Manage security as an organizational capability, not as a liability. For sustained competitive advantage, an organization must consider security their friend, not a foe.
Business State
Regardless of the industry and size of the organization, there is a fundamental shift within every business and operating model. Organizations are dependent on each other, requiring a much tighter, integrated, and timely flow of information. The type of information and with whom they share information will only expand with time. In the online world, everything is a service and is fast becoming a self-service. Organizations can no longer function in isolation.
The organizations will continue to push the envelope on how technology can help them become more productive, reduce the cost of doing business, provide new and better products and services to their customers and partners, make better and faster decisions, and introduce new business and operating models.
To manage business, leaders are always looking for ways to innovate and drive their competitiveness in the marketplace. They are always asking the IT function to simplify and enhance their capabilities to communicate, collaborate, connect, and consolidate information and transactions across people and processes inside and outside the organization. Organizations like to collect a lot more information about their customers so that they can become more responsive to customers’ needs, and thereby, better respond to their needs and promote relevant products and services. Organizations want their customers to self-help themselves through their mobile devices or whatever method they choose. They want to seamlessly integrate or interact with machines, devices, and systems belonging to other people or organizations for a real-time flow of information and actions.
In every organization we have worked with, consistently, it has been found that business management spends lot of time, energy, and money in thinking and managing the capabilities they need to run and grow the business. We have also found that business-initiated projects mostly, if not entirely, are about new business capabilities. The capabilities generally require new roles or new tools of trade. As most of the functionality or capabilities are grounded on digital technologies, unlike wet floors or operating machinery, most organizations don’t think their people will get hurt. As a result, the safety and security of information is not often considered in advance or during process or solution engineering. Over the years, the organizations have learned that a rework does not always produce the same quality, controls, and satisfaction even after spending a great amount of time and money. The same is true for information and transactional security in any business process. To overcome the unnecessary spending and associated risks, any business capability planning must include delivery of a secured business capability.
Security as a Competitive Differentiation
A recent report,1 published by AIG that is based on a study conducted in the United Kingdom shows the following results:
45% of companies surveyed have already experienced a cyber security breach.
62% believe it likely that their company will suffer an attack within the next 12 months.
56% of European data breaches were caused by internal company employees or by other areas internal to the company.
52% of companies said they either rarely or never discussed information security in board meetings.
36% still designate maintenance of cyber security as an IT department function.
In the previous chapter, we questioned the need for a growing cybersecurity industry . Even with the large sum of money spent on information security infrastructure, organizations continue to fear and experience security breaches because of the low level of maturity in their security management capabilities. It means, if planned and managed right, security can be a major competitive differentiation in the age of digital business where everything is a service.
If you look back, you can clearly see how business management attitude has changed over the last few decades around product and service quality. At the start of global competition, it all began with the need to survive in the marketplace and considered cost of quality as a cost of doing business. Just like the information security industry today, there was a growing industry around total quality management with plenty of methodologies. Many organizations embarked on major transformational, quality initiatives and promoted themselves as quality-first organizations. In spite of these quality initiatives, some organizations could not survive while others were able to create a sustainable competitive advantage with quality as a core differentiating ingredient.2 This time cybersecurity is no different than quality. Just like quality, security is not one person’s or one group’s responsibility . It is everyone’s responsibility. It takes people, process, information, technology, and culture to do it right and, more importantly, sustain it. If done right and managed right, secured business operations will also be a key contributor to ongoing business advantage. The organizations recognize that product quality is not a difficult subject for business leaders to understand, and therefore they have been willing to commit and proactively drive desired outcomes. For business leaders to see security as a business differentiation rather than a business nuisance, they need to describe and organize it in a business context. Not in terms of their negative impact on the business but in terms of business outcomes. Not as a shiny object but as an integral part of the culture.
Secured Business Operations, an Organizational Capability
Let’s start with a term that is business-centric and clearly articulates the business objective – Secured Business Operations. Cybersecurity may be a mean; the secured business operation is the destination or outcome that will ultimately produce the desired results.
Secured Business Operations is an organizational capability , providing an ongoing ability for protecting information and assets, preventing unauthorized access, ensuring trust and peace of mind, and safeguarding a firm’s brand while continuing innovation and delivering differentiating experience and services for its customers, partners, and employees.
