marketing a machine. Unless specifically stated, in such advertisements, memory invariably means it is RAM that is required to run the system.
Programs from hard disk are loaded into RAM to run by the processor, and the data the loaded program uses is also in another part of the hard disk.
- A)
Implement a large secondary hard disk to avoid any memory problems
- B)
Provide cheap and large flash memory sticks to each user as required
- C)
Use DRAM to update the memory of desktops and laptops
- D)
User SROM for laptops and DRAM for desktops
Analysis: Once the question talks about memory, anything related to hard disk, ROM, or flash is irrelevant since memory means it is RAM that is required to load the programs. Thus, the question is only asking what type of RAM the IT systems can be put with so the total price is economical to the company. Also note that there is no such thing as SROM mentioned in option D.
Statement: A company wants to update all its desktop computers with more memory. The cost to upgrade the memory is a factor, and the company wants reliable memory for an economical price.
Question: The company wants reliable memory for an economical price; what is the best solution the company can implement across all the desktop and laptop computers?
Solution: The straightaway answer is option C. Option A is wrong since hard disk is not what memory (asked in the question) stands for. Option B is wrong since flash memory is a backup type of device and not main RAM used in desktop or laptop computers. Option D is wrong because there is no such thing as SROM. DRAM is the best and cheapest solution for either desktop or laptop.
Review Questions
- 1.Which of the following is a write-once-read-many-times memory?
- A)
Partition memory (PM)
- B)
Read-only always memory (ROAM)
- C)
Random access memory
- D)
Digital video disk (DVD)
Answer: Option D
- A)
- 2.Which of the following is the BEST write-many-times-read-many-times memory with or without power supply being present?
- A)
Read-only memory (ROM)
- B)
Erasable programmable read-only memory (EPROM)
- C)
Random access memory (RAM)
- D)
Compact disk read-only memory (CD-ROM)
Answer: The BEST option is option B. Note that option C can be written to and read from many times, but if power is off, RAM has no data and loses everything. ROM and CD-ROM are typically “write once and read many times” types of memories.
- A)
- 3.
Why is flash memory usually flagged for high security?
Answer: Flash memory sticks and disks are too small (typically the size of a human thumbnail) and can carry very large capacity data. Thus, data theft and loss can be easier compared to other memories. It is always best to encrypt such memory sticks to protect the data.
- 4.
What type of memory is used for BIOS in a Windows operating system computer?
Answer: EEPROM is the usual version for BIOS. It allows writing updates to BIOS. It can be also flash memory that is not available for the user to modify.
Data Security Controls, Data Protection
Tip #21: Learn the intricacies of mathematical operators used for modulo and division in cryptography
Understand how the modulo (%) and division (/) operators work. These operators are extensively used in cryptography and in ciphers.
Domains: Asset Security, Security Engineering, Communications, and Network Security.
Subdomain: Data security controls, Cryptography.
Subject background: The modulo function is represented by MOD and sometimes also used in math with %. Substitution ciphers and running key ciphers use the modulo operator. Adding a 3 (or any other number) to shift a value and then obtaining the modulo of the resulting value is a common method. For the CISSP certification exam, it is necessary to know how the MOD function works and how cryptography uses the integer division.
Many programming languages use the / operator as an integer division unless the variables used in the division are decimal point variables called decimals or floating-point variables.
The modulo used on two variables X and Y is indicated as X%Y, and integer division used on those is indicated as X/Y.
Things to Remember
- When we say division (/), it is considered as integer division. This means there are no decimal places left over. For example, 12/7 is 1 (remainder 5 is discarded). Other examples are given here:
205/2 = 102
35/4 = 8
93/8 = 11
4/7 = 0
- Modulo gives the remainder of an integer division. For example, 12%7 is 5. Other examples are given here:
28%5 = 3 (divides 5 times with a remainder of 3)
42%7 = 0 (divides 6 times with a remainder of 0)
275%9 = 5 (divides 30 times with a remainder of 5)
3%5 = 3 (cannot divide; the remainder is 3)
In a modulo value, the remainder is always less than the divisor.
