6
Artifacts that Attackers Can Collect from You
Traditionally, IT security and cyber security professionals concentrated on protecting the perimeter. The perimeter is the area in our infrastructure that separates the internal infrastructure from the external world. This practice is commonly known as castle security. It was used by conventional security systems to try to protect information from external perpetrators. Most systems were closed systems and the only connectivity to the external world was the internet; this practice was quite acceptable for traditional systems. However, today’s complex requirements and the introduction of cloud systems have made this practice worthless. Also, insiders play an active role in many attacks, meaning security professionals are forced to find a better approach. Since attackers must also access enterprise systems through the perimeter, security professionals can collect indicators of compromise from perimeter devices.
Typically, artifacts are what get left behind after an activity. We can treat them as footprints of the end user or an attacker. This chapter focus on the artifacts that can be collected from you by attackers and other interested parties.
In this chapter, we will explore the following topics:
- Artifacts that attackers can collect from you
- Artifacts that companies would like to collect
- Devices that can be compromised
- Ways that an attacker can access your networks
- Compromising browsers
Artifacts that attackers can collect from you
Attackers can collect artifacts from you in many ways. Traditionally, artifacts were used by cyber-forensic professionals to trace back perpetrators after an attack. In today’s modern world, artifacts are quite useful to collect information about targeted users or companies to understand their behavior patterns, buying patterns from online stores, interests, and other exciting information. Artifacts can be collected by attackers on any device including desktops, laptops, or mobile devices. They can be collected from deep inside the operating system, memory, temporary files, and various locations inside the filesystem. Artifacts can provide significant information about the activities performed by cyber attackers, as well as users. This is the reason why artifacts are the main source of evidence for cyber-forensic professionals when analyzing an attack. For forensic professionals, artifacts provide information related to unauthorized access, tools that are installed or used by the attackers, attacker locations, and other relevant information, including attackers’ IP addresses.
On the other hand, if attackers collect artifacts from users, they also can collect information about user activities.
Attackers use different ways to collect artifacts from target systems. Artifacts from the targeted systems that are commonly collected by attackers include the following:
- Cookies: Attackers use cookies to understand the locations you frequently checked into, login information such as session IDs, and products you have clicked on. Cookies are files that are very small in size, created by websites that you have visited and stored within your browser. These cookies allow websites to monitor your behavior to streamline your searches and provide you with a rich experience.
- Files that are created by operating systems: Security Accounts Manager (SAM) on the Windows operating system and /etc/shadow on the Linux operating system.
- Files that contain browser preferences, passwords, and history.
- Files that contain sensitive and personal information.
Let’s look at the ways attackers can steal artifacts from your computer:
- Malware attacks: Malicious software, commonly known as malware, is the most commonly used way attackers steal artifacts from your computers. Hackers create malware to enter systems and perform other malicious activities. It’s like throwing a net to catch fish. Whoever is infected by the malware provides attackers access to the infected system, allowing them to steal information and collect artifacts. Malware uses different entry points to get itself planted on targeted systems. It can be a vulnerability that is exploited by the malware, a link sent to a user that they clicked on to unwittingly install the malware, an attachment sent to the user’s mailbox that is opened by them, or removable media that contains malware that is attached to the system. Malware is the common name used to refer to a large variety of programs of a similar nature. Let’s look at some of the different categories of malware:
- Viruses: Viruses can replicate themselves and infect other programs. Viruses need host files to exist and are often attached to another executable. Nowadays, even script kiddies (attackers with little or no knowledge of advanced technologies that use existing tools to launch attacks) can create viruses using construction kits.

Figure 6.1 – JPS Virus Maker
- JPS Virus Maker is a virus-constructing kit with which you can create your own virus. You can disable any program or process of a Windows system using this construction kit, including turning off the firewall or Windows Defender. As you can see in the preceding screenshot, an attacker can use this type of construction kit to create a virus. If they are an elite hacker, the attacker can write their own code to do the same.