Every product or service provided by an organization can be viewed like a coin with two sides. One side represents its value for the consuming organization or an individual; and the other side represents the warranty from the issuer, that is, it can be trusted for using whenever or wherever. Any business operation, whether internally within the organization or externally with other people or organizations, must have the right functional capabilities, that is, fit for purpose to produce the desired outcomes. At the same time, the business operation should also be secured and reliable enough, that is, fit for use for people to trust and participate in the operation. It doesn’t matter how good the functional capabilities are if no one is willing to adopt and use them. For sustainable business advantage , every business operation needs to be fit for purpose and fit for use – in other words, it must be a secured business operation.
Now, how secure do the “secured” business operations need to be?
Whenever you talk with technology, process, compliance, or a framework subject-matter expert about securing business, the typical response is in terms of a list of “ideal” practices. Frequently, these experts quote these practices as best practices, not best for you but what has been best for someone else. Many of them also take the mindset of being risk-averse, that is, anything short of the extreme or what is considered the best, has a risk that must be eliminated.
Except in case of life and death or some moral, ethical issues, most of the business decisions are based on return on investment . Any lack of appropriate investment does introduce potential business or financial risk. It should not be about eliminating future potential risk today, it must be about understanding and willingness to accept the potential cost of follow-up actions needed in response to the situation when potential risk is materialized. In the end, good business decisions are based on cost and value of doing something, and not on cost and risk of not doing something. There is no right or wrong answer on what that something is. To adequately answer the question, “how secured your business operations need to be?,” you must first identify the appropriate level of risk resilience for your organization. So, rather than getting caught up in the details and frankly in the noise of all the technical opinions, the next framework and practices need to be business-centric by design and must leverage the laws of gravity.
“Where will the apple fall” – can be determined quite easily when we are looking from the top of the tree compared to looking up from the ground and not sure which apple are we focusing on.
A safety and security risk is introduced whenever there is a handshake or distribution of information between two parties. The parties can be individuals, processes, systems, or devices regardless of their location and affiliation with the organization . If the information remains in the sole custody of the source and there are no windows or holes in the walls around the source for someone to peak in, there will not be a cybersecurity industry and we won’t be writing this book. As we studied many organizations across industries, we found that the security risk resilience level of the organization can be reasonably evaluated and projected based on the types of interaction with its own employees; between its own functions; and with external people, processes, and organizations. Consider the business engagement model to understand these interactions.
A business engagement model helps you identify the “right” security posture or risk resilience level for the business, and guide the execution trajectory for achieving and sustaining secured business operations, thus avoiding overengineering and ensuring alignment at every level and across the organization.
The model consists of four distinct engagement levels, describing the reach and range of engagement. See Table 2-1 for a summary of the engagement models. The engagement levels are progressive, that is, as the organization grows, it typically extends its ecosystem and capabilities, thus increasing the reach and range of interactions.
Table 2-1 Business Engagement model
Level | Archetype | Characteristics |
|---|---|---|
1 | Core Business | All business transactions and information are maintained and managed within the confines of the business. No information in digital form is shared outside the walls of the organization. |
2 | Business to Business | Business regularly performs electronic transactions and shares documents/information with customers and partners. |
3 | Connected Business | Employees, customers, and partners can access information and conduct business over the Internet. |
4 | Digital Business | We are a well-integrated and transparent organization, working like a virtual organization with many of our customers and partners. |
The business engagement model provides for every planner and decision maker in a business context. It also ensures that downstream security measures and actions support required and desired business activities. With this understanding and alignment, risk and necessary actions needed to manage the risk can be characterized.
At each engagement level , the organization needs to have business capabilities and a competency level in recognizing, analysing, and managing various types of security risks an organization may face. Even if the two organizations are operating at the same engagement level , say connected business, their risk resilience capabilities and competencies may vary. Table 2-2 outlines the summary and structure of a security risk resilience capability map. The subsequent chapters will leverage this map for in-depth assessment and planning of various business and operational capabilities.