- A)
X – ( X/Y )
- B)
Y – ( X/Y )
- C)
( X/Y ) – ( Y/X )
- D)
X – ( ( X/Y ) * X )
Analysis: If we consider a couple of values for X and Y, we can easily find the solution for this question. The options we can choose for X and Y are X < Y, X > Y when the division is a perfect integer division with zero remainder. When X=Y, the modulo always evaluates obviously to zero.
Case 1: X > Y. Assume X = 13, Y = 3. For these values, the modulo evaluates as 13%3, which has a value of 1.
Option A evaluates as 13 – (13/3) = 13 – 4 = 11. Option B evaluates as 3 – (13/3) = 3 – 4 = -1. Option C evaluates as (13/3) – (3/13) = 4 – 0 = 4. Option D evaluates as 13 – ( (13/3)*3). Remember that the inner parentheses, 13/3, is an integer division that evaluates as 4. Thus, we have 13 – (4*3) = 13 – 12 = 1, and option D is correct when X > Y.
Case 2: X < Y. Assume X = 7, Y = 11. For these values, the modulo evaluates as 7%11 = 7.
If we check the options given, option A evaluates to 7 – (7/11) = 7 – 0 = 7; option B evaluates to 11 – (7/11) = 11 – 0 = 11; option C evaluates to (7/11) – (11/7) = 0 – 1 = -1; and option D evaluates to 7 – ( (7/11)*7 ). Since there is integer division inside the parentheses, we get the value as 7 – (0*7) = 7- 0 = 7. Both options A and D are correct answers for this instance.
Case 3: X and Y have a perfect division. Consider X = 125 and Y = 5. X/Y gives us 25, and X%Y evaluates as 0. Checking the options again, option A evaluates as 125 – (125/5) = 125 – 25 = 100. Option B evaluates as 5 – (125/5) = 5 – 25 = -20. Option C evaluates as (125/5) – (5/125) = 25 – 0 = 25. Option D evaluates as 125 – ( (125/5) * 5) ) = 125 – (25*5) = 125 – 125 = 0. Again, here we conclude that option D is the correct answer.
There are many other options, but these three cases will be sufficient to answer the question.
Statement: Which of the following functions is the BEST equivalent of X%Y?
Since we are aware of the symbols %, /, and *, which stand for modulo, integer division, and multiplication, the first sentence is just that – a statement of facts. The second sentence of the question is asking for the BEST equivalent of X%Y. In other words, in the absence of a mod function, how can we derive the modular value, if values X and Y are given?
Question: Which of the following functions is the BEST equivalent of X%Y?
Solution: Notice that from the analysis section case 2, we found there are two possible solutions, option A and option D. But option A does not work for cases 1 and 3. That’s why we always have to choose the BEST answer where all cases fit comfortably.
Modulo Values Calculated by a Given Function
X | Y | X – ( (X/Y) * Y ) | X%Y |
|---|---|---|---|
18 | 7 | 18 – ( (18/7) * 7 ) = 18 – (2*7) = 18-14 = 4 | 4 |
13 | 15 | 13 – ( (13/15)*15 ) = 13 – (0*15) = 13 – 0 = 13 | 13 |
34 | 17 | 34 - ( (34/17)*17 ) = 34 – (2*17) = 34 – 34 = 0 | 0 |
29 | 12 | 29 – ( (29/12)*12 ) = 29 – (2*12) = 29-24 = 5 | 5 |
97 | 97 | 97 – ( (97/97) * 97 ) = 97 – (1*97) = 97 -97 = 0 | 0 |
Please also note that when there is a double parentheses as in option D, the inner parentheses and the multiplication take precedent first followed by the outer ones. See Table 2-4.
Review Questions
- 1.Which operator is widely used in cryptography and ciphering and deciphering data?