Figure 6.2 – More features of JPS Virus Maker
- JPS Virus Maker has even more advanced features, such as changing a computer’s name and running custom commands once executed. You can even convert the output to a worm, backdoor virus, or logical bomb. Once everything is configured using the GUI, an attacker can choose any icon they want, create the virus, and start sending it to the targets.
- Worms: Worms don’t need host files as they are self-contained programs. Often, worms propagate through networks to infect other systems. Mostly, worms use emails to attach themselves and send copies to email recipients. As well as virus construction kits, there are worm construction kits available – for example, Internet Worm Maker Thing.
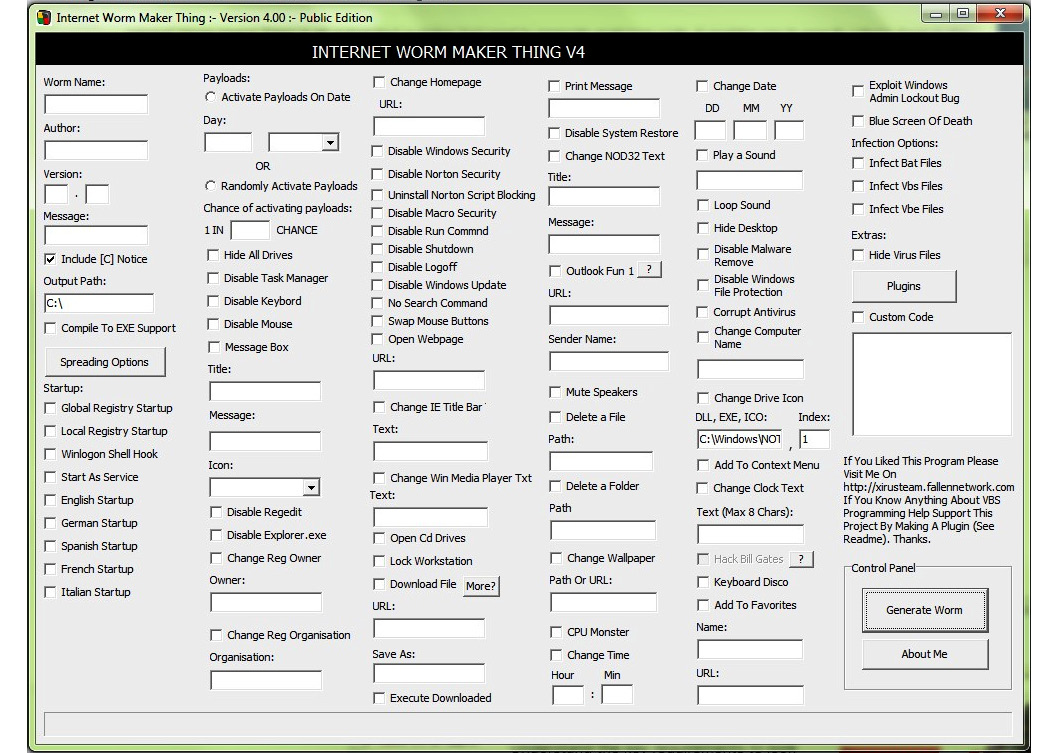
Figure 6.3 – Internet Worm Maker Thing to create worms
- Internet Worm Maker Thing is a GUI tool that generates malicious code or automated script the way you configure it. You can define the criteria using the given options, including actions that you want the worm to perform. You can change the startup of the program, change the home page of the browsers, drive icons and names, change wallpapers, and many other options, as you can see in the preceding screenshot. Once you create the worm, it will be in Visual Basic Script format or .vbs. You can convert .vbs to .exe if you want to.
- Trojans: Trojans are malicious code hiding inside a legitimate program and performing malicious activities. Trojans don’t replicate themselves like viruses and mostly create backdoors for attackers to enter and connect to a target system. This provides them with access to the system to collect artifacts from it. When it comes to collecting artifacts from systems, Trojans are the most commonly used malware by attackers.
- As with viruses and worms, there are many Trojan construction kits available. Theef is one of the Trojans that attackers use to create a backdoor connection to a target machine. There are two parts to this Trojan, a server and a client. The attacker executes the Trojan server on the target system, and once the Trojan server is executed, the Theef client can be used to connect the target system to the server to control it, as shown in Figure 6.4.

Figure 6.4 – The Theef Trojan client is connected to the server
- When the Theef client is connected to the server, the attacker can obtain lots of information about the target system, including PC details, operating system information, registered user information, and network information, including the system name, whether it is attached to a workgroup or domain, any file sharing, and information about a registered organization.

Figure 6.5 – The Theef Trojan can spy on the target
- Once connected, the Theef Trojan can capture the screens of a target system, view and control the Task Manager and the Process Viewer, work as a keylogger, obtain passwords saved on the system, and remotely access Command Prompt, internet messenger chats, and the microphone.

Figure 6.6 – The Theef Trojan can access the filesystem to collect artifacts from the target
- Importantly, the Theef Trojan can access the filesystem of a target system and collect artifacts. This is a very important feature that the Theef Trojan has; it can search for important files of the target system, access the files, remotely execute them, open them, and transfer them to the attacker’s system. This is a great way of collecting artifacts from the target system.
- Spyware: Spyware is another common malicious tool that attackers often use to collect sensitive information and artifacts from a target. Spyware is used in many devices, including mobile devices, to collect artifacts. There is a lot of spyware that attackers use to collect information from target systems, including commercial spyware. SpyAgent is one of the most commonly used commercial spyware software, which can spy on a target system using an open or stealth method.
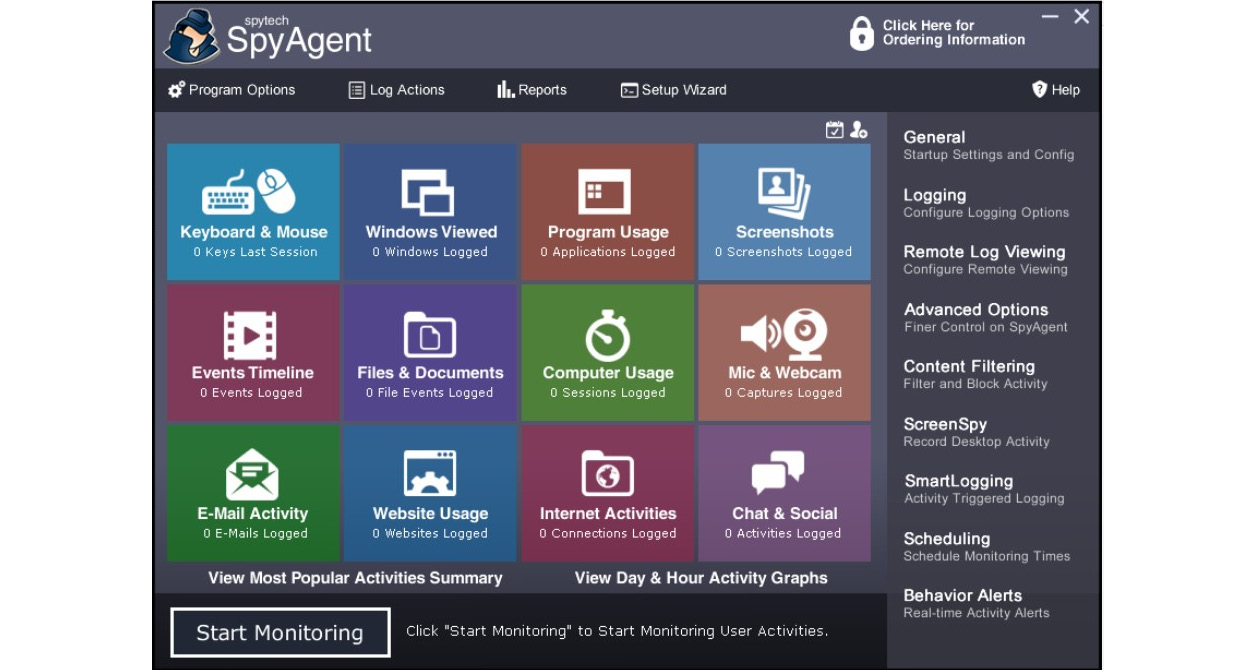
Figure 6.7 – SpyAgent can collect artifacts and information from the target and send them to the attacker
- As you can see from the preceding screenshot, Spytech SpyAgent can monitor a target system and extract information from the target to the attacker. This information includes keystrokes and mouse movements, windows accessed, program usage, screenshots, event timelines, access to files and folders, email and internet activities, and chats on social media. Attackers can also set advanced configurations, as shown in the following screenshot:

Figure 6.8 – SpyAgent advanced configuration that can be configured by the attacker
- If attackers want, they can run the program in stealth mode so that a victim will not have any idea that they are being spied on and monitored. This also includes remote log delivery and viewing; attackers can configure SpyAgent to send logs to a specific email address, File Transfer Protocol (FTP) location, or spyware cloud so that they can monitor them remotely. Attackers can block applications, chats, and specific web categories from a target system. Attackers can even use this tool to compromise credentials through keylogging and screenshots. Attackers will receive credentials and sensitive information by email or FTP accounts.
- SpyAgent introduced a feature called smart logging, which can log only special events, such as a user entering credentials, web addresses, and keywords. Once the attacker configures the schedule, SpyAgent sends emails at a scheduled time to them.
- Ransomware: This type of malware will encrypt important files when infected and make a ransom demand to release a key to unencrypt files. This is a very common type of attack these days, as attackers are more interested in quick financial gain from compromised systems.
- Compromised credentials: Usernames and passwords are the more common credentials used on many systems. Attackers are interested in collecting artifacts from systems using compromised credentials. Credentials can be lost, stolen, or exposed by other attacks, which attackers can use to access target systems. If the users are using weak credentials, guessable credentials, or compromised credentials, attackers can exploit the weak point. This includes system credentials, online web application credentials, and online services such as FTP credentials.
- Phishing and spear-phishing attacks: As discussed in previous chapters, attackers use sophisticated phishing attacks against individual users and companies mainly to compromise credentials.
- Session hijacking attacks: An attacker can take over a session established in client and server communication. In some attacks, the attacker steals the session ID and recreates it from their system, taking over the session without any usernames or passwords.
- Application-level attacks: Cross-site scripting and SQL injection are common application layer attacks that attackers use, especially crafter scripts or queries, to access sensitive information stored in a backend database connected to an application. If successful, the attacker even gets to control the database and the data stored in it.
Artifacts that competitors would like to collect
As discussed in the previous section, attackers are interested in collecting artifacts from you. These artifacts contain valuable information about you. These artifacts are used to find more information about targets. Some artifacts even contain the buying and surfing patterns of a user. For example, there are artifacts that keep information about most frequently visited websites, items of interest, and items purchased over the internet. For this reason, competitors are also interested in collecting artifacts from individuals and competitor companies. Mainly, they use cookies, known as third-party cookies, to collect information about competitors and individuals. If you understand how cookies work, then you can block and prevent disclosing your information as an individual or a company.
These tracking cookies can be categorized as direct web tracking cookies and third-party tracking cookies.
Direct web tracking cookies
Direct web tracking cookies are used to track visitor information and browsing information on a website directly. This helps to analyze visitors who return to the same website and their access behavior on the website. The cookies also track different pages that are visited on the same website. This allows website owners to provide a rich experience to web surfers when they visit the same website.
Third-party tracking cookies
Third-party cookies are not created by a website directly; typically, third-party cookies are created by an external server or service through embedded code on the original website. Third-party cookies are created by mass advertisers, by data analytics services, and through advertisements and plugins.
What can tracking cookies do?
As tracking cookies are typically used for advertising purposes, they collect data related to users’ web-browsing behavior. Tracking cookies can collect information, including the websites you visited, web pages accessed on each website, items that you were interested in, files you download, images that you click on, location information, and device-specific information. Companies and vendors can send you personalized advertisements using the data collected by tracking cookies. Typically, cookies are not as harmful as viruses or worms, and they cannot generally make your computer open to infection by other malware. This means they cannot tamper with the computing process, or the way a computer usually works. However, one danger is that attackers can design viruses and worms that look like innocent cookies.
Another concern is that internet service providers (ISPs) and large marketing companies can create extraordinary cookies that have additional capabilities compared to normal cookies. These cookies can even recreate themselves after being deleted. These cookies are generally inserted into HTTP headers by ISPs. They use these cookies to collect information about browsing patterns and activities. The main concern is that most users have no idea that these cookies are tracking all their online behavior and passing them to specific companies.
How to handle cookies
Every time you visit a website, the website will create at least one cookie on your browser. This cookie is known as a direct cookie. A cookie created by the website you visited will then remember all your basic activities on that website, including how long you stayed on a web page and the number of pages visited on the website. A direct cookie will not record information about any other websites that you visited. Information collected by the direct cookie is limited only to the website you visited.
Third-party cookies are different from direct cookies. If a third-party cookie is stored on your browser, it allows advertising companies, social media companies, ISPs, other websites, and many other service providers to track your online activities and browsing behaviors. Third-party cookies can be stored on your browser by many websites. This is a direct threat to your online privacy. In other words, if you are concerned about your online privacy, you must block third-party cookies.
We must block third-party cookies from our browser, so let’s see how. The settings can differ from browser to browser. However, all the popular browsers use similar options to block cookies, although the navigation and terminology can be a little different.
Disabling third-party cookies on Google Chrome
The default setting on Google Chrome is Block third-party cookies in Incognito According to Chrome, while in Incognito, “Sites can’t use your cookies to see your browsing activity across different sites, for example, to personalize ads. Features on some sites may not work.” (Refer to the following screenshot for reference.)
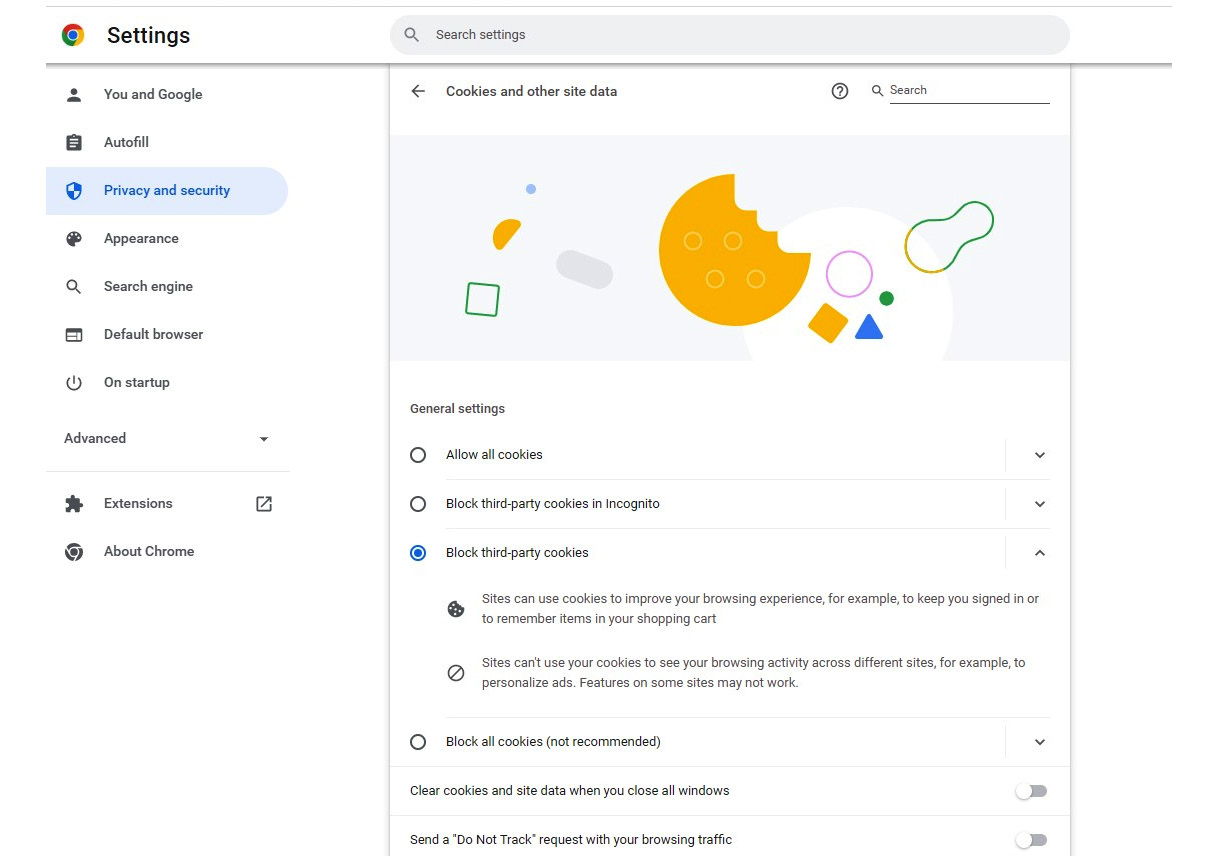
Figure 6.9 – Block third-party cookies in the Chrome browser
As a temporary solution for this, we can use the private browsing capabilities of the browser. Google Chrome has Incognito, Microsoft Edge has InPrivate browsing, and Mozilla Firefox provides Private Browsing. When you use a private browsing option to surf the internet, websites cannot use cookies to collect information of your browsing activities and personalized advertisements won’t work. However, even if you use private browsing, websites can still collect information, such as the IP addresses that you use to access the websites and the specification of the device that you are using.
Disabling third-party cookies on Microsoft Edge
You need to click the three dots in the top-right corner of Microsoft Edge and select Settings, then select Cookies and site permissions on the left menu, and click on the Cookies and data stored option. Third-party cookies are allowed by default. If you want to disable third-party cookies, you need to enable the switch next to the Block third-party cookies option.