Table 2-2 Risk Resilience capability map
Level 1 Initial | Level 2 Basic | Level 3 Standard | Level 4 Competing | Level 5 Leading | |
|---|---|---|---|---|---|
Scope or Reach | Regulatory | Corporate | Functional | Cross-functional (end-to-end) | Cross-organization (extended enterprise) |
Key Attributes | Legal, Ad hoc practices | Mandatory, Requirement driven, Reactive processes | Operationally oriented, Event or risk driven | Policy-centric, Proactive planning | Value and life cycle driven, Measurement and monitoring |
It is obvious in this capability map, initially business leaders and organizations in general are focused on what must be absolutely addressed and managed, that is, risk related to legal compliance . The scope of risk management increases as the business engagement model expands beyond the internal processes. In terms of organizational competencies, initially most of the risk-related practices, including discovery and mitigation, are reactive. Competent organizations become proactive with defined processes, and even more effective and risk resilient with the ability to sense things before they happen. It is not expected, and not even recommended, that every organization must seek to be level 5 in all capabilities. The emphasis must be on value generation, including being risk resilient, for the business engagement level . Use Figure 2-1 to determine the right place on the capability map based on the assessment of your engagement model.
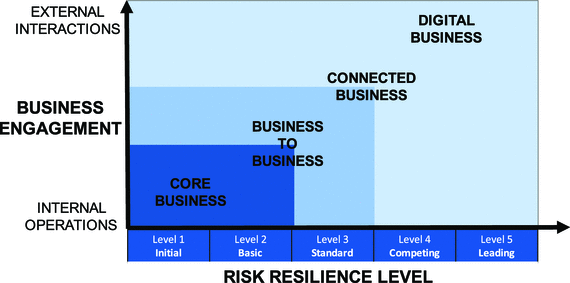
Figure 2-1 Business Engagement vs. Resilience Level
With the introduction of the business engagement model and risk resilience capability map, an organization can determine how secure their business operations need to be.
This is a first step in achieving and sustaining secured business operations as an organizational capability. In the next section and subsequent chapters, additional components of this framework are explained, and the remaining steps are outlined for making it happen in any organization.
Achieving and Sustaining Secured Business Operations
We understand businesses are different, and there are many different solutions to a problem, yet we also see how people leverage their experiences across functions, organizations, industries, and even cultures. The framework and approach for achieving and sustaining secured business operations is industry, language, and technology agnostic. At the same time, it allows an organization to quickly focus on what is important and relevant to them and personalize for specific needs and solutions.
As it was stated earlier in this chapter, the secured business operation is an organizational capability, and it needs to be articulated, assessed, and planned in such a way that everyone in the organization can understand, support, and benefit from it based on their individual perspective. Therefore, the capability framework for secured business operations includes two capability models – (1) Management and (2) Operational perspectives. As depicted in Figure 2-2, these two models drive and influence each other.

Figure 2-2 Capability Models
Almost all solution frameworks and methodologies emphasize alignment with business objectives, but generally lack specificity in helping people in finding the alignment. The biggest barrier in any alignment and decision making is that people can only plan based on what they know. So, how do people learn more and sooner?
It is very hard to achieve, let alone sustain, if we don’t begin with the end in mind. The secured business model is the first capability model from a business perspective, breaking down the barriers to alignment and learning.
For secured business operations, what should business leaders be asking, planning, and managing ? In the secured business model, five performances (5 Ps) domains are defined for business management to identify the risk posture of their business operations. Figure 2-3 outlines 5 Ps with the business intent they address.

Figure 2-3 5 Ps of Secured Business Model
Each of the 5 Ps has multiple capability dimensions. Each dimension is characterized across 5 maturity levels. For example, Prevent Domain includes what kind of unauthorized access and what kind of information leakage you want to prevent as a business. The maturity levels, progressively, define the types of unauthorized access or leakage you can be preventing. The higher the maturity, the broader the reach and range of prevention. Based on your business engagement model, you should be able to identify where you need to be across these 5 Ps, evaluate where you are, and what you could be doing to close the gap.
The secured business model acts as a planning and execution guide as well as an accountability and value management tool for the organization, a critical requirement of an effective alignment and oversight. See Chapter 3 for the detailed, inside view of the secured business model .
With the knowledge of “what” is needed across 5 Ps, the organization can now proceed to assess and plan the operational practices needed to support the 5 Ps. The operational practices are encapsulated in the secured operating model. See Figure 2-4 for various operational domains included in the model.
