Broadcast receivers often hold useful information about an application's attack surface and could offer attackers the opportunity to do many things, from performing arbitrary code execution to proliferating information; because of this, they cannot be ignored during an application-focused security assessment. The drozer developers were well aware of this fact and provided modules to help gain information about broadcast receivers.
The following recipe demonstrates the app.broadcast.info module by detailing its different invocation options.
The enumeration of broadcast receivers is performed using the following command:
dz> run app.broadcast.info
The output for the previous command should be similar to the following screenshot:
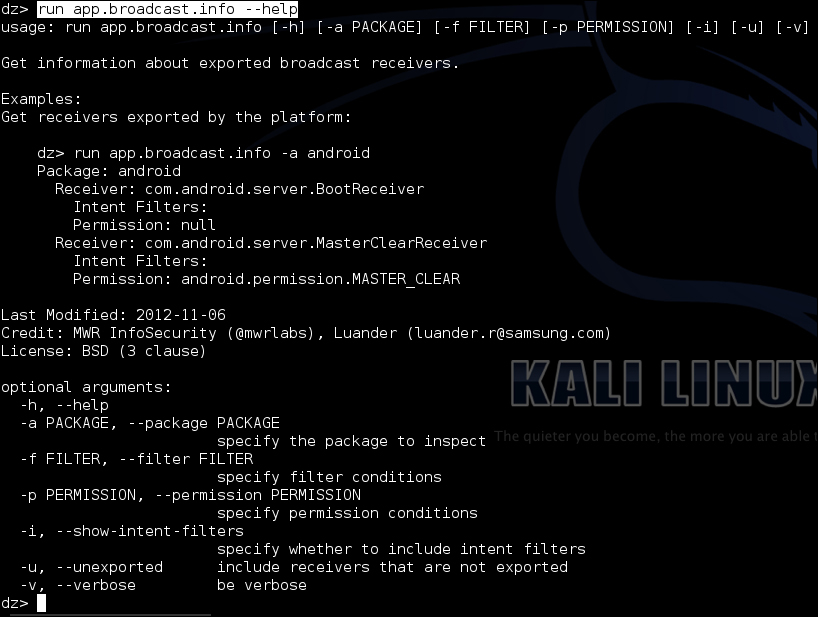
This app.broadcast.info module has all the cool features the other .info modules have and some more broadcast-receiver-specific options.
You can specify a specific package from which to extract information on receivers; the following command is an example:
dz> run app.broadcast.info –a [package]
The command that follows is another example:
dz> run app.broadcast.info –-package [package]
You can also search and list broadcast receivers based on their names; for example:
dz> run app.broadcast.info –f [filter]
Or use the longer form:
dz> run app.broadcast.info –-filter [filter]
Another option is to choose to include the unexported receivers:
dz> run app.broadcast.info –u dz> run app.broadcast.info –-unexported
And lastly, you can choose whether to include the intent filters in the requested information; for example:
dz> run app.broadcast.info –i
Or:
dz> run app.broadcast.info –-show-intent-filters
- The BroadcastReceivers – Android Reference webpage at http://developer.android.com/reference/android/content/BroadcastReceiver.html
- The drozer Source broadcast.py module at https://github.com/mwrlabs/drozer/blob/master/src/drozer/modules/app/broadcast.py