Figure 6.10 – Blocking third-party cookies in the Microsoft Edge browser
Disabling third-party cookies on Mozilla Firefox
Similar to Microsoft Edge, you need to click on the three lines in the Firefox browser’s top-right corner, and then select the Preferences menu. You need to select Privacy & Security, and under the Enhanced Tracking Protection option, select Custom. Under the Cookies dropdown, select All third-party cookies. This will block all third-party cookies when you are using the Mozilla Firefox browser.

Figure 6.11 – Blocking third-party cookies in the Mozilla Firefox browser
Another option is to use secure browsers such as Brave, which was created by Brendan Eich, the founder of JavaScript, which provides total control over your own security and privacy. The Brave browser doesn’t collect user information by default, and it is privacy-focused. Brave is built on Chromium, which was a Google-initiated, open source project from which many other browsers, such as Vivaldi, Microsoft Edge, Opera, and Google Chrome, were created.
The Brave browser
The Brave browser was created from a Google-led, open source Chromium project. The Brave open source browser is developed by Brave Software. Brave was developed with privacy and security in mind. Its browser is faster than other popular browsers. When considering all the security aspects of popular web browsers, Brave is the best for all aspects of security as a browser. As an open source browser, Brave has many useful built-in security features, including ad blocking, script blocking, auto upgrades to HTTPS, blocks against third-party cookies and other storage, and blocks against user fingerprinting. The main advantage of Brave is that all its privacy features are configured by default, whereas with other browsers, users usually need to configure privacy features.

Figure 6.12 – Block trackers and ads in the Brave browser
As you can see in the preceding screenshot, Brave blocks all trackers and ads, and upgrades connections to HTTPS. If prefer, you can block scripts too. The preceding screenshot doesn’t show blocking scripts, as when blocking scripts is enabled, most of the trackers are also be removed. Apart from these capabilities, Brave also supports blocking or allowing advertisements based on content types.
Devices can be compromised
In today’s world, devices have many uses, with schoolkids to retired people all using devices for day-to-day activities. As well as individuals, most enterprises use devices to make their lives easy. Many users use multiple devices for different purposes. Devices range from workstations, laptops, and mobile devices to wearables, Internet of Things (IoT) devices, and assistant devices such as Alexa. These devices are primary targets for attackers. Even enterprise systems can be compromised through end devices, also known as endpoints. Due to this, a new approach was introduced for cyber security known as endpoint security. This protects endpoints from a range of attacks. The following list shows devices categorized as endpoints:
- Desktops
- Laptops
- Tablets
- Smartphones
- Servers
- IoT devices
- Point of Sales (PoS) devices
- Digital printers
- Smartwatches
- Assistant devices
Endpoints are important to monitor, as they can increase the attack surface and be an entry point for a corporate attack. Endpoints are easy targets for attackers, as users directly interact with endpoints. Information gathering and malware attacks are especially common at endpoints.
Let’s look at some of the common endpoint attack types:
- Theft of credentials
- Phishing and social engineering
- Malware attacks
- Stolen devices
- Ransomware attacks
- Compromising devices
Since the endpoint devices are smaller in size compared to typical devices, they are prone to physical theft quite easily. Once stolen, attackers can obtain information stored on the device and exploit the information if the device is not encrypted.
As we discussed earlier, malware attacks are another common way of compromising endpoint devices. Apart from malware, attackers use password dumpers to copy and steal saved passwords on systems. Once initial access is gained, an attacker can pull credentials from an endpoint. If it’s a Windows endpoint, the attacker can try to collect credentials from the following locations:
- Security Accounts Manager (SAM) file: This file is a self-contained database that exists in Windows systems from Windows XP onward. SAM databases authenticate users, locally and remotely, who provide credentials that match the credentials on the database. Many attackers steal this SAM database and try to decrypt it using multiple methods, including rainbow tables (tables with precomputed hashes). Attackers can dump this file using the fgdump, samdump, and pwddump tools.
- Local Security Authority (LSA): LSA is a service that manages authentication on a Windows system and a local security policy. When this service is running and active on a system, attackers can dump LSA secrets from the memory and acquire sensitive information from the memory dump. They create a memory dump from the LSA Subsystem Service (LSASS) from the target system.

Figure 6.13 – Creating a memory from the LSA process
The preceding figure shows the creation of a memory dump by an LSA process on a Windows system. Once the memory dump is created, attackers have multiple ways to steal the credentials. The most common way is by using mimikatz.
The following figure shows how an attacker retrieves credentials from a memory dump created by the LSASS process:

Figure 6.14 – The mimikatz dump password hash from the LSASS memory dump
- WDigest: Digest authentication is another authentication protocol used in Windows systems for Lightweight Directory Access Protocol (LDAP) and web authentication. This is a challenge-response protocol that keeps a plain text copy of the current user’s password when enabled. Even though this protocol is disabled by default on the latest Windows systems, attackers can still enable this to steal credentials.
- NTDS folder: This folder can be located in the Windows domain controller, which holds a local database of domain objects. If an attacker gets access to this directory, it is not that hard to acquire users, groups, and credential information of the domain.
- SYSVOL folder: This folder contains group policy configuration-related information, including what types of policies are enforced in the domain and configurations of the policies. For example, if a password policy is enforced, an attacker can see the minimum length of the password enforced, the maximum age of the password, and the minimum age of the password, which the attacker can fine-tune with password-cracking tools accordingly.
Ways that an attacker can access your networks
Compromising networks is another common avenue for attackers to access systems. Typically, networks provide connectivity to other entities – for example, your home network that connects you to the internet. Typically, ISPs connect you to the internet over a modem. In today’s world, the most commonly used network system for domestic requirements is Wi-Fi networks. There can be multiple devices connected to the same Wi-Fi network. Compared to wired networks, Wi-Fi networks have fewer risks.
Mainly, the coverage of a Wi-Fi network can go beyond your house or your premises. Wi-Fi networks use radio frequencies as a medium for transferring data. When you implement a Wi-Fi network, if the network range goes beyond your premises, anyone outside your premises can receive signals. Also, they can collect a lot of information, including the MAC address of the Wi-Fi device, the MAC addresses of the devices connected to the network, the number of devices connected, and active devices.
First, the attackers need an external Wi-Fi adapter to start Wi-Fi cracking; the reason for this is that most of the tiger boxes (operating systems with security and hacking tools installed for penetration testing), such as Kali Linux, Parrot Security, and Security Onion, run as virtual machines. For an attacker to crack Wi-Fi credentials, they need to monitor the signals first. In order to convert a Wi-Fi connection to monitoring mode, most of the cracking tools require a USB Wi-Fi adapter, although there are a few adaptors that are supported by these cracking tools.
The following is a list of Wi-Fi adapters fully compatible with Kali Linux, Security Onion, and Parrot Security:
- Alfa AWUS036NHA
- Alfa AWUS036NH
- Alfa AWUS036ACH
- Panda PAU06
- Panda PAU09
- TP-Link N150 TL-WN722N
Attackers will connect these Wi-Fi devices and start monitoring the networks. Some attackers even use high-gain antennas to receive signals from long distances. Once they start monitoring, they can collect information about targets.
Attackers use a range of techniques and tools to connect to target networks and gain access to them. Mainly, they use open source distributions such as Kali Linux and Parrot Security to crack target networks. They listen to the networks silently and collect information about the networks.
The following are some of the most used Wi-Fi cracking tools:
- Aircrack-ng
- Fern Wifi Cracker
- Kismet
- inSSIDer
- CoWPAtty
- AirJack
Once the external USB Wi-Fi adapter is connected, attackers can put the Wi-Fi adaptor into monitoring mode and monitor all surrounding Wi-Fi networks.
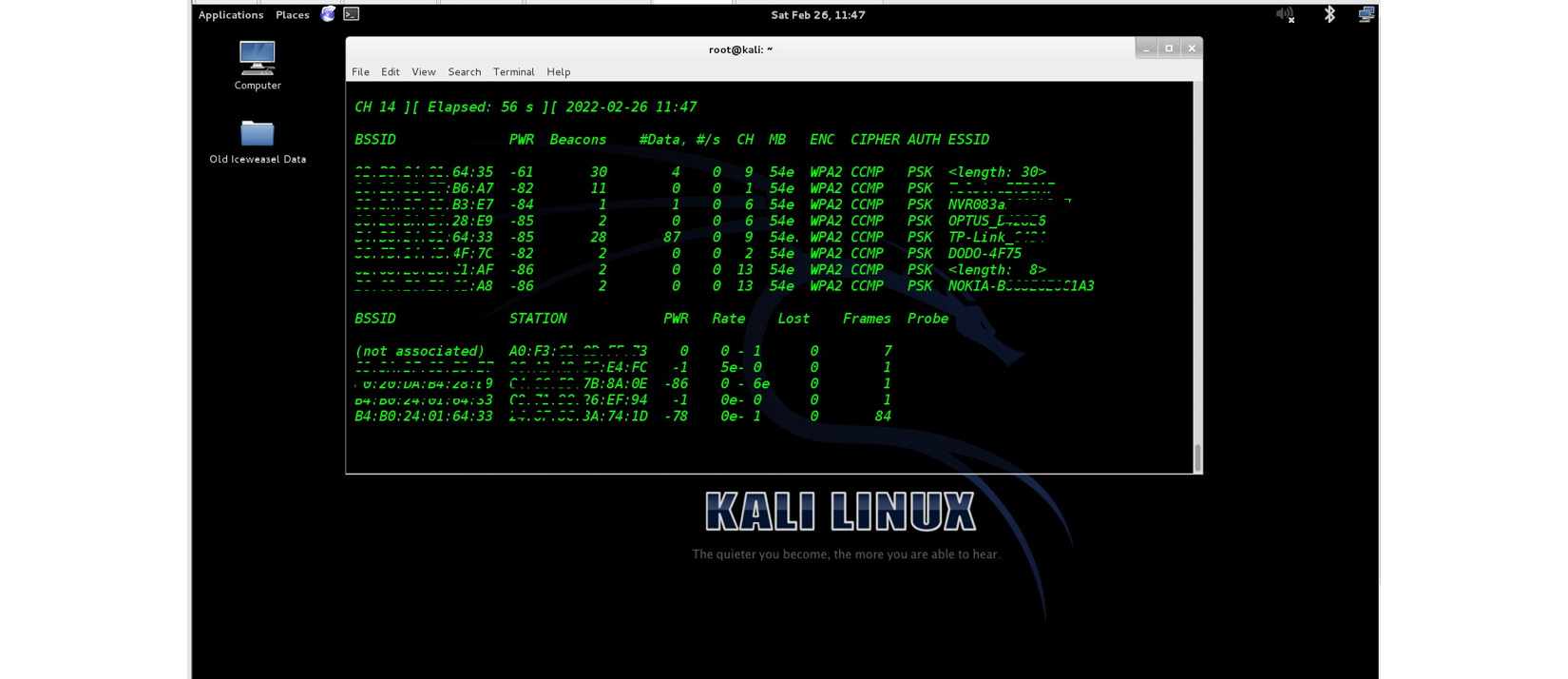
Figure 6.15 – Using the Aircrack-ng suite attacker to monitor all Wi-Fi networks within range
When an attacker starts monitoring, without even connecting to any of these networks, they can see a list of Wi-Fi networks within range, the signal strength, the number of data packets transmitted, the speed, the encryption type, the authentication type, and associated devices on each Wi-Fi network. From the list of surrounding Wi-Fi networks, the attacker selects the network they want to compromise and specifically collects information from the required network. When selecting a Wi-Fi network, the attacker must select from an active network, as they use data communicated between the access point and the connected devices to compromise the Wi-Fi network, depending on the encryption they use. Commonly used encryption types include Wired Equivalent Privacy (WEP), the oldest encryption protocol, which is less secure compared with the other available Wi-Fi encryption and is rarely used now; Wi-Fi Protected Access (WPA), which provides better encryption and user authentication than WEP; and Wi-Fi Protected Access 2 (WPA2), which provides better encryption, using the industry-standard Advanced Encryption Standard (AES). Recently, WPA-3 has been released, but most devices still connect using WPA2 encryption.