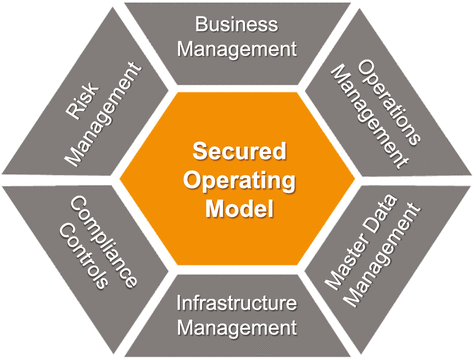
Figure 2-4 Secured Operating Model
The secured operating model provides a 360° view of various cross-functional, operational capabilities needed for achieving and sustaining secured business operations. The six capability domains shown in Figure 2-4 include 21 critical capabilities every organization should be regularly evaluating and improving in alignment with the secured business model. Just like 5 Ps in secured business model, 21 critical capabilities in secured operating model are also characterized along the 5 maturity levels. For example, Business Management includes change management, governance, and KPI measurement as three critical capabilities. As noted in the previous chapter, most of the existing operational and technical practices and frameworks are operational and technical in content. They form the underpinning, supporting practices for the capabilities in the secured operating model. Therefore, the secured operating model acts as a unifying capability model by accounting and incorporating current practices and solutions. The organizations can assess the current capabilities built on current industry practices and solutions, and leverage other frameworks and expert knowledge in the context of a secured operating model.
We can’t clap with one hand, at least not loud enough and not for long. At a low level of maturity, everyone can make some improvements on their own. To get to a higher ground and sustain, we depend on others as much as they depend on us. Achieving and sustaining higher maturity in secured business operations, organizations need to understand and address interdependencies as much as they need to improve individual capabilities. Therefore, in addition to capability maturity models and underlying enabling practices, the framework also includes inbound and outbound dependencies between various capabilities across the organization. This body of knowledge can help the organization on two fronts –
Achieving desired maturity and outcomes by recognizing and addressing gaps in the dependent capabilities.
Driving change and communicating value by enabling upstream capabilities to improve their maturity.
See Figure 2-5 as an example of how a dependency map can help understand and manage risk and value.

Figure 2-5 Capability Dependency Map
A body of knowledge is critical, but, on its own, is neither sufficient nor does it guarantee successful adoption and implementation. We have seen technologies failing to deliver expected results, and training courses failing to change behavior. To close the gap between information and transformation, there is a need of an execution discipline by leveraging the body of knowledge for desired outcomes. Therefore, in the overall framework for secured business operations, a secured management model is included. Figure 2-6 provides the high-level model that is explored in detail in Chapter 5.

Figure 2-6 Secured Management Model
The secured management model is an outcome-oriented approach to sustain secured business operations in a scalable way holistically from a people, process, information, and technology perspective. It incorporates cumulative learning from many process management practices, such as lean six-sigma, value management, and program management. The model emphasizes measurement and includes a list of potential KPIs that organizations can use at each level of maturity in order to monitor progress and impact.
So far, we have introduced many components of the framework for achieving and sustaining secured business operations. The framework details follow in subsequent chapters. Let’s quickly summarize how one can use the framework for managing cyber and security risks, as well as create competitive advantage with secured business operations as an organizational capability .
Use the business engagement model to identify the kind of interactions with employees, customers, and partners. The depth and breadth of the engagement defines the cyber risk exposure the organization needs to manage.
Use the secured business model to identify what an organization must secure while enabling the business engagement. The model includes a capability maturity model addressing 5 Ps of risk posture – Prevent, Protect, People, Policy, and Profile. Using the model, business leaders can clearly articulate their risk posture, provide necessary guidance, and monitor organization performance against desired outcomes.
Use the secured operating model to assess, develop, and maintain the required practices involving people, process, information, and technology for secured business operations, guided by the risk posture defined using a secured business model.
Use the secured management model to implement the discipline necessary to adjust and sustain secured business operations aligned with the business engagement model.
Figure 2-7 outlines the purpose of each model in the framework for secured business operations.
