During your application security assessments, you may want to know what the attack surface of a given application is. drozer has a really neat module that helps you determine just that. In terms of this module, the attack surface for an application is simply the number of exported components.
Execute the following command from your drozer console:
dz> app.package.attacksurface [package name]
This command will list all the exported activities for a given package as determined by the package manager API.
As an example, you could try running it against a sample package as follows:
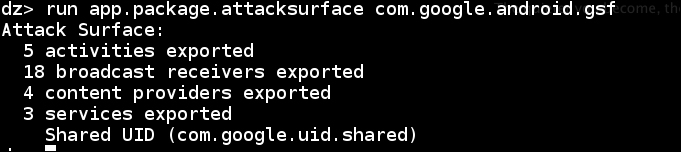
Let's take a look at the app.package.attacksurface module code. I think this is probably one of the most interesting modules, and walking through its code should spark some ideas on how to write automated testing tools in the form of applications. It will most certainly come in handy when you want to do mass automated application scanning!
The code from drozer-master/src/mrw/droidhg/modules/package.py is as follows:
from drozer import android
from drozer.modules import common, Module
class AttackSurface(Module,common.Filters, common.PackageManager):
def execute(self,arguments):
If arguments.package != None:
Package = self.packageManger().getPackageInfo(arguments.package, common.PackageManager.GET_ACTIVITIES | common.PackageManager.GET_RECEIVERS | common.PackageManager.GET_PROVIDERS | common.PackageManager.GET_SERVICES)
application = package.applicationInfo
activities = self.match_filter(package.activities, 'exported',True)
receivers = self.match_filter(package.receivers, 'exported', True)
providers = self.match_filter(package.proviers, 'exported', True)
services = self.match_filter(package.services, 'exported', True)
self.stdout.write("Attack Surface:
")
self.stdout.write(" %d activities exported
" % len(activities))
self.stdout.write(" %d broadcast receivers exported
" % len(receivers))
self.stdout.write(" %d content providers exported
" % len(providers))
self.stdout.write(" %d services exported
" % len(services))
if (application.flags & application.FLAG_DEBUGGABLE) != 0:
self.stdout.write("is debuggable
")
if package.sharedUserId != None:
self.stdout.write("Shared UID (%s)
" % package.sharedUserId)
else:
self.stdout.write("Package Not Found
")A lot of code here, but what's great about this module is that it follows the same style as the rest by interfacing the package manager. The module pulls information about services, activities, broadcast receivers, and content providers from the package manager and simply tries to determine whether they are exported according to the package manager. Determining which of the components are exported, it simply enumerates them and prints a count of the number of exported components on the screen. The thing the module does is it tries to determine whether the app is debuggable and whether it uses a shared user ID, which is very valuable information with regards to the attack surface. I'll explain why in the next chapter.
- The drozer Source broadcast.py module at https://github.com/mwrlabs/drozer/blob/master/src/drozer/modules/app/package.py