- A)
Multiplication operator (“*”)
- B)
Modulo operator (“%”)
- C)
Subtraction operator (“-“)
- D)
Comparison operator (“>” or “<”)
Answer: Option B
- A)
- 2.The Caesar cipher adds a shift of three characters and uses the MOD function. If the ciphered function is stated as C = (P+3) MOD 26, what is the BEST possible deciphering function?
- A)
P = (C - 26) MOD 3
- B)
P = (C + 26) MOD 3
- C)
P = (C + 3) MOD 26
- D)
P = (C - 3) MOD 26
Answer: Option D
- A)
- 3.The value of 39%8 is equivalent to:
- A)
8
- B)
4
- C)
7
- D)
-1
Answer: Option C
- A)
Data Handling Requirements: Markings, Labels, Storage, Destruction
Tip #22: Understanding the methods of physical and virtual destruction of information/data by various methods
Understand data destruction and erasure methods, both physical and virtual either manually or with software/hardware.
Domain: Asset Security, Security and Risk Management.
Subdomain: Data handling requirements, Marking, Labeling and destruction.
Subject background: Deleting files, pictures, or any data from hard disk, may not delete data permanently. Data remanence is a continuous problem on computers, memory chips, hard drives, and even paper copies. Several methods are required for each medium for the data to be completely erased or physically destructed. Data handling such as labeling, marking, storage, and destruction are part of the data life cycle and asset security.
Data remanence is the persistent data that remains on a medium after the deletion process.
It is important to remove data completely when not required because inadvertent disclosure may cause problems.
Methods to remove data are clearing, purging/sanitizing, overwriting, physical destruction, and degaussing among others.
The method to adapt to remove data depends on the accessibility of the medium, the type of medium, and the possible consequences of destruction.
Data destruction must follow the policies and not just destruct anything that is not currently used because data not currently used may be useful in the future.
The complete removal of data is also known as “elimination of data remanence.”
Many operating systems keep the files in a temporary “holding area” when deleted because accidental deletion can or may require retrieval of the deleted file.
A permanently deleted file even from the holding area may exist in some part of the disk or media in some cases. Therefore, such devices may need physical destruction or other form of cleaning/purging/sanitization.
Reformatting, re-paging memory, reimaging, and repartitioning may or may not clear the data completely as well because all these are software-dependent utilities.
Clearing: This is the removal of sensitive data in a way that it cannot be reconstructed with known utilities. But even with clearing, data may be recovered by disassembling and finding bits and pieces of the data.
Purging: Also known as sanitizing, this is the removal of sensitive data so that it can never be reconstructed in anyway, even with physical disassembly.
Destruction: This is the physical destruction. If the physical destruction is not done correctly, the data may still be recoverable. An example is tearing a sensitive document into just four pieces, assuming that nobody can find details. The four (or 8 or 16) pieces can be easily added together to gather the data.
Overwriting: This is a method of repeatedly writing new data over the old tracks so that the old data is completely gone out of the medium. This is purely a software tool and erases data by writing a standard 0 or 1 to all fields/tracks all over the disk or memory device.
For clearing, the process of overwriting the data, must be repeated at least seven times before making sure that the data is completely erased.
Encryption is another process of preventing data theft. The contents of the memory or media are usually encrypted on a file-by-file basis or on an entire disk/media basis. Coupled with self-destructing/erasing methods, encryption is usually implemented by organizations such as the FBI in the case of theft or loss of equipment. After entering the wrong login password a fixed number of times, the device is programmed to self-destruct or encrypt so that the device cannot be used.
Degaussing, as the name suggests, is a form of removing the magnetic field over the medium to erase the data stored on magnetic media. Degaussing needs to be repeated several times before the media is completely free of the old sensitive data. Degaussing will NOT work on optical data media such as CD/DVD/Blu-ray disks.
Physical destruction: This includes breaking the media to pieces, altering the tracks with chemicals, pulverizing with a mill, and other such routes.