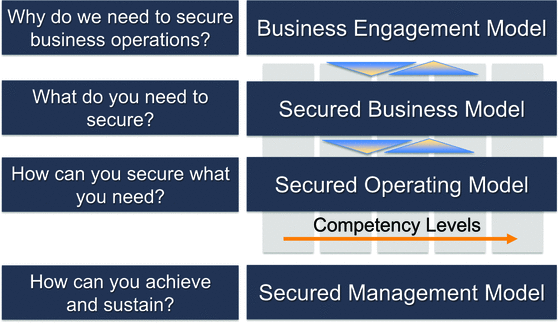
Figure 2-7 Secured Business Operations
Now, let’s review two use cases - how the framework was used by different organizations. In the current business environment, you may find your organization somewhere in between the two studied organizations. During the initial assessment and follow-through planning in these organizations and otherwise, we noticed the following:
Increased business involvement and accountability. Cybersecurity is no longer an IT-centric topic.
Change in business and IT posture toward risk management. They started moving from being risk-averse toward risk-managed in their decision making and planning.
Knowledge of “unknowns” that helped in planning. Because of unknowns, there was a lot of fear that was leading to overengineering and overspending.
By-design mindset. Everyone begins to think about their role and responsibility in achieving and sustaining secured business operations.
Manufacturing Organization (B2B Engagement Model )
An industrial product manufacturing and distribution organization primarily works with other business organizations, rather than the end-user consumers. It has multiple manufacturing and warehouse locations. It has strategic and operationally integrated partnerships with a set of customers and suppliers.
Based on its interaction and flow of information with customers and partners, it was determined that the business engagement model was to be Business to Business (B2B). Over time, it may evolve into a connected business as it expands collaboration and integration beyond supply chain, order processing, shipping, and support. As a conservative and cautious organization, the business and IT management have been very methodical in leveraging new technologies, particularly for communicating and sharing information outside the company. In spite of careful planning and safety-first culture, the management felt pressure on both fronts – increasing security-related cost and fear, and pressure from customers and partners for more and more electronic processing and timely information. Business leadership along with the CIO decided to take an outside-in or business-centric view of their security practices, and find a happy medium between required innovation in their business processes and resistance to change due to security risk.
A small project team consisting of business, IT, and external consultants worked for about six weeks in assessing the current practices and developing the recommendations. The team leveraged the secured business capability maturity model to survey many business senior- and middle-level managers to capture their thoughts on the security posture. As expected, there was a sufficient variability in responses due to different perceptions or varying maturity across business processes. As shown in Figure 2-8, the average maturity of many of their 5P capabilities was close to level 2. Referring back to Figure 2-1, for a B2B organization seeking to become better connected with its customers and partners, being level 2 is not a bad place to be. Definitely, there were areas they needed to improve to reduce the unnecessary risk exposure.

Figure 2-8 Assessment - Secured Business Model
Once the management understood the current risk posture , the project team proceeded to assess current practices. It invited business and IT process owners and stakeholders to participate in a survey. As processes are integrated with customers and partners, the team decided to invite select customers and partners to understand their point of view. A heat map of current capabilities based on a secured operating model was produced, highlighting the level of competency in various areas. Figure 2-9 shows that most of the operational capabilities were between maturity levels 2 and 3. Dependency management and life cycle management capabilities were operating even at lower maturity levels than 2.

Figure 2-9 Assessment - Secured Operating Model
Although many aspects of the assessment were obvious, there were a couple of interesting observations.
A few current practices were overinvested based on the business engagement model and risk posture identified from the secure business model. Continued investment or improvement in these areas was contributing to the cost but not necessarily the value.
Some areas were overlooked or significantly underinvested, that is, below desired maturity level, negatively impacting overall posture and return on other capabilities.
With understanding of the business engagement model, and assessment of the risk posture and current operational capabilities, the board and executive leadership made necessary changes to the governance, funding, metrics, execution, and reporting activities.
Health Care Organization (Digital Business )
Health care is one industry where time is of an essence and right information to the right people is paramount. Care and convenience is putting pressure on security and risk measures. Health care is transforming greatly with the focus on digitizing health care information and providing health care services virtually to patients. The privacy and security regulations , HIPAA , PHI, PCI, PII, and EDPA are all putting a lot of controls to provide health care services in a safe manner and by keeping the consumer, patient, in mind. With advancement in technologies, medical devices and the desire to share information with various parties in real time for timely and quality care while reducing the cost of care, it is quite evident that the business engagement model for most health care organizations can be categorized as digital business.