Depending on the encryption that is enabled on a network, attackers use different techniques to crack the Wi-Fi passwords of a target system. Once they crack the Wi-Fi password, they also can connect to the network and see the other connected devices and their communication. Sometimes, users think that when a network range is limited, attackers cannot access the network, as Wi-Fi signals are low. However, attackers can come equipped with high-gain antennas that allow them to receive signals from longer distances than users expect.
If a target network uses WEP encryption, attackers will try to collect a large number of communicated data packets (about 10,000 packets), and with the help of a wordlist, they can recover a Wi-Fi password. But when WPA2 encryption is used, an attacker can only find out the password using a four-way handshake. This is communication that happens between access points and a device before establishing a connection. The client device must produce an already configured key to the access point to authenticate. The attacker tricks this communication and intercepts the four-way handshake, which has information about the Wi-Fi key. Later, the attacker can crack this key offline using a wordlist or brute-forcing.
If attackers use aircrack-ng to crack Wi-Fi passwords, they open the terminal and execute the following commands:
- Iwconfig: When executed, this command will show attackers the number of network interfaces available including external Wi-Fi adaptors.
- ifconfig wlan0: When executed, this command will show information about the wlan0 interface; if it is different, you need to change the interface accordingly from the information collected from the previous command.
- airmon-ng start wlan0: This command creates a monitoring mode using the wlan0 Wi-Fi interface.
- Mairodump-ng mon0: When executed, this command will display the available Wi-Fi networks in the range. Then, attackers can select which network they want to compromise.
- airodump-ng -w ourfile --bssid 58:6D:8F:XX:XX:XX mon0: This command starts writing data to a file called ourfile, but only from the specified network access point (bssid specifies the MAC address of the access point, collected from the previous command).
Cloned session
While an attacker captures data communicated from an access point, they can start another terminal to initiate a four-way handshake so that it will be captured and written to the file by another running terminal. The following command is executed on a different terminal while the other terminal is running:
aireplay-ng --deauth 5 -a 58:6D:8F:A0:5B:16 mon0This command sends de-authentication (a request to perform a four-way handshake) requests, spoofing the attacker’s MAC address as an authentic access-point MAC address. Once this is successfully performed, other devices that are connected to the Wi-Fi network will perform a four-way handshake with the access point and be captured as ourfile.
When the attacker captures the four-way handshake successfully, the last step is to decrypt the four-way handshake to find the Wi-Fi key. This is performed by aircrack-ng, as shown here:
aircrack-ng ourfile-01.cap -w /pentest/passwords/wordlists/darc0de.lstThis command will crack the Wi-Fi password from the captured ourfile-01.cap file with the help of a word list at /pentest/passwords/wordlists/darc0de.lst, or the attacker can use their own wordlist files. There are also free online services available to decrypt a four-way handshake once it is captured to a file.
If communication is over unencrypted protocols, attackers can sniff the network and collect information from the communication. Typically, HTTP, FTP, Telnet, SMTP, and SNMP are unencrypted protocols that communicate using unencrypted plain text. If any credentials are sent over a network, attackers can collect credentials easily. Since Wi-Fi networks with modern protocols don’t broadcast information, attackers will not receive all the communication, even if they are connected to the target network. Then, attackers use Address Resolution Protocol (ARP) poisoning attacks to collect desired information from the target computer.
One of the most commonly used tools is Cain & Abel, which can perform ARP poisoning and collect credentials sent over a network.