Typical hard-wired applications that destroy data on hard disks, tapes, etc., are ineffective on solid-state devices (SSDs). Physical destruction is the best way.
- A)
Erasure, reformatting, and rewriting must be seven times.
- B)
Paper records need to be torn seven times before put in the trash.
- C)
Degaussing methods are not used at all.
- D)
None of the outlined procedures is really sufficient.
Analysis: Notice that the statement says that the company has several forms of media, such as paper, magnetic, and disks. Paper files put in the trash are not safe since anyone can pull them from the trash and steal the data (dumpster diving). Erasure must be properly done, and clearing data seven times will only work on one media. Since the organization has different media, one method does not fit these media. The options are all talking about one type of destruction or several types that may not suit all media. Note that the media will be given away for reuse. So, the erasing methods must ensure that the media is really, completely and reliably erased.
Statement: A company wants to destroy older magnetic tapes, hard disks, and some paper files. The company proposes to do a process of erasing data by overwriting the media five times and reformatting the hard disks four times. The paper files will be put in the trash for recycling.
Question: A company wants to destroy older magnetic tapes, hard disks, and some paper files. As a security expert, what do you think is wrong with these procedures?
Solution: The obvious answer is option D since none of the other methods given in the distractors of options A, B, and C is sufficient for various media that need to be cleaned up.
Review Questions
- 1.At a minimum, how many times does the data need to be overwritten for protection?
- A)
Six times
- B)
Five times
- C)
Eight times
- D)
Seven times
Answer: Option D
- A)
- 2.The BEST way to completely erase data on a CD/DVD media is:
- A)
Degaussing seven times
- B)
Overwriting four times
- C)
Physical destruction
- D)
Purging with 1s and 0s
Answer: Option C
- A)
- 3.The BEST definition of degaussing a media is:
- A)
Rewriting additional data to the existing magnetic media
- B)
Removing the data by passing the media through strong magnetic fields
- C)
Rewriting magnetic data to other forms of storage
- D)
Removing magnetic media for physical destruction
Answer: Option B
- A)
- 4.Which of the following BEST describes the process of purging sensitive data?
- A)
Data is overwritten once with 0s and 1s.
- B)
Once removed, data cannot be recovered by any method.
- C)
Reformatting the storage media for future use.
- D)
Reimaging the media with a known baseline image.
Answer: Option B
- A)
- 5.Which of the following is the BEST way to remove sensitive data from any medium?
- A)
Physical destruction
- B)
Reformat, reimage, and restore
- C)
Rewrite data seven times
- D)
Degauss and overwrite
Answer: Option A
- A)
- 6.What is the BEST way to clear the data remanence in random access memory (RAM) in an electronic device?
- A)
Cool with liquid nitrogen.
- B)
Write new data to RAM.
- C)
Power down the device.
- D)
RAM data clears automatically.
Answer: Option C
- A)
- 7.The BEST way to destroy data on a Blu-ray optical disk is:
- A)
Overwrite and reformat data seven times
- B)
Submersion in Acetone or other polycarbonate solvent
- C)
Submersion in hot water and Clorox for three days
- D)
Reimage the CD as a startup disk
Answer: Option B. It is a chemical process that destroys data.
- A)
- 8.What is the BEST definition of data remanence?
- A)
Data that remains on the media after deleting/removal
- B)
Data that was erased after deleting/removal
- C)
Data that remains to be written to the media
- D)
Blank data space that is left over on media after writing
Answer: Option A
- A)
- 9.
Why are several methods required to address data remanence?
Answer: One method is never really sufficient to delete data from a medium in a reliable manner. The only sure way to completely remove sensitive data from a medium is by complete physical destruction.
Public Key Infrastructure (PKI)
Tip #23: Securing devices with personal electronic certificates and private and public keys
Learn about Public Key Infrastructure/Certificate Authority (PKI/CA), public and private keys, and certificate publishing.
Domain: Security Engineering, Asset Security.