To provide secured patient care services and securely manage patient health information, health care providers, insurance organizations, and pharmaceuticals are required to work in tight integration while abiding to all regulatory requirements. Achieving and sustaining end-to-end secured business operations is more challenging in heavily siloed and disjointed systems environment. As digitization plays the significant role, the approach was taken to look into the full spectrum of the five Ps of the secured business model as an internationally recognized health care provider. The board and the senior leadership understood the profiles of risks, associated vulnerabilities, and exceptions; and the business importance of preventing breaches and protecting assets was realized. The understanding led to improving policies by creating a supporting executive-level governance committee for making decisions and developing appropriate policies. The core team of 50 plus subject-matter experts and consultants was formed to focus on developing the strategy and operationalization of secured business operations by changing the mindset of people. To achieve the business goals of guest-friendly patient care, extending reach to global health care providers and pharmaceuticals in a trustworthy, reliable, and safe manner, a multimillion and multiyear enterprise-level strategic initiative was spawned.
Using the secured operating model , the following strategic business-critical initiatives were initiated for planning and overall enterprise architecture purposes:
Business Management – The cross-functional governance committee, including health care providing hospitals, finance, legal, and operations, was established with the focus on providing the secured health care services.
Operations Management – Multiple initiatives were in focus for securing the operations from payment cards processing, health care and supporting services management, patient identity and health information, IT operations, and network operations perspective.
Risk Management – The risk profiles were established to understand, prioritize, manage, and execute projects to eliminate associated vulnerabilities and exceptions for the overall management of the relevant risks.
Compliance Controls – To meet the regulatory requirements, enterprise-level architecture was established for aligning business and technology architecture and meeting the compliance controls requirements in a sustainable manner.
Infrastructure Management – The vulnerabilities associated with networks, data center servers, storage, and middleware posed the fundamental risks for achieving the desired level of security associated with cybercrime and securing the business operations.
Master Data Management – The data associated with managed assets, patients, health care provider workforce, other providers, research, and insurance companies were not centrally managed and had vulnerabilities posing security risks.
To start with, the board decided to give importance to strengthen the foundation elements and the focus was given to manage the associated infrastructure risks. The strategic program was spawned with well-defined key performance indicators and associated measurements to successful manage such a business-critical initiative using the execution discipline defined by the secured management model.
The administrators recognized that this is a journey and they are now engaged on a continuum basis to ensure new capabilities developed based on the risks associated with the change or advancements in interactions with people and systems in the ecosystem.
Achieving and Sustaining Secured Business Operations in Your Organization
A change and persistent transformation starts with awareness. As you can see through the above case studies, many people in these organizations were taking care of the security, doing more than necessary in some cases while being unaware of many other things. How do you know your weak links? How do you know that you are doing the right things, not just for today but for tomorrow as well? If you begin with the end in mind, every step you take will help you achieve and sustain progress.
Therefore, awareness among your board and senior management for a secured business operation is critical for creating a competitive edge for your business growth; and just like other critical capabilities, they must take active interest in building and maintaining this capability. Use the body of knowledge in this book and state of your organization for creating the required management mindset. You may conduct an initial, quick assessment using the business engagement model and 5 Ps in the secured business model to create awareness and support.
As we stated earlier, secured business operations are an organizational capability. It means you would need representation and engagement of various functions and roles across the organization. Conduct a survey using the business engagement model, secured business model, and secured operating model with a broader group of people with follow-up interviews with select people. These models and assessments will drive learning, common language, and shared objectives across the organization.
Based on the gaps between the current and desired risk posture , develop a plan for addressing the 5 Ps. Start by assessing, building, and maintaining the profile of various vulnerabilities in your business operations. Ensure that you have business-driven policies and holistic governance in place to prevent breaches and protect enterprise-level business operations internally and externally with employees, customers, partners, and suppliers. The behavior and attitude of the people define the culture of the enterprise. Generally, people are often the weakest links in sustaining secured business operations.
Strengthen your culture and ensure people who are part of your workforce, including internally and externally, are well educated on an ongoing basis regarding the security measures.
The subsequent chapters provide detailed explanation of the framework and the models introduced in this chapter. They also include underlying practices, dependencies, and metrics to help you further in developing plans and operationalizing the framework for achieving and sustaining secured business operations in your organization.
Footnotes
2 Hung Chung Su, Kevin Linderman, Roger G. Schroeder, and Andrew H. Van De Ven, “A Comparative Case Study of Sustaining Quality as a Competitive Advantage,” Journal of Operations Management 32:7-8 (2014): 429–45.