Figure 6.16 – Using the Cain & Abel attacker to capture data sent through unencrypted protocols
Now that we have seen the ways attackers can access our networks, let us see more details about how our information can be compromised by browsers.
Compromising browsers
The second topic of this chapter discussed how cookies are stored in the browser and can collect your information, especially the way third-party cookies will collect information about you. Apart from how cookies collect your information, your browsers keep heaps of other information. Importantly, if an attacker gets access to your computer, they can access and review your online habits, behaviors, and sensitive information. As well as attackers, many web applications can collect this information, using third-party cookies.
Let’s look at the information that a browser reveals about you:
- Web history and cached data: Most of the popular browsers provide a history feature. This feature is important if you accidentally or deliberately close a web page and forget the URL – it can be your savior. On the other hand, think about privacy. As the browser history keeps information about every single web page you visited, if anyone gets access to your device, it can reveal every single web page you have accessed.
Most browsers today create profiles for you. At face value, this is an exciting feature, as irrespective of the device, users can access the same information if they use the same profile of the browser on a different device. However, what about privacy? If any single device is compromised, an attacker can access all the information that the browser is storing, even if the user has deleted it from the local browser.
Let’s take Google Chrome as an example. Since Chrome is from Google, users don’t have to create an additional profile or account; they can use their existing Google account instead. If the user is logged in to their Google account while using the Chrome browser, it keeps track of all the information in their Gmail profile. You can try this by accessing https://myactivity.google.com/:

Figure 6.17 – My Google Activity keeps all the information related to your search history
This shows how much data Google collects from users and keeps within their profiles. If you analyze a single search item that is saved in the My Google Activity section in your Google account, you will understand more about how much data that browser can collect. From the items that are listed under My Google Activity, let’s click on the Details link on an item and see how much information Google keeps about that item.