Subdomain: Cryptography, Key infrastructure, Certificate authority, Public Key Infrastructure (PKI).
Subject background: Public key cryptography deals with public and private keys and how to manage those keys. Asymmetric algorithms that can generate the public and private keys deal with key pairs, do the exchange of keys, and can generate digital signatures. Key pairs can be used with the Advanced Encryption Standard (AES) for authentication, encryption, and electronic signature as well.
Asymmetric algorithms are used to create public and private key pairs. A message that is sent with one key can only be opened with the other key. The same key will not work for both creating/writing and reading. This means if a user creates an email message and encrypts with his private key, other people can only decrypt the message with the user’s public key.
Public and private keys are functions of large prime numbers.
Encryption creates cipher text from normal text, and decryption creates a normal text from encrypted text.
Salt is a random number used in the encryption process.
A prime number is defined as a number that has only two factors: 1 and the number itself. Examples are 11, 17, 23, etc.
PKI is a group of formats, programs, data, protocols, associated protocols, etc. PKI is created for a wide range of people to exchange messages, data, and other details.
PKI creates and maintains a level of trust among users who in turn trust the infrastructure.
PKI uses a public key certificate (PKC) and has an X.509 standard for its certificates. PKI can work with different authentication tools among different networks as well.
PKI contains keys, authorities, users, and users’ certificates.
A certificate authority (CA) is a trusted third party that allows people to communicate in a secure way. CA issues digital certificates for each user and maintains them.
A private key is known only to the user. But a user’s public key is known to all others who communicate with that user.
A CA can be internal or external to an organization. Examples of trusted external CAs are Entrust and VeriSign, which are typically used for credit card processing on the Internet.
The main responsibility of CAs is to create and maintain digital certificates.
When a certificate is revoked or made invalid, it is stored in a certificate revocation list (CRL) .
There are several reasons to create an entry in CRL. One is the expiration of certificates, and the others are a user leaving an organization voluntarily and a user’s certificate being compromised by a hacking attack.
The Online Certificate Status Protocol (OCSP) is also used instead of CRL.
The registration authority (RA) performs registration duties.
Asymmetric algorithms use private and public keys.
Signature generation and encryption go one way, whereas signature verification and decryption goes the other way in messages (for authentication and security).
If a message is encrypted with a private key, it can only be decrypted with a public key, or vice versa. The same key will not work for both encryption and decryption. This is also known as a one-way function.
The work factor is the amount of time and resources that would need to break the encryption method.
Examples of asymmetric algorithms are RSA, El Gamal, elliptic curve cryptosystem, Diffie-Hellman, and Knapsack among others.
A session key created from a user’s public key has a limited time of life before which it should be used to exchange information.
The CA issues certificates, and the RA acts as a middleman between the CA and the end user.
When users need new certificates, the request is sent to the RA, which verifies all the necessary details before the CA can issue a certificate.
PKI must conform to confidentiality, integrity, and authenticity. It also has the security features of nonrepudiation and access control.
PKI retains the key history (of users).
Hashing is a one-way function and provides data integrity only.
The most challenging job of cryptography is key management.
A digital signature is created always with a sender’s private key, and nobody else has access to this key except the sender.
In asymmetric algorithm, a message being sent is always encrypted with the receiver’s public key, and the receiver will decrypt it with his private key.
- A)
Request a certificate with the certificate authority (CA)
- B)
Request a certificate with the registration authority (RA)
- C)
Request a certificate with the certificate revocation authority (RCA)
- D)
Encrypt email with David’s signature and public key
Analysis: Note that the question is asking what a new user David should do FIRST. When a user joins an organization, his first step is to request for a certificate since the organization has its own CA. Sending email or exchange of information and all that comes much later once the CA issues a certificate.
But how does the new user apply for a certificate? It is through the registration authority that the user confirms his identity and initiates a process for new certificate.
Statement: An organization has created its own certificate authority (CA).
We can easily remove the verbiage used and re-coin the question as follows:
Question: If a new user David wants to send an email to another user named John, what should David do FIRST?
Solution: Option B is the correct answer. Option A looks tempting, but the CA does not confirm identity or checks. It just issues certificates. To apply for that certificate, David will need the RA. Option C is wrong because the CRA is used for people whose certificates have been invalidated or revoked. Option D is not the FIRST thing David needs to do and is thus wrong too.
Review Questions
- 1.
What is the difference between public key cryptography (PKC) and public key infrastructure (PKI)?
Answer: PKC is the usage of an algorithm. PKI is an infrastructure created to deal with PKC.
- 2.If David sends an email message with a disclaimer and his digital signature to another user John, the term used for the fact that David cannot claim he did not send the message with disclaimer is known as:
- A)
Nondisclaimer
- B)
Nonrepudiation
- C)
Repudiation
- D)
Disclaimer
Answer: Option B
- A)
- 3.
If David wants to send message to John, what key should David use for encrypting the message and for the digital signature?
Answer: For encryption David uses John’s public key, and for the signature David uses his own private key to generate the signature.
- 4.For which of the following the Online Certification Status Protocol (OCSD) is BEST used?
- A)
To create new status for a digital certificate
- B)
To check for a revoked digital certificate online
- C)
To renew the status of an expired digital certificate
- D)
To request for a new digital certificate online
Answer: Option B
- A)
- 5.What is the main purpose of a hash?
- A)
To encrypt the message
- B)
To provide integrity of the message
- C)
To provide a public key to the message
- D)
To encrypt and decrypt the message
Answer: Option B
- A)
- 6.What is the standard for digital certificates?
- A)
X.590
- B)
X.509
- C)
X.950
- D)
X.905
Answer: Option B
- A)
- 7.What is the main purpose of a certificate authority (CA)?
- A)
Create certificates via registration service
- B)
Create and maintain certificates
- C)
Create, maintain, and revoke certificates
- D)
Create, maintain, revoke, and register certificates
Answer: Option B
- A)
Intellectual properties and protection
Tip #24: Learning the detailed life spans of intellectual properties such as documents and inventions
Remember the time frames for each of the types of trade documents, intellectual property, etc.
Domain: Asset security, Security and Risk Management.
Subdomain: Intellectual properties, Protection of data/trade secrets.
Life Spans of Intellectual Properties
Type | Length | Details |
|---|---|---|
Trademark | 10 years | A symbol, word, slogan, design, color, or logo that identifies the source of a product or service. Can be a product or a service. Examples are iPhone, WhatsApp, etc. Uses SM or TM symbol. Can be renewed indefinitely. |
Patent | 20 years | Most patents are for businesses as utility patents or design patents. Some can be plant design patents. Improvements of a process also fall as patents. The United States Patent and Trademark Office (US PTO) helps with registration or patents. |
Copyright | Lifetime of author + 70 years for people and 95 years for organizations or companies | Print, copy, publish, perform, film or record, etc. Also derivative work like translations, etc. Examples: novels, paintings, films, songs, etc. Uses the © symbol |
Trade secret | As long as possible | Trade secrets are usually formulas that mix to make a drink, a medicine, a dose, or anything such. They can be protected for as long as required, and there is no paper registration or document required but can be written down and stored. An example is the drink formula for Coca-Cola or an energy drink. |
License | Fixed period mutually agreed between parties and can be usually renewed | These are contracts between one or more parties, called the licensor and licensee(s). the licensees pay a royalty for transfer of intellectual property to the licensor. Licenses help market better products to markets over a wide range of geographic areas. |
A product or service can have multiple intellectual property rights such as patents, trademarks, copyrights, and so on.
A service mark (SM) is a typical trademark, but it is for a service rather than a tangible product.
Royalties are usually based on a percentage of the revenue the licensee generates from the sale of products and pays to the licensor.
Patents protect the right of original inventor.
Registering for a trademark is not necessary by law but helps the owner of product. Registered trademarks are valid for 10 years and can be renewed and used with the® symbol.