Figure 6.18 – Google keeps information about every item searched
As the preceding screenshot shows, Google keeps track of the search keyword, the type of search, device information, and the location of each search item.
As well as Google Chrome, the most popular browsers do the same. They also keep track of a lot of information about each search that you performed.
Browsers also keep the cached information. Cache refers to the contents that are stored in the browser from previously accessed websites. A cache provides faster access and loads web pages much faster. But from a privacy point of view, if anyone has access to the device, they can also access a cache quite easily and acquire information that you would not want anyone to see. To access a cache, you can type chrome://cache in the Google Chrome browser address bar or about:cache in Mozilla Firefox.
There are some tools that retrieve cached information from browsers. You can download some tools from https://www.nirsoft.net/ to retrieve cached data. The following are some of the tools that can retrieve cached data from browsers:
- ChromeCacheView: Retrieve cached contents from Google Chrome:
Figure 6.19 – ChromeCacheView to retrieve cached information from Google Chrome
- IECacheView: Retrieve cached contents from Internet Explorer.
- MZCacheView: Retrieve cached contents from Mozilla Firefox.
- VideoCacheView: If you watch a video on a browser, this utility can automatically search videos cached in Chrome, Firefox, Internet Explorer, and Opera and can save the video to another folder.

Figure 6.20 – VideoCacheView can search videos cached in various browsers
From https://www.nirsoft.net/, you can download and test a range of tools that can be useful to retrieve information from browsers. Even though these tools are GUI-based tools, they also support command-line scripting. Attackers use these tools to alter the scripts or create AutoRun files (when attackers create AutoRun files, they will automatically get executed when an event is triggered) that will automatically execute and write important information to a text file.
For example, MyLastSearch is a small free utility that can be downloaded from the same site that scans the cache and history files on the target web browser, and it can also collect your search queries executed in popular search engines, such as Google and Yahoo. If you want to include this in a script, you can easily write a script with the following:
- MyLastSearch.exe /stext <FileName>: This will save the located search queries in a text file.
- MyLastSearch.exe /scomma <FileName>: This will save the located search queries in a comma-separated file.
- MyLastSearch.exe /shtml <FileName>: This will save the located search queries in an html file.
- Cookies: Cookies collect information about the user, devices, and other information, as we discussed in the second topic of this chapter.
- Bookmarks: You may be wondering what an attacker can do with your bookmarks. If you access the bookmark manager built into your browser, you will realize that it not only keeps shortcuts to your financial websites, banks, and insurance websites but also very specific login information. For example, when you save a website login as a bookmark, some web applications generate a very specific URL for you to log in to the application securely. When we save it as a bookmark, we save the special link generated by the web application as a shortcut. If an attacker discovers you are with a specific bank (which can be collected from your bookmarks or favorites) and your email address, it’s just a matter of stealing a password, which can be easily done by creating a phishing website, as the attacker already knows the bank that you are with. Let’s go to the bookmark manager of the browser and click on any of the saved web logins, go to More Actions (or right-click), and then click Edit:

Figure 6.21 – Bookmarks keep special URLs generated by web applications
As you can see from the preceding screenshot, this user has saved a financial institution’s login URL, but when the user saved the login, it also saved a specially crafted URL generated by the web application. This could be to validate the device or a trustworthy user. If an attacker uses the same link, the application might accept the attacker as a trustworthy device or user.
- Browser extensions: Most of the popular browsers support extensions to enhance their capabilities. These extensions were created by companies and individuals. Most of the extensions are legitimate, but can we be sure that they all are? As extensions are connected to a browser, they also have access to most of the functions of the browser. Even without our knowledge, these extensions can collect sensitive information.
Most of the extensions are free, but we never know what the real intention of the extension is. It might look like a very useful extension, but under the hood, what does it really do?
Microsoft SysInternals has an interesting set of freeware for different purposes. If you download TCPView, which is a lightweight free tool, it will show you what the connections are that were created by your device. If the process creates any connections from your browser to suspicious remote addresses, you can monitor using TCPView.
Figure 6.22 – TCPView will show the connection information
This is a useful tool to monitor the connection status from a device to remote addresses. This tool shows the list of current processes and the connections created and initiated by different processes. If the browser extension creates suspicious links to remote addresses, you can review them using this tool.
The best practice is not to use any of these extensions. But if you really want to use an extension, it is better to assess and monitor before you start to use any extension, as we never know the real intention of the developer. As discussed, most of the extensions are legitimate, but there can be extensions developed with malicious intent.
Summary
This chapter focused on the different artifacts that attackers collect from target users and companies. As well as attackers, competitors collect large amounts of information from you. Attackers target devices to collect information using different approaches. Devices collect and keep various information about users and their activities. When a device is compromised, attackers will have access to this information. We also looked at the ways attackers compromise networks. Finally, we discussed the ways attackers compromise browsers and the types of information that can be collected from the browsers.
In the next chapter, we will explain what cyber anonymity is and its different levels, as well as the difference between privacy and anonymity. We will also explain the best practices to maintain cyber anonymity. Cyber anonymity is not something that you might have to do only once, but you need to develop a cyber-anonymity mindset to properly maintain cyber anonymity and face the various types of privacy-related attacks.