Patent holders have an obligation to enforce their rights. Failure to enforce rights is considered as patent abandonment.
There is no fixed number of patents or copyrights or trademarks one can own or a product/service can have.
Service agreements can also force a user or business to abide the rules of the agreement despite having a trademark or patent. For example, AT&T can enforce a service agreement for two years by selling you an iPhone and service at a lower price than T-Mobile.
- A)
Patent for tennis racket, copyright for book, trade secret for energy drink
- B)
License for energy drink, trademark for tennis racket, patent for energy drink
- C)
Trademark for tennis racket, license for book, trade secret for energy drink
- D)
Trade secret for energy drink, trademark for tennis racket, patent for book
Analysis: Observe that the player is trying to put more than one business into market and needs several things to be registered. The easiest of these is an autobiography that will be automatically protected under copyright laws. There is no registration required for copyrights. The tennis racket is a tangible product as well, and it needs a patent for the innovative design. The energy drink has a mixture the player alone probably knows and needs a trade secret. It need not be registered but needs to be protected with utmost care. If we know these facts, the question is easy to answer.
Statement: A T-shirt is given freely, and it appears from the question that the player does not want to worry about it since it is being given freely if anyone purchases a racket, book, or the drink. Removing the verbiage we can find the following:
Question: A tennis player has a new idea for an energy drink, an idea for a book to write his autobiography, and a new design for a tennis racket. What should the player register for to protect the BEST interests of his businesses?
Solution: Licenses are given for a product after the product is already in the market and when the original inventor wants to expand his marketing territory to larger areas. The license does not apply immediately to a new product. Licenses do not also apply to books. Thus, options B and C are wrong choices. Books also do not carry patents since the writing is considered a type of copyright material. Thus, option D can be easily eliminated. This gives the correct answer as option A.
Review Questions
- 1.How long is a copyright valid for a business or an organization?
- A)
Lifetime plus 70 years
- B)
95 years
- C)
Lifetime plus 100 years
- D)
Lifetime
Answer: Option B. For an individual, copyright is valid for a lifetime plus 70 years, but for a business it is 95 years.
- A)
- 2.The symbol issued by the United States Patent and Trademark Office for a service is:
- A)
SMr
- B)
SM
- C)
SeM
- D)
SrM
Answer: Option B
- A)
- 3.A company wants to protect its intellectual property for a health drink has the BEST protection under what?
- A)
Trademark
- B)
Copyright
- C)
License
- D)
Trade secret
Answer: Option D is correct. Trade secrets protect the property better than anything for a health drink.
- A)
- 4.Where should the trade secrets be mandatorily registered?
- A)
US Patent Trademark Office
- B)
Federal government
- C)
State government
- D)
No registration required
Answer: Option D. Trade secrets do not need any mandatory registration.
- A)
- 5.What is the BEST term for the money a licensor gets from one or more licensees to transfer intellectual property?
- A)
Service fees
- B)
License fees
- C)
Royalty fees
- D)
Product fees
Answer: Option C
- A)
- 6.
An inventor wants to patent his product and give a license to another company to market it in the state of California. How long are the patent and license valid for at BEST?
Answer: A patent is valid for 10 years, and a license is valid for mutually agreeable period.
- 7.In how many ways can a patent be BEST registered?
- A)
Service patent, plant patent, and supply patent
- B)
Business patent, utility patent, and design patent
- C)
Utility patent, trade patent, and product patent
- D)
Private patent, public patent, and universal patent
Answer: Option B
- A)
- 8.A parent, trademark, copyright, or a license of an inventor at BEST can protect what?
- A)
Intellectual property
- B)
Business property
- C)
Public and private property
- D)
Financial property
Answer: Option A
- A)
- 9.
A publisher translates a book without the original author’s permission and releases the book in the translated language in another country. What rights can the original author BEST use to protect his literary work?
Answer: Copyright laws protect the author even for translations and derivatives.
